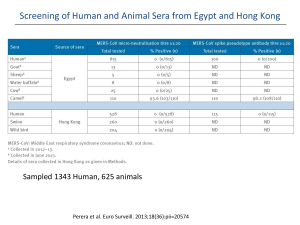
Verbatim Mac - SpartanDebateInstitute
advertisement

Racial, Ethnic, and Religious Surveillance Aff Plans Plan – Policy The United States Federal Judiciary should rule that domestic surveillance on the basis of race, religion, and ethnicity are unconstitional. Plan solves. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] The grant of surveillance power to monitor individuals without suspicion of criminal or terrorist activity and the ability to collect personal information from various sources on the basis of race or ethnicity has resulted in the discrimination of domestic individuals who belong to a particular racial or ethnic group. This discrimination is generated through a disparate impact that the new government surveillance authority has on various ethnic and religious groups, specifically those that are Arab, South Asian, or practitioners of the Islamic religion. Through a balancing test of five factors established through Supreme Court jurisprudence, it is apparent that there is sufficient indirect evidence of the government's intent to discriminate. Because there is an established intent to discriminate, the new government surveillance authority and procedures can only be constitutionally upheld if the acts are narrowly tailored to a compelling government interest. The compelling state interest is satisfied through the goal of nationally security; however, the narrowly tailored prong fails because of the monitoring system's over-inclusiveness. Therefore, the government national security surveillance authority and procedures, via the NCTC amendments and DIOG guidelines, are in violation of the Fourteenth Amendment's Equal Protection Clause. Plan – K The United States Federal Government should end domestic surveillance on the basis of race, religion, and ethnicity. Plan solves. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] The grant of surveillance power to monitor individuals without suspicion of criminal or terrorist activity and the ability to collect personal information from various sources on the basis of race or ethnicity has resulted in the discrimination of domestic individuals who belong to a particular racial or ethnic group. This discrimination is generated through a disparate impact that the new government surveillance authority has on various ethnic and religious groups, specifically those that are Arab, South Asian, or practitioners of the Islamic religion. Through a balancing test of five factors established through Supreme Court jurisprudence, it is apparent that there is sufficient indirect evidence of the government's intent to discriminate. Because there is an established intent to discriminate, the new government surveillance authority and procedures can only be constitutionally upheld if the acts are narrowly tailored to a compelling government interest. The compelling state interest is satisfied through the goal of nationally security; however, the narrowly tailored prong fails because of the monitoring system's over-inclusiveness. Therefore, the government national security surveillance authority and procedures, via the NCTC amendments and DIOG guidelines, are in violation of the Fourteenth Amendment's Equal Protection Clause. Policy 1ac Terror Adv Voluntary informants won’t come forward now – FBI surveillance of Muslim communities undermines involvement. Reversing that is critical to stop terrorism. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] Moreover, Professor David A. Harris claims that "the unregulated use of informants in mosques and other religious and cultural settings can also do great damage because it poses the risk of cutting off our best possible source of intelligence: the voluntary, cooperative relationships that have developed between law enforcement and Muslim communities." 102Link to the text of the note Having community members report suspicious information to the FBI may be a more effective way of obtaining reliable terrorism intelligence from these communities. 103Link to the text of the note For example, in the few domestic terrorist prosecutions where a terrorist attack plan actually existed prior to informant involvement, community members who had noticed something amiss were the first to alert the FBI and identify the subjects. 104Link to the text of the note In fact, since 9/11, community members have assisted law enforcement in stopping potential terrorism plots in a number of cases. 105Link to the text of the note A [252] recent example, the case of Umar Farouk Abdulmutallab, the "Underwear Bomber," shows that the attempted bombing could have been prevented had law enforcement heeded the warnings that Abdulmutallab's father gave the CIA at the U.S. embassy in Nigeria. 106Link to the text of the note As the president of the San Francisco Board of Supervisors and former criminal prosecutor, David Chiu testified regarding the Arab, Middle Eastern, Muslim, and South Asian communities in San Francisco: "Without that level of cooperation, that level of trust, everything falls apart … . Surveillance only serves to continue to drive wedges when cooperation is what is needed most." 107Link to the text of the note FBI surveillance fails now – it produces a massive chilling effect and alienates Muslim communities inside the United States. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] In the past, the FBI's Domestic Investigations and Operations Guide ("DIOG"), which provides guidance on implementing the Attorney General's Guidelines, allowed supervisory agents to delegate to inferior agents decisions concerning the surveillance of mosques and other religious gathering places. 72Link to the text of the note Recently, however, restrictions have been slightly strengthened by requiring agents in charge of the field operations to approve surveillance. 73Link to the text of the note Nevertheless, this change may not really improve matters, as numerous instances of mosque surveillance have already eroded Muslim communities' trust of law enforcement. 74Link to the text of the note By placing informants in places of worship and cultural spaces, the FBI has chilled free speech and damaged the most reliable way of obtaining accurate terrorism intelligence from these communities. In a well-publicized and egregious case, an FBI informant named Craig Monteilh was assigned to surveil a mosque in Irvine, California. 75Link to the text of the note The FBI instructed Monteilh, a convicted felon working as a paid informant, 76Link to the text of the note to [248] indiscriminately surveil worshippers at the mosque, without concentrating on a particular target or activity. 77Link to the text of the note After congregants noticed Monteilh's inflammatory rhetoric and repeated talks about instigating terrorism, they reported him to the FBI. 78Link to the text of the note The FBI failed to investigate further, and after the arrest of another suspected terrorist, Monteilh revealed his identity as an FBI informant. 79Link to the text of the note This incensed the Islamic community, in part because an FBI Assistant Director had promised a year earlier that the agency would not surveil mosques. 80Link to the text of the note In response, Islamic groups like the Council on American-Islamic Relations and the American Muslim Task Force on Civil Rights and Elections, which had previously cooperated with the FBI and urged community members to do the same, reversed course and stopped their outreach efforts to aid law enforcement. 81Link to the text of the note In the end, Craig Monteilh's story is just one of many that demonstrate why Muslim communities have soured on helping the FBI locate suspicious people within their communities. 82Link to the text of the note Although Monteilh was neither an immigrant nor was offered immigration incentives in return for intelligence, his story shows how the use of informants can potentially damage both law enforcement and immigrant communities. Monteilh's story also illustrates why many communities feel mosque surveillance infringes on their freedom of speech. Once a community becomes aware that FBI informants may be surveilling its mosques, the fear that informants will target them chills the free exchange and expression of ideas and speech. 83Link to the text of the note Given the constitutional guarantees of the First Amendment, places of worship should be treated with utmost sensitivity by law enforcement, 84Link to the text of the note as the self-editing that occurs when people know they are being watched curtails the free exchange of ideas. The very knowledge of potential surveillance may caution people against discussing their political and religious viewpoints for fear of being targeted by informants like Monteilh. Consequently, mosque attendance falls 85Link to the text of the note and community cohesion suffers, thwarting the First Amendment's protection of free expression. Even those not harboring extreme viewpoints may be [249] dissuaded from political speech for fear of misinterpretation. For example, after revelations of potential FBI surveillance surfaced at the Islamic Center of Irvine, congregant Omar Turbi attested, "It gives you a little bit of apprehension about who you trust … . Makes you think twice about what you say; what if people misunderstand you?" 86Link to the text of the note Similarly, the executive director of the Council on American-Islamic Relations in Anaheim stated, "Some average Muslims interested only in praying are avoiding mosques for fear of somehow being monitored or profiled … . Everybody is afraid, and it is leading to an infringement of the free practice of our religion." 87Link to the text of the note Although some states like Indiana, Pennsylvania, and Oregon have enacted laws prohibiting the surveillance of religious sites without reasonable suspicion, 88Link to the text of the note it should not be necessary to rely on state laws to protect the integrity and values of the First Amendment. B. Mosque Surveillance Encourages Religious and Ethnic Profiling In addition to eroding the First Amendment's free speech rights of Muslims and Middle Easterners, the FBI's informant surveillance tactics also inappropriately target these religious and ethnic groups. Most of the organizations designated as Foreign Terrorist Organizations by the State Department are Muslim or Arab groups. 89Link to the text of the note Many post-9/11 policies, like the extensive detention of Muslims and Middle Easterners, indicate that the federal government views Muslims and Middle Eastern immigrants as potential terrorists. 90Link to the text of the note Popular perception of Muslims has moved in the same direction, with huge opposition, for example, to the construction of an Islamic community center - Park 51 - near the site of the World Trade Center in New York. 91Link to the text of the note Other examples include state laws banning the use of Shari'ah law in judicial decisions 92Link to the text of the note and Islamophobia 93Link to the text of the note rising in the United States 94Link to the text of the note and abroad. 95Link to the text of the note [250] By sending immigrant informants into mosques and religious and ethnic communities with little more than a vague directive to find terrorists, the FBI perpetuates ethnic profiling and the conflation of Islam and terrorism. In recruiting terrorism informants from the immigrant population, the FBI puts an ethnic and religious face on terrorism, and perpetuates the popular perception of what terrorists look like. Sending these informants into mosques and immigrant communities greatly increases the chances that alleged suspects fit the ethnic and religious stereotypes of terrorists. Put differently, if an informant is assigned to surveil a mosque, the chances of the informant bringing back a non-Muslim or non-Middle Eastern suspect are low. This surveillance policy becomes a vicious cycle. The FBI recruits immigrant individuals from suspect communities to become informants, pressures them into producing terrorism suspects that fit the popular perception of what terrorists are like, and then prosecutes these suspected terrorists. All this reinforces the public conflation of immigrants, Muslims, Middle Easterners, and terrorists. Ethnic and religious profiling further alienates Muslim and Middle Eastern communities, and deepens their mistrust for government. 96Link to the text of the note Additionally, by predisposing many Americans to view Muslims, immigrants, and Middle Easterners as potential terrorist threats, ethnic and religious profiling may also bias juries in terrorism prosecutions. 97Link to the text of the note Although suspects often claim entrapment as a defense, after 9/11 the entrapment defense has never been successfully used in terrorism cases. 98Link to the text of the note In fact, many, if not most, terrorism cases never reach the jury because the chances of successfully defending against terrorism charges after 9/11 are almost nonexistent. 99Link to the text of the note Popular stereotypes concerning Muslims and Middle Easterners play a role in this. Although the use of immigration law in recruiting informants is only one of many factors contributing to this harmful cycle, the use of coercive tactics like immigration law to recruit informants creates a [251] higher risk of unfounded terrorism prosecutions against innocent individuals who do not pose a risk. Consequently, this fuels the public perception that a stereotypical terrorist is a Middle Easterner or Muslim. FBI surveillance of racial, ethnic, and religious minorities creates a chilling effect – it undermines the legitimacy of informant cooperation programs, trades off with resources for countering terrorism, and produces false intelligence. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] The FBI's use of immigration rewards and threats to recruit informants undermines civil liberties and cooperation with Muslim, Middle Eastern, and other immigrant communities. 67Link to the text of the note In general, the presence of informants in mosques and the surrounding community creates suspicion and distrust of law enforcement efforts, chilling free speech. That is, when community members know that informants are potentially monitoring their speech, community members are less likely to cooperate with law enforcement efforts. Furthermore, by sending informants into Muslim and Middle Eastern communities without specific targets to surveil, the FBI encourages ethnic and religious profiling and helps conflate Islam and terrorism in the public eye. Because informants recruited via immigration law possess less bargaining power and face potentially more serious consequences than those recruited via criminal law incentives, there is greater incentive for these informants to supply false information and accuse innocent individuals. Ethnic and religious profiling, combined with the indiscriminate surveillance carried out by informants, can entrap individuals who do not pose a threat. Entrapment wastes government resources and undermines public confidence in the justice system and law enforcement. Although the FBI's problematic surveillance of Muslim and Middle Eastern communities stems from the use of all types of informants and not merely those recruited with immigration promises, a modification to the use of immigration law in rewarding or coercing terrorism informants would provide a step toward producing more useful intelligence and reducing the risk of harm to innocent individuals. Perception of government accountability is critical to effective informants – limiting arbitrary surveillance is critical to the perception of legitimacy of surveillance programs. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] [245] Third, while false and inaccurate intelligence has generally been a problem with informants, 58Link to the text of the note recent terrorism investigations raise the question of whether the alleged terrorist crimes would have occurred without law enforcement instigating the terrorist activities. 59Link to the text of the note Informants in these cases aggressively instigated the defendants' participation in the plot. 60Link to the text of the note Recruiting informants who lack ties to terrorist organizations may be at the root of this problem, because they lack predetermined targets known to be involved in terrorist groups. 61Link to the text of the note Without these targets, informants under pressure to avoid deportation or other immigration consequences, for example, are more likely to produce false information. 62Link to the text of the note Further complicating this issue, the government has suffered from credibility problems in terrorism investigations for not always fulfilling the promises made to informants. 63Link to the text of the note One FBI informant, a Yemeni citizen named Mohamed Alanssi, set himself on fire in front of the White House after alleging that the FBI had broken numerous promises to him. 64Link to the text of the note Governmental credibility is critical to maintaining a relationship of trust between law enforcement and informants, and thereby facilitates the gathering of credible intelligence. Due to the vast number of terrorism informants today, the secrecy underlying the investigations, 65Link to the text of the note and the potential for false intelligence, the recruitment and use of informants in terrorism investigations present unique problems to the FBI. Because of increased confidentiality surrounding national security issues, the government has the means and incentives to shield the true extent of its recruitment and use of terrorism informants from courts and the public. 66Link to the text of the note To increase accountability and lessen the risk of abuse, more oversight over the FBI's dealings with terrorism informants is needed. Notably, some limits on the FBI's use of informants do exist. However, given the secrecy [246] surrounding national security concerns, whether these limits apply in terrorism investigations remains unclear. Rebuilding trust between Muslim communities and law enforcement is critical – curtailing surveillance is key to law enforcement credibility. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] In order to procure accurate intelligence from any community, a relationship of trust and respect between law enforcement and the community must exist. 116Link to the text of the note However, from the mass arrest and detention of Muslims shortly after 9/11 117Link to the text of the note to the ongoing allegations of ethnic and religious profiling today, 118Link to the text of the note the federal government has made serious errors in dealing with Muslim and Middle Eastern communities since 9/11. While the government recognizes that community policing 119Link to the text of the note is the best way to obtain reliable intelligence, 120Link to the text of the note the FBI is caught between two contradictory strategies and must choose between sending informants into mosques without reasonable suspicion, and gaining the trust and cooperation of Muslim and Middle Eastern communities. As one congregant in a surveilled mosque observed, "The FBI wants to treat the Muslim community as a partner while investigating us behind our backs … . They can't have it both ways." 121Link to the text of the note While it is unrealistic to think that the FBI will stop using informants in these communities, a more restrained use of informants based on reasonable suspicion of wrongdoing would mitigate perceived damages to community relations. Requiring the FBI to have preexisting reasonable suspicion would add credibility to the agency and alleviate some of the fear surrounding terrorism investigations involving informants. Nuclear terrorism triggers extinction. Dvorkin, Major General (retired), 12 (Vladimir, doctor of technical sciences, professor, and senior fellow at the Center for International Security of the Institute of World Economy and International Relations of the Russian Academy of Sciences. The Center participates in the working group of the U.S.-Russia Initiative to Prevent Nuclear Terrorism, 9/21/12, "What Can Destroy Strategic Stability: Nuclear Terrorism is a Real Threat," belfercenter.ksg.harvard.edu/publication/22333/what_can_destroy_strategic_stability.html] Hundreds of scientific papers and reports have been published on nuclear terrorism. International conferences have been held on this threat with participation of Russian organizations, including IMEMO and the Institute of U.S. and Canadian Studies. Recommendations on how to combat the threat have been issued by the International Luxembourg Forum on Preventing Nuclear Catastrophe, Pugwash Conferences on Science and World Affairs, Russian-American Elbe Group, and other organizations. The UN General Assembly adopted the International Convention for the Suppression of Acts of Nuclear Terrorism in 2005 and cooperation among intelligence services of leading states in this sphere is developing.¶ At the same time, these efforts fall short for a number of reasons, partly because various acts of nuclear terrorism are possible. Dispersal of radioactive material by detonation of conventional explosives (“dirty bombs”) is a method that is most accessible for terrorists. With the wide spread of radioactive sources, raw materials for such attacks have become much more accessible than weapons-useable nuclear material or nuclear weapons. The use of “dirty bombs” will not cause many immediate casualties, but it will result into long-term radioactive contamination, contributing to the spread of panic and socio-economic destabilization.¶ Severe consequences can be caused by sabotaging nuclear power plants, research reactors, and radioactive materials storage facilities. Large cities are especially vulnerable to such attacks. A large city may host dozens of research reactors with a nuclear power plant or a couple of spent nuclear fuel storage facilities and dozens of large radioactive materials storage facilities located nearby. The past few years have seen significant efforts made to enhance organizational and physical aspects of security at facilities, especially at nuclear power plants. Efforts have also been made to improve security culture. But these efforts do not preclude the possibility that well-trained terrorists may be able to penetrate nuclear facilities. ¶ Some estimates show that sabotage of a research reactor in a metropolis may expose hundreds of thousands to high doses of radiation. A formidable part of the city would become uninhabitable for a long time.¶ Of all the scenarios, it is building an improvised nuclear device by terrorists that poses the maximum risk. There are no engineering problems that cannot be solved if terrorists decide to build a simple “gun-type” nuclear device. Information on the design of such devices, as well as implosion-type devices, is available in the public domain. It is the acquisition of weapons-grade uranium that presents the sole serious obstacle. Despite numerous preventive measures taken, we cannot rule out the possibility that such materials can be bought on the black market. Theft of weapons-grade uranium is also possible. Research reactor fuel is considered to be particularly vulnerable to theft, as it is scattered at sites in dozens of countries. There are about 100 research reactors in the world that run on weaponsgrade uranium fuel, according to the International Atomic Energy Agency (IAEA).¶ A terrorist “gun-type” uranium bomb can have a yield of least 10-15 kt, which is comparable to the yield of the bomb dropped on Hiroshima. The explosion of such a bomb in a modern metropolis can kill and wound hundreds of thousands and cause serious economic damage. There will also be long-term sociopsychological and political consequences.¶ The vast majority of states have introduced unprecedented security and surveillance measures at transportation and other large-scale public facilities after the terrorist attacks in the United States, Great Britain, Italy, and other countries. These measures have proved burdensome for the countries’ populations, but the public has accepted them as necessary. A nuclear terrorist attack will make the public accept further measures meant to enhance control even if these measures significantly restrict the democratic liberties they are accustomed to. Authoritarian states could be expected to adopt even more restrictive measures.¶ If a nuclear terrorist act occurs, nations will delegate tens of thousands of their secret services’ best personnel to investigate and attribute the attack. Radical Islamist groups are among those capable of such an act. We can imagine what would happen if they do so, given the anti-Muslim sentiments and resentment that conventional terrorist attacks by Islamists have generated in developed democratic countries. Mass deportation of the non-indigenous population and severe sanctions would follow such an attack in what will cause violent protests in the Muslim world. Series of armed clashing terrorist attacks may follow. The prediction that Samuel Huntington has made in his book “The Clash of Civilizations and the Remaking of World Order” may come true. Huntington’s book clearly demonstrates that it is not Islamic extremists that are the cause of the Western world’s problems. Rather there is a deep, intractable conflict that is rooted in the fault lines that run between Islam and Christianity. This is especially dangerous for Russia because these fault lines run across its territory. To sum it up, the political leadership of Russia has every reason to revise its list of factors that could undermine strategic stability. BMD does not deserve to be even last on that list because its effectiveness in repelling massive missile strikes will be extremely low. BMD systems can prove useful only if deployed to defend against launches of individual ballistic missiles or groups of such missiles. Prioritization of other destabilizing factors—that could affect global and regional stability—merits a separate study or studies. But even without them I can conclude that nuclear terrorism should be placed on top of the list. The threat of nuclear terrorism is real, and a successful nuclear terrorist attack would lead to a radical transformation of the global order. All of the threats on the revised list must become a subject of thorough studies by experts. States need to work hard to forge a common understanding of these threats and develop a strategy to combat them. High risk of agroterror which collapses the economy and food security. Olson, Federal Bureau of Investigation National Academy MA, 2012 [Dean, FBI Law Enforcement Bulletin, “Threats to America’s Economy and Food Supply” http://www.fbi.gov/stats-services/publications/law-enforcement-bulletin/february2012/agroterrorism, accessed 3-23-14, TAP] The United States enjoys a safe, plentiful, and inexpensive food supply. Americans spend only 11 percent of their income on food compared with the global average of 20 to 30 percent.1 The nation’s agricultural abundance helps drive its economic prosperity. As many as 1 of 6 jobs are linked to agriculture, a trillion-dollar industry. Agriculture-related products comprise nearly 10 percent of all U.S. exports, amounting to nearly $68 billion in 2006.2¶ Terrorists consider America’s agriculture and food production tempting targets. They have noticed that its food supply is among the most vulnerable and least protected of all potential targets of attack. When American and allied forces overran al Qaeda sanctuaries in the caves of eastern Afghanistan in 2002, among the thousands of documents they discovered were U.S. agricultural documents and al Qaeda training manuals targeting agriculture.¶ A subset of bioterrorism, agroterrorism is defined as “the deliberate introduction of an animal or plant disease for the purpose of generating fear, causing economic losses, or undermining social stability.”3 It represents a tactic to attack the economic stability of the United States. Killing livestock and plants or contaminating food can help terrorists cause economic crises in the agriculture and food industries. Secondary goals include social unrest and loss of confidence in government.¶ Serious Concern¶ Agroterrorism is not new. The Assyrians poisoned enemy wells with rye ergot during the 6th century B.C. During World War I, German agents in the United States infected horses and cattle in transit across the Atlantic to France. In 1994, in The Dalles, Oregon, a religious cult intentionally contaminated 10 restaurant salad bars with salmonella, sickening more than 750 people in an attempt to influence the outcome of a local election. Since 1912, 12 documented cases have involved the substate use of pathogenic agents to infect livestock or contaminate food.4¶ Terrorist leaders realize that America&rsquo;s strength stems largely from its economic vitality.¶ The agroterrorism threat emanates from four categories of perpetrators. The foremost threat is posed by transnational groups, like al Qaeda—widely believed to present the most probable threat of inflicting economic harm on the United States.¶ The second group is comprised of economic opportunists tempted to manipulate markets. They understand that a foot and mouth disease (FMD) outbreak, for example, would have a dramatic impact on markets. By introducing the virus, they could exploit the markets for personal economic gain. ¶ The third category includes domestic terrorists who may view the introduction of FMD as a blow against the federal government. As an outlier of this category, the unbalanced individual or disgruntled employee may perpetrate an attack for a variety of idiosyncratic or narcissistic motivations.¶ Finally, militant animal rights or environmental activists pose a threat because they consider immoral the use of animals for food. Groups, such as the Animal Liberation Front and its sister organization, the Earth Liberation Front, could view an attack on the animal food industry a positive event.5¶ Threat Environment¶ Because it lacks the drama and spectacle of more common terrorist violence, such as bombings and murders, agroterrorism has remained a secondary consideration, and no documented attacks in the homeland have occurred since 9/11. Several recent factors may have made agroterrorism a more attractive tactic.¶ First, the threat environment has changed dramatically. America has had recent successes against al Qaeda’s leadership. These victories have forced the group to morph in both structure and tactics. The increasingly dangerous environment it now must operate in has prevented it from mounting catastrophic terrorist attacks on the scale of 9/11. Now, al Qaeda places its emphasis on smaller, independent attacks following a “death by a thousand cuts” strategy to exhaust, overwhelm, and distract U.S. Department of Homeland Security forces. The group seeks to flood America’s already information overloaded intelligence systems with myriad threats and “background noise.”6 Agroterrorism also may serve as a way to magnify the social upheaval caused by smaller, independent attacks, like bombings.¶ Second, Usama Bin Ladin consistently had argued that attacking the U.S. economy represented the best way to destroy America’s ability to project military power abroad. Underpinning this view is al Qaeda’s historical narrative that jihad against the Soviets following the invasion of Afghanistan led not only to the defeat of the Red Army but, ultimately, to the demise of the U.S.S.R.7 As divorced from reality as this view seems, economic harm remains one of the pillars of al Qaeda’s terror strategy against the United States. In a video broadcast before the 2004 U.S. presidential elections, Usama Bin Ladin bragged that his organization “…bled Russia for 10 years until it went bankrupt and was forced to withdraw in defeat…. We are continuing in the same policy to make America bleed profusely to the point of bankruptcy….” He boasted that the 9/11 attacks had cost al Qaeda $500,000 while inflicting a staggering $500 billion in economic losses to America.8 According to Bin Ladin, “every dollar of al Qaeda defeated a million dollars [of America]...besides the loss of a huge number of jobs.”¶ Analysts believe that al Qaeda’s evolving tactics increasingly will “focus on targets that will yield the most economic damage .”9 Terrorist leaders realize that America’s strength stems largely from its economic vitality. They pursue an overarching strategy that all attacks should focus on weakening America’s economic strength, especially through protracted guerilla warfare. In their view, as the United States loses its standing in the Middle East, groups, like al Qaeda, can gain ground and remove from power regimes they view as corrupt and illegitimate.10¶ Terrorists know that a successful agroterrorism incident threatens America’s economic welfare and its standing as a leading exporter of agricultural products to the world. A significant disruption in agricultural exports caused by such an attack would have ripple effects in the United States’ and global economies. This economic disruption would occur on three levels.¶ The first involves direct losses due to containment measures, such as stop-movement orders (SMOs) or quarantines of suspected stock. Additional costs would arise from the culling and destruction of disease-ridden livestock.11 Second, indirect multiplier effects, such as compensation to farmers for destruction of agricultural commodities and losses suffered by directly and indirectly related industries, would arise.12 And, third, international costs would result from protective trade embargoes. Less measurable consequences would include the undermining of confidence in and support of government, creation of social panic, and threat to public health on the national and global levels.¶ Given its ease of execution and low cost to high benefit ratio, agroterrorism fits the evolving strategy of al Qaeda that focuses on inexpensive but highly disruptive attacks in lieu of monumental ones. Agroterrorism could exacerbate the social upheaval caused by random bombings. The ability to employ cheap and unsophisticated means to undermine America’s economic base, combined with the added payoff to potentially overwhelm its counterterrorism resources, makes livestock- and food-related attacks increasingly attractive.13¶ Foot and Mouth Disease¶ Attacks directed against the cattle, swine, or poultry industries or via the food chain pose the most serious danger for latent, ongoing effects and general socioeconomic and political disruption. Experts agree that FMD presents the most ominous threat.14 Eradicated in the United States in 1929, FMD remains endemic in South America, Africa, and Asia.15 An especially contagious virus 20 times more infectious than smallpox, FMD causes painful blisters on the tongues, hooves, and teats of cloven-hoofed animals, including cattle, hogs, sheep, goats, and deer, rendering them unable to walk, give milk, eat, or drink. Although people generally cannot contract the disease, they can carry the virus in their lungs for up to 48 hours and transmit it to animals. The animal-to-animal airborne transmission range is 50 miles.16 An infected animal can shred the virus in large quantities from its upper respiratory tract via drooling, coughing, and discharging mucus. Extremely stable, FMD can survive in straw or clothing for 1 month and spread up to 100 kilometers via the wind. Because herds exist as highly crowded populations bred and reared in extremely close proximity to one another, a significant risk exists that such pathogenic agents as FMD will spread well beyond the locus of a specific outbreak before health officials become aware of a problem. An FMD outbreak could spread to as many as 25 states in as little as 5 days simply through the regulated movement of animals from farm to market.17¶ From a tactical perspective, an FMD attack holds appeal for several reasons. First, unlike biological warfare directed against humans, no issue of weaponization exists. In an FMD attack, the animals themselves serve as the primary medium for pathogenic transmission, and countries as close as those in South America offer a ready source of the virus. As one analyst described it, the virus “can be spread by simply wiping the mucus from an infected animal on a handkerchief and then transferring the virus to healthy animals by wiping their noses…by stopping on a highway in rural America and releasing the virus among curious livestock an outbreak could be initiated.”18¶ Second, FMD is nonzoonotic, presenting no risk of accidental human infection. There exists no need for elaborate personal protective equipment or an advanced understanding of animal disease science. In a biowarfare attack targeting people, the deadly pathogen poses a threat to the perpetrators, as well as their intended victims. Preparing the pathogen so that terrorists can handle it safely yet disseminate it effectively to intended victims can prove difficult. For instance, the Aum Shinrikyo sarin gas attacks on the Tokyo subway in 1994 largely failed to kill the number of people intended due to the crude method of dissemination.¶ Third, terrorists could introduce and subsequently disperse the virus throughout the American food production system through multiple carriers, including animals carrying and introducing it into susceptible herds; animals exposed to contraband materials, such as contaminated food, hay, feedstuffs, hides, or biologics; people wearing clothing or using equipment, including tractors and trucks, to transmit the virus to uninfected animals; and contaminated facilities, such as feed yards, sale barns, and trucks that commonly hold or transport susceptible animals.19¶ The same factors that yield inexpensive and plentiful food by promoting maximum production efficiency also make American agricultural systems inherently vulnerable. The highly concentrated and intensive nature of livestock production encourages the rapid spread of contagious pathogens.20 Most dairies house at least 1,500 cows, with the largest facilities containing 10,000. Animals often are born on breeding farms and then transported to another state for slaughtering and processing. Otherwise isolated and widely dispersed farms often share equipment, vehicles, and veterinary instruments. Feedlots and auctions routinely intermingle animals from a wide geographic area. On average, a pound of meat travels 1,000 miles before it reaches the consumer’s table.21¶ The introduction of FMD would require the mass slaughter and disposal of infected animals. An outbreak could halt the domestic and international sale of meat and meat products for years. In this regard, in 2001, FMD in the United Kingdom affected 9,000 farms and required the destruction of more than 4,000,000 animals. Researchers believe that a similar outbreak in the United States would cost taxpayers up to $60 billion.22 An FMD attack could result in massive herd culling, the need to destroy processed goods, and extensive decontamination efforts of production and livestock-containment facilities. Most Americans have not witnessed the intense media coverage of high-volume culling operations involving the destruction and disposal of tens of thousands of animals. Large-scale eradication and disposal of livestock likely would be especially controversial as it affects farmers and ranchers and offends the sensibilities of animal rights activists and environmental organizations.¶ Food Production and Distribution¶ If terrorists strive for human deaths, the food production and distribution chain offers a low-tech but effective mechanism for disseminating toxins and bacteria, such as botulism, E. coli, and salmonella. Developments in the farm-to-table continuum greatly have increased the number of entry points for these agents. Many food processing and packing plants employ large, unscreened seasonal workforces. They commonly operate uneven standards of internal quality and inadequate biosurveillance control to detect adulteration.23 These vulnerabilities, combined with the lack of security at many processing and packing plants, contribute to the ease of perpetrating a food-borne attack.¶ Beyond the economic and political impact, low-tech bioterrorist assaults against the food chain have the potential to create social panic as people lose confidence in the safety of the food supply. A large-scale attack potentially could undermine the public’s confidence in its government. Because most processed food travels to distribution centers within a matter of hours, a single case of chemical or biological adulteration could have significant latent ongoing effects, particularly if the source of the contamination is not immediately apparent and there are acute ailments or deaths.24 Supermarkets in major American cities stock only a 7-day supply of food; therefore, any significant and continuing disruption in supply quickly will lead to severe shortages.¶ Experts believe that fruit- and vegetable-packing plants are among the most vulnerable venues for food-borne attacks. Many represent small-scale manufacturers that specialize in ready-to-eat meats or aggregated foodstuffs. They do not practice uniform biosecurity methods, and they do not use heat, an effective front-end barrier against pathogens, in food processing. Also, because they deal in alreadyprepared produce that does not require cooking—a good back-end defense against microbial introduction—they provide a viable portal to introduce pathogens.¶ Law Enforcement Preparedness¶ Farms, ranches, and feedlots in America are dispersed, open, and generally unprotected. The majority of state and local law enforcement agencies face financial and strategic challenges when responding to agroterrorism, yet the laws of many states treat agroterrorism as a crime investigation, giving local law enforcement agencies primary responsibility.¶ An outbreak of FMD would exhaust law enforcement resources quickly. After recognition of the disease by state agriculture authorities, subsequent steps in the emergency response involve containment and eradication, often involving multiple herds and a large quarantine area that may encompass multiple counties. State agriculture authorities working with the U.S. Department of Agriculture’s Animal and Plant Health Inspection Service have responsibility and authority for animal disease.25 Specially trained animal health officials make decisions on disease control, such as livestock quarantine and the timing and method of livestock depopulation—culling, destroying, and disposing of diseased animals from infected herds by burning or burial.¶ Following strict biosecurity measures can prevent the spread of disease. Local and state law enforcement would play a pivotal role in this effort by adhering to three primary responsibilities. ¶ First, police officials would enforce quarantine orders given by state agriculture authorities. This involves isolating and containing infected stock to prevent the spread of disease. A quarantine area would comprise a 6-mile radius, approximately 113 square miles, surrounding the point of origin; numerous roadblocks would prevent vehicles, equipment, or persons from entering or leaving without detailed decontamination measures and authorization.26 Inside the quarantine area, officials would establish an “exposed zone” in which all cloven-hoofed animals would be destroyed. For effectiveness, quarantine of infected premises and SMOs would have to remain in effect for a minimum of 30 days.27¶ The second responsibility occurs in conjunction with quarantine. Officers would enforce SMOs issued by the state governor to prevent the spread of the disease.28 Initial biosecurity efforts could require placement of all animals under an SMO. Law enforcement may be empowered to restrict human and animal movement in and out of the quarantine zone. This authority would include all animals in transit within a wide geographic area until the investigation clarified the extent of the infection and determined which animals can move safely. Although FMD affects only cloven-hoofed animals, humans, horses, and other animals may carry the virus.¶ Enforcing an SMO would require care and shelter for animals in transit that must be temporarily unloaded and housed at local sites providing feed and water.29 During the SMO, law enforcement would interview drivers to determine points of origin and destinations of animals. Research indicates that officers would stop and evaluate an average of nearly 50 vehicles per hour in the first day of an SMO.¶ Third, the criminal investigation of the outbreak further would tax already strained law enforcement resources. The investigation would focus on identifying the source of the virus and the mechanism used to infect susceptible animals. The danger of additional infections by the perpetrators would make the criminal investigation time sensitive.¶ Many law enforcement agencies lack the sufficient resources and procedures to simultaneously cope with quarantines, SMOs, and criminal investigations while also staffing widely dispersed checkpoints around the clock for the duration of the emergency. When combined with the need also to deliver routine law enforcement services, most agencies would struggle to meet these demands, especially during the protracted nature of an FMD outbreak.¶ Conclusion¶ Agriculture may not represent terrorists’ first choice of targets because it lacks the shock factor of more traditional attacks; however, it comprises the largest single sector in the U.S. economy, making agroterrorism a viable primary aspiration. Such terrorist groups as al Qaeda have made economic and trade disruption key goals. They believe that by imposing economic hardship on America, its citizens will tire of the struggle and force their elected leaders to withdraw from commitments abroad.