references
advertisement

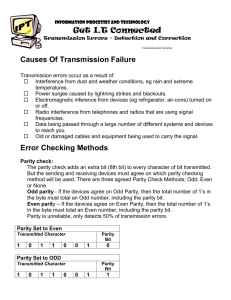
Error Detection Technique in Network Security with respect to Decoy Computer System Prof. Tarannum S. Shaikh Assistant Professor of Master of Computer Application Department,A.C.Patil College of Engineering,Kharghar-410210,Navi Mumbai,Maharashtra tarannumshaikh527@gmail.com Mst. Jay Mahapadi Student of Master of Computer Application Department,A.C.Patil College of Engineering, Kharghar-410210,Navi Mumbai,Maharashtra jay.mahapadi@gmail.com Abstract—Error control describes how the network handles and detects. In this paper, I present on an overview of error control regarding error detection and error correction with respect to decoy system. Error control happens in data link layer. I mainly discuss the type of error detection mechanisms that is used to detect the errors and how the errors will be corrected so the receiver can extract the real data.Decoy Systems, also known as deception systems, honey-pots or tar-pits, are phony components setup to entice unauthorized users by presenting numerous system vulnerabilities, while attempting to restrict unauthorized access to network information systems. At the end of this paper, the conclusion is presented. I. INTRODUCTION Environmental interference and physical defects in the communication medium can cause random bit errors during data transmission. Error coding is a method of detecting and correcting these errors to ensure information is transferred intact from its source to its destination. Error coding is used for fault tolerant computing in computer memory, magnetic and optical data storage media, satellite and deep space communications, network communications, cellular telephone networks, and almost any other form of digital data communication. Error coding uses mathematical formulas to encode data bits at the source into longer bit words for transmission. The "code word" can then be decoded at the destination to retrieve the information. The extra bits in the code word provide redundancy that, according to the coding scheme used, will allow the destination to use the decoding process to determine if the communication medium introduced errors and in some cases correct them so that the data need not be retransmitted. Different error coding schemes are chosen depending on the types of errors expected, the communication medium's expected error rate, and whether or not data retransmission is possible. Faster processors and better communications technology make more complex coding schemes, with better error detecting and correcting capabilities, possible for smaller embedded systems, allowing for more robust communications. However, tradeoffs between bandwidth and coding overhead, coding complexity and allowable coding delay between transmissions, must be considered for each application. Even if we know what type of errors can occur, we can’t simple recognize them. We can do this simply by comparing this copy received with another copy of intended transmission. In this mechanism the source data block is send twice. The receiver compares them with the help of a comparator and if those two blocks differ, a request for retransmission is made. To achieve forward error correction, three sets of the same data block are sent and majority decision selects the correct block. These methods are very inefficient and increase the traffic two or three times. Fortunately there are more efficient error detection and correction codes. There are two basic strategies for dealing with errors. One way is to include enough redundant information (extra bits are introduced into the data stream at the transmitter on a regular and logical basis) along with each block of data sent to enable the receiver to deduce what the transmitted character must have been. The other way is to include only enough redundancy to allow the receiver to deduce that error has occurred, but not which error has occurred and the receiver asks for a retransmission. Decoys are typically thought of as larger - scale, lower fidelity systems intended to change thestatistical success rate of tactical attacks. For example, Deception ToolKit, DWALL, the InvisibleRouter, HoneyD, and Responder are designed to produce large number s of deceptive services ofdifferent characteristics that dominate a search space. The basic idea is to fill the search space ofthe attacker’s intelligence effort with decoys so that detection and differentiation of real targetsbecomes difficult or expensive. In this approach, the attacker seeking to find a target does a typical sweep of an address space looking for some set of services of interest. II. ERROR DETECTION TECHNIQUES There are many reasons such as noise, cross-talk etc., which may help data to get corrupted during transmission. The upper layers work on some generalized view of network architecture and are not aware of actual hardware data processing.Hence, the upper layers expect error-free transmission between the systems. Most of the applications would not function expectedly if they receive erroneous data. Applications such as voice and video may not be that affected