UTHealth Research Questionnaire - University of Texas
advertisement
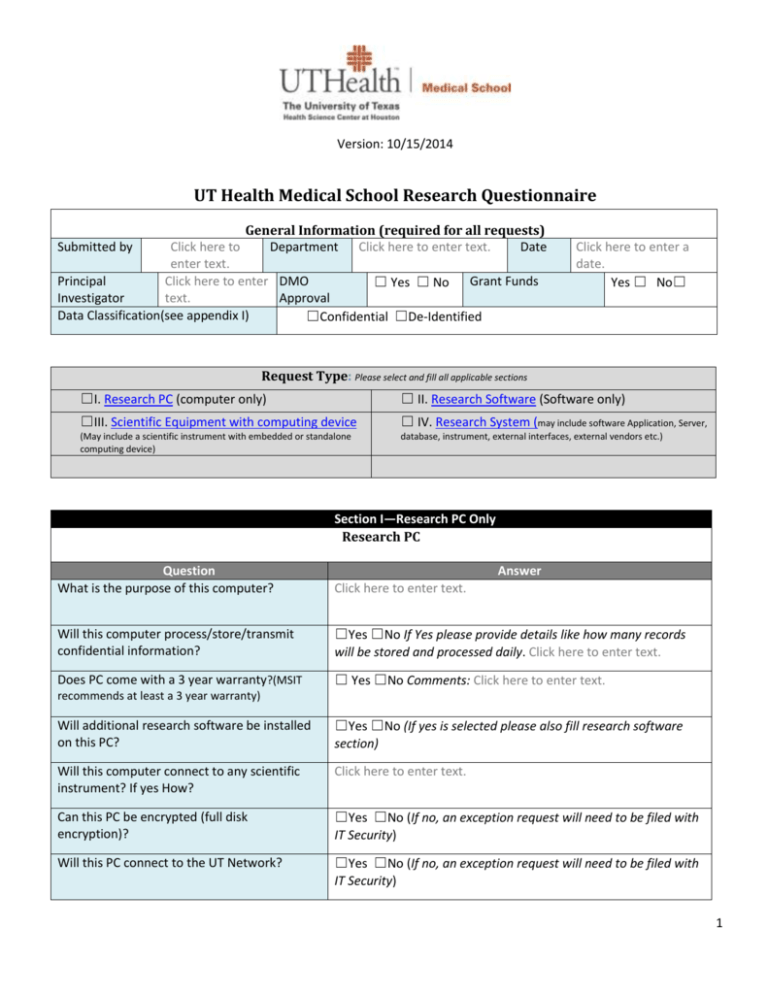
Version: 10/15/2014 UT Health Medical School Research Questionnaire General Information (required for all requests) Submitted by Click here to Department Click here to enter text. Date enter text. Principal Click here to enter DMO ☐ Yes ☐ No Grant Funds Investigator text. Approval Data Classification(see appendix I) ☐Confidential ☐De-Identified Click here to enter a date. Yes ☐ No☐ Request Type: Please select and fill all applicable sections ☐I. Research PC (computer only) ☐ II. Research Software (Software only) ☐III. Scientific Equipment with computing device ☐ IV. Research System (may include software Application, Server, (May include a scientific instrument with embedded or standalone computing device) database, instrument, external interfaces, external vendors etc.) Section I—Research PC Only Research PC Question What is the purpose of this computer? Answer Click here to enter text. Will this computer process/store/transmit confidential information? ☐Yes ☐No If Yes please provide details like how many records will be stored and processed daily. Click here to enter text. Does PC come with a 3 year warranty?(MSIT ☐ Yes ☐No Comments: Click here to enter text. recommends at least a 3 year warranty) Will additional research software be installed on this PC? ☐Yes ☐No (If yes is selected please also fill research software section) Will this computer connect to any scientific instrument? If yes How? Click here to enter text. Can this PC be encrypted (full disk encryption)? ☐Yes ☐No (If no, an exception request will need to be filed with IT Security) Will this PC connect to the UT Network? ☐Yes ☐No (If no, an exception request will need to be filed with IT Security) 1 Operating System Click here to enter text. Can this PC connect to Active Directory? ☐Yes ☐No (If no is selected describe how will this computer be managed i.e. patches etc.)?Click here to enter text. Can regular security updates be applied? ☐Yes ☐No If no, a research exemption needs to be filed with details on patching intervals Can Forefront antivirus be installed on the machine? ☐Yes ☐No (If no, an exception request will need to be filed with IT Security) Who in the department will be responsible for this PC? Click here to enter text. What is the typical data file size output? Click here to enter text. Where will this data be saved and backed up? Click here to enter text. Any interfaces to other systems (i.e. Allscripts, external to UT)? Click here to enter text. Any environmental concerns (i.e. extra cooling need, located in a restricted area? Click here to enter text. Any other comments? Click here to enter text. 2 Section II—Research Software Software Name Research Software For New Software Requests(see below for license renewals) Click here to enter text. Vendor Name Click here to enter text. Does the vendor provide support for the software? If yes please provide details Click here to enter text. Vendor Contact Click here to enter text. Business need for this software? Click here to enter text. Software functionality? (How does this software work?) Click here to enter text. How many licenses are needed? Click here to enter text. Is there an annual license renewal? ☐ Yes ☐ No What are the hardware requirements? Click here to enter text. On what hardware will the software be installed? Click here to enter text. Is the hardware running this software encrypted? ☐Yes ☐No Does the software create process or store confidential data? ☐Yes ☐No If confidential data is involved, how many confidential records are processed/stored daily? Click here to enter text. What is the format and size of data created by this software? Click here to enter text. 3 Where will data generated by this software be saved and backed up?(MSIT recommends NAS) Click here to enter text. Who in the department will manage this software Click here to enter text. (i.e. upgrades)? How will access be granted to the software? Click here to enter text. How many users will have a userid to access this software? Does the software support LDAP/AD integration for access control? ☐Yes ☐ No If no please provide details on where user accounts will be created Click here to enter text. Who will have admin rights to this software? Click here to enter text. Does this software track changes made by users? Click here to enter text. Will this software be used to provide high availability patient care? ☐ Yes ☐ No Does this software communicate to the internet? ☐Yes ☐ No If yes please provide details Click here to enter text. Brief description of the software For License Renewals only Click here to enter text. Where is this software installed? Click here to enter text. Does the software create process or store confidential data? ☐Yes ☐ No Who is responsible for managing this software (i.e. upgrades)? Click here to enter text. Any changes to vendor contact Information? 