¶ Every level of the food chain, including farms, feedlots, chemical storage facilities, meatpacking plants, and distribution operations, remains vulnerable to agroterrorism. Because terrorists rely on a lack of preparedness, law enforcement agencies should develop a plan to prevent agroterrorism and minimize the results of an attack. Officers must investigate from an agroterrorism perspective thefts of livestock; a criminal organization may steal animals with the intent of infecting them and placing them back into the population. Thefts of vaccines, medicines, and livestock-related equipment should be of concern and carefully investigated. It also is vital that law enforcement officials forward reports of such incidents to their states’ intelligence-fusion centers, threat-integration centers, or law enforcement intelligence units or networks. Economic collapse leads to global war. Lind, New America Foundation Economic Growth Program Policy Director, 5/11/2010 [Michael, "Will the great recession lead to World War IV?," http://www.salon.com/news/economics/index.html?story=/opinion/feature/2010/05/11/great _recession_world_war_iv] an era of global economic stagnation will help the nationalist and populist right, at the expense of the neoliberal and cosmopolitan/multicultural left. During the Long Depression of the late 19th century, which some historians claim lasted from 1873 to 1896, the nations of the West adopted protectionist measures to promote their industries. Beginning with Bismarck’s Germany, many If history is any guide, countries also adopted social reforms like government pensions and health insurance. These reforms were often favored by the nationalist right, as a way of luring the working class away from the temptations of Marxism and left-liberalism. By and large the strategy worked. When World War I broke out, the working classes and farmers in most countries rallied enthusiastically around their respective flags. The Great Depression of the 1930s similarly led to the rise of one or another version of the authoritarian, nationalist right in Europe. Only in a few societies with deeply established liberal traditions, like the English-speaking countries and Scandinavia, did liberals or liberal conservatives hold on. And Franklin Delano Roosevelt’s New Deal Democratic Party, a coalition that included racist Southerners and traditionalist Catholic immigrants, was not particularly liberal by today’s standards. In both eras of depression, great-power rivalry for resources and markets intensified and ultimately led to a world war. Following World War II, the U.S. sought to avert a repetition of that pattern, by creating a global market secured by a global great-power concert in the form of the Security Council. But the project of economic disarmament and security cooperation broke down almost immediately after 1945 and the split between the Soviets and the Anglo-Americans produced the Cold War. The second attempt at a global market that began after the Cold War may be breaking down now, as the most important economic powers pursue their conflicting national interests. A functioning global market system can work only if its members abandon mercantilism -- the policy of trying to enjoy perpetual trade surpluses, by fair means or foul. However, the nations with the three largest economies after the U.S. -- China, Japan and Germany -- all want to enjoy never-ending merchandise trade surpluses. All three have used "currency mercantilism" to help their export industries, to the detriment of the global economic system. China and Japan, by different methods, have deliberately undervalued their currencies, to help their exports and keep imports out of their markets. Germany accomplished something similar, by persuading its trade partners to give up independent currencies that they were able to revalue for the crippling straitjacket of the euro. The system worked only as long as Americans borrowed to pay for imports from Japan and China, while southern Europeans borrowed to pay for imports from Germany. But the consumers are tapped out and neither Americans nor southern Europeans are in a mood for austerity measures in the middle of a near-depression. Unless the Chinese, Japanese and Germans turn into credit-happy consumer societies the global economy may be in for prolonged stagnation. Instead of changing their ways, however, the surplus This will not end happily. As the oversold promise of free-market globalization fades, countries large and small may turn increasingly toward state capitalism. At countries are denouncing their own customers for their profligacy in buying their goods and insisting that the same customers be penalized by austerity programs. home, this would mean permanent state support of troubled industries like banking and the automobile industries, which all of the major industrial countries have bailed out. In trade, this would mean a retreat from global trade areas toward regional blocs and bilateral deals. Examples include agreements between energy-hungry governments like those of China and Japan and the state-owned oil or natural gas companies of Saudi Arabia and Russia. In a world of diplomatic rivalries among great powers to win contracts with Direct war between great powers seems unlikely, but if the Cold War was World War III, then a cold World War IV resembling Orwell’s shifting coalitions of Eurasia, Eastasia and Oceania in 1984 is all too easy to imagine. state-owned corporations, the distinctions between geoeconomics and geopolitics would erode, with potentially dangerous consequences. Ag collapse causes extinction Lugar, Senate foreign relations committee former member, 2K [Richard, former senator from Indiana, “Calls for a new green revolution to combat global warming and reduce world instability” http://www.unep.org/OurPlanet/imgversn/143/lugar.html, accessed 1-17-13, TAP] In a world confronted by global terrorism, turmoil in the Middle East, burgeoning nuclear threats and other crises, it is easy to lose sight of the long-range challenges. But we do so at our peril. One of the most daunting of them is meeting the world’s need for food and energy in this century. At stake is not only preventing starvation and saving the environment, but also world peace and security. History tells us that states may go to war over access to resources, and that poverty and famine have often bred fanaticism and terrorism. Working to feed the world will minimize factors that contribute to global instability and the proliferation of [WMDs] weapons of mass destruction. With the world population expected to grow from 6 billion people today to 9 billion by mid-century, the demand for affordable food will increase well beyond current international production levels. People in rapidly developing nations will have the means greatly to improve their standard of living and caloric intake. Inevitably, that means eating more meat. This will raise demand for feed grain at the same time that the growing world population will need vastly more basic food to eat. Complicating a solution to this problem is a dynamic that must be better understood in the West: developing countries often use limited arable land to expand cities to house their growing populations. As good land disappears, people destroy timber resources and even rainforests as they try to create more arable land to feed themselves. The long-term environmental consequences could be disastrous for the entire globe. Productivity revolution To meet the expected demand for food over the next 50 years, we in the United States will have to grow roughly three times more food on the land we have. That’s a tall order. My farm in Marion County, Indiana, for example, yields on average 8.3 to 8.6 tonnes of corn per hectare – typical for a farm in central Indiana. To triple our production by 2050, we will have to produce an annual average of 25 tonnes per hectare. Can we possibly boost output that much? Well, it’s been done before. Advances in the use of fertilizer and water, improved machinery and better tilling techniques combined to generate a threefold increase in yields since 1935 – on our farm back then, my dad produced 2.8 to 3 tonnes per hectare. Much US agriculture has seen similar increases. But of course there is no guarantee that we can achieve those results again. Given the urgency of expanding food production to meet world demand, we must invest much more in scientific research and target that money toward projects that promise to have significant national and global impact. For the United States, that will mean a major shift in the way we conduct and fund agricultural science. Fundamental research will generate the innovations that will be necessary to feed the world. The United States can take a leading position in a productivity revolution. And our success at increasing food production may play a decisive humanitarian role in the survival of billions of people and the health of our planet. Internet Freedom Adv – Insert from Old Aff Surveillance undermines US internet credibility – reviving judicial accountability is key. Clement, University of Toronto Faculty of Information professor, 2013 [Andrew, Information Policy Research Program coordinator and Identity, Privacy, and Security Institute co-founder, and PhD in computer science, 3-13-13, “Democratic State Surveillance, Transparency and Trust” http://www.cyberdialogue.ca/2013/03/democratic-state-surveillancetransparency-and-trust-by-andrew-clement/, accessed 7-10-15, TAP] Those of us who believe that democratic governments have a central role to play in multistakeholder cyberspace governance have received in the past few weeks a bracing reminder of both the hazards of this ideal in practice and the importance of broad-based civil society mobilization. Democratic states, while not sufficient for effective internet governance, are necessary parties because no other institutions have yet emerged that combine as well as they do the inclusivity, legitimacy and resources to help manage the internet effectively in the broad public interest. However, when such states violate the democratic principles that they espouse and are built on, they seriously undermine their legitimacy as well as the viability of the internet governance project overall. Two events in February related to state surveillance in North America illustrate such problematic governmental behaviour and point to the importance of transparency for restoring trust in governance processes. On February 26 the U.S. Supreme Court ruled against a group of human rights organizations and journalists seeking to challenge the constitutionality of the warrantless domestic surveillance program that the National Security Agency (NSA) has been conducting since 2001. Earlier that month the Canadian government announced that in light of strong public opposition, it had dropped proposed legislation mandating many of the same controversial internet surveillance features. Far from being isolated events, these cases are just two among a larger set of contentious, on-going governmental attempts to surveil individuals and criminalize many common internet activities that raise disturbing civil liberties issues and provoke popular resistance. Shortly after 9/11, the NSA embarked on what is likely the largest domestic surveillance operation in history . On presidential order but without warrants, court orders or legislative sanction, the NSA installed fibre-optic splitters in the main switching centres of the major telecom carriers, enabling the agency to selectively intercept, store and analyse a large portion of internet communications. We only know of this surveillance dragnet thanks to brave whistleblowers formerly at AT&T (Mark Klein) and the NSA (William E. Binney, Thomas A. Drake, and J. Kirk Wiebe), determined journalists (e.g. James Bamford and Jane Mayer) and the more than 40 court cases filed against the telecommunications carriers and the government (mainly litigated by the American Civil Liberties Association (ACLU) and the Electronic Frontier Foundation (EFF)). While the federal government subsequently acknowledged the existence of the warrantless wiretapping program, it has fought to keep every aspect of it away from public scrutiny. The Foreign Intelligence Surveillance Amendments Act (FISAA) gave retroactive immunity from prosecution to AT&T, Verizon/MCI, BellSouth, Sprint and Cingular, all of which had pending court cases against them. In the cases against it, the federal government has consistently invoked a ‘state secrets’ override that has so far successfully kept all but one of them from going to trial. When FISAA passed in 2008, the ACLU immediately challenged its constitutionality on behalf of a group of journalists and human rights lawyers in Clapper v. Amnesty. The recent Supreme Court decision closed this case by finding that the plaintiffs lacked the standing to bring charges because they couldn’t demonstrate that the NSA had targeted them, nor that they had faced “certainly impending” injury by its surveillance. In other words, the constitutional issues raised by the warrantless wiretapping program have not been addressed and further it appears that they may never be, because no party would be granted standing until they can positively demonstrate they have been its victims. In a Kafkaesque twist, the government has in effect rendered its secret surveillance activities immune from legal challenge and public accountability — a clear undermining of liberal democratic norms to say the least. In Canada, ‘lawful access’ legislation designed to give law enforcement, security agencies (such as the Communications Security Establishment Canada (CSEC), and Canadian Security Intelligence Service (CSIS)) and other branches of government similarly broad surveillance powers has been introduced into Parliament on four occasions since 2005. Each time it died on the order paper without parliamentary debate, until February 2012 when the Conservative government introduced it as Bill C-30 and began actively promoting it. Anticipating this re-introduction a broad coalition of civil liberties and on-line advocacy organizations, academics and privacy commissioners mounted the oppositional Stop Online Spying campaign that included videos, public service announcements, posters, letter writing, screenings, and an on-line petition that eventually garnered over 125,000 signatories. The major concerns highlighted in the campaign included allowing authorities access to internet subscriber information without a warrant, no substantial justification for the additional surveillance and policing powers, a requirement that telecommunications service providers install equipment to enable interception of subscriber communication and no effective reporting or accountability. Evidently to boost its appeal, the government changed the name of the bill on the day of the announcement to “Protecting Children from Internet Predators Act”, but this backfired when the Public Safety Minister, Vic Toews, declared that one could either stand with the government or “with the child pornographers” prowling online. This provoked an immediate storm of protest with a large social media component. Public opinion polls showed a significant drop in public support, from a majority (56% Ipsos-Reid) shortly after re-introduction to just 23% (Postmedia News) a year later. Though with a parliamentary majority the government could have forced this bill through, they deemed the political price too high and on February 11, 2013 declared that they were dropping the legislation. While much of the surveillance covered by the lawful access bill continues quietly under the current privacy legislation and some of the key proposed measures are being re-introduced piecemeal as parts of other legislation, this declaration constituted a surprising victory for civil liberties advocates. This outcome echoes similar campaigns in the US a year earlier around the Stop Online Piracy Act (SOPA) and PROTECT IP Act (PIPA), both of which contained new surveillance measures and appeared set to pass the legislative branch until massive popular opposition forced a dramatic reversal. It remains to be seen whether the Cyber Intelligence Sharing and Protection Act (CISPA), now before Congress with similar surveillance provisions as the Canadian lawful access legislation, will also be turned back by popular opposition. In each of these cases we can see a recurring pattern of lack of transparency of government action in relation to the surveillance and related ‘security’ measures. This lack of transparency is observed in both the process of developing surveillance capabilities and in the substance of their (proposed) enactments. Far from providing a basis for informed public decision making about matters affecting the relationship between state and citizen that is hallmark of democratic societies, we repeatedly witness the marginalization of public involvement at every stage. The familiar invocation of security and protection as taking such precedence over other considerations that it doesn’t merit discussion is wearing thin after more than a decade of exaggerated fears and little evidence of positive results. Both the US and Canadian governments appear to offer as little information as possible about proposed surveillance measures, provide bogus or at best flimsy justifications, avoid opportunities to examine or debate issues, dismiss or close down public discussion when it occurs, and actively resist critical inquiry. In stark contrast to the lack of public consultation, but well in keeping with neo-liberal norms, the leading private sector actors have in each case been heavily involved behind the scene, and at least with the intellectual property legislation, they have been prime movers pushing the state to tighten internet surveillance. When details of state surveillance practices do emerge, they show similar patterns of governmental preemption of citizen rights previously taken for granted. These include fine-grained surveillance of individual on-line behavior, weakening or elimination of conventional norms of judicial oversight such as court orders or search warrants and a lack of mandated reporting, review requirements or other forms of public accountability . Few would disagree that states have a legitimate interest in developing the capacity to intercept communication in the service of national security, law enforcement and protection of vital infrastructure. But when they pursue even legitimate surveillance ends with illegitimate means it invites suspicion and opposition. The recent history of secrecy, over-reach, false claims and unwarranted targeting of individuals and groups unsurprisingly brings hostile responses from those concerned for democratic values. This reaction may make governments even more wary of disclosure, thus fueling the vicious cycle we are witnessing. However, if they were to act more in line with the ideals of openness, transparency and democracy they espouse and insist others respect, they would gain significantly in the forms of trust that are so vital for effective governance . For a start, transparent governments would earn more domestic support for the surveillance they actually do need. In addition, they would gain credibility in the international fora , such as the recent conferences Roger Hurwitz mentions in his blog post, whether making claims for national sovereignty or advancing openness and freedom . The principle of transparency of course needs to apply to other cyberspace actors, in proportion to their power and influence. In particular the large private sector enterprises, notably the telecommunication carriers and equipment vendors, that have so closely colluded with state security agencies across ‘democratic’ as well as authoritarian regimes, would do well to be more transparent. The Transparency Reports that several major internet enterprises, such as Google and Twitter, have begun producing represent a small but promising step in this direction. If all parties to multi-stakeholder forums insisted on greater transparency and led by example, it would contribute significantly to building the necessary trust and confidence while mitigating the ‘fortress’ approach that is so hampering the internet governance discussion. Growing transparency, especially in the area of internet surveillance, is an essential pre-condition for developing global cyberspace governance as a welcoming ‘oasis’ where everyone has a part to play, thereby enriching us all. K 1ac Anti-Blackness Contention The FBI has surveillance authority to commit prejudicial monitoring on the basis of race, religion, and ethnicity. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] In addition to the procedural power given to the NCTC through its amended guidelines, the FBI has been given express surveillance procedural authority through the DIOG . 93Link to the text of the note The new rules were enacted to give agents more latitude as they search for indications of criminal and terrorist activity. 94Link to the text of the note The various FBI surveillance procedures that have been outlined include the ability to observe and collect any form of protected speech by citizens and those residing within the country's jurisdiction. 95Link to the text of the note Furthermore, the FBI has the authority to use religion as a factor when determining whether an individual or group deserves greater scrutiny and monitoring. 96Link to the text of the note Race and ethnicity may be considered as a factor in its national security assessment, as long as it is not the dominant factor for focusing on a particular person. 97Link to the text of the note Another power that has been granted is the authority to retain personal information that has been collected on an individual, even if an assessment does not suggest that an individual is engaged in any wrongdoing. 98Link to the text of the note Perhaps the most daunting new permission that has been granted to the FBI is the ability to monitor domestic individuals and citizens without there being any presupposed suspicion of terrorist or criminal activity. 99Link to the text of the note The manual prohibits "racial profiling" in the national security assessments; however, it allows an assessor to monitor [449] "religious practitioners or religious facilities," 100Link to the text of the note and to identify locations of concentrated ethnic communities. 101Link to the text of the note The FBI, in essence, has the authority to infiltrate lawful and peaceful places of worship, communities and businesses, and take race, religion and ethnicity into account when developing its threat analysis. 102Link to the text of the note The guidelines permitting the use of race, religion, or ethnicity to assess national security threats or criminal activity could result in the unconstitutional and prejudicial monitoring of individuals . 103Link to the text of the note The massive expansion of the surveillance state depended on the perfection of imperial techniques abroad combined with concerns for regulating the market – these two forces combined to result in the racialized surveillance practices that created the era of the New Jim Crow in the Post Civil Rights period. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] The expansion of the surveillance state in the twentieth century was one aspect of a wider penetration of the state into the lives of Americans. Working class struggle had somewhat unexpectedly driven this expansion: the state responded by taking on a mediating role between labor and capital, offering a measure of protection from the ravages of a market economy through Keynesian economics and the creation of a welfare state after the New Deal—albeit one that was underdeveloped compared to Western Europe. State managers sought to stabilize capitalism by imposing a degree of “rationality” on the system through regulating the economy and providing social services, all of which required a greater penetration of the state into civil society.48 In the new era of neoliberal capitalism that began in the 1970s, ruling elites sought to break this social contract, which rested on the premise that, if the working class “played by the rules,” it could see increases in wages and living conditions. From the 1970s onwards, this arrangement was undone. Alongside, there were also the beginnings of a contraction of the social wage of welfare provisions, public housing, education, and healthcare. The end result was growing inequality and a new regime of the one percent. The state responded to the permanent joblessness, ghettoization, and stigmatization that neoliberalism produced among the poor by turning to policies of mass criminalization and incarceration. Thus, the neoliberal onslaught went hand in hand with securitization. As Loïc Wacquant writes, since the civil rights era America has launched into a social and political experiment without precedent or equivalent in the societies of the postwar West: the gradual replacement of a (semi-) welfare state by a police and penal state for which the criminalization of marginality and the punitive containment of dispossessed categories serve as social policy at the lower end of the class and ethnic order .49 The law and order rhetoric that was used to mobilize support for this project of securitization was racially coded, associating Black protest and rebellion with fears of street crime. The possibilities of such an approach had been demonstrated in the 1968 election, when both the Republican candidate Richard Nixon and the independent segregationist George Wallace had made law and order a central theme of their campaigns. It became apparent that Republicans could cleave Southern whites away from the Democratic Party through tough-on-crime rhetoric that played on racial fears. The Southern Strategy, as it would be called, tapped into anxieties among working-class whites that the civil rights reforms of the 1960s would lead to them competing with Blacks for jobs, housing, and schools. With the transformation of the welfare state into a security state, its embedding in everyday life was not undone but diverted to different purposes. Social services were reorganized into instruments of surveillance. Public aid became increasingly conditional on upholding certain behavioral norms that were to be measured and supervised by the state, implying its increasing intrusion into the lives of the poor—culminating in the “workfare” regimes of the Clinton administration.50 In this context, a new model of crime control came into being. In earlier decades, criminologists had focused on the process of rehabilitation; those who committed crimes were to be helped to return to society. While the actual implementation of this policy was uneven, by the 1970s, this model went out of fashion. In its place, a new “preventive” model of crime control became the norm, which was based on gathering information about groups to assess the “risk” they posed. Rather than wait for the perpetrator to commit a crime, risk assessment methods called for new forms of “preventive surveillance,” in which whole groups of people seen as dangerous were subject to observation, identification, and classification.51 The War on Drugs—launched by President Reagan in 1982—dramatically accelerated the process of racial securitization. Michelle Alexander notes that At the time he declared this new war, less than 2 percent of the American public viewed drugs as the most important issue facing the nation. This fact was no deterrent to Reagan, for the drug war from the outset had little to do with public concern about drugs and much to do with public concern about race. By waging a war on drug users and dealers, Reagan made good on his promise to crack down on the racially defined “others”—the undeserving.52 Operation Hammer, carried out by the Los Angeles Police Department in 1988, illustrates how racialized surveillance was central to the War on Drugs. It involved hundreds of officers in combat gear sweeping through the South Central area of the city over a period of several weeks, making 1,453 arrests, mostly for teenage curfew violations, disorderly conduct, and minor traffic offenses. Ninety percent were released without charge but the thousands of young Black people who were stopped and processed in mobile booking centers had their names entered onto the “gang register” database, which soon contained the details of half of the Black youths of Los Angeles. Entry to the database rested on such supposed indicators of gang membership as high-five handshakes and wearing red shoelaces. Officials compared the Black gangs they were supposedly targeting to the National Liberation Front in Vietnam and the “murderous militias of Beirut,” signaling the blurring of boundaries between civilian policing and military force, and between domestic racism and overseas imperialism.53 In the twelve years leading up to 1993, the rate of incarceration of Black Americans tripled,54 establishing the system of mass incarceration that Michelle Alexander refers to as the new Jim Crow.55 And yet those in prison were only a quarter of those subject to supervision by the criminal justice system, with its attendant mechanisms of routine surveillance and “intermediate sanctions,” such as house arrests, boot camps, intensive supervision, day reporting, community service, and electronic tagging. Criminal records databases, which are easily accessible to potential employers, now hold files on around onethird of the adult male population.56 Alice Goffman has written of the ways that mass incarceration is not just a matter of imprisonment itself but also the systems of policing and surveillance that track young Black men and label them as would-be criminals before and after their time in prison. From stops on the street to probation meetings, these systems, she says, have transformed poor Black neighborhoods into communities of suspects and fugitives. A climate of fear and suspicion pervades everyday life, and many residents live with the daily concern that the authorities will seize them and take them away.57 A predictable outcome of such systems of classification and criminalization is the routine racist violence carried out by police forces and the regular occurrences of police killings of Black people, such as Michael Brown in Ferguson, Missouri, on August 9, 2014. Racism is unethical and causes extinction Memmi, Professor Emeritus of Sociology at the University of Paris, 1997 [Albert, RACISM, p. 165] Of course, this is debatable. There are those who think that if one is strong enough, the assault on and oppression of others is permissible. But no one is ever sure of remaining the strongest. One day, perhaps, the roles will be society contains within itself the seeds of its own death. It is probably smarter to treat others with respect so that they treat you with respect. "Recall," says the Bible, "that you were once a stranger in Egypt," which means both that you ought to respect the stranger because you were a stranger yourself and that you risk becoming once again someday. It is an ethical and a practical appeal -- indeed, it is a contract, however implicit it might be. In short, the refusal of racism is the condition for all theoretical and practical morality . reversed. All unjust Public deliberation and informed public involvement over domestic surveillance is shut down now. Clement, University of Toronto Faculty of Information professor, 2013 [Andrew, Information Policy Research Program coordinator and Identity, Privacy, and Security Institute co-founder, and PhD in computer science, 3-13-13, “Democratic State Surveillance, Transparency and Trust” http://www.cyberdialogue.ca/2013/03/democratic-state-surveillancetransparency-and-trust-by-andrew-clement/, accessed 7-10-15, TAP] In each of these cases we can see a recurring pattern of lack of transparency of government action in relation to the surveillance and related ‘security’ measures. This lack of transparency is observed in both the process of developing surveillance capabilities and in the substance of their (proposed) enactments. Far from providing a basis for informed public decision making about matters affecting the relationship between state and citizen that is hallmark of democratic societies, we repeatedly witness the marginalization of public involvement at every stage. The familiar invocation of security and protection as taking such precedence over other considerations that it doesn’t merit discussion is wearing thin after more than a decade of exaggerated fears and little evidence of positive results. Both the US and Canadian governments appear to offer as little information as possible about proposed surveillance measures, provide bogus or at best flimsy justifications, avoid opportunities to examine or debate issues, dismiss or close down public discussion when it occurs, and actively resist critical inquiry . In stark contrast to the lack of public consultation, but well in keeping with neo-liberal norms, the leading private sector actors have in each case been heavily involved behind the scene, and at least with the intellectual property legislation, they have been prime movers pushing the state to tighten internet surveillance. When details of state surveillance practices do emerge, they show similar patterns of governmental preemption of citizen rights previously taken for granted. These include fine-grained surveillance of individual on-line behavior, weakening or elimination of conventional norms of judicial oversight such as court orders or search warrants and a lack of mandated reporting, review requirements or other forms of public accountability . Few would disagree that states have a legitimate interest in developing the capacity to intercept communication in the service of national security, law enforcement and protection of vital infrastructure. But when they pursue even legitimate surveillance ends with illegitimate means it invites suspicion and opposition. The recent history of secrecy, overreach, false claims and unwarranted targeting of individuals and groups unsurprisingly brings hostile responses from those concerned for democratic values. This reaction may make governments even more wary of disclosure, thus fueling the vicious cycle we are witnessing. However, if they were to act more in line with the ideals of openness, transparency and democracy they espouse and insist others respect, they would gain significantly in the forms of trust that are so vital for effective governance. For a start, transparent governments would earn more domestic support for the surveillance they actually do need. In addition, they would gain credibility in the international fora , such as the recent conferences Roger Hurwitz mentions in his blog post, whether making claims for national sovereignty or advancing openness and freedom . The principle of transparency of course needs to apply to other cyberspace actors, in proportion to their power and influence. In particular the large private sector enterprises, notably the telecommunication carriers and equipment vendors, that have so closely colluded with state security agencies across ‘democratic’ as well as authoritarian regimes, would do well to be more transparent. The Transparency Reports that several major internet enterprises, such as Google and Twitter, have begun producing represent a small but promising step in this direction. If all parties to multi-stakeholder forums insisted on greater transparency and led by example, it would contribute significantly to building the necessary trust and confidence while mitigating the ‘fortress’ approach that is so hampering the internet governance discussion. Growing transparency, especially in the area of internet surveillance, is an essential pre-condition for developing global cyberspace governance as a welcoming ‘oasis’ where everyone has a part to play, thereby enriching us all. Informed and active citizens are necessary to challenge the surveillance state. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] Initially, Americans welcomed the heightened security measures; however, as the government's surveillance measures began to increasingly violate domestic civil liberties, American sentiment became wearier of these government measures. 67Link to the text of the note In fact, a new CBS poll found [445] that nearly six in ten Americans said they were very concerned or somewhat concerned about losing privacy because of federal efforts to fight terrorism. 68Link to the text of the note The debate on national security surveillance practices has resulted in the public's awareness and disdain for the government's intrusive practices. Some of this disdain is sparked by the June 2013 information leak by Edward Snowden, a former intelligence agent who leaked to the public highly sensitive intelligence. 69Link to the text of the note He asserted that the public deserved to be aware of the government's intrusive intelligence gathering practices. 70Link to the text of the note In an interview with The Guardian, Snowden stated "'I, sitting at my desk,' … could 'wiretap anyone, from you or your accountant, to a federal judge or even the president, if I had a personal email.'" 71Link to the text of the note This country's well-founded focus of national security has led to a development of policy and laws that create a very fine line between national security and the unrestrained infringement upon civil liberties. Because of responses to Freedom of Information Act requests, the government's surveillance practices are now exposed and shed some light on the inappropriate measures that are being taken in the post-9/11 national security era. 72Link to the text of the note High School Students learning about Surveillance is key to solve war and threatconstruction that justifies atrocities Ralston ’14 (Robert Ralston is a second-year Master's student in the Department of Political Science at Virginia Tech. His research interests broadly include international relations, critical security studies, cyberpolitics, and surveillance. Robert is writing a thesis that examines state ontological insecurity with respect to cyberspace, and how state surveillance practices are justified through narratives of liberty and security, MILTON WOLF SEMINAR, “CYBERSPACE AND SURVEILLANCE: CHALLENGES TO STATE IDENTITY AND ONTOLOGICAL SECURITY IN THE DIGITAL AGE” http://www.global.asc.upenn.edu/app/uploads/2015/04/Milton-Wolf-2014Compendium.pdf#page=41 DA:7/8/15 CB) Increasing state surveillance of the internet and regarding foreign and domestic internet policies a seeming lack of global accountability and best practices demands the attention of students, scholars, and practitioners of media and communication, political science, sociology, computer science, and the like. With these concerns in mind, the 2014 Milton Wolf Seminar highlighted themes of surveillance, visibility, disclosure, and espionage in the digital age. This essay seeks to touch upon some of these themes, and to present a case for the study of ontological security in international relations as a way to explain, in part, U.S. practices of surveillance following the leaks by former National Security Administration (NSA) contractor Edward Snowden. Politically, the stakes are high as cyberpolitics becomes an issue of “high politics” in the study of international relations; states and the agents who produce narratives about the state frame cyber discourse in ways that attempt to justify practices of surveillance, espionage, and censorship. States justify intrusion into cyberspace in the name of stability and an idealized self-image. This, can prove violent and costly, with parallels to justifying war on the basis of empire in offline venues. In cyber venues, the United States in particular has had to justify state intrusion into cyber venues. Void of routinized responses to “traditional” threats, the state must reshape or reconfigure its self-image in order to combat the contradictions inherent in state intrusions into cyberspace. Taking in consideration such concerns and dynamics, this essay first sets out to explain ontological security in the study of international relations and the discursive practices of U.S. state agents in justifying state surveillance practices. It then concludes by drawing parallels between these discursive practices and various presentations at the 2014 Milton Wolf Seminar. Ontological Security in International Relations Theory Physical security concerns dominate realist accounts of security in world politics (Mitzen 2006: 342). Ontological security in international relations goes beyond the premise that states are solely concerned with physical security. The assumption that states only seek physical security, Mitzen (2006: 364) argues, constrains international relations theory by failing to explain why states may seek or continue conflict at the expense of physical security. Inherent in the conception of a state’s ontological security is the notion of the state as person, or at the very least, that states are concerned with their own self-image. 20 Ontological security is about constructing and maintaining the stability of a state’s self-image. Power, in this regard, can be understood in terms 20 See Wendt (2004) for a discussion of the validity and appropriateness of understanding the state as person in international relations theory. 40 of “a centralized body’s internal capacity to perceive its ability to operate upon its own selfimage, as well as influence others and determine outcomes” (Steele 2010: 15). Thus, power is not solely based upon a state’s ability to make other actors do what they would otherwise not do, to pose material threats to other states, or assert global influence; power is about the state’s recognition that it can use and recreate its own self-image. States put forward narratives about themselves through state agents, such as government officials. State actions must be justified, even if they go against the grain of international norms or expectations (Steele 2008: 10). What is particularly interesting about the U.S response to the Snowden disclosures is the manner in which the disclosures were framed, the contradictions that arose as a result of this framing, and how the narratives that the state produced regarding NSA practices harken back to the self-image-making of the U.S. state. Why the United States? When examining speeches made by U.S. state agents, publications regarding U.S. citizenship, and the ways the United States is presented in popular culture, common trends emerge: The United States is presented as exceptional, as a land of shared values-- liberty, freedom, and prosperity—which were created by the nation’s founding fathers. David Campbell (1998: 131) suggests that America is an imagined community “par excellence.” America, like all other states, is dependent upon practices that make up its ontological being. However, as Campbell (1998) argues: Defined, therefore, more by absence than presence, America is peculiarly dependent on representational practices for its being. Arguably more than any other state, the imprecise process of imagination is what constitutes American identity (p. 91). Space and time in reference to U.S. identity is crucial to this analysis because successful fulfillment of ontological state security is predicated upon that state’s ability to maintain a consistent self-identity and self-image. Void of a people as a foundational element, the United States’ self-identity is quite fleeting, and, thus, hinges on representational, symbolic, and iconic imagery in order to ascribe to itself some form of identity (Campbell 1998: 132). The U.S. State Narrative In a speech made prior to Snowden’s disclosures, President Obama spoke of the necessity to secure cyber infrastructure while maintaining the internet as a free and open space: Our pursuit of cybersecurity will not—I repeat, will not include—monitoring private sector networks or Internet traffic. We will preserve and protect the personal privacy and civil liberties that we cherish as Americans. Indeed, I remain firmly committed to net neutrality so we can keep the Internet as it should be—open and free. In light of the Snowden disclosures, a contradiction arises between the actual behavior of the state through its national security agency and the self-image of the state. President Obama sends two distinct and seemingly irreconcilable messages regarding cyberspace: First, the United States, as a centralized power, recognizes the tensions that it must mediate between security and 41 liberty; Second, the United States has a vision for cyberspace, one focused on being “open and free.” But free for whom? U.S. security policy is decentralized insofar as it attempts to do too much while still trying to keep a constant self-image (See Campbell 1998 and Gould and Steele 2014). Cyberspace is not an “American thing,” but from cyberspace comes a multitude of images that only exacerbate the imagined nature of American identity. Thus, what cyberspace is and what cyberspace means, from an American perspective, is inherently American. Addressing the “noise” surrounding the practices of the National Security Administration, President Obama first noted the history of intelligence gathering by the United States: At the dawn of our Republic, a small, secret surveillance committee, born out of the Sons of Liberty, was established in Boston. And the group’s members included Paul Revere. At night, they would patrol the streets, reporting back any signs that the British were preparing raids against America’s early patriots. In order to find footing and precedent in the face of ontological insecurity in cyberspace two rhetorical moves are deployed. First, history is resurfaced and reworked to create a seemingly appropriate metaphor for the present. This history is doused in a patriotic whitewash, whereby particular events are chosen but not others that are perhaps more indicative and relevant to the current situation. Further, the parallels put forward by Obama are not parallels at all; the nature of surveillance, global politics, globalization, and technology are not the same as they were 200 or so years ago. This history serves to maintain the state’s self-image over time. Campbell (1998: 130) notes that the American quasi-war with France “demonstrated how previously established discursive strategies of otherness could be invoked in novel circumstances to provide powerful modes of understanding.” Much in the same way, President Obama’s return to history serves not only to ground justifications for NSA activities in seemingly consistent practices of state surveillance, but also in actions against threats from an “other,” in this case, the British during the Revolutionary War. Threats in cyberspace come from a plethora of sources, including: other states, non-state actors, rogue Americans, or even cyberspace itself. Obama’s second rhetorical move is to argue for American exceptionalism. He goes on to note, But America’s capabilities are unique, and the power of new technologies means that there are fewer and fewer technical constraints on what we can do. That places a special obligation on us to ask tough questions about what we should do. The justification for (at least toned down) policies of NSA surveillance centers on the notion that “someone has to do it,” and “we can do it better than anyone else.” America’s status as “the world’s only superpower,” as President Obama declares, opens itself up for interrogation. At the end of his speech on NSA reforms, President Obama demonstrates, perhaps unintentionally, that ontological insecurity is a powerful motivator for the United States in cyberspace: When you cut through the noise, what’s really at stake is how we remain true to who we are in a world that is remaking itself at dizzying speed. Whether it’s the ability of 42 individuals to communicate ideas, to access information that would have once filled every great library in every country in the world, or to forge bonds with people on the other side of the globe, technology is remaking what is possible for individuals and for institutions and for the international order . This is not to say that the United States consciously and reflexively recognizes its ontological insecurity in its relationship to cyberspace. However, the examples that are raised concerning the dangers of cyberspace—from cyberspace as a mechanism for terrorist mobilization to cyber wars of the future—do not paint an entirely clear picture of what makes cyberspace something truly different in global politics. This shift is not universal, or at least to the same degree, for every state. Cyberspace may provide a vehicle for dissent, organization, etc. for every state, but it burdens states that are fixed in terms of physical security and depend on an idealized self-image. States are pressured into explaining the contradictions that arise as a result of their self-image (freedom, openness, transparence, for example) and state-led intrusions into cyberspace. Foreign Policies of the Internet: Surveillance and Disclosure Revisited The 2014 Milton Wolf Seminar brought to bear, and framed well, this theoretical construction of state ontological security in international relations. In particular, many of the presentations dealt with the critical problematic of the balance that must be struck between state self-interest by way of national security and internet diplomacy, global governance, and transparency. Panelists discussed this problematic in various contexts ranging from state censorship of information, international law, and state sovereignty. The internet, and cyberspace more generally, has very real physical characteristics that are often forgotten in discourses of a “borderless digital world” or the metaphor of the internet as a “cloud.” Indeed, the internet is built upon a physical framework, logical building blocks, and interaction (Choucri 2012); and each of these “layers” carries very real political ramifications. State ontological security in cyberspace, as described above, assumes the structural realities of power in international relations regarding the internet, and seeks to elaborate upon how states, beyond concern for their physical security, come to justify surveillance practices on the internet. In this sense, the Milton Wolf Seminar proved invaluable as practitioners and scholars sought to elaborate upon the role of the internet, censorship, privacy, and surveillance in diverse contexts including the national policies and practices of Russia, South Africa, the United States, China, and Britain. Further, the seminar participants elaborated upon shifting or different physical as well as content-layer considerations that need to be taken into account, such as changing modes of internet use, types of surveillance practices, and statecraft in the digital age. The discussion held over the course of the two-day seminar invoked more questions than answers; analysis of such issues has thus far moved, as one seminar participant described, “glacially” alongside the need for internet governance. Thus, the seminar was both timely and a necessary given the salience of internet security, privacy, and surveillance in international politics, along with the perhaps shifting role of the state, and traditional concepts of international politics: state power, sovereignty, and global governance Domestic surveillance is a necessary starting point – surveillance is a critical facet in the historically contingent construction of race under the neoliberal order of Empire. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] In what follows, we argue that the debate on national security surveillance that has emerged in the United States since the summer of 2013 is woefully inadequate, due to its failure to place questions of race and empire at the center of its analysis. It is racist ideas that form the basis for the ways national security surveillance is organized and deployed, racist fears that are whipped up to legitimize this surveillance to the American public, and the disproportionately targeted racialized groups that have been most effective in making sense of it and organizing opposition. This is as true today as it has been historically: race and state surveillance are intertwined in the history of US capitalism. Likewise, we argue that the history of national security surveillance in the United States is inseparable from the history of US colonialism and empire. The argument is divided into two parts. The first identifies a number of moments in the history of national security surveillance in North America, tracing its imbrication with race, empire, and capital, from the settler-colonial period through to the neoliberal era. Our focus here is on how race as a sociopolitical category is produced and reproduced historically in the United States through systems of surveillance. We show how throughout the history of the United States the systematic collection of information has been interwoven with mechanisms of racial oppression. From Anglo settler-colonialism, the establishment of the plantation system, the post–Civil War reconstruction era, the US conquest of the Philippines, and the emergence of the national security state in the post- World War II era, to neoliberalism in the post-Civil Rights era, racialized surveillance has enabled the consolidation of capital and empire. It is, however, important to note that the production of the racial “other” at these various moments is conjunctural and heterogenous. That is, the racialization of Native Americans, for instance, during the settler-colonial period took different forms from the racialization of African Americans. Further, the dominant construction of Blackness under slavery is different from the construction of Blackness in the neoliberal era; these ideological shifts are the product of specific historic conditions. In short, empire and capital, at various moments, determine who will be targeted by state surveillance, in what ways, and for how long. In the second part, we turn our attention to the current conjuncture in which the politics of the War on Terror shape national security surveillance practices. The intensive surveillance of Muslim Americans has been carried out by a vast security apparatus that has also been used against dissident movements such as Occupy Wall Street and environmental rights activists, who represent a threat to the neoliberal order. This is not new; the process of targeting dissenters has been a constant feature of American history. For instance, the Alien and Sedition Acts of the late 1790s were passed by the Federalist government against the Jeffersonian sympathizers of the French Revolution. The British hanged Nathan Hale because he spied for Washington’s army in the American Revolution. State surveillance regimes have always sought to monitor and penalize a wide range of dissenters, radicals, and revolutionaries. Race was a factor in some but by no means all of these cases. Our focus here is on the production of racialized “others” as security threats and the ways this helps to stabilize capitalist social relations. Further, the current system of mass surveillance of Muslims is analogous to and overlaps with other systems of racialized security surveillance that feed the mass deportation of immigrants under the Obama administration and that disproportionately target African Americans, contributing to their mass incarceration and what Michelle Alexander refers to as the New Jim Crow.4 We argue that racialized groupings are produced in the very act of collecting information about certain groups deemed as “threats” by the national security state—the Brown terrorist, the Black and Brown drug dealer and user, and the immigrant who threatens to steal jobs. We conclude that “security” has become one of the primary means through which racism is ideologically reproduced in the “post-racial,” neoliberal era. Drawing on W. E. B. Dubois’s notion of the “psychological wage,” we argue that neoliberalism has been legitimized in part through racialized notions of security that offer a new “psychological wage” as compensation for the decline of the social wage and its reallocation to “homeland security.” The 1AC is a prerequisite to the alternative – the 1AC posits a critique of the national security state that is a better starting point and explanation for the current manifestations of the impact of the K than the alternative. