No. 1 Technique Automating and Improving Regression Testing
advertisement
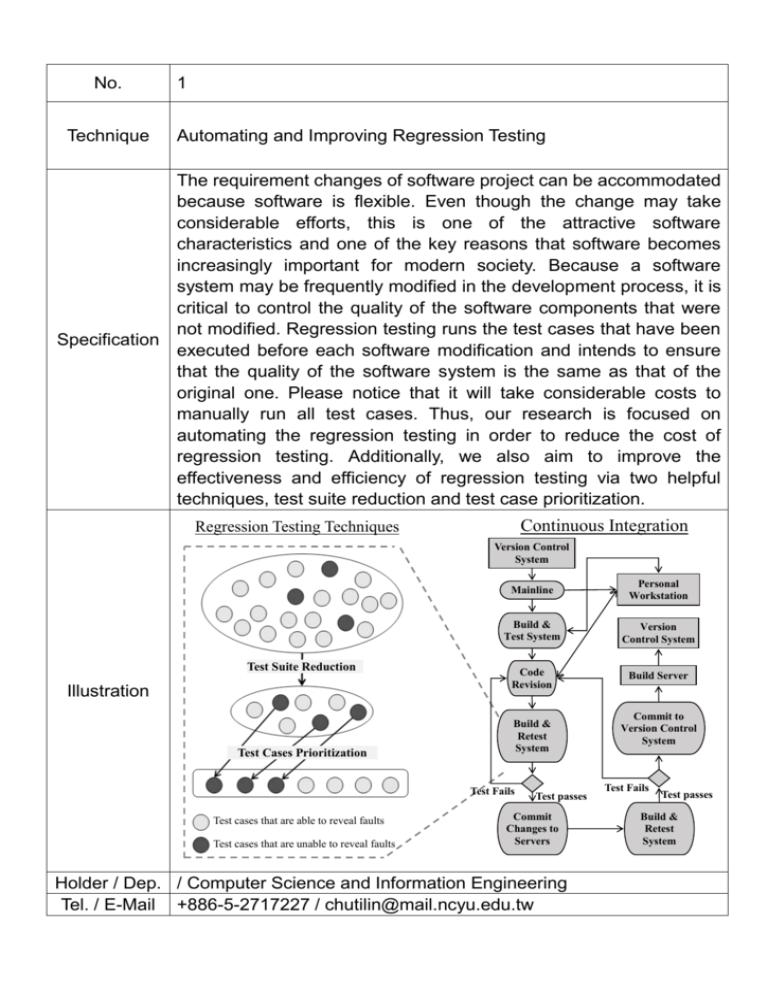
No. Technique 1 Automating and Improving Regression Testing The requirement changes of software project can be accommodated because software is flexible. Even though the change may take considerable efforts, this is one of the attractive software characteristics and one of the key reasons that software becomes increasingly important for modern society. Because a software system may be frequently modified in the development process, it is critical to control the quality of the software components that were not modified. Regression testing runs the test cases that have been Specification executed before each software modification and intends to ensure that the quality of the software system is the same as that of the original one. Please notice that it will take considerable costs to manually run all test cases. Thus, our research is focused on automating the regression testing in order to reduce the cost of regression testing. Additionally, we also aim to improve the effectiveness and efficiency of regression testing via two helpful techniques, test suite reduction and test case prioritization. Continuous Integration Regression Testing Techniques Version Control System Test Suite Reduction Illustration Test Cases Prioritization Mainline Personal Workstation Build & Test System Version Control System Code Revision Build Server Build & Retest System Test Fails Test cases that are able to reveal faults Test cases that are unable to reveal faults Test passes Commit Changes to Servers Holder / Dep. / Computer Science and Information Engineering Tel. / E-Mail +886-5-2717227 / chutilin@mail.ncyu.edu.tw Commit to Version Control System Test Fails Test passes Build & Retest System No. Technique 2 Chinese Document Classification Document classification is a natural language processing technique, which assigns a document to a class according to its content. Machine learning method is often used in practice to implement the technique. Learning algorithm analyzes training data to generate the classification model, which is used to determine the class of the input document. In order to classify Chinese document, we develop Specification techniques such as Chinese pre-processing, feature generation, feature selection, and generating classification model using SVM. These techniques can be used to process a large number of Chinese documents and determine their classes. There are many application areas: spam filtering, assessing document readability for elementary school students, determining whether a product review is positive or negative, finding documents that have similar main topics, etc. Illustration Holder/Dep. Yaw-Huei Chen/ Computer Science and Information Engineering Tel. / E-Mail +886-5-2717737 / ychen@mail.ncyu.edu.tw No. Technique 3 Environment-Adopting Characters Locomotion Controller for Quadruped 3D graphics technologies have grown rapidly over the past ten years due to the fact that both computer games and 3D animations require diverse motions of humanlike characters to pour the contents. We propose two 3D animating methods, including kinematic and dynamic techniques, towards both bipedal and quadrupedal characters for motion simulations. Kinematics-based approach is an intuitive and easy-to-implement method that has less computational complexity than the dynamic approach, but users need to formulate animation Specification rules and to deploy the parameters of character bodies, such as step height or rotation of bones. On the other hand, the dynamic approach must follow the laws of physics to determine the joint forces and torque so that it is capable of simulating more plausible motion effects than applying the kinematic approach. We experiment the proposed techniques on articulated characters and we also give the simulation results to demonstrate that the techniques can be used in a wide variety of ways, including locomotion and reaction simulations. Illustration Holder/Dep. Tainchi Lu/ Computer Science and Information Engineering Tel. / E-Mail +886-5-2717730 / tclu@mail.ncyu.edu.tw No. Technique 4 Spelling Error Detection based on Language Models and Web Resource for printing People often find out spelling errors after printing the documents, therefore they need to