246-305
advertisement
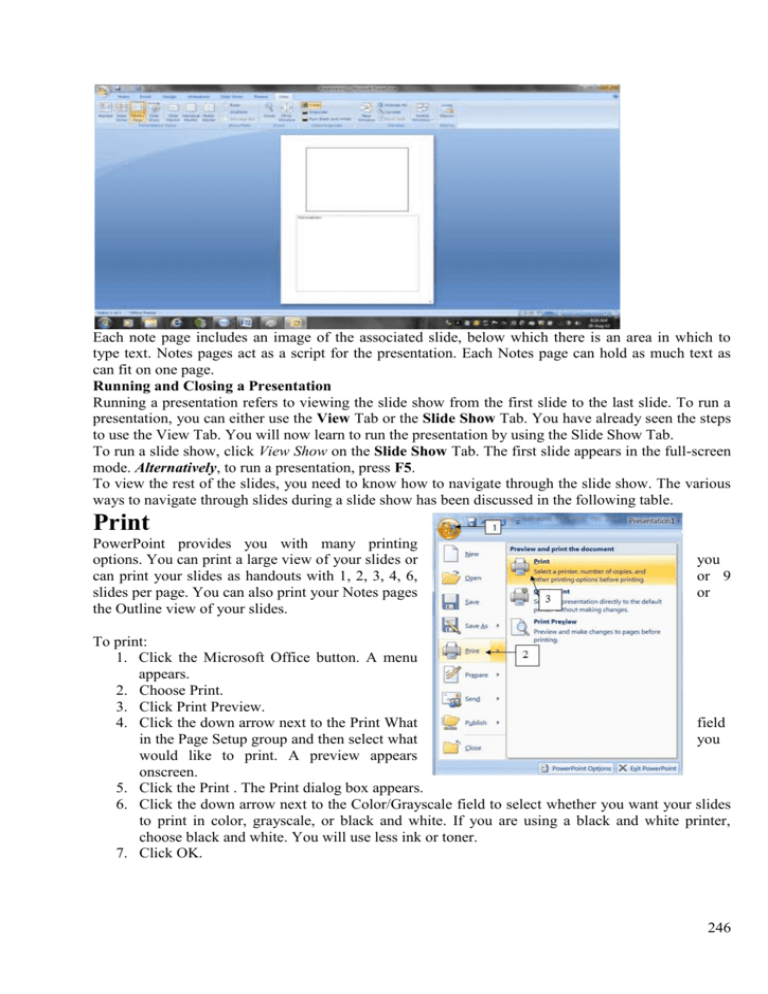
Each note page includes an image of the associated slide, below which there is an area in which to type text. Notes pages act as a script for the presentation. Each Notes page can hold as much text as can fit on one page. Running and Closing a Presentation Running a presentation refers to viewing the slide show from the first slide to the last slide. To run a presentation, you can either use the View Tab or the Slide Show Tab. You have already seen the steps to use the View Tab. You will now learn to run the presentation by using the Slide Show Tab. To run a slide show, click View Show on the Slide Show Tab. The first slide appears in the full-screen mode. Alternatively, to run a presentation, press F5. To view the rest of the slides, you need to know how to navigate through the slide show. The various ways to navigate through slides during a slide show has been discussed in the following table. Print PowerPoint provides you with many printing options. You can print a large view of your slides or can print your slides as handouts with 1, 2, 3, 4, 6, slides per page. You can also print your Notes pages the Outline view of your slides. you or 9 or To print: 1. Click the Microsoft Office button. A menu appears. 2. Choose Print. 3. Click Print Preview. 4. Click the down arrow next to the Print What field in the Page Setup group and then select what you would like to print. A preview appears onscreen. 5. Click the Print . The Print dialog box appears. 6. Click the down arrow next to the Color/Grayscale field to select whether you want your slides to print in color, grayscale, or black and white. If you are using a black and white printer, choose black and white. You will use less ink or toner. 7. Click OK. 246 Print an Outline 1. 2. 3. 4. Click the Microsoft Office button. A menu appears. Choose Print. Click Print Preview. The Print Preview tab appears. Click the down arrow next to the Print What field in the Page Setup group and then select Outline View. 5. Click the Print button . The Print dialog box appears. 6. Click the down arrow next to the Color/Grayscale field to select whether you want your slides to print in color, grayscale, or black and white. If you are using a black and white printer, choose black and white. You will use less ink or toner. 7. Set the other print settings. 8. Click OK. Your outline prints. Print Your Slides 1. Click the Microsoft Office button. A menu appears. 2. Choose Print. 3. Click Print Preview. The Print Preview tab appears. 247 4. Click the down arrow next to the Print What field in the Page Setup group and then select Slides. 5. Click the Print button . The Print dialog box appears. 6. Click the down arrow next to the Color/Grayscale field to select whether you want your slides to print in color, grayscale, or black and white. If you are using a black and white printer, choose black and white. You will use less ink or toner. 7. Set the other print settings. 8. Click OK. Your slides print. Print Your Slides as a Handout Click the Microsoft Office button. A menu appears. Choose Print. Click Print Preview. The Print Preview tab appears. Click the down arrow next to the Print What field in the Page Setup group and then select Handouts (4 slides per page). Click the Print button . The Print dialog box appears. Click the down arrow next to the Color/Grayscale field to select whether you want your slides to print in color, grayscale, or black and white. If you are using a black and white printer, choose black and white. You will use less ink or toner. Set the other print settings. Click OK. Your handouts print. EXISTING POWER POINT When all the tasks relating to the presentation have been completed, you can close the PowerPoint application. To close the PowerPoint application, click Exit on the Microsoft Office Button. PowerPoint will be closed. Keystrokes Used During a Slide Show Keystroke Action ENTER, SPACEBAR, N, DOWN Advances to the next slide ARROW or PAGE DOWN P, BACKSPACE, UP ARROW or Goes back to the previous slide PAGE UP Slide Number and then ENTER Goes to slide number B Displays or turns off a black screen W Displays or turns off a white screen ESC Ends the slide show CTRL + P Changes the mouse pointer to a pen, allowing you to make notations on the screen during the slide show. To restore the original shape of the mouse pointer, press ESC. When you have finished running your presentation, you will want to exit the slide show and close the file. 1. To exit the slide show, press ESC. 2. To close a presentation, click Close on the Microsoft Office button. Alternatively, to close a presentation, press ALT + F4 248 Knowledge Check Points a) To create a new blank presentation you could _____. a. click on the New button b. use the Office button| New command c. both of the above d. none of the above b) The primary goal for your slide design should be _____. a. to attract the eyes of your audience b. to coordinate with your company logo and color scheme c. to make the information easy to read d. to make the slides interesting and even exciting c) How do you add a slide a. Go to file and click New b. Go to HOME tab and click new Slide c. Go to slide show and click custom animation. d) Which type of template provides a design concept, fonts, and a color scheme for a presentation? a. Format b. Normal c. Content d. Design e) You're giving your presentation, and you need to click to a slide that's a few slides back. How do you get there? a. Press ESC to get back into normal view; click the correct slide thumbnail in normal view; then click the Resume Slide Show button. b. Press BACKSPACE until you hit the slide you're looking for. c. Right-click, point to Go on the shortcut menu, point to By Title, and click the slide you want to go to. 249 f) Suppose you want to create a slide that contains the heading Parts of a computer followed by a list of various parts and a picture of a computer. For this purpose, you can use the _____________ layout. a. Title Only b. Title Slide c. Title and Text d. Title, Text and Content g) To modify an animation effect, you can use _____. a. the Custom Animation task pane b. the Effect Options dialog box c. Both a) and b) d. None of the above h) Using a custom animation effect, how do you make text appear on a slide letter by letter? a. Apply the animation scheme Fade in one by one. b. Apply an entrance effect, and then set it to by letter in the Effect Options dialog box. c. Apply the Fly In entrance effect to the text, and then set its speed to Very Slow. i) The effect that looks like the new slide is pushing the old one off the screen is an example of a _____. a. slide transition b. slide animation c. custom animation d. none of the above j) This is not one of the view options provided by PowerPoint to look at and modify your presentation. Slide Show Format Slide Normal Slide Sorter The commands used to change views in PowerPoint are located on this tab. Home View Design Animation You can quickly navigate through your slides by: Using the vertical Scroll Bar to the right of your slide OR using the Page UP and Page Down keys on the keyboard, OR using the double arrows at the bottom of the vertical Scroll Bar Using the RIGHT or LEFT arrows on the keyboard Using the [ENTER] key on the keyboard Using the UP or DOWN arrows on the keyboard a. b. c. d. k) a. b. c. d. l) a. b. c. d. 250 m) a. b. c. n) o) a. b. c. d. p) a. b. c. d. q) a. b. c. d. r) 1. 2. 3. 4. Your employee has created a presentation on Spic and Span. He has spelt the word conservation as conservation. He wants to correct the spelling. How can he do this? He can place the insertion point before the letter to be deleted, press BACKSPACE, and then type t. He can place the insertion point after the letter to be deleted, press DELETE, and then type t. He can place the insertion point after the letter to be deleted, press BACKSPACE, and then type t. At the time of slide show, you want to change the shape of the mouse pointer to a pen. To do so, you need to press _____ + ___. You are viewing the third slide of a presentation in slide show. You want to end the slide show. To do so, you need to press ________ Esc Ctrl Shift Spacebar You want to change the order of slides in a presentation. To do this quickly and easily, you can use the ________ view. Notes Page Slide Sorter Outline Normal You want to include notes for the slides in your presentation. To do so, you can use the ____________ view. Notes Page Slide Sorter Outline Normal You are viewing the second slide of a presentation in slide show. You want to navigate to the tenth slide. To do so, you need to type 10, and then press ______ key. Enter Spacebar Ctrl None of the above Hands on Activities Guided Practice 1 In this activity you will create a simple presentation 1. Open the PowerPoint and create a new blank presentation. 2. Choose the “ layout” in home tab.. 3. The Title text is: My First Presentation 4. The subtitle text is: Your First and Last name 5. Go to Office button and Save the Presentation with the file name PP1. 6. Close the presentation. Guided Practice 2 251 In this activity you will apply colors, font style to Text, background color and Slide Design for the PowerPoint presentation. 1. Open any PowerPoint presentation which had been already created. To apply a color scheme 2. Go to Design tab. 3. In the Slide Design task pane, click themes. 4. Click a gray color scheme to apply the style. To change background color 1. On the Design tab, click Background. 2. Under Background fill, select the color as desired. 3. Click Apply. To change background texture 1. On the Design Tab menu, click Background. 2. Under Background fill, click the arrow on the right of the drop-down menu, and click Fill Effects.... 3. Select the Texture tab, and then double-click a texture. 4. Click Apply. 5. Format text as follows: a. Change the font of text on all slides to Century Gothic. b. Change the font size of the slide headings to 40. c. Italicize the title of the presentation. d. Change the font color of the text to blue. 6. Save and close the presentation. Exit PowerPoint. Guided Practice 3 a. b. c. d. a. b. c. d. a) The area on a slide that holds text that will appear in the presentation outline is a _____. textbox placeholder bullet point title box b) PowerPoint can automatically reduce the size of your text when there are too many characters to fit into the placeholder. This feature is called _____. AutoCorrect AutoFit Auto Layout Auto Align 252 c) Once you have modified a color scheme, you _____ save it for use later in a different presentation. a. can b. can not d) To select ALL the text within a box (for example, a bulleted text box) WITHOUT highlighting the text manually, you can click anywhere inside the box, then click the border of the box. a. True b. False e) You can set custom animation on an object in a number of ways. Which item below is NOT a method for setting animation? a. Right click on the object, select 'Custom Animation', then add the effect b. With the object selected, from the Task Pane, select 'Custom Animation' from the Task Pane dropdown arrow, and add the effect c. With the object selected, from the tabs, select SLIDESHOW/Custom Animation, and add the effect d. With the object selected, from the tabs, select INSERT/Custom Animation and add the effect f) In PowerPoint 2007 and higher versions, you can set multiple custom animations on an object. a. True b. False g) To make a new slide within a presentation, what shortcut key can you use? a. CTRL/I b. CTRL+S c. CTRL+M d. There is NO shortcut key to insert a new slide h) Reena has created a slide about aircraft in her presentation. She wants to add a picture of an aircraft to the slide, but she does not have one. What is the easiest solution? a. Use the Clip Art gallery to insert a relevant picture. b. Draw the picture and show it to the audience separately from her presentation. c. Ask the audience to imagine an aircraft, because she does not have a picture. i) Praveen wants to include a picture in a slide. He wants to insert a picture of a computer that he has created by using the Paint application. How can he do that? a. It is not possible to insert pictures created with Paint in a PowerPoint slide. b. By using the From File command on the Insert tab. c. By using the From File command on the View tab. j) Diya has created a presentation. There are two slides in the presentation that she does not want to appear during the slide show. What should she do? a. Delete the two slides. b. Hide the slides. c. Add special effects to the two slides. 