DOCX 2.5MB - National Literacy and Numeracy Week
advertisement

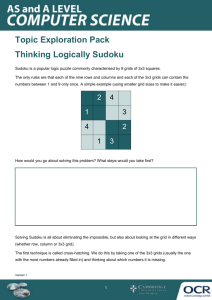
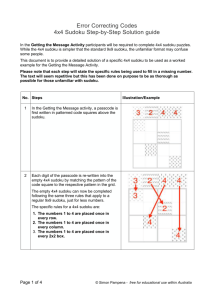
Error Correcting Codes Getting the Message Activity Instructions Purpose This activity is designed to provide a simple way of explaining and solving the problem of data loss and error correction. It will demonstrate how to transmit a simple code between two people even when a third person is actively trying to block the message being sent. Overview There are three parts to this lesson: Introduction Sets up the problem of random data loss and error correction. Thinking through the problem Highlights the issues by working through two simple methods, neither of which can be depended on in every scenario, logically leading up to an effective and reliable method, the Sudoku. Activity Opportunity for students to embed their learning and test the method using a simplified version of the Sudoku in a group activity. Lesson planning • • • • • Watch the related videos on the National Literacy and Numeracy Week website. Consider how you will work through the three lesson parts. Some teachers may like to show one or more of the videos from the National Literacy and Numeracy Week website as a lead into the activity, others may prefer to work through the examples from the Thinking through the Problem document. It is important to provide some understanding for the problem by starting with some simpler methods. These are early historical attempts at error correction which on the surface, seem like they should work. This frames the activity and the effectiveness of the method, despite the random errors. Tailor the activity to your class, there are notes on difficulty level and extension included at the end of this document. Decide how you would like to set up the activity. Some teachers may like to include a scenario that suits their class group or follow the activity as it is. It could be as simple as accessing your favourite app via your phone or a secret that could save the world! Print off the required templates listed in the equipment list Page 1 of 10 © Simon Pampena - free for educational use within Australia Equipment list All documents and templates are available on the Getting the message webpage. Introduction – provided in this document. • • • • Thinking through the problem– resources developed from the Thinking through the Problem document. Or related videos from the National Literacy and Numeracy Week website and any equipment needed to show them, such as the IT and screen. Printouts of 4x4 Sudoku Templates (there are two blank grids per sheet, two needed per group of students). A list of 120 Four-digit Passcodes with Unique Solutions. You might like to display this onscreen or print off enough copies to cut in sections and provide a section to each group. If required for the extension activity the Extension Activity Guide. Optional If there are concerns about being able to solve any of the 4 x 4 sudokus used in this activity there are guides: • a 4x4 Sudoku Step-by-Step Solution guide. This solves a sudoku for a specific passcode specifying which rules are used along the way. • a Detailed Unique Solutions guide that provides detailed solutions for every unique passcode used in the activity. Page 2 of 10 © Simon Pampena - free for educational use within Australia Lesson introduction Setting the scene: When you send a message on your phone, how does it get to the other end? When information is being sent to access an app or your bank account or even stream a song, how does it get through? The world is a noisy place. Whenever you share photos or stream a song, there are long ribbons of 0s and 1s (the language of computers) flying around connecting you to what you want. But when static interference occurs, the ribbon snaps. The continuous transmission of 0s and 1s becomes littered with errors, missing or incorrect digits, making the original unreadable. Random data loss is a problem that modern technology grapples with every day and without a solution, our world would grind to a halt. Yet mathematicians have come up with an answer. Your messages are converted into digital data and then protected with a buffer of excess data that you can afford to lose. But for the buffer to work, it must provide meaning or context to the core data for the original message to be retrievable. For example, consider the musical notation mnemonic of Every Good Boy Deserves Fruit. The core data are the notes E G B D F and the buffer data are the words attached to each letter. Then if some letters are randomly lost - _very G_od B_y _es_rv_s _r_it - we are still able to work out what the words were meant to be because of the context they are in. So, even when static interference attacks at random, there will still be a way to recover your original message. There are various ways to create a data buffer, some more effective than others, but each method must be written as a list of instructions: something that a computer can easily follow. These instructions are also called an algorithm or a programme or simply, a code. As these codes correct errors they are called Error Correcting Codes. Thinking through the problem What does this problem look like in practice? Let’s start with a simplified situation. We need to access our favourite app or a bank account with a four-digit passcode - ‘3214’ for example. For the passcode to be verified, it is sent off to a central computer somewhere else. The problem is, when the message is sent we could randomly lose one of the digits through static interference. This may not happen all the time or you may lose more than one digit, but for simplicity, the activity works on the assumption that you always lose one in four digits. From this simple starting point, two methods are introduced representing the most straightforward solutions possible. The shortcomings of each method are used to highlight the extent of the problem to overcome. This frames the sudoku activity as a method that works, no matter what pattern of random errors. Note: To work through the examples, use the Thinking through the Problem document as a guide or use the Getting the message – a break in transmission video available on the National Literacy and Numeracy Week website. Page 3 of 10 © Simon Pampena - free for educational use within Australia Lesson steps for the activity 1. Ideally, the class is broken up into groups of three students for the activity. 