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] The election of Barack Obama as president in 2008 was said to have ushered in a new “postracial” era, in which racial inequalities were meant to be a thing of the past. African Americans and Muslim Americans placed their hopes in Obama, voting for him in large numbers. But in the so-called post-racial era, the security narrative of hard-working families (coded white) under threat from dangerous racial others has been as powerful as ever. The unprecedented mass deportation of more than two million people during the Obama presidency is one form taken by this post-racial racialized securitization. Over the last two decades, the progressive criminalization of undocumented immigrants has been achieved through the building of a militarized wall between Mexico and the United States, hugely expanding the US border patrol, and programs such as Secure Communities, which enables local police departments to access immigration databases. Secure Communities was introduced in 2008 and stepped up under Obama. It has resulted in migrants being increasingly likely to be profiled, arrested, and imprisoned by local police officers, before being passed to the federal authorities for deportation. Undocumented migrants can no longer have any contact with police officers without risking such outcomes. There is an irony in the way that fears of “illegal immigration” threatening jobs and the public purse have become stand-ins for real anxieties about the neoliberal collapse of the old social contract: the measures that such fears lead to—racialization and criminalization of migrants—themselves serve to strengthen the neoliberal status quo by encouraging a precarious labor market. Capital, after all, does not want to end immigration but to profit from “a vast exploitable labor pool that exists under precarious conditions, that does not enjoy the civil, political and labor rights of citizens and that is disposable through deportation.”66 What brings together these different systems of racial oppression—mass incarceration, mass surveillance, and mass deportation—is a security logic that holds the imperial state as necessary to keeping “American families” (coded white) safe from threats abroad and at home. The ideological work of the last few decades has cultivated not only racial security fears but also an assumption that the security state is necessary to keep “us” safe. In this sense, security has become the new psychological wage to aid the reallocation of the welfare state’s social wage toward homeland security and to win support for empire in the age of neoliberalism. Through the notion of security, social and economic anxieties generated by the unraveling of the Keynesian social compact have been channeled toward the Black or Brown street criminal, welfare recipient, or terrorist . In addition, as Susan Faludi has argued, since 9/11, this homeland in need of security has been symbolized, above all, by the white domestic hearth of the prefeminist fifties, once again threatened by mythical frontier enemies, hidden subversives, and racial aggressors. That this idea of the homeland coincides culturally with “the denigration of capable women, the magnification of manly men, the heightened call for domesticity, the search for and sanctification of helpless girls” points to the ways it is gendered as well as racialized.67 Reformism Contention Radical critiques of the criminal justice system mislocate the proximate cause of racism – reforms are necessary and good from within institutions. - Prison abolition/Rodriguez k alt bad – doesn’t solve racism Perm solves AT: Reform Prisons v Legalize weed Wilkinson, US Court of Appeals 4th Circuit judge, 2014 [J Harvie, former University of Virginia law professor and former DOJ civil rights attorney, Vanderbilt Law Review, “In Defense of American, Criminal Justice” http://www.vanderbiltlawreview.org/content/articles/2014/06/In-Defense-of-AmericanCriminal-Justice.pdf, p.1168-1172, accessed 9-29-14, TAP] One final count in the indictment remains. Can we truly call a system democratic when a very large section of the citizenry—African-Americans—feel oppressed by or excluded from it? Is this a reason to discredit American criminal justice? The reaction to the verdict in the George Zimmerman trial in July 2013—in parts angry, reflective, and resigned—reminded us that many African-Americans feel as though the criminal justice system does not work for them. Washington Post columnist Eugene Robinson argued, “Our society considers young black men to be dangerous, interchangeable, expendable, guilty until proven innocent.”362 Manhattan Institute scholar and New Republic contributor John McWhorter argued that, for African-Americans, “the poisonous relationship between young black men and law enforcement is the prime manifestation of racism in modern America.”363 And President Obama noted that “the African American community is looking at this issue through a set of experiences and history that doesn’t go away,” one wrapped up in “a history of racial disparities in the application of our criminal law.”364 There is something to these criticisms. Americans have tried to address them over the years by requiring objective, race-neutral justifications for government actions within the criminal justice system. We have, for example, required that the jury venire be composed of a fair cross-section of the community,365 and in Batson v. Kentucky,366 the Supreme Court outlawed the use of peremptory challenges of jurors based upon their race. We can insist that objective criteria support stop and frisks. And we can focus on racial discrepancies in criminal-law enforcement—which may lead, for example, to four times as many marijuana arrests for black Americans as white Americans, despite similar rates of use.367 But efforts such as these won’t solve our problems altogether. This is because the story is more complicated than simply a criminal justice system that has failed to win the trust and confidence of many in the African-American community. The problem of racial equality and criminal justice is one of “painful complexity.”368 We can acknowledge that we have not yet reached our goal of race neutrality in the dispensation of justice while acknowledging also that this alone does not account for the racial makeup of our prisons and halfway houses . Then– New York Mayor Michael Bloomberg stated, “Ninety percent of all people killed in our city—and 90 percent of all those who commit the murders and other violent crimes—are black and Hispanic.”369 That is the great double-edged sword. It understandably leads to more stops and more arrests in high-crime areas. It understandably leads to more convictions of those of whatever race who commit the crimes. But it also leads to understandable anger and resentment on the part of disadvantaged young black males who want to make a decent go of American life, only to find themselves the object of recurrent false suspicion and repeated frisks. The solution to the problem of race and criminal justice is not a total overhaul of the system. That just renders the criminal justice system the scapegoat for a much larger set of social problems. The criminal justice system feels the effects of those problems; it does not cause them. Drug and gun crimes are not any less a blight upon society because of the racial makeup of the offenders; indeed, as Robinson noted, “[N]owhere will you find citizens more supportive of tough law-and-order policies than in poor, high-crime neighborhoods.”370 Our criminal justice system rightly aims to reduce dangerous behavior, and the beneficiaries of success in that endeavor may be those less advantaged citizens for whom basic safety will make for greater opportunity, not to mention better prospects for a brighter life. To cast ceaseless blame on America’s criminal justice system is to ignore the enormity of the problems it has been asked to solve. It only diverts attention from the larger ways in which America has failed its underclass. As Michael Gerson recently noted, “The problem of African American boys and young men is a complex mix of lingering racial prejudice, urban economic dislocation, collapsing family structure, failing schools and sick, atomized communities.”371 To chastise criminal justice when many levers of upward mobility are so compromised is an inversion of priorities. A complete “fix” of what the critics allege ails criminal justice will do nothing to restore shattered family structures, improve failing schools, impart necessary job skills, restore religious and community support groups, or provide meaningful alternatives in deprived neighborhoods to the gangs and drug rings that steer young people toward lifelong addictions and lives of crime. Society doesn’t create opportunity by sacrificing the basic social need for order. To the contrary, improvements in communities and institutions will only take root in the kind of safe environment that, at its best, a strong criminal justice system can provide. And when we provide opportunity, we in turn reduce the pressure on the criminal justice system and lessen the monumental task that lack of opportunity for the poorest Americans has left it to perform. How a society chooses to balance justice and safety with rights and liberties will invariably be the subject of vigorous debate. Our criminal justice system is no exception. Many good and intelligent people will disagree passionately about the contours of our criminal law. That is all to the good. We should not grow complacent in both for the sake of individual defendants and for the rule of law itself. the face of particular problems, But instead of engaging in a constructive debate about the American approach to criminal justice, legal elites largely have condemned the entire enterprise. The system, we are told, is broken, and only sweeping reforms imposed from on high can save it. But the rhetoric that fuels the wholesale assault upon the system not only will fail to achieve any meaningful change, it obscures the many strengths of our institutions. By focusing so much on what is wrong, we inevitably forget what is right. The terms of engagement must change. My call is not for scholars to whitewash our system’s failings but to realize the picture is far more nuanced and complex than they have presented it. Given the volume of matters it is asked to address and immensity of the task it is asked to perform, our criminal justice system functions rather well. It is both unrealistic and uncharitable to portray the system as an engine of oppression and injustice. Ironically, many of the features that critics claim operate one-sidedly against defendants often work to their benefit. The American criminal justice system strikes a valuable front-end note. It strikes difficult balances between protecting the innocent and convicting the guilty, between procedural protections and administrative realities. It rightly allows these contestable choices to be made democratically, but only to a point. Such qualities are hardly the hallmarks of a failed system. Indeed, those who have been among the most persistent critics of the criminal justice system were among the first to call for its utilization in the aftermath of the September 11th terrorist attacks.372 And since that time, the refrain has often been that acts of terrorism are crimes that should be dealt with in the customary way through enforcement of federal criminal law.373 I recognize that this plea for criminal trials does not constitute an acknowledgment of the system’s perfection, but it does indicate that the system imparts a legitimacy for the deprivation of liberty that other routes of trying suspected terrorists may lack. This is no place to explore the complicated question of whether alleged terrorism is more aptly regarded as a criminal offense or as an act of war. Separation of powers concerns and the need for action to prevent mass casualties make the question an exceptionally complicated one. I note only the irony that many who reject the considerable virtues of the American criminal justice system are at least prepared to look upon it as a preferred solution when the values of liberty and security are in epochal tension. To be sure, there is plenty of room for reform, and all parts of the legal profession should head for the front lines. But let us not forget our system’s virtues as we seek to correct its vices. Otherwise, any legitimate concerns will be lost in the din of diatribe. We have gone too long without a degree of balance or moderation in our assessment of the American criminal justice system. It is time we gave our institutions a fair trial. Reformism is effective and brings the revolution closer – intellectual idealism is a privileged mode of thought that fails to eradicate racism. Delgado, University of Alabama minority scholar and chair of law, 2009 [Richard, in Arguing about Law, “Does Critical Legal Studies Have What Minorities Want” http://books.google.com/books?id=g75cAgAAQBAJ&pg=PA1&lpg=PA1&dq=arguing+about+law &source=bl&ots=8q7fJpE0h&sig=Y2nyM2lsR2roG3IEFPisRXGs3Q8&hl=en&sa=X&ei=zfooVJrlOo6gyASRmYDwCw&ved= 0CEsQ6AEwBw#v=onepage&q=imperialistic&f=false, p.589-90, accessed 9-29-14, TAP] 2. The CLS critique of piecemeal reform Critical scholars reject the idea of piecemeal reform. Incremental change, they argue, merely postpones the wholesale reformation that must occur to create a decent society. Even worse, an unfair social system survives by using piecemeal reform to disguise and legitimize oppression. Those who control the system weaken resistance by pointing to the occasional concession to, or periodic court victory of, a black plaintiff or worker as evidence that the system is fair and just. In fact, Crits believe that teaching the common law or using the case method in law school is a disguised means of preaching incrementalism and thereby maintaining the current power structure.“ To avoid this, CLS scholars urge law professors to abandon the case method, give up the effort to find rationality and order in the case law, and teach in an unabashedly political fashion. The CLS critique of piecemeal reform is familiar, imperialistic and wrong. Minorities know from bitter experience that occasional court victories do not mean the Promised Land is at hand. The critique is imperialistic in that it tells minorities and other oppressed peoples how they should interpret events affecting them. A court order directing a housing authority to disburse funds for heating in subsidized housing may postpone the revolution, or it may not. In the meantime, the order keeps a number of poor families warm. This may mean more to them than it does to a comfortable academic working in a warm office. It smacks of paternalism to assert that the possibility of revolution later outweighs the certainty of heat now, unless there is evidence for that possibility. The Crits do not offer such evidence. Indeed, some incremental changes may bring revolutionary changes closer, not push them further away. Not all small reforms induce complacency; some may whet the appetite for further combat. The welfare family may hold a tenants‘ union meeting in their heated living room. CLS scholars‘ critique of piecemeal reform often misses these possibilities, and neglects the question of whether total change, when it comes, will be what we want. 3. CLS’ idealism The CLS program is also idealistic.45 CLS scholars’ idealism transforms social reality into a mental construct.46 Facts become intelligible only through the categories of thought that we bring to experience. Crits argue that the principle impediments to achieving an ideal society are intellectual. People are imprisoned by a destructive system of mental categories that blocks any vision of a better world.47 Liberal-capitalist ideology so shackles individuals that they willingly accept a truncated existence and believe it to be the best available. Changing the world requires primarily that we begin to think about it differently.48 To help break the mental chains and clear the way for the creation of a new and better world, Crits practice “trashing” – a process by which law and social structures are shown to be contingent, inconsistent and irrationally supportive of the status quo without good reason.49 CLS scholars’ idealism has a familiar ring to minority ears. We cannot help but be reminded of those fundamentalist preachers who have assured us that our lot will only improve once we “see the light” and are “saved.” Are the chains really mental? They may be so for members of privileged groups. They are much less so for minorities. Imagine that the Crit’s trashing program succeeded and that all laws were repealed. Would our lot improve? That proposition is open to serious doubt. The forces that hold us back are not largely mental, legal, or even political. What holds us back is, simply, racism – the myriad of insults, threats, indifference, and other “microaggressions” to which we are continually exposed.50 Because the Crits are intellectuals, they assign a large role to reason and ideology. Yet reason and ideology do not explain all evil. Telling an individual that he or she harbors racism will not make it go away; telling a black person that a rebuff was racially motivated will not ease its sting. Racism will not go away simply because Crits show that legalisms are indeterminate, that rights are alienating and legitimizing, and that law is a reflection of the interests of the ruling class. Whatever utility these concepts may have in other settings and in attempting to explain the angst of CLS members,51 they have limited application in helping to understand, much less cure, racism. Revolution requires a strategy – reforms pave the way to revolution – creating a dichotomy between reform and revolution fails to cause systemic change. Wray, International Socialist Group, 4-14-14 [Ben, “The case for revolutionary reforms” http://internationalsocialist.org.uk/index.php/2014/04/the-case-for-revolutionary-reforms/, accessed 9-29-14, TAP] But as I’ve discussed in the previous five parts of this series, getting from where we are to a revolutionary transformation that overthrows the dominant property relations of the capitalist economy and replaces them with social relations based on democratic control of the world’s resources is not as simple as declaring our desire for it to be so. I saw a petition on change.org the other day proposing the overthrow of capitalism. If one million people signed that petition and one million people signed a further petition to introduce full collective bargaining rights for trade-unions in the UK, which one would move us closer to the overthrow of capitalism? I wager the latter. Whilst having an end goal in sight is important, most people don’t change their thinking about the world based on bold visions of what could be done at some point in the future: they change their ideas based on evidence from their material lives which points to the inadequacy or irrationality of the status quo. In other words, we need to have ideas that build upon people’s lived experience of capitalism, and since that it is within the framework of a representative democracy system, we need ideas based around proposals for reforms. At the same time those reforms have to help rather than hinder a move to more revolutionary transformation that challenges the very core of the capitalist system. The dialectic of reform and revolution What we need, therefore, is a strategy of revolutionary reforms . Such a notion would appear as a contradiction in terms to many who identify as reformists or revolutionaries and see the two as dichotomous, but there is no reason why this should be the case. Indeed, history has shown that revolutionary transformations have always happened as a dialectical interaction between rapid, revolutionary movements and more institutional, reform-based challenges. Even the revolutionary part of that dialectic has always been motivated by the immediate needs of the participants involved – ‘land, bread and peace’ being the first half of the slogan of the Russian Revolution. What does a strategy of ‘revolutionary reforms’ entail? Ed Rooksby explains that it is a political strategy that builds towards revolutionary change by using reforms to ‘push up against the limits’ of the ‘logic of capitalism’ in practice: “At first these “feasible objectives” will be limited to reforms within capitalism—or at least to measures which, from the standpoint of a more or less reformist working class consciousness, appear to be legitimate and achievable within the system, but which may actually run counter to the logic of capitalism and start to push up against its limits. As the working class engages in struggle, however, the anti-capitalist implications of its needs and aspirations are gradually revealed. At the same time, through its experience of struggle for reform, the working class learns about its capacity for “self-management, initiative and collective decision” and can have a “foretaste of what emancipation means”. In this way struggle for reform helps prepare the class psychologically, ideologically and materially for revolution.” The late Daniel Bensaid expressed this argument through the lens of the history of the socialist movement: “In reality all sides in the controversy agree on the fundamental points inspired by The Coming Catastrophe (Lenin’s pamphlet of the summer of 1917) and the Transitional Programme of the Fourth International (inspired by Trotsky in 1937): the need for transitional demands, the politics of alliances (the united front), the logic of hegemony and on the dialectic (not antinomy) between reform and revolution. We are therefore against the idea of separating an (‘anti-neoliberal’) minimum programme and an (anti-capitalist) ‘maximum’ programme. We remain convinced that a consistent anti-neoliberalism leads to anti-capitalism and that the two are interlinked by the dynamic of struggle.” So revolutionary reforms means a policy agenda that, as Alberto Toscano has put it, “at one and the same time make concrete gains within capitalism which permits further movement against capitalism”. The Italian marxist Antonio Gramsci described this approach as a ‘war of positon’. Racial progress has occurred though legal change and more is still possible – reject monolithic theories of racism because they doom resistance to be selffulfilling and lack empirical validity. Omi, University of California Berkeley ethnic studies professor, and Winant, University of California Santa Barbara sociology professor, 2013 [Michael and Howard, Ethnic and Racial Studies Volume 36, Issue 6, p. 961-973, “Resistance is futile?: a response to Feagin and Elias” Social Text, accessed 9-29-14, TAP] In Feagin and Elias's account, white racist rule in the USA appears unalterable and permanent. There is little sense that the ‘white racial frame’ evoked by systemic racism theory changes in significant ways over historical time. They dismiss important rearrangements and reforms as merely ‘a distraction from more ingrained structural oppressions and deep lying inequalities that continue to define US society’ (Feagin and Elias 2012, p. 21). Feagin and Elias use a concept they call ‘surface flexibility’ to argue that white elites frame racial realities in ways that suggest change, but are merely engineered to reinforce the underlying structure of racial oppression. Feagin and Elias say the phrase ‘racial democracy’ is an oxymoron – a word defined in the dictionary as a figure of speech that combines contradictory terms. If they mean the USA is a contradictory and incomplete democracy in respect to race and racism issues, we agree. If they mean that people of colour have no democratic rights or political power in the USA, we disagree. The USA is a racially despotic country in many ways, but in our also in many respects a racial democracy, capable of being influenced towards more or less inclusive and redistributive economic policies, social policies, or for that matter, imperial policies. What is distinctive about our own epoch in the USA (post-Second World War to the present) with respect to race and view it is racism? Over the past decades there has been a steady drumbeat of efforts to contain and neutralize civil rights, to restrict racial democracy, and to maintain or even increase racial inequality. Racial disparities in different institutional sites – employment, health, education – persist and in many cases have increased. Indeed, the post-2008 period has seen a dramatic increase in racial inequality. The subprime home mortgage crisis, for example, was a major racial event. Black and brown people were disproportionately affected by predatory lending practices; many lost their homes as a result; race-based wealth disparities widened tremendously. It would be easy to conclude, as Feagin and Elias do, that white racial dominance has been continuous and unchanging throughout US history. But such a perspective misses the dramatic twists and turns in racial politics that have occurred since the Second World War and the civil rights era. Feagin and Elias claim that we overly inflate the significance of the changes wrought by the civil rights movement, and that we ‘overlook the serious reversals of racial justice and persistence of huge racial inequalities’ (Feagin and Elias 2012, p. 21) that followed in its wake. We do not. In Racial Formation we wrote about ‘racial reaction’ in a chapter of that name, and elsewhere in the book as well. Feagin and Elias devote little attention to our arguments there; perhaps because they are in substantial agreement with us. While we argue that the right wing was able to ‘rearticulate’ race and racism issues to roll back some of the gains of the civil rights movement, we also believe that there are limits to what the right could achieve in the post-civil rights political landscape. So we agree that the present prospects for racial justice are demoralizing at best. But we do not think that is the whole story. US racial conditions have changed over the post-Second World War period, in ways that Feagin and Elias tend to downplay or neglect. Some of the major reforms of the 1960s have proved irreversible; they have set powerful democratic forces in motion. These racial (trans)formations were the results of unprecedented political mobilizations, led by the black movement, but not confined to blacks alone. Consider the desegregation of the armed forces, as well as key civil rights movement victories of the 1960s: the Voting Rights Act, the Immigration and Naturalization Act (Hart- Celler), as well as important court decisions like Loving v. Virginia that declared anti-miscegenation laws unconstitutional. While we have the greatest respect for the late Derrick Bell, we do not believe that his ‘interest convergence hypothesis’ effectively explains all these developments. How does Lyndon Johnson's famous (and possibly apocryphal) lament upon signing the Civil Rights Act on 2 July 1964 – ‘We have lost the South for a generation’ – count as ‘convergence’? The US racial regime has been transformed in significant ways. As Antonio Gramsci argues, hegemony proceeds through the incorporation of opposition (Gramsci 1971, p. 182). The civil rights reforms can be seen as a classic example of this process; here the US racial regime – under movement pressure – was exercising its hegemony. But Gramsci insists that such reforms – which he calls ‘passive revolutions’ – cannot be merely symbolic if they are to be effective: oppositions must win real gains in the process. Once again, we are in the realm of politics, not absolute rule. So yes, we think there were important if partial victories that shifted the racial state and transformed the significance of race in everyday life. And yes, we think that further victories can take place both on the broad terrain of the state and on the more immediate level of social interaction: in daily interaction, in the human psyche and across civil society . Indeed we have argued that in many ways the most important accomplishment of the anti-racist movement of the 1960s in the USA was the politicization of the social. In the USA and indeed around the globe, race-based movements demanded not only the inclusion of racially defined ‘others’ and the democratization of structurally racist societies, but also the recognition and validation by both the state and civil society of racially-defined experience and identity. These demands broadened and deepened democracy itself. They facilitated not only the democratic gains made in the USA by the black movement and its allies, but also the political advances towards equality, social justice and inclusion accomplished by other ‘new social movements’: secondwave feminism, gay liberation, and the environmentalist and anti-war movements among others. By no means do we think that the post-war movement upsurge was an unmitigated success. Far from it: all the new social movements were subject to the same ‘rearticulation’ (Laclau and Mouffe 2001, p. xii) that produced the racial ideology of ‘colourblindness’ and its variants ; indeed all these movements confronted their mirror images in the mobilizations that arose from the political right to counter them. Yet even their incorporation and containment, even their confrontations with the various ‘backlash’ phenomena of the past few decades, even the need to develop the highly contradictory ideology of ‘colourblindness’, reveal the transformative character of the ‘politicization of the social’ . While it is not possible here to explore so extensive a subject, it is worth noting that it was the long-delayed eruption of racial subjectivity and self-awareness into the mainstream political arena that set off this transformation, shaping both the democratic and antidemocratic social movements that are evident in US politics today. What are the political implications of contemporary racial trends? Feagin and Elias's use of racial categories can be imprecise. This is not their problem alone; anyone writing about race and racism needs to frame terms with care and precision, and we undoubtedly get fuzzy too from time to time. The absence of a careful approach leads to ‘racial lumping’ and essentialisms of various kinds. This imprecision is heightened in polemic. In the Feagin and Elias essay the term ‘whites’ at times refers to all whites, white elites, ‘dominant white actors’ and very exceptionally, anti-racist whites, a category in which we presume they would place themselves. Although the terms ‘black’, ‘African American’ and ‘Latino’ appear, the term ‘people of colour’ is emphasized, often in direct substitution for black reference points. In the USA today it is important not to frame race in a bipolar manner. The black/white paradigm made more sense in the past than it does in the twenty-first century. The racial make-up of the nation has now changed dramatically. Since the passage of the Immigration Reform Act of 1965, the USA has become more ‘coloured’. A ‘majority–minority’ national demographic shift is well underway. Predicted to arrive by the mid-twenty-first century, the numerical eclipse of the white population is already in evidence locally and regionally. In California, for example, non-Hispanic whites constitute only 39.7 per cent of the state's population. While the decline in the white population cannot be correlated with any decline of white racial dominance, the dawning and deepening of racial multipolarity calls into question a sometimes implicit and sometimes explicit black/white racial framework that is evident in Feagin and Elias's essay. Shifting racial demographics and identities also raise general questions of race and racism in new ways that the ‘systemic racism’ approach is not prepared to explain.3 Class questions and issues of panethnicizing trends, for example, call into question what we mean by race, racial identity and race consciousness. No racially defined group is even remotely uniform; groups that we so glibly refer to as Asian American or Latino are particularly heterogeneous. Some have achieved or exceeded socio-economic parity with whites, while others are subject to what we might call ‘engineered poverty’ in sweatshops, dirty and dangerous labour settings, or prisons. Tensions within panethnicized racial groups are notably present, and conflicts between racially defined groups (‘black/brown’ conflict, for example) are evident in both urban and rural settings. A substantial current of social scientific analysis now argues that Asians and Latinos are the ‘new white ethnics’, able to ‘work toward whiteness’4 at least in part, and that the black/white bipolarity retains its distinct and foundational qualities as the mainstay of US racism (Alba and Nee 2005; Perlmann 2005; Portes and Rumbaut 2006; Waters, Ueda and Marrow 2007). We question that argument in light of the massive demographic shifts taking place in the USA . Globalization, climate change and above all neoliberalism on a global scale, all drive migration. The country's economic capacity to absorb enormous numbers of immigrants, low-wage workers and their families (including a new, globally based and very female, servant class) without generating the sort of established subaltern groups we associate with the terms race and racism, may be more limited than it was when the ‘whitening’ of Europeans took place in the nineteenth and twentieth centuries. In other words this argument's key precedent, the absorption of white immigrants ‘of a different color’ (Jacobson 1998), may no longer apply. Indeed, we might think of the assimilationist model itself as a general theory of immigrant incorporation that was based on a historically specific case study – one that might not hold for, or be replicated by, subsequent big waves of immigration. Feagin and Elias's systemic racism model, while offering numerous important insights, does not inform concrete analysis of these issues. It is important going forward to understand how groups are differentially racialized and relatively positioned in the US racial hierarchy: once again racism must be seen as a shifting racial project. This has important consequences, not only with respect to emerging patterns of inequality, but also in regard to the degree of power available to different racial actors to define, shape or contest the existing racial landscape. Attention to such matters is largely absent in Feagin and Elias's account. In their view racially identified groups are located in strict reference to the dominant ‘white racial frame’, hammered into place, so to speak. As a consequence, they fail to examine how racially subordinate groups interact and influence each others’ boundaries, conditions and practices. Because they offer so little specific analysis of Asian American, Latino or Native American racial issues, the reader finds her/himself once again in the land (real or imaginary, depending on your racial politics) of bipolar US racial dynamics, in which whites and blacks play the leading roles, and other racially identified groups – as well as those ambiguously identified, such as Middle Eastern and South Asian Americans (MEASA) – play at best supporting roles, and are sometimes cast as extras or left out of the picture entirely. We still want to acknowledge that blacks have been catching hell and have borne the brunt of the racist reaction of the past several decades. For example, we agree with Feagin and Elias's critique of the reactionary politics of incarceration in the USA. The ‘new Jim Crow’ (Alexander 2012) or even the ‘new slavery’ that the present system practises is something that was just in its beginning stages when we were writing Racial Formation. It is now recognized as a national and indeed global scandal. How is it to be understood? Of course there are substantial debates on this topic, notably about the nature of the ‘prison-industrial complex’ (Davis 2003, p. 3) and the social and cultural effects of mass incarceration along racial lines. But beyond Feagin and Elias's denunciation of the ferocious white racism that is operating here, deeper political implications are worth considering. As Alexander (2012), Mauer (2006), Manza and Uggen (2008) and movement groups like Critical Resistance and the Ella Baker Center argue, the upsurge over recent decades in incarceration rates for black (and brown) men expresses the fear-based, law-and-order appeals that have shaped US racial politics since the rise of Nixonland (Perlstein 2008) and the ‘Southern strategy’. Perhaps even more central, racial repression aims at restricting the increasing impact of voters of colour in a demographically shifting electorate. There is a lot more to say about this, but for the present two key points stand out: first, it is not an area where Feagin and Elias and we have any sharp disagreement, and second, for all the horrors and injustices that the ‘new Jim Crow’ represents, incarceration, profiling and similar practices remain political issues. These practices and policies are not ineluctable and unalterable dimensions of the US racial regime. There have been previous waves of reform in these areas. They can be transformed again by mass mobilization, electoral shifts and so on. In other words, resistance is not futile. Speaking of electoral shifts and the formal political arena, how should President Barack Obama be politically situated in this discussion? How do Feagin and Elias explain Obama? Quite amazingly, his name does not appear in their essay. Is he a mere token, an ‘oreo’, a shill for Wall Street? Or does Obama represent a new development in US politics, a black leader of a mass, multiracial party that for sheer demographic reasons alone might eventually triumph over the white people's party, the Republicans? If the President is neither the white man's token nor Neo, the One,5 then once again we are in the world of politics: neither the near-total white despotism depicted by Feagin and Elias, nor a racially inclusive democracy. President Obama continues to enjoy widespread black support, although it is clear that he has not protected blacks against their greatest cumulative loss of wealth in history. He has not explicitly criticized the glaring racial bias in the US carceral system. He has not intervened in conflicts over workers’ rights – particularly in the public sector where many blacks and other people of colour are concentrated. He has not intervened to halt or slow foreclosures, except in ways that were largely symbolic. Workers and lower-middle-class people were the hardest hit by the great recession and the subprime home mortgage crisis, with black families faring worst, and Latinos close behind (Rugh and Massey 2010); Obama has not defended them. Many writers have explained Obama's centrism and unwillingness to raise the issue of race as functions of white racism (Sugrue 2010). The black community – and other communities of colour as well – remains politically divided. While black folk have taken the hardest blows from the reactionary and racist regime that has mostly dominated US politics since Reagan (if not since Nixon), no united black movement has succeeded the deaths of Malcolm and Martin. Although there is always important political activity underway, a relatively large and fairly conservative black middle class, a ‘black bourgeoisie’ in Frazier's (1957) terms, has generally maintained its position since the end of the civil rights era. Largely based in the public sector, and including a generally centrist business class as well, this stratum has continued to play the role that Frazier – and before him, Charles S. Johnson. William Lloyd Warner, Alison Davis and other scholars – identified: vacillation between the white elite and the black masses. Roughly similar patterns operate in Latino communities as well, where the ‘working towards whiteness’ framework coexists with a substantial amount of exclusion and super-exploitation. Alongside class issues in communities of colour, there are significant gender issues. The disappearance of blue-collar work, combined with the assault by the criminal justice system – chiefly profiling by the police (‘stop and frisk’) and imprisonment, have both unduly targeted and victimized black and brown men, especially youth. Women of colour are also targeted, especially by violence, discrimination and assaults on their reproductive rights (Harris-Perry 2011); profiling is everywhere (Glover 2009). Here again we are in the realm of racial politics. Debate proceeds in the black community on Obama's credibilty, with Cornel West and Tavis Smiley leading the critics. But it seems safe to say that in North Philly, Inglewood or Atlanta's Lakewood section, the president remains highly popular. Latino support for Obama remains high as well. Feagin and Elias need to clarify their views on black and brown political judgement. Is it attuned to political realities or has it been captured by the white racial frame? Is Obama's election of no importance? In conclusion, do Feagin and Elias really believe that white power is so complete, so extensive, so ‘sutured’ (as Laclau and Mouffe might say) as they suggest here? Do they mean to suggest, in Borg-fashion, that ‘resistance is futile?’ This seems to be the underlying political logic of the ‘systemic racism’ approach, perhaps unintentionally so. Is white racism so ubiquitous that no meaningful political challenge can be mounted against it ? Are black and brown folk (yellow and red people, and also others unclassifiable under the alwaysabsurd colour categories) utterly supine, duped, abject, unable to exert any political pressure? Is such a view of race and racism even recognizable in the USA of 2012? And is that a responsible political position to be advocating? Is this what we want to teach our students of colour? Or our white students for that matter? We suspect that if pressed, Feagin and Elias would concur with our judgement that racial conflict, both within (and against) the state and in everyday life, is a fundamentally political process. We think that they would also accept our claim that the ongoing political realities of race provide extensive evidence that people of colour in the USA are not so powerless, and that whites are not so omnipotent, as Feagin and Elias's analysis suggests them to be. Racial formation theory allows us to see that there are contradictions in racial oppression. The racial formation white racism is unstable and constantly challenged, from the national and indeed global level down to the personal and intra-psychic conflicts that we all experience, no matter what our racial identity might be. While racism – largely white – continues to flourish, approach reveals that it is not monolithic . Yes, there have been enormous increases in racial inequality in recent years. But movement-based anti-racist opposition continues, and sometimes scores victories. Challenges to white racism continue both within the state and in civil society . Although largely and properly led by people of colour, anti-racist movements also incorporate whites such as Feagin and Elias themselves. Movements may experience setbacks, the reforms for which they fought may be revealed as inadequate, and indeed their leaders may be co-opted or even eliminated, but racial subjectivity and self-awareness, unresolved and conflictual both within the individual psyche and the body politic, abides. Resistance is not futile . Pessimism fails – it foregoes legitimate reforms, creates defeatism, crushes movements, and results in pursuing simplistic and counter-productive proposals. Kennedy, Harvard University law profeesor, 2012 [Randall, “Race, Crime, and the Law” http://books.google.com/books?id=TE3cE4UnghgC&pg=PA388&lpg=PA388&dq=kennedy,+%22T rue,+it+is+sometimes+genuinely+difficult+to+determine+an+appropriate+remedial+response% 22&source=bl&ots=4eTFbno1dG&sig=yox9NLgt7uA_pAeDhrB7FOPmCzU&hl=en&sa=X&ei=kIop VKuSC81sQTD14CgDQ&ved=0CB4Q6AEwAA#v=onepage&q=kennedy%2C%20%22True%2C%20it%20is% 20sometimes%20genuinely%20difficult%20to%20determine%20an%20appropriate%20remedial %20response%22&f=false, p.388-9, accessed 9-29-14, TAP] True, it is sometimes genuinely difficult to determine an appropriate remedial response. The proper way to address that difficulty, however, is to acknowledge and grapple with it, not bury it beneath unbelievable assertions that, in fact, no real problem exists. Whitewashing racial wrongs (especially while simultaneously proclaiming that courts are doing everything reasonably possible to combat racially invidious government action) corrupts officials and jades onlookers, nourishing simplistic, despairing, and defeatist critiques of the law that are profoundly destructive. The second impression that I want to leave with readers should serve as an antidote to these overwrought, defeatist critiques by acknowledging that the administration of criminal law has changed substantially for the better over the past half century and that there is reason to believe that, properly guided, it can be improved even more. Today there are more formal and informal protections against racial bias than ever before, both in terms of the protections accorded to blacks against criminality and the treatment accorded to black suspects, defendants, and convicts. That deficiencies, large deficiencies, remain is clear. But comparing racial policies today to those that prevailed in 1940 or 1960 or even 1980 should expose the fallacy of asserting that nothing substantial has been changed for the better. This point is worth stressing because of the prevalence and prominence of pessimistic thinking about the race question in American life. Some commentators maintain, in all seriousness, that there has been no significant improvement in the overall fortunes of black Americans during the past half century, that advances that appear to have been made are merely cosmetic, and that the United States is doomed to remain a pigmentocracy. This pessimistic strain often turns paranoid and apocalyptic in commentary about the administration of criminal law. It is profoundly misleading, however, to focus exclusively on the ugliest aspects of the American legal order. Doing so conceals real achievements: the Reconstruction Constitutional Amendments, the Reconstruction civil rights laws, Strauder v. Alabama, Dempsey v. Moore, Brown v. Mississippi, Powell v. Alabama, Norris v. Alabama, Batson v. Kentucky, the resuscitation of Reconstruction by the civil rights movement, the changing demographics of the bench, bar, and police departments—in sum, the stigmatization (albeit incomplete) of invidious racial bias. Neglecting these achievements robs them of support. Recent sharp attacks upon basic guarantees bequeathed by the New Deal ought to put everyone on notice of the perils of permitting social accomplishments to lose one-dimensional condemnations of the racial situation in America renders attractive certain subversive proposals that are, given actual conditions, foolish, counterproductive , and immoral. I think here in particular of the call for racially selective jury their rightful stature in the public's estimation. Moreover, nullification. Such proposals should be openly challenged on the grounds that they fundamentally misperceive the racial realities of American life. The law is problematic but it is a lived reality –the only effective method is redeploying institutional logic against itself. Crenshaw, University of California Los Angeles law professor, 1988 [Kimberle, Harvard law review, “RACE, REFORM, AND RETRENCHMENT: TRANSFORMATION AND LEGITIMATION IN ANTIDISCRIMINATION LAW” http://www.jstor.org/stable/pdfplus/1341398.pdf?acceptTC=true&jpdConfirm=true, JSTOR, p.1366-8, accessed 9-29-14, TAP] The Critics' product is of limited utility to Blacks in its present form. The implications for Blacks of trashing liberal legal ideology are troubling, even though it may be proper to assail belief structures that obscure liberating possibilities. Trashing legal ideology seems to tell us repeatedly what has already been established -- that legal discourse is unstable and relatively indeterminate. Furthermore, trashing offers no idea of how to avoid the negative consequences of engaging in reformist discourse or how to work around such consequences. Even if we imagine the wrong world when we think in terms of legal discourse, we must nevertheless exist in a present world where legal protection has at times been a blessing -- albeit a mixed one . The fundamental problem is that, although Critics criticize law because it functions to legitimate existing institutional arrangements, it is precisely this legitimating function that has made law receptive to certain demands in this area. The Critical emphasis on deconstruction as the vehicle for liberation leads to the conclusion that engaging in legal discourse should be avoided because it reinforces not only the discourse itself but also the society and the world that it embodies. Yet Critics offer little beyond this observation. Their focus on delegitimating rights rhetoric seems to suggest that, once rights rhetoric has been discarded, there exists a more productive strategy for change, one which does not reinforce existing patterns of domination. Unfortunately, no such strategy has yet been articulated, and it is difficult to imagine that racial minorities will ever be able to discover one. As Frances Fox Piven and Richard Cloward point out in their [*1367] excellent account of the civil rights movement, popular struggles are a reflection of institutionally determined logic and a People can only demand change in ways that reflect the logic of the institutions that they are challenging. 138 Demands for change that do not reflect the challenge to that logic. 137 institutional logic -- that is, demands that do not engage and subsequently reinforce the dominant ideology -- will probably be ineffective . 