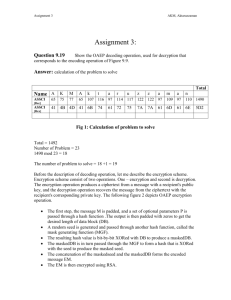
Relaxing IND-CCA: Indistinguishability Against Chosen Ciphertext
advertisement

Relaxing IND-CCA: Indistinguishability Against Chosen Ciphertext Verification Attack Sumit Pandey, Indian Statistical Institute The definition of IND-CCA security model for public key encryption allows an adversary to obtain (adaptively) decryption of ciphertexts of its choice. That is, the adversary is given oracle access to the decryption function corresponding to the decryption key in use. The adversary may make queries that do not correspond to a valid ciphertext, and the answer will be accordingly (i.e., a special ``failure'' symbol). In this article, we investigate the case where we restrict the oracle to only determine if the query made is a valid ciphertext or not. That is, the oracle will output 1 if the query string is a valid ciphertext (do not output the corresponding plaintext) and output 0 otherwise. We call this oracle as ``ciphertext verification oracle'' and the corresponding security model as Indistinguishability against chosen ciphertext verification attack (IND-CCVA). We point out that this seemingly weaker security model is meaningful, clear and useful to the extent where we motivate that certain cryptographic functionalities can be achieved by ensuring the IND-CCVA security where as IND-CPA is not sufficient and IND-CCA provides more than necessary. We support our claim by providing nontrivial construction (existing/new) of: – public key encryption schemes that are IND-CCVA secure but not IND-CCA secure, – public key encryption schemes that are IND-CPA secure but not IND-CCVA secure. Our discoveries are another manifestation of the subtleties that make the study of security notions for public key encryption schemes so attractive and are important towards achieving the definitional clarity of the target security.