253 k) Deepak has created a presentation on the topic of wildlife conservation. He wants to add a different animation effect to each item on a particular slide. Which option should he use? a. Animation b. Custom animation c. Color l) Harpreet creates a presentation about Independence Day. She wants to add an entry animation effect to the objects on the slide. Which command should she use to do this? a. Emphasis b. Start c. Entrance m) You save a presentation in the My Documents folder, and then close it. You open the file and make some modifications to it. However, you want to be able to compare the previous work to the changes, and have the old version, as well as the new. How can this best be accomplished? 1. By printing out the previous work and saving the new, revised presentation. 2. This cannot be done. 3. By using the Save As feature in PowerPoint to save one of the presentations with a different filename. Guided Practice 4 In this activity, you will create a presentation to introduce a lesson in your classroom. Include the following topics for creating a PowerPoint presentation: a. Recap of the subject matter from the previous classes b. Introduction to the lesson c. Description of the topic d. List of sub-topics that will be covered e. Activities that will be done during the lesson f. Expected outcomes g. How the student learning will be evaluated h. Duration of the lesson Following points should be kept in mind while creating the above presentation. Prepare at least six slides. Topic title, grade level and your name should appear on the first slide. Choose bullet list layout for describing the content. For all the slides set the slide design background of your choice. For all the slides set the animation schemes of your choice. Save the presentation in the My Documents with the filename “lessonintro”. Close the file and exit from PowerPoint application. 254 Guided Practice 5 In this activity, you will navigate slides and make changes to the presentation. 1. Start PowerPoint. Open the presentation “lessonintro.ppt.” 2. View the third slide of the presentation, and then navigate to the last slide. 3. Add another slide and type in the “list of references” for the lesson. 4. Save and close the presentation, then exit PowerPoint. Guided Practice 6 In this activity, you will change the style of the bullets used in a presentation. You will also align the text in the presentation; change the font size, font style and font color of text in a presentation. 1. Start PowerPoint and open the file “lessonintro.pptx”. 2. Change the font of the entire presentation to Verdana. 3. Change the font size of the presentation title to 36. 4. Change the font style of the presentation title to bold. 5. Italicize the text in the subtitle area of the title slide. 6. Align the text to the right in the subtitle area of the first slide. 7. Apply an attractive bullet style to the bulleted text in the slides. 8. Print your slide in Slides View. 9. Save the changes and close the file. Guided Practice 7 In this activity, you will view the presentation in various modes and save the presentation. a. Open the presentation “lessonintro.pptx”. b. Switch to Notes Page view. c. Type notes for all the slides. d. Switch to Slide Sorter view to view miniatures of the slides. e. Switch to Normal view. f. Print the presentation with the notes. g. Run the presentation from slide show view. h. Save and close the presentation. Guided Practice 8 1. The Print dialog does NOT allow you to choose _____. a. a print layout b. page orientation c. which slides to print d. a printer 2. In Normal view, this tab displays the content of each slide. a. Slides b. View c. Outline d. Sort 3. This is not one of the view options provided by PowerPoint to look at and modify your presentation. a. Slide Show b. Format Slide c. Normal d. Slide Sorter 4. Ashish wants to print the slides of a presentation so that he can show them to his manager. However, he does not have enough paper to print one slide on each page. He decides to print 255 two slides per page. Which command should he click under Print what of the Print dialog box to do this? 1. Notes Page 2. Outline View 3. Handouts Skill Check Points Self Practice 1: In this activity, you will create a presentation to teach a lesson in your classroom. Include the following topics for creating a PowerPoint presentation: i. j. k. l. m. Description of your topic Important sub-topics to be covered Images and videos to support the content Thought provoking questions List of references Following points should be kept in mind while creating the above presentation. 1. 2. 3. 4. 5. 6. 7. 8. Prepare at least ten slides. Topic title, grade level and your name should appear on the first slide. Choose bullet list layout for describing the content. Create charts and tables to support the content. For all the slides set the slide design background of your choice. For all the slides set the animation schemes “Ellipse motion”. Save the presentation in the My Documents with the filename “Lesson”. Close the file and exit from PowerPoint application. Self Practice 2: In this activity, you will navigate slides and make changes to the presentation. 1. Start PowerPoint. Open the presentation “Lesson.pptx.” 2. View the fourth slide of the presentation, and then navigate to the first slide. 3. Add your last name also along with the first name. 4. In the subtitle area, type today’s date. 5. Save and close the presentation, then exit PowerPoint. Self Practice 3: In this activity, you will change the style of the bullets used in a presentation. You will also align the text in the presentation; change the font size, font style and font colour of text in a presentation. A. Start PowerPoint and open the file “Lesson.pptx”. B. Change the font of the entire presentation to Comic Sans MS. C. Change the font size of the presentation title to 48. D. Change the font style of the presentation title to bold. E. Italicize the text in the subtitle area of the title slide. F. Align the text to the right in the subtitle area of the first slide. G. Apply an attractive bullet style to the bulleted text in the slides. H. Save the changes and close the file. Self Practice 4: 256 Pretend you are the Principal of the school, or you are one of the members of the school management committee. Prepare a presentation spotlighting why your school is the best. Include: 1. 2. 3. 4. Vision of the school Curricular and co-curricular activities available Other facilities available Staff qualification and experience Self Practice 5: In this activity you will design a PowerPoint presentation of 4 slides for your resume. Follow the following points for the content of your resume. Open Microsoft PowerPoint 1. Insert Title slide and type the following with the specified fonts: a. Your name: 48-point, Times New Roman, bold b. Your address and phone number: 24-point, Times New Roman, italic c. Your e-mail address: 18-point, Times New Roman, underline d. Draw a rectangle around the name/address box, and fill the box purple. e. Go to design tab and change the background, light blue for all the slides. 2. Your Mission Statement: Please type out at least two paragraphs of your Mission Statement. For this insert new slide and choose the layout “Title and Text”. Draw a rectangle around it. Color the letters WHITE and BOLD them; change the background light blue. 3. Your Education and Objective: a. List your education: University followed by Community College, if necessary. List your anticipated degree, department, and date of expected graduation. b. Below that, in a box, please type out your career objective, in 24-point, Times New Roman, italic and bold. Make the letters WHITE and the background light blue. 4. Your Work Experience: a. On the new slide make a bulleted list of your work experiences (job, employer, date of joining). Follow each with a brief one or two-sentence description of what the business does, and what your role was at the employer. 5. Save the presentation in the My Documents with the file name “My Resume”. 6. Close the file. Self Practice 6: In this activity, you will view the presentation in various modes and save the presentation. Open the presentation “My Resume”. Switch to Notes Page view. Type notes for second slide. Switch to Slide Sorter view to view miniatures of the slides. Switch to Normal view. Run the presentation from slide show view. Save and close the presentation. 257 Chapter Six Internet and Security Spotlight 1. What is Internet 2. Internet Search engines 3. Finding Information from web 4. Communicating Wisely 5. E- Mails Management 6. Computer Virus 7. Knowledge Check Points 8. Hands on Activities 9. Skill Check Points 258 Introduction to Internet What is Internet? The Internet is a worldwide network of computer networks. Consider a network of computers in the administrative office of your school and another network of computers in the computer lab of your school. Assume that the two networks spread over different locations are connected together so that you can send and receive data from a computer on one network to a computer on the other network. Similarly, when several networks are connected together, a network of networks is formed. The internet connects millions of computers all over the world, forming a network in which computers across different locations can communicate with each other. The Internet represents the transformation and evolution of the information age. The flexibility, ease and speed with which people can communicate by using the Internet, as compared to the other means of communication, have made it very popular. Advantages of the Internet The Internet is a vast sea of information. It provides information on all topics and can be accessed by people across the globe. All you need in order to gain access to the Internet is a PC, a modem and a telephone line through which you connect to the Internet Service Provider (ISP). Internet Service Providers are companies that provide access to the Internet. The Internet is simultaneously all of the following: Network Medium Marketplace Transaction Platform Source of Information The Internet as a Network Organizations use the Internet to link their offices and employees, thus using the Internet as a private network. Such a network can be used to transfer official data and to conduct meetings and conferences. The Internet as a Medium The Internet is used as an effective means of communication for product marketers, corporate communications and so on. For example, by using the Internet, a company can advertise its products to the whole world the moment they are launched. The Internet as a Marketplace The Internet is a vast virtual market. Thousands of companies promote their products by advertising them on the Internet. They also allow you to order products on the Internet. This is called online shopping or e-shopping. For example, on the Web site www.indianbooks.com, you can shop for books and place orders online. The Internet as a Transaction Platform You can use the Internet to complete business and financial transactions online by connecting to suppliers, customers or financial institutions. The Internet as a Source of Information The Internet is a vast source of information. You can search for information on any topic by using the Internet. For example, you can search for information on the various cultures prevalent in India, the latest technologies followed in education or medicine and so on. You can also share information with others over the Internet by using various Internet services, such as e-mail and chat. 259 Connecting to the Internet Connecting a computer to the Internet involves the process of connecting your computer with another computer