and with some errors they may still function well. There are number of error detection techniques I will discuss parity check, checksums and CRC checks Thus if the probability of a single bit being is error is 10-6, then theprobability of an error in an 8-bit pattern (7 + parity) is about 8 x 10-6 and the probabilityof a double error is about 3 x 10-11 which is quite small.An additional issue is that in some circumstances when an error does occur, it occursin a clump - i.e. groups of bits may get corrupted together. Thus if the probability of one bitbeing corrupted is P (small) then the probability of two successive bits being corrupted is notP2, but something much larger, maybe even approaching P. A way around that is to “matrix the check as follows D11 D21 D31 D41 P1 D12 D22 D32 D42 P2 D13 D23 D33 D44 P3 D14 D24 D34 D44 P4 D15 D25 D35 D45 P5 Table1 : Parity check matrix 2.1 Parity The most common method for detectingbits error with asynchronous character and characterorientedsynchronous transmission is parity bit method.There are two types of parity check schemes: even andodd parity checks [9]. With the even parity check, theredundant bit is chosen so that an even number of bits areset to one in the transmitted bit string of N+r bits, where is the bit that used to be the even parity check and N is the bit that is transmitted by the transmitter of thenetwork. The receiver re-computes the parity of eachreceived bits from the transmitter and discard the stringswith the invalid parity. The parity scheme is always usedif 7-bits character is exchanged. If there are 7-bits that aretransmitted by the transmitter and parity check are usedto detect the error, the eight bit is often the parity bit. Parity is the simplest form of error checking. It adds one bit to the pattern and thenrequires that the modulo-2 sum of all the bits of the pattern and the parity bit have a definedanswer. The answer is 0 for even parity and 1 for odd parity. An alternative way of makingthe same statement is that odd(even) parity constrains there to be an odd(even) number of“1"s in the pattern plus parity bit. Parity bits are sufficient to catch all single errors in the pattern plus parity bit as thiswill change a single 1 to a 0 or vice versa and therefore upset the parity calculation. Arepeat of the parity calculation at any time will reveal this problem. However the system willnot catch any double errors (except the trivial case of two errors on the same bit) and thesewill be flagged as valid. For example a pattern of 0110100 becomes 00110100 with the addition of a parity bitand enforcement of odd parity. A single error would (for example) change the pattern to00110000 which has the wrong parity. However a further error to 10110000 looks OK - butis in fact wrong.The length of pattern which each parity bit “guards” should be as long as possible sothat the parity bit takes up the least amount of extra storage, but not so long that a doubleerror becomes likely. In this matrix the parity bits P1-P5 are computed through the columns whereas the data iscorrupted (for whatever reason) by rows. In this case a “burst error” of D22, D23 willproduce parity errors on recalculation for bits P2 and P3 whereas a double error in row twowould “fool” the system if parity were computed in rows. Performance of Parity Check Parity check mechanismcan detect all single-bit errors. It can also detectburst errors only if the total number of errors ineach data unit is odd/even (based on paritycheck used). For example, even parity checkmechanism cannot detect errors where the total numberof hits changed is even. If any two bits change intransmission, the changes cancel each other and the dataunit will pass a parity check even though the data unit isdamaged. The same holds true for any further evennumber of errors. 2.2 CRC Checks Cyclic Redundancy Check is the most powerful and easy toimplement technique. Unlike checksum scheme, which is based on addition, CRC is based on binary division. In CRC, a sequence of redundant bits, called cyclic redundancy check bits, are appended to the end of data unit so that the resulting data unit becomes exactly divisible by a second, predetermined binary number. At the destination, the incoming data unit is divided by the same number. If at this step there is no remainder, the data unit is assumed to be correct and is therefore accepted. A remainder indicates that the data unit has been damaged in transit and therefore must be rejected. The generalized technique can be explained as follows. Unlike parity check which is based on the submission ofthe binary, CRC is based on the binary division. In CRC,instead of adding bits to achieve a desired parity, asequence of redundant bits, called the CRC or the CRCremainder, is appended to the end of a data unit so thatthe resulting data unit becomes exactly divisible by asecond. On the destination side, the incoming data thebinary data is divided by the same number to be comparedon the source side. Means that, if the remainder of thedivision is same as the value on the added CRC when thedata was transmit, the data will be accepted, otherwise