4 Section III—Scientific Equipment with Embedded and or standalone PC Scientific Equipment with Embedded and or standalone PC Business need for this equipment? Click here to enter text. Will the equipment process and or store confidential information? ☐ Yes ☐No Is the PC embedded in the instrument? ☐ Yes ☐No If PC is not embedded, how is it connected to the instrument? Click here to enter text. Does the vendor provide support for the PC? Click here to enter text. Can the pc be encrypted? ☐ Yes ☐No Security Do the instrument and or PC need to connect to the network? Click here to enter text. Are there any external interfaces?(i.e. remote support) Click here to enter text. What operating system is installed on the PC? Click here to enter text. Can the PC component connect to Active Directory? ☐Yes ☐No If no is selected describe how will this computer be managed i.e. patches etc.Click here to enter text. Can regular Security updates be applied? ☐ Yes ☐No If no, a research exemption needs to be filed with details on patching intervals Can Forefront antivirus be installed on the machine? ☐Yes ☐No If no, an exception request will need to be filed with IT Security What is the typical data file size output from the instrument? Click here to enter text. Where will this data be saved? Click here to enter text. Any special needs (i.e. extra cooling, power etc.) Click here to enter text. If no, an exemption needs to be filed with IT 5 Section IV—Research System Research System (may include software Application, Server, database, instrument, external interfaces, external and vendors etc.) What is the business need for this system? General Info Click here to enter text. How does this system work? (Functionality). Click here to enter text. Does this system provide patient care? ☐Yes ☐ No Does the system process, store and transmit confidential data? ☐Yes ☐ No Please provide a list of hardware that comprises this system? Click here to enter text. Hardware location ☐ UT Data Center ☐Cloud ☐ Other Please provide details Click here to enter text. Please provide a list of software that comprises this system (including databases)? Click here to enter text. Is there a need to create a test/dev environment(recommended for high availability systems) Does the system involve desktop software component? ☐Yes ☐ No If yes increased hardware costs Does the system involve use of mobile devices (i.e. iPad, USB drive, External Storage)? Click here to enter text. Is there a need for an SLA (Service Level Agreement) with the vendor? ☐Yes ☐ No Is there a need for a BAA (Business Associate Agreement)? ☐Yes ☐ No BAA is needed if vendor will have access to UT confidential data Who is the system/data owner (usually a PI)? ☐Yes ☐ No If yes please provide detailsClick here to enter text. Roles and Responsibilities Click here to enter text. Who will be the application custodian (responsible for maintaining/supporting the application)? Who will be the Server custodian (responsible for maintaining/supporting server hardware) Click here to enter text. Will the vendor provide support? ☐Yes ☐ No ☐NA If yes, how long will the vendor provide support Click here to enter text. Click here to enter text. 6 Who will have admin rights to the system? Click here to enter text. Is a guest account needed for the vendor? ☐Yes ☐ No Risk Classification Data Flow ☐ High ☐ Medium ☐Low Please see Appendix II How is data collected and entered into the system? Click here to enter text. What type of data is it? Click here to enter text. How is this data backed up? Click here to enter text. What is the data retention period? Click here to enter text. What type and size of data will be created by the system? Click here to enter text. Are there any special network bandwidth considerations? Click here to enter text. How is this system accessed by end users? (i.e. via client, website etc.)? Are these users internal, external or both? Access Control Click here to enter text. Click here to enter text. How many users will have userids access to this Click here to enter text. system? How many desktop computers will have access Click here to enter text. to this system? Where are these desktop computers located? Click here to enter text. Will the system utilize SAML/LDAP for access control?