Data Hiding in Motion Vectors of Compressed Video Abstract
Data Hiding in Motion Vectors of Compressed Video
Based on Their Associated Prediction Error
Abstract:
This paper deals with data hiding in compressed video. Unlike data hiding in images and raw video which operates on the images themselves in the spatial or transformed domain which are vulnerable to steganalysis, we target the motion vectors used to encode and reconstruct both the forward predictive (P)frame and bidirectional (B)-frames in compressed video. The choice of candidate subset of these motion vectors are based on their associated macro block prediction error, which is different from the approaches based on the motion vector attributes such as the magnitude and phase angle, etc. A greedy adaptive threshold is searched for every frame to achieve robustness while maintaining a low prediction error level. The secret message bit stream is embedded in the least significant bit of both components of the candidate motion vectors. The method is implemented and tested for hiding data in natural sequences of multiple groups of pictures and the results are evaluated. The evaluation is based on two criteria: minimum distortion to the reconstructed video and minimum overhead on the compressed video size.
Based on the aforementioned criteria, the proposed method is found to perform well and is compared to a motion vector attribute-based method from the literature.
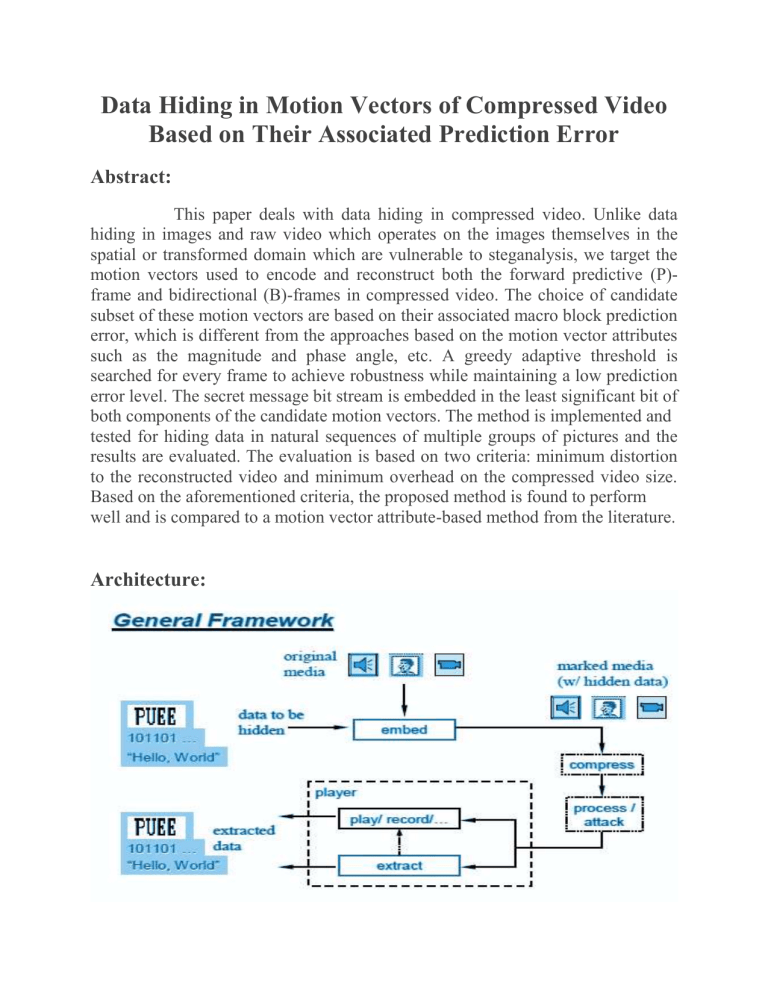
Architecture:
Existing System:
D ATA hiding and watermarking in digital images and raw video have wide literature. In case the data is extracted, it will be encrypted. But still there is a chance that the intruder can break the code.
However, we find that in most existing approaches, the choice of embedding positions within a cover image mainly depends on a pseudorandom number generator without considering the relationship between the image content itself and the size of the secret message.