139 The possibility for ideological change is created through the very process of legitimation, which is triggered by crisis. Powerless people can sometimes trigger such a crisis by challenging an institution internally, that is, by using its own logic against it. 140 Such crisis occurs when powerless people force open and politicize a contradiction between the dominant ideology and their reality. The political consequences [*1368] of maintaining the contradictions may sometimes force an adjustment -- an attempt to close the gap or to make things appear fair. 141 Yet, because the adjustment is triggered by the political consequences of the contradiction, circumstances will be adjusted only to the extent necessary to close the apparent contradiction. This approach to understanding legitimation and change is applicable to the civil rights movement. Because Blacks were challenging their exclusion from political society, the only claims that were likely to achieve recognition were those that reflected American society's institutional logic: legal rights ideology. Articulating their formal demands through legal rights ideology, civil rights protestors exposed a series of contradictions -- the most important being the promised privileges of American citizenship and the practice of absolute racial subordination. Rather than using the contradictions to suggest that American citizenship was itself illegitimate or false, civil rights protestors proceeded as if American citizenship were real, and demanded to exercise the “rights” that citizenship entailed. By seeking to restructure reality to reflect American mythology, Blacks relied upon and ultimately benefited from politically inspired efforts to resolve the contradictions by granting formal rights. Although it is the need to maintain legitimacy that presents powerless groups with the opportunity to wrest concessions from the dominant order, it is the very accomplishment of legitimacy that forecloses greater possibilities. In sum, the potential for change is both created and limited by legitimation . Institutional macropolitical policy engagement is vital to solve – any alternative results in failure to actualize change, cooption, and moot activism Lobel, University of San Diego assistant law professor, 2007 [Orly, Harvard law review, “THE PARADOX OF EXTRALEGAL ACTIVISM: CRITICAL LEGAL CONSCIOUSNESS AND TRANSFORMATIVE POLITICS” http://cdn.harvardlawreview.org/wpcontent/uploads/pdfs/lobel.pdf, p.983-7, accessed 9-29-14, TAP] Both the practical failures and the fallacy of rigid boundaries generated by extralegal activism rhetoric permit us to broaden our inquiry to the underlying assumptions of current proposals regarding transformative politics — that is, attempts to produce meaningful changes in the political and socioeconomic landscapes. The suggested alternatives produce a new image of social and political action. This vision rejects a shared theory of social reform, rejects formal programmatic agendas, and embraces a multiplicity of forms and practices. Thus, it is described in such terms as a plan of no plan,211 “a project of pro-jects,”212 “anti-theory theory,”213 politics rather than goals,214 presence rather than power,215 “practice over theory,”216 and chaos and openness over order and formality. As a result, the contemporary message rarely includes a comprehensive vision of common social claims, but rather engages in the description of fragmented efforts. As Professor Joel Handler argues, the commonality of struggle and social vision that existed during the civil rights movement has disappeared.217 There is no unifying discourse or set of values, but rather an aversion to any metanarrative and a resignation from theory. Professor Handler warns that this move away from grand narratives is selfdefeating precisely because only certain parts of the political spectrum have accepted this new stance: “[T]he opposition is not playing that game . . . . [E]veryone else is operating as if there were Grand Narratives . . . .”218 Intertwined with the resignation from law and policy, the new bromide of “neither left nor right” has become axiomatic only for some.219 The contemporary critical legal consciousness informs the scholarship of those who are interested in progressive social activism, but less so that of those who are interested, for example, in a more competitive securities market. Indeed, an interesting recent development has been the rise of “conservative public interest lawyer[ing].”220 Although “public interest law” was originally associated exclusively with liberal projects, in the past three decades conservative advocacy groups have rapidly grown both in number and in their vigorous use of traditional legal strategies to promote their causes.221 This growth in conservative ad-vocacy is particularly salient in juxtaposition to the decline of traditional progressive advocacy. Most recently, some thinkers have even suggested that there may be “something inherent in the left’s conception of social change — focused as it is on participation and empowerment — that produces a unique distrust of legal expertise.”222 Once again, this conclusion reveals flaws parallel to the original disenchantment with legal reform. Although the new extralegal frames present themselves as apt alternatives to legal reform models and as capable of producing significant changes to the social map, in practice they generate very limited improvement in existing social arrangements. Most strikingly, the cooptation effect here can be explained in terms of the most profound risk of the typology — that of legitimation. The common pattern of extralegal scholarship is to describe an inherent instability in dominant structures by pointing , for example, to grassroots strategies,223 and then to assume that specific instances of counterhegemonic activities translate into a more complete transformation. This celebration of multiple microresistances seems to rely on an aggregate approach — an idea that the multiplication of practices will evolve into something substantial. In fact , the myth of engagement obscures the actual lack of change being produced, while the broader pattern of equating extralegal activism with social reform produces a false belief in the potential of change. There are few instances of meaningful reordering of social and economic arrangements and macroredistribution . Scholars write about decoding what is really happening, as though the scholarly narrative has the power to unpack more than the actual conventional experience will admit.224 Unrelated efforts become related and part of a whole through mere reframing. At the same time, the elephant in the room — the rising level of economic inequality — is left unaddressed and comes to be understood as natural and inevitable.225 This is precisely the problematic process that critical theorists decry as losers’ self-mystification, through which marginalized groups come to see systemic losses as the product of their own actions and thereby begin to focus on minor achievements as representing the boundaries of their willed reality. The explorations of micro-instances of activism are often fundamentally performative, obscuring the distance between the descriptive and the prescriptive. The manifestations of extralegal activism — the law and organizing model; the proliferation of informal, soft norms and norm-generating actors; and the celebrated, separate nongovernmental sphere of action — all produce a fantasy that change can be brought about through small-scale, decentralized transformation. The emphasis is local, but the locality is described as a microcosm of the whole and the audience is national and global. In the context of the humanities, Professor Carol Greenhouse poses a comparable challenge to ethnographic studies from the 1990s, which utilized the genres of narrative and community studies, the latter including works on American cities and neighborhoods in trouble.226 The aspiration of these genres was that each individual story could translate into a “time of the nation” body of knowledge and motivation.227 In contemporary legal thought, a corresponding gap opens between the local scale and the larger, translocal one. In reality, although there has been a recent proliferation of associations and grassroots groups, few new local-state-national federations have emerged in the United States since the 1960s and 1970s, and many of the existing voluntary federations that flourished in the mid-twentieth century are in decline.228 There is, therefore, an absence of links between the local and the national, an absent intermediate public sphere, which has been termed “the missing middle” by Professor Theda Skocpol.229 New social movements have for the most part failed in sustaining coalitions or producing significant institutional change through grassroots activism. Professor Handler concludes that this failure is due in part to the ideas of contingency, pluralism, and localism that are so embedded in current activism.230 Is the focus on small-scale dynamics simply an evasion of the need to engage in broader substantive debate? It is important for next-generation progressive legal scholars, while maintaining a critical legal consciousness, to recognize that not all extralegal associational life is transformative. We must differentiate, for example, between inward-looking groups, which tend to be self-regarding and depoliticized, and social movements that participate in political activities, engage the public debate, and aim to challenge and reform existing realities.231 We must differentiate between professional associations and more inclusive forms of institutions that act as trustees for larger segments of the community.232 As described above, extralegal activism tends to operate on a more divided and hence a smaller scale than earlier social movements, which had national reform agendas. Consequently, within critical discourse there is a need to recognize the limited capacity of small-scale action. We should question the narrative that imagines consciousness-raising as directly translating into action and action as directly translating into change. Certainly not every cultural description is political. Indeed, it is questionable whether forms of activism that are opposed to programmatic reconstruction of a social agenda should even be understood as social movements. In fact, when groups are situated in opposition to any form of institutionalized power, they may be simply mirroring what they are fighting against and merely producing moot activism that settles for what seems possible within the narrow space that is left in a rising convergence of ideologies. The original vision is consequently coopted, and contemporary discontent is legitimated through a process of self-mystification. Aff Solvency Solvency – General Plan solves. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] The grant of surveillance power to monitor individuals without suspicion of criminal or terrorist activity and the ability to collect personal information from various sources on the basis of race or ethnicity has resulted in the discrimination of domestic individuals who belong to a particular racial or ethnic group. This discrimination is generated through a disparate impact that the new government surveillance authority has on various ethnic and religious groups, specifically those that are Arab, South Asian, or practitioners of the Islamic religion. Through a balancing test of five factors established through Supreme Court jurisprudence, it is apparent that there is sufficient indirect evidence of the government's intent to discriminate. Because there is an established intent to discriminate, the new government surveillance authority and procedures can only be constitutionally upheld if the acts are narrowly tailored to a compelling government interest. The compelling state interest is satisfied through the goal of nationally security; however, the narrowly tailored prong fails because of the monitoring system's over-inclusiveness. Therefore, the government national security surveillance authority and procedures, via the NCTC amendments and DIOG guidelines, are in violation of the Fourteenth Amendment's Equal Protection Clause. Solvency – 14th Amendment Surveillance targets religious, ethnic, and racial minorities disproportionately which violates the Equal Protection Clause of the 14th Amendment. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] Picture this: you live in a society in which the government is allowed to partake in intrusive surveillance measures without the institutionalized checks and balances upon which the government was founded. In this society, the government pursues citizens who belong to a particular race or ethnicity, practice a certain religion, or have affiliations with specific interest groups. Individuals who have these characteristics are subject to surreptitious monitoring, which includes undercover government officials disguising themselves as community members in order to attend various community events and programs. The government may also place these individuals on watch lists, even where there is no evidence of wrongdoing. These watch lists classify domestic individuals as potential or suspected terrorists and facilitate the monitoring of their personal activity through various law enforcement agencies for an extended period of time. This "hypothetical" society is not hypothetical at all; in fact, it is the current state of American surveillance. The government's domestic spying activities have progressed to intrusive levels, primarily due to an increased fear of terrorism. 1Link to the text of the note This fear has resulted in governmental intelligence efforts that are focused on political activists, racial and religious minorities, and immigrants. 2Link to the text of the note [435] The government's domestic surveillance efforts are not only geared toward suspected terrorists and those partaking in criminal activity, but reach any innocent, non-criminal, non-terrorist national, all in the name of national security. The government's power to engage in suspicionless surveillance and track innocent citizens' sensitive information has been granted through the creation and revision of the National Counterterrorism Center 3Link to the text of the note and the FBI's (Federal Bureau of Investigation) Domestic Investigations and Operations Guide. 4Link to the text of the note The grant of surveillance power has resulted in many opponents, including those within the current presidential administration, who challenge the order for numerous reasons. 5Link to the text of the note These reasons include the inefficiency of storing citizens' random personal information for extended periods of time, 6Link to the text of the note the broad unprecedented authority granted to this body of government without proper approval from Congress, 7Link to the text of the note and the constitutional violations due to the deprivation of citizens' rights. 8Link to the text of the note [436] This Comment argues that the wide-sweeping surveillance authority granted to the government results in a violation of the Fourteenth Amendment's Equal Protection Clause due to far-reaching domestic monitoring practices. Surveillance practices, such as posing as members of the community and placing individuals on watch lists without suspicion of terrorist activity, result in the impermissible monitoring of individuals on the basis of their race or ethnicity. These practices, although done in the name of national security, an established compelling government interest, violate the Equal Protection Clause of the Fourteenth Amendment because they are not narrowly tailored to the stated interest. The procedures are not narrowly tailored to the interest of national security because of the over-inclusiveness of the measures. K Advs – Solvency K Adv – Public Key As we continue to accept government surveillance, they are able to continue <Zach Beauchamp writer for Thinkprogress.org, contributed at Newsweek and the daily beast. He has also written for other foreign policy magazines. Has BAs in philosophy and political science from Brown University and a M.Sc in international relations form the London School of economics June 7th 2013 http://thinkprogress.org/justice/2013/06/07/2120141/why-the-nsas-secret-online-surveillance-should-scare-you/ “Why the NSA’s secret online surveillance should scare you” Accessed 7-8-2015 PAM> That second reaction illustrates precisely why this program is so troubling. The more we accept perpetual government and corporate surveillance as the norm, the more we change our actions and behavior to fit that expectation — subtly but inexorably corrupting the liberal ideal that each person should be free to live life as they choose without fear of anyone else interfering with it. Put differently, George Orwell isn’t who you should be reading to understand the dangers inherent to the NSA’s dragnet. You’d be better off turning to famous French social theorist Michel Foucault. Currently the government is unwilling to pass any more surveillance reform, leaving it up to us <Grant Gross covers news in technology policy in the government for IDG news services June 5th 2015 http://www.fastcoexist.com/3019312/heres-an-idea/could-a-new-privacy-generation-change-our-surveillancepolitics “Could a New "Privacy Generation" Change Our Surveillance Politics?” Accessed 7-8-2015 PAM> The Senate this week passed the USA Freedom Act, which aims to end the NSA's mass collection of domestic phone records, and President Barack Obama signed the bill hours later. After that action, expect Republican leaders in both the Senate and the House of Representatives to resist further calls for surveillance reform. That resistance is at odds with many rank-and-file lawmakers, including many House Republicans, who want to further limit NSA programs brought to light by former agency contractor Edward Snowden. Civil liberties groups and privacy advocates also promise to push for more changes. It may be difficult to get "broad, sweeping reform" through Congress, but many lawmakers seem ready to push for more changes, said Adam Eisgrau, managing director of the office of government relations for the American Library Association. --- People are willing to get involved. Recent polls prove <Stan Alcorn multi-media journalist based in New York City. Frequently reports for WNYC and NPR. October 9th 2013 http://www.fastcoexist.com/3019312/heres-an-idea/could-a-new-privacy-generation-change-oursurveillance-politics “Could A New "Privacy Generation" Change Our Surveillance Politics?” Accessed 7-8-2015 PAM> In a recent poll conducted at the Center for Public Opinion at the University of MassachusettsLowell, we asked a series of questions about people’s willingness to trade privacy for security or vice versa. Across a series of questions, we find that people under 40 are extremely concerned about privacy issues and willing to sacrifice their safety to keep their lives away from the eyes and ears of government monitors, but that those over 40 are far more likely to trade their privacy for security. The fact that younger people are more apt to be anti-surveillance state may not contradict the conventional wisdom of the Internet as much as it (apparently) does that of political scientists. But whether or not its catalyst is 9/11, the generational divide does seem to suggest that the way our politicians balance privacy and security will shift as the under-40s take control. The arc of history is long, but it bends toward the youngs. --- Uniqueness – Racial Targeting Now Domestic surveillance is inherently racist. Mass surveillance will inevitably target marginalized communities of color. Khalek ‘13 Khalek, Rania Rania Khalek is an independent journalist reporting on the underclass and marginalized. In addition to her work for Truthout, she's written for Extra, The Nation, Al Jazeera America, the Electronic Intifada and more. October 30 2013.Activists of Color Lead Charge Against Surveillance, NSA http://www.truth-out.org/news/item/19695-activists-of-color-atforefront-of-anti-nsa-movement. July 8, 2015 Steven Renderos, national organizer for the Center for Media Justice, who helped put together the panel, told Truthout that examining the legacy of surveillance in communities of color could help lead to solutions. "It's critical to understand the history so we can learn how to dismantle it," Renderos said. "Those of us from marginalized communities grew up in environments very much shaped by surveillance, which has been utilized to ramp up the criminal justice system and increase deportations," Renderos said. "It's having real consequences in our communities where children are growing up without parents in the home and families are being torn apart through raids and deportations, a lot of which is facilitated through the use of surveillance. "Panelist Fahd Ahmed, legal and policy director for the South Asian-led social justice organization Desis Rising Up and Moving, argued that mass surveillance is the predictable outgrowth of programs that have targeted marginalized communities for decades. "Just by the very nature of [the United States] being a settler-colonialist and capitalist nation, race and social control are central to its project," Ahmed said. "Anytime we see any levels of policing - whether it's day-to-day policing in the streets, surveillance by the police or internet surveillance - social control, particularly of those that resist the existing system, becomes an inherent part of that system. "But, he warned, "These policies are not going to be limited to one particular community. They're going to continue to expand further and further" because "the surveillance has a purpose, which is to exert the power of the state and control the potential for dissent."Seema Sadanandan, program director for ACLU DC, acknowledged the collective resentment felt by people of color who are understandably frustrated that privacy violations are only now eliciting mass public outrage when communities of color have been under aggressive surveillance for decades. "The Snowden revelations represent a terrifying moment for white, middle-class and upper-middle-class people in this country, who on some level believe that the Bill of Rights and Constitution were protecting their everyday lives," Sadanandan said. "For people of color from communities with a history of discrimination and economic oppression that prevents one from realizing any of those rights on a day-to-day basis, it wasn't a huge surprise. "But Sadanandan argued that NSA surveillance still "has particular concerns for communities of color because of their unique relationship to the criminal justice or social control system, a billion-dollar industry with regard to, for example, border patrol or data mining as it's applied to racially profile." Sadanandan warned that NSA surveillance more than likely would strengthen that system of control. The Black community is racially targeted by domestic surveillance. Targeted surveillance is a form of anti-black violence. Cyril ’15 Cyril, Malkia A.- Malkia Amala Cyril is founder and executive director of the Center for Media Justice (CMJ) and cofounder of the Media Action Grassroots Network, a national network of 175 organizations working to ensure media access, rights, and representation for marginalized communities. April 15 2015 “Black America’s State of Surveillance” http://www.progressive.org/news/2015/03/188074/black-americas-state-surveillance. July 7, 2015 government surveillance is laser-focused on the revelations by Edward Snowden that millions of Americans were being spied on by the NSA. Yet my mother’s visit from the FBI reminds me that, from the slave pass system to laws that deputized white civilians as enforcers of Jim Crow, black people and other people of color have lived for centuries with surveillance practices aimed at maintaining a racial hierarchy. It’s time for journalists to tell a new story that does not start the clock Today, media reporting on when privileged classes learn they are targets of surveillance. We need to understand that data has historically been overused to repress dissidence, monitor perceived criminality, and perpetually maintain an impoverished underclass. In an era of big data, the Internet has increased the speed and secrecy of data collection. Thanks to new surveillance technologies, law enforcement agencies are now able to collect massive amounts of indiscriminate data. Yet legal protections and policies have not caught up to this technological advance. Concerned advocates see mass surveillance as the problem and protecting privacy as the goal. Targeted surveillance is an obvious answer—it may be discriminatory, but it helps protect the privacy perceived as an earned privilege of the inherently innocent. The trouble is, targeted surveillance frequently includes the indiscriminate collection of the private data of people targeted by race but not involved in any crime. For targeted communities, there is little to no expectation of privacy from government or corporate surveillance. Instead, we are watched, either as criminals or as consumers. We do not expect policies to protect us. Instead, we’ve birthed a complex and coded culture— from jazz to spoken dialects—in order to navigate a world in which spying, from AT&T and Walmart to public benefits programs and beat cops on the block, is as much a part of our built environment as the streets covered in our blood. The violence of anti-blackness subjugates black existence. The only way to solve is acknowledging the violence and recognizing the Black identity within civil society. R.L ‘13 R.L. R.L. is an informal theorist working on the problematic of racialised identities, gender and communisation theory. June 5, 2013. WANDERINGS OF THE SLAVE: BLACK LIFE AND SOCIAL DEATH. http://www.metamute.org/editorial/articles/wanderings-slave-black-life-and-social-death. July 8, 2015. This gratuitous violence, on the one hand, subjugates black existence to an irrational accumulation of bodies, and subsequently produces a condensed delimitation of blackness in space. Whether it was the owning and trading of slaves or the contemporary phenomena of the ghetto and mass incarceration, black existence is excluded and stockpiled as so many objects within a spatial boundary. In this condition, life is reduced to a statistical quantity, black existence is made exchangeable with any other. Therefore, on the other hand, black existence is also a fungible object, infinitely malleable in its content due to the abstraction of its quality and open for use for anyone who can claim subjecthood.11 These structural features come to their fullest expression in the contemporary scenario of police shootings. The endless stream of young black men shot by police borders on excess, demonstrating the pure interchangeability of such names as equivalents, meaning that such seemingly particular empirical cases are in actuality a general condition. Blackness is as devalued as it is susceptible to all aspects of material and social containment, control and debility. Yet, in these instances, even morally indignant liberals are complicit with anti-blackness by focusing on police shootings as a contingent rather than structural feature of black existence. Often such moral indignation emphasises the atrocious nature of such events and spectacularises the use of ‘excessive force’ so as to fundamentally produce a completely inert body. Attention is then focalised on the excess of black suffering, reducing the victim to a tabula rasa upon which all manners of empathetic projection obscures the basis of a morbid white enjoyment that garners pleasure through the depiction of excoriated black flesh.12 In short; there is no prior positive blackness that could be potentially appropriated. Black existence is , the violence of anti-blackness produces black existence simultaneously produced and negated by racial domination, both as presupposition and consequence. Affirmation of blackness proves to be impossible without simultaneously affirming the violence that structures black subjectivity itself. And these conditions that procure black existence consistently repeat the sombre refrain of anti-blackness: there is no black identity, there is no black subject, there is no black life as such. As a consequence, black existence is fundamentally marked by social death, materially living as a sentient object but without a stable or guaranteed social subjectivity. And as such, the status of blackness forms the basis upon which white life can subjectivise itself, socially and materially through the negation of the black body. White life recognises itself as a positive counterpart to the non-subjecthood of blacks. However, Afro-pessimists claim that this relation between black death and white life is not merely asymmetrical. The distinction between the two is qualitatively different, and potential for reconciliation between whites and blacks is impossible. This particular distinction instead procures an antagonism in relation to the social totality. The inordinate amount of violence perpetuated against blacks – naturalised and thus ontological – means that such a situation is untranslatable to any representable terms of ‘experience’ or ‘identity’. Such a structural feature of blackness mired in violence cannot be related to contingent ‘experiences’ of social, political or economic violence, such as the struggles of workers or immigrants. Black existence forms the bottom line, the condition of possibility, of general social and material integration. It is not necessarily one’s ‘whiteness’ that matters inasmuch as one is not black enabling entrance and participation in civil society. Barred from the immanent capacities of living, anti-blackness is the necessary ground for the definition and propagation of life in general.13 In this way, Afro-pessimism also enacts a political intervention onto the terrain of identity politics and multiracial coalitions. Perhaps more generally, Afro-pessimism can be seen as a critique of the Left and all forms of activism that participate in representational politics. In the US, the past decades have seen the proliferation of identity-based politics predicated on a politics of recognition. It is this position that was made possible by the legacies of the black struggles of the 1950s to 1970s, epitomised in black liberation and the civil rights movement. However, contemporary anti-racist formations obfuscate and implicitly disavow such a legacy, while simultaneously utilising their impact to promote reform and integration. The basis of such perspectives is a wider acceptance and visibility of marginalised identities within the stronghold of civil society. Calls for unity by multiracial coalitions mask complicity with the structures of anti-blackness. They proffer an analysis that seeks to go beyond the framework of black and white racial dynamics. Yet in this gesture to ‘go beyond black and white’, the specificity of anti-blackness is obscured. In such instances, these analyses aim to discover common ground through the particularity of non-black racial identities or other oppressed categories. But this common ground is predicated on an underlying humanness, from which black existence is fundamentally barred. Such a perspective presents an atomised individual traversed by a variety of oppressions, yet these oppressions are representable and conditional to a historic instance of violence (as opposed to the ontological unconditionality of violence perpetuated against blacks), and could potentially be recognised and addressed. For it is on the basis of (human) recognition and self-representation from which minoritarian identities can wage their struggle. Black existence is barred from such a possibility due to the fact that such recognition is based upon not being black. As long as one can distance onself enough from blackness, then one has the possibility of integrating into civil society generally: The only way to solve for anti-blackness is to destroy civil society. R.L ‘13 R.L. R.L. is an informal theorist working on the problematic of racialised identities, gender and communisation theory. June 5, 2013. WANDERINGS OF THE SLAVE: BLACK LIFE AND SOCIAL DEATH. http://www.metamute.org/editorial/articles/wanderings-slave-black-life-and-social-death. July 8, 2015 Whereas redress for grievances can be sought and gained through these minoritarian struggles, ultimately they rely upon the further subjection of blacks in order to achieve such goals. Violence deployed against non-black minoritarian positions is contingent and effectively communicable through shared experiences, and therefore could be formulated into coherent demands that might be met or not. If these demands are recognised and met, they necessitate anti-blackness as a sine qua non for further integration. It is inside this ambiguous nature of empirical demands that black existence introduces a categorical antagonism reaching far beyond any empirical enunciation for socio-political recognition. For Afro-pessimists, there is no possible empirical redress for its structural position in relation to civil society, for it is the very condition that enables civil society to cohere in the first place. And this condition is that of an inordinate suffering that is not commensurate to mere experience. For this reason, black existence figures as an antagonism that transcends any empirical injustice, an antagonism that splits the world between black or human. Consequently this antagonism entails a total disorganisation of what it would mean to exist in the world at all. Black existence is essentially a structural position that positions itself as demandless, an antagonsim which is irreconcilable, and without any possible future of organic synthesis of black existence and humanity. For the form of freedom that would enable the abolition of black existence is not empirical but ontological in nature. To overcome anti-blackness, there would have to be what Fanon had called a ‘program of complete disorder,’ an expropriation and affirmation of the very violence perpetuated against black existence and a fundamental reorientation of the social coordinates of the Human relation. It would entail a war against the concept of humanity and a war that splits civil society to its core, a civil war that would elaborate itself to the death. The alternative is to reject the affirmative and reorient ourselves towards the world through an unflinching paradigmatic analysis Wilderson 10 [Frank B. III, Ph.D., Associate Professor at UC Irvine, former ANC member, “on some guerilla shit”, Red, White & Black: Cinema and the Structure of U.S. Antagonisms, pages ix-x, OG] STRANGE AS it might seem, this book project began in South Africa. During the last years of apartheid I worked for revolutionary change in both an underground and above-ground capacity, for the Charterist Movement in general and the ANC in particular. During this period, I began to see how essential an unflinching paradigmatic analysis is to a movement dedicated to the complete overthrow of an existing order. The neoliberal compromises that the radical elements of the Chartist Movement made with the moderate elements were due, in large part, to our inability or unwillingness to hold the moderates' feet to the fire of a political agenda predicated on an unflinching paradigmatic analysis. Instead, we allowed our energies and points of attention to be displaced by and onto pragmatic considerations. Simply put, we abdicated the power to pose the question—and the power to pose the question is the greatest power of all. Elsewhere, I have written about this unfortunate turn of events (Incognegro: A Memoir of Exile and Apartheid), so I'll not rehearse the details here. Suffice it to say, this book germinated in the many political and academic discussions and debates that I was fortunate enough to be a part of at a historic moment and in a place where the word revolution was spoken in earnest, free of qualifiers and irony. For their past and ongoing ideas and interventions, I extend solidarity and appreciation to comrades Amanda Alexander, Franco Barchiesi, Teresa Barnes, Patrick Bond, Ashwin Desai, Nigel Gibson, Steven Greenberg, Allan Horowitz, Bushy Kelebonye (deceased), Tefu Kelebonye, Ulrike Kistner, Kamogelo Lekubu, Andile Mngxitama, Prishani Naidoo, John Shai, and S'bu Zulu Policing/Settler societies allow for the black body to be a magnet for gratuitous violence Wilderson, Professor UCI, 2003 (Frank B., “The Prison Slave as Hegemony’s (Silent) Scandal”, Soc Justice 30 no2 2003, Accessed 8-4-12, MR) It makes no difference that in the U.S. the "casbah" and the "European" zone are laid one on top of the other. What is being asserted here is an isomorphic schematic relation the schematic interchangeability - between Fanon' s settler society and Martinot and Sexton's policing paradigm. For Fanon, it is the policeman and soldier (not the discursive, or hegemonic, agents) of colonialism that make one town white and the other Black. For Martinot and Sexton, this Manichean delirium manifests itself by way of the U.S. paradigm of policing that (re)produces, repetitively, the inside/outside, the civil society/Black world, by virtue of the difference between those bodies that do not magnetize bullets and those that do. "Police impunity serves to distinguish between the racial itself and the elsewhere that mandates it...the distinction between those whose human being is put permanently in question and those for whom it goes without saying" (Ibid.: 8). In such a paradigm, white people are, ipso facto, deputized in the face of Black people, whether they know it (consciously) or not. Whiteness, then, and by extension civil society, cannot be solely "represented" as some monumentalized coherence of phallic signifiers, but must first be understood as a social formation of contemporaries who do not magnetize bullets. This is the essence of their construction through an asignifying absence; their signifying presence is manifested by the fact that they are, if only by default, deputized against those who do magnetize bullets. In short, white people are not simply "protected" by the police, they are - in their very corporeality - the police. This ipso facto deputization of white people in the face of Black people accounts for Fanon's materiality, and Martinot and Sexton's Manichean delirium in America. What remains to be addressed, however, is the way in which the political contestation between civil society's junior partners (i.e., workers, white women, and immigrants), on the one hand, and white supremacist institutionality, on the other hand, is produced by, and reproductive of, a supplemental antiBlackness. Put another way: How is the production and accumulation of junior partner social capital dependent upon on an anti-Black rhetorical structure and a decomposed Black body? Technological surveillance creates a new space for racially profiled stop-andfrisk. Hackman ‘15 Hackman, Rose. New York journalist. April 23 2015. Online surveillance: The new stop-and-frisk. http://www.theguardian.com/us-news/2015/apr/23/online-surveillance-black-teenagers-new-stop-and-frisk. July 8, 2015. In 2013, stop-and-frisk was found unconstitutional by a federal judge for its use of racial profiling. Since then, logged instances have dropped from an astonishing 685,000 in 2011 to just 46,000 in 2014. But celebrations may be premature, with local policing increasingly moving off the streets and migrating online. In 2012, the NYPD declared a war on gangs across the city with Operation Crew Cut. The linchpin of the operation’s activities is the sweeping online surveillance of individuals as young as 10 years old deemed to be members of crews and gangs. This move is being criticized by an increasing number of community members and legal scholars, who see it as an insidious way of justifying the monitoring of young men and boys of color in low-income communities. These days, crews are understood geographically (“turf-based”). They’re no longer “entrepreneurial” – that is, heavily within the organized crime world, like LA gangs were in the 1990s. In other words, New York City crew membership, which mostly appeals to teenagers, is simply related to the block you grew up on, your community and family ties, and perhaps even your interest in partying, dance or graffiti. Advertisement Mostly, being a member of a gang or a crew is a fleeting moment of adolescence, and something that people grow out of, explains Jeffrey Lane, a professor in communication at Rutgers University whose research has looked at the way in which adolescent street life is lived online. What is unquestionably worrying – and what the NYPD is using to justify broad monitoring of large swaths of people – is when these crews turn on each other, and rivalries between crews become violent, or even deadly. And while some of the humiliation and potential violence is avoided by diverting resources away from the physical practice of stop-and-frisk, online surveillance raises a vast series of questions tied to the civil liberties of young men of color. Counter surveillance good/Bad Counter surveillance good EPIS ’15 Empire Pacific Investigation Services. Feburary 2015. Counter Surveillance Investigation.http://www.epis.us/services/domestic-surveillance-investigations/counter-surveillance.html. July 8, 2015. Counter surveillance refers to measures undertaken to prevent surveillance, including covert surveillance. Counter surveillance may include electronic methods such as bug sweeping, the process of detecting surveillance devices, including covert listening devices and visual surveillance devices. More often than not, counter surveillance will employ a set of actions that, when followed, reduce the risk of surveillance. Counter surveillance is the art of performing surveillance on those who are performing surveillance themselves and is used to ensure that the target is not being followed or under surveillance from another source. For instance, on one of the Counter surveillance cases, our client hired one of our counter surveillance private investigators to watch see who was following him, he become aware that someone is following him around and videotaping his activities. The client then hired Counter Surveillance investigators to identify the people watching him and to determine who hired them. In another case, Counter surveillance is used in cases where someone may be stalking another person. Stalkers attempt to follow and determine the patterns and activities of their targets. Counter surveillance can be used to determine who is responsible for the stalking without alerting the stalker or causing the stalker to withdraw. If the stalker withdrew, it would make it impossible to identify and neutralize their threat. Counter surveillance is an extremely difficult surveillance operation. Not only is the investigator attempting to perform surveillance on someone that may be proficient in surveillance techniques themselves, but they must do it without being detected during times when that person is performing surveillance and is, therefore, actively monitoring their surroundings. Starting Point Good – Surveillance Key Surveillance is a key starting point. Kundani and Kumar ’15 (Spring 2015 Arun Kundnani teaches at New York University. His latest book is The Muslims Are Coming! Islamophobia, Extremism, and the Domestic War on Terror, Deepa Kumar is an associate professor of Media Studies and Middle East Studies at Rutgers University. She is the author of Islamophobia and the Politics of Empire, International Socialist Review Issue 96, “Race, surveillance, and empire” http://isreview.org/issue/96/race-surveillance-and-empire DA:7/8/15 CB) Beginning in June 2013, a series of news articles based on whistle-blower Edward Snowden’s collection of documents from the National Security Agency (NSA) took the world by storm. Over the course of a year, the Snowden material provided a detailed account of the massive extent of NSA’s warrantless data collection. What became clear was that the NSA was involved in the mass collection of online material. Less apparent was how this data was actually used by the NSA and other national security agencies. Part of the answer came in July 2014 when Glenn Greenwald and Murtaza Hussain published an article that identified specific targets of NSA surveillance and showed how individuals were being placed under surveillance despite there being no reasonable suspicion of their involvement in criminal activity.1 All of those named as targets were prominent Muslim Americans. The following month, Jeremy Scahill and Ryan Devereaux published another story for The Intercept, which revealed that under the Obama administration the number of people on the National Counterterrorism Center’s no-fly list had increased tenfold to 47,000. Leaked classified documents showed that the NCC maintains a database of terrorism suspects worldwide—the Terrorist Identities Datamart Environment—which contained a million names by 2013, double the number four years earlier, and increasingly includes biometric data. This database includes 20,800 persons within the United States who are disproportionately concentrated in Dearborn, Michigan, with its significant Arab American population.2 By any objective standard, these were major news stories that ought to have attracted as much attention as the earlier revelations. Yet the stories barely registered in the corporate media landscape. The “tech community,” which had earlier expressed outrage at the NSA’s mass digital surveillance, seemed to be indifferent when details emerged of the targeted surveillance of Muslims. The explanation for this reaction is not hard to find. While many object to the US government collecting private data on “ordinary” people, Muslims tend to be seen as reasonable targets of suspicion. A July 2014 poll for the Arab American Institute found that 42 percent of Americans think it is justifiable for law enforcement agencies to profile Arab Americans or American Muslims.3 In what follows, we argue that the debate on national security surveillance that has emerged in the United States since the summer of 2013 is woefully inadequate, due to its failure to place questions of race and empire at the center of its analysis. It is racist ideas that form the basis for the ways national security surveillance is organized and deployed, racist fears that are whipped up to legitimize this surveillance to the American public, and the disproportionately targeted racialized groups that have been most effective in making sense of it and organizing opposition. This is as true today as it has been historically: race and state surveillance are intertwined in the history of US capitalism . Likewise, we argue that the history of national security surveillance in the United States is inseparable from the history of US colonialism and empire. The argument is divided into two parts. The first identifies a number of moments in the history of national security surveillance in North America, tracing its imbrication with race, empire, and capital, from the settler-colonial period through to the neoliberal era. Our focus here is on how race as a sociopolitical category is produced and reproduced historically in the United States through systems of surveillance. We show how throughout the history of the United States the systematic collection of information has been interwoven with mechanisms of racial oppression. From Anglo settler-colonialism, the establishment of the plantation system, the post–Civil War reconstruction era, the US conquest of the Philippines, and the emergence of the national security state in the post-World War II era, to neoliberalism in the post-Civil Rights era, racialized surveillance has enabled the consolidation of capital and empire. It is, however, important to note that the production of the racial “other” at these various moments is conjunctural and heterogenous. That is, the racialization of Native Americans, for instance, during the settler-colonial period took different forms from the racialization of African Americans. Further, the dominant construction of Blackness under slavery is different from the construction of Blackness in the neoliberal era; these ideological shifts are the product of specific historic conditions. In short, empire and capital, at various moments, determine who will be targeted by state surveillance, in what ways, and for how long. In the second part, we turn our attention to the current conjuncture in which the politics of the War on Terror shape national security surveillance practices. The intensive surveillance of Muslim Americans has been carried out by a vast security apparatus that has also been used against dissident movements such as Occupy Wall Street and environmental rights activists, who represent a threat to the neoliberal order. This is not new; the process of targeting dissenters has been a constant feature of American history. For instance, the Alien and Sedition Acts of the late 1790s were passed by the Federalist government against the Jeffersonian sympathizers of the French Revolution. The British hanged Nathan Hale because he spied for Washington’s army in the American Revolution. State surveillance regimes have always sought to monitor and penalize a wide range of dissenters, radicals, and revolutionaries. Race was a factor in some but by no means all of these cases. Our focus here is on the production of racialized “others” as security threats and the ways this helps to stabilize capitalist social relations. Further, the current system of mass surveillance of Muslims is analogous to and overlaps with other systems of racialized security surveillance that feed the mass deportation of immigrants under the Obama administration and that disproportionately target African Americans, contributing to their mass incarceration and what Michelle Alexander refers to as the New Jim Crow.4 We argue that racialized groupings are produced in the very act of collecting information about certain groups deemed as “threats” by the national security state —the Brown terrorist, the Black and Brown drug dealer and user, and the immigrant who threatens to steal jobs. We conclude that “security” has become one of the primary means through which racism is ideologically reproduced in the “post-racial,” neoliberal era. Drawing on W. E. B. Dubois’s notion of the “psychological wage,” we argue that neoliberalism has been legitimized in part through racialized notions of security that offer a new “psychological wage” as compensation for the decline of the social wage and its reallocation to “homeland security.” Settler- colonialism and racial security National security surveillance is as old as the bourgeois nation state, which from its very inception sets out to define “the people” associated with a particular territory, and by extension the “non-peoples,” i.e., populations to be excluded from that territory and seen as threats to the nation. Race, in modern times, becomes the main way that such threats—both internal and external—are mediated; modern mechanisms of racial oppression and the modern state are born together. This is particularly true of settler-colonial projects, such as the United States, in which the goal was to territorially dispossess Indigenous nations and pacify the resistance that inevitably sprang up. In this section, we describe how the drive for territorial expansion and the formation of the early American state depended on an effective ideological erasure of those who peopled the land. Elaborate racial profiles, based on empirical “observation”—the precursor to more sophisticated surveillance mechanisms—were thus devised to justify the dispossession of native peoples and the obliteration of those who resisted. The idea of the American nation as the land of white Anglo-Saxon Protestants enabled and justified the colonial-settler mission.5 Thus, when the US state was formed after the Revolutionary War, white supremacy was codified in the Constitution; the logical outcome of earlier settlercolonial systems of racial discrimination against African slaves and Indigenous populations.6 But the leaders of the newly formed state were not satisfied with the thirteen original colonies and set their sights on further expansion. In 1811, John Quincy Adams gave expression to this goal in the following way: “The whole continent of North America appears to be destined by Divine Providence to be peopled by one nation, speaking one language, professing one general system of religious and political principles, and accustomed to one general tenor of social usages and customs.”7 This doctrine, which would later come to be known as “manifest destiny” animated the project of establishing the American nation across the continent. European settlers were the “chosen people” who would bring development through scientific knowledge, including state-organized ethnographic knowledge of the very people they were colonizing.8 John Comaroff’s description of this process in southern Africa serves equally to summarize the colonial states of North America: “The ‘discovery’ of dark, unknown lands, which were conceptually emptied of their peoples and cultures so that their ‘wilderness’ might be brought properly to order—i.e., fixed and named and mapped—by an officializing white gaze.”9 Through, for example, the Bureau of Indian Affairs, the United States sought to develop methods of identification, categorization, and enumeration that made the Indigenous population “visible” to the surveillance gaze as racial “others.” Surveillance that defined and demarcated according to officially constructed racial typologies enabled the colonial state to sort “tribes” according to whether they accepted the priorities of the settler-colonial mission (the “good” Indians) or resisted it (the “bad” Indians).10 In turn, an idea of the US nation itself was produced as a homeland of white, propertied men to be secured against racial others. No wonder, then, that the founding texts of the modern state invoke the Indigenous populations of America as bearers of the “state of nature,” to which the modern state is counterposed—witness Hobbes’s references to the “the Savage people of America.”11 The earliest process of gathering systematic knowledge about the “other” by colonizers often began with trade and religious missionary work. In the early seventeenth century, trade in furs with the Native population of Quebec was accompanied by the missionary project. Jesuit Paul Le Jeune worked extensively with the Montagnais-Naskapi and maintained a detailed record of the people he hoped to convert and “civilize.”12 By studying and documenting where and how the “savages” lived, the nature of their relationships, their child-rearing habits, and the like, Le Juene derived a four-point program to change the behaviors of the Naskapi in order to bring them into line with French Jesuit morality. In addition to sedentarization, the establishment of chiefly authority, and the training and punishment of children, Le Juene sought to curtail the independence of Naskapi women and to impose a European family structure based on male authority and female subservience.13 The net result of such missionary work was to pave the way for the racial projects of colonization and/or “integration” into a colonial settler nation. By the nineteenth century, such informal techniques of surveillance began to be absorbed into government bureaucracy. In 1824, Secretary of War John C. Calhoun established the Office of Indian Affairs (later “Bureau”), which had as one of its tasks the mapping and counting of Native Americans. The key security question was whether to forcibly displace Native Americans beyond the colonial territory or incorporate them as colonized subjects; the former policy was implemented in 1830 when Congress passed the Indian Removal Act and President Jackson began to drive Indians to the west of the Mississippi River. Systematic surveillance became even more important after 1848, when Indian Affairs responsibility transferred from the Department of War to the Department of the Interior, and the Bureau of Indian Affairs sought to comprehensively map the Indigenous population as part of a “civilizing” project to change “the savage into a civilized man,” as a congressional committee put it. By the 1870s, Indians were “the quantified objects of governmental intervention”; resistance was subdued as much through “rational” techniques of racialized surveillance and a professional bureaucracy as through war.14 The assimilation of Indians became a comprehensive policy through the Code of Indian Offenses, which included bans on Indigenous cultural practices that had earlier been catalogued by ethnographic surveillance. Tim Rowse writes that For the U.S. government to extinguish Indian sovereignty, it had to be confident in its own. There is no doubting the strength of the sense of “manifest destiny” in the United States during the nineteenth-century, but as the new nation conquered and purchased, and filled the new territories with colonists, it had also to develop its administrative capacity to govern the added territories and peoples. U.S. sovereign power was not just a legal doctrine and a popular conviction; it was an administrative challenge and achievement that included acquiring, by the 1870s, the ability to conceive and measure an object called “the Indian population.”15 The use of surveillance to produce a census of a colonized population was the first step to controlling it. Mahmood Mamdani refers to this as “define and rule,” a process in which, before managing a heterogeneous population, a colonial power must first set about defining it; to do so, the colonial state “wielded the census not only as a way of acknowledging difference but also as a way of shaping, sometimes even creating, difference.”16 The “ethnic mapping” and “demographics unit” programs practiced by US law enforcement agencies today in the name of counterterrorism are the inheritors of these colonial practices . Both then and now, state agencies’ use of demographic information to identify “concentrations” of ethnically defined populations in order to target surveillance resources and to identify kinship networks can be utilized for the purposes of political policing. Likewise, today’s principles of counterinsurgency warfare—winning hearts and minds by dividing the insurgent from the nonresistant—echo similar techniques applied in the nineteenth century at the settler frontier. Class, gender, and racial security While racial security was central to the settler-colonial project in North America, territorial dispossession was only one aspect of the process of capital accumulation for the new state; the other was the discipline and management of labor. As Theodore Allen shows in The Invention of the White Race, the “white race” did not exist as a category in Virginia’s colonial records until the end of the seventeenth century. Whiteness as an explicit racial identity had to be cultivated over a period of decades before it could become the basis for an organized form of oppression.17 A key moment in the production of whiteness was the response of the ruling Anglo elite to Bacon’s Rebellion of 1676. The rebellion was begun by colonial settlers who wanted a more aggressive approach to securing the territory against Indigenous peoples. But it also involved African and Anglo bond laborers joining together in a collective revolt against the system of indentured servitude. This threatened not only the profitability but also the very existence of the plantation system. Over the following three decades, the Virginia Assembly passed a series of acts that racialized workers as Black and white. Those who could now call themselves white were granted some benefits by law, whereas those designated Black were turned from bond laborers (who could therefore expect to be free after a period of time) into slaves— property with no rights whatsoever and no hope of freedom. To win them to the side of the plantation bourgeoisie, poor white men were given privileges—they had access to land and enjoyed common law protections such as trial by jury and habeas corpus that were denied to Black enslaved people.18 In practice this meant that white men, for instance, could rape Black women and not be charged with a crim e (because Blacks were property and so only “damages” were to be paid to the slave owner). Further, property rights and the legal notion of settled land not only denied Native American property claims but even erased the existence of Indigenous people on the basis that, because white settlers had transformed the pristine North American wilderness into productive land, they were the real “natives.”19 Once the legal and ideological work had been done to naturalize race as a visible marker of inherent difference and to separate “us” from “them,” it could be made use of as a stable category of surveillance; the patrols set up to capture runaway slaves—arguably the first modern police forces in the United States20—needed only to “see” race in order to identify suspects. Moreover, the plantation system was stabilized by enabling non-elite whites to see security as a racial privilege and shared responsibility. W. E. B. Du Bois argued in Black Reconstruction that, in the slave plantations of the South, poor whites were brought into an identification with the planter elite by being given positions of authority over Blacks as overseers, slave drivers, and members of slave patrols. With the associated feeling of superiority, their hatred for the wider plantation economy that impoverished them was displaced onto Black enslaved people: class antagonism was racialized and turned into a pillar of stability for the system. Meanwhile, in the North, labor leaders had little appetite for abolition, fearing competition from a newly freed Black workforce.21 After abolition, the same racial anxieties were mobilized to disenfranchise the Black laborer in the South. Du Bois used the term “psychological wage” to describe this sense of superiority granted to non-elite whites in the South: It must be remembered that the white group of laborers, while they received a low wage, were compensated by a sort of public and psychological wage. They were given public deference and titles of courtesy because they were white. They were admitted freely with all classes of white people to public functions, public parks, and the best schools. The police were drawn from their ranks, and the courts, dependent under their votes, treated them with such leniency as to encourage lawlessness.