System Security Assessment Form
advertisement
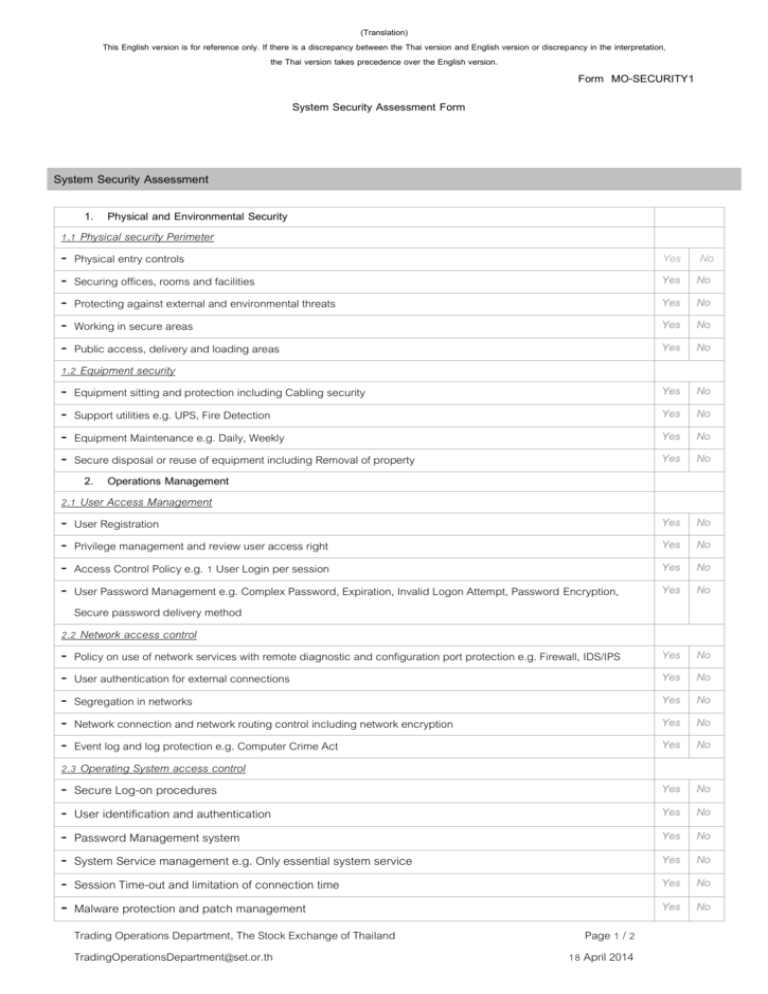
(Translation) This English version is for reference only. If there is a discrepancy between the Thai version and English version or discrepancy in the interpretation, the Thai version takes precedence over the English version. Form MO-SECURITY1 System Security Assessment Form System Security Assessment 1. Physical and Environmental Security 1.1 Physical security Perimeter - Physical entry controls - Securing offices, rooms and facilities - Protecting against external and environmental threats - Working in secure areas - Public access, delivery and loading areas 1.2 Equipment security - Equipment sitting and protection including Cabling security - Support utilities e.g. UPS, Fire Detection - Equipment Maintenance e.g. Daily, Weekly - Secure disposal or reuse of equipment including Removal of property 2. Operations Management 2.1 User Access Management - User Registration - Privilege management and review user access right - Access Control Policy e.g. 1 User Login per session - User Password Management e.g. Complex Password, Expiration, Invalid Logon Attempt, Password Encryption, Secure password delivery method 2.2 Network access control - Policy on use of network services with remote diagnostic and configuration port protection e.g. Firewall, IDS/IPS - User authentication for external connections - Segregation in networks - Network connection and network routing control including network encryption - Event log and log protection e.g. Computer Crime Act 2.3 Operating System access control - Secure Log-on procedures Yes Yes Yes Yes Yes No No No No No Yes Yes Yes Yes No No No No Yes Yes Yes Yes No No No No Yes Yes Yes Yes Yes No No No No No Yes No - User identification and authentication Yes No - Password Management system Yes No - System Service management e.g. Only essential system service Yes No - Session Time-out and limitation of connection time Yes No - Malware protection and patch management Yes No Trading Operations Department, The Stock Exchange of Thailand TradingOperationsDepartment@set.or.th Page 1 / 2 18 April 2014 (Translation) This English version is for reference only. If there is a discrepancy between the Thai version and English version or discrepancy in the interpretation, the Thai version takes precedence over the English version. - Event log and log protection e.g. Computer Crime Act Form MO-SECURITY1 Yes No 2.4 Application access control - Information access restriction Sensitive system isolation User identification and authentication Password Management system Risk Agreement messages to aware user Trading Application control as compliance and legal requirements Secure coding e.g. protect some special characters (sql injection protection) Event log and log protection e.g. Computer Crime Act 3. Business Continuity Management Management of Information Security Incidents and Improvements e.g. Responsibilities and Procedures, Collection of evidence Business continuity management process e.g. developing and implementing continuity plans including information security Business continuity and Risk Assessment Testing, maintaining and re-assessing business continuity plans Backup Management Trading Operations Department, The Stock Exchange of Thailand TradingOperationsDepartment@set.or.th Page 2 / 2 18 April 2014 Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No Yes No







