1 introduction
advertisement

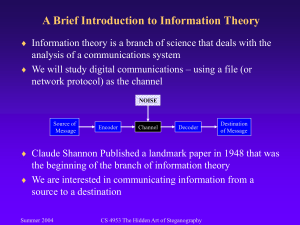
1 INTRODUCTION Steganography is derived from Greek words: steganos meaning covered/secret and graphy meaning writing. So, it is defined as the art and science of hiding information by embedding messages within seemingly harmless messages. It also refers to the “Invisible” communication. The power of Steganography is in hiding the secret message by obscurity, hiding its existence in a non-secret file. Steganography works by replacing bits of useless or unused data in regular computer files. It leaves behind detectable traces in the stego objects and modifies the statistical properties. This hidden information can be plaintext or ciphertext and even images. In an image Steganography, it uses some reliable Steganography algorithms or secret keys to transform or encrypt secret images into ciphered images. Only the authorized users can decrypt secret images from the ciphered images. The ciphered images are meaningless and non-recognizable for any unauthorized users who grab them without knowing the decryption algorithms. In our project, we aim to develop an application for police department or secret service like organizations where the communication needs to be confidential in order to prevent information leaks about their ongoing investigation on cases, task assignment, working strategy etc. It provides a user friendly environment for the secret service personnel to type their message, encrypt the written text and save the encrypted text in a .txt file which can then be used to hide inside an image file using steganographic technique. On the other hand the receiver can use the application to retrieve the .txt file hidden inside the image and hence decrypt the actual message from the retrieved file containing encrypted message. It allows the use of webcam for taking snapshots of the criminals. For encryption of the original message, AES (Advanced Encryption Standard) is used and for hiding the txt file inside the image SDSA (Spatially Desynchronized Steganography Algorithm) is chosen. 1 2 OBJECTIVES The chief objectives of the project are: i) To encrypt the message to be transmitted ii) To use image steganography in police department iii) To keep confidential details hidden during information exchange iv) To securely communicate important messages v) To practically implement image processing knowledge 2 3 FEATURES The major features of the project are listed below: i) Encryption and Decryption of text files ii) Web-cam function for image capture iii) Hide encrypted confidential details within the image iv) Use of Spatially Desynchronized Steganography Algorithm(SDSA) and Advanced Encryption Standard(AES) v) Secure information exchange for police and security service like sector 3 4 LITERATUREREVIEW Invisible ink, a form of steganography, has been used for centuries. George Washington used it to spy against the British during the American Revolution and it was extensively used during World War II. It continues to be used today not only by spies but for commercial purposes, e.g. marking dice, chips and gaming equipment to protect against counterfeiting. The organizations that work in crime and security sectors such as police, army, secret services, FBI, CIA etc. have been following various techniques to communicate like emails, telephone which are more prone to attacks by the eavesdroppers and call tappers. Sometimes, the message to be transferred is even encrypted so that even if the outsiders succeed to receive the message they become unable to read the original content. Still, the fact is not hidden that the ciphertext contains some confidential information. Now, they have been driving their attention towards steganography whereby they can easily hide secret informations inside other cover objects which can be anything in today’s digital world such as image, audio, video etc. Keeping this in mind, we have been doing this project in order to hide confidential messages forwarded from one place to another encrypted and hidden inside image file so that no information leaks occurs. Despite the fact that cryptography and steganography are basically not the same, we apply the combination of both these techniques in order to achieve better results for security. Basically, the model for steganography for encrypted file can be represented as: Original text Cover-object, C F(X,M,K) Message,file M Encrypted Stego Object, Z Stego-key, K Fig 4.1: Steganography combined with encryption Original text is the data that the sender wishes to remain it confidential. It can be encrypted using any encryption techniques, particularly we follow Advanced 4 Encryption Stantard (AES) to convert to ciphertext that can be embedded in a bit stream. Password is known as stego-key, which ensures that only recipient who know the corresponding decoding key will be able to extract the message from a cover-object which is an image file in case of image steganography. The coverobject with the secretly embedded message is then called the Stego-object. Image Steganography has been done using various algorithms such as least significant bit (LSB) modification, masking and filtering etc. But our project will follow Spatially Desynchronized Steganography Algorithm (SDSA) and so far it has not been used in police department to hide any police details. 