Schedule B: Business Systems Responsibilities
advertisement
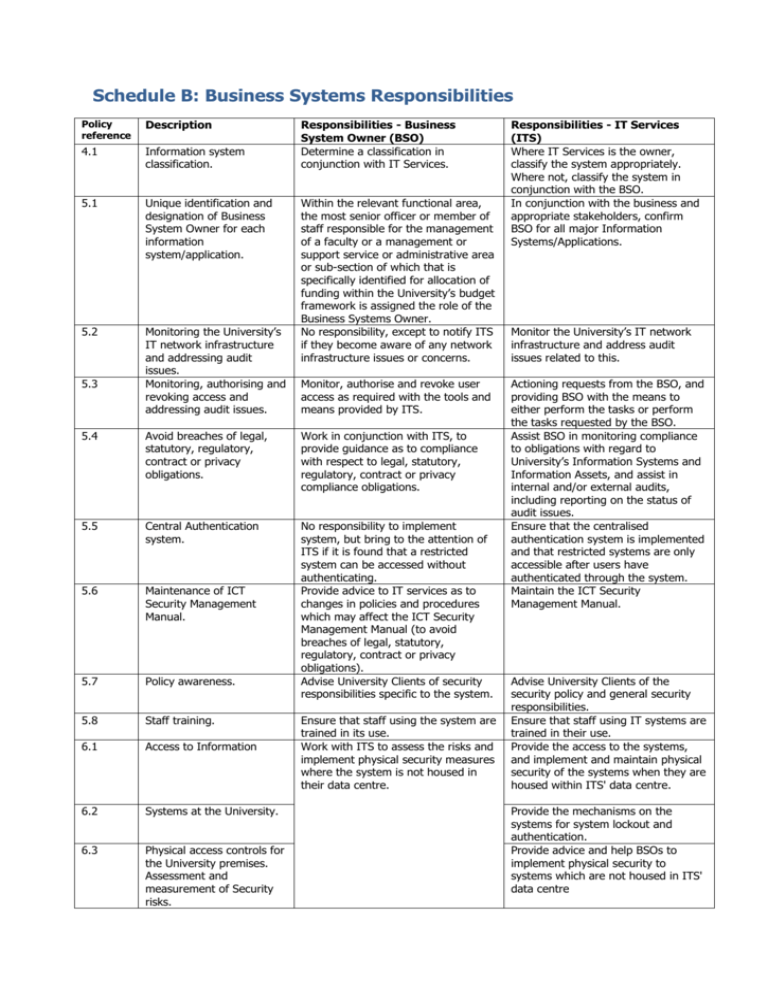
Schedule B: Business Systems Responsibilities Policy reference Description 4.1 Information system classification. 5.1 Unique identification and designation of Business System Owner for each information system/application. 5.2 Monitoring the University’s IT network infrastructure and addressing audit issues. Monitoring, authorising and revoking access and addressing audit issues. 5.3 Responsibilities - Business System Owner (BSO) Determine a classification in conjunction with IT Services. Within the relevant functional area, the most senior officer or member of staff responsible for the management of a faculty or a management or support service or administrative area or sub-section of which that is specifically identified for allocation of funding within the University’s budget framework is assigned the role of the Business Systems Owner. No responsibility, except to notify ITS if they become aware of any network infrastructure issues or concerns. Monitor, authorise and revoke user access as required with the tools and means provided by ITS. 5.4 Avoid breaches of legal, statutory, regulatory, contract or privacy obligations. Work in conjunction with ITS, to provide guidance as to compliance with respect to legal, statutory, regulatory, contract or privacy compliance obligations. 5.5 Central Authentication system. 5.6 Maintenance of ICT Security Management Manual. 5.7 Policy awareness. No responsibility to implement system, but bring to the attention of ITS if it is found that a restricted system can be accessed without authenticating. Provide advice to IT services as to changes in policies and procedures which may affect the ICT Security Management Manual (to avoid breaches of legal, statutory, regulatory, contract or privacy obligations). Advise University Clients of security responsibilities specific to the system. 5.8 Staff training. 6.1 Access to Information 6.2 Systems at the University. 6.3 Physical access controls for the University premises. Assessment and measurement of Security risks. Ensure that staff using the system are trained in its use. Work with ITS to assess the risks and implement physical security measures where the system is not housed in their data centre. Responsibilities - IT Services (ITS) Where IT Services is the owner, classify the system appropriately. Where not, classify the system in conjunction with the BSO. In conjunction with the business and appropriate stakeholders, confirm BSO for all major Information Systems/Applications. Monitor the University’s IT network infrastructure and address audit issues related to this. Actioning requests from the BSO, and providing BSO with the means to either perform the tasks or perform the tasks requested by the BSO. Assist BSO in monitoring compliance to obligations with regard to University’s Information Systems and Information Assets, and assist in internal and/or external audits, including reporting on the status of audit issues. Ensure that the centralised authentication system is implemented and that restricted systems are only accessible after users have authenticated through the system. Maintain the ICT Security Management Manual. Advise University Clients of the security policy and general security responsibilities. Ensure that staff using IT systems are trained in their use. Provide the access to the systems, and implement and maintain physical security of the systems when they are housed within ITS' data centre. Provide the mechanisms on the systems for system lockout and authentication. Provide advice and help BSOs to implement physical security to systems which are not housed in ITS' data centre 6.5 Third Party University Clients. Ensure the third party signs a confidentiality agreement, and after access has been assigned to the network, assign lowest level access to the application. 6.6 Security of the information in all media formats that will be used. Consult with ITS to consider the security of media. 6.7 Remote access to Restricted Information Systems. Approve / Deny users for remote access to the systems they are responsible for. 6.8 Ownership of information, data and software within the University. 7.1 Operations management procedures. 7.2 Changes to Information Systems. Ensure ownership of information, data and software within the University for which the BSO is responsible, is assigned in a manner consistent with the University’s Intellectual Property Policy or with other contracts and agreements. In consultation with ITS, develop procedures to fulfil the duties of this policy, and provide them to ITS for inclusion in the Information Security Management Manual. Make changes to systems in accordance with ITS policy and procedures to ensure the confidentiality, integrity and availability of data. 7.3 Segregation of Duties. 