(MSIT does not recommend local user accounts) How will userids be managed? Skip if UT accounts are being used? ☐Yes ☐ No Comments: Click here to enter text. Click here to enter text. What is the process a new user would follow to Click here to enter text. request a user ID for the application/system? Is communication during the authentication process encrypted? Click here to enter text. 7 Who will review system access list on a regular Click here to enter text. basis? How will access be terminated? Click here to enter text. Is there a need to provide different levels of access (i.e. elevated for doctors, restricted for administrative staff)? Click here to enter text. Login Management Is there an application lockout feature available Click here to enter text. after X number of failed attempts? Does the application logout after X minutes of Click here to enter text. inactivity? Audit/Logs Does the application/system have an audit trail Click here to enter text. feature? Does the application/system record all changes Click here to enter text. made by users? How long are the audits kept? Does the application/system require a specific database solution (Oracle, DB2, SQL, etc.)?Please include database version Does the application/system need a dedicated database server? Click here to enter text. Database Click here to enter text. ☐Yes ☐No What will be the initial database size in MB? Click here to enter text. What will be the anticipated yearly growth in MB? Click here to enter text. If SQL is used can the database reside on the UT SQL cluster? ☐ Yes: ☐SQL 2008 Cluster ☐SQL 2012 Cluster ☐ No What type of environment is this database intended for? ☐Development ☐Testing ☐Production ☐ Vendor ☐ In-house (database provided) ☐ In-house n(blank database) ☐Other. Please explainClick here to enter text. Click here to enter text. How is the database being developed? Describe in detail the front end interface making a connection to this database? 8 What are the requirements for the interface connectivity with the database (i.e. firewall ports? Click here to enter text. Interfaces Click here to enter text. Will the system be interfacing with other UT applications? Will the system be interfacing with external entities on the internet? Click here to enter text. Will data be transferred to other systems? Please provide details. Click here to enter text. Business Continuity Disaster Recover Please specify how long your users/managers could be without the system if there was an unplanned downtime or a system outage.(Recovery Time Objective) Please specify what amount of data loss would be either acceptable or re-creatable (manual entry, etc.) if your application were to encounter an unplanned downtime or service interruption during the backup intervals.(Recovery Point Objective) Is there a need for specific backup solution? UT backups are kept for 14 days. Click here to enter text. Click here to enter text. Click here to enter text. Application Development (please answer the following questions if application/Web development is involved) How will the application be developed? Where will the application be hosted? Who in the department will manage this application? ☐ In House: ☐ Custom developed by the vendor ☐Off the Shelf ☐Off the shelf with customization ☐ Internally ☐ Externally Click here to enter text. Storage Needs Are there any storage needs? Click here to enter text. Location of storage ☐ Internal ☐ External Please provide details Click here to enter text. Size in GB Click here to enter text. Any special needs(i.e. high speed, data replication, archiving) Click here to enter text. 9 Is confidential data involved? Click here to enter text. Is there a need to replicate data? Click here to enter text. Is there a need to archive data? Mobile Devices(iPad, usb drive)(please provide this information if Mobile Devices are involved) How will mobile devices be secured?(i.e. Click here to enter text. Airwatch, Lok IT) Will mobile device process store confidential data? Click here to enter text. If yes how long will confidential data reside on the mobile devices? Click here to enter text. How many records of patient data will be stored at any given day and time? Click here to enter text. Will the device have an automated mechanism to regularly purge patient data? Click here to enter text. Will the department maintain a check-in-check out sheet? Click here to enter text. 10 Appendixes Appendix I—Data Classification Term Definition Confidential Information (Data) Confidential data is defined under UTS 165 as data that is exempt from disclosure under the provisions of the Public Records Act or other applicable state and federal laws. i.e. De-identified Information Human subject research information, Patient health records, Social Security Numbers, Protected student records, Payroll records, Any data that is protected by federal and state law. Some academic data De-identified is generally defined under the HIPAA Privacy Rule as information (1) that does not identify the individual and (2) for which there is no reasonable basis to believe the individual can be identified from it. Note: De-Identified data cannot include categories shown in Appendix III Internal / Official Use Information Type Any information not identified as confidential that is considered internal or proprietary to the institution that if disclosed has the potential to cause harm to business operations or its reputation. Non-Public Information Any information that is classified as Confidential or Sensitive Information according to the data classification scheme defined in this policy. 