that provides the Internet services. (See figure below) To connect to the Internet, you need the following: Computer It must have sufficient memory to run your browser, along with other programs you might run simultaneously. Browser A browser is a software program that is necessary in order for you to view Web pages on the Web, for example, Microsoft Internet Explorer. Internet Connection The most widely used Internet connection requires a modem and a telephone line, but broadband connections are gaining in popularity. Internet Service Provider (ISP) Internet Service Providers are companies that provide access to the Internet. ISPs have computers that are always connected to the Internet. The biggest service provider in India is Videsh Sanchar Nigam Limited (VSNL*). Other common ISPs are Dishnet*, Sify*, Airtel* and Rediff*. Types of Internet Connection There are three different ways of connecting to the Internet. They are: Dedicated Internet Connection With a dedicated Internet connection, you can gain access to the Internet directly, without going through an ISP. A dedicated connection allows your computer to remain connected to the Internet all the time. You do not have to specifically dial up, as you would with a standard modem connection. A dedicated connection requires a leased telephone line, rented from a telephone company. Usually, large companies and universities have dedicated Internet connections. This type of connection is quite expensive, because it requires special hardware. Dial-up Internet Connection To use this type of connection, you have to purchase an Internet connection for a specific duration (typically, hours per month) from an Internet Service Provider. When you purchase an Internet connection, the ISP provides you with a CD that contains a software package, a user name and a password. To activate the connection, you have to install the software on the CD by following the step-by- step instructions provided during the process. After you install the software, you can connect to the ISP by dialing the ISP’s phone number. You need a telephone line to connect to the ISP and you have to provide your user name and password when you dial the ISP’s number. The user name and password are used to check whether you are an authorized user. When you are using the Internet through a dial-up connection, you cannot make or receive phone calls via the telephone line that your modem is using. Broadband Internet Connection 260 A broadband connection allows a great amount of information to pass through a high-capacity cable to speed up the delivery of data. Standard dial-up connections are sometimes described as narrowband. A broadband connection is a high-speed permanent connection to the Internet. You can stay connected to the Internet from the minute you turn on your computer until you turn it off. Broadband uses a DSL (Digital Subscriber Line) or a cable modem to connect to the Internet. A broadband connection can send and receive vast amounts of data up to 10 to 40 times faster than a standard dial-up connection. It uses a fibre-optic cable to transmit data at high speeds. A broadband cable is similar to a four-lane highway, whereas the conventional telephone network is similar to a narrow lane. What Is the Web (WWW)? The term World Wide Web (WWW) refers to the collection of information accessible on the Internet. The WWW is also referred to as the Web. The Web is similar to a library. It consists of millions and millions of pages of text, pictures, sounds and animation on various topics. These pages, called Web pages, are stored on different computers that are connected to the Internet. The Web pages have links between them, that is, when you click a certain word or picture in a page, it will take you to another page. These words or pictures that help you move from one page to another are called hyperlinks. A collection of related Web pages is known as a Web site. A Web site can be accessed by means of the unique name assigned to it. You need a browser, such as Microsoft Internet Explorer to view Web pages. Features of Web E-mail Newsgroups Chat Rooms Instant Messaging Search Engines These are discussed in detail in the next sessions. Web Addresses or URLs You know that each house has a unique address, which helps us to identify it. Every address has a door number, street name or number, city name and pin code. This address is used to locate a house. Similarly, each Web site has a unique address commonly referred to as a URL, that is, a Uniform Resource Locator. A URL specifies the exact location of the Web page on the Internet. Certain conventions have to be followed when naming a Web page. The following is an example of a URL: http://www.microsoft.com/catalog/navigation.asp. The explanation of the URL is given in the table below 261 Table Explanation of the Example URL URL Element Explanation http www Identifies the protocol necessary to retrieve the file. A protocol is a set of rules that enables computers to exchange information. There are several protocols used on the Web. Hyper Text Transfer Protocol is one of them. Indicates that the site is on the World Wide Web Microsoft Indicates the name of the Web site .com Indicates the domain type (in this case, commercial) of the Web site Specifies the path of the file stored on the Web server’s hard disk /catalog/navigation. Asp The domain name suffix (.com in the example above) in a URL is important because it provides information about the type of organization the Web site belongs to. Table lists some suffixes that you might commonly come across in a URL. There are more, but these are the most typical. Table: Common Domain Name Suffixes in a URL URL Suffix Represents .co Company .com Commercial organization .edu Educational institution .mil Military site .net Communications organization .gov Government department .org Non-profit organization Introduction to Internet Explorer As explained earlier, you need a software program called a Web browser to explore the information available on the World Wide Web. A Web browser is used to display Web pages on your computer. Microsoft* Internet Explorer* (IE) is a Web browser developed by Microsoft. It is one of the components of the Microsoft Windows XP* operating system. Starting Internet Explorer This section assumes that you are connected to the Internet. To explore the information available on the Web, you need to start Internet Explorer. To start Internet Explorer: Double-click the Internet Explorer icon on the desktop. Or, Click Start, point to All Programs, and then click Internet Explorer. Internet Explorer appears. (See figure below) 262 The Internet Explorer Interface The user interface of Internet Explorer is similar to that of Microsoft Office applications, such as Microsoft PowerPoint and Microsoft Word. Like these other interfaces, the Internet Explorer interface consists of a title bar, a toolbar, a menu bar and a status bar. In addition, it includes an address bar. (See Figure) The address bar displays the URL of the Web page you are currently viewing. The toolbar in IE provides navigation buttons that can be used to explore the Web. The Internet Explorer Toolbar You can move from one page of a Web site to another page of the same Web site or to a different Web site by clicking the hyperlinks on the page. The Internet Explorer toolbar provides various navigation buttons that can be used to move through the Web pages. Table describes the buttons available on the toolbar. Table: Buttons on the IE Toolbar and Their Functions Function Button Back Forward Stop Refresh Home Search Favorites Media History Mail Print To return to the previously visited Web page. To move to the Web page you were viewing before you clicked the Back button. To terminate the operation currently being performed by the browser. To retrieve a Web page again. Clicking this button updates the content of the current Web page with the latest content. To move to the default home page of the browser. To search the Web for information on a particular topic. To display the list of your favorite pages. To play music, video and multimedia files. To display the list of Web sites and pages that you have already visited. To read and send e-mail To print the current Web page. 263 Internet Search engines Most people are primarily interested in tools for finding information on the World Wide Web. There are millions and millions of web pages out there. However, as most of us have troubles finding an old letter on our own computer, how can we find relevant information on this "global hard drive"? After all, this is the closest thing we get to a World Wide Anarchy. A Web search engine is a tool designed to search for information on the World Wide Web. The search results are usually presented in a list and are commonly called hits. The information may consist of web pages, images, information and other types of files. an application that searches for, and retrieves, data based on some criteria, especially one that searches the Internet for documents containing specified words However, the main problem is not that the search engines and the search directories find too little, but that they find too much. It is hard to uncover the needle in a list of 400,000 hits. To get the right answer, you must ask the right question. By improving your searching skills you will be able to find what you are looking for faster and more efficiently. Originally there were two kinds of search services on the Web: 1. Search directories 2. Search engines. Search directories are hierarchical databases with references to websites. A search directory is not a search engine. Do not let the similarity of the search fields fool you. When you search a search directory, you search an index hand picked by a living and breathing human being like you and me and classified according to the rules of that particular search service. When you use a search engine, on the other hand, you search a database inventory gathered by software based robots that travel the net, indexing the text of the webpages they find. So why are the directories useful? The key word is relevance. The search engines give you thousands of hits, including webpages of -- well -- dubious quality. The sites listed in the search directories on the other hand will normally hold a minimum standard. Moreover, the directories are useful when you just have a general idea of what you are looking for. In the directories, however, you are guaranteed to find websites with a lot of information in the field of your choice. These sites will in turn contain links to other sites specializing in this field. Below we list some of the best search directories. The first page of the search directory normally gives you the most general categories like "Computers and Internet" or "Education". Click your way down the hierarchy to the right category, select the website you find the most interesting and start reading. If you use the search form when exploring a directory, remember that you are not searching the text of the actual web pages of a particular site. Instead you are searching the text contained in the site title and the description of the site. These are composed by the directory editors, and are often based on suggestions from the site owners themselves. In addition most directories will also search the words contained in the category titles or descriptions. Examples of search Directories: Yahoo! http://dir.yahoo.com/ Yahoo is the mother of all search sites, and by far the most popular. It is easy to use, and lists sites of high quality. If you are searching for a broad topic and you want a few good results, Yahoo! is the place to go. 264 Yahooligans: search directory for kids http://kids.yahoo.com/ http://www.yahooligans.com Yahoo! also has a The Open Directory http://www.dmoz.org/ The Open Directory is an open that is free index that any site can use.. About.com http://www.about.com/ About is different. Really different. While most search directories give you a site title and a one line description, About gives you in depth site reviews, articles written by specialists, and links to the best sites on the net. It is a