CS 465 Introduction to Computer Security
advertisement
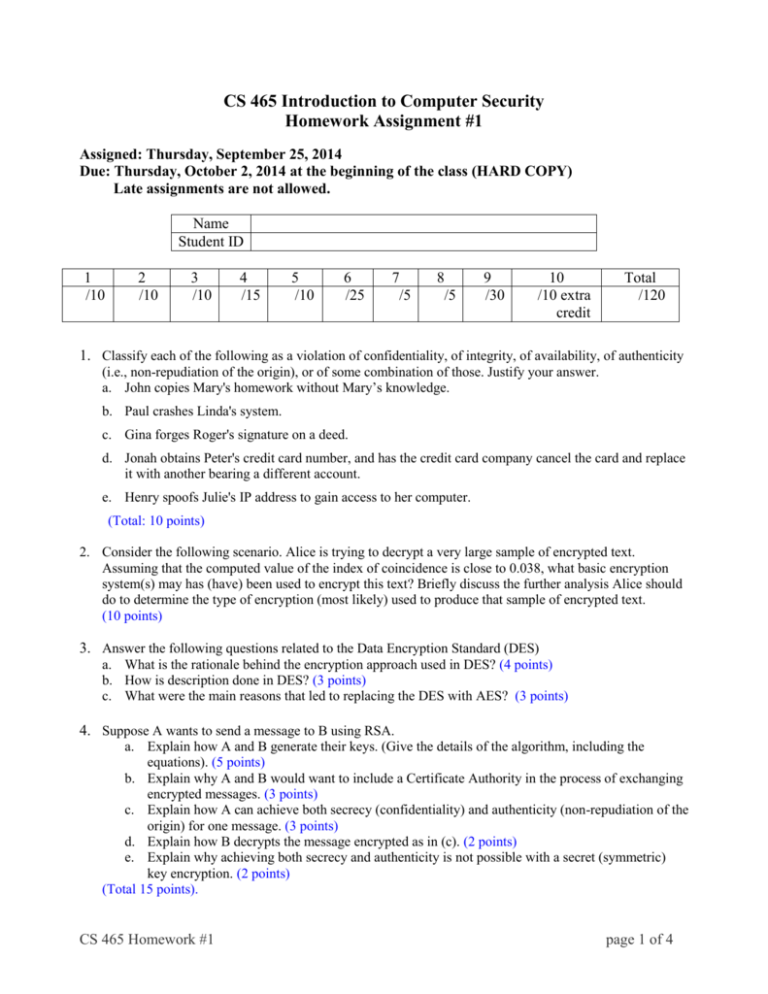
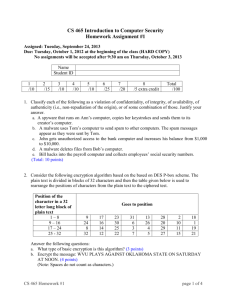
CS 465 Introduction to Computer Security Homework Assignment #1 Assigned: Thursday, September 25, 2014 Due: Thursday, October 2, 2014 at the beginning of the class (HARD COPY) Late assignments are not allowed. Name Student ID 1 /10 2 /10 3 /10 4 /15 5 /10 6 /25 7 /5 8 /5 9 /30 10 /10 extra credit Total /120 1. Classify each of the following as a violation of confidentiality, of integrity, of availability, of authenticity (i.e., non-repudiation of the origin), or of some combination of those. Justify your answer. a. John copies Mary's homework without Mary’s knowledge. b. Paul crashes Linda's system. c. Gina forges Roger's signature on a deed. d. Jonah obtains Peter's credit card number, and has the credit card company cancel the card and replace it with another bearing a different account. e. Henry spoofs Julie's IP address to gain access to her computer. (Total: 10 points) 2. Consider the following scenario. Alice is trying to decrypt a very large sample of encrypted text. Assuming that the computed value of the index of coincidence is close to 0.038, what basic encryption system(s) may has (have) been used to encrypt this text? Briefly discuss the further analysis Alice should do to determine the type of encryption (most likely) used to produce that sample of encrypted text. (10 points) 3. Answer the following questions related to the Data Encryption Standard (DES) a. What is the rationale behind the encryption approach used in DES? (4 points) b. How is description done in DES? (3 points) c. What were the main reasons that led to replacing the DES with AES? (3 points) 4. Suppose A wants to send a message to B using RSA. a. Explain how A and B generate their keys. (Give the details of the algorithm, including the equations). (5 points) b. Explain why A and B would want to include a Certificate Authority in the process of exchanging encrypted messages. (3 points) c. Explain how A can achieve both secrecy (confidentiality) and authenticity (non-repudiation of the origin) for one message. (3 points) d. Explain how B decrypts the message encrypted as in (c). (2 points) e. Explain why achieving both secrecy and authenticity is not possible with a secret (symmetric) key encryption. (2 points) (Total 15 points). CS 465 Homework #1 page 1 of 4 5. a. The first invented public key encryption algorithm, Diffie-Hellman, is still in use. What is this algorithm used for? Why is that problem important? (2 points) b. In what phase of SSL (Secure Sockets Layer) protocol Diffie-Hellman’s is one of the algorithms of choice? (2 points) c. Explain briefly how SSL protocol combines secret and public key encryption systems to provide secure e-commerce transactions over Internet. (3 points) d. What is the goal of using hash functions (i.e., message digests)? Explain when and how hash functions are used in SSL. (Hint: There are two different usages of hash functions in SSL.) (3 points) (Total: 10 points) 6. The exercises included in this problem demonstrate the use of OpenSSL which is a cryptography toolkit implementing the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) network protocols and related cryptography standards required by them. Specifically, you will use the openssl program which is a command line tool for using the various cryptography functions of OpenSSL’s crypto library from the shell. Information on OpenSSL can be found at http://www.openssl.org or by viewing the man pages of the appropriate commands on the LDCSEE shell server. SYNOPSIS: openssl command [ command_opts ] [ command_args ] The openssl program provides a rich variety of commands (command in the SYNOPSIS above), each of which often has a wealth of options and arguments (command_opts and command_args