Chapter 6. Modern Block Ciphers (Part 2)
advertisement
Chapter 6. Modern Block Ciphers (Part 2)
RC5 Encryption
1.
2.
3.
RC5 uses 3 primitive operations and their inverses:
Addition modulo 2w - +
XOR -
Left circular shift denoted by x<<<y, where word x is rotated y bits.
Right circular shift is denoted by x>>>y.
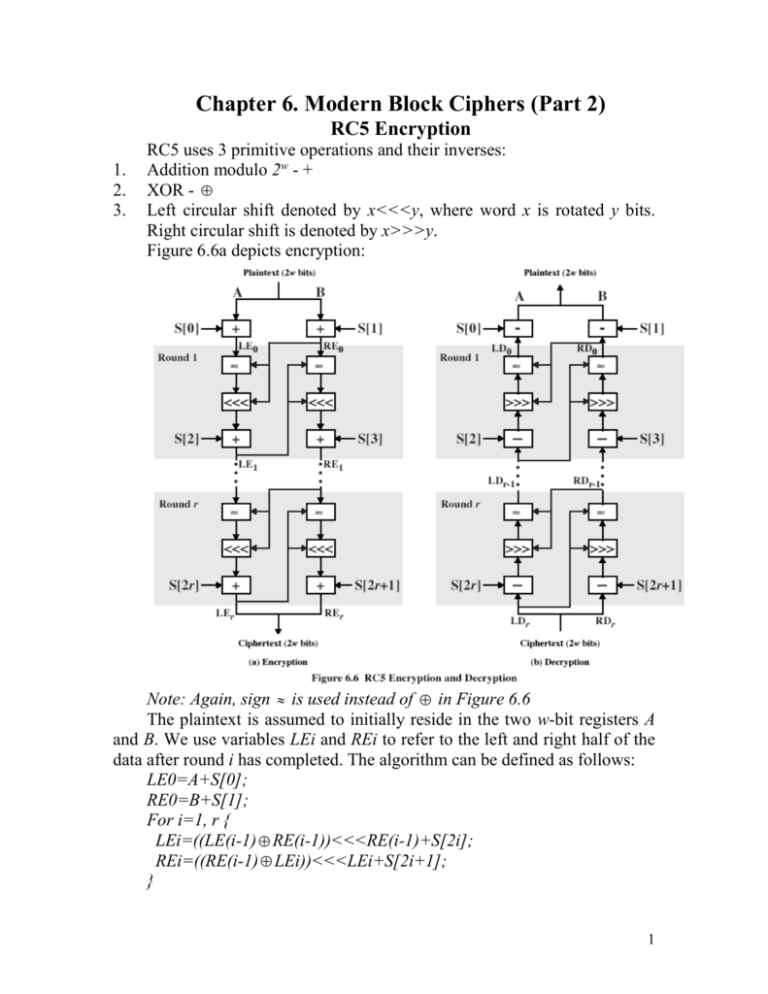
Figure 6.6a depicts encryption:
Note: Again, sign is used instead of in Figure 6.6
The plaintext is assumed to initially reside in the two w-bit registers A
and B. We use variables LEi and REi to refer to the left and right half of the
data after round i has completed. The algorithm can be defined as follows:
LE0=A+S[0];
RE0=B+S[1];
For i=1, r {
LEi=((LE(i-1) RE(i-1))<<<RE(i-1)+S[2i];
REi=((RE(i-1) LEi))<<<LEi+S[2i+1];
}
1
RC5 Encryption (Cont 1)
The resulting cipher-text is contained in LEr and REr. Note that both
halves of data are updated each round.
Decryption
Decryption, shown in Figure 6.6b, is easily derived from the encryption
algorithm. In this case, the 2w bits of cipher-text are represented by LDr and
RDr. We use LDi and RDi to refer to the left and right half of data before
round i has begun, where rounds are numbered from r down to 1:
For i=r downto 1{
RD(i-1)=((RDi-S[2i+1])>>>LDi) LDi);
LD(i-1)=((LDi-S[2i])>>>RD(i-1)) RD(i-1));
}
B=RD0-S[1];
A=LD0-S[0];
RC5 Modes
RFC 2040 defines 4 different modes of operation:
RC5 block cipher: 2w plaintext -> 2w cipher-text
RC5-CBC (Cipher Block Chaining) – repeated plaintext blocks produce
different cipher-text blocks (total length is a multiple of 2w)
RC5-CBC-Pad – handles plaintext of any length by padding extra
symbols to have length as multiple of 2w. The pad bytes are all the same and
are set to byte that represents the number of padded bytes. For example, if
the are 8 bytes of padding, each byte has the pattern 0000 1000.
RC5-CTS – cipher-text stealing mode, which is also a CBC style of the
algorithm. This mode handles plaintext of any length and produces ciphertext of equal length.
Padding may not always be appropriate. For example, one might wish
to store the encrypted data in the same memory buffer that originally
contained the plaintext. In that case, the cipher-text must be the same length
as the original plaintext. The RC5-CTS mode provides this capability
(Figure 6.7).