directory, a magazine and an encyclopedia in one. The internet Public Library http://www.ipl.org Look smart http://www.looksmart.com WebBrain http://www.webbrain.com Search engines Search engines are a program that searches documents for specified keywords and returns a list of the documents where the keywords were found. Although search engine is really a general class of programs, the term is often used to specifically describe systems like Google, Alta Vista and Excite that enable users to search for documents on the World Wide Web and USENET newsgroups. Typically, a search engine works by sending out a spider to fetch as many documents as possible. Another program, called an indexer, then reads these documents and creates an index based on the words contained in each document. Each search engine uses a proprietary algorithm to create its indices such that, ideally, only meaningful results are returned for each query. None of them cover the whole Net, but some of them are quite large. Search engines should be your first choice when you know exactly what you are looking for. They also cover a much larger part of the Web than the directories. The major search engines are Google o http://www.google.com MSN o http://www.msn.com Yahoo! Search (which is not the same as the Yahoo! Directory) o http://www.saerch.yahoo.com Alta Vista o http://www.altaviata.com Excite o http://www.excite.com Bing o http://www.bing.com Ask. 265 o http://www..ask.com Meta search engines There are also "metasearch" services that search several search engines and directories at the same time, trying to extract the most relevant hits from all of them. Metasearch engines give you a small part of the results from each individual search engine. You might find it useful to start your searching with one of these, just to get a general feeling for what is out there. The main reason for using metasearch engines today is that some of them provide special features not found in the regular search engines. Ask o http://www.ask.com/ Clusty o http://clusty.com/ Clusty, uses a special clustering technology that sorts the results into different groups or "clusters" that might help you pinpoint the right set of web sites more easily. Dogpile o http://www.dogpile.com/ Metacrawler o http://www.metacrawler.com/ Kids friendly search engines Awesome Library - 14,000 carefully reviewed resources o http://www.awesomelibrary.org/ Berit's Best Sites - directory of kids' web sites. o http://www.beritsbest.com/search/ Britannica - websites, magazines, books and the Encyclopedia Britannica. o http://www.britannica.com/ INFOMINE - scholarly internet resources in K-12 o http://infomine.ucr.edu/cgi-bin/search?k12 SuperKids SuperSearch - selected sites o http://www.super-kids.com/ 100 Top Kid Sites - 100 Hand Picked Top Kid Sites o http://www.100topkid.com/ Awesome Library - K-12 education directory o http://www.awesomelibrary.org/ ExtremeKids.com - Kids-Links from education to games o http://extremekids.com/index.htm KidsClick - web directory by a bunch of librarians o http://www.kidsclick.org/ KidCyber - primary student research materials o http://www.kidcyber.com.au/ KidsKonnect - web directory maintained by educators o http://www.kidskonnect.com Ask for Kids o http://www.askforkids.com/ Specialized search engines 266 There are also what we call specialized search engines that focus on one type of information. Some of them just present sub-sets of what is found in the regular search engine results, while others may provide information not found there. 1. Geographical limited scope - India a. http://Guruji.com 2. Accountancy a. http://IFAC.net 3. Job a. http://Bixee.com b. http://monster.com c. http://recruit.net 4. Legal a. http://manupatra.com 5. Medical a. http://harvester.fzk.de/harvester/ b. www.nextbio.com/ (Life Science Search Engine) 6. Real property a. http://www.magicbricks.com 7. Video Games a. http://genieKnows.com 8. Maps a. http://Bing_Maps.com b. http://googlemaps.com 9. Question and answer: Human answers a. http://answers.com 10. Automatic answers a. http://askmenow.com b. http://brainboost.com c. http://trueknowledge.com Finding Information from web We learnt that Search engines are Web sites that are used to find information on the Internet. Searches are based on a word or a combination of words or topics. A few examples of search engines are MSN*, Google*, Khoj* and AltaVista*. Using search engines Some search engines provide a list of topics grouped under categories. They allow you to locate resources on a common subject quickly. These search engines are like libraries in which books on different subjects are categorized and arranged. You can start with a broad category and narrow down to subcategories until you find a direct listing of the pages you want. This type of search produces better results because the grouping of Web sites under various categories is usually done manually. To find some games for children by using the MSN search engine: 1. Open internet explorer and type http://www.msn.com in the address bar 2. Click the link Search on the MSN home page. (See figure below) 267 A list of categories will be displayed. (See figure below) 3. Click a category. In this case, click Games under the Entertainment category. (See figure below) A list of subcategories is displayed. (See figure below) 4. Click the topic you want. In this case, click Children’s Games. (See figure below) 5. You can click a link on the page or choose further subcategories to find the information you want. (See figure below) 268 Similarly, you can click the links that follow a category till you find the information you need. Some categories that are available on the MSN Search page are Sports, Computing, Travel and so on. Note: Some search engines display the search categories in their home page itself. You can choose a category from the list in the home page and search for the information you want. Keyword Search You can find information based on a word or a group of words. These words are called keywords. The search engine uses the keywords to locate the required information. This type of search can be used if you do not know the category under which you have to search for the information you seek. In this type of search, the search engines use a program called spider to visit Web sites, read the information on them and follow the links that the sites connect to. The spider returns the important words and phrases it identifies in each Web page to a central database. The spider periodically returns to the sites to check for any information that has changed. When you search for information using keywords, the search engine searches the database and returns the list of Web sites that contain the search text. Assume you want to search for information on the various methods of teaching by using the MSN search engine. You should type the words methods of teaching in the Search the Web box, and then click Search. The engine locates the Web pages that contain the phrase and displays a list of links. (See figure below) You can click a link to view the corresponding Web page. 269 Searching the Web using Boolean Logic You're hungry. You go into a restaurant, sit down by the table and wait for the waiter. The waiter arrives, coughs politely, and asks: "What do you want for dinner, sir?" or "What would you like today, madam?" "Food," you answer, "food". Fortunately, waiters are an understanding and patient lot. "Certainly, sir, what kind of food did you have in mind? May I recommend the salmon?" Your average search engine is not that understanding. A search for food in Google brings up some 977 million web pages. 977 million pages are just too many to see and locate desired information. And, no, the search engine does not try to find out what you're really looking for. So, what do you do? You refine your question. You become more specific. You provide more information. The more refined the information the less time you waste sorting the required information form the hundreds of pages listed. "I would like a pizza with pepperoni and ham, but with no olives and no garlic." If you are able to order a pizza like that, you are able to use advanced "Boolean" searching on the Internet. You have asked for pizza with pepperoni and ham, but without olives and garlic. Here's how your order will look using Boolean operators: pizza AND pepperoni AND ham AND NOT olives AND NOT garlic. A search engine would interpret this Boolean expression in the following way: "The user wants me to show him or her links to all the pages that include the word pizza as well as the word pepperoni and the word ham, but he or she wants me to subtract pages that include the word olives or the word garlic. It is logical and it works. The operator AND means that the word that follows has to be in the text of the pages that are to be listed. Pages including the words following AND NOT will not be listed. If you suspect that the restaurant is out of pepperoni, you may be a little more open-minded about this, and say: "I would like pepperoni or chicken". In Boolean terms that is: Pepperoni OR chicken On the Net an order like this one will give you all the pages that include the word pepperoni, all the pages that include the word chicken and all the pages that include both of these words. What happens if you take out the operators AND, AND NOT and OR and write the following line instead? pizza pepperoni ham olives garlic Most search engines interpret the space between the words as AND. That is, they will give you all the pages that include all these word. But that was not what you were looking for, was it? You are interested in pages that do not include the word olives or garlic, not in pages that have to include these words. Then again, some engines may interpret the space between the words as OR. This means that they will even give you pages that include only one of these words. You will, for instance, end up with a lot of irrelevant information about the garlic industry. At the moment true Boolean searching is supported by most of the major search engines. You can also use the mathematical symbols + for AND and, – for AND NOT 270 Browsing the Internet Browsing the Internet refers to viewing and moving through Web pages. To view a Web site: 1. Type the URL in the address bar. 2. Press ENTER. Suppose you want information about Office from the Microsoft Web site. 1. Type the Web site address www.microsoft.com in the address bar. 2. Press ENTER. The home page of the Microsoft Web site appears, as shown in figure below. The main page of a Web site is called its home page. You can move to other pages on the Web site by using hyperlinks. When you point to a hyperlink, the pointer changes to a hand . When you click a hyperlink, it takes you to the corresponding page. To go back to the previous page, click the Back button on the Internet Explorer toolbar. To return to the page from where you clicked Back, click the Forward button on the Internet Explorer toolbar. Note: To use the Back button, you should have visited at least two Web pages. Similarly, to use the Forward button, you should have used the Back button. To close Internet Explorer, click the Close button. Exploring the Web with Microsoft Internet Explorer You are familiar with the process of starting Internet Explorer and browsing the Web. In this session, you will learn about the other features of Internet Explorer. Changing the Default Home Page Suppose you view a Web page often and want the Web page to appear automatically when you start Internet Explorer. You can set the page as your home page. The first Web page that appears whenever you start Internet Explorer is called the default home page. Suppose you want to set your default home page to http://www.google.co.in. To set the default home page: 1. Open the Web page that you want to set as the home page. 2. On the Tools menu, click Internet Options. The Internet Options dialog box appears. 