Disadvantages:
We find that the existing PVD (Pixel value differentiation)-based approaches cannot make full use of edge information for data hiding, and they are also poor at resisting some statistical analyses.
Proposed System:
We expand the LSB matching revisited image steganography and propose an edge adaptive scheme which can select the embedding regions according to the size of secret message and the difference between two consecutive pixels in the cover image.
For lower embedding rates, only sharper edge regions are used while keeping the other smoother regions as they are. When the embedding rate increases, more edge regions can be released adaptively for data hiding by adjusting just a few parameters.
Advantages:
The proposed method is found to have lower distortion to the quality of the video and lower data size increase.
Modules:
1.
Image Steganography
Analysis the image
JPEG Frame
MPEG Frame
Data hiding through image
2.
Video Compression
3.
Motion Vector of Video
1.
Image Steganography:
We have chosen this stage because its contents are processed internally during the image encoding/ decoding which makes it hard to be detected by image steganalysis methods and is lossless coded, thus it is not prone to quantization distortions. In the literature, most work applied on data hiding in motion vectors relies on changing the motion vectors based on their attributes such as their magnitude, phase angle, etc. The data bits of the message are hidden in some of the image whose magnitude is above a predefined threshold. A single bit is hidden in the least significant bit of the larger component of each image.
Analysis the image:
Admin choose the image and has to be entered the text, image or shape, the admin has the permission to alter the image as he like; this is the first process of analyzing.
JPEG Frame:
At the encoder, the intrapredicted (I)-frame is encoded using regular image techniques similar to JPEG but with different quantization table and step; hence the decoder can reconstruct it independently. The Algorithm tests the robustness of the hidden message to the quantization effect of the JPEG
Compression. Using the variable macro block sizes is 8*8 pixel analysis of the image.
MPEG Frame:
In the commonly used Motion Picture Expert Group
(MPEG) standard, it is ordered into groups of pictures (GOPs). The temporal redundancy between frames is exploited using block-based motion estimation that is applied on macro blocks of size is 16*16 Pixel Analysis in or and searched in target frame(s).
Data hiding through image:
Finally, Admin encrypt the key and embed in the image send to the newly registered member who is the authenticated. After receiving the key to the authenticated he has only the permission to take the key when extract the image.
2.
Video Compression:
Generally, the motion field in video compression is assumed to be translational with horizontal component and vertical component and denoted in vector form by for the spatial variables in the underlying image. Such as three steps search, etc.; this is based on the video device processing power, the required compression ratio, and the reconstruction quality.Admin has to be choose one video file along with one key, both will be compression and create one encoding key send to the member. The Authenticated member uncompresses the video file and takes the second privacy key.
3.
Motion Vector of Video:
Authenticated person after taking the second privacy key he has only the authority what are the video which was sent by Admin, the member can see the video in our application, in that video it can detect the motion vector.
After seeing this, the member obtain both of the key and given to the login section and send the message to the Admin.
Algorithm:
Data Hiding & Data Extraction
Input : message bitstream , , , ,
Output : Data embedded in the Encoded GOP
1 foreach P and B-frame in the GOP do
2 initialize ;
3 Simulate the decoder: decompress to obtain ;
4 repeat
5 set ;
6 Obtain the candidate motion vectors:
;
7 while & do
8 replace the least significant bit ,
;
9 ;
10 if B-frame then
11 replace for the backward compensation motion vectors the least significant bit
, ;
12 ;
13 end
14 ;
15 end
16 Compute associated by suitable compensation using ;
17 ;
18 until KeyFound or ;
System Requirements:
Hardware Requirements:
•
System : Pentium IV 2.4 GHz.
• Hard Disk : 40 GB.
• Floppy Drive : 1.44 Mb.
• Monitor
• Data Base
: 15 VGA Colour.
•
Mouse : Logitech.
•
Ram : 512 Mb.
Software Requirements:
•
Operating system : - Windows XP.
•
Coding Language : C#.net
: SQL Server 2005










![paper_ed18_2[^]](http://s3.studylib.net/store/data/007654176_2-a85c7206c503097e0e1313288009d169-300x300.png)