103.0111App 3.1 Attachment 11
advertisement

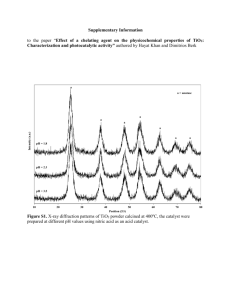
The Signalling Programme Fjernbane Infrastructure East/West BAFO Tender Document / Appendix 3.1 Att 11 Online Key Management System Concept Banedanmark The Signalling Programme Amerika Plads 15 DK-2100 Copenhagen E Denmark Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Author: Fjernbane Signalling System Project Mail: Fjernbane@bane.dk Phone: +45 8234 0000 www.banedanmark.dk Att 11 OKMS Concept Page 2 of 12 Att 11 OKMS Concept Table of Contents 1 Change Log 2 2.1 2.1.1 2.1.2 Introduction Goals and prerequisites Concept Description KMS Delivery Fjernbane Infrastructure East/West Document1 Page 4 Tender Document / Appendix 3.1 Version 2.0 5 5 7 11 Att 11 OKMS Concept Page 3 of 12 1 Change Log Made by Version SODE/ 2.0 Commented Approved by Status by Issued to Tenderers for BAFO 27.06.2011 Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 4 of 12 2 Introduction Introduction The security in the message flow in ERTMS Level2 signalling systems is based on the use of a secret key that must be known by both the train and the infrastructure. The distribution of these secret keys (KMACs) is a problem due to the fact that KMACs -as per current practise described in the UNISIG subset - are to be installed “manually” during service periods in trains, and infrastructure. This has lead to praxis in specific Level2 networks to simplify the KMAC usage by having only one KMAC common for many trains and large infrastructure areas. This has both Security and Safety implications because a secret shared by many parties is effectively not a secret. A mismanaged KMAC can easily be compromised and thereby potentially compromise the security of the railway network which in turn compromises safety of operations.1 The large number of ETCS elements in the Signalling Programme that is supposed to enclose the whole country makes it even more demanding to create an enhanced system for handling and distributing KMACs. In the following the “Online Key Management System Concept” (OKMS) for the Danish infrastructure describes a Key Management System as a combination of a Key Managemnet Centre and an online Key Distribution System. The aim is to keep the basic functionalities of the current specifications as they are while enhancing the security of using secret key pairs by enhancing the possibility to renew KMACs for entities in the Danish domain. It is our belief that OKMS will solve the security as well as the safety issues mentioned and that the established system will be able to manage a large ERTMS Level2 infrastructure cost effectively. 2.1 Goals and prerequisites The main goals for the OKMS concept are the following: 1. To implement a Key Management Centre that is: o Interoperable The secret key – the KMAC - is regarded as an obvious target for hackers and others that might want to introduce threats, denial of service attacks or catastrophic events on the rail traffic. As the railway infrastructure turns more and more towards IP based solutions threats are to be found in new types of communities. 1 Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 5 of 12 o provides the management interface for: Creating Renewing Disabling of KMACs 2. To implement a secure online service for the Danish domain entities based on “Commercial Off The Shelf” products for IP based systems. 3. To implement an online distribution system for KMACs for the Danish domain entities2 covering as both visiting trains and roaming trains. Prerequisites The prerequisites of the requirements are the following strategic decisions taken by the Signalling Programme: 1. The Danish ERTMS infrastructure and OBUs must be enabled for packet switched mobile data access (GPRS/EDGE) and thus consists of IP enabled entities. 2. The security of transmission based on the Euroradio protocol must be enhanced without impacting the protocol by allowing changing the security keys on a regular basis or on request. 3. The KMAC distribution concept should be based on “One Unique KMAC per OBU” in order to make it easy to revoke compromised KMACs. 4. Use of an asymmetric key (Private- and Public- Key) based online distribution system for secured online data exchange instead of symmetric KTRANS keys, to provide authenticity, integrity and confidentiality on distribution of files containing KMACs. 