theunmatched reminderproduced on the destination after theCRC is indicates the data unit has been damage during the transmission of data. If a k bit message is to be transmitted, the transmitter generates an r-bit sequence, known as Frame Check Sequence (FCS) so that the (k+r) bits are actually being transmitted. Now this r-bit FCS is generated by dividing the original number, appended by r zeros, by a predetermined number. This number, which is (r+1) bit in length, can also be considered as the coefficients of a polynomial, called Generator Polynomial. The remainder of this division process generates the r-bit FCS. On receiving the packet, the receiver divides the (k+r) bit frame by the same predetermined number and if it produces no remainder, it can be assumed that no error has occurred during the transmission. Operations at both the sender and receiver end are shown below receiver side. At the receiver side, the data string and the CRC value is divided by the same value of divisor in the sender part. Then the remainder of this division determines either the received data bit string that to be accepted or not. If the remainder is zero, then the data will be accepted or else it will be rejected. Fig 2 : CRC in sender side. Fig 3 : CRC in receiver side. Fig1 : Basic scheme for Cyclic Redundancy Checking Figure-2 shows the calculation for the CRC in the sender, as shown, the added of the data plus extra zero that is added to the data string and divided with the divisor. The remainder of the division will be the value of CRC that will replace the data plus extra zeros at the receiver side. Figure-3 shows the calculation for the CRC in the The redundancy bits used by CRC are derived by dividing the data unit by a predetermined divisor; the remainder is the CRC. To be valid, a CRC must satisfy two conditions: It must have exactly one less bit than the divisor and appending it to the end of the data string must make the resulting bit sequence exactly divisible by the divisor. The transmitter can generate the CRC by using a feedback shift register circuit. The same circuit can also be used at the receiving end to check whether any error has occurred. All the values can be expressed as polynomials of a dummy variable X. For example, for P = 11001 the corresponding polynomial is X4+X3+1. A polynomial is selected to have at least the following properties: o It should not be divisible by X. o It should not be divisible by (X+1). bits, called the checksum field. The extended data unit is transmitted across the network. So if the sum of the data segments is T, the checksum will be –T. The first condition guarantees that all burst errors of a length equal to the degree of polynomial are detected. The second condition guarantees that all burst errors affecting an odd number of bits are detected. CRC process can be expressed as XnM(X)/P(X) = Q(X) + R(X) / P(X) Performance of CRC CRC has a very good performancein detecting single-bit errors, double errors, an oddnumber of errors and burst errors. They can easily beimplemented in hardware and software. They areespecially fast when implemented in hardware. This hasmade CRC a good candidate for many networks. 2.3 Checksum The checksum method which is a very simple method based on adding up all the words that are transmitted and then transmit them including the complement result of that sum. Like the parity check and CRC, the checksum is based on the concept ofredundancy. A checksum is a count of the number of bits in a transmission unit that is included with the unit so that the receiver can check to see whether the same number of bits arrived. If the counts match, it's assumed that the complete transmission was received. Checksum is a calculated value that is used to determine the integrity of data. Checksum serves as a unique identifier for the data (a file, a text string, or a hexadecimal string). If the data changes then so does the checksum value. This makes it easy to verify the integrity of the data. To test data integrity, the sender of the data calculates checksum value by taking the sum of the binary data transmitted. When receiving the data, the receiver can perform the same calculation on the data and compare it with the checksum value provided by the sender. If the two values match, the receiver has a high degree of confidence that the data was received correctly. Checksum value is also called hash value. The data that is calculated can be a file, a text string, or a hexadecimal string. In checksum error detection scheme, the data is divided into k segments each of m bits. In the sender’s end the segments are added using 1’s complement arithmetic to get the sum. The sum is complemented to get the checksum. As shown in Figure 4, in the sender, the checksum generator subdivides the data unit into equal segments of n bits (usually 16). These segments are added using ones complement arithmetic in such a way that the total is also n bits long. That total (sum) is then complemented and appended to the end of the original data unit as redundancy Fig 4 : Checksum operation The receiver performs the same calculation