5 5 SYSTEM REQUIREMENTS 5.1 Hardware Requirements Personal Computer Webcam 5.2 Software Requirements C#, .NET Framework Database: MsSQL 2008 Microsoft Visual Studio Microsoft SQL Server 6 6 METHODOLOGY Our application is basically a desktop application that is specially designed for police department where the department head has the full authority to all the services since he is the administrator of the application. After login verification for admin, he can write some information, encrypt the secret information thus forming ciphertext and then hiding the ciphertext containing file in the image of any kind. Other officers working in the same police station if get forwarded the stego-image, only that particular message can be decrypted by the same officer and if the image has been forwarded to any other station head, he can not only unhide and decrypt the file but also reply for the message in the same way hiding encrypted file in image. The staff in the station can use the webcam to capture criminals photograph for criminal records and also keep police officers’ records in database so that the information can be retrieved easily whenever required. The staff responsible for such data entries can have access only to database stuffs like adding, editing, deleting records and nothing others such as encryption and hiding inside image. 6.1 Algorithms 6.1.1 Spatially Desynchronized Steganography Algorithm (SDSA) Domain separation (or randomization) is a technique which is used for hiding the embedding domain from the attacker. It is observed that existing domain randomization techniques cannot provide enough randomization such that they are easily be detected by recent steganalysis techniques. SDSA algorithm is less detectable against the calibration based blind as well as targeted steganalytic attacks than the existing JPEG domain steganographic schemes. The SDSA uses blocks of 8x8(m x n) to embed the document in the carrier image in specific stego chunks which are returned back to the image. SDSA is based on spatial block desynchronization to disturb the successful prediction of cover image statistics from the stego image. 7 Fig 6.1.1.1: Spatial block desynchronization 6.1.2 Advanced Encryption Standard (AES) AES is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001. It is based on the Rijndael cipher developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen. AES is a symmetric block cipher that is intended to replace DES as the approved standard for a wide range of applications. For AES, NIST selected three members of the Rijndael family, each with a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits. The key size used for an AES cipher specifies the number of repetitions of transformation rounds that convert the input, called the plaintext, into the final output, called the ciphertext. The number of cycles of repetition are as follows: 10 cycles of repetition for 128-bit keys. 12 cycles of repetition for 192-bit keys. 14 cycles of repetition for 256-bit keys. Four different stages are used, one of permutation and three of substitution: Substitute bytes: Uses an S-box to perform a byte-by-byte substitution of the block 8 ShiftRows: A simple permutation MixColumns: A substitution that makes use of arithmetic over GF(28) AddRoundKey: A simple bitwise XOR of the current block with a portion of the expanded key Fig 6.1.2.1: AES algorithm 9 6.2 Software Development Life Cycle (Rapid Application Development- RAD) Rapid application development (RAD) is a software development methodology that uses minimal planning in favor of rapid prototyping. The "planning" of software developed using RAD is interleaved with writing the software itself. RAD involves iterative development and the construction of prototypes. The four phases of RAD are: Requirements Planning phase – It combines elements of the system planning and systems analysis phases of the Systems Development Life Cycle (SDLC). It ends when the team agrees on the key issues and obtains management authorization to continue. User design phase – During this phase, users interact with systems analysts and develop models and prototypes that represent all system processes, inputs, and outputs. User Design allows users to understand, modify, and eventually approve a working model of the system that meets their needs. Construction phase –In RAD, users continue to participate and can still suggest changes or improvements as actual screens or reports are developed. Its tasks are programming and application development, coding, unitintegration and system