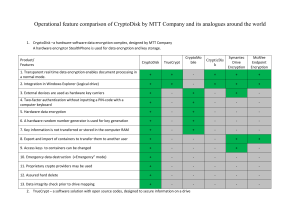
Encryption assignment
advertisement
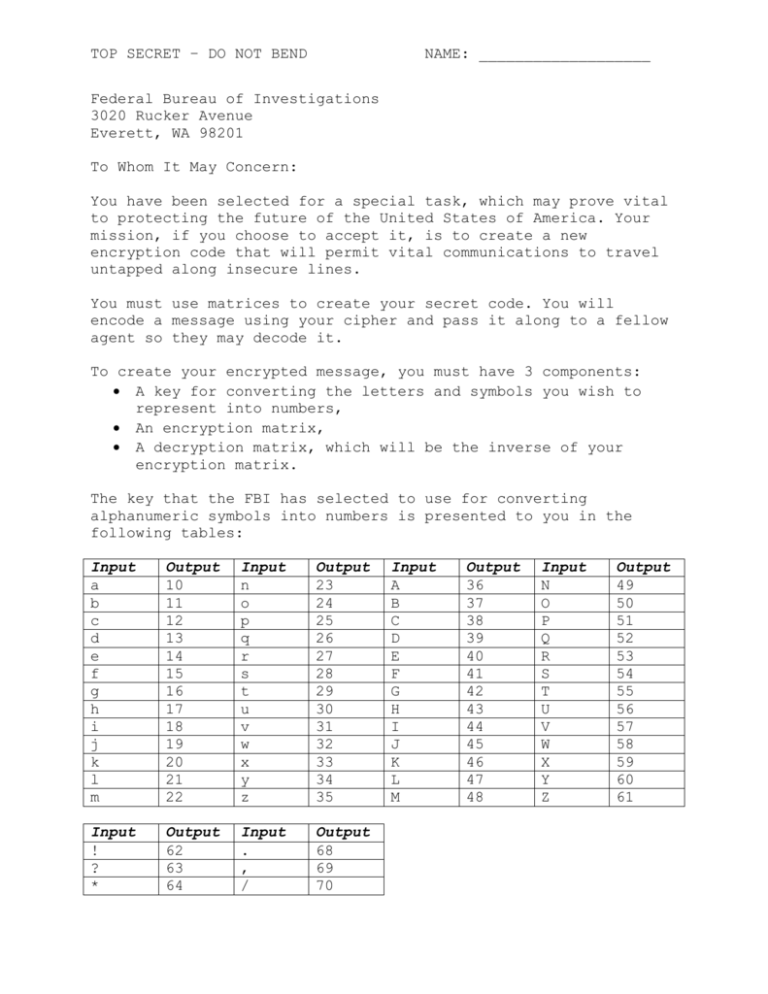
TOP SECRET – DO NOT BEND NAME: ___________________ Federal Bureau of Investigations 3020 Rucker Avenue Everett, WA 98201 To Whom It May Concern: You have been selected for a special task, which may prove vital to protecting the future of the United States of America. Your mission, if you choose to accept it, is to create a new encryption code that will permit vital communications to travel untapped along insecure lines. You must use matrices to create your secret code. You will encode a message using your cipher and pass it along to a fellow agent so they may decode it. To create your encrypted message, you must have 3 components: A key for converting the letters and symbols you wish to represent into numbers, An encryption matrix, A decryption matrix, which will be the inverse of your encryption matrix. The key that the FBI has selected to use for converting alphanumeric symbols into numbers is presented to you in the following tables: Input a b c d e f g h i j k l m Output 10 11 12 13 14 15 16 17 18 19 20 21 22 Input n o p q r s t u v w x y z Output 23 24 25 26 27 28 29 30 31 32 33 34 35 Input ! ? * Output 62 63 64 Input . , / Output 68 69 70 Input A B C D E F G H I J K L M Output 36 37 38 39 40 41 42 43 44 45 46 47 48 Input N O P Q R S T U V W X Y Z Output 49 50 51 52 53 54 55 56 57 58 59 60 61 $ # @ 65 66 67 ( ) Space 71 72 73 The numbers 0-9 are represented by 0-9 (no change). For example: “Sally went to the store.” would convert to: 54 10 21 21 34 73 32 14 23 29 73 29 24 73 29 17 14 73 28 29 24 27 14 68 Now that we have a message represented as numbers, we must fit it into a matrix. The example message is 24 characters long and can therefore fit easily into a matrix, but for messages with prime numbers of characters, you may pad the end with whitespace. Try to keep the number of rows low, as these will be multiplied by our encryption matrix later on. Our example, formatted as a 6x4 matrix, is below: 54 34 23 𝑀= 24 14 [24 10 73 29 73 73 27 21 32 73 29 28 14 21 14 29 17 29 68] It is now time to create an encryption matrix. You will multiply your message matrix by the encryption matrix to cipher the message it contains. Then the recipient will multiply it by the inverse of the encryption matrix – the decryption matrix – to turn it back into the original, clear text message. Therefore, it is vital that your encryption matrix be invertible. If not, there will be no way to decrypt your message! Equally important is that your encryption matrix must remain secret; otherwise the security of your code will be compromised. The encryption matrix can contain whatever numbers you want, as long as it is invertible. It must be a square, and contain the same number of rows as the message matrix has columns. For example: 7 1 5 4 3 9 𝐸=[ −1 −9 2 0 1 8 8 4 ] 6 4 Then multiply your message matrix by your encryption matrix to get your encrypted message: 397 498 204 𝑀𝐸 = 431 362 [262 −84 −21 −518 −1 10 47 570 1003 754 971 1015 935 682 812 854 726 688 656] Once your partner has your encryption key, they can decode the original message by multiplying it by the inverse of the key: 𝑀 = 𝑀𝐸𝐸 −1 This will give them back the original message (with text still represented by numbers). Then simply use the provided table to convert the numbers back to the original text. Now you must create an encoded message using your own encryption matrix. Follow the steps below to do so. 1. Write your original message text. 2. Write the series of numbers which represent it, using the table provided. 3. In the space below, determine a matrix which your message will fit into. Remember, the more rows you have, the larger your encryption matrix will have to be. 4. Write a square encryption matrix with the same number of columns as your message matrix has rows. Ideally, use a cryptographically secure pseudorandom number generator to determine the numbers within it. Remember, this matrix must be invertible or your message will not be decodable! 5. Multiply your message matrix by the encryption matrix and write down the result below. 6. Cut this paper on the dotted line, and pass it to your neighbor so they can test your encryption.