on the received data and compares the result with the receivedchecksum. If the result is 0, the receiver keeps the transmitted data; otherwise, the receiver knows that anerror occurred discards the transmitted data.The checksum detects all errors involving an oddnumber of bits as well as most errors involving an evennumber of bits. The checksum segment is sent along with the data segments as shown in Fig. 5. At the receiver’s end, all received segments are added using 1’s complement arithmetic to get the sum. The sum is complemented. If the result is zero, the received data is accepted; otherwise discarded, as shown in Fig. 6. Fig 5 : Sender’s end for the calculation of the checksum Fig 6 : Receiving end forcalculation of the checksum Performance of Checksum The checksum detects all errors involving an odd number of bits. It also detects most errors involving even number of bits. The traditional checksum uses a small number of bits (16) to detect errors in a message of any size (sometimes thousands of bits). However, it is not as strong as the CRC in errorchecking capability. For example, if the value of one word is incremented and the value of another word is decremented by the same amount, the two errors cannot be detected because the sum and checksum remain the same. Also if the values of several words are incremented but the total change is a multiple of 65535, the sum and the checksum does not change, which means the errors are not detected. III. DECOY COMPUTER SYSTEM The use of deception, or decoys, plays a valuable role in the protection of systems, networks,and information. Decoys are constructs which containdata that appears valuable but is in fact spurious. Since authentic users will have a naturalfamiliarity with their working environment, they are capable of remembering which resourcesare real and which are fabricated. They will have no need, therefore, to access inauthenticdecoys that contain no truly useful data. Adversaries without a thorough knowledge of a target system, on the other hand, will have difficulty differentiating decoys from desirable data. After the number of decoy accessevents pass a certain threshold, an organization can respond by enacting more restrictivesecurity measures and launching an investigation into the account which caused the alertsto occur. Monitoring access to decoy _les and content can thus provide protection againstcyberattacks in a practical and cost effective fashion. Decoy technology also addresses the asymmetry that currently exists with respect to responding to different types of security violations after they have already occurred. In thecase of data integrity breaches, recovery mechanisms have been developed that allow administrators to \roll back" systems to a checkpointed state that existed prior to when themalicious event took place. Similarly, attacks against the availability of computer networkscan be thwarted by increasing the amount of redundant resources that are deployed. Previously, there was no such solution for reacting to attacks against system confidentiality afterthe fact, however. Decoys can serve this role by providing a mechanism through which datacan be tracked after an adversary has already absconded with it. Computers whose primary function is to attract the attention of malicious actors are oftencalled honeypots." Entire networks of such spurious machines are known as honeynets." These systems are usually constructed in a way such that they appear as though they arean unassuming component of a larger network architecture. In reality, however, they failto contain any useful data and are cordoned o_ from network resources which are actuallyvalued. Honeypots and honeynets can be quite effective when used to detect external threats.Their applicability towards defending against attacks originating from within an organizationis limited, though. This is due to the fact that this class of adversaries typically alreadyhave the knowledge that is required to access the portion of a network where legitimatedata resides. Furthermore, honeypots offer no utility after a successful attack has alreadyoccurred. Decoys are typically thought of as larger - scale, lower fidelity systems intended to change thestatistical success rate of tactical attacks. For example, Deception ToolKit, DWALL, the InvisibleRouter, HoneyD and Responder are designed to produce large number s of deceptive services ofdifferent characteristics that dominate a search space. The basic idea is to fill the search space ofthe attacker’s intelligence effort with decoys so that detection and differentiation of real targetsbecomes difficult or expensive. In this approach, the attacker seeking to find a target does atypical sweep of an address space looking for some set of services of interest. A decoy system wants to be compromised. Once an intruder comes in, it can track activity, figure out what data is being targeted and be a foundation for incident response and network forensics.The decoy network, in effect, can send off alarm bells – alerts – that an attack is under way. And protect the actual network from attack, by taking