… On the other hand, in the same way, the Negro was subject to public insult; was afraid of mobs; was liable to the jibes of children and the unreasoning fears of white women; and was compelled almost continuously to submit to various badges of inferiority. The result of this was that the wages of both classes could be kept low, the whites fearing to be supplanted by Negro labor, the Negroes always being threatened by the substitution of white labor.22 We suggest below that, since the 1970s, neoliberalism has involved a similar kind of process, in which the social wage of the New Deal welfare state was progressively withdrawn and racialized notions of security offered in its place as a psychological compensation. These racialized notions of security are also inflected by gender. As Du Bois notes in the above quote, free Black men were positioned as threats to white women in the post–Civil War era. Unlike during slavery, when Black men were not indiscriminately labeled as rapists and lynching was rare, the period between 1865 and 1895 saw the lynching of over ten thousand African Americans. Fredrick Douglass argued that, when all the other methods of demonizing Black people failed, the myth of the Black rapist was developed to justify lynchings and white terror.23 Vigilante groups like the Ku Klux Klan justified their brutality by claiming to keep white women safe from the Black rapist, as visualized, for instance, in D. W. Griffith’s Birth of a Nation. Such constructions of white women in need of protection from predatory Black men were reminiscent of the “captivity scenarios” of the seventeenth century, in which Native Americans were accused of kidnapping white women, a charge that then justified genocide.24 Thus, from the early settler-colonial period onwards, “security” and “protection” were defined by elites in gendered and racial terms. In particular, the white, heterosexual family was positioned as the subject of a security narrative that cast racialized others as threats to the “homeland.” The “homeland” so defined also needed to be secured from racialized immigrant threats, but which immigrants counted as white in this “homeland” was somewhat unstable. When Irish immigrants began to arrive in the United States in large numbers from the 1850s onwards, they were considered nonwhite because they were perceived to be of Celtic rather than Anglo Saxon background. More importantly, Irish Catholics faced the same exclusionary practices that Catholics did in previous centuries. Even though by the mid-eighteenth century, the need for “English colonies to be economically sustainable and militarily secure from indigenous threat,” opened up non-English immigration to North America, Catholics (along with Indian tribes) were denied basic rights on the grounds that they were religiously and culturally different from the WASP population.25 Over time, however, Irish and Italian immigrants were made white. From the late nineteenth century, the policing of the United States’s borders was another context where racial and imperial security was intertwined with practices of surveillance. Congress first sought to police borders as part of a strategy of regulating labor in 1882, when it excluded Chinese immigrants. In 1909, US immigration officials began excluding around half of all Asian Indians from entering. Following concern from the British government that anti-colonial nationalists from India were using the United States as a base to spread radical politics, US officials began to interrogate Indian migrants at West Coast ports, and a British agent arranged for the Justice Department to monitor all mail moving between India and the Berkeley and San Francisco post offices.26 In 1917, legislation was introduced to create a “barred Asiatic zone,” stretching from Afghanistan to the Pacific, from which no one could be admitted to the United States.27 With the Johnson-Reed Immigration Act of 1924, a comprehensive system of national quotas was introduced reflecting a global racial hierarchy. Through immigration policy, an idea of the US homeland as a Western European, white ethnoracial identity was institutionalized. To implement such a vision, appropriate systems of record keeping and surveillance of immigrants were required.28 Through these various means, Mae M. Ngai argues, Asian Americans and Mexican Americans were produced as “alien citizens,” formally US citizens but legally racialized and excluded. The surveillance of these groups made possible the repatriation of 400,000 persons of Mexican descent during the Great Depression (of whom half had been thought to be US citizens) and the internment of 120,000 of Japanese ancestry during World War II (two-thirds of whom were citizens).29 In the nineteenth century, the political surveillance of labor militancy had routinely been practiced by private agencies such as Pinkerton and Burns, who were directly contracted by capitalists rather than through the state. But toward the end of the century, such practices began to be absorbed into government agencies. Following the so-called Tompkins Square Riot of 1874—actually a demonstration in New York against unemployment that was attacked by the police—the New York Police Department began to assign detectives to spy on socialist and union meetings. By the mid-1890s, the department was tapping 350 phones.30 By 1900, a number of police departments in the United States had created “red squads” specifically to deploy informants to left-wing organizations and meetings. Empire and the national security state By 1890, coast-tocoast colonization was effectively complete, with the surviving Native American population consigned to reservations. Thereafter, the priority became the projection of US power further afield, again justified through a racialized understanding of American exceptionalism. As Paul Kramer writes in the context of the US conquest of the Philippines: [T]he war’s advocates subsumed US history within longer, racial trajectories of “Anglo-Saxon” history which folded together US and British imperial histories. The Philippine-American War, then, was a natural extension of Western conquest, and both taken together were the organic expression of the desires, capacities, and destinies of “Anglo-Saxon” peoples. Americans, as Anglo-Saxons, shared Britons’ racial genius for empire-building, a genius which they must exercise for the greater glory of the “race” and to advance “civilization” in general. Unlike other races, they “liberated” the peoples they conquered; indeed, their expressions of conquest as “freedom” proliferated as the terrors they unleashed became more visible.31 The resistance that Filipinos mounted to American benevolence could then only be seen as an atavistic barbarism to be countered through modern techniques of surveillance and repression. While local police departments within the United States had begun to develop techniques of political surveillance, it was under the US colonial regime in the Philippines that systematic and widespread surveillance of political opponents and the manipulation of personal information as a form of political control was first institutionalized. A unit within the police called the Constabulary Information Section was established in Manila in 1901, founded by Henry Allen, a former military attaché to Tsarist Russia.32 The Constabulary Information Section cultivated hundreds of paid Filipino agents across the country, making it “scarcely possible for seditionary measures of importance to be hatched without our knowledge,” as Allen wrote to President Theodore Roosevelt.33 The techniques of compiling dossiers on dissidents’ private lives, spreading disinformation in the media, and planting agents provocateurs among militants were applied to combating radical nationalist groupings in Manila. Control over information proved as effective a tool of colonial power as physical force. As historian Alfred W. McCoy notes, during World War I police methods that had been tested and perfected in the colonial Philippines migrated homeward to provide both precedents and personnel for the establishment of a US internal security apparatus.… After years of pacifying an overseas empire where race was the frame for perception and action, colonial veterans came home to turn the same lens on America, seeing its ethnic communities . . . as internal colonies requiring coercive controls.34 On this basis, a domestic national security apparatus emerged, with notions of race and empire at its core. From 1917, the FBI and police department red squads in US cities increasingly busied themselves with fears of subversion from communists, pacifists, anarchists, and the ten million German Americans who were suspected of harboring disloyalties. During World War I, thirty million letters were physically examined and 350,000 badge-carrying vigilantes snooped on immigrants, unions, and socialists.35 Concerns over privacy set limits to such surveillance after the war, but with increasing left-wing and right-wing radicalization in the 1930s, President Roosevelt decided to issue a secret executive order that authorized a shift in the FBI’s role from a narrowly conceived law enforcement agency focused on gathering evidence for criminal prosecutions into an intelligence agency. Thereafter, it was dedicated to spying on “subversive” political movements (primarily communists, but also fascists) and countering their ability to influence public debate . This meant the FBI systematically identifying subversives based on “ideological and associational criteria.”36 It also opened the door to the burgeoning counter-subversion practices that the bureau would launch over the following decades. Already during World War II, the FBI was collecting detailed files on suspected communists while Black organizations such as the National Association for the Advancement of Colored People and the Nation of Islam were also surveillance targets.37 At the end of the Second World War, the United States emerged as one of two superpowers on the world stage. Pushing back against the isolationists, Cold War liberals made the case for the establishment of a permanent national security state. According to historian Paul Hogan, the national security mindset that emerged involved a conviction that a new era of total war had dawned on the United States. In total war, the battle was not confined to the front lines but extended to the home front as well, as did the awesome destruction that modern weapons could inflict not only on military combatants but also on industry, urban centers, and civilian populations. Modern war was total war in this sense that modern armies depended on the output of citizen soldiers in farms and factories behind the battle line. In total war all of the nation’s resources and all of its energy and talent had to be mobilized on behalf of the war effort, thereby obliterating the old distinction between civilian and military, between citizen and soldier, between home front and the front line. When American leaders talked about total war they did so in these terms and also in terms that recognized that modern weapons could bring massive destruction from great distances with barely a moment’s notice. In the new age, American leaders would no longer have the time to debate the issue of war or peace or to prepare at a slow pace.38 This was an updating and reworking of the settler-colonial mentality, with the notion of Manifest Destiny being explicitly drawn on in making the case for an exceptional American empire. The notion of the “citizen-soldier” was built upon earlier settler-colonial racialized security narratives. However, American exceptionalism, as it emerged in this period, was based on the premise that the United States was not only unique among other nations and therefore destined to play a leading global role, but also a nation built upon liberal principles. This meant that the centrality of whiteness to the security narrative was muted and less prominent. Even though the white middle-class home was cast as the locus of a privatized notion of self-defense and military preparedness through government civil defense policies and programs,39 the image of the US empire was one of liberalism, inclusivity, and the “melting pot.” The United States sought quite consciously to differentiate itself from past empires as it positioned itself to be one of two hegemons on the global stage. In this context, the existence of Jim Crow segregation was an embarrassment for the ruling class. In 1947, the National Security Act was passed which entrenched “security” as a key element of the postwar order. Every aspect of life—the social, political, intellectual, and economic— was conceived as playing a role in national defense, and a massive security establishment was built up. The 1947 act created the Office of the Secretary of Defense, the Joint Chiefs of Staff, the National Security Council (NSC), and the Central Intelligence Agency (CIA). The National Security Agency (NSA) was formed in 1952, conceived as an organization to carry out the gathering of “signals intelligence.” During this period, there was also the integration of corporate America, of universities, of research institutions, and of the media into the machinery of the national security state. The earlier distinctions between the citizen and soldier and between the home front and the battle front were blurred to shore up an imperial system at home and abroad. Surveillance was central to sustaining and reproducing this system. From the 1940s to the early 1970s, FBI wiretapping and bugging operations focused on a wide range of movements, activists, and public figures. The following list of targets compiled by historian Athan Theoharis gives a flavor of the surveillance and is worth quoting in full: Radical activists (David Dallin, Charles Malamuth, C. B. Baldwin, Frank Oppenheimer, Bertolt Brecht, Thomas Mann, Heinrich Mann, Helene Weigel, Berthold Viertel, Anna Seghers, Bodo Uhse, Richard Criley, Frank Wilkinson), prominent liberal and radical attorneys (Bartley Crum, Martin Popper, Thomas Corcoran, David Wahl, Benjamin Margolis, Carol King, Robert Silberstein, National Lawyers Guild, Fred Black), Radical labor leaders and unions (Harry Bridges; United Auto Workers; National Maritime Union; National Union of Marine Cooks and Stewards; United Public Workers; United Electrical Radio and Machine Workers; Food, Tobacco, Agricultural and Allied Workers; International Longshoremen’s and Warehousemen’s Union; CIO Maritime Committee; Congress of Industrial Organizations Council), Journalists (I. F. Stone, Philip Jaffe, Kate Mitchell, Mark Gayn, Leonard Lyons, William Beecher, Marvin Kalb, Henry Brandon, Hedrick Smith, Lloyd Norman, Hanson Baldwin, Inga Arvad), Civil-rights activists and organizations (Martin Luther King, Jr.; Malcolm X; Southern Christian Leadership Conference; National Association for the Advancement of Colored People; March on Washington Movement; Gandhi Society for Human Rights; Elijah Muhammad; Nation of Islam; Stokely Carmichael; H. Rap Brown; Student Non-Violent Coordinating Committee; Alabama Peoples Education Association; Committee to Aid the Monroe Defendants; Southern Conference for Human Welfare; Black Panther Party; Universal Negro Improvement Association; African Liberation Day Committee), The Students for a Democratic Society, Ku Klux Klan, National Committee to Abolish HUAC, Socialist Workers Party, Washington Bookstore Association, Northern California Association of Scientists, Federation of American Scientists, American Association of Scientific Workers, pre–World War II isolationists (Henry Grunewald, Ethel Brigham, John O’Brien, Lillian Moorehead, Laura Ingalls, America First, Jehovah’s Witnesses, Los Angeles Chamber of Commerce), and even prominent personalities (Joe Namath, Harlow Shapley, Edward Condon, Edward Prichard, Muhammad Ali, Benjamin Spock).40 In a bid to shape public opinion, the FBI also launched a mass media campaign in 1946 that released “educational materials” to cooperative journalists and legislators. In the late 1950s, the FBI launched its secret counterintelligence program (COINTELPRO), which used provocateurs and informants to infiltrate communist groups initially, but later widened to include Puerto Rican nationalists, the student movement, the civil rights movement, and Black liberation movements. About 1,500 of the 8,500 American Communist Party members were likely FBI informants in the early 1960s. By the end of the decade, agents who had previously worked in US foreign intelligence were transferring to the burgeoning field of domestic intelligence to spy on radical movements, whether employed by the bureau, military intelligence, or the expanding red squads in local police departments.41 A key part of the FBI’s countersubversion strategy was the manipulation of political activists into committing criminal acts so that they could be arrested and prosecuted. Agents provocateurs working for the FBI initiated disruptions of meetings and demonstrations, fights between rival groups, attacks on police, and bombings. FBI agents also secretly distributed derogatory and scurrilous material to police, Congress, elected officials, other federal agencies, and the mass media.42 In an attempt to “neutralize” Martin Luther King, Jr., who, the FBI worried, might abandon his “obedience to white liberal doctrines” (as indeed he did), he was placed under intense surveillance, and attempts were made to destroy his marriage and induce his suicide. In various cities, the FBI and local police used fake letters and informants to stir up violence between rival factions and gangs to disrupt the Black Panther Party.43 In a number of cases, police departments or federal agents carried out the direct assassination of Black Panthers.44 Since 1945, the government had been running a mass spying program known as Project Shamrock, which the NSA took over in 1952. The telecommunications companies at the time handed over to the NSA all telegrams sent out of and into the United States. By the early 1970s, NSA analysts were collecting and analyzing approximately 150,000 telegrams a month. In 1967, the FBI and CIA submitted lists of names to the National Security Agency of key activists in the civil rights and anti-Vietnam War movements, hoping that the NSA would be able to find evidence of the communist conspiracy that President Lyndon Johnson thought must be causing the new militancy of the 1960s. The list included politically active public figures such as actress Jane Fonda and singer Joan Baez, as well as Martin Luther King, Jr., Eldridge Cleaver, and Abbie Hoffman. NSA officers began surveillance of these activists’ communications, using special records procedures to prevent discovery of what they knew to be an illegal program. This “watch list” program was expanded under President Nixon and named Operation Minaret; in all, the international communications of more than a thousand US citizens and organizations and more than two thousand foreign citizens were intercepted.45 Such was the proliferation of government spying in the 1960s that even such a minor law enforcement agency as the Ohio Highway Patrol ran an intelligence unit claiming to have student informers on every campus in the state.46 The vast expansion of state surveillance in the 1960s was a response to the new militancy of the movements against the imperialist war in Vietnam and for civil rights and Black liberation. Initially, security officials assumed the Civil Rights movement in the South, the campus protests, and the Black insurrections in northern cities were the result of a communist conspiracy; informants and electronic monitoring were deployed to try to identify the hidden agitators thought to be manipulating events behind the scenes. But it soon became apparent that these movements were manifestations of a new kind of politics that could not be understood according to the conspiratorial calculus of “front groups” and “fellow travelers”; surveillance therefore had to be widened to monitor ordinary participants, particularly in Black communities, in what was increasingly seen as a popular insurgency. Even then, the hope was that new electronic technologies would be the answer. National security advisor Zbigniew Brzezinski commented in 1970 that technology would make it “possible to assert almost continuous surveillance over every citizen and maintain up-to-date files, containing even personal information about the . . . behavior of the citizen, in addition to the more customary data.”47 Neoliberalism and racial security The expansion of the surveillance state in the twentieth century was one aspect of a wider penetration of the state into the lives of Americans. Working class struggle had somewhat unexpectedly driven this expansion: the state responded by taking on a mediating role between labor and capital, offering a measure of protection from the ravages of a market economy through Keynesian economics and the creation of a welfare state after the New Deal—albeit one that was underdeveloped compared to Western Europe. State managers sought to stabilize capitalism by imposing a degree of “rationality” on the system through regulating the economy and providing social services, all of which required a greater penetration of the state into civil society.48 In the new era of neoliberal capitalism that began in the 1970s, ruling elites sought to break this social contract, which rested on the premise that, if the working class “played by the rules,” it could see increases in wages and living conditions. From the 1970s onwards, this arrangement was undone. Alongside, there were also the beginnings of a contraction of the social wage of welfare provisions, public housing, education, and healthcare. The end result was growing inequality and a new regime of the one percent. The state responded to the permanent joblessness, ghettoization, and stigmatization that neoliberalism produced among the poor by turning to policies of mass criminalization and incarceration. Thus, the neoliberal onslaught went hand in hand with securitization. As Loïc Wacquant writes, since the civil rights era America has launched into a social and political experiment without precedent or equivalent in the societies of the postwar West: the gradual replacement of a (semi-) welfare state by a police and penal state for which the criminalization of marginality and the punitive containment of dispossessed categories serve as social policy at the lower end of the class and ethnic order.49 The law and order rhetoric that was used to mobilize support for this project of securitization was racially coded, associating Black protest and rebellion with fears of street crime. The possibilities of such an approach had been demonstrated in the 1968 election, when both the Republican candidate Richard Nixon and the independent segregationist George Wallace had made law and order a central theme of their campaigns. It became apparent that Republicans could cleave Southern whites away from the Democratic Party through tough-on-crime rhetoric that played on racial fears. The Southern Strategy, as it would be called, tapped into anxieties among working-class whites that the civil rights reforms of the 1960s would lead to them competing with Blacks for jobs, housing, and schools. With the transformation of the welfare state into a security state, its embedding in everyday life was not undone but diverted to different purposes. Social services were reorganized into instruments of surveillance. Public aid became increasingly conditional on upholding certain behavioral norms that were to be measured and supervised by the state, implying its increasing intrusion into the lives of the poor—culminating in the “workfare” regimes of the Clinton administration.50 In this context, a new model of crime control came into being. In earlier decades, criminologists had focused on the process of rehabilitation; those who committed crimes were to be helped to return to society. While the actual implementation of this policy was uneven, by the 1970s, this model went out of fashion. In its place, a new “preventive” model of crime control became the norm, which was based on gathering information about groups to assess the “risk” they posed. Rather than wait for the perpetrator to commit a crime, risk assessment methods called for new forms of “preventive surveillance,” in which whole groups of people seen as dangerous were subject to observation, identification, and classification.51 The War on Drugs—launched by President Reagan in 1982—dramatically accelerated the process of racial securitization. Michelle Alexander notes that At the time he declared this new war, less than 2 percent of the American public viewed drugs as the most important issue facing the nation. This fact was no deterrent to Reagan, for the drug war from the outset had little to do with public concern about drugs and much to do with public concern about race. By waging a war on drug users and dealers, Reagan made good on his promise to crack down on the racially defined “others”—the undeserving.52 Operation Hammer, carried out by the Los Angeles Police Department in 1988, illustrates how racialized surveillance was central to the War on Drugs. It involved hundreds of officers in combat gear sweeping through the South Central area of the city over a period of several weeks, making 1,453 arrests, mostly for teenage curfew violations, disorderly conduct, and minor traffic offenses. Ninety percent were released without charge but the thousands of young Black people who were stopped and processed in mobile booking centers had their names entered onto the “gang register” database, which soon contained the details of half of the Black youths of Los Angeles. Entry to the database rested on such supposed indicators of gang membership as high-five handshakes and wearing red shoelaces. Officials compared the Black gangs they were supposedly targeting to the National Liberation Front in Vietnam and the “murderous militias of Beirut,” signaling the blurring of boundaries between civilian policing and military force, and between domestic racism and overseas imperialism.53 In the twelve years leading up to 1993, the rate of incarceration of Black Americans tripled,54 establishing the system of mass incarceration that Michelle Alexander refers to as the new Jim Crow.55 And yet those in prison were only a quarter of those subject to supervision by the criminal justice system, with its attendant mechanisms of routine surveillance and “intermediate sanctions,” such as house arrests, boot camps, intensive supervision, day reporting, community service, and electronic tagging. Criminal records databases, which are easily accessible to potential employers, now hold files on around one-third of the adult male population.56 Alice Goffman has written of the ways that mass incarceration is not just a matter of imprisonment itself but also the systems of policing and surveillance that track young Black men and label them as would-be criminals before and after their time in prison. From stops on the street to probation meetings, these systems, she says, have transformed poor Black neighborhoods into communities of suspects and fugitives. A climate of fear and suspicion pervades everyday life, and many residents live with the daily concern that the authorities will seize them and take them away.57 A predictable outcome of such systems of classification and criminalization is the routine racist violence carried out by police forces and the regular occurrences of police killings of Black people, such as Michael Brown in Ferguson, Missouri, on August 9, 2014. The mass surveillance of Muslim Americans Discussions of the surveillance of Muslim Americans usually begin with 9/11 and make little attempt to locate them in the longer history of racial surveillance in the United States. Yet the continuities are striking, particularly for Black Muslims, who have been seen as extremists and subject to national security monitoring since the 1940s. Already in the late 1960s, Arab American student groups involved in supporting the Palestinian national movement had come under surveillance and, in 1972, the Nixon administration issued a set of directives known as Operation Boulder that enabled the CIA and FBI to coordinate with the pro-Israel lobby in monitoring Arab activists. By the 1980s, but especially after 9/11, a process was under way in which “Muslimness” was racialized through surveillance—another scene of the state’s production of racial subjects. Since all racisms are socially and politically constructed rather than resting on the reality of any biological “race,” it is perfectly possible for cultural markers associated with Muslimness (forms of dress, rituals, languages, etc.) to be turned into racial signifiers.58 This signification then serves to indicate a people supposedly prone to violence and terrorism, which, under the War on Terror, justifies a whole panoply of surveillance and criminalization, from arbitrary arrests, to indefinite detention, deportation, torture, solitary confinement, the use of secret evidence, and sentencing for crimes that “we” would not be jailed for, such as speech, donations to charitable organizations, and other such acts considered material support for terrorism. Significantly, the racial underpinnings of the War on Terror sustain not just domestic repression but foreign abuses—the war’s vast death toll in Afghanistan, Iraq, Pakistan, Somalia, Yemen, and elsewhere could not be sustained without the dehumanization of its Muslim victims. As before, racism at home goes hand in hand with empire abroad. Counterinsurgency thinking that informed the strategies used in Iraq and Afghanistan in the face of popular insurrection are also brought home to be deployed in relation to Muslim American populations. Winning “hearts and minds,” the counterinsurgency slogan first introduced by British colonialists in Malaya, and then adopted by the US military in Vietnam, reappears as the phrase that state planners invoke to prevent “extremism” among young Muslims in the United States. Counterinsurgency in this context means total surveillance of Muslim populations, and building law enforcement agency partnerships with “good Muslims,” those who are willing to praise US policy and become sources of information on dissenters, making life very difficult for “bad Muslims” or those who refuse (in ways reminiscent of the “good” and “bad” Indians). It is a way of ensuring that the knowledge Muslims tend to have of how US foreign policy harms the Middle East, Africa, and Asia is not shared with others. The real fear of the national security state is not the stereotypical Muslim fanatic but the possibility that other groups within US society might build alliances with Muslims in opposition to empire. The various measures that the US national security system has adopted in recent years flow from an analysis of Muslim “radicalization,” which assumes that certain law-abiding activities associated with religious ideology are indicators of extremism and potential violence. Following the preventive logic discussed above, the radicalization model claims to be able to predict which individuals are not terrorists now but might be at some later date. Behavioral, cultural, and ideological signals are assumed to reveal who is at risk of turning into a terrorist at some point in the future.59 For example, in the FBI’s radicalization model, such things as growing a beard, starting to wear traditional Islamic clothing, and becoming alienated from one’s former life are listed as indicators, as is “increased activity in a pro-Muslim social group or political cause.”60 Thus, signifiers of Muslimness such as facial hair, dress, and so on are turned into markers of suspicion for a surveillance gaze that is also a racial (and gendered) gaze; it is through such routine bureaucratic mechanisms that counterterrorism practices involve the social construction of racial others. Official acceptance of the model of radicalization implies a need for mass surveillance of Muslim populations and collection of as much data as possible on every aspect of their lives in order to try to spot the supposed warning signs that the models list. And this is exactly the approach that law enforcement agencies introduced. At the New York Police Department, for instance, the instrumentalizing of radicalization models led to the mass, warrantless surveillance of every aspect of Muslim life. Dozens of mosques in New York and New Jersey and hundreds more “hot spots,” such as restaurants, cafés, bookshops, community organizations, and student associations were listed as potential security risks. Undercover officers and informants eavesdropped at these “locations of interest” to listen for radical political and religious opinions. A NYPD “Moroccan Initiative” compiled a list of every known Moroccan taxi driver. Muslims who changed their names to sound more traditionally American or who adopted Arabic names were investigated and catalogued in secret NYPD intelligence files. It is clear that none of this activity was based on investigating reasonable suspicions of criminal activity. This surveillance produced no criminal leads between 2006 and 2012, and probably did not before or after.61 As of 2008, the FBI had a roster of 15,000 paid informants62 and, according to Senator Dianne Feinstein of the Senate Intelligence Committee, the bureau had 10,000 counterterrorism intelligence analysts in 2013.63 The proportion of these informants and analysts who are assigned to Muslim populations in the United States is unknown but is likely to be substantial. The kinds of infiltration and provocation tactics that had been practiced against Black radicals in the 1960s are being repeated today. What has changed are the rationales used to justify them: it is no longer the threat of Black nationalist subversion, but the threat of Muslim radicalization that is invoked. With new provisions in the Clinton administration’s 1996 Antiterrorism and Effective Death Penalty Act, the FBI can launch investigations of a suspected individual or organization simply for providing “material support” to terrorism—a vague term that could include ideological activity unrelated to any actual plot to carry out violence. While COINTELPRO violated federal laws, today similar kinds of investigation and criminalization of political dissent can be carried out legitimately in the name of countering terrorism. For Muslim populations on the receiving end of state surveillance programs designed to prevent “radicalization,” everyday life increasingly resembles the patterns described in classic accounts of authoritarianism. There is the same sense of not knowing whom to trust and choosing one’s words with special care when discussing politics, and of the arbitrariness and unpredictability of state power.64 With the 2011 leaking of some NYPD intelligence files, individual Muslims have had the disturbing experience of seeing their names mentioned in government files, along with details of their private lives. Numerous businesses, cafés, restaurants, and mosques in New York are aware that the NYPD considers them hotspots and deploys informants to monitor them. And the recent outing of a small number of NYPD informants has meant some Muslims in New York have found that relationships they thought of as genuine friendships were actually covert attempts to gather intelligence.65 Racial security in the “post-racial” era The election of Barack Obama as president in 2008 was said to have ushered in a new “post-racial” era, in which racial inequalities were meant to be a thing of the past. African Americans and Muslim Americans placed their hopes in Obama, voting for him in large numbers. But in the so-called post-racial era, the security narrative of hardworking families (coded white) under threat from dangerous racial others has been as powerful as ever. The unprecedented mass deportation of more than two million people during the Obama presidency is one form taken by this post-racial racialized securitization. Over the last two decades, the progressive criminalization of undocumented immigrants has been achieved through the building of a militarized wall between Mexico and the United States, hugely expanding the US border patrol, and programs such as Secure Communities, which enables local police departments to access immigration databases. Secure Communities was introduced in 2008 and stepped up under Obama. It has resulted in migrants being increasingly likely to be profiled, arrested, and imprisoned by local police officers, before being passed to the federal authorities for deportation. Undocumented migrants can no longer have any contact with police officers without risking such outcomes. There is an irony in the way that fears of “illegal immigration” threatening jobs and the public purse have become stand-ins for real anxieties about the neoliberal collapse of the old social contract: the measures that such fears lead to—racialization and criminalization of migrants—themselves serve to strengthen the neoliberal status quo by encouraging a precarious labor market. Capital, after all, does not want to end immigration but to profit from “a vast exploitable labor pool that exists under precarious conditions, that does not enjoy the civil, political and labor rights of citizens and that is disposable through deportation.”66 What brings together these different systems of racial oppression—mass incarceration, mass surveillance, and mass deportation—is a security logic that holds the imperial state as necessary to keeping “American families” (coded white) safe from threats abroad and at home. The ideological work of the last few decades has cultivated not only racial security fears but also an assumption that the security state is necessary to keep “us” safe. In this sense, security has become the new psychological wage to aid the reallocation of the welfare state’s social wage toward homeland security and to win support for empire in the age of neoliberalism. Through the notion of security, social and economic anxieties generated by the unraveling of the Keynesian social compact have been channeled toward the Black or Brown street criminal, welfare recipient, or terrorist. In addition, as Susan Faludi has argued, since 9/11, this homeland in need of security has been symbolized, above all, by the white domestic hearth of the prefeminist fifties, once again threatened by mythical frontier enemies, hidden subversives, and racial aggressors. That this idea of the homeland coincides culturally with “the denigration of capable women, the magnification of manly men, the heightened call for domesticity, the search for and sanctification of helpless girls” points to the ways it is gendered as well as racialized.67 The post-Snowden debate The mechanisms of surveillance outlined in this essay were responses to political struggles of various kinds—from anticolonial insurgencies to slave rebellions, labor militancy to anti-imperialist agitation. Surveillance practices themselves have also often been the target of organized opposition. In the 1920s and 1970s, the surveillance state was pressured to contract in the face of public disapproval. The antiwar activists who broke into an FBI field office in Media, Pennsylvania, in 1971 and stole classified documents managed to expose COINTELPRO, for instance, leading to its shut down. (But those responsible for this FBI program were never brought to justice for their activities and similar techniques continued to be used later against, for example in the 1980s, the American Indian Movement, and the Committee in Solidarity with the People of El Salvador.68) Public concern about state surveillance in the 1970s led to the Church committee report on government spying and the Handschu guidelines that regulated the New York Police Department’s spying on political activities. Those concerns began to be swept aside in the 1980s with the War on Drugs and, especially, later with the War on Terror. While significant sections of the public may have consented to the security state, those who have been among its greatest victims—the radical Left, antiwar activists, racial justice and Black liberation campaigners, and opponents of US foreign policy in Latin America and the Middle East— understand its workings. Today, we are once again in a period of revelation, concern, and debate on national security surveillance. Yet if real change is to be brought about, the racial history of surveillance will need to be fully confronted—or opposition to surveillance will once again be easily defeated by racial security narratives. The significance of the Snowden leaks is that they have laid out the depth of the NSA’s mass surveillance with the kind of proof that only an insider can have. The result has been a generalized level of alarm as people have become aware of how intrusive surveillance is in our society, but that alarm remains constrained within a public debate that is highly abstract, legalistic, and centered on the privacy rights of the white middle class. On the one hand, most civil liberties advocates are focused on the technical details of potential legal reforms and new oversight mechanisms to safeguard privacy. Such initiatives are likely to bring little change because they fail to confront the racist and imperialist core of the surveillance system. On the other hand, most technologists believe the problem of government surveillance can be fixed simply by using better encryption tools. While encryption tools are useful in increasing the resources that a government agency would need to monitor an individual, they do nothing to unravel the larger surveillance apparatus. Meanwhile, executives of US tech corporations express concerns about loss of sales to foreign customers concerned about the privacy of data. In Washington and Silicon Valley, what should be a debate about basic political freedoms is simply a question of corporate profits.69 Another and perhaps deeper problem is the use of images of state surveillance that do not adequately fit the current situation—such as George Orwell’s discussion of totalitarian surveillance. Edward Snowden himself remarked that Orwell warned us of the dangers of the type of government surveillance we face today.70 Reference to Orwell’s 1984 has been widespread in the current debate; indeed, sales of the book were said to have soared following Snowden’s revelations.71 The argument that digital surveillance is a new form of Big Brother is, on one level, supported by the evidence. For those in certain targeted groups—Muslims, left-wing campaigners, radical journalists—state surveillance certainly looks Orwellian. But this level of scrutiny is not faced by the general public. The picture of surveillance today is therefore quite different from the classic images of surveillance that we find in Orwell’s 1984, which assumes an undifferentiated mass population subject to government control. What we have instead today in the United States is total surveillance, not on everyone, but on very specific groups of people, defined by their race, religion, or political ideology: people that NSA officials refer to as the “bad guys.” In March 2014, Rick Ledgett, deputy director of the NSA, told an audience: “Contrary to some of the stuff that’s been printed, we don’t sit there and grind out metadata profiles of average people. If you’re not connected to one of those valid intelligence targets, you are not of interest to us.”72 In the national security world, “connected to” can be the basis for targeting a whole racial or political community so, even assuming the accuracy of this comment, it points to the ways that national security surveillance can draw entire communities into its web, while reassuring “average people” (code for the normative white middle class) that they are not to be troubled. In the eyes of the national security state, this average person must also express no political views critical of the status quo. Better oversight of the sprawling national security apparatus and greater use of encryption in digital communication should be welcomed. But by themselves these are likely to do little more than reassure technologists, while racialized populations and political dissenters continue to experience massive surveillance. This is why the most effective challenges to the national security state have come not from legal reformers or technologists but from grassroots campaigning by the racialized groups most affected. In New York, the campaign against the NYPD’s surveillance of Muslims has drawn its strength from building alliances with other groups affected by racial profiling: Latinos and Blacks who suffer from hugely disproportionate rates of stop and frisk. In California’s Bay Area, a campaign against a Department of Homeland Security-funded Domain Awareness Center was successful because various constituencies were able to unite on the issue, including homeless people, the poor, Muslims, and Blacks. Similarly, a demographics unit planned by the Los Angeles Police Department, which would have profiled communities on the basis of race and religion, was shut down after a campaign that united various groups defined by race and class. The lesson here is that, while the national security state aims to create fear and to divide people, activists can organize and build alliances across race lines to overcome that fear. To the extent that the national security state has targeted Occupy, the antiwar movement, environmental rights activists, radical journalists and campaigners, and whistleblowers, these groups have gravitated towards opposition to the national security state. But understanding the centrality of race and empire to national security surveillance means finding a basis for unity across different groups who experience similar kinds of policing: Muslim, Latino/a, Asian, Black, and white dissidents and radicals. It is on such a basis that we can see the beginnings of an effective multiracial opposition to the surveillance state and empire. Surveillance Good – Starting Point Surveillance Good – Comes First Surveillance Good – Starting Point Domestic surveillance is a necessary starting point – surveillance is a critical facet in the historically contingent construction of race under the neoliberal order of Empire. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] In what follows, we argue that the debate on national security surveillance that has emerged in the United States since the summer of 2013 is woefully inadequate, due to its failure to place questions of race and empire at the center of its analysis. It is racist ideas that form the basis for the ways national security surveillance is organized and deployed, racist fears that are whipped up to legitimize this surveillance to the American public, and the disproportionately targeted racialized groups that have been most effective in making sense of it and organizing opposition. This is as true today as it has been historically: race and state surveillance are intertwined in the history of US capitalism. Likewise, we argue that the history of national security surveillance in the United States is inseparable from the history of US colonialism and empire. The argument is divided into two parts. The first identifies a number of moments in the history of national security surveillance in North America, tracing its imbrication with race, empire, and capital, from the settler-colonial period through to the neoliberal era. Our focus here is on how race as a sociopolitical category is produced and reproduced historically in the United States through systems of surveillance. We show how throughout the history of the United States the systematic collection of information has been interwoven with mechanisms of racial oppression. From Anglo settler-colonialism, the establishment of the plantation system, the post–Civil War reconstruction era, the US conquest of the Philippines, and the emergence of the national security state in the postWorld War II era, to neoliberalism in the post-Civil Rights era, racialized surveillance has enabled the consolidation of capital and empire. It is, however, important to note that the production of the racial “other” at these various moments is conjunctural and heterogenous. That is, the racialization of Native Americans, for instance, during the settler-colonial period took different forms from the racialization of African Americans. Further, the dominant construction of Blackness under slavery is different from the construction of Blackness in the neoliberal era; these ideological shifts are the product of specific historic conditions. In short, empire and capital, at various moments, determine who will be targeted by state surveillance, in what ways, and for how long. In the second part, we turn our attention to the current conjuncture in which the politics of the War on Terror shape national security surveillance practices. The intensive surveillance of Muslim Americans has been carried out by a vast security apparatus that has also been used against dissident movements such as Occupy Wall Street and environmental rights activists, who represent a threat to the neoliberal order. This is not new; the process of targeting dissenters has been a constant feature of American history. For instance, the Alien and Sedition Acts of the late 1790s were passed by the Federalist government against the Jeffersonian sympathizers of the French Revolution. The British hanged Nathan Hale because he spied for Washington’s army in the American Revolution. State surveillance regimes have always sought to monitor and penalize a wide range of dissenters, radicals, and revolutionaries. Race was a factor in some but by no means all of these cases. Our focus here is on the production of racialized “others” as security threats and the ways this helps to stabilize capitalist social relations. Further, the current system of mass surveillance of Muslims is analogous to and overlaps with other systems of racialized security surveillance that feed the mass deportation of immigrants under the Obama administration and that disproportionately target African Americans, contributing to their mass incarceration and what Michelle Alexander refers to as the New Jim Crow.4 We argue that racialized groupings are produced in the very act of collecting information about certain groups deemed as “threats” by the national security state—the Brown terrorist, the Black and Brown drug dealer and user, and the immigrant who threatens to steal jobs. We conclude that “security” has become one of the primary means through which racism is ideologically reproduced in the “post-racial,” neoliberal era. Drawing on W. E. B. Dubois’s notion of the “psychological wage,” we argue that neoliberalism has been legitimized in part through racialized notions of security that offer a new “psychological wage” as compensation for the decline of the social wage and its reallocation to “homeland security.” Anti-Blackness Adv Uniqueness – Racial Targeting Now Black peace movements are being labeled as terrorists in the SQ PARTON ’15 (HEATHER DIGBY PARTON, a political writer for Salon.com, “A racial “Big Brother” debacle: Why is the government spying on Black Lives Matter protests?”, Salon.com, THURSDAY, MAR 19, 2015 02:22 PM EDT, http://www.salon.com/2015/03/19/a_racial_big_brother_debacle_why_is_the_g overnment_spying_on_black_lives_matter_protests/, Accessed July 2015, CMT) After all, in these days of hyper awareness over the terrorist threat, it doesn’t take much imagination to see how that sort of thing could get out of hand, so it’s important that they follow the rules. Now there was a time when the cause of anti-communism required that we be extra-vigilant because the Russians were coming and dissent was closely monitored by police and the FBI in order that the government keep tabs on all those potential commie infiltrators such as Martin Luther King and John Lennon. And even quite recently, it was found that the authorities had peace activists under surveillance in the wake of 9/11. The Washington Post reported in 2006: A database managed by a secretive Pentagon intelligence agency called Counterintelligence Field Activity, or CIFA, was found last month to contain reports on at least four dozen antiwar meetings or protests, many of them on college campuses. Ten peace activists who handed out peanut butter and jelly sandwiches outside Halliburton’s headquarters in Houston in June 2004 were reported as a national security threat. So were people who assembled at a Quaker meeting house in Lake Worth, Fla., or protested military recruiters at sites such as New York University, the State University of New York and campuses of the University of California at Berkeley and at Santa Cruz. The protesters were written up under a Pentagon program called Talon, which is supposed to collect raw data on threats to defense facilities in the United States. CIFA, an agency created just under four years ago that now includes nine directorates and more than 1,000 employees, is charged with working to prevent terrorist attacks. The logic that peace activists must be in league with terrorists has never been adequately explained, but it follows along the same line of thought which leads conservatives to assume that decadent left-wing hippies are natural allies of Muslim fundamentalists. FYI- Many different types of anti-black surveillance KHALEK ‘13 (RANIA KHALEK, an independent journalist reporting on the underclass and marginalized who has written for Extra, The Nation, Al Jazeera America “Activists of Color Lead Charge Against Surveillance, NSA”, Truth-out.org, Published 30 October 2013, http://www.truth-out.org/news/item/19695activists-of-color-at-forefront-of-anti-nsa-movement, Accessed July 7th 2015, CMT) "We been exposed to this type of surveillance since we got here," declared Kymone Freeman, director of the National Black LUV Fest as he emceed the historic rally against NSA surveillance in Washington, DC. He continued, "Drones is [are] a form of surveillance. Racial profiling is a form of surveillance. Stop-and-frisk is a form of surveillance. We all black today!" Mass surveillance in communities of color increase the amount of minorities in the criminal justice system KHALEK ‘13 (RANIA KHALEK, an independent journalist reporting on the underclass and marginalized who has written for Extra, The Nation, Al Jazeera America “Activists of Color Lead Charge Against Surveillance, NSA”, Truth-out.org, Published 30 October 2013, http://www.truth-out.org/news/item/19695activists-of-color-at-forefront-of-anti-nsa-movement, Accessed July 7th 2015, CMT) Steven Renderos, national organizer for the Center for Media Justice, who helped put together the panel, told Truthout that examining the legacy of surveillance in communities of color could help lead to solutions. "It's critical to understand the history so we can learn how to dismantle it," Renderos said. "Those of us from marginalized communities grew up in environments very much shaped by surveillance, which has been utilized to ramp up the criminal justice system and increase deportations," Renderos said. "It's having real consequences in our communities where children are growing up without parents in the home and families are being torn apart through raids and deportations, a lot of which is facilitated through the use of surveillance." Panelist Fahd Ahmed, legal and policy director for the South Asian-led social justice organization Desis Rising Up and Moving, argued that mass surveillance is the predictable outgrowth of programs that have targeted marginalized communities for decades. "Just by the very nature of [the United States] being a settler-colonialist and capitalist nation, race and social control are central to its project," Ahmed said. "Anytime we see any levels of policing - whether it's day-to-day policing in the streets, surveillance by the police or internet surveillance - social control, particularly of those that resist the existing system, becomes an inherent part of that system." But, he warned, "These policies are not going to be limited to one particular community. They're going to continue to expand further and further" because "the surveillance has a purpose, which is to exert the power of the state and control the potential for dissent." Seema Sadanandan, program director for ACLU DC, acknowledged the collective resentment felt by people of color who are understandably frustrated that privacy violations are only now eliciting mass public outrage when communities of color have been under aggressive surveillance for decades. "The Snowden revelations represent a terrifying moment for white, middle-class and upper-middle-class people in this country, who on some level believe that the Bill of Rights and Constitution were protecting their everyday lives," The black community has and will always been surveilled, empirics prove Kayyali ’14 (Nadia Kayyali, Nadia earned a B.A. from UC Berkeley with a major in Cultural Anthropology and minored in Public Policy, “The History of Surveillance and the Black Community”, eff.com, published February 13, 2014, https://www.eff.org/deeplinks/2014/02/history-surveillance-and-blackcommunity, Accessed July 7th 2015, CMT) Government surveillance programs, most infamously the FBI’s “COINTELPRO”, targeted Black Americans fighting against segregation and structural racism in the 1950s and 60s. COINTELPRO, short for Counter Intelligence Program, was started in 1956 by the FBI and continued until 1971. The program was a systemic attempt to infiltrate, spy on, and disrupt activists in the name of “national security.” While it initially focused on the Communist Party, in the 1960s its focus expanded to include a wide swathe of activists, with a strong focus on the Black Panther Party and civil rights leaders such as Dr. Martin Luther King, Jr. FBI papers show that in 1962 “the FBI started and rapidly continued to gravitate toward Dr. King.” This was ostensibly because the FBI believed black organizing was being influenced by communism. In 1963 FBI Assistant Director William Sullivan recommended “increased coverage of communist influence on the Negro.” However, the FBI’s goal in targeting Dr. King was clear: to find “avenues of approach aimed at neutralizing King as an effective Negro leader,” because the FBI was concerned that he might become a “messiah.” Anti-Blackness Adv – Surveillance Bad Threat-constructing Surveillance rhetoric justifies racism as: “necessary for the common good”. This normalizes racism and makes it invisible even to its victims. Declaring Solidarity with the victims is necessary to solve this discrimination. Prison Culture ’13 (June 12 2013, Site dedicated to exposing racism of the military-industrial complex, “On (Some) Black People and the Surveillance State…”, http://www.usprisonculture.com/blog/2013/06/12/on-some-black-people-and-thesurveillance-state/ DA: 7/6/15 CB) Some black folks in my life have no patience for some white people’s new found interest/discovery of Cointelpro and particularly of their (now incessant) invocation of the FBI’s surveillance of Martin Luther King Jr. The interest seems to them instrumental and transactional. It’s as if folks who have had little concern about black people’s daily experiences of state violence are now demanding our support in safeguarding their rights. There has been no prior relationship or trust-building so some black folks are feeling used and exploited. It brings to mind the lyric: “Will you still love me, tomorrow?” This sentiment is understandable. As the revelations about NSA surveillance roil the political world, media outlets & others are suddenly very interested in Americans’ views on matters of privacy, civil liberties, and individual rights. A poll was released a few days ago. It apparently found that “blacks were more likely than whites and hispanics to consider the patriot act a necessary tool [that helps the government find terrorists] (58% to 42% and 40% respectively). On my Twitter timeline, several people mused about why this would be the case. After all, black people are the disproportionate targets of government surveillance at all levels (city, county, state, and federal). We’ve always been under the gaze of the state and we know that our rights are routinely violable. Moreover, we are used to these abuses being ignored by the majority of our fellow citizens. Shouldn’t black people then be the most opposed to violations of civil liberties and to laws that encroach on those liberties? Civil liberties and individual rights have different meanings for different groups of people. They also have different priorities depending on social contexts. A review of black history suggests that considerations of civil liberties are always embedded within concepts of equality and social justice. In other words by design or necessity, black people have focused on our collective rights over our individual liberties. This makes sense in a society where we don’t just assume individual black guilt and suspicion. We are all guilty and we are all suspicious (even if we may want to deny this reality). In that context, individual liberties and rights take a back seat to a collective struggle for emancipation and freedom. Additionally, as a people, we have always known that it is impossible for us to exercise our individual rights within a context of more generalized social, economic, and political oppression. Individual rights are necessarily rooted within a larger social context. Civil liberty concerns take a back seat to putting food on the table and to survival more generally. To guarantee our individual rights as black people, we know that we must address broader social concerns. We don’t have the luxury to ignore this fact. For others not to understand this reality is to foreclose on any opportunities to recruit more black people to the cause of dismantling the surveillance state. Returning to the poll: what might account for a majority of (polled) black people’s seeming ‘support’ of using the Patriot act to find ‘terrorists?’ Are they indirectly expressing their support for President Obama’s foreign policy through their response? It’s possible. Are some black people answering yes & perhaps hoping that concentrating on ‘terrorists’ might shift the focus away from the government’s targeting of African-Americans? Maybe. It isn’t crazy to think that if the government develops a new public enemy #1, it might lower its black people as threat matrix just a little bit. This is of course wishful thinking but it’s a plausible explanation. My personal hypothesis is that black people living in the U.S. are Americans and that we have, like millions of other Americans, bought into some of the law & order rhetoric espoused by the government. In this context, it should be unsurprising that some black people would express support for the Patriot act. Many other Americans do too. picimage2 Black people are disproportionately incarcerated in the U.S. Prisoners have no presumption of ‘privacy'; that idea is an abstraction. Blacks are disproportionately subjected to bodily searches and seizures through practices like stop and frisk. Stop and frisk is a neon ‘no tresspassing sign’ for young black people in particular. Unfortunately too many of us have become acclimated to the daily assaults on our persons and the trampling of our individual rights. Can you blame us? If you are a black woman, then you may have the direct experience of the state policing your body in various ways. Many of us resist policies intended to do this but some of us don’t (for a number of good and bad reasons). The examples that I have cited suggest that for most of us (black people) government surveillance and being perceived as threats are a daily fact of life; not an academic/analytical exercise. Many black people living in public housing, for example, can attest to the fact that they aren’t seen as having any privacy rights when law enforcement routinely kicks down their doors supposedly looking for narcotics. The vast majority of the country accepts these “law and order” practices as the price of “freedom” and “safety.” The outcry against mass incarceration and stop & frisk is still overwhelmingly confined to people of color and other marginalized communities like LGBTQ individuals. Yet even in those communities, many have become inured to the routine violations of rights and liberties. In order to have an elusive sense of “safety,” we are told by politicians and law enforcement that these practices are necessary and that they are in fact “color-blind.” We mostly swallow their propaganda. It doesn’t matter that incarceration and intense policing & surveillance are actually decimating black communities. Black people know that the state and its gatekeepers exert their control over all aspects of our lives. So when we mention that the NSA surveillance regime isn’t new to us, the appropriate response is not to mock, ridicule, belittle and berate. No. The response that conveys solidarity and a desire to partner is to say: “Yes that’s true and while I may have been personally concerned about these issues, I am sorry that more of my peers haven’t been outraged for years. How can we work together to dismantle the surveillance state that harms us all?” Check your privilege, please. Anti-Blackness ADv – Colorblindness Bad Colorblindness is the experiences of different racial groups become overlooked. Hobson ‘15 Mellody Hobson is an American businesswoman who is the president of Ariel Investments and the current Chairman of the Board of Directors of Dreamworks Animation. Feburary 3 2015. “Colorblindness vs. ColorBRAVE”. Progressive Pupil. https://progressivepupil.wordpress.com/2015/02/03/colorblindess-vs-colorbrave/. July 9, 2015 In her Ted Talk, Mellody Hobson, a Financial Executive, discusses her stance on colorblindness. She opens the Ted Talk by acknowledging that race in our country is an uncomfortable subject. However, by using her personal experiences as a successful Black women in a field dominated by White men, she provides compelling arguments as to why we should no longer be colorblind, but start the conversation of race in the workplace. Colorblindness is a term used to describe one’s ability or choice to disregard and/or overlook race. Variations of phrases similar to “I don’t see color” are distinct examples. As Hobson points out, avoiding the topic of race is not the answer, for it mutes the discussion of diversity and inclusiveness ultimately. This neglects a significance piece of one’s identity. I personally remember a time when the people around me chose to be colorblind. It was my freshman year of high school, and I was the only Black person on our cheerleading team. One of our away games took place in a very conservative town in North Georgia. There were approximately fifteen people of color in the entire gym, including the members of our basketball team and their families. At some point, the game got heated; racial slurs and threats were exchanged to the Black basketball players and myself. Yes I was upset in that moment, but I remember feeling more disappointed that the other cheerleaders chose it act like it didn’t happen. My race was never discussed during practices or at games. The only reference to my color would arise while trying to explain to my coaches that my hair does not curl while in box braids. My teammates and coaches chose to overlook the difference in my hair, just like they did during the Georgia situation. I wanted them to acknowledge that my Blackness made me a victim to racial threats. So no, they did not spit out the racial slurs, but choosing to not acknowledge my race and the experiences that come with it, is form of racism. While some choose to be colorblind, others seem to be on the opposite end of the extreme by being color conscious. Color Consciousness is when one thinks they are aware of someone’s reality due to the assumptions they have about their race. While I do think it’s important to be aware of race, assuming to know anyone’s reality without being that person can be offensive. During her Ted Talk Hobson stated that she was recently mistaken for kitchen help. Though I don’t have details about the situation, I believe her skin color played a role is one’s decision to mistake her as kitchen help. Concluding her Ted Talk Hobson challenged us to be Colorbrave. We have to start creating spaces where we can have these difficult conversations. As Hobson stated if we don’t begin this conversation about race and discrimination it threatens to rob another generation of all the opportunities wanted for them regardless of the color of their skin. Colorblindness isn’t actually color blind; it’s a hidden form of racism. Color consciousness is better. Wilkins ‘96 David Wilkins is the Lester Kissel Professor of Law, and Faculty Director of the Program on the Legal Profession and the Center on Lawyers and the Professional Services Industry at Harvard Law School. He is a Senior Research Fellow of the American Bar Foundation, the Harvard Law School's Vice Dean for Global Initiatives on the Legal Profession, and a Faculty Associate of the Harvard University Edmond J. Safra Foundation Center for Ethics. “Color Conscious: The Political Morality of Race” https://thenatureofrace.files.wordpress.com/2014/01/color-conscious-the-political-morality-of-race-copy.pdf. July 9, 2015. Not only are we as a nation destined to fail to solve the problem of the color-line in this century, but we are in danger of losing our ability even to talk about the subject intelligently. Far too often, speakers on both sides of contemporary debates about race acknowledge only half of America’s complex racial legacy. Those who oppose taking race into account, for example, when awarding benefits or designing educational curricula, point to the fact that our political institutions rest on principles of individual freedom and equality that expressly deny the moral or political significance of ascriptive characteristics such as race. Echoing Justice Harlan’s famous dissent in Plessy v. Fergusson, these advocates passionately assert that “our Constitution is color blind,” and morality is as well.2 Supporters of affirmative action or multiculturalism, on the other hand, cite the fact that Americans— frequently acting in the name of individual freedom and equality—exterminated the indigenous Native American population, kidnapped and enslaved millions of Africans, held JapaneseAmericans (but not German-Americans) in internment camps during World War II, and, from 1790 to 1952, restricted legal naturalization to “white” persons. For these advocates, “color blindness” in our political and moral discourse has been little more than a smoke screen for the pervasive “color consciousness” (and, more specifically, white supremacy) that has been a dominant feature of the American saga since the Pilgrims first landed on Plymouth Rock. Given this dual legacy, it is not surprising, as Anthony Appiah observes in his thoughtful epilogue to this volume, that so much of what is said today about race is “dishonest, confused, illinformed, unhelpful.” If we are to fare any better on Du Bois’s challenge in the next century, we must create a discourse about race that acknowledges both parts of America’s racial heritage. This volume is an attempt to create such a discourse. It does so by bringing together two leading scholars and, to quote Appiah again, “passionate democrats,” to ask the kind of probing and critical questions about the meaning and significance of race that are rarely addressed in our sound bite culture. Each author brings a wealth of experience and expertise to the task. Anthony Appiah has written extensively about a wide range of topics relating to African and African-American intellectual history and literary studies, ethics, and the philosophy of mind and language. Amy Gutmann is one of the country’s leading scholars in the fields of democratic theory, ethics, and public education. In the essays that follow, both these accomplished authors strive to give an account of race in contemporary American society that pays due regard both to the promise of America’s ideals and to its persistent failure to live up to these noble aspirations. Appiah’s essay, entitled “Race, Culture, Identity: Misunderstood Connections,” explores the role of race in the formation of individual identity. His central claim is that the concept of race 2 Plessy v. Fergusson, 163 U.S. 537 (1896), p. 559. 4 INTRODUCTION: THE CONTEXT OF in this country neither adequately explains existing American social distinctions nor properly acts as a surrogate for culture or identity. Although America’s history of racial oppression creates a role for “racial identities,” Appiah concludes, if we are ever to realize the promise of individual freedom and equality embedded in the other part of our racial heritage, “we shall have, in the end, to move beyond current racial identities.” In “Responding to Racial Injustice,” Amy Gutmann brings the two parts of America’s RACE developed racial dilemma together to provide a “color blind” argument in favor of “color consciousness” in public policy. Gutmann argues that in order to treat individuals fairly, the ultimate goal of a just society, it will sometimes be necessary to enact color conscious policies that recognize the extent to which race continues to influence the life chances of citizens. At the same time, Gutmann insists, these policies must also be consistent with the truth about color blindness that all persons, regardless of their skin color, are civic equals. Only those color conscious public policies that are both instrumentally valuable to overcoming racial injustice and consistent with the fundamental equality of all human beings, Gutmann concludes, are justifiable in a democracy that hopes one day to live up to its professed ideals. Color Consciousness is superior to color blindness. Chaky 14 Chris Chaky, Muhlenberg College, Politics Department, Undergraduate. Studies History, International Relations, and Cultural Studies. “Thoughts of Color Conscious.” July 7 2014. Contemporary Racism. http://contemporaryracism.org/2744/thoughts-oncolor-consciousness/. July 9, 2015 The recent literature in social psychology and other disciplines is clear: colorblind racial ideology is a harmful way of viewing the world. By ignoring both the material disadvantages faced by people of color and the implicit racial biases that influence decision-making, subscribing to colorblind racial ideology leads people to ignore the realities of racism in modern America and thus oppose policies that would address racial inequalities. In a recent class, we discussed how some white people who subscribe to such an ideology will go to any length to avoid mentioning a person of color’s race. This avoidance occurs despite the fact that, in all likelihood, this person is thinking about the person of color’s race. Research has shown that people who practice this kind of avoidance are perceived by many people of color as more racially biased. The solution to colorblindness, then, is color-consciousness, which involves the active acknowledgment of race. One should not actively ignore the race of a person of color; one should feel free to discuss it. It is this recognition that can lead to an overcoming of system and implicit racial bias. All of this sounds good, but there is one issue I want to raise. It occurred to me that subscribing to a color-conscious ideology might be problematic if one only recognizes the races of people of color and ignores the race of white people. This reinforces white normativity, the idea that white is the default or normal identity in America. Any other race is different and even less American. How would this play out in the real world? Interpersonally, it could mean not just refusing to avoid using the race of people of color as a descriptor (granted, it should never be the only descriptor) but also actively using the race of white people as a descriptor. It could mean that one could discuss the effect race has not only on black politicians but also on white politicians. Do you think this is a good idea? Would such a strategy be able to gradually chip away at the dominance of white normativity? My reasoning is that calling attention to the fact that white Americans are in fact white will reduce the tendency to automatically associate white with American. It could also call attention to white privilege and not just the subordination of people of color. Racial color blindness is a form of modern day racism. Neville 11 Helen Neville Professor, Department of Psychology B.A., University of British Columbia M.A., Simon Fraser University Ph.D., Cornell University. August 17 2011. “Color-Blind Racial Ideology” http://studysites.sagepub.com/healeyregc6e/study/chapter/encycarticles/ch11/NEVILL~1.PDF. July 9, 2015 Over the past 2 decades scholars and popular authors have written about racial color-blindness as a way to characterize racial beliefs in the post–civil rights era. At its core, racial color-blindness refers to the belief that racism is a thing of the past and that race no longer plays a role in understanding people’s lived experience. Conceptually, racial color-blindness has its roots in the law field and traditionally has been applied mainly to the Constitution. More recently, scholars have redefined the term to better capture the new social relations within the current racial climate. As early as 1997, the field of psychology questioned the underlying assumption that ignoring race and color was a desirous and appropriate approach to interracial interactions. In a pamphlet on color-blind racial attitudes, the American Psychological Association (APA) concluded that “research conducted for more than two decades strongly supports the view that we cannot be, nor should we become, color-blind” (p. 3). The APA further provided a critique of the color-blind perspective, arguing that a color-blind approach “ignores research showing that, even among well-intentioned people, skin color . . . figures prominently in everyday attitudes and behavior” (p. 2). The APA thus argued that to get beyond racism it is essential to take into account differences between the lived experiences of people. There are a number of complementary but competing definitions of racial color-blindness. Couching racial color-blindness as an expression of modern-day racism, sociologist Eduardo Bonilla-Silva identified four frames or types: abstract liberalism (i.e., emphasizing political liberalism and the availability of equal opportunities to everyone, regardless of race, and the belief that political/economic interventions only serve to create a schism between racial groups); naturalism (i.e., interpreting racial clustering as a natural and preferred occurrence); cultural (i.e., using essentialist arguments to explain racial disparities, thus rooting racial differences in cultural practices); and minimization of racism in today’s society. Ruth Frankenberg, also a sociologist, viewed racial color-blindness as a perspective consisting of two types: color-evasion (i.e., placing an emphasis on racial sameness to the detriment of seeing or acknowledging differences in experiences and political realities) and power-evasion (i.e., the belief that resources are fairly distributed to everyone and success is attributed to individual effort). In the Guidelines on Multicultural Education, Training, Research, Practice, and Organizational Change for Psychologists, authored by the APA, the interpersonal aspects of racial colorblindness are emphasized. Based on this perspective potential racial differences are minimized in favor of universal or human experiences. There is a great deal of commonality across cultures; however, the color-blind perspective dismisses potential differences based on racial group membership and downplays how these differences may shape human experiences. This limited awareness of the manifestation of race and racism in society is the foundation for most conceptualizations of racial color-blindness. Regardless of the definition, racial color-blindness is also thought to help justify existing racial practices or policies that ultimately create and support existing racial inequalities. Consistent with these articulations, researchers argue that racial color-blindness reflects a broader ideological stance. Racial ideology is complex, but essentially it can be conceptualized as a global term referring to the dominant views about race within a hierarchical society. Ideology in this regard consists of a shared worldview about race that helps to justify and legitimize the current racial status quo; it accounts for individual beliefs and dominant societal racial beliefs or ideas that are commonly understood and transmitted through a variety of civil society and structural mechanisms. From this perspective racial color-blind ideology is a set of commonly held beliefs that minimize and distort the existence of institutional racism. This perspective is most consistent with the minimization type of color-blind racism identified by Bonilla-Silva and the power-evasion type proffered by Frankenberg. Recently, scholars have challenged the assumption of the emergence of a new racism. Based on the review of the interdisciplinary literature in the United States and in other English-speaking countries, Colin Wayne Leach concluded that old-fashioned racism or the endorsement of racial inferiority/superiority ideology and actions have not been supplanted by more covert forms of racial expressions. Although he did not name racial color-blindness in his critique, Leach raised questions about whether or not a shift has occurred in the manifestation of racism since the passage of civil rights laws. In sum, racial colorblindness is premised on the persistence of racism as manifested in contemporary racial disparities across a range of indexes, including housing, health, and employment. The complex set of beliefs used to restrict awareness of the persistence of racism is part of a larger ideological stance that serves to legitimize and further perpetuate racial inequalities. There is some debate about whether racial colorblindness is a new phenomenon or whether it reflects a dimension of racism that, until relatively recently, has received attention in the social science literature. Color blindness causes racial backgrounds, ethnic stories, heritage, and culture to be destroyed. Williams 11 Monnica T Williams received her Master's and Doctoral Degrees in clinical psychology from the University of Virginia, where she conducted research in the areas of psychopathology, tests and measurement, and ethnic differences,Dec 27, 2011 Psychology Today, ‘’Colorblind Ideology Is a Form of Racism’’, https://www.psychologytoday.com/blog/culturallyspeaking/201112/colorblind-ideology-is-form-racism, Date Accessed; July 9th, 2015 Racial issues are often uncomfortable to discuss and rife with stress and controversy. Many ideas have been advanced to address this sore spot in the American psyche. Currently, the most pervasive approach is known as colorblindness. Colorblindness is the racial ideology that posits the best way to end discrimination is by treating individuals as equally as possible, without regard to race, culture, or ethnicity. At its face value, colorblindness seems like a good thing — really taking MLK seriously on his call to judge people on the content of their character rather than the color of their skin. It focuses on commonalities between people, such as their shared humanity. However, colorblindness alone is not sufficient to heal racial wounds on a national or personal level. It is only a half-measure that in the end operates as a form of racism . Racism? Strong words, yes, but let's look the issue straight in its partially unseeing eye. In a colorblind society, White people, who are unlikely to experience disadvantages due to race, can effectively ignore racism in American life, justify the current social order, and feel more comfortable with their relatively privileged standing in society (Fryberg, 2010). Most minorities, however, who regularly encounter difficulties due to race, experience colorblind ideologies quite differently. Colorblindness creates a society that denies their negative racial experiences, rejects their cultural heritage, and invalidates their unique perspectives . Let's break it down into simple terms: Color-Blind = "People of color — we don't see you (at least not that bad ‘colored' part)." As a person of color, I like who I am, and I don't want any aspect of that to be unseen or invisible . The need for colorblindness implies there is something shameful about the way God made me and the culture I was born into that we shouldn't talk about. Thus, colorblindness has helped make race into a taboo topic that polite people cannot openly discuss. And if you can't talk about it, you can't understand it, much less fix the racial problems that plague our society. Many Americans view colorblindness as helpful to people of color by asserting that race does not matter (Tarca, 2005). But in America, most underrepresented minorities will explain that race does matter, as it affects opportunities, perceptions, income, and so much more. When race-related problems arise, color blindness tends to individualize conflicts and shortcomings, rather than examining the larger picture with cultural differences, stereotypes, and values placed into context . Instead of resulting from an enlightened (albeit well-meaning) position, color blindness comes from a lack of awareness of racial privilege conferred by Whiteness (Tarca, 2005). White people can guiltlessly subscribe to colorblindness because they are usually unaware of how race affects people of color and American society as a whole. How might colorblindness cause harm? Here's an example close to home for those of you who are psychologically-minded. In the not-so-distant past, in psychotherapy a client's racial and ethnic remarks were viewed as a defensive shift away from important issues, and the therapist tended to interpret this as resistance (Comas-Diaz & Jacobsen, 1991). However, such an approach hinders the exploration of conflicts related to race, ethnicity, and culture. The therapist doesn't see the whole picture, and the client is left frustrated. A colorblind approach effectively does the same thing. Blind means not being able to see things. I don't want to be blind. I want to see things clearly, even if they make me uncomfortable . As a therapist I need to be able to hear and "see" everything my client is communicating on many different levels. I can't afford to be blind to anything. Would you want to see a surgeon who operated blindfolded? Of course not. Likewise, a therapist should not be blinded either, especially to something as critical as a person's culture or racial identity. By encouraging the exploration of racial and cultural concepts, the therapist can provide a more authentic opportunity to understand and resolve the client's problems (Comas-Diaz & Jacobsen, 1991). Nonetheless, I have encountered many fellow therapists who ascribe to a colorblind philosophy. They ignore race or pretend its personal, social, and historical effects don't exist. This approach ignores the incredibly salient experience of being stigmatized by society and represents an empathetic failure on the part of the therapist. Colorblindness does not foster equality or respect; it merely relieves the therapist of his or her obligation to address important racial differences and difficulties. Research has shown that hearing colorblind messages predict negative outcomes among Whites, such as greater racial bias and negative affect; likewise colorblind messages cause stress in ethnic minorities, resulting in decreased cognitive performance (Holoien et al., 2011). Given how much is at stake, we can no longer afford to be blind. It's time for change and growth. It's time to see. The alternative to colorblindness is multiculturalism, an ideology that acknowledges, highlights, and celebrates ethnoracial differences. It recognizes that each tradition has something valuable to offer. It is not afraid to see how others have suffered as a result of racial conflict or differences. So, how do we become multicultural? The following suggestions would make a good start (McCabe, 2011): Recognizing and valuing differences, Teaching and learning about differences, and Fostering personal friendships and organizational alliances, Moving from colorblindness to multiculturalism is a process of change, and change is never easy, but we can't afford to stay the same . Color blindness promotes a ''post-racial'' society that excludes the history of people of color. Iweala 08 Uzodinma Iweala is the author of "Beasts of No Nation," a novel about child soldiers in Africa, January 23,2008, Los Angeles Times, ''Race still matters'' http://articles.latimes.com/2008/jan/23/opinion/oe-iweala23 Date Accessed; July 9th 2015 I am shocked by the commentary on the prominence of race as a theme in the Democratic Party primaries. Shocked not because race is a theme but because so many in the media seem to think that race would not be or should not be mentioned. It is as if we think that not speaking about race is the equivalent of making progress on race issues. The only thing more amusing than the use of a new term, "post-racial," to describe the positive response to Barack Obama's campaign is the lamentation at the loss of "post-raciality." This entire narrative is a media-concocted fiction. America is decidedly not "post-racial ." One need only observe the prosecution of the Duke University lacrosse team or the Jena Six, the debate about race-based affirmative action and the atrocity that was and is Hurricane Katrina to know that racial issues are still with us. The desire that the subject of race be set aside in the current "post-racial" political conversation shows that society is unwilling to openly face its worst fear: Not only could a black man ably lead this nation, but the mere fact of a black president would force both the majority and minority populations to reset our parameters for normality. Some (perhaps many) white Americans don't think it's normal for a black person to be successful; their stereotypes can't accommodate the fact of a black person having gone to Harvard and achieved some prominence. As an African American writer, I am reminded of this each time I finish a reading, when without fail a white person overzealously praises my speaking ability. The most recent version of this was a 15-yearold high school student who was amazed that I had actually attended college. Also telling is Obama's initial lack of support in the black community, which may have been a result of an African American unwillingness to see him as representative of traditional (very different from stereotypical) black America. The majority of Americans are comfortable accepting successful blacks in stereotypically prescribed fields such as entertainment or sports, where blacks are expected to be physically and emotionally strong and yet largely politically mute. When a black person becomes successful in another field, he or she becomes a "surprise" to the majority and is subsequently stripped of color. How many times have you heard a white person say that he or she thinks of Obama not as a black man but as a man, or of Oprah not as a black woman but as just, well, Oprah? I have lost count. This well-meaning, praise-expectant affirmation of colorblindness may seem like progress, but it's really indicative of having avoided the central issue: Someone who looks different (read black) could be just as qualified, just as deserving as a "normal" person (read white). The in-your-face, un-stereotypical blackness of Obama therefore forces all of us to question our ideas of race and racial progress in a way that makes us work. This type of work is difficult and scary, and it's understandable why some would rather delay the discussion or label it unnecessary and unproductive. But having this discussion will allow us to grow stronger as a country. Obama's presence forces us to ask whether it is reasonable to call a biracial man black; whether definitions of race designed to benefit slave-owners are still necessary and valid in 2008. His openness about past drug use could put front and center the debate about the patently racist sentencing guidelines our "post-racial" society employs to punish narcotics- related offenses. In general, Barack Hussein Obama brings us face to face with the discomfort our society feels with this idea of difference. Indeed, fascination with Obama's name recalls studies that show how hard it is for those with unique African American names to find employment. And it is interesting that no one has mentioned an obvious reason for the Obama campaign's initial reluctance to attack Hillary Rodham Clinton -- that it might conjure up the age-old assumption that aggressive young black men are a menace to older white women. (If that statement offends you, I'm sure plenty of young black men like myself can tell you about older white women crossing the street to avoid us in our "post-racial" society.) Even if we were to confront head-on these and other questions surrounding race, we are unlikely to grow into the "post-racial" modifier some of us so crave. That's because the idea of "post-raciality" is a total fallacy. Should Obama become president, he will not suddenly cease to be black, nor will white Americans be any less white. However, Obama's continual presence in our newspapers, on television and in our national consciousness would force us to reconsider just what these colors mean. A President Obama (or any other black president) would bring us face to face with the threatening idea that colorblindness and equality are not the same, and that real progress on racial issues means respect for, and not avoidance of, difference. Our racial past and future is something that we Americans must address. Thanks to Obama, there is no better time than now. Color-blindness is the new arise form of racism to oppress people of color. Neville 11 Helen. A Neville is a Professor in the Departments of Educational Psychology and African American Studies at the UIUC. August 17, 2011, ''SAGE PUBLICATIONS'' http://dx.doi.org/10.4135/9781412963978.n343 Date accessed; July 9, 2015 Recently, scholars have challenged the assumption of the emergence of a new racism. Based on the review of the interdisciplinary literature in the United States and in other Englishspeaking countries, Colin Wayne Leach concluded that old-fashioned racism or the endorsement of racial inferiority/superiority ideology and actions have not been supplanted by more covert forms of racial expressions. Although he did not name racial color-blindness in his critique, Leach raised questions about whether or not a shift has occurred in the manifestation of racism since the passage of civil rights laws. In sum, racial color-blindness is premised on the persistence of racism as manifested in contemporary racial disparities across a range of indexes, including housing, health, and employment. The complex set of beliefs used to restrict awareness of the persistence of racism is part of a larger ideological stance that serves to legitimize and further perpetuate racial inequalities. There is some debate about whether racial colorblindness is a new phenomenon or whether it reflects a dimension of racism that, until relatively recently, has received attention in the social science literature. Islamophobia Adv Uniqueness – Islamophobic Targeting Now Islamophobic targeting by the FBI is rampant now. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] In accordance with its surveillance and national security investigation power, the FBI has conducted various undercover monitoring procedures that call into question their constitutional permissibility. 115Link to the text of the note In 2009, the FBI participated in a career day event conducted in San [451] Jose, CA sponsored by an Assyrian community organization. 116Link to the text of the note The FBI's observations were placed in a mapping report. 117Link to the text of the note In the report, the FBI recited information about the organization's activities, the identities of several leaders within the organization, and the content of conversations at the event. 118Link to the text of the note This content included opinions, backgrounds, travel histories, educations, occupations, and charitable activities. 119Link to the text of the note Similarly, a memo submitted by the Sacramento Division of the FBI details a conversation in which an undercover agent discusses the Saudi Student Association with an innocent California State University student. 120Link to the text of the note The conversation included the organization's size, purpose, and activities. 121Link to the text of the note The memo, which included the student's social security number, telephone number, and address, was submitted to the FBI in Washington, DC. 122Link to the text of the note Additionally, in San Francisco, the FBI submitted a 2007 and 2008 report that detailed FBI spy efforts at Ramadan Iftar dinners. 123Link to the text of the note In the reports, the FBI documented the names of attendees, the contents of various conversations and presentations, a photo of dinner participants, and other information. 124Link to the text of the note Both of the reports indicate that the information was disseminated outside of the FBI. 125Link to the text of the note There are several other instances, similar to these, in which the FBI utilized individuals' race or ethnicity as a basis for monitoring. 126Link to the text of the note The American Civil Liberties Union and [452] other organizations have protested the wide-sweeping authority that has been granted to the national government to monitor domestic individuals, especially those that are not suspected of terrorism or criminal activity. 127Link to the text of the note Furthermore, the government has received criticism in the past for misusing its surveillance authority. 128Link to the text of the note In March of 2007, the Director of the FBI, Robert Mueller III, acknowledged that the bureau had improperly used the Patriot Act to obtain surveillance information. 129Link to the text of the note An investigation into the government's surveillance practices found that national security letters, which allow the bureau to obtain records from telephone companies, internet service providers, banks, credit companies, and other businesses without a judge's approval, were improperly, and sometimes illegally, used. 130Link to the text of the note Additionally, incorrect recordkeeping was exposed, in which the actual number of national security letters utilized were frequently understated when reported to Congress. 