in the SYNOPSIS). openssl [ list-standard-commands | list-message-digest-commands | list-cipher-commands ] The pseudo-commands list-standard-commands, list-message-digest-commands, and listcipher-commands output a list (one entry per line) of the names of all standard commands, message digest commands, or cipher commands, respectively, that are available in the present openssl utility. PROBLEM: For each of the following steps (Step 1&2 for Secret key encryption and Steps 1-5 for Public key encryption) provide the complete openssl command line (with all necessary options and arguments). Run the command on LDCSEE shell server using the time command to display the information about resources used by that command. Use of secret key: Step 1: (3 points) Encrypt the input file input.txt using AES with 128 bit key. (The command for symmetric cipher routines is enc and the ciphername is aes-128-ecb.) Choose the appropriate command options and arguments to use salt and password to generate the key and write the encrypted text in an output file named outputEncAES128.txt. CS 465 Homework #1 page 2 of 4 Step 2: (3 points) Decrypt the encrypted text generated in Step 1 (given in the file outputEncAES128.txt). Remember to use the same password as in Step 1. Use of public key: Step 1: (3 points) Using the openssl command genrsa, generate an RSA private key long 2304 bits. (Note that 2304 bits key has the same resistance to a brute force attack as 128 bits long secret key.) Use the appropriate command options to save the key in a file named myPrivateKey.pem. Step 2: (3 points) Using the openssl command rsa, generate the RSA public key that corresponds to the private key generated in Step 1. Read the private key from the file myPrivateKey.pem and write the public key in another file myPublicKey.pem. Step 3: (3 points) Using the openssl command rsautl, encrypt the text given in the input.txt file with the public key generated in Step 2 (and saved in the file myPublicKey.pem). Write the encrypted text in the file outputEnc.txt. Step 4: (3 points) Decrypt the text encrypted in Step 3 (saved in the file outputEnc.txt) using the private key generated in Step 1 (saved in the file myPrivateKey.pem) and write the decrypted text in the output file outputDec.txt. Step 5: (3 points) Use the appropriate option(s) of the openssl command rsautl to sign the text given in the input.txt file using the appropriate key generated in the previous steps. ANALYSIS: Use the values measured by the time command to compare the time used for secret encryption (Step 1) and times used for public encryption (Steps 1, 2 & 3) and discuss what these values demonstrate. (4 points) NOTE: As a part of your homework, provide printouts of the files that contain the public/private keys for RSA and the encrypted/decrypted text for both AES and RSA. 7. Describe at least three ways computer viruses can spread. (5 points) 8. Explain why computer worms are bigger threat to computer security than computer viruses. (5 points) CS 465 Homework #1 page 3 of 4 9. Search the Web and/or professional journals for information on (1) Sapphire/Slammer worm and (2) Samy worm. For each of them briefly address the following points. a. The vulnerability (vulnerabilities) it has exploited b. The way it spread c. How fast it spread d. The effect it had on systems e. How hard/easy it was to clean the system from the worm. (30 points) 10. Extra credit: Please provide brief answers to the open-ended questions given below. I will carefully consider your feedback to improve this and future offerings of the class. Thank you for providing your individual perceptions on this class. (Total: 10 points) a. What do you like best about this class? b. What do you like least about this class? c. What is the one thing you would most like to see explained better? CS 465 Homework #1 page 4 of 4