Internet Protocol - Blog Unsri
advertisement

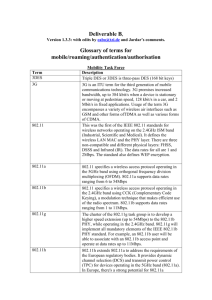
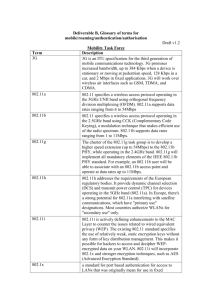
Internet Protocol dear d34r123@yahoo.co.id KOMUNITAS BLOGGER UNIVERSITAS SRIWIJAYA SECURITY+ ACRONYM LIST 0 – 9 3DES Triple Data Encryption Standard A ACL Access Control List AD Active Directory AD-IDS Anomaly Detection Intrusion Detection System AES Advanced Encryption Standard AFS Apple File Sharing AH Authentication Header ALE Annual Loss Expectancy APIs Application Program Interfaces APIPA Automatic Private Internet Protocol Addressing ARO Annualized Rate of Occurrence ARP Address Resolution Protocol ASR Automated System Recovery B BCP Business Continuity Plan BGP Border Gateway Protocol BIA Business Impact Analysis C CA Certificate Authority CAST Carlisle Adams Stafford Tavares CBF Critical Business Functions CC Common Criteria CD-R Compact Disk Recordable CEI Computer Ethics Institute CESA Cyberspace Electronic Security Act CFO Chief Financial Officer CGI Common Gateway Interface CHAP Challenge Handshake Authentication Protocol CMP Certificate Management Protocols CN Canonical Name CO Central Office CPS Certificate Practice Statement CPSR Computer Professionals of Social Responsibility CRL Certificate Revocation List CSIRT Computer Security Incident Response Team CSS Central Security Service D DAC Discretionary Access Control DDoS Distributed Denial of Service DES Data Encryption Standard DFS Distributed File System DHCP Dynamic Host Configuration Protocol DMZ Demilitarized Zone DN Distinguished Name DNS Domain Name Service DoS Denial of Service DRP Disaster Recovery Plan DSA Digital Signature Algorithm DSL Digital Subscriber Line DSSS Direct Sequence Spread Spectrum E EAL Evaluation Assurance Level ECC Elliptic Curve Cryptography EIGRP Enhanced Interior Gateway Routing Protocol EM Emergency Management EMI Electromagnetic Interference ESP Encapsulating Security Payload EULA End User License Agreement F FAT File Allocation Table FERPA Family Educational Rights and Privacy Act FHSS Frequency Hopping Spread Spectrum FIPS Federal Information Processing Standard FTP File Transfer Protocol G GFS Grandfather Father Son GSM Global System for Mobile Communications GUID Globally Unique Identifier H H-IDS Host-based Intrusion Detection System HIPPA Health Insurance Portability and Accountability HR Human Resources HTML Hyper Text Markup Language HTTP Hyper Text Transfer Protocol HTTPS Hyper Text Transfer Protocol Secure I I&A Identification and Authentication IANA Internet Assigned Numbers Authority ICMP Internet Control Message Protocol ID Intrusion Detection IDEA International Data Encryption Algorithm IDS Intrusion Detection System IEEE Institute of Electrical and Electronics Engineers IETF Internet Engineering Task Force IGMP Internet Group Management Protocol IGRP Interior Gateway Routing Protocol IIS Internet Information Server IM Instant Messaging IMAP Internet Message Access Protocol IP Internet Protocol IPSec Internet Protocol Security IPX/SPX Internetwork Packet Exchange / Sequenced Packet Exchange IR Infrared IRP Incident Response Plan IS Information Systems ISDN Integrated Systems Digital Network ISN Initial Sequence Number ISO International Organization for Standardization ISP Internet Service Provider ITU International Telecommunications Union J JFS Journaled File System K KDC Key Distribution Center KEA Key Exchange Algorithm L L2F Layer Two Forwarding L2TP Layer Two Tunneling Protocol LCP Link Control Protocol LDAP Lightweight Data Access Protocol LRA Local Registration Authority M MAC Mandatory Access Control MAC Media Access Control MAC Message