131Link to the text of the note Several legislatures have expressed concern about the misuse of government surveillance. 132Link to the text of the note It is apparent that this concern is not misguided since the Justice Department's Office of the Inspector General noted, in a 2007 audit report, that many FBI failures had occurred as a result of its surveillance procedures. 133Link to the text of the note These failures include a lack of internal controls 134Link to the text of the note and the absence of required information in national security letter approval memoranda. 135Link to the text of the note Critics of the government's surveillance procedures assert that the broad monitoring authority given to the government not only is unconstitutional because of a lack of checks and balances that would [453] allow for proper controls of the monitoring of citizens, 136Link to the text of the note but also because it has the effect of inappropriately singling out individuals for no other reason than their race or ethnicity. 137Link to the text of the note Therefore, the surveillance power given to the government and the anti-terrorist domestic monitoring procedures must be analyzed to determine their constitutional permissibility. NYPD’s undercover operation have been targeting Muslims and other minorities APUZZO AND GOLDMAN ’11 (matt and adam, , “With CIA help, NYPD moves covertly in Muslim areas,”8/23,Associated Press, With CIA help, NYPD moves covertly in Muslim areas, LS) In New Brunswick, N.J., a building superintendent opened the door to apartment No. 1076 one balmy Tuesday and discovered an alarming scene: terrorist literature strewn about the table and computer and surveillance equipment set up in the next room. The panicked superintendent dialed 911, sending police and the FBI rushing to the building near Rutgers University on the afternoon of June 2, 2009. What they found in that first-floor apartment, however, was not a terrorist hideout but a command center set up by a secret team of New York Police Department intelligence officers. From that apartment, about an hour outside the department's jurisdiction, the NYPD had been staging undercover operations and conducting surveillance throughout New Jersey. Neither the FBI nor the local police had any idea. Since the terrorist attacks of Sept. 11, 2001, the NYPD has become one of the country's most aggressive domestic intelligence agencies. A months-long investigation by The Associated Press has revealed that the NYPD operates far outside its borders and targets ethnic communities in ways that would run afoul of civil liberties rules if practiced by the federal government. And it does so with unprecedented help from the CIA in a partnership that has blurred the bright line between foreign and domestic spying. Neither the city council, which finances the department, nor the federal government, which contributes hundreds of millions of dollars each year, is told exactly what's going on. The department has dispatched teams of undercover officers, known as "rakers," into minority neighborhoods as part of a human mapping program, according to officials directly involved in the program. They've monitored daily life in bookstores, bars, cafes and nightclubs. Police have also used informants, known as "mosque crawlers," to monitor sermons, even when there's no evidence of wrongdoing. NYPD officials have scrutinized imams and gathered intelligence on cab drivers and food cart vendors, jobs often done by Muslims. Many of these operations were built with help from the CIA, which is prohibited from spying on Americans but was instrumental in transforming the NYPD's intelligence unit. A veteran CIA officer, while still on the agency's payroll, was the architect of the NYPD's intelligence programs. The CIA trained a police detective at the Farm, the agency's spy school in Virginia, then returned him to New York, where he put his new espionage skills to work inside the United States. And just last month, the CIA sent a senior officer to work as a clandestine operative inside police headquarters. While the expansion of the NYPD's intelligence unit has been well known, many details about its clandestine operations, including the depth of its CIA ties, have not previously been reported. The NYPD denied that it trolls ethnic neighborhoods and said it only follows leads. In a city that has repeatedly been targeted by terrorists, police make no apologies for pushing the envelope. NYPD intelligence operations have disrupted terrorist plots and put several would-be killers in prison. "The New York Police Department is doing everything it can to make sure there's not another 9/11 here and that more innocent New Yorkers are not killed by terrorists," NYPD spokesman Paul Browne said. "And we have nothing to apologize for in that regard." But officials said they've also been careful to keep information about some programs out of court, where a judge might take a different view. The NYPD considers even basic details, such as the intelligence division's organization chart, to be too sensitive to reveal in court. One of the enduring questions of the past decade is whether being safe requires giving up some liberty and privacy. The focus of that debate has primarily been federal programs like wiretapping and indefinite detention. The question has received less attention in New York, where residents do not know for sure what, if anything, they have given up. The story of how the NYPD Intelligence Division developed such aggressive programs was pieced together by the AP in interviews with more than 40 current and former New York Police Department and federal officials. Many were directly involved in planning and carrying out these secret operations for the department. Though most said the tactics were appropriate and made the city safer, many insisted on anonymity, because they were not authorized to speak with reporters about security matters. The story begins with one man. David Cohen arrived at the New York Police Department in January 2002, just weeks after the last fires had been extinguished at the debris field that had been the twin towers. A retired 35-year veteran of the CIA, Cohen became the police department's first civilian intelligence chief. Cohen had an exceptional career at the CIA, rising to lead both the agency's analytical and operational divisions. He also was an extraordinarily divisive figure, a man whose sharp tongue and supreme confidence in his own abilities gave him a reputation as arrogant. Cohen's tenure as head of CIA operations, the nation's top spy, was so contentious that in 1997, The New York Times editorial page took the unusual step of calling for his ouster. He had no police experience. He had never defended a city from an attack. But New York wasn't looking for a cop. "Post-9/11, we needed someone in there who knew how to really gather intelligence," said John Cutter, a retired NYPD official who served as one of Cohen's top uniformed officers. At the time, the intelligence division was best known for driving dignitaries around the city. Cohen envisioned a unit that would analyze intelligence, run undercover operations and cultivate a network of informants. In short, he wanted New York to have its own version of the CIA. Cohen shared Commissioner Ray Kelly's belief that 9/11 had proved that the police department could not simply rely on the federal government to prevent terrorism in New York. "If anything goes on in New York," one former officer recalls Cohen telling his staff in the early days, "it's your fault." Among Cohen's earliest moves at the NYPD was making a request of his old colleagues at CIA headquarters in Langley, Va. He needed someone to help build this new operation, someone with experience and clout and, most important, someone who had access to the latest intelligence so the NYPD wouldn't have to rely on the FBI to dole out information. CIA Director George Tenet responded by tapping Larry Sanchez, a respected veteran who had served as a CIA official inside the United Nations. Often, when the CIA places someone on temporary assignment, the other agency picks up the tab. In this case, three former intelligence officials said, Tenet kept Sanchez on the CIA payroll. When he arrived in New York in March 2002, Sanchez had offices at both the NYPD and the CIA's station in New York, one former official said. Sanchez interviewed police officers for newly defined intelligence jobs. He guided and mentored officers, schooling them in the art of gathering information. He also directed their efforts, another said. There had never been an arrangement like it, and some senior CIA officials soon began questioning whether Tenet was allowing Sanchez to operate on both sides of the wall that's supposed to keep the CIA out of the domestic intelligence business. "It should not be a surprise to anyone that, after 9/11, the Central Intelligence Agency stepped up its cooperation with law enforcement on counterterrorism issues or that some of that increased cooperation was in New York, the site of ground zero," CIA spokeswoman Jennifer Youngblood said. Just as at the CIA, Cohen and Sanchez knew that informants would have to become the backbone of their operation. But with threats coming in from around the globe, they couldn't wait months for the perfect plan. They came up with a makeshift solution. They dispatched more officers to Pakistani neighborhoods and, according to one former police official directly involved in the effort, instructed them to look for reasons to stop cars: speeding, broken tail lights, running stop signs, whatever. The traffic stop gave police an opportunity to search for outstanding warrants or look for suspicious behavior. An arrest could be the leverage the police needed to persuade someone to become an informant. For Cohen, the transition from spying to policing didn't come naturally, former colleagues said. When faced with a decision, especially early in his tenure, he'd fall back on his CIA background. Cutter said he and other uniformed officers had to tell Cohen, no, we can't just slip into someone's apartment without a warrant. No, we can't just conduct a search. The rules for policing are different. While Cohen was being shaped by the police department, his CIA background was remaking the department. But one significant barrier stood in the way of Cohen's vision. Since 1985, the NYPD had operated under a federal court order limiting the tactics it could use to gather intelligence. During the 1960s and 1970s, the department had used informants and undercover officers to infiltrate anti-war protest groups and other activists without any reason to suspect criminal behavior. To settle a lawsuit, the department agreed to follow guidelines that required "specific information" of criminal activity before police could monitor political activity. In September 2002, Cohen told a federal judge that those guidelines made it "virtually impossible" to detect terrorist plots. The FBI was changing its rules to respond to 9/11, and Cohen argued that the NYPD must do so, too. "In the case of terrorism, to wait for an indication of crime before investigating is to wait far too long," Cohen wrote. U.S. District Judge Charles S. Haight Jr. agreed, saying the old guidelines "addressed different perils in a different time." He scrapped the old rules and replaced them with more lenient ones. It was a turning point for the NYPD.With his newfound authority, Cohen created a secret squad that would soon infiltrate Muslim neighborhoods, according to several current and former officials directly involved in the program.The NYPD carved up the city into more than a dozen zones and assigned undercover officers to monitor them, looking for potential trouble. At the CIA, one of the biggest obstacles has always been that U.S. intelligence officials are overwhelmingly white, their mannerisms clearly American. The NYPD didn't have that problem, thanks to its diverse pool of officers. Using census data, the department matched undercover officers to ethnic communities and instructed them to blend in, the officials said. Pakistani-American officers infiltrated Pakistani neighborhoods, Palestinians focused on Palestinian neighborhoods. They hung out in hookah bars and cafes, quietly observing the community around them. The unit, which has been undisclosed until now, became known inside the department as the Demographic Unit, former police officials said. "It's not a question of profiling. It's a question of going where the problem could arise," said Mordecai Dzikansky, a retired NYPD intelligence officer who said he was aware of the Demographic Unit. "And thank God we have the capability. We have the language capability and the ethnic officers. That's our hidden weapon." The officers did not work out of headquarters, officials said. Instead, they passed their intelligence to police handlers who knew their identities. Cohen said he wanted the squad to "rake the coals, looking for hot spots," former officials recalled. The undercover officers soon became known inside the department as rakers. A hot spot might be a beauty supply store selling chemicals used for making bombs. Or it might be a hawala, a broker that transfers money around the world with little documentation. Undercover officers might visit an Internet cafe and look at the browsing history on a computer, a former police official involved in the program said. If it revealed visits to radical websites, the cafe might be deemed a hot spot. Ethnic bookstores, too, were on the list. If a raker noticed a customer looking at radical literature, he might chat up the store owner and see what he could learn. The bookstore, or even the customer, might get further scrutiny. If a restaurant patron applauds a news report about the death of U.S. troops, the patron or the restaurant could be labeled a hot spot. The goal was to "map the city's human terrain," one law enforcement official said. The program was modeled in part on how Israeli authorities operate in the West Bank, a former police official said. Mapping crimes has been a successful police strategy nationwide. But mapping robberies and shootings is one thing. Mapping ethnic neighborhoods is different, something that at least brushes against what the federal government considers racial profiling. Browne, the NYPD spokesman, said the Demographic Unit does not exist. He said the department has a Zone Assessment Unit that looks for locations that could attract terrorists. But he said undercover officers only followed leads, disputing the account of several current and former police and federal officials. They do not just hang out in neighborhoods, he said. "We will go into a location, whether it's a mosque or a bookstore, if the lead warrants it, and at least establish whether there's something that requires more attention," Browne said. That conflicts with testimony from an undercover officer in the 2006 trial of Shahawar Matin Siraj, who was convicted of planning an attack on New York's subway system. The officer said he was instructed to live in Brooklyn and act as a "walking camera" for police. "I was told to act like a civilian _ hang out in the neighborhood, gather information," the Bangladeshi officer testified, under a false name, in what offered the first narrow glimpse at the NYPD's infiltration of ethnic neighborhoods. Officials said such operations just made sense. Islamic terrorists had attacked the city on 9/11, so police needed people inside the city's Muslim neighborhoods. Officials say it does not conflict with a 2004 city law prohibiting the NYPD from using religion or ethnicity "as the determinative factor for initiating law enforcement action." "It's not profiling," Cutter said. "It's like, after a shooting, do you go 20 blocks away and interview guys or do you go to the neighborhood where it happened?" In 2007, the Los Angeles Police Department was criticized for even considering a similar program. The police announced plans to map Islamic neighborhoods to look for pockets of radicalization among the region's roughly 500,000 Muslims. Criticism was swift, and chief William Bratton scrapped the plan. "A lot of these people came from countries where the police were the terrorists," Bratton said at a news conference, according to the Los Angeles Daily News. "We don't do that here. We do not want to spread fear." In New York, current and former officials said, the lesson of that controversy was that such programs should be kept secret. Some in the department, including lawyers, have privately expressed concerns about the raking program and how police use the information, current and former officials said. Part of the concern was that it might appear that police were building dossiers on innocent people, officials said. Another concern was that, if a case went to court, the department could be forced to reveal details about the program, putting the entire operation in jeopardy. That's why, former officials said, police regularly shredded documents discussing rakers. When Cohen made his case in court that he needed broader authority to investigate terrorism, he had promised to abide by the FBI's investigative guidelines. But the FBI is prohibited from using undercover agents unless there's specific evidence of criminal activity, meaning a federal raking program like the one officials described to the AP would violate FBI guidelines. The NYPD declined to make Cohen available for comment. In an earlier interview with the AP on a variety of topics, Police Commissioner Kelly said the intelligence unit does not infringe on civil rights. "We're doing what we believe we have to do to protect the city," he said. "We have many, many lawyers in our employ. We see ourselves as very conscious and aware of civil liberties. And we know there's always going to be some tension between the police department and so-called civil liberties groups because of the nature of what we do." The department clashed with civil rights groups most publicly after Cohen's undercover officers infiltrated anti-war groups before the 2004 Republican National Convention in New York. A lawsuit over that program continues today. During the convention, when protesters were arrested, police asked a list of questions which, according to court documents, included: "What are your political affiliations?" "Do you do any kind of political work?" and "Do you hate George W. Bush?" "At the end of the day, it's pure and simple a rogue domestic surveillance operation," said Christopher Dunn, a New York Civil Liberties Union lawyer involved in the convention lawsuit. Undercover agents like the rakers were valuable, but what Cohen and Sanchez wanted most were informants. The NYPD dedicated an entire squad, the Terrorist Interdiction Unit, to developing and handling informants. Current and former officials said Sanchez was instrumental in teaching them how to develop sources. For years, detectives used informants known as mosque crawlers to monitor weekly sermons and report what was said, several current and former officials directly involved in the informant program said. If FBI agents were to do that, they would be in violation of the Privacy Act, which prohibits the federal government from collecting intelligence on purely First Amendment activities. The FBI has generated its own share of controversy for putting informants inside mosques, but unlike the program described to the AP, the FBI requires evidence of a crime before an informant can be used inside a mosque. Valerie Caproni, the FBI's general counsel, would not discuss the NYPD's programs but said FBI informants can't troll mosques looking for leads. Such operations are reviewed for civil liberties concerns, she said. "If you're sending an informant into a mosque when there is no evidence of wrongdoing, that's a very high-risk thing to do," Caproni said. "You're running right up against core constitutional rights. You're talking about freedom of religion." That's why senior FBI officials in New York ordered their own agents not to accept any reports from the NYPD's mosque crawlers, two retired agents said. It's unclear whether the police department still uses mosque crawlers. Officials said that, as Muslims figured out what was going on, the mosque crawlers became cafe crawlers, fanning out into the city's ethnic hangouts. "Someone has a great imagination," Browne, the NYPD spokesman, said. "There is no such thing as mosque crawlers." Following the foiled subway plot, however, the key informant in the case, Osama Eldawoody, said he attended hundreds of prayer services and collected information even on people who showed no signs of radicalization. NYPD detectives have recruited shopkeepers and nosy neighbors to become "seeded" informants who keep police up to date on the latest happenings in ethnic neighborhoods, one official directly involved in the informant program said. The department also has a roster of "directed" informants it can tap for assignments. For instance, if a raker identifies a bookstore as a hot spot, police might assign an informant to gather information, long before there's concrete evidence of anything criminal. To identify possible informants, the department created what became known as the "debriefing program." When someone is arrested who might be useful to the intelligence unit _ whether because he said something suspicious or because he is simply a young Middle Eastern man _ he is singled out for extra questioning. Intelligence officials don't care about the underlying charges; they want to know more about his community and, ideally, they want to put him to work. Police are in prisons, too, promising better living conditions and help or money on the outside for Muslim prisoners who will work with them. Early in the intelligence division's transformation, police asked the taxi commission to run a report on all the city's Pakistani cab drivers, looking for those who got licenses fraudulently and might be susceptible to pressure to cooperate, according to former officials who were involved in or briefed on the effort. That strategy has been rejected in other cities. Boston police once asked neighboring Cambridge for a list of Somali cab drivers, Cambridge Police Chief Robert Haas said. Haas refused, saying that without a specific reason, the search was inappropriate. "It really has a chilling effect in terms of the relationship between the local police department and those cultural groups, if they think that's going to take place," Haas said. The informant division was so important to the NYPD that Cohen persuaded his former colleagues to train a detective, Steve Pinkall, at the CIA's training center at the Farm. Pinkall, who had an intelligence background as a Marine, was given an unusual temporary assignment at CIA headquarters, officials said. He took the field tradecraft course alongside future CIA spies then returned to New York to run investigations. "We found that helpful, for NYPD personnel to be exposed to the tradecraft," Browne said. The idea troubled senior FBI officials, who saw it as the NYPD and CIA blurring the lines between police work and spying, in which undercover officers regularly break the laws of foreign governments. The arrangement even made its way to FBI Director Robert Mueller, two former senior FBI officials said, but the training was already under way and Mueller did not press the issue. NYPD's intelligence operations do not stop at the city line, as the undercover operation in New Jersey made clear. The department has gotten some of its officers deputized as federal marshals, allowing them to work out of state. But often, there's no specific jurisdiction at all. Cohen's undercover squad, the Special Services Unit, operates in places such as New Jersey, Pennsylvania and Massachusetts, officials said. They can't make arrests and, if something goes wrong _ a shooting or a car accident, for instance _ the officers could be personally liable. But the NYPD has decided it's worth the risk, a former police official said. With Police Commissioner Kelly's backing, Cohen's policy is that any potential threat to New York City is the NYPD's business, regardless of where it occurs, officials said. That aggressiveness has sometimes put the NYPD at odds with local police departments and, more frequently, with the FBI. The FBI didn't like the rules Cohen played by and said his operations encroached on their responsibilities. Once, undercover officers were stopped by police in Massachusetts while conducting surveillance on a house, one former New York official recalled. In another instance, the NYPD sparked concern among federal officials by expanding its intelligence-gathering efforts related to the United Nations, where the FBI is in charge, current and former federal officials said. The AP has agreed not to disclose details of either the FBI or NYPD operations because they involve foreign counterintelligence. Both Mueller and Kelly have said their agencies have strong working relationships and said reports of rivalry and disagreements are overblown. And the NYPD's outof-state operations have had success. A young Egyptian NYPD officer living undercover in New Jersey, for example, was key to building a case against Mohamed Mahmood Alessa and Carlos Eduardo Almonte. The pair was arrested last year at John F. Kennedy Airport en route to Somalia to join the terrorist group al-Shabab. Both pleaded guilty to conspiracy. Cohen has also sent officers abroad, stationing them in 11 foreign cities. If a bomber blows himself up in Jerusalem, the NYPD rushes to the scene, said Dzikansky, who served in Israel and is the coauthor of the forthcoming book "Terrorist Suicide Bombings: Attack Interdiction, Mitigation, and Response." "I was there to ask the New York question," Dzikansky said. "Why this location? Was there something unique that the bomber had done? Was there any pre-notification. Was there a security lapse?" All of this intelligence _ from the rakers, the undercovers, the overseas liaisons and the informants _ is passed to a team of analysts hired from some of the nation's most prestigious universities. Analysts have spotted emerging trends and summarized topics such as Hezbollah's activities in New York and the threat of South Asian terrorist groups. They also have tackled more contentious topics, including drafting an analytical report on every mosque within 100 miles of New York, one former police official said. The report drew on information from mosque crawlers, undercover officers and public information. It mapped hundreds of mosques and discussed the likelihood of them being infiltrated by al-Qaida, Hezbollah and other terrorist groups. For Cohen, there was only one way to measure success: "They haven't attacked us," he said in a 2005 deposition. He said anything that was bad for terrorists was good for NYPD. Though the CIA is prohibited from collecting intelligence domestically, the wall between domestic and foreign operations became more porous. Intelligence gathered by the NYPD, with CIA officer Sanchez overseeing collection, was often passed to the CIA in informal conversations and through unofficial channels, a former official involved in that process said. By design, the NYPD was looking more and more like a domestic CIA. "It's like starting the CIA over in the post-9/11 world," Cohen said in "Protecting the City," a laudatory 2009 book about the NYPD. "What would you do if you could begin it all over again? Hah. This is what you would do." Sanchez's assignment in New York ended in 2004, but he received permission to take a leave of absence from the agency and become Cohen's deputy, former officials said. Though Sanchez's assignments were blessed by CIA management, some in the agency's New York station saw the presence of such a senior officer in the city as a turf encroachment. Finally, the New York station chief, Tom Higgins, called headquarters, one former senior intelligence official said. Higgins complained, the official said, that Sanchez was wearing both hats, sometimes acting as a CIA officer, sometimes as an NYPD official. The CIA finally forced him to choose: Stay with the agency or stay with the NYPD. Sanchez declined to comment to the AP about the arrangement, but he picked the NYPD. He retired last year and is now a consultant in the Middle East. Last month, the CIA deepened its NYPD ties even further. It sent one of its most experienced operatives, a former station chief in two Middle Eastern countries, to work out of police headquarters as Cohen's special assistant while on the CIA payroll. Current and former U.S. officials acknowledge it's unusual but said it's the kind of collaboration Americans expect after 9/11. Officials said revealing the CIA officer's name would jeopardize national security. The arrangement was described as a sabbatical. He is a member of the agency's senior management, but officials said he was sent to the municipal police department to get management experience. At the NYPD, he works undercover in the senior ranks of the intelligence division. Officials are adamant that he is not involved in actual intelligence-gathering. The NYPD has faced little scrutiny over the past decade as it has taken on broad new intelligence missions, targeted ethnic neighborhoods and partnered with the CIA in extraordinary ways. The department's primary watchdog, the New York City Council, has not held hearings on the intelligence division's operations and former NYPD officials said council members typically do not ask for details. "Ray Kelly briefs me privately on certain subjects that should not be discussed in public," said City Councilman Peter Vallone. "We've discussed in person how they investigate certain groups they suspect have terrorist sympathizers or have terrorist suspects." The city comptroller's office has audited several NYPD components since 9/11 but not the intelligence unit, which had a $62 million budget last year. The federal government, too, has done little to scrutinize the nation's largest police force, despite the massive federal aid. Homeland Security officials review NYPD grants but not its underlying programs. A report in January by the Homeland Security inspector general, for instance, found that the NYPD violated state and federal contracting rules between 2006 and 2008 by buying more than $4 million in equipment through a no-bid process. NYPD said public bidding would have revealed sensitive information to terrorists, but police never got approval from state or federal officials to adopt their own rules, the inspector general said. On Capitol Hill, where FBI tactics have frequently been criticized for their effect on civil liberties, the NYPD faces no such opposition. In 2007, Sanchez testified before the Senate Homeland Security Committee and was asked how the NYPD spots signs of radicalization. He said the key was viewing innocuous activity, including behavior that might be protected by the First Amendment, as a potential precursor to terrorism. That triggered no questions from the committee, which Sanchez said had been "briefed in the past on how we do business." The Justice Department has the authority to investigate civil rights violations. It issued detailed rules in 2003 against racial profiling, including prohibiting agencies from considering race when making traffic stops or assigning patrols. But those rules apply only to the federal government and contain a murky exemption for terrorism investigations. The Justice Department has not investigated a police department for civil rights violations during a national security investigation. "One of the hallmarks of the intelligence division over the last 10 years is that, not only has it gotten extremely aggressive and sophisticated, but it's operating completely on its own," said Dunn, the civil liberties lawyer. "There are no checks. There is no oversight." The NYPD has been mentioned as a model for policing in the post-9/11 era. But it's a model that seems custom-made for New York. No other city has the Big Apple's combination of a low crime rate, a $4.5 billion police budget and a diverse 34,000-person police force. Certainly no other police department has such deep CIA ties. Perhaps most important, nobody else had 9/11 the way New York did. No other city lost nearly 3,000 people in a single morning. A decade later, police say New Yorkers still expect the department to do whatever it can to prevent another attack. The NYPD has embraced that expectation. As Sanchez testified on Capitol Hill: "We've been given the public tolerance and the luxury to be very aggressive on this topic." Since 9/11 Muslims have been unlawfully targeted. NYPD proves CCR ‘14 The center for constitutional rights is a website that reports on social injustices such as the unjust surveillance of people based on their race, ethnicity or religion. March 6th 2014 https://ccrjustice.org/home/get-involved/tools-resources/fact-sheets-and-faqs/nypd-ssurveillance-and-targeting-muslims-new July 7th 2015 Since 9/11, (actual or perceived) Muslims, Arabs and South Asians have been viewed by law enforcement as a potential threat on no basis other than religion, casting guilt on all members of that faith. The New York City Police Department (NYPD) has developed a sweeping and secretive human surveillance program that targets Muslims and members of the Arab and South Asian communities in New York City, New Jersey, and elsewhere – solely on the basis of their religious affiliation. This massive mapping and surveillance program has been used to monitor the lives of Muslims, their businesses, houses of worship, organizations and schools – despite any basis for belief of criminal activity. The methods the NYPD uses in their surveillance program are extremely invasive and places targeted make little sense CCR ‘14 The center for constitutional rights is a website that reports on social injustices such as the unjust surveillance of people based on their race, ethnicity or religion. March 6th 2014 https://ccrjustice.org/home/get-involved/tools-resources/fact-sheets-and-faqs/nypd-ssurveillance-and-targeting-muslims-new July 7th 2015 As part of the surveillance program, NYPD officers have snapped pictures, taken video, and mounted cameras aimed at mosques for the purpose of round-the-clock surveillance in order to help identify worshippers. The NYPD has also employed “Mosque crawlers” are undercover officers who monitor sermons and conversations in mosques and report back to the NYPD. As a result, thousands of prayer services in mosques have been monitored and documented. The NYPD also uses undercover officers called “rakers” to monitor daily life in neighborhoods and locations they believe to be heavily Muslim – including bookstores, bars, businesses, cafes, delis, restaurants and nightclubs. Officers have taken note of flyers offering Qur’an classes and which delis that offer halal meat. One woman was surveilled because she operates a gradeschool for Muslim girls. The only effect of the surveillance the NYPD has conducted is harming the Muslim American Community, no criminal leads have been produced CCR ‘14 The center for constitutional rights is a website that reports on social injustices such as the unjust surveillance of people based on their race, ethnicity or religion. March 6th 2014 https://ccrjustice.org/home/get-involved/tools-resources/fact-sheets-and-faqs/nypd-ssurveillance-and-targeting-muslims-new July 7th 2015 The NYPD’s surveillance program has had a chilling effect on Muslim American communities, particularly in New Jersey and New York City. By suggesting that Muslims pose a special threat to public safety and treating them with suspicion as such, the program has led to the alteration and reduction of religious practices, decreased mosque attendance, and loss of business—not to mention a widespread sense of fear, distrust, and alienation. Furthermore, in ten years, this surveillance program has not produced any leads to criminal activity. Instead, by targeting Muslims based on their beliefs and affiliations rather than their actions, the NYPD has equated Islam with predisposition to criminality. - This surveillance is not only discriminatory but unconstitutional CCR ‘14 The center for constitutional rights is a website that reports on social injustices such as the unjust surveillance of people based on their race, ethnicity or religion. March 6th 2014 https://ccrjustice.org/home/get-involved/tools-resources/fact-sheets-and-faqs/nypd-ssurveillance-and-targeting-muslims-new July 7th 2015 The targeting of Muslim communities in New Jersey by the NYPD must be contextualized as another facet of the Department’s use of discriminatory policing practices – that is, when law enforcement targets communities for enforcement activities not on the basis of what they have done, but who they are. This is not only unjust, it is also unconstitutional. The FBI pushed vulnerable Muslims to commit acts of terror for sting operations CAIR 14 (The Council on American-Islamic Relations (CAIR) is a grassroots civil rights and advocacy group and CAIR America's largest Muslim civil liberties organization, with regional offices nationwide, Pub. 7/22/14, “HRW Report: FBI encourage, paid Muslims to plot attacks”, http://www.cair.com/press-center/american-muslim-news/12571-hrw-report-fbi-encouragedpaid-muslims-to-plot-attacks.html, Access 7/7/15) The FBI encouraged and sometimes even paid Muslims to commit terrorist acts during numerous sting operations after the 9/11 attacks, a human rights group said in a report published Monday. "Far from protecting Americans, including American Muslims, from the threat of terrorism, the policies documented in this report have diverted law enforcement from pursuing real threats," said the report by Human Rights Watch. Aided by Columbia University Law School's Human Rights Institute, Human Rights Watch examined 27 cases from investigation through trial, interviewing 215 people, including those charged or convicted in terrorism cases, their relatives, defense lawyers, prosecutors and judges. "In some cases the FBI may have created terrorists out of law-abiding individuals by suggesting the idea of taking terrorist action or encouraging the target to act," the report said. In the cases reviewed, half the convictions resulted from a sting operation, and in 30 percent of those cases the undercover agent played an active role in the plot. "Americans have been told that their government is keeping them safe by preventing and prosecuting terrorism inside the US," said Andrea Prasow, the rights group's deputy Washington director. "But take a closer look and you realise that many of these people would never have committed a crime if not for law enforcement encouraging, pressuring and sometimes paying them to commit terrorist acts." The report cites the case of four Muslim converts from Newburgh, New York who were accused of planning to blow up synagogues and attack a US military base. A judge in that case "said the government 'came up with the crime, provided the means, and removed all relevant obstacles,' and had, in the process, made a terrorist out of a man 'whose buffoonery is positively Shakespearean in scope,'" the report said. The rights group charged that the FBI often targets vulnerable people, with mental problems or low intelligence. It pointed to the case of Rezwan Ferdaus, who was sentenced to 17 years in prison at age 27 for wanting to attack the Pentagon and Congress with mini-drones loaded with explosives. An FBI agent told Ferdaus' father that his son "obviously" had mental health problems, the report said. But that didn't stop an undercover agent from conceiving the plot in its entirety, it said. "The US government should stop treating American Muslims as terrorists-inwaiting," the report concluded. Insert Tag Phelps ’13 (Paulina, Author at the Seattle Globalist, Georgetown media group, Africa.redux media, and Saratoga wire, “Arab and Muslim communities react to NSA surveillance leak,” June/25, Seattle Globalist, http://seattleglobalist.com/2013/06/25/araband-muslim-nsa-surveillance-leak/14225,LS) So the government’s been spying on us? Arab and Muslim activists in Seattle say they aren’t surprised. When news broke earlier this month of the NSA’s vast, intrusive surveillance programs, U.S. citizens had the uncomfortable experience of suddenly feeling like suspects. Even for the majority of Americans who say they approve of the program, it was hard not to rack your brain for things you had said in a phone call or email that might have caught the government’s attention. But that feeling was nothing new for Arabs, Muslims, South Asians and other groups who have been subject to surveillance and prejudice since 9/11. President Obama responded to the leak with assurances that “nobody is listening to your telephone calls.” Instead, he said, the surveillance only takes place when “they may identify potential leads with respect to people that might engage in terrorism.” Devon Abdallah, secretary of the Arab American Community Coalition (AACC), based here in Seattle, says that the kind of “reasonable suspicion” used to justify NSA surveillance often amounts to little more than racial profiling. “The reality is, in our society there is so much institutional racism and subconscious stereotyping that people naturally are going to just pay more attention to someone with an Arab name,” Abdallah said. “I’ve seen the people they’ve deported that they’ve seen as ‘terrorists’ and I can guarantee you that they aren’t.” Damon Shadid, a Lebanese-American attorney who also works with the AACC believes that if people knew the extent of the personal information that has been collected, they wouldn’t be as supportive of the program. “The thing that disturbs me most…is this poll that is being cited all over the Internet that is saying 60% of Americans are okay with [the surveillance system]… the poll does not ask the right questions.” Shadid said. “If they asked the question ‘are you okay with your text messages being read,’ or ‘are you okay with the subject line of your email being read by the government’ the public would have a completely different response.” “As a Lebanese-American who deals with international clients, all the sudden my metadata may be looked at closer. [That] could create suspicion on me where none should exist,” Shadid said. “And that goes for every Arab and Muslim in the community.” “Suspicionless surveillance does not become okay simply because it’s only victimizing 95 percent of the world instead of 100 percent,” whistleblower Edward Snowden said in an online Q & A hosted by the Guardian last week, referring to assurances that only communications outside the US are being monitored. “Our founders did not write, ‘we hold these Truths to be self-evident, that all US Persons are created equal.’” Arsalan Bukhari, executive director of the Council on American-Islamic Relations (CAIR) Washington Chapter, agrees that the system is unconstitutional. But he’s more optimistic about the ultimate outcome of the leak. “I hope the good that comes out of this are clear guidelines that regulate when and how the government can survey a person.” he said. “For too long we’ve had unconstitutional surveillance. We want to make sure the constitution is the law of the land and is followed — which means you have to get a warrant.” Egyptian-American Muslim activist Tarek Dawoud compared the government’s actions to that of other countries. “This is what is happening in Egypt… it’s not a good sign you can see this country going down that path and it’s a concern because one of the greatest gifts people have here is to be free and the ability to challenge authority.” Ultimately all of these voices on the issue, including the person behind the leak, echo feelings of betrayal by the government. And they seem to agree that the existing system is unconstitutional and vulnerable to racial profiling. Arabs, Muslims, and South Asians have been experiencing government surveillance as a “national security measure” ever since 9/11. So for the entire country to suddenly realize they may be subject to the same thing is almost a relief. Insert Tag Kayyali ’06 (Randa, course instructor at George Mason University, Director of Finance and Administration at the Safe Energy communication Council, Excutive Director for the Association of Arab-American University Graduates, Director of Public Relations/Office Manager at the American Educational Trust, Writer at the American Anti-Discrimination Committee, and Presidential Intern at the American University in Cairo, anti-discrimination advocate , “The People Perceived as a Threat to Security: Arab Americans Since September 11,” 7/1, Migration Policy Institute, http://www.migrationpolicy.org/article/people-perceivedthreat-security-arab-americans-september-11,LS) Since the terrorist acts of September 11, 2001, Arab Americans have regularly been featured in the press as a group "of interest" to many federal agencies, particularly the Federal Bureau of Investigation (FBI). Yet government security agencies have recruited them for their language skills — the FBI has hired 195 Arabic linguists since 9/11 although other agencies, such as the Central Intelligence Agency (CIA), have not released the number of new hires. Despite demand, the number of recruits is low due to bureaucratic problems and the difficulties Arab Americans face in getting top-level security clearances. Similar to other U.S. immigrant groups in the past, they are viewed as suspect simply because of their origin. Although the term "Arab American" is often used, it remains misunderstood. Who exactly is an Arab American? Are all Arab Americans Muslim? Has the immigration rate of Arab Americans decreased as a result of 9/11? What has been the net fall-out effect of 9/11 on this group? This article will provide definitions, look at flow data from recent years, and examine the trend of immigration and security policies affecting Arab Americans. Definitions Arab Americans are the immigrants (and their descendents) from the Arabic-speaking countries of the Middle East and North Africa. Under this classification, Arabic-speaking countries include the members of the Arab League and range from Morocco in the west to Iraq in the east (see sidebar). Individuals from Iran and Turkey, where the predominant languages are Farsi and Turkish, respectively, are not considered to be of Arab origin even though these countries are part of the Middle East. According to the U.S. Census Bureau, Arab Americans are those who responded to the 2000 census question about ancestry by listing a predominantly Arabic-speaking country or part of the world as their place of origin. The main Arab-speaking countries cited in the 2000 census included Egypt, Iraq, Jordan, Lebanon, Morocco, Palestine, and Syria. Although some people from Arabic-speaking countries identify themselves as Arab, many do not but are regularly defined as such in the United States by the government and the average American, adding further weight to the term. Because some choose a national identity, such as Lebanese or Egyptian, over the term Arab, the diversity of the community must be recognized at the outset of any discussion about Arab Americans. In truth, there are hot debates about whether there is one or many communities of Arab Americans because of the distance, both physical and emotional, between various groups. In regards to religious affiliation among Arab Americans, surprisingly few studies have been done. However, the Arab American Institute, based on a 2002 Zogby International poll, estimates that 63 percent of Arab Americans are Christian, 24 percent are Muslim, and 13 percent belong to another religion or have no religious affiliation. The Muslim Arab-American population includes Sunni, Shi'a, and Druze. Among the Christians, 35 percent are Catholics (Maronites, Melkites, and Eastern Rite Catholics), 18 percent are Eastern Orthodox (Antiochian, Syrian, Greek, and Coptic Christians), and 10 percent are Protestant. The high proportion of Christians among Arab Americans is partially due to the descendants of Arab immigrants who arrived in the late 19th and early 20th centuries; they mostly came from Mount Lebanon, an area inhabited by Maronite Christians and Druze that is now in Lebanon. Also, minority groups — Maronites and Orthodox Christians from Lebanon, Coptic Christians from Egypt, Shia' Muslims and Chaldeans from Iraq, and Orthodox Christians from Palestine — are immigrating to the United States today in larger numbers than the majority Sunni Muslim population of the Middle East. How Arab Americans Are Counted Unlike Asian, white, or black, "Arab" is not a racial category for the Census Bureau. Rather, Arab Americans are considered white, defined by the Census Bureau as "a person having origins in any of the original peoples of Europe, the Middle East, or North Africa." This distinction dates back to court decisions from 1913 to 1917 on the "whiteness" of Syrian and Palestinian immigrants. Arab Americans who received only the short form of the 2000 census, which is sent to all U.S. households, could check the "white" box for race; if they self-identified as "other" and then identified themselves on the long form as a person from the Middle East or North Africa, the Census Bureau reassigned them to the "white" category. This classification system is in line with other federal guidelines on race and ethnic standards, as set out by Directive 15 by the Office of Management and Budget, and therefore is present in many administrative forms. Since the 2000 census, the Census Bureau has published two reports on Arab Americans, both of which are based on the long form that asks about ancestry and is sent to only one-sixth of all U.S. households. The first report, issued in 2003, reported that about 1.2 million people in the United States reported Arab ancestry alone or in combination with another ancestry. The second report, issued in 2005, focused on the 850,000 people who reported at least one Arab ancestry and no non-Arab ancestries (see Table 1 and Figure 1). Therefore, a person of British-Egyptian heritage would have been included in the first report and excluded from the second. In both reports, the Census Bureau differs from the Arab League membership definition in that it excludes those from Mauritania, Somalia, Djibouti, Sudan, and the Comoros — countries that are members of the Arab League and include large Arabic-speaking populations. Arab-American organizations estimate that the Census Bureau counted only one of every three Arab Americans in 2000, and therefore these organizations estimate the number at approximately 3.5 million, or 1.2 percent of the total U.S. population. This 3.5 million estimate of Arab Americans in 2000 also includes those of mixed Arab and non-Arab heritage, unlike the 2005 Census report. Another way to examine the Arab-American population is to look at the foreign-born population from Arab countries. Although the media portray the Arab-American population as wholly foreign born, the 2005 census report found that only about 50 percent of Arabs in the United States were foreign born; of these, about half were naturalized U.S. citizens and the other half were not citizens. Therefore, half of the Arab Americans in 2005 report were either born in the United States or born abroad to U.S.