3. On the General tab, under Home page, click Use Current. You will notice that the address http://www.google.co.in appears in the Address box. 4. Click Apply, and then click OK. 271 When you open the browser window the next time, the home page of the Google Web site appears automatically. Adding a Web Site to Your Favorites List When you find Web sites or pages that you like and want to visit again, you can keep track of them by using the Favorites. This feature is used to store shortcuts to your favorite Web pages. It eliminates the need to remember the addresses of the Web pages you visit frequently. When you add a Web page to your list of favorite pages, you can open the Web page easily by clicking its shortcut on the Favorites list. You can also create folders for various categories of Web pages on the Favorites list and organize the Web pages in these folders. When you click the Favorites button on the toolbar, a list of Web pages, folders and files is displayed in the Favorites pane on the left side of Internet Explorer. To add a Web page to your Favorites list: 1. Open the page that you want to add to your collection of favourite pages. 2. On the Favorites menu, click Add to Favorites. The Add Favorite dialog box appears. 3. Click Create in to view the folder list in the Add Favorite dialog box. (See figure below) 4. Click the folder to which you want to add the Web page. If you want to add the Web page to a new folder, click New Folder to create the new folder. The Create New Folder dialog box appears. (See figure below) 5. Enter a name for the folder in the Folder name box. 6. Click OK. The folder is created. 7. Click OK to close the Add Favorite dialog box. The shortcut to the Web page is added to your list of favorite pages. Returning to Favorite Pages Suppose you have added www.Microsoft.com and www.Webopedia.com to your Favorites list. When you want to view these Web pages again, you can use the Favorites button on the toolbar to access these pages. To view a Web page added to your Favorites list: 272 1. Click the Favorites button on the toolbar. The Favorites pane is displayed on the left side of the browser window. (See Figure below) 2. Click the Web page you want to view. The page is displayed in the right pane of the browser window. (See Figure above) Tracking Your History of Recently Viewed Web Pages Consider the following situation. You want to view a Web page you visited recently but neither do you remember the address of the Web page nor have you stored it in your Favorites list. In such cases, you can use the History feature of Internet Explorer to view the Web page. The History folder contains a list of all the Web pages you have visited. It stores the links for Web sites and pages visited in previous days and weeks. To revisit a Web page you visited earlier: 1. Click the History button on the toolbar. The History pane appears. (See figure below) 2. Click a week or day. The list of Web sites you have viewed during the day or week is displayed. 3. Click a Web site to view the list of Web pages you visited on that site. 4. Click the Web page icon to view the Web page. Opening Multiple Browser Windows Sometimes, a Web page may take a long time to download. You can start another instance of Internet Explorer and open another Web page during that time. 273 Sometimes, you may want to view a Web page and also view a link on the page at the same time. To open a link in a new window, right-click the link, and then click Open in New Window. The Web page opens in a new browser window. To switch between the Web pages, you can either click the appropriate Web page button on the taskbar or use ALT + TAB. Stopping a Web Page from Loading Sometimes the Web page you want to view may take a long time to load. In such a case, you can stop the process by clicking the Stop button on the toolbar. You can also use the Stop button to stop loading a page you decide not to view. Refreshing a Web Page Consider a Web page that displays the scoreboard of an ongoing cricket match. These details are constantly updated. To view the updated scoreboard, you need to refresh the Web page. To refresh a page, click Refresh on the toolbar. When you click the Refresh button, Internet Explorer retrieves the latest version of the Web page from the Web. Internet Explorer File Management With Internet Explorer, you can not only view Web pages, but also save files, programs, audio files and pictures. This session explores how to download files and work offline. Downloading Files and Images If you find an interesting Web page while browsing the Web, you can save it for future use. The steps for saving a Web page are the same as those for saving a presentation in PowerPoint or saving a document in Word. You can also take print outs of the downloaded Web pages as you would take printouts of Word documents. The Internet also offers a vast collection of downloadable games, software, files and images, which you can download, install or save in your computer. For example, you can download MSN Messenger, a type of chat software, from the Microsoft Web site. Apart from software, you can also download images from the Web and save them on your computer. To save an image: 1. Right-click the image. (See figure below) 2. Click Save Picture As. The Save Picture dialog box appears. This dialog box is similar to the Save As dialog box in Word. 3. Specify the location where you want to save the picture. 4. Enter a name for the picture in the File name box. 5. Specify the format in which you want to save the picture in the Save as type box. 6. Click Save. The picture is saved in the specified location. Note: On some Web sites, you will find that when you point to the image, the Picture toolbar appears. Click the Save this image button on the Picture toolbar to save the image. Working Offline 274 You can also view your favorite Web page without connecting to the Internet. One way of doing this is to save the Web page on your computer. However, you will not be able to view the updated contents of the Web page, and the Web page has to be saved in a specified location. To overcome this problem, you can use the Offline feature of the Web browser. When you make a Web page available offline, you can view its contents without connecting to the Internet, and the Web page appears in the Favorites list of the browser. Note: You can make either a single Web page or an entire Web site available offline. To make the current Web page available offline: 1. Open the Add Favorite dialog box. 2. Select the Make available offline check box. 3. Click OK. The Synchronizing dialog box appears. The synchronization is performed, and the Web page is made available offline. (See figure below) After you make a Web page available offline, you can view it without connecting to the Internet. To view a Web page offline, click Work Offline on the File menu. The Web page is now available offline and the title bar of Internet Explorer shows the status information “Working Offline” along with the title of the Web page. (See figure below) Note: When you click Work Offline on the File menu, you will only be able to view the Web page in offline mode. To get back to the online mode, click Work Offline again to clear the check mark. 275 Fair use guidelines This addresses issues concerning the use of copyrighted material in an academic setting. Guidelines for protecting works created by faculty and students are available from the library. What is a copyright? A copyright is the set of exclusive legal rights authors have over their works for a limited period of time. These rights include copying the works (including parts of the works), making derivative works, distributing the works, and performing the works (this means showing a movie or playing an audio recording, as well as performing a dramatic work). Currently, the author's rights begin when a work is created. A work does not have to bear a copyright notice or be registered to be copyrighted. Why do we have copyright? The Constitution of the United States says that its purpose is to promote science and the useful arts. The government believed that those who create an original expression in any medium need protection for their work so they can receive appropriate compensation for their intellectual effort. What is a work in the public domain? A work in the public domain can be copied freely by anyone. Such works include those of the Government and works for which the copyright has expired. Generally, for works created after 1978, the copyright lasts for 70 years beyond the life of the author. Works created before but not published before 1978 have special rules. For works created and first published between 1950 and 1978 the copyright lasts for 95 years. For works created and first published before 1950, the copyright lasts for 28 years but could have been renewed for another 67 years. When planning a project, start by identifying works in the public domain which can be repurposed in the new work. Request permissions for materials not in the public domain early in the project. If there are images or sounds for which permission to copy cannot be obtained, it is easier to redesign the project at the beginning rather waiting until the project nears completion. What is fair use? Fair use provisions of the copyright law allow for limited copying or distribution of published works without the author's permission in some cases. Examples of fair use of copyrighted materials include quotation of excerpts in a review or critique, or copying of a small part of a work by a teacher or student to illustrate a lesson. How can I tell if my copying is allowed by fair use provisions of the Law? There are no explicit, predefined, legal specifications of how much and when one can copy, but there are guidelines for fair use. Each case of copying must be evaluated according to four factors: 1. The purpose and nature of the use. If the copy is used for teaching at a non-profit institution, distributed without charge, and made by a teacher or students acting individually, then the copy is more likely to be considered as fair use. In addition, an interpretation of fair use is more likely if the copy was made spontaneously, for temporary use, not as part of an "anthology" and not as an institutional requirement or suggestion. 2. The nature of the copyrighted work. 276 For example, an article from a newspaper would be considered differently than a workbook made for instruction. With multimedia material there are different standards and permissions for different media: a digitized photo from a National Geographic, a video clip from Jaws, and an audio selection from Peter Gabriel's CD would be treated differently--the selections are not treated as a equivalent chunks of digital data. 3. The nature and substantiality of the material used. In general, when other criteria are met, the copying of extracts that are "not substantial in length" when compared to the whole of which they are part may be considered fair use. 4. The effect of use on the potential market for or value of the work. In general, a work that supplants the normal market is considered an infringement, but a work does not have to have an effect on the market to be an infringement. How can a work reference the copyright owner of digital photographs, video, or sounds? Include the copyright symbol and the name of the copyright owner directly on/under/around the digital material. It is virtually impossible to ensure that digital information located at any distance from the image/video would be seen by a user if the copyright notice is not directly attached to the material. If the material is only used once for a class or a project, does the copyright owner need to be acknowledged? Images, graphics and video should be credited to their owners/sources just as written material. Also, if you should change your mind and want to use material for commercial purposes, then it is important that you would know where and when you found the material and who the copyright owner is. Can I download information to my computer? Digital resources are mostly allowed for the non-profit educational use. Systematic downloading, distributing, or retaining substantial portions of information is prohibited. Following are the copying limits. The smallest amount of . . . Motion Media 10% or 3 minutes Text 10% or 1000 words Poetry 250 words; no