re-print the contents of the documents. However, it is a waste of paper, ink, printer, power, other resources and so on. Even more they would need to spend extra time without efficient. This paper addresses reducing spelling errors before printing. The language model used in this research to compare and increase a new feature additionally that is a function of Internet search. Combining these research manners, this paper expect to achieve the goals of confirming, improving the spelling error, and reducing the waste of resources. This investment proposed a spelling Specification check method that combined language model and knowledge resource. Since typos and error hidden in printed document is frequent, rework will cause the waste of paper and ink. Even more they would need to spend extra time without efficient. This paper addresses reducing spelling errors before printing by the proposed spelling check method. In this method, the language model used in this research to compare and increase a new feature additionally that is a function of Internet search. Combining these research manners, this paper expect to achieve the goals of confirming, improving the spelling error, and reducing the waste of resources. Experimental results shows, the proposed method is practicable and efficient. Illustration Holder/Dep. Ralph J.-F. Yeh/ Computer Science and Information Engineering Tel. / E-Mail +886-5-2717709 / ralph@mail.ncyu.edu.tw No. Technique 5 Encrypting high dynamic range images Multimedia information, especially images, has been consumed in people’s daily life. With therapid development and convenience of networks, we are surfing, obtaining and transferring varied multimedia via the Internet. Consequently, there are security issues worthy to concern about such as confidentiality, authentication, etc. Due to the restriction of consumer electronics, the monitor or projector can only display images of low-dynamic range (LDR). LDR images are represented with size of 8, 10 and even 12 bits for each color channel of RGB format. It is difficult to cover the gamut of human’s vision because the human visual system can distinguish more colors in the real world than the display of LDR images. Fortunately, high-dynamic range (HDR) imaging formats have al-ready been developed. The HDR format is more accurate than Specification LDR to display such that the darkest area as shadow and brightest area as sunlight in HDR images are possible. In HDR imaging, the raw format is 32-bits for each color channel R, G, B and totally 96-bits. The size of raw HDR format is comparatively huge, therefore we are used to adopt other fewer bits HDR format such as LogLuv, RGBE, or OpenEXR instead. While HDR imaging has become a new trend in academia and industry, it comes with the issues of security including confidentiality. In recent years, there is more and more attention drawn for image encryption. However, these schemes for encryption are suitable only for LDR images, not applied on HDR images directly. In our research interest, the HDR tailor-made encryption scheme is proposed to encode LogLuv/RGBE/OpenEXR images for guaranteeing confidentiality while format-compliance is achieved. Illustration Holder/Dep. Tzung-Her Chen/ Computer Science and Information Engineering Tel. / E-Mail +886-5-2717723 / thchen@mail.ncyu.edu.tw No. Technique 6 The Technology of Clouding and APP Most Management Information Systems need the computer applications to improve the working efficiency. The development trend of mobile devices advances the massive need for the APPs of the mobile devices. We have the capability of APP development for the newest version of Google Android system. We can also develop the APPs in Apple’s iOS system and Microsoft System. Since the Specification limitation of the mobile device, a large number of data of Management Information System always has been designed in the Internet Cloud. We provide the Cloudy technology to reengineer the Management Information System. We can also redesign the Cloudy applications to be suitable the mobile device by the new design style, such as Web 3.0, Representational State Transfer (RESTful), Push Technology, Responsive Web Design (RWD), and etc. Illustration Holder/Dep. Long-Sheng Li / Computer Science and Information Engineering Tel. / E-Mail +886-5-2717733 / sheng@mail.ncyu.edu.tw