its brunt. The unauthorized user’s keystrokes get captured and sent to a system log. Bogus files can be spirited away, with no harm done. Etc. The decoy network becomes a sensor and a prosecution system. It’s relatively simple, the journal notes, to put an extra interface on a firewall to control communications with the intruder. And programmable toolkits can even make it look like the system is vulnerable to attack, when a hacker starts a probe.Such systems are not considered traps, legally, because there is no advertising of the decoy network. Hackers must take it upon themselves to find it and infiltrate it. Properties of Decoys In order to design decoys that are as effective as possible, it is also beneficial to analyzethem in a more general sense by considering characteristics that are independent of a particular context.A “perfectly believable decoy” would precisely conform to all of these guidelines, though practical restrictions prevent this from occurring in most situations. Although there exists some overlap between these traits, it is also worth noting that they are not completely orthogonal. For example, believability and differentiability are in contention to some extent. Believability One of a decoy's primary functions is to be believable. Upon inspection, a decoy shouldappear authentic and trustworthy. In the absence of any additional information, it shouldbe impossible to discern a spurious decoy from authentic data. For example, a decoy taxdocument should contain all of the same fields as one that is actually in use, and each of its fields should be populated with realistic values. Believability can be formalized via the following thought experiment. Consider a pool of files, some of which contain real data and some of which are fabricated decoys. Select a decoy file and real piece of data from this pool, and present it to an adversary. The selected decoycan be considered perfectly believable if this attacker has an equal probability of selectingthe decoy and the legitimate document.This characteristic is of critical importance to externally observable features of decoys. Delectability Delectabilitydescribes the ability of decoysto notify their owner when they have been accessed. An ideal decoy system would issue analert each and every time a decoy is accessed, but technical challenges, including networkavailability and variability between software platforms, mean that this may not always bepossible in practice.Deploying multiple overlapping decoy monitors that operate at different system levelscan help mitigate the possibility of an attacker accessing a decoy while remaining undetected. Features of the decoy documents themselves can be leveraged to equip them withembedded alert code. Monitoring software can be placed in the operating system to detectpredetermined tokens placed within decoys when they are opened. Further, operating system auditing can be enabled to record decoy interactions. In order to check for document exfiltration, software can be placed on network equipment to check for such tokens as well.Finally, the content of decoy documents can also serve as an alert system. For example,credentials for spurious accounts can be placed within a decoy. Since there is no reason thata legitimate user would ever access these accounts, any activity they exhibit would send astrong signal of malicious intent. Variability Although a decoy distribution system should strive to make its fake documents seem asauthentic as possible, it would certainly be undesirable if precisely the same well-crafted decoy file were placed repeatedly throughout a given system or network. This would greatly simplify the task of distinguishing between legitimate data and the planted decoys that serve as monitors. In general, there should be as much variability between decoy documents as there exists in the pool of documents that they are intended to detect. That is, the task of identifying a decoy should not be reducible to identifying a particular invariant that exists between all generated decoys. A different way to conceptualize variability is to consider the task of an adversary whowishes to extract information from a system while remaining undetected. Assume thatthe attacker has been able to discern which documents that have been accessed thus far areauthentic and which are traps. With a collection of \perfectly variable" decoys, this adversarywould still be unable to discern future decoy material from real data with a probabilitygreater than one half. Previous decoy knowledge, therefore, should not impact the task ofidentifying future decoys. Note the relationship that exists between the trait of variabilityand the believability characteristic. Variability among decoys essentially means that decoysshould remain believable even after the presence of other decoys has been revealed. Stealth While it is clearly desirable that every decoy access event be perceptible to the owners of a system, care must be taken lest the alarms that accomplish this arouse suspicion. An overt mechanism for issuing alert beacons would provide adversaries with an obvious signal