more than 3 poems by same author Music, Lyrics, Video 10% or 30 seconds Photos & Illustrations 5 images from one author Numerical Data Sets 10% of 2500 fields or cells 277 What should I do if I want more information? Contact the website or the individual who has created the resource on the web and ask for permission citing the reason you want the use of the resource. Communicating Wisely E-mail is one of the most revolutionary inventions of this century. It stands for electronic mail. You can use it to send letters, documents, information, and projects from one part of the world to another almost instantaneously. Email is a cost effective and fairly reliable means of communication. You will find that sending Email is more convenient. After all, there are no stamps to be pasted and no need to go to the nearest post box to post the letter. Most importantly, it will take probably 7 minutes instead of 7 days to reach its destination. Now let us discuss some features of E- mail Electronic mail (e-mail) is a message sent electronically over the internet. Here are a few e-mail terms that you should be familiar with. Address book: list of personal contact with their e-mail addresses Forward: sends the original message on to someone else Reply: sends a e-mail to the sender of the message you are currently reading (sort of like someone sending you a self addressed stamped envelope) - this copies the senders e-mail address as well as the text from the message, you type your additional comments if necessary and send the message. Attachments: sends actual documents created with other programs along with (or attached to) your email CC: carbon copy -sends the same message to several people (separate their addresses with commas) BC: blind carbon copy - send message to several addresses without showing everyone all of the addresses (this is a good way to avoid those annoying messages that are 2 lines but 4 pages of addresses you really could care less about) Bounced: if a message has an invalid e-mail address it will be marked undeliverable and will bounce back to your e-mail 278 Creating and using E-Mail account Let us try opening an e-mail account in Yahoo! though you many use any other free e-mail service. The process of opening an account will be broadly the same everywhere. Start the Browser by double clicking on the Browser Icon on the Desktop After starting the browser, enter the address http://mail.yahoo.com, in the address bar. You’ll notice the Window as shown below: Click on Sign Up 279 Once you click there, you would see the following form. Fill up the form. The most important part of the registration form is the Yahoo! Mail Name and password. Enter a mail name (this is the same as e-mail ID), which is unique. Remember that you can only include letters, numbers and ___(underscore).if you add any other type of character, Yahoo will not accept them. Enter a password, which you will not forget but which others will find hard to guess. Password Question: Here you must enter a question that will remind you of the password. Secret Answer: If you supply this answer, Yahoo will help you retrieve your password in case you forget it. Next you are asked a series of question relating to personal details: first and last name, birth date, gender, industry, occupation, country, postal code, city, state, time zone (for India this is GMT +5.5) and primary language. 280 You will need to enter the verification code as it is written. This code will vary for every account. Finally click on the I Agree the Yahoo ID enter is already taken, button. In case If all entries in the form are valid, you get enrolled as a member of Yahoo service, A welcome message appear. Yahoo will ask form securely You have successfully created your ID. Your ID is the first part of your address i.e. all the words 281 and No. that are before the @ sign. ID is for your use: to check your mail. Address is inclusive of @ yahoo.com/ co. in. You give your complete address to people to receive mails. Know the difference between email addresses & Website addresses: Anything with an @ sign (i.e. webmaster@nwrel.org, george@mycats.com) is an email address, Anything with www or http is a WWW address (i.e. http://www.nwrel.org, www.washingtonpost.com) E- Mails Management How do I read my mail? Start the Browser by double clicking on the Browser Icon on the Desktop 282 You’ll notice the Window as shown below: After starting the browser, enter the address http://mail.yahoo.com, in the address bar. Fill up your ID and password and click on sign in The main page of the Yahoo mail service has the following menu: Click on the Inbox option. You are taken to the mailbox where all mails you have received is listed 283 To open a mail, double click on the subject of the mail After reading the mail, click on the Back button, to return to the mailbox. After you have read a mail, and want to either Reply to the Sender or Forward it to Someone Else by Clicking on the required button. After reading the mail, click on the Back button to return to the mailbox . If you Reply the Address of the Sender is already inserted in the to column If you forward you have to write the complete address of the Person you are forwarding the Mail to in the To Column 284 After you have read a mail, you may want to delete it. Select the mail and then click on the Delete button (or move to trash can) button. Once you have moved mail to the trash can, it lies there for sometime. Yahoo empties the trash can automatically from time to time.How Do I send mail? To send mail, click on the Compose option in the Yahoo main menu. The following window appears: You will see the above Window 285 In the To box, enter the email address of the person to whom you are sending this email. You can add CC and BCC column by clicking on the required Icon. Cc and Bcc: If you enter two more addresses in these boxes, a copy of the same letter goes to these addresses. You can add more than one address in each of the boxes (To, CC, BCC). Each address should be separated with a comma. You can write up to 50 address in each box . 286 Next in the Subject, enter a topic for your letter. Next type the letter in the box below. If you wish to save time on the Internet, type your letter in any word processor application before going online, then Copy ( Ctrl+C ) and paste (Ctrl+V) it in this grid box. Attachments: When you want to send a file which is rather large in size, you may use the Attachment option. Below the subject in the Compose window, you will find the Attach Files button. Click on it . The Attachment window appears. Click on the Browse button. 287 Select a path to the file that you want to attach. want to attach then click on the open attach a maximum of 5 files but y n . 288 Opening and downloading attachments Open the message, which has the attachment by clicking on the subject of the mail of the mail with an attachment. The Mail which has an attachment can be identified by the Clip that appears in front of the subject of the Mail. 1. Once the mail is open Click on the attachment button. Once the attachment is scanned 2. Click on download attachment link, and then when asked click on the open button. 3. The file will open and then you can save the file by clicking on file –Save as option. And selecting the desired location 4. Once you have finished checking and sending mails sign out of your account by clicking on the sign out option For mat ting text You can format the text message using the tool bar in the same way as you do in other Office documents. You can change the style, size and alignment of the message as you wish. Printing an email To print an e mail click on file print select no. of copies and print. Net Etiquettes: Netiquette Netiquette is a set of rules (mainly unwritten) to follow while your on-line. These rules have sort of evolved and exist to make the internet a better place. While these are not carved in stone - you may become un-welcomed if you deviate too far from them. Some places on the net have different variations of what is considered acceptable. Remember that no matter where you are (online or in real life) you are the only one that is accountable for your actions. We expect other drivers to observe the rules of the road and the same is true as we travel through cyberspace. Here are a few pointers to help you out: 1. Avoid writing e-mail messages or posting in newsgroups using all caps. IT LOOKS LIKE YOU'RE SHOUTING! 2. Keep your communications to the point. Some people pay for Internet access by the hour. The longer it takes to read your messages, the more it may cost them. 3. You should never do anything online that you wouldn't do in real life. Being online does not hide your identity or turn you into anything less that you are. 4. Remember your audience. These are real people that you are communicating with. If you wouldn't say something to their face - you should not say it over the internet. If you are 289 5. 6. 7. 8. 9. sending a message to a listserv remember that there could be lots of people that you have never meet reading your comments. Respect your audience. Good discussion should always be welcomed but don't waste other peoples time with idle nonsense. If you respond to a listserv and mean to send a private message to one person - you have wasted a lot of peoples time and possibly shared information that was not intended to be viewed by anyone else. Before you participate in a newsgroup discussion - read the FAQ (frequently asked questions). NEVER send unsolicited junk mail. Don't forward junk-mail. Don't forward chain letters. Don't forward the letter from Bill Gates saying that the first 1,000 people to forward this letter will get money. It is not real. If it says "FORWARD" this to everyone you know - DON'T. Don't try to gain access to places or resources that you don't have the proper permission. To add humor and personality to your messages, use smiley, also known as emoticons, expressions you create from the characters on your keyboard. A few popular ones include: :-) Happy :-e Disappointed :-( Sad :-< Mad :-o Surprised :-D Laughing :-@ Screaming ;-) Winking :-I Indifferent Computer Virus Computer viruses are programs written by "mean" people. These virus programs are placed into a commonly used program so that program will run the attached virus program as it boots, therefore, it is said that the virus "infects" the executable file or program. Executable files include application programs [such as word processing programs and spreadsheet programs. A virus is inactive until you execute an infected program or application OR start your computer from a disk that has infected system files. Once a virus is active, it loads into your computer's memory and may save itself to your hard drive or copies itself to applications or system files on disks you use. Some viruses are programmed specifically to damage the data on your computer by corrupting programs, deleting files, or even erasing your entire hard drive. Many viruses do nothing more than display a message or make sounds / verbal comments at a certain time or a programming event after replicating themselves to be picked up by other users one way or another. Other viruses make your computer's system behave erratically or crash frequently. Sadly many people who have problems or frequent crashes using their computers do not realize that they have a virus and live with the inconveniences. It is important to note that a virus cannot be spread without a human action, (such as running an infected program) to keep it going. People continue the spread of a computer virus, mostly unknowingly, by sharing infecting files or sending e-mails with viruses as attachments in the e-mail. Computer virus verses biological virus 290 A biological virus spreads by inserting itself into living cells. A computer virus behaves in a similar way. Extending the analogy, the insertion of a virus into the program is termed as an "infection", and the infected file, or executable code that is not part of a file, is called a "host". A computer virus will pass from one computer to another like a real life biological virus passes from person to person. A computer "virus" can be defined as a piece of code with a self-reproducing mechanism riding on other programs which cannot exist by itself. The choice of the term Self-Reproducing Program (SRP) appears to be unambiguous in comparison to the word "virus". Virus classification Viruses can be subdivided into a number of types, the main ones being: 1. Boot sector viruses Companion viruses Email viruses Logic bombs and time bombs Macro viruses Cross-site scripting virus 2. Two other types of malware are often classified as viruses, but are actually forms of distributing malware: 3. Trojan horses Worms 291 Boot sector virus A virus written into the boot sectors of a floppy disk that infects the boot records on floppy diskettes and hard drives and is designed to self-replicate from one disk to another. A popular way to spread a virus when floppy disks were widely used, the boot virus relied on people forgetting to remove the last floppy they inserted when they turned the machine off. When turned back on, the machine read the boot sector program, which normally loads the operating system, but ran the infected program instead. Once infected, the boot virus replicated itself onto all subsequent floppies used in the machine. Companion Virus A companion virus does not have host files per se, but exploits MS-DOS. A companion virus creates new files (typically .COM but can also use other extensions such as ".EXD") that have the same file names as legitimate .EXE files. When a user types in the name of a desired program, if a user does not type in ".EXE" but instead does not specify a file extension, DOS will assume he meant the file with the extension that comes first in alphabetical order and run the virus. For instance, if a user had "(filename).COM" (the virus) and "(filename).EXE" and the user typed "filename", he will run "(filename).COM" and run the virus. The virus will spread and do other tasks before redirecting to the legitimate file, which operates normally. Path companion viruses create files that have the same name as the legitimate file and place new virus copies earlier in the directory paths. E-mail Virus An e-mail virus is computer code sent to you as an e-mail note attachment which, if activated, will cause some unexpected and usually harmful effect, such as destroying certain files on your hard disk and causing the attachment to be remailed to everyone in your address book. Although not the only kind of computer virus, e-mail viruses are the best known and undoubtedly cause the greatest loss of time and money overall. The Melissa virus macro virus and the ILOVEYOU virus are among the most famous e-mail viruses. Each of these also spawned copycat variations with different words in the subject line. The best defenses against e-mail viruses for the individual user are: 1. a policy of never opening (for example, double-clicking on) an e-mail attachment unless you know who sent it and what the attachment contains. 2. Look at Your Extensions! Files with .EXE or .VBS extensions are always suspect, because once the file name is clicked, the program is run, and it can do anything it wants within the computer. SHS files, a somewhat obscure file type, can also contain executable code. Another approach is to attach a Windows link file (.LNK), which is a shortcut, or pointer, to an executable file (.EXE) that is also attached. Since many have been warned not to click an .EXE attachment, the link file is a sneaky way of launching the .EXE file for unaware users. See dangerous extensions, e-mail bombing, virus, Klez, Worm. ExploreZip virus, BubbleBoy virus and SHS virus. 3. Installing and using anti-virus software to scan any attachment before you open it. Business firewall servers also attempt, but not always successfully, to filter out e-mail that may carry a virus attachment. 292 Logic Bomb A logic bomb Also called slag code, programming code is a piece of code intentionally inserted into a software of an application or operating system that lies dormant until a predetermined period of time and will set off a malicious function when specified conditions are met. For example, a programmer may hide a piece of code that starts deleting files (such as the salary database trigger), should they ever be terminated from the company. In fact, viruses that are set to be released at a certain time are considered logic bombs. They can perform such actions as reformatting a hard drive and/or deleting, altering or corrupting data. Software that is inherently malicious, such as viruses and worms, often contain logic bombs that execute a certain payload at a pre-defined time or when some other condition is met. This technique can be used by a virus or worm to gain momentum and spread before being noticed. Many viruses attack their host systems on specific dates, such as Friday the 13th or April Fool's Day. Trojans that activate on certain dates are often called "time bombs". To be considered a logic bomb, the payload should be unwanted and unknown to the user of the software. As an example, trial programs with code that disables certain functionality after a set time are not normally regarded as logic bombs. Macro Virus In computing terminology, a macro virus is a virus that is written in a macro language: that is to say, a language built into a software application such as a word processor. Since some applications allow macro programs to be embedded in documents, so that the programs may be run automatically when the document is opened, this provides a distinct mechanism by which viruses can be spread. This is why it may be dangerous to open unexpected attachments in e-mails. Modern antivirus software detects macro viruses as well as other types. A macro virus can be spread through e-mail attachments, discs, networks, modems, and the Internet and is notoriously difficult to detect. Uninfected documents contain normal macros. Most malicious macros start automatically when a document is opened or closed. A common way for a macro virus to infect a computer is by replacing normal macros with the virus. The macro virus replaces the regular commands with the same name and runs when the command is selected. In the cases where the macro is run automatically, the macro is opened without the user knowing. Once the application opens a file that contains a macro virus, the virus can infect the system. When triggered, it will begin to embed itself in other documents and templates, as well as future ones created. It may corrupt other parts of the system as well, depending on what resources a macro in this application can get access to. As the infected documents are shared with other users and systems, the virus will spread Cross Site scripting Virus Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications which allow code injection by malicious web users into the web pages viewed by other users. Examples of such code include client-side scripts. An exploited cross-site scripting vulnerability can be used by attackers to bypass access controls such as the same origin policy. Vulnerabilities of this kind have been exploited to craft powerful phishing attacks and browser exploits. Cross-site scripting carried out on websites were roughly 80% of all documented security vulnerabilities as of 2007. Often during an attack "everything looks fine" to the end-user who may be subject to unauthorized access, theft of sensitive data, and financial loss. Worm and Trojan 293 A worm is similar to a virus by design and is considered to be a sub-class of a virus. Worms spread from computer to computer, but unlike a virus, it has the capability to travel without any human action. A worm takes advantage of file or information transport features on your system, which is what allows it to travel unaided. The biggest danger with a worm is its capability to replicate itself on your system, so rather than your computer sending out a single worm, it could send out hundreds or thousands of copies of itself, creating a huge devastating effect. One example would be for a worm to send a copy of itself to everyone listed in your e-mail address book. Then, the worm replicates and sends itself out to everyone listed in each of the receiver's address book, and the manifest continues on down the line. Due to the copying nature of a worm and its capability to travel across networks the end result in most cases is that the worm consumes too much system memory (or network bandwidth), causing Web servers, network servers and individual computers to stop responding. In recent worm attacks such as the much-talked-about Blaster Worm, the worm has been designed to tunnel into your system and allow malicious users to control your computer remotely. Trojan horse is not a virus. A Trojan Horse is full of as much trickery as the mythological Trojan Horse it was named after. The Trojan Horse, at first glance will appear to be useful software but will actually do damage once installed or run on your computer. Those on the receiving end of a Trojan Horse are usually tricked into opening them because they appear to be receiving legitimate software or files from a legitimate source. When a Trojan is activated on your computer, the results can vary. Some Trojans are designed to be more annoying than malicious (like changing your desktop, adding silly active desktop icons) or they can cause serious damage by deleting files and destroying information on your system. Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing confidential or personal information to be compromised. Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they self-replicate. Effects of Computer Virus 1. Viruses are programmed to damage the computer by damaging programs, deleting files, or reformatting the hard disk. 2. Computer viruses can not infect write protected disks or infect written documents. 3. Viruses do not infect compressed files, unless the file was infected prior to the compression. 4. Viruses do not infect computer hardware, such as monitors or computer chips; they only infect software. 5. Viruses do not necessarily let you know they are present in your machine, even after being destructive. 6. If your computer is not operating properly, it is a good practice to check for viruses with a current "virus checking" program. Vulnerability of Operating System to virus Another analogy to biological viruses: just as genetic diversity in a population decreases the chance of a single disease wiping out a population, the diversity of software systems on a network similarly limits the destructive potential of viruses. Microsoft software is targeted by virus writers due to their desktop dominance, and is often criticized for including many errors and holes for virus writers to exploit. Windows is by far the most popular operating system for virus writers, some viruses also exist on other platforms. 294 Protection from Virus 1. Load only software from original disks or CD's. Pirated or copied software is always a risk for a virus. 2. Execute only programs of which you are familiar as to their origin. Programs sent by email should always be suspicious. 3. Computer uploads and "system configuration" changes should always be performed by the person who is responsible for the computer. Password protection should be employed. 4. Check all shareware and free programs downloaded from on-line services with a virus checking program. 5. Purchase a virus program that runs as you boot or work your computer. Up-date it frequently. Use of popular Anti – virus software The internet is a glorious and exciting world, but unless you're properly protected with a good antivirus application, it can also be a dangerous one. Here is a list of excellent freeware software that can keep your computer safe from malware just as well as their more expensive counterparts. AVG Anti-Virus (Freeware and Shareware) The lightweight AVG Free provides protection against the various nasties floating around the internet. Like many of the options in the Hive Five, AVG provides freeware (with limitations) and commercial versions of their software, but most users find AVG Free is all they need— though many users prefer versions prior to the most recent 8.0 release. 