2
RC5 Modes (Cont 1)
Assume that the last block of plaintext is only L bytes long, where
L<2w/8. The encryption sequence is as follows:
1. Encrypt the first (N-2) blocks using the traditional CBC technique.
2. XOR P(N-1) with the previous cipher-text block C(N-2) to create
Y(N-1)
3. Encrypt Y(N-1) to create E(N-1)
4. Select the first L bytes of E(N-1) to create C(N)
5. Pad P(N) with zeros at the end and XOR with E(N-1) to create
Y(N).
6. Encrypt Y(N) to create C(N-1)
The last two blocks of cipher-text are C(N-1) and C(N).
Characteristics of Advanced Symmetric Block
Ciphers
Modern ciphers are similar to Feistel cipher but have such features
as:
Variable key length,
Mixed operators
Data dependent rotation
Key-dependent S-boxes
3
Characteristics of Advanced Symmetric Block
Ciphers (Cont 1)
Lengthy key schedule algorithm – generation of sub-keys may be
much longer than a single encryption or decryption – this makes effort
for brute-force attack greatly magnified
Variable plaintext/cipher-text block length
Variable number of rounds
Operation on both halves of data
Variable F
Key-dependent rotation
Stream Ciphers
A typical stream cipher encrypts plaintext byte by byte, although a
stream cipher may be designed to operate on a bit at a time or on units
larger than a byte at a time. Figure 6.8 is a representative diagram of
stream cipher structure:
The stream cipher is similar to the one-time pad discussed in chapter
2. The difference is that a one-time pad uses a genuine random number
stream, whereas a stream cipher uses a pseudo-random number stream.
Pseudo-random generators should provide:
- long enough period of encryption sequence
- approximate the properties of a true random number stream
(e.g., there should be approximately equal number of 1’s and 0’s)
4
Stream Ciphers (Cont 1)
- a key length of at least 128 bits is desirable
With a properly designed pseudorandom number generator, a stream
cipher can be as secure as block cipher of comparable key length. The
primary advantage of a stream cipher is that stream ciphers are almost
always faster and use far less code than do block ciphers. RC4 can be
implemented in just a few lines of code. Table 6.2 compares execution
times of RC4 with three well-known symmetric block ciphers
RC4
RC4 was designed by Ron Rivest in 1987 for RSA Security. The
algorithm is based on the use of a random permutation. Analysis shows
that the period of the cipher is greater than 10100. It is used in SSL/TLS (
Secure sockets Layer/ Transport Layer Security) standards that have been
defined for communications between Web browsers and servers. It is also
used in WEP (Wired Equivalent Privacy) protocol that is part of the IEEE
802.11 wireless LAN standard. RC4 was kept as a trade secret by RSA
Security. In September 1994, the RC4 algorithm was anonymously
posted on the Internet on the Cypherpunks anonymous remailers list. A
variable-length key of from 1 to 256 bytes is used to initialize a 256-byte
state vector S, with elements S[0], S[1],.., S[255]. At all times S contains
a permutation of all 8-bit numbers from 0 to 255. For encryption and
decryption, a byte k (see Figure 6.8) is generated from S by selecting one
of the 256 entries in a systematic fashion. As each value of k is generated,
the entries in S are again permuted.
Initialization of S
To begin, entries of S are equal to the values from 0 to 255 in ascending
order; that is, S[i]=i, i=0,..,255. A temporary vector, T, is also created. If the
length of the key K is 256 bytes, then K is transferred to T. Otherwise, for a
5
Initialization of S (Cont 1)
key of length keylen bytes, the first keylen elements of T are copied from K
and then K is repeated as many times as necessary to fill out T. These
preliminary operations can be summarized as follows:
/*Initialization*/
for i=0, 255{
S[i]=i;
T[i]=K[i mod keylen];
}
Next we use T to produce the initial permutation of S. This involves
starting with S[0] and going through to S[255], and, for each S[i], swapping
S[i] with another byte in S according to scheme dictated by T:
/*Initial permutation of S*/
j=0;
for i=0,255{
j=(j+S[i]+T[i]) mod 256;
swap(S[i], S[j]);
}
Because the only operation on S is a swap, the only effect is a
permutation. S still contains all the numbers from 0 to 255.
Stream Generation
Once the vector S is initialized, the input key is no longer used. Stream
generation involves starting with S[0] and going through to S[255], and, for
each S[i], swapping S[i] with another byte in S according to a scheme
dictated by the current configuration of S. After S[255] is reached, the
process continues, starting over again at S[0]:
/*Stream generation*/
i=j=0;
while (true){
i=(i+1) mod 256;
j=(j+S[i]) mod 256;
Swap(S[i], S[j]);
t=(S[i]+S[j]) mod 256;
k=S[t];
}
To encrypt, XOR the value of k with the next byte of plaintext. To
decrypt, XOR the value of k with the next byte of cipher-text.
Figure 6.9 summarizes the RC4 logic:
6
Stream Generation (Cont 1)
7