-citizen parents. Of the foreign born, 46 percent arrived between 1990 and 2000, compared to 42 percent of the total foreign-born population. Immigrant and Nonimmigrant Flows Since 9/11 Many assume that the immigration of Arabs to the United States decreased after 9/11. However, the numbers of those admitted as immigrants or those who became legal permanent residents from Arabic-speaking countries has remained level at around four percent of the total number of foreign nationals admitted as immigrants to the United States, even though there was a drop in 2003. In 2005, over 4,000 nationals from Egypt, Iraq, Lebanon, Morocco, Somalia, and Sudan, in addition to an unknown number of Palestinians, became permanent residents (see Table 2). What has dropped drastically post-9/11 is the number of nonimmigrants who are issued visas and admitted to the United States as tourists, students, or temporary workers. The largest numerical drop between 2000 and 2004 (70 percent) has been in the number of tourist and business visas issued to individuals from Gulf countries, which include Kuwait, Saudi Arabia, Bahrain, Qatar, United Arab Emirates, and Oman. Although there was a decrease in the number of all incoming foreign students between 2001 and 2004, the number of student visas issued to individuals from Arabic-speaking countries dropped substantially. The greatest numerical drop, from 19,696 student visas in 2000 to 6,826 in 2004 (65.3 percent), came from the Gulf countries. The number of Egyptians who entered on student visas dropped 52.7 percent between 2000 and 2004 (see Table 3). One of the first reasons cited for the decrease in the number of foreign students was increased security measures, particularly the Patriot Act and its provision that required the implementation of the Student and Exchange Visitor Information System (SEVIS). SEVIS is an online database that monitors international student compliance with immigration laws by requiring all schools to be certified and to regularly update information on each foreign student, including their visa type, status as a student (full-time enrollment is required), biographical information, class registration, and current address. Recent reports by the Government Accountability Office (GAO) and the Institute of International Education (IIE) found that the decline in the number of international students is not due to SEVIS but, according to IIE, to "real and perceived difficulties in obtaining students visas (especially in scientific and technical fields), rising U.S. tuition costs, vigorous recruitment activities by other English-speaking nations, and perceptions abroad that it is more difficult for international students to come to the United States." Increasing global competition for the best students has added to the drop in the numbers of international students. While these reasons may be the most significant deterrents for all international students, such observations do not adequately answer why the number of Arab students has been disproportionately reduced. The numbers of visitors for business and pleasure has similarly decreased. Businessmen and tourists from the Gulf went from 84,778 in 2000 to 25,005 in 2004, a 70.5 percent decrease. The number of Egyptian visitors dropped 51.5 percent, from 48,904 in 2000 to 23,742 in 2004. The decrease in the number of both visitors and students from Morocco, Jordan, and Lebanon was also significant but lower than that of Egypt and the Gulf states. The causes for these declines have not been investigated although some researchers cite visa delays and fears of discrimination. Security-Related Policy and Arab Americans Another consequence of 9/11 has been the increased monitoring of Arab and Muslim Americans for security reasons. Although most FBI interviews of Arab and/or Muslim Americans have been conducted voluntarily, the increased attention has caused tension, nervousness, and concern to many individuals, as well as community leaders and organizations. A two-year study conducted by the Vera Institute of Justice and funded by the National Institute of Justice, a research agency of the U.S. Department of Justice, confirmed that 9/11 had a substantial impact on Arab Americans and their perceptions of federal agencies, particularly the FBI. The report states, "Although community members also reported increases in hate victimization, they expressed greater concern about being victimized by federal policies and practices than by individual acts of harassment or violence." A major issue of concern remains the 2001 Patriot Act and its provisions that allow increased surveillance without approved court orders. The number of people who have been charged or convicted for terrorism under the act is unclear. In June 2005, President Bush stated that over 400 charges were made as a result of terrorism investigations, but in almost all of these cases, the federal prosecutors chose to charge the plaintiffs with nonterror charges, such as immigration violations. Under the Patriot Act, anyone asked for information about an individual or group of people by the FBI has a gag order placed on them, regardless of whether the identity of the individual becomes public knowledge. In December 2005, President Bush confirmed that he authorized warrantless searches in which the National Security Agency (NSA) monitored phone calls and emails from possibly thousands of citizens and others in the United States who contacted persons abroad. Despite the former NSA director’s reassurances that the program was targeted and focused on persons associated with Al Qaeda, Arab Americans are concerned about the legality of warrantless searches, and the program has increased feelings of being targeted and put under surveillance due to their ethnic background and contact with friends and family in the Middle East. In 2006, several organizations filed lawsuits challenging the legality of warrantless domestic spying as well as the release of thousands of customer phone records by BellSouth, AT&T, and Verizon, citing violation of privacy. In addition, in 2003, the Department of Homeland Security implemented the National Security Entry/Exit Registration System (NSEERS), which required males over the age of 16 from certain countries who had entered the United States since October 2002 to report to immigration offices to be photographed and fingerprinted on an annual basis. Shortly after NSEERS was implemented, immigration authorities fingerprinted, photographed, and questioned 80,000 men. It is not known how many individuals were Arab, but 19 out of the 25 countries on the NSEERS list were Arabicspeaking. Although the main features of this program were suspended in December 2003, nationals of some countries — Iraq, Iran, Libya, Sudan, and Syria — are still bound by the NSEERS requirements. As a result of NSEERS and other initiatives, the number of deportations from the Arab countries on the NSEERS list and an additional five predominantly Muslim countries also on the list increased 31.4 percent in the two-year period following 9/11. The percentile rise in deportation orders for nationals of other countries was 3.4 percent in comparison. Human rights, civil liberties, and Arab-American organizations believe these facts point to a trend of profiling and patterns of selective enforcement of immigration laws. Together, these security and immigration measures have given the impression that the U.S. government believes Arabs and Muslims to be a suspicious and dangerous group to whom constitutional rights and liberties do not apply. Looking Ahead One of the long-term consequences of 9/11 was a questioning of identity and the outward expression of ethnicity and religion. In the last five years, many Arab Americans have asked themselves, How do I present myself when the mention of my ethnicity and/or religion is enough to make others uncomfortable? While some have decided to hide their heritage or privilege another ethnic background — also the reaction of some German Americans after World War I and Japanese Americans after World War II — others have channeled this dilemma into artistic expression. As a result, Arab-American arts have blossomed. Fiction and poetry — particularly by Arab-American women — art exhibits, and comedy acts have found their way into the public domain, giving Arab Americans a more human face. However, heightened security fears and recent terrorist attacks in Europe have kept the Arab American community under the microscope of the FBI and NSA. The perception of surveillance that dominates many local and national-level discussions between Arab Americans and these agencies is not likely to decrease unless pending lawsuits result in the courts finding the warrantless searches or the release of phone records to be unconstitutional and a violation of due process or privacy. While the flow of immigrants has remained slow but steady, the number of students and visitors has slowed down substantially. Although these decreases are unlikely to isolate Arab Americans from their friends and family in the Middle East and North Africa, it may indicate a decrease in the interactions between people who are Arab and live in the Middle East and Americans who live in the United States. In the current political climate, it seems there is a growing need for cultural exchanges — yet the opportunities for those very cultural exchanges are declining. The Arab American Identity Phelps ’13 (Paulina, Author at the Seattle Globalist, Georgetown media group, Africa.redux media, and Saratoga wire, “Arab and Muslim communities react to NSA surveillance leak,” June/25, Seattle Globalist, http://seattleglobalist.com/2013/06/25/araband-muslim-nsa-surveillance-leak/14225,LS) Since the terrorist acts of September 11, 2001, Arab Americans have regularly been featured in the press as a group "of interest" to many federal agencies, particularly the Federal Bureau of Investigation (FBI). Yet government security agencies have recruited them for their language skills — the FBI has hired 195 Arabic linguists since 9/11 although other agencies, such as the Central Intelligence Agency (CIA), have not released the number of new hires. Despite demand, the number of recruits is low due to bureaucratic problems and the difficulties Arab Americans face in getting top-level security clearances. Similar to other U.S. immigrant groups in the past, they are viewed as suspect simply because of their origin. Although the term "Arab American" is often used, it remains misunderstood. Who exactly is an Arab American? Are all Arab Americans Muslim? Has the immigration rate of Arab Americans decreased as a result of 9/11? What has been the net fall-out effect of 9/11 on this group? This article will provide definitions, look at flow data from recent years, and examine the trend of immigration and security policies affecting Arab Americans. Definitions Arab Americans are the immigrants (and their descendents) from the Arabic-speaking countries of the Middle East and North Africa. Under this classification, Arabic-speaking countries include the members of the Arab League and range from Morocco in the west to Iraq in the east (see sidebar). Individuals from Iran and Turkey, where the predominant languages are Farsi and Turkish, respectively, are not considered to be of Arab origin even though these countries are part of the Middle East. According to the U.S. Census Bureau, Arab Americans are those who responded to the 2000 census question about ancestry by listing a predominantly Arabic-speaking country or part of the world as their place of origin. The main Arab-speaking countries cited in the 2000 census included Egypt, Iraq, Jordan, Lebanon, Morocco, Palestine, and Syria. Although some people from Arabic-speaking countries identify themselves as Arab, many do not but are regularly defined as such in the United States by the government and the average American, adding further weight to the term. Because some choose a national identity, such as Lebanese or Egyptian, over the term Arab, the diversity of the community must be recognized at the outset of any discussion about Arab Americans. In truth, there are hot debates about whether there is one or many communities of Arab Americans because of the distance, both physical and emotional, between various groups. In regards to religious affiliation among Arab Americans, surprisingly few studies have been done. However, the Arab American Institute, based on a 2002 Zogby International poll, estimates that 63 percent of Arab Americans are Christian, 24 percent are Muslim, and 13 percent belong to another religion or have no religious affiliation. The Muslim Arab-American population includes Sunni, Shi'a, and Druze. Among the Christians, 35 percent are Catholics (Maronites, Melkites, and Eastern Rite Catholics), 18 percent are Eastern Orthodox (Antiochian, Syrian, Greek, and Coptic Christians), and 10 percent are Protestant. The high proportion of Christians among Arab Americans is partially due to the descendants of Arab immigrants who arrived in the late 19th and early 20th centuries; they mostly came from Mount Lebanon, an area inhabited by Maronite Christians and Druze that is now in Lebanon. Also, minority groups — Maronites and Orthodox Christians from Lebanon, Coptic Christians from Egypt, Shia' Muslims and Chaldeans from Iraq, and Orthodox Christians from Palestine — are immigrating to the United States today in larger numbers than the majority Sunni Muslim population of the Middle East. How Arab Americans Are Counted Unlike Asian, white, or black, "Arab" is not a racial category for the Census Bureau. Rather, Arab Americans are considered white, defined by the Census Bureau as "a person having origins in any of the original peoples of Europe, the Middle East, or North Africa." This distinction dates back to court decisions from 1913 to 1917 on the "whiteness" of Syrian and Palestinian immigrants. Arab Americans who received only the short form of the 2000 census, which is sent to all U.S. households, could check the "white" box for race; if they self-identified as "other" and then identified themselves on the long form as a person from the Middle East or North Africa, the Census Bureau reassigned them to the "white" category. This classification system is in line with other federal guidelines on race and ethnic standards, as set out by Directive 15 by the Office of Management and Budget, and therefore is present in many administrative forms. Since the 2000 census, the Census Bureau has published two reports on Arab Americans, both of which are based on the long form that asks about ancestry and is sent to only one-sixth of all U.S. households. The first report, issued in 2003, reported that about 1.2 million people in the United States reported Arab ancestry alone or in combination with another ancestry. The second report, issued in 2005, focused on the 850,000 people who reported at least one Arab ancestry and no non-Arab ancestries (see Table 1 and Figure 1). Therefore, a person of British-Egyptian heritage would have been included in the first report and excluded from the second. In both reports, the Census Bureau differs from the Arab League membership definition in that it excludes those from Mauritania, Somalia, Djibouti, Sudan, and the Comoros — countries that are members of the Arab League and include large Arabic-speaking populations. Arab-American organizations estimate that the Census Bureau counted only one of every three Arab Americans in 2000, and therefore these organizations estimate the number at approximately 3.5 million, or 1.2 percent of the total U.S. population. This 3.5 million estimate of Arab Americans in 2000 also includes those of mixed Arab and non-Arab heritage, unlike the 2005 Census report. Another way to examine the Arab-American population is to look at the foreign-born population from Arab countries. Although the media portray the Arab-American population as wholly foreign born, the 2005 census report found that only about 50 percent of Arabs in the United States were foreign born; of these, about half were naturalized U.S. citizens and the other half were not citizens. Therefore, half of the Arab Americans in 2005 report were either born in the United States or born abroad to U.S.-citizen parents. Of the foreign born, 46 percent arrived between 1990 and 2000, compared to 42 percent of the total foreign-born population. Immigrant and Nonimmigrant Flows Since 9/11 Many assume that the immigration of Arabs to the United States decreased after 9/11. However, the numbers of those admitted as immigrants or those who became legal permanent residents from Arabic-speaking countries has remained level at around four percent of the total number of foreign nationals admitted as immigrants to the United States, even though there was a drop in 2003. In 2005, over 4,000 nationals from Egypt, Iraq, Lebanon, Morocco, Somalia, and Sudan, in addition to an unknown number of Palestinians, became permanent residents (see Table 2). What has dropped drastically post-9/11 is the number of nonimmigrants who are issued visas and admitted to the United States as tourists, students, or temporary workers. The largest numerical drop between 2000 and 2004 (70 percent) has been in the number of tourist and business visas issued to individuals from Gulf countries, which include Kuwait, Saudi Arabia, Bahrain, Qatar, United Arab Emirates, and Oman. Although there was a decrease in the number of all incoming foreign students between 2001 and 2004, the number of student visas issued to individuals from Arabic-speaking countries dropped substantially. The greatest numerical drop, from 19,696 student visas in 2000 to 6,826 in 2004 (65.3 percent), came from the Gulf countries. The number of Egyptians who entered on student visas dropped 52.7 percent between 2000 and 2004 (see Table 3). One of the first reasons cited for the decrease in the number of foreign students was increased security measures, particularly the Patriot Act and its provision that required the implementation of the Student and Exchange Visitor Information System (SEVIS). SEVIS is an online database that monitors international student compliance with immigration laws by requiring all schools to be certified and to regularly update information on each foreign student, including their visa type, status as a student (full-time enrollment is required), biographical information, class registration, and current address. Recent reports by the Government Accountability Office (GAO) and the Institute of International Education (IIE) found that the decline in the number of international students is not due to SEVIS but, according to IIE, to "real and perceived difficulties in obtaining students visas (especially in scientific and technical fields), rising U.S. tuition costs, vigorous recruitment activities by other English-speaking nations, and perceptions abroad that it is more difficult for international students to come to the United States." Increasing global competition for the best students has added to the drop in the numbers of international students. While these reasons may be the most significant deterrents for all international students, such observations do not adequately answer why the number of Arab students has been disproportionately reduced. The numbers of visitors for business and pleasure has similarly decreased. Businessmen and tourists from the Gulf went from 84,778 in 2000 to 25,005 in 2004, a 70.5 percent decrease. The number of Egyptian visitors dropped 51.5 percent, from 48,904 in 2000 to 23,742 in 2004. The decrease in the number of both visitors and students from Morocco, Jordan, and Lebanon was also significant but lower than that of Egypt and the Gulf states. The causes for these declines have not been investigated although some researchers cite visa delays and fears of discrimination. Security-Related Policy and Arab Americans Another consequence of 9/11 has been the increased monitoring of Arab and Muslim Americans for security reasons. Although most FBI interviews of Arab and/or Muslim Americans have been conducted voluntarily, the increased attention has caused tension, nervousness, and concern to many individuals, as well as community leaders and organizations. A two-year study conducted by the Vera Institute of Justice and funded by the National Institute of Justice, a research agency of the U.S. Department of Justice, confirmed that 9/11 had a substantial impact on Arab Americans and their perceptions of federal agencies, particularly the FBI. The report states, "Although community members also reported increases in hate victimization, they expressed greater concern about being victimized by federal policies and practices than by individual acts of harassment or violence." A major issue of concern remains the 2001 Patriot Act and its provisions that allow increased surveillance without approved court orders. The number of people who have been charged or convicted for terrorism under the act is unclear. In June 2005, President Bush stated that over 400 charges were made as a result of terrorism investigations, but in almost all of these cases, the federal prosecutors chose to charge the plaintiffs with nonterror charges, such as immigration violations. Under the Patriot Act, anyone asked for information about an individual or group of people by the FBI has a gag order placed on them, regardless of whether the identity of the individual becomes public knowledge. In December 2005, President Bush confirmed that he authorized warrantless searches in which the National Security Agency (NSA) monitored phone calls and emails from possibly thousands of citizens and others in the United States who contacted persons abroad. Despite the former NSA director’s reassurances that the program was targeted and focused on persons associated with Al Qaeda, Arab Americans are concerned about the legality of warrantless searches, and the program has increased feelings of being targeted and put under surveillance due to their ethnic background and contact with friends and family in the Middle East. In 2006, several organizations filed lawsuits challenging the legality of warrantless domestic spying as well as the release of thousands of customer phone records by BellSouth, AT&T, and Verizon, citing violation of privacy. In addition, in 2003, the Department of Homeland Security implemented the National Security Entry/Exit Registration System (NSEERS), which required males over the age of 16 from certain countries who had entered the United States since October 2002 to report to immigration offices to be photographed and fingerprinted on an annual basis. Shortly after NSEERS was implemented, immigration authorities fingerprinted, photographed, and questioned 80,000 men. It is not known how many individuals were Arab, but 19 out of the 25 countries on the NSEERS list were Arabic-speaking. Although the main features of this program were suspended in December 2003, nationals of some countries — Iraq, Iran, Libya, Sudan, and Syria — are still bound by the NSEERS requirements. As a result of NSEERS and other initiatives, the number of deportations from the Arab countries on the NSEERS list and an additional five predominantly Muslim countries also on the list increased 31.4 percent in the two-year period following 9/11. The percentile rise in deportation orders for nationals of other countries was 3.4 percent in comparison. Human rights, civil liberties, and Arab-American organizations believe these facts point to a trend of profiling and patterns of selective enforcement of immigration laws. Together, these security and immigration measures have given the impression that the U.S. government believes Arabs and Muslims to be a suspicious and dangerous group to whom constitutional rights and liberties do not apply. Targeted surveillance hurts the Arab American Identity Phelps ’13 (Paulina, Author at the Seattle Globalist, Georgetown media group, Africa.redux media, and Saratoga wire, “Arab and Muslim communities react to NSA surveillance leak,” June/25, Seattle Globalist, http://seattleglobalist.com/2013/06/25/araband-muslim-nsa-surveillance-leak/14225,LS) Since the terrorist acts of September 11, 2001, Arab Americans have regularly been featured in the press as a group "of interest" to many federal agencies, particularly the Federal Bureau of Investigation (FBI). Yet government security agencies have recruited them for their language skills — the FBI has hired 195 Arabic linguists since 9/11 although other agencies, such as the Central Intelligence Agency (CIA), have not released the number of new hires. Despite demand, the number of recruits is low due to bureaucratic problems and the difficulties Arab Americans face in getting top-level security clearances. Similar to other U.S. immigrant groups in the past, they are viewed as suspect simply because of their origin. Although the term "Arab American" is often used, it remains misunderstood. Who exactly is an Arab American? Are all Arab Americans Muslim? Has the immigration rate of Arab Americans decreased as a result of 9/11? What has been the net fall-out effect of 9/11 on this group? This article will provide definitions, look at flow data from recent years, and examine the trend of immigration and security policies affecting Arab Americans. Definitions Arab Americans are the immigrants (and their descendents) from the Arabic-speaking countries of the Middle East and North Africa. Under this classification, Arabic-speaking countries include the members of the Arab League and range from Morocco in the west to Iraq in the east (see sidebar). Individuals from Iran and Turkey, where the predominant languages are Farsi and Turkish, respectively, are not considered to be of Arab origin even though these countries are part of the Middle East. According to the U.S. Census Bureau, Arab Americans are those who responded to the 2000 census question about ancestry by listing a predominantly Arabic-speaking country or part of the world as their place of origin. The main Arab-speaking countries cited in the 2000 census included Egypt, Iraq, Jordan, Lebanon, Morocco, Palestine, and Syria. Although some people from Arabic-speaking countries identify themselves as Arab, many do not but are regularly defined as such in the United States by the government and the average American, adding further weight to the term. Because some choose a national identity, such as Lebanese or Egyptian, over the term Arab, the diversity of the community must be recognized at the outset of any discussion about Arab Americans. In truth, there are hot debates about whether there is one or many communities of Arab Americans because of the distance, both physical and emotional, between various groups. In regards to religious affiliation among Arab Americans, surprisingly few studies have been done. However, the Arab American Institute, based on a 2002 Zogby International poll, estimates that 63 percent of Arab Americans are Christian, 24 percent are Muslim, and 13 percent belong to another religion or have no religious affiliation. The Muslim Arab-American population includes Sunni, Shi'a, and Druze. Among the Christians, 35 percent are Catholics (Maronites, Melkites, and Eastern Rite Catholics), 18 percent are Eastern Orthodox (Antiochian, Syrian, Greek, and Coptic Christians), and 10 percent are Protestant. The high proportion of Christians among Arab Americans is partially due to the descendants of Arab immigrants who arrived in the late 19th and early 20th centuries; they mostly came from Mount Lebanon, an area inhabited by Maronite Christians and Druze that is now in Lebanon. Also, minority groups — Maronites and Orthodox Christians from Lebanon, Coptic Christians from Egypt, Shia' Muslims and Chaldeans from Iraq, and Orthodox Christians from Palestine — are immigrating to the United States today in larger numbers than the majority Sunni Muslim population of the Middle East. How Arab Americans Are Counted Unlike Asian, white, or black, "Arab" is not a racial category for the Census Bureau. Rather, Arab Americans are considered white, defined by the Census Bureau as "a person having origins in any of the original peoples of Europe, the Middle East, or North Africa." This distinction dates back to court decisions from 1913 to 1917 on the "whiteness" of Syrian and Palestinian immigrants. Arab Americans who received only the short form of the 2000 census, which is sent to all U.S. households, could check the "white" box for race; if they self-identified as "other" and then identified themselves on the long form as a person from the Middle East or North Africa, the Census Bureau reassigned them to the "white" category. This classification system is in line with other federal guidelines on race and ethnic standards, as set out by Directive 15 by the Office of Management and Budget, and therefore is present in many administrative forms. Since the 2000 census, the Census Bureau has published two reports on Arab Americans, both of which are based on the long form that asks about ancestry and is sent to only one-sixth of all U.S. households. The first report, issued in 2003, reported that about 1.2 million people in the United States reported Arab ancestry alone or in combination with another ancestry. The second report, issued in 2005, focused on the 850,000 people who reported at least one Arab ancestry and no non-Arab ancestries (see Table 1 and Figure 1). Therefore, a person of British-Egyptian heritage would have been included in the first report and excluded from the second. In both reports, the Census Bureau differs from the Arab League membership definition in that it excludes those from Mauritania, Somalia, Djibouti, Sudan, and the Comoros — countries that are members of the Arab League and include large Arabic-speaking populations. Arab-American organizations estimate that the Census Bureau counted only one of every three Arab Americans in 2000, and therefore these organizations estimate the number at approximately 3.5 million, or 1.2 percent of the total U.S. population. This 3.5 million estimate of Arab Americans in 2000 also includes those of mixed Arab and non-Arab heritage, unlike the 2005 Census report. Another way to examine the Arab-American population is to look at the foreign-born population from Arab countries. Although the media portray the Arab-American population as wholly foreign born, the 2005 census report found that only about 50 percent of Arabs in the United States were foreign born; of these, about half were naturalized U.S. citizens and the other half were not citizens. Therefore, half of the Arab Americans in 2005 report were either born in the United States or born abroad to U.S.-citizen parents. Of the foreign born, 46 percent arrived between 1990 and 2000, compared to 42 percent of the total foreign-born population. Immigrant and Nonimmigrant Flows Since 9/11 Many assume that the immigration of Arabs to the United States decreased after 9/11. However, the numbers of those admitted as immigrants or those who became legal permanent residents from Arabic-speaking countries has remained level at around four percent of the total number of foreign nationals admitted as immigrants to the United States, even though there was a drop in 2003. In 2005, over 4,000 nationals from Egypt, Iraq, Lebanon, Morocco, Somalia, and Sudan, in addition to an unknown number of Palestinians, became permanent residents (see Table 2). What has dropped drastically post-9/11 is of nonimmigrants who are issued visas and admitted to the United States as tourists, students, or temporary workers. The largest numerical drop between 2000 and 2004 (70 percent) has been in the the number number of tourist and business visas issued to individuals from Gulf countries, which include Kuwait, Saudi Arabia, Bahrain, Qatar, United Arab Emirates, and Oman. Although there was a decrease in the number of all incoming foreign students between 2001 and 2004, the number of student visas issued to individuals from Arabic-speaking countries dropped substantially. The greatest numerical drop, from 19,696 student visas in 2000 to 6,826 in 2004 (65.3 percent), came from the Gulf countries. The number of Egyptians who entered on student visas dropped 52.7 percent between 2000 and 2004 (see Table 3). One of the first reasons cited for the decrease in the number of foreign students was increased security measures, particularly the Patriot Act and its provision that required the implementation of the Student and Exchange Visitor Information System (SEVIS). SEVIS is an online database that monitors international student compliance with immigration laws by requiring all schools to be certified and to regularly update information on each foreign student, including their visa type, status as a student (full-time enrollment is required), biographical information, class registration, and current address. Recent reports by the Government Accountability Office (GAO) and the Institute of International Education (IIE) found that the decline in the number of international students is not due to SEVIS but, according to IIE, to "real and perceived difficulties in obtaining students visas (especially in scientific and technical fields), rising U.S. tuition costs, vigorous recruitment activities by other English-speaking nations, and perceptions abroad that it is more difficult for international students to come to the United States." Increasing global competition for the best students has added to the drop in the numbers of international students. While these reasons may be the most significant deterrents for all international students, such observations do not adequately answer why the number of Arab students has been disproportionately reduced. The numbers of visitors for business and pleasure has similarly decreased. Businessmen and tourists from the Gulf went from 84,778 in 2000 to 25,005 in 2004, a 70.5 percent decrease. The number of Egyptian visitors dropped 51.5 percent, from 48,904 in 2000 to 23,742 in 2004. The decrease in the number of both visitors and students from Morocco, Jordan, and Lebanon was also significant but lower than that of Egypt and the Gulf states. The causes for these declines have not been investigated although some researchers cite visa delays and fears of discrimination. Security-Related Policy and Arab Americans Another consequence of 9/11 has been the increased monitoring of Arab and Muslim Americans for security reasons. Although most FBI interviews of Arab and/or Muslim Americans have been conducted voluntarily, the increased attention has caused tension, nervousness, and concern to many individuals, as well as community leaders and organizations. A two-year study conducted by the Vera Institute of Justice and funded by the National Institute of Justice, a research agency of the U.S. Department of Justice, confirmed that 9/11 had a substantial impact on Arab Americans and their perceptions of federal agencies, particularly the FBI. The report states, "Although community members also reported increases in hate victimization, they expressed greater concern about being victimized by federal policies and practices than by individual acts of harassment or violence." A major issue of concern remains the 2001 Patriot Act and its provisions that allow increased surveillance without approved court orders. The number of people who have been charged or convicted for terrorism under the act is unclear. In June 2005, President Bush stated that over 400 charges were made as a result of terrorism investigations, but in almost all of these cases, the federal prosecutors chose to charge the plaintiffs with nonterror charges, such as immigration violations. Under the Patriot Act, anyone asked for information about an individual or group of people by the FBI has a gag order placed on them, regardless of whether the identity of the individual becomes public knowledge. In December 2005, President Bush confirmed that he authorized warrantless searches in which the National Security Agency (NSA) monitored phone calls and emails from possibly thousands of citizens and others in the United States who contacted persons abroad. Despite the former NSA director’s reassurances that the program was targeted and focused on persons associated with Al Qaeda, Arab Americans are concerned about the legality of warrantless searches, and the program has increased feelings of being targeted and put under surveillance due to their ethnic background and contact with friends and family in the Middle East. In 2006, several organizations filed lawsuits challenging the legality of warrantless domestic spying as well as the release of thousands of customer phone records by BellSouth, AT&T, and Verizon, citing violation of privacy. In addition, in 2003, the Department of Homeland Security implemented the National Security Entry/Exit Registration System (NSEERS), which required males over the age of 16 from certain countries who had entered the United States since October 2002 to report to immigration offices to be photographed and fingerprinted on an annual basis. Shortly after NSEERS was implemented, immigration authorities fingerprinted, photographed, and questioned 80,000 men. It is not known how many individuals were Arab, but 19 out of the 25 countries on the NSEERS list were Arabic-speaking. Although the main features of this program were suspended in December 2003, nationals of some countries — Iraq, Iran, Libya, Sudan, and Syria — are still bound by the NSEERS requirements. As a result of NSEERS and other initiatives, the number of deportations from the Arab countries on the NSEERS list and an additional five predominantly Muslim countries also on the list increased 31.4 percent in the two-year period following 9/11. The percentile rise in deportation orders for nationals of other countries was 3.4 percent in comparison. Human rights, civil liberties, and Arab-American organizations believe these facts point to a trend of profiling and patterns of selective enforcement of immigration laws. Together, these security and immigration measures have given the impression that the U.S. government believes Arabs and Muslims to be a suspicious and dangerous group to whom constitutional rights and liberties do not apply. Looking Ahead One of the long-term consequences of 9/11 was a questioning of identity and the outward expression of ethnicity and religion. In the last five years, many Arab Americans have asked themselves, How do I present myself when the mention of my ethnicity and/or religion is enough to make others uncomfortable? While some have decided to hide their heritage or privilege another ethnic background — also the reaction of some German Americans after World War I and Japanese Americans after World War II — others have channeled this dilemma into artistic expression. As a result, Arab-American arts have blossomed. Fiction and poetry — particularly by Arab-American women — art exhibits, and comedy acts have found their way into the public domain, giving Arab Americans a more human face. However, heightened security fears and recent terrorist attacks in Europe have kept the Arab American community under the microscope of the FBI and NSA. The perception of surveillance that dominates many local and national-level discussions between Arab Americans and these agencies is not likely to decrease unless pending lawsuits result in the courts finding the warrantless searches or the release of phone records to be unconstitutional and a violation of due process or privacy. Islamophobia Adv – Surveillance Bad Fear of terrorism results in targeting of Muslims. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] INVASIVE SURVEILLLANCE MEASURES After the 9/11 attacks, domestic fear of future terrorist attacks grew, spurring the national government's focus of more intrusive levels of surveillance. 56Link to the text of the note The government's focus on national security surveillance was indicative of the ballooning of the post-9/11 national security budget, the expansion of technological abilities, and the almost complete unaccountability and secrecy of national security covert operations. 57Link to the text of the note Former Vice President Dick Cheney, a well-known advocate of the government's surveillance programs, has argued that the surveillance programs are necessary if terrorist attacks are to be stopped. 58Link to the text of the note Other major political figures, like Robert Mueller, the current director of the FBI, assert that the loss of privacy for everyday Americans is justified because the eavesdropping has thwarted terrorist plots. 59Link to the text of the note In an address to Congress in 2013, Mueller stated that the "challenge in a position such as I have held in the last 11 years is to [444] balance on the one hand the security of the nation and on the other hand the civil liberties that we enjoy in this country." 60Link to the text of the note Following 9/11, the government instituted specific profiling of U.S. nationals who were residents or citizens of a foreign country of interest and were traveling through the airways. 61Link to the text of the note After the Abdulmutallab attack, the Obama administration reinstated this airport profiling of approximately fourteen countries, most of which were majority Muslim countries. 62Link to the text of the note This program may be similarly compared to the National Security Entry-Exit Registration System Program implemented by President George W. Bush in 2002. 63Link to the text of the note Critics of the 2002 program noted that it failed to capture any terrorists, yet it placed approximately 14,000 of the individuals into deportation proceedings. 64Link to the text of the note This program required male nationals from twenty-five countries, twenty-four of which were predominantly Muslim, who were working, visiting, or living in the United States to report to immigration authorities for fingerprinting and interviews. 65Link to the text of the note Critics of both programs contend that the singling out of individuals from these countries has the effect of singling them out because of their religion or nationality. 66Link to the text of the note Government informants are inserted into Islamic communities to create “terrorist plots” where none exist Al-Arain, 14 (Abdullah Al-Arian, Assistant professor history at Georgetown, School of Foreign Servicein Quatar, “The Informants: Manufacturing Terror”, http://www.aljazeera.com/indepth/opinion/2014/07/informants-manufacturingterror-20147218131267614.html, Al Jazeera Media Network, 21 Jul 2014) On the surface, the scene unfolds without any hint of intrigue. A young Muslim convert named Darren Griffin meets fellow congregants at a local mosque in northwest Ohio. In addition to sharing the same faith as his new friends, they enjoy similar interests: watching sports, playing video games, working out at the local gym, and discussing international affairs. Except the scene ends tragically with a string of arrests, a national media frenzy, and self-congratulation among federal officials claiming to have foiled yet another terrorist plot. The only problem is that Griffin was an FBI plant and the terror plot he supposedly helped thwart was entirely manufactured by the United States government. Purely on the strength of Griffin's aggressive recruitment tactics, three young American Muslims received prison sentences ranging from eight to 20 years. Similar scenarios have played out in many cities across the US during the past decade. "Informants", the new documentary film from Al Jazeera's Investigative Unit, explores a phenomenon that has been far more pervasive than the media, government officials, or community leaders have acknowledged. In addition to sharing the heart-wrenching stories of the victims of these entrapment tactics, the film is unique because it shines a light on the informants themselves, highlighting the crucial role that they played in actively enlisting young men who never demonstrated any inclinations toward engaging in violence. The informants In order to understand how the use of paid informants became such a crucial cog in the FBI's counterterrorism policy, one need only trace the major shift in the US national security paradigm after 9/11. Prior to the September 11 attacks, the FBI employed 10,500 agents, about 2,500 of whom were dedicated to national security investigations. After 9/11, however, the overall number of agents expanded to 13,600, half of whom became devoted to national security. The annual budget of the FBI has risen dramatically from $3.1bn in 2001 to $8.4bn in the current fiscal year. Together, expanded budgets, the availability of advanced technological capabilities, and a permissive political climate combined to create an environment where federal law enforcement agencies enjoyed vastly expanded powers but were also expected to demonstrate immediate results. In the course of investigating American Muslims for possible terrorist threats, the government cast a wide net. It placed tens of thousands of Muslims under constant surveillance, infiltrated community spaces, including mosques, dug through private records, interrogated many Muslims because of their political views and probed for any links to violent activities. These investigations largely turned up nothing, and that was a problem. In order to continue to justify the robust expenditure of resources and the expansive investigative powers, officials needed results in the form of thwarted terrorist plots that demonstrated to American citizens that unless the FBI acted, the next attack was right around the corner. That climate of fear helped rationalise many of the country's worst civil liberties violations committed under the Bush Administration and consolidated as standard practice during Obama's presidency. To sustain the perception of the threat, one had to be created where it did not exist. Enter the informants. As Al Jazeera's investigative film lays out, many of the most high-profile terrorism cases of the last decade were not a product of insidious Muslim sleeper cells uncovered by skillful investigators. Rather, in the absence of actual plots, the FBI actively targeted communities, identifying particularly vulnerable individuals, and sending them informants with the expressed purpose of ensnaring them in a conspiracy. The informants are not government agents. Rather, they are almost always criminal offenders attempting to avoid prison time through their cooperation with the government. From drug dealing to fraud, their criminal history ostensibly provides them the tools they need to maintain their deception, though a crash course on basic Islamic beliefs and rituals is a must. With codenames like "The Trainer", "The Closer", and "The Bodybuilder", they play to their particular strengths while identifying the weaknesses of those they are sent to entrap. In the case of the latter, Craig Monteilh hung out in mosques where he hoped to meet Muslim youth and invite them to work out at a local gym. There, he could ostensibly engage them in conversation about volatile political subjects and broach the topic of terrorism over an intense workout regimen. When his aggressive posture provoked suspicion on the part of community members in southern California, local leaders reported Monteilh to the FBI, apparently not realising that it was the FBI which had sent him into their community in the first place. The community's experience with the "Bodybuilder" is particularly egregious, given the seeming vindictive nature of the FBI's conduct in that case. The local imam, Sheikh Yassir Fazaga, dared to question publicly the veracity of claims made by a local FBI official at a town hall meeting. "The FBI does not take that lightly," Monteilh recalled to Al Jazeera. "So they had me get close to Mr Fazaga, to get into his inner circle." When Monteilh failed to ensnare Fazaga or any other local Muslims into a terrorist plot the FBI attempted to pursue immigration charges against Ahmadullah Sais Niazi, an Afghan immigrant who was one of those who reported Monteilh to the FBI for his suspicious behaviour. But the Department of Justice eventually dropped those charges and so Operation Flex, it seems, ended in failure. This case, however, was the exception. The overwhelming majority of so-called "pre-emptive prosecutions" end in convictions on terrorism charges of individuals who the government is unable to prove would have ever entered into a violent plot on their own accord. More often than not, the FBI targets young Muslims with strong political opinions, usually concerning the role of the US in the plight of Muslims in places like Iraq, Syria, Palestine, and Kashmir. As a former FBI special agent told Al Jazeera about the Ohio case, "The whole purpose was to verify whether it was more than just talk." By treating the political opinions of American Muslims as cause for suspicion, government investigators operate on the assumption that free speech rights guaranteed by the First Amendment of the US Constitution do not extend to a particular segment of the American people. Over the years, the FBI's actions have had a dramatic chilling effect on the ability of Muslims to express their political views. Motivated by such pressures from the government, many community leaders around the country have since attempted to suppress political expression in mosques and community centres. But absent such healthy community spaces through which to channel passions for humanitarian concerns around the globe, it actually becomes more likely that young Muslims could channel their frustrations through alternative modes of oppositional politics. This type of quietist, disaffected atmosphere sanitised of all political expression is precisely the environment in which agent provocateurs thrive. Exploiting poverty In some cases, there is not even any "talk" to motivate the FBI into infiltrating communities. The Liberty City case with which Al Jazeera's investigative film begins concerns a group of impoverished black men in Florida with no history of political activism or inflammatory speech. Nevertheless, the FBI sent in "The Closer" a fast-talking informant named Elie Assaad who operated as the ringleader for an alleged plot to blow up the Sears Tower in Chicago. Swaying the impressionable and impoverished young men with promises of everything from shoes to wear to large sums of cash, Assaad enlists Rothschild Augustine and six others in his conspiracy. The use of informants to target communities is one of the most alarming trends to have developed since 9/11, as it threatens to undo the fabric of a free society. In relaying this story to Al Jazeera's investigators, Assaad and Augustine reveal a number of disturbing practices in the concocted plot. The FBI specifically selected its own south Florida offices as a surveillance target, attempting to position itself as the victim of the conspiracy rather than the originator of it, despite the fact that there is no indication that the men even knew where or what it was. The ceremonial oath of allegiance to al-Qaeda that Assaad administered to the seven men displayed what can only be described as a symbol of the cartoonish imagery with which many in the US government associate Islam and Muslims. Perhaps most worrisome in the case of the Liberty City 7, and an eerily similar case in New York, is the ways in which the FBI has exploited the endemic poverty and social problems from drug use to lack of education that are prevalent within some black communities across the US in order to construct the perception of a terrorist threat. In the latter case, the Newburgh Four were promised a payment of $250,000 by a government informant who they hoped to manipulate in turn. The Newburgh Sting is an HBO documentary, also premiering soon, which chronicles the government's excesses in carrying out this plot and the devastation it has caused to an impoverished community. A startling report utilising the Department of Justice's internal statistics recently stated that in the decade after 9/11, 94.2 percent of federal terrorism convictions were obtained, at least in part, on the basis of preemptive prosecutions. Given how pervasive this practice has been, it is noteworthy that American Muslim civil rights groups have not developed a coordinated response to what has plainly become a widespread use of informants nationwide. In some instances, they have even attempted to downplay the problem of preemptive prosecutions, as in one report by a prominent American Muslim organisation that states that "while the numbers clearly show informants are frequently used by federal law enforcement, a majority of these cases do not involve them at all." The use of informants to target communities is one of the most alarming trends to have developed since 9/11, as it threatens to undo the fabric of a free society. That these recent investigative films have laid bare this troubling phenomenon and displayed its consequences for all to