1. NOD32 (Shareware) NOD32 is best known for its speed and small system footprint, but users also swear by NOD32 as a comprehensive and bulletproof solution. At $40/year for a home license, it's not free, but NOD32 die-hards claim the pricetag is well worth it. 2. Avast Antivirus (Freeware and Shareware) Available in both freeware (Home) and shareware (Professional) flavors, Avast Antivirus is the happy home of many an AVG-switcher. Avast is slightly heavier on system resources, but users argue its excellent protection more than makes up for the increased footprint. The freeware version will cost you an email address to get a free registration code from their website. 3. Avira AntiVirus (Freeware and Shareware) According to many of its users, Avira is the go-to freeware app for detecting viruses and other malware that other antivirus apps miss. Like several of its peers, Avira is available in both freeware (Personal) and shareware (Premium) versions, and most people find the freeware alternative plenty to suit their needs. One downside to Avira on install is pop-up ads enabled by default (adware, anyone?), but you can disable the ads with a couple of clicks. 4. Kaspersky Anti-Virus (Shareware) Fans of shareware antivirus app Kaspersky point out its consistently strong ratings in malware protection as well worth the $60 license. Kaspersky also boasts an extremely quick response time to new viruses, earning it a special place in the hearts and system trays of its users. 295 Knowledge Check Points a) How does the Internet serve as an effective communication medium? b) State differences between Internet and the World Wide Web. c) Statement: Web pages use hyperlinks to connect related topics together Reason: It is not possible to create Web pages without hyperlinks. a. The statement is true and the reason is valid. b. The statement is true but the reason is not valid. c. The statement is false but the reason is true. d) Identify the elements of the following Web site address http://www.computerworld.com/news e) What are the four elements necessary to establish an Internet connection? f) Match the following a. .edu Communications organization b. .mil Government department c. .net Commercial site d. .com Educational site e. .gov Military site g) Name the interface element in Internet Explorer that is not present in Word. h) Statement: The Web is a part of the Internet. Reason: You can use the Internet for purposes other than accessing information. a. The statement is true and the reason is valid. b. The statement is true but the reason is not valid. c. The statement is false but the reason is true. i) You click a hyperlink on a page. When the page starts appearing, you find that the content is not what you are looking for. What should you do to stop the process of page loading? j) Suppose a Web page does not load properly and some of the pictures on the page do not appear fully. To retrieve the page again, click____________ a. Home b. Refresh c. Favorites k) Suppose you have accidentally clicked a link and the page has started loading. The two buttons that you must click to go to back to the original page are ________ and_________ a. Stop and Forward b. Stop and Back c. Home and Forward l) You visit a Web site that contains a lot of information on your favourite topic. You want to store its address so that you can visit the Web page later. To do so, you have to click______ on the _______ menu. m) You want to visit a Web page that you visited yesterday, but you do not remember its URL and you did not add the Web page to your Favorites list. You can click __________to find the Web site address. a. History b. Favorites c. Back n) What is the use of search engines? o) State one difference between a search based on categories and a search based on keywords. p) Assume that you want to search for information on the topic “dowry system in India” and you do not know the Web addresses of the sites. Which of the following should you use? 296 1. URLs 2. E-mail 3. Search engines Hands on Activities Guided Practice 1 In this exercise, you will start Internet Explorer, open a Web site and move through links in the Web site. 1. Start Internet Explorer. 2. Open the Web site http://indianchild.com. 3. Click the link Flag of India and view it. 4. Go back to the home page. 5. Click the link Optical Illusions. 6. Follow the links in the page to view the various images on optical illusions. 7. Close Internet Explorer. Guided Practice 2 In this exercise, you will add Web pages to the Favorites list and set a page as home page. 1. Start Internet Explorer. 2. Open the Web site http://goidirectory.nic.in.Click the Banking, Financial & Insurance link. Click the Punjab National Bank (PNB) link. 3. Open the Web site http://indiaimage.nic.in/ .Click President of India link. 4. Click Rashtrapati Bhavan link. 5. Add the page to your list of favorite pages. 6. Move to the home page of the site. Make the home page of the site your default home page. 7. Revisit the Punjab National Bank (PNB) page by accessing it from your History list. Refresh its contents. 8. Close Internet Explorer. Guided Practice 3 In this exercise, you will use buttons available on the Internet Explorer toolbar to move from one Web page to another. You will save the required Web pages on your computer and download images to your computer. 1. Start Internet Explorer. 2. Go to the Web site http://www.indian-heritage.org. 3. Click the Architecture link. Save the Web page. 4. Refresh the page. As the page refreshes, click Stop. 5. Move to the previous page. 6. Click the Paintings link. 7. Download the images of your choice and save them on your computer. 8. Print the web page. 9. Close Internet Explorer Guided Practice 4: In this exercise, you will search for the information as described in the instructions given below. With your partner, discuss which Web pages are the most relevant and write down the Web page addresses so that you can visit them later. 1. Start Internet Explorer. 297 2. Use the MSN search engine to seek information on “E-Learning.” 3. Use the MSN search engine to find information on “the history of computer education in India.” 4. Close Internet Explorer. Guided Practice 5 In this activity, you will open Internet Explorer and search for information as described in the instructions given below. a. Start Internet Explorer. b. Search for sites that have the keywords “metropolitan cities”. Save the relevant web pages on the desktop. c. Search for sites that have the keywords “Constitution of India”. Add the relevant web pages to your Favorites list. d. Close Internet Explorer. Guided practice 6 1. Statement: A Web site can be identified by means of a Uniform Resource Locator. Reason: A URL holds the address of the Web site. a. The statement is true and the reason is valid. b. The statement is true but the reason is not valid. c. The statement is false but the reason is true. 2. Shashi wants to store the e-mail addresses of his friends in his computer. Which of the following features in Outlook should he use? 1. Tasks 2. Appointments 3. Contacts 3. Aman tries to connect his computer to the Internet, but he is unable to do it. He asks Bharat to help him out. Bharat finds that an important device used to connect to the Internet is missing. Which one of the following devices is it? a. Speaker b. Modem c. Scanner 4. Suppose you visit a Web site that contains information on the topic to be taught the next day. If you want to connect to the site each time you start Internet Explorer, you have to set this page as the ________ page. a. favorite b. home c. default 5. Manoj wants to use the Internet for the following purposes. Identify the Internet service he should use for each of the following: a. He wants to find information about the tigers of Ranthambore. b. He wants to send a file to his Delhi office branch manager as soon as possible. 6. Suppose you performed a category search on the word “technology”, but you were overwhelmed with the results. How would you refine your search? 298 Skill Check Points Self Practice 1 1. Start Internet Explorer. 2. Open the Web site http://www.indianembassy.org. Click the India Information link. On the India Information page, click the Incredible India link. 3. Move to the India Information page. 4. Visit the site http://www.valueeducation.nic.in to get information about the various activities related to value education. 5. Browse the http://www.indiatravelinfo.com/wildlife.htm Web site to get information about wildlife. 6. Close Internet Explorer. Self Practice 2 1. Start Internet Explorer. 2. Visit the site http://www.indian-heritage.org to get information about the various activities related to Indian Heritage. 3. Add the page to your Favorites list. 4. Browse the http://www.languageshome.com Web site to get information about Indian Languages. 5. Open a Web page from the list of recently visited Web pages. 6. Search for information on a topic of your choice by using Search. 7. Revisit http://www.indian-heritage.org by accessing it from your Favorites list. 8. Close Internet Explorer. Self Practice 3 a. Start Internet Explorer. b. Open the Web site www.indianwildlifeportal.com. Move to the Web page on Wildlife of India and save it. Move to the previously viewed Web page, and then move to the page titled Nature Travel in India. c. Go to the following Web sites and collect information on topics of your interest 1. http://www.travel-india.com 2. http://www.mapsofindia.com 3. http://www.festivalsofindia.in d. If any Web page takes a lot of time to download, stop downloading the Web page and proceed with browsing through other pages in the site. e. Save copies of the Web pages you visit on the computer. f. Open the Website http://www.msn.co.in. Make the page your home page. g. Save the home page on the desktop. h. Refresh the Web page. i. Make the home page of the Web site http://www.travel-india.com available offline. j. Close Internet Explorer. Self Practice 4 1. Start Internet Explorer. 2. Search for sites that have the keywords “care for animals in India” 3. Use a search engine to retrieve all pages that contain information about “Five star hotels in Mumbai.” 4. Use Category Search to find information on “Travel”. Use MSN Search Engine. 299 Annexure 1: Working with Microsoft*Publisher Spotlight 1. Overview MS Publisher 2. Types of Publication 3. Creating a Print Publication 4. Modifying a print Publication 5. Preparing Print Publication for Distribution 6. Preview and Print Publication 7. Change a Print Publication to e-mail 8. Create a webpage 300 301 Overview of MS Publisher Introduction to Microsoft Publisher Microsoft® Publisher is a full-featured desktop publishing and printing software program that helps you design and publish professional print and Web-based materials with ease. From greeting cards to brochures, newsletters to websites, Microsoft Publisher 2003 allows you the creativity to create any printed/ web document required Using Publisher’s familiar interface, you can precisely lay out blocks of text, graphics, calendars, order forms, and more, while Publisher’s many built-in designs help you to quickly create a professional publication in a matter of minutes. Open the Microsoft Office Publisher 2007 1. 2. 3. 4. 2007 Start All Programs Microsoft Office Microsoft Office Publisher Following screen will open 302 You can create: ---- Advertisements Award Certificates Banners Brochures Business Cards Business Forms (expense reports, fax cover letters, invoices, and more) Calendars Catalogs E-mail (e-mail template for an event, speaker, or newsletter) Envelopes Flyers Gift Certificates Greeting Cards (for many occasions) Invitation Cards (for various events) Labels (mailing, return address, CD/DVD, Binder, and more) Letterhead 303 Menus Newsletters Paper Folding Projects (airplanes & origami) Postcards Programs Quick Publications (signs, flyers, etc.) Resumes Signs (For Rent, For Sale, etc.) Web Sites With Compliments Cards And more… Create a New Microsoft Office Publisher 2007 1. 2. 3. 4. Getting Started Publication Types Blank Page Sizes Standard 304 Blank Page Size Open:-- Advertisement 305 Awards Certificates Banners 306