5. The Danish enhancements to the ERTMS standard must follow or be compatible with ERA specifications. That applies particularly for the usage of packet switching in ETCS (CR741) and the evolving specifications and recommandations for off-line Key Management (SUBSET 114 and SUBSET 038). 2 Danish domain includes Danish Radio Block Centres (RBCs) and Danish OnBoard Units (OBUs) Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 6 of 12 2.2 Concept Description The goals and prerequisites lead to the following subdivision of the OKMS concept: 2.2.1 Key Management Centre (KMC).3 Infrastructure for secure online distribution (PKI). Key Distribution Centre functionality (KDC). OnBoard enhancements for Online Key Distribution (OBU+). Key Management Centre The concept for the Management of KMACs in the Signalling Programme domain is basically the same as in any other KMC: It must be interoperable it must provide the security consistent with the domain it must provide access management for trains visiting the domain and for own OBUs that need to roam to foreign ERTMS domains “Neighbouring KMC” domains EAST and WEST is and option in the Danish infrastructure. If OPT 10 is chosen ther will be only one KMC in Denmark. 3 Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 7 of 12 The basic ERTMS KMC functionality of the KMC is to manage the secret key usage (KMAC) in the domain of the KMC and to provide interface for KMACs that are to be exchanged with foreign KMCs. The KMC controls the use KMAC keys in the domain for as well domain OBUs and RBCs as for visitors in the domain. The KMC is also managing foreign KMACs to be used by national trains that need to visit foreign domains (roamers)4. The user interface of the KMC should support creation of “secret key racks” for OBUs and RBCs in the domain and be able to issue “immediate” and coordinated renewal of “secret key racks” in security/safety critical situations. According to the evolving SUBSET 114 it may also be required to handle lifetime confined KMACs in RBCs – these and other details should be defined during the “Joint Design” process. The KMC should be able to establish and update a “Domain” view of the KMAC usage. The figure below is an example of how such a “domain view” may look5: 4 5 Roaming needs to be prearranged and secret kys exchanged in advance by the KMCs KMACs to be used in RBC-RBC handovers should be specified seperately. Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 8 of 12 DOMAIN TRAFFIC NATIONAL TRAFFIC RBCy.se RBCx.de RBCy.de Remarks KM1.dk KM1.dk KM1.dk KM1.dk KM1.dk KM1.dk KM1.dk KMx.de KMy.de DSB example KM2.dk KM2.dk KM2.dk KM3.dk KM2.dk KM3.dk KM2.dk KM2.dk KM2.dk KMx.de KMy.de KMx.dk KM2.dk ... KMx.dk KMx.dk KMx.dk KMx.se KMy.se KMx.dk KMy.dk KMx.nl KMx.nl KMx.se KMy.se KMx.dk KMy.dk KMx.nl KMx.nl KMx.se KMy.se KMx.dk KMæ.dk KMz.de KMø.dk KMæ.dk KMå.dk KMø.dk RBCz.se RBCx.se RBC-RBC KMACK Left RBC-RBC KMACK Rigth RBCx.dk VISITOR TRAFFIC OBU x.se OBU y.se OBU x.de OBU y.de OBU x.nl OBU y.nl .. .. RBC3.dk OBU 2.dk OBU 3.dk . . OBU x.dk National OBU´s in foreign Domains RBC2.dk 2) 1) RBC1.dk OBUid/RBCid KMAC OBU 1.dk FOREIGN DOMAIN (ROAMING) TOC example KM2.dk KM2.dk KMx.de KMy.de TOC example 1) RBC secret key rack 2) OBU secret key rack KMx.dk KMx.nl KMx.nl KMx.se KMå.dk RBCs uses KMAC Euroradio over IP during domain RBC-RBC HO RBCs uses KMAC Euroradio over a joint design connection during borderline RBC-RBC HO KMC-KMC KTRANS SE KMC-KMC KTRANS DE KMC-KMC KTRANS NL KMC-KMC KTRANS BE " " Figur 1 Domain view Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 9 of 12 The table shows “OBU secret key rack”s in rows and “RBC secret key rack”s in columns. The yellow and the green area shows the KMAC references to be used by domain OBUs inside (yellow) the home domain and outside (green) in foreign domains. The extensions of the KMAC references KMx.dk or .se or .de are denoting the origin or the KMC that have issued the KMAC. The example reflects the possibility to have “one KMAC per train” within the home domain and either having exported or imported KMACs when roaming. The blue area shows foreign OBUs that need to have access to the domain either using imported keys in the KMC or keys issued by BDK to be used foreign trains. 