2. Explain the role of each person in the group of three: In each group there are three roles: The SENDER The person who picks the passcode and is trying to relay it to the RECEIVER. The JAMMER The RECEIVER The person who interrupts the The person who has to recover passcode from the SENDER to the SENDER’s passcode with the RECEIVER with errors. the JAMMER’s errors. The SENDER choses a four-digit passcode from the list of 120 Four-digit Passcodes with Unique Solutions. Each passcode is a combination of four digits using the numbers 1,2,3 or 4. Codes with repeated digits are included in the list e.g. 1123 This four-digit passcode is entered into the 4x4 Sudoku Template. The SENDER solves the 4x4 sudoku and passes it on to the JAMMER. The JAMMER re-writes the completed 4x4 sudoku, leaving out up to 6 numbers of their choice, including the original passcode. The JAMMER passes the incomplete 4x4 sudoku to the RECEIVER who solves it to reveal the original four-digit passcode. Page 4 of 10 © Simon Pampena - free for educational use within Australia Detail No. Steps 3 Students decide which role they will play: the SENDER, the RECEIVER or the JAMMER. 4 Provide each group with two empty 4x4 Sudoku Templates. 5 Explain to the class that the SENDER needs to select a passcode from the list of 120 Four-digit Passcodes with Unique Solutions. The code is to be written in the code squares which are patterned boxes above the top of each 4x4 sudoku. Page 5 of 10 Illustration/Example © Simon Pampena - free for educational use within Australia No. Steps 6 Illustration/Example The SENDER then enters each digit of the passcode into the empty 4x4 sudoku by matching the pattern of the code square to the respective pattern in the grid. The SENDER then completes the template following rules similar to a regular 9x9 sudoku. The rules are specified in the following steps. 7 Numbers 1 through to 4 appear once in every row… 8 …once in every column… Page 6 of 10 © Simon Pampena - free for educational use within Australia No. Steps 9 …and once in every 2x2 block. 10 Following the rules of 4x4 sudoku the SENDER completes the grid. Illustration/Example If you have trouble solving the sudoku there is a 4x4 Sudoku Step-by-Step Solution document to use as a guide. The completed grid is then given to the JAMMER. 11 Explain to the class that the JAMMER rewrites numbers from the completed sudoku grid leaving empty all the code squares (patterned squares in the grid). He or she can remove up to six numbers in total from the SENDER’s completed grid. Page 7 of 10 © Simon Pampena - free for educational use within Australia No. Steps 12 The JAMMER then gives only the incomplete sudoku grid to the RECIEVER. Explain to the class that the JAMMER now needs to complete the sudoku to find the passcode. 13 Once the sudoku has been correctly filled in there will be numbers in the patterned code squares. 14 Explain to the class that the JAMMER can now fill in the code squares at the top of the sudoku grid which correspond to the patterned code squares in the grid. Page 8 of 10 Illustration/Example © Simon Pampena - free for educational use within Australia No. Steps 15 Illustration/Example The RECEIVER then checks with the SENDER if the code has been correctly recovered. If so, ACCESS GRANTED and if not… THE JAMMER HAS WON! Additional Teachers Notes Passcodes in the list of 120 Fourdigit Passcodes with Unique Solutions are arranged numerically from smallest to biggest. They are also split into 5 columns: A, B, C, D and E. These columns refer to separate documents where each passcode is given a detailed solution in the 4x4 Sudoku. The page number next to each passcode refers to the location of the solution in the respective document. The 5 documents are: Detailed Unique Solutions_Column A Detailed Unique Solutions_Column B Detailed Unique Solutions_Column C Detailed Unique Solutions_Column D Detailed Unique Solutions_Column E Page 9 of 10 © Simon Pampena - free for educational use within Australia Difficulty This activity is designed to be as straightforward as possible. As such, we have limited the number of four-digit passcodes that can be used. Each code in the list of 120 Four-digit Passcodes with Unique Solutions only has one solution when entered in our 4x4 sudoku grid. This is not true for every combination code. For example, the code 3333 entered in our 4x4 sudoku grid can be solved 18 different ways. Without any restrictions there are a total of 256 different four digit codes using 1,2,3 or 4. There are many of these codes that could also be used in a 4x4 sudoku but they no longer produce a unique grid. There are also some codes that do not work at all in a 4x4 sudoku. We leave open the use of these more exotic passcodes as an extension activity for the more adventurous sudoku masterminds. For details see the Extension Activity Guide. Page 10 of 10 © Simon Pampena - free for educational use within Australia