that an element contains a trap, which completely violates the property of decoy variability. The messages that are transmitted by decoys must therefore be as subtle and covert as possible. Raising an alert that decoy content has been accessed necessarily involves taking some action, however. Even if precautions are taken, there is always the possibility that this act will be perceptible to a malicious actor. It is therefore also desirable to trigger beacon events as early as possible to prevent their interception. For example, alerts for _le based decoys should be raised as soon as they are accessed and prior to any content being displayed, if feasible. This would eliminate the possibility of a decoy being recognized and discarded before the decoy system has an opportunity to detect that is has been accessed. Non-interference This property is the first to describe how decoys should coexist with legitimate users whoare not masquerading with assumed credentials. An optimal masquerader detection network would not affect the habits of typical users in any way. By inserting decoy material into anoperating environment, however, we introduce the possibility that this data will confuse usersor otherwise hinder their ability to complete their everyday tasks. It is therefore desirablefor decoys to demonstrate the property of non-interference by not obstructing the behaviourof normal users. If a file system is populated with decoy documents that serve as intrusion sensors, forexample, the probability that the file system's primary owner is able to access a particularstandard document should remain the same as it was prior to the introduction of the decoycontent. Similarly, introducing decoy applications to a mobile device's operating systemshould not impact a user's ability to access real applications as they normally would. IV. CONCLUSION Decoy computer system and error detection methods have been discussed in this paper. There are different ways to detect error. But not all the methods of error detection can detect error accurately and effectively. Every method has its own specialty, advantage and its own mechanism to detect error. Parity check is simple and can detect all single-bit error. CRC has a very good performance in detecting single-bit errors, double errors, an odd number of errors, and burst errors while checksum is not efficient as the CRC in error detection when the two words are incremented with the same amount, the two errors cannot be detected because the sum and checksum remain the same. Decoys represent a drastic departure from existing security solutions in several important ways. By placing content that is spurious yet believable and enticing in the path of potential adversaries, decoys serve as a potent last line of defence against attacks. Decoy content can be proactively seeded throughout a system to defend against potential attacks, or fed to an adversary once malicious activity has been detected. Furthermore, by tracking decoy material, violations of confidentiality can be addressed after they have occurred. This is a capability that alternative security measures are not capable of offering. Decoys can be integrated as useful components of any full featured security solution and will only increase in prominence as threats against computer systems continue to grow. With all this factors error detection techniques can be used with decoy computer systems. ACKNOWLEDGMENT I would gratefully and sincerely appreciate my supervisor: Assistant Prof. Tarannum Shaikh. Her inspiring guidance, rich experience and sustained encouragement enabled me to develop an intensive understanding of my research area. Without the generous help of my supervisor, this work would not have been possible. I am honored to have Prof. Tarannum Shaikh from A.C.Patil College as my opponent. I thank her for her kind support and helpful suggestions during the discussions in my MCA. REFERENCES 1. AfiqahAzahari, RaedAlsaqour, Mueen Uddin and Mohammed Al-Hubaishi "Review Of Error Detection Of Data Link LayerIn Computer Network" January 2014 2. L. L. Peterson and B. S. Davie. 2007. Computer networks: a systems approach 3. Andrew S. Tanenbaum, David “Computer Networks” Fifth Edition 4. Saad Mneimneh detection” 5. Kurose, J.F. and Ross K.W., "Computer Networking: A Top-Down Approach Featuring the Internet", Third Edition, 2005 6. M. Ben Salem and S. Stolfo. Decoy Document Deployment for Effective Masquerade Attack Detection, 2011. 7. Jonathan Voris, Jill Jermyn, Angelos D. Keromytis, and Salvatore J. Stolfo "Bait and Snitch: Defending Computer Systems withDecoys" 8. B. Bowen and S. Hershkop and A. Keromytis and S. Stolfo. "Baiting Inside AttackersUsing Decoy Documents" 9. Kellep A. CharlesDecoy Systems:A New Player in Network Security and Computer Incident Response “Computer J. Wetherall Networks Error 10. Y. Park and S. Stolfo. Software Decoys for Insider Threat.2012 11. B. M. Bowen, V. P. Kemerlis, P. Prabhu, A. D. Keromytis, and S. J. Stolfo. Automatingthe injection of believable decoys to detect snooping, 2010. 12. Fred Cohen "The Use of Techniques:Honeypots and Decoys" Deception