Full Description
advertisement
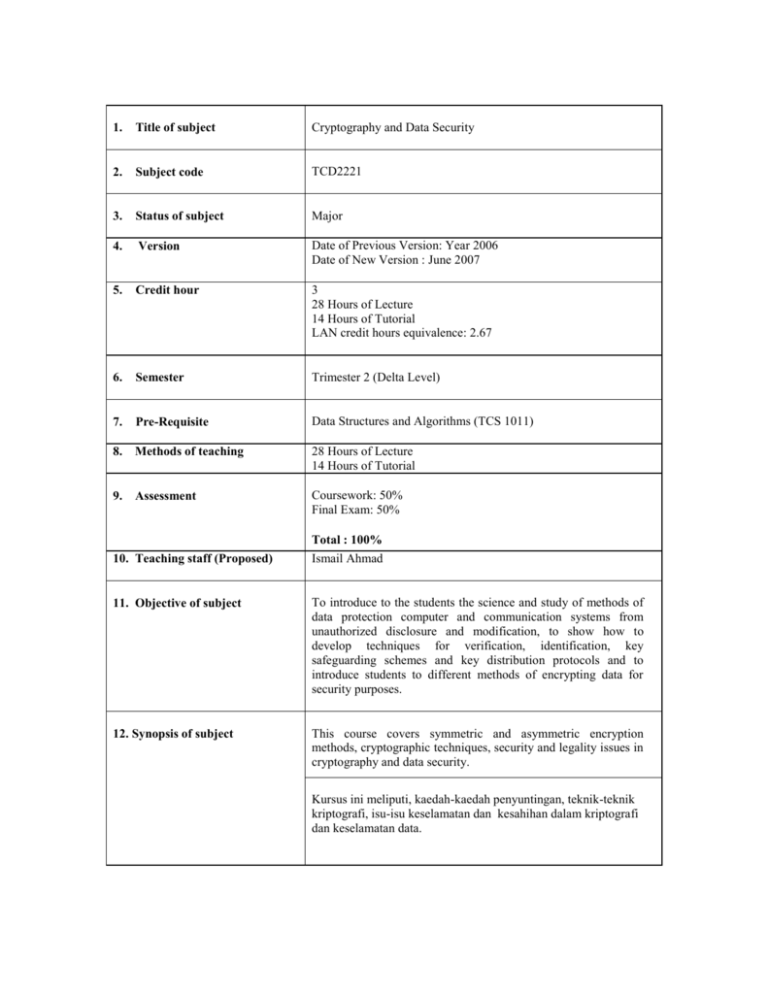
1. Title of subject Cryptography and Data Security 2. Subject code TCD2221 3. Status of subject Major 4. Version Date of Previous Version: Year 2006 Date of New Version : June 2007 5. Credit hour 3 28 Hours of Lecture 14 Hours of Tutorial LAN credit hours equivalence: 2.67 6. Semester Trimester 2 (Delta Level) 7. Pre-Requisite Data Structures and Algorithms (TCS 1011) 8. Methods of teaching 28 Hours of Lecture 14 Hours of Tutorial 9. Assessment Coursework: 50% Final Exam: 50% Total : 100% 10. Teaching staff (Proposed) Ismail Ahmad 11. Objective of subject To introduce to the students the science and study of methods of data protection computer and communication systems from unauthorized disclosure and modification, to show how to develop techniques for verification, identification, key safeguarding schemes and key distribution protocols and to introduce students to different methods of encrypting data for security purposes. 12. Synopsis of subject This course covers symmetric and asymmetric encryption methods, cryptographic techniques, security and legality issues in cryptography and data security. Kursus ini meliputi, kaedah-kaedah penyuntingan, teknik-teknik kriptografi, isu-isu keselamatan dan kesahihan dalam kriptografi dan keselamatan data. By the end of the subject, students should be able to: 13. Learning Outcomes Understand the concepts and the fundamentals of encryption methods. Able to understand and work with different encryption methods. Understand the different cryptographic techniques. Programmes Outcomes % of contribution 5 Ability to apply soft skills in work and career related activities 35 Good understanding of fundamental concepts Acquisition and mastery of knowledge in specialized area 20 20 Acquisition of analytical capabilities and problem solving skills Adaptability and passion for learning 5 5 Cultivation of innovative mind and development of entrepreneurial skills Understanding of the responsibility with moral and professional ethics 14. Details of subject 1. 10 Topics Covered Hours Introduction Definition of the Cryptographic System: Encryption & Decryption, Symmetric & Asymmetric Ciphers Background History of Cryptography Steganography Message Security Threats: Passive & Active attacks Types of Cryptanalytic Attacks (ciphertext only, known plaintext, chosen plaintext, chosen ciphertext, chosen text) The goals of cryptography and data security: Confidentiality, Integrity, Authenticity 3 2. 3. 4. 5. 6. Symmetric Encryption Brief Introduction to Symmetric Key Encryption Model Classical ciphers: Transposition ciphers, Substitution ciphers, Knapsack ciphers Product Cipher: DES and triple DES, brief introduction to AES Symmetric Block Cipher Characteristics: Block Cipher Modes of Operations (ECB, CBC, CFB, CTR, OFB). Stream Cipher and One-Time Pads (Perfect Secrecy). Number Theory Modular Arithmetic Prime Numbers Greatest Common Divisor (GCD) Multiplicative Inverse Fermat’s Little Theorem Euler Totient Function Euler’s Theorem Asymmetric Encryption Brief Introduction to the Asymmetric Key Encryption Model Asymmetric (Public-Key) Encryption Characteristics Public Key Encryption: RSA Authentication Password Authentication, Message Authentication Code (MAC) properties and basic uses of MAC Hash properties and basic uses of hash Brief Introduction to the Digital Signature Model and Threats to Digital Signatures (i.e. Replay Attacks) Key Distribution, Key Management & Digital Certificates Brief introduction to Key Distribution Methods Simple Key Distribution (Merkle) Key Management Diffie-Hellman Key Exchange Public Key Infrastructure (PKI): Public Key Certificates, Certificate Authority (CA) & Certificate Servers Total Contact Hours 1. 15. Text Text books 2. 8 4 3 5 5 28 William Stallings, Cryptography and Network Security - Principles and Practices, 4th Edition, Prentice Hall.ISBN:0-13-111502-2 (2006). Atul Kahate, Cryptography and Network Security, McGraw-Hill, ISBN:0070494835 (2003) References 1. 2. 3. WadeTrappe, Lawrence Washington, Introduction to Cryptography with Coding Theory, Second Edition, Prentice Hall.ISBN : 0-13-186239-1 (2006) Bruce Schneier, Applied Cryptography, 2nd Edition Protocols, Algorithms and Source Code in C,John Wiley & Sons.ISBN:0-471-12845-7 (1996) Josef Pieprzyk,Thomas Hardjono,Jennifer Seberry, Fundamentals of Computer Security, Springer-Verlag.ISBN: 3-540-43101-2 (2003)





















