Summary25

Summary of Pseudorandom Numbers
Yu Zhang yz08@fsu.edu
The paper has two main parts. The first part is a survey about random number generators. The other part is about computational information theory and the discussion of secure pseudorandom bit generators.
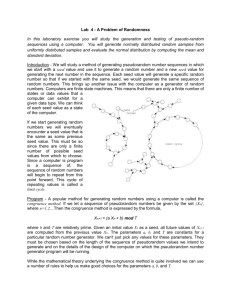
First, the author gave the definition of pseudorandom bit generator and the reason for using it. Then, the author listed three principles in constructing pseudorandom sequences: expansiveness, nonlinearity and computational complexity. Bases on these, there are many kinds of function were proposed and used in pseudorandom bit generators. To support this, the author gave several examples of pseudo-random number generators: multiplicative congruential generator defined by x n+1
= a*x n
+ b
(mod M); power generator defined by x n+1
= (x n
) d (mod M); discrete exponential generator defined by x n+1
= g xn (mod M) and kneading map. At last, the author pointed out that hashing and composition is two mixing constructions we can use for constructing more complicated pseudorandom number generators.
In section 3, the author discussed the basis of secure pseudorandom bit generators: computational information theory. Then he talked about the problem about the existence of secure pseudorandom bit generators. The fact is that among a secure pseudorandom bit generator, a one-way function and a secure private key cryptosystem, if one of them exits, all of them exit. However, the problem is not solved yet.
Bases on the analysis above, the author introduced secure pseudorandom bit generators used in practice. LCGs are not suitable to keep secret because of its correlation property. RSA bit generator is a good choice. By analyzing its theory, the author proved that it can work well in practice.