11 Appendix –II Risk Classification Risk Category (H / M / L) Impact of Data Loss Examples of UT Health Information Types Security Measures Category : High Confidential Information Human subject research information, Major data breach and privacy Based on an annual risk assessment liabilities, Patient health records, Social Security Numbers, Protected student records, Loss of public confidence and trust, Major project delay or cancellation, Payroll records, Any data that is protected by federal and state law. Some academic data Logging and monitoring Access Control and Monitoring Incident HandlingBreaches/Unauthorized Access/Use or Abuse Negative publicity and/or damaged institutional reputation, Backups/DR Plans/Contingency Injury to faculty, staff, and third Plans party affiliates, Loss of revenue, grants, gifts, and donations, Category : Moderate Research data/detail that is not classified as Public or Internal/ Official Use Confidential, Financial transactions exclusive of Confidential data, Law Enforcement Investigation Data, HR Employment Data, Strong password requirements Damaged/destroyed data, or loss of information resources and critical operations. Minimum loss of public confidence and trust, Limited project delay or cancellation, Change Management Data Encryption when applicable Access privileges for authorized users only Electronic media and hard copies are to be sanitized or shredded according to university procedures Physical Security Controls (see 6.2.2) Strong passwords Backups Limited access to internal data Restricted from any publicly Minor negative publicity and/or accessible websites. damaged institutional reputation, Protect within controlled area for data at rest or encryption Minimum loss of revenue, grants, gifts, and donations, IT Infrastructure Data (i.e. server Minimum damage or loss of names, internal IP addresses), information resources and ID Badge with magnetic strip. operations. Electronic media and hard copies are to be sanitized or shredded according to university procedures Access privileges for authorized 12 Category : Low Some academic data users only University information available No loss of public confidence to the general public (e.g. and trust, Unrestricted UT Health web Minimum to no negative pages.) publicity and/or damaged News or press releases, institutional reputation, Backups when required by data or information owner. NonConfidential/Public University calendar, student course schedules, Campus map, university directory No damage or loss of information resources and information. operations. Some academic data Write access privileges for authorized users only No loss of revenue, grants, gifts, and donations, 13 Appendix III—De-Identified Data Validation De-Identified data can not contain any of the following HIPAA identifiers: ☐ Addresses - All geographical subdivisions smaller than a State (e.g., street address, city, county, precinct, zip code) ☐ All elements of dates (except year) for dates directly related to an individual, including birth date, admission date, discharge date, date of death; all ages over 89 and all elements of dates (including year) indicative of such age, except that such ages and elements of dates may be aggregated into a single category of age 90 or older ☐ Phone numbers (e.g., phone, fax, and cell) ☐ Electronic mail addresses ☐ Social Security Numbers(or other number originated by a government that specifically identities an individual) ☐ Medical records numbers ☐ Medical notes ☐ Health plan beneficiary numbers ☐ Account numbers -Financial account information and/or numbers (e.g., checking account number and Personal Identification Numbers (PIN) ☐ Certificate/license numbers ☐ Vehicle identifiers and serial numbers, including license plate numbers ☐ Device identifiers and serial numbers (e.g., pacemaker, hearing aid, or other) ☐ Web Uniform Resource Locators (URL) ☐ Internet Protocol (IP) address numbers ☐ Biometric identifiers including finger and voice prints ☐ Photographic identifiers (e.g., full face photographic images, x-rays, and video) ☐ Any other unique identifying number, characteristic, or code (e.g., Mother’s maiden name) Protected student records: ☐ Education records (FERPA) Human Resources and Payroll records: ☐ Employment status and/or records ☐ Certificates (e.g., birth, death, and marriage) ☐ Military status and/or records 14 Legal Documents: ☐ Legal documents or notes (e.g., divorce decree, criminal records, or other) 15