Authentication Code MDA Message Digest Algorithm MD-IDS Misuse Detection Intrusion Detection System MIME Multipurpose Internet Mail Extensions MOV Metal Oxide Varistor MS-CHAP Microsoft Challenge Handshake Authentication Protocol MSSP Managed Security Service Provider MTBF Mean Time Before Failure MTTR Mean Time To Repair N NAT Network Address Translation NCP Network Control Protocol NDA Nondisclosure Agreement NDS Netware/Novell Directory Services NetBEUI Network Basic Input Output System Extended User Interface NetBIOS Network Basic Input Output System NFS Network File System NIC Network Interface Card N-IDS Network-based Intrusion Detection System NIST National Institute of Standards and Technology NLM Netware Loadable Modules NNTP Network News Transfer Protocol NOC Network Operations Center NOS Network Operating System NSS Netware Storage Service NTFS New Technology File System O OCSP Online Certificate Status Protocol OES Open Enterprise Server OFDM Orthogonal Frequency Division Multiplexing OS Operating System OSPF Open Shortest Path First OU Organizational Unit P PAP Password Authentication Protocol PBX Private Branch Exchange PDA Personnel Digital Assistant PGP Pretty Good Privacy PKC Public Key Cryptography PKCS Public Key Cryptography Standards PKI Public Key Infrastructure PKIX Public Key Infrastructure X.509 POP Post Office Protocol POTS Plain Old Telephone Service PPP Point to Point Protocol PPTP Point to Point Tunneling Protocol Q R RA Registration Authority RAS Remote Access Services RADIUS Remote Authentication Dial-In User Service RAID Redundant Array of Independent/Inexpensive Disks RBAC Role-Based Access Control RC Ron’s Code OR Rivest’s Cipher RDN Relative Distinguished Name RF Radio Frequency RFC Request For Comments RFI Radio Frequency Interference RIP Routing Information Protocol RPC Remote Procedure Call RRAS Routing and Remote Access Services RSA Rivest Shamir Adleman RSH Remote Shell S SAINT Security Administrator’s Integrated Network Tool SEI Software Engineering Institute SET Secure Electronic Transfer SHA Secure Hash Algorithm S-HTTP Secure Hypertext Transport Protocol SIM Subscriber Identification Model SLA Service Level Agreement SLE Single Loss Expectancy SLIP Serial Line Internet Protocol S/MIME Secure Multipurpose Internet Mail Extensions SMS Systems Management Server SMTP Simple Mail Transfer Protocol SNMP Simple Network Management Protocol SPX Sequenced Packet Exchange SQL Structured Query Language SSH Secure Shell SSID Service Set Identifier SSL Secure Socket Layer SSO Single Sign On STP Shielded Twisted Pair T TACACS Terminal Access Controller Access Controller System TCP/IP Transmission Control Protocol / Internet Protocol TCSEC Trusted Computer Systems Evaluation Criteria TFTP Trivial File Transfer Protocol TLS Transport Layer Security U UDP User Datagram Protocol UPN User Principal Name UPS Uninterruptible Power Supply USA PATRIOT Uniting and Strengthening America by Providing Appropriate Tools Required and Obstruct Terrorism UTP Unshielded Twisted Pair UV Ultraviolet V VLAN Virtual Local Area Network VNC Virtual Network Computing VoIP Voice over Internet Protocol VPN Virtual Private Network W W3C World Wide Web Consortium WAP Wireless Access Point WAP Wireless Application Protocol WAN Wide Area Networks WDP Wireless Datagram Protocol WEP Wired Equivalent Privacy WINS Windows Internet Naming Service WML Wireless Markup Language WSP Wireless Session Protocol WTLS Wireless Transport Layer Security WTP Wireless Transaction Protocol WWW World Wide Web X XKMS eXtensible Markup Language Key Management Specifications XML eXtensible Markup Language Y Z DOWNLOAD