7.4 Detection and prevention of malicious software. 7.5 The installation of unauthorised information and communications technology on the network. 7.6 Backup of Information Systems. 7.7 Appropriate activity logging. 7.8 ICT Security incidents. If the system allows, turn on activity logging and periodically review the logs either manually or automatically. Review the logs provided by ITS (if any). Inform ITS of any security incidents. 7.9 Transmission of confidential information. Use means provided by ITS to transmit data in an encrypted In consultation with ITS, ensure Segregation of duties exists for roles and responsibilities within the application and consider segregations when making changes to users' access as well as roles and responsibilities themselves. No responsibility to implement Antivirus, but inform ITS if system is compromised. No Responsibility, except to notify ITS if they become aware of any unauthorised information and communications technology on the network. Inform ITS of backup requirements for their application. Ensure that third parties receive the lowest access to the systems administered by ITS, and only provide the access to the network after receiving a signed third party confidentiality agreement. In conjunction with BSOs, decide whether the use of certain media on systems is to be restricted, and implement the restrictions. Provide the mechanisms and infrastructure for remote access, and provide the access after permission from the BSO is received. Ensure ownership of information, data and software within ITS is assigned in a manner consistent with the University’s Intellectual Property Policy or with other contracts and agreements. Incorporate procedures gained from BSOs into the ICT Security Management Manual. Implement, maintain and enforce the use of a single, overarching IT change management policy for the university, including all phases from request, development, testing, authorisation, and implementation. Assist BSO in developing and maintaining Segregation of Duties within their systems. Implement antivirus application(s) on the University network. Apply policies to the underlying systems and network to prevent the installation of unauthorised software. Operate, support, maintain, and ensure the ongoing testing of backups, and that backup media is moved offsite. Backup systems as required by BSOs. As far as practical, log all activities performed on the network, and provide the logs to BSOs for review. Alternatively, use an application to report on the logs automatically. Investigate known incidents in accordance with the University’s Critical Incident Management Institutional Operating Policy. Provide the means for all staff and users to transmit data in an encrypted manner. 7.10 Business continuity management. 8.2 Information security requirements. 8.4 End user developed systems. 9.1 Activity monitoring and logging. 9.2 Periodic IT Security Audits. 9.3 Breaches of the Policy. Ensure that appropriate Business Continuity plans are developed and in place and that these are aligned with the IT Services Disaster Recovery plans for the application. Ensure ITS is aware of any specific information security requirements for the business unit so they can be addressed as part of the acquisition, implementation, development or enhancement of the Information System / application. Ensure ITS is aware and kept up to date of any End user developed applications (such as Excel spreadsheets or Access databases) used by the business unit which are being relied upon heavily. Liaise with both ITS (if appropriate) and the authority requesting to review logs and provide the data required. Liaise with ITS and the auditors to provide the requested data. Restrict access for specific users to the application after being instructed by the relevant governing body. matter, such as via a secured file transfer service. Ensure that appropriate Disaster Recovery plans are developed and in place and that these are aligned with the Business Continuity Plans for the application. Address information security requirements, including those specified by the BSO, as part of the acquisition, implementation, development or enhancement of the Information System. If informed of any important End user developed applications where continuity and support becomes critical, ensure these are institutionalised and brought under the control of either ITS or the relevant department. Provide the means for the university to monitor and log activities performed on the systems and network. Liaise with the BSO and the auditors to provide the requested data. Restrict access for specific users to the network after being instructed by the relevant governing body.





















