acheck-week3
advertisement

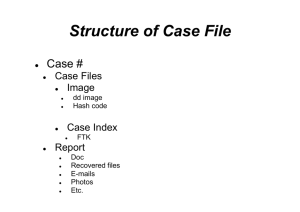
COS 397 - Computer Forensics Attendance Check - Week 03 – 1 Name: _____Nikolai Ladokhin_______________________ID: 100080857 Answer the following questions: 1. What are some reasons that an employee might leak information to the press? One of the reasons could be a pursuit of personal gain, financial or of other kinds. It also might be advantageous for them to make certain company information private. 2. What name refers to labs constructed to shield EMR emissions? TEMPEST 3. Name the three formats for computer forensics data acquisitions. Raw format Proprietary format Advanced Forensic Format 4. What are two advantages and disadvantages of the raw format? Advantages: Raw format allows comparably faster data transfer speed, plus some minor data errors can be ignored Most forensic tools are capable of reading raw format Disadvantages: It requires equal, or even bigger disk space for storage It doesn’t contain hash values in the file 5. Corporate investigations are typically easier than law enforcement investigations for which of the following reasons? a. Most companies keep inventory databases of all hardware and software used. 6. What are the three rules (characteristics) for a forensic hash? It can’t be predicted It’s not possible for two files to have the same hash-value If a file changes, so does its hash-value 7. Find on the Internet On-line Hash Generator for MD5, SHA1 and SHA256. Provide the links: MD5 - http://www.adamek.biz/md5generator.php SHA1 - http://online-code-generator.com/sha1-hash-withoptional-salt.php SHA256 - http://www.xorbin.com/tools/sha256-hashcalculator Try creating MD5 hash of a short file and of a simple English word. Copy/paste here the word and its MD5 hash. Conspiracy (MD5: 62690a95c6fbc88af4490ae89922fef4) 8. Find on the Internet some "hash decrypters". Provide the link - http://www.md5online.org/ Test this decrypter with the MD5 hash of the word from step 3. Does it work? Yes Add to this word one space at the end, calculate again MD5 hash and try to "decrypt" the hash again. Does it work again or no? 9. Explain in your view how do such hash "decrypters" work. 10. Why the hash "decrypter" doesn't work for more than one word?