testing. Cutover phase – It resembles the final tasks in the SDLC implementation phase, including data conversion, testing, changeover to the new system and user training. Fig 6.2.1: RAD model 10 7 USECASE DIAGRAM Fig 7.1: Usecase Diagram 11 8 DEVELOPMENT STATUS 8 .1 Work Accomplished At this moment we have completed the basic layout of our project. We have created entry form for storing the officer and criminal records. Database design for keeping the records of login details, officer and criminal information, file sent details etc. has been accomplished. More importantly, encryption of typed text, writing ciphertext to txt files and decryption of the file contents have been completed. Since our major task is to encrypt information and then hide the file in cover image, it adds 35-40% of the work accomplished. 8.2 Work Remaining About 60% of work is still remaining. The main objective of our project is to use steganography in order to hide the information i.e to make the secure communication amongst the department members. We now are working and researching in this topic. The core part of the project is hence left untouched. Also we tend to develop a working and complete application for police department which is still in ongoing development phase. 8.3 Problems Encountered The main problem encountered is to decide an application area where we can use image steganography. As the project is being done in C# and .NET programming language which is new for us, we have to study it well. So, different problems were encountered during the project development. Making the concept vivid and deciding how to develop the system was the most time consuming part. Also it was time consuming to decide which algorithm to use for cryptography and steganography. Since these topics are quite new for us, we find it difficult how the chosen algorithm actually works. 12 9 PROJECT SCHEDULE Fig9.1: Gantt Chart 13 10 CONCLUSION Steganography means hiding message inside a cover message. Steganography and cryptography are closely related but their goals are different. In cryptography, the data is encypted and unreadable but the existence of data is not hidden whereas steganography leaves no evidence of the existence of data. Steganography and cryptography can be used together to produce better protection. In a digital world, both Steganography and cryptography are intended to protect information from unwanted parties. Basically, digital images are well-known to be used as a cover object to hide a secret message. The proposed project is the application of image steganography in police department to hide confidential police details inside image file. Various techniques are widely used for this purpose but we are attempting to use Spatially Desynchronized Steganography Algorithm (SDSA). It causes slight loss in cover message but is not detectable to human eye. What is important is the preservation of the hidden message. The stego-image is decrypted using stego-key generated by the same algorithm to separate and securely extract the embedded files. Also AES algorithm encrypts and decrypts the contents of text files using same key since the algorithm is symmetric. Steganography can be used to hide important data inside another file so that only the authorized person intended to get the message even knows a secret message exists .It is better technique for information hiding in the digital images with the encrypted form. To conclude, our application would be user friendly and wellfunctioning to produce ciphertext from the actual information and hide besides a cover image and it would definitely be practically applicable in several sectors where secret message transfer is required. Also this technique can be applicable to deliver required confidential matter even through social networking sites where people will not even think that the image could hold something else. 14 REFERENCE J. J. Eggers, R. Bauml, and B. Girod, “A communications approach to image steganography”, in Proc. SPIE Security and Watermarking of Multimedia Contents IV. J. Fridrich, M. Goljan, and D. Hogea,“Steganalysis of JPEG Images: Breaking the F5 Algorithm”, in Proc. 5th International Workshop on Information Hiding, Noordwijkerhout, The Netherlands. J. Fridrich, T. Pevny, and J. Kodovsky, “Statistically Undetectable JPEG Steganography: Dead Ends, Challenges, and Opportunities”, in Proc. ACM Multimedia and Security Workshop, Dallas, TX. Ã, A. C., Condell, J., Curran, K., & Kevitt, P. M. (2010). Digital image steganography : Survey and analysis of current methods. Signal Processing, 90(3), 727–752. doi:10.1016/j.sigpro. Westlund, Harold B. (2002). "NIST reports measurable success of Advanced Encryption Standard". Journal of Research of the National Institute of Standards and Technology. Westlund, Harold B. (2002). "NIST reports measurable success of Advanced Encryption Standard". Journal of Research of the National Institute of Standards and Technology. 15