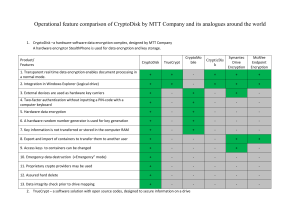
Portable Device Acceptable Encryption
advertisement
#HHSN268201100025C INTERMACS Interagency Registry for Mechanically Assisted Circulatory Support INTERMACS Operating Instructions IOI Title: Portable Device Acceptable Encryption: Public/Complete Document Number: IOI-06-007-V1 Document Storage Location: M:\INTERMACS 2011-2015\6 Information Security\2 IOI Public\IOI-06-007-V1 Portable Acceptable Encryption.Docx IOI Author: Position: Robert Kasco ISS2 Approved by: Position: David Naftel DCC Director Approved Date: Effective Date: Last Edited Date: 03-05-2012 03-05-2012 03-05-2012 Page 1 of 2 IOI-06-007-V1 Portable Device Acceptable Encryption Portable Device Acceptable Encryption 1. PURPOSE AND SCOPE The purpose of this policy is to provide guidance that limits the use of encryption to those algorithms that have received substantial public review and have been proven to work effectively. Additionally, this policy provides direction to ensure that Federal regulations are followed, and legal authority is granted for the dissemination and use of encryption technologies outside of the United States. 2. APPLICABLE REGULATION AND POLICIES All INTERMACS encryption shall be done using NIST approved cryptographic modules. Common and recommended ciphers include AES 256, Triple DES and RSA. Symmetric cryptosystem key lengths must be at least 128 bits. Asymmetric crypto-system keys must be of a length that yields equivalent strength. INTERMACS’s key length requirements shall be reviewed annually as part of the yearly security review and upgraded as technology allows. 3. PERSONNEL / RESPONSIBILITIES All users of portable devices that access INTERMACS information. 4. DEFINITIONS Proprietary Encryption An algorithm that has not been made public and/or has not withstood public scrutiny. The developer of the algorithm could be a vendor, an individual, or the government. Symmetric Cryptosystem decryption of the data. A method of encryption in which the same key is used for both encryption and Asymmetric Cryptosystem A method of encryption in which two different keys are used: one for encryptingand one for decrypting the data (e.g., public-key encryption). 5. PROCEDURE Encryption is completed by Desktop Support. 6. SCHEDULE Perminant, Annual review. 7. SUPPORTING DOCUMENTATION AND RESOURCES http://www.uab.edu/policies/Documents/PortableComputingDeviceSecurity.pdf 8. REVISION HISTORY Revision 01 Author RJK Revisions Made New IOI Effective Date 03-05-2012 Page 2 of 2