2.2.2 PKI infrastructure for secure online distribution As online distribution of KMACs and other online communications e.g. between Hand Held Terminals and TMS, are containing safety critical data, special measures need to be taken to communicate data securely. It is envisaged that there is a need to set up a Public key Infrastructure server and to take advantage of the TCP/IP protocol suite in order to secure authentication, integrity and confidentiality on online communications. 2.2.3 The PKI should be using a de facto standardised hybrid-cryptosystem including mutual authentication. It is recommended that the system should be based on TLS6 as it provides a high level of security and is well-known IP technology. Key Distribution Centre (KDC) functionality. The functionality of the KDC is to establish a distribution server for “secret key rack” /KMAC data produced in the KMC to be delivered to domain OBUs and RBCs. The KDC shall have access to KMC data and utilize the secure PKI infrastructure to connect domain OBUs and RBCs and manage a download processes of the “secret key rack”s. The aim of current draft UNISIG SUBSET 114 is to specify an offline distribution standard for KMAC data between KMC and OBU. Therefore the joint design process should take SUBSET 114 into consideration. 6 Transport Layer Security (TLS) standardised by IETF in RFC 5246 Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 10 of 12 The KDC shall be able to send a “semaphore” to let an OBU/RBC know that an immediate “secret key rack” update is necessary. The semaphore might be sent via SMS for triggering the OBUs to look for new keys. The fact that the KDC and the RBCs are IP connected makes it fast and easy to revoke a compromised key from the infrastructure and thereby mitigate the risk of masquerading MAs. As the OBUs are not aways online seen form the KDC a “network first” migration strategy should be preferred also in case of a normal frequent key renewal procedure. RBCs should accept both “current and new” KMACs over a migration period large enough for all OBUs to be updated. 2.2.4 OnBoard Online Key Management enhanced functionality In order to provide support for Online Key Management a Danish domain OBU must include special software to support the following key management process: The EVC should activate an ”update secret key rack” procedure before the Euroradio protocol is activated during the “open desk procedure”.7 or The EVC should activate at any time the ”update secret key rack” procedure caused be “a semaphore request” received e.g. via SMS . The procedure8 should establish a TLS based session to the KDC and download new versions of “secret key rack” tables. When the procedure has taken place the normal procedure should be continued. Note: When OBUs are travelling in GSM-R networks that do not support GPRS/EDGE it will not be possible for the OBU to contact the home domain KDC. As a consequence the OBU sw should not activate the update process if the ETCS variable for GPRS support is not “true” (i.e. last ETCS session balise read). 2.3 OKMS Delivery For the Fjernbane Infrastructure and On-board Contracts the Suppliers will be asked to deliver an online Key Management System encompassing both ETCS Infrastructure, Onboard Units and other relevant parts of the Signalling System like TMS and Handheld Terminals. On-line secured solutions as mentioned above are commonly used in client server solutions IP based solutions. The Customer will work for the timely specification of On7 The key update procedure must not conflict with interoperability ie be finalised before SoM is initiated. 8 The protocol vher the OBU present its EVC-id and current ”key rack version” and eventually downloads a new version (joint design issue). Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 11 of 12 line Key Management for ERTMS in the framework of the ERTMS Users Group and the Fjernbane Infrastructure and On-board Suppliers will be expected to jointly drive the work on UNISIG side. Requirements not covered by the evolving ERTMS specifications for Key Management will be defined during the “Joint Design Phase” of the Signalling Programme. Fjernbane Infrastructure East/West Document1 Tender Document / Appendix 3.1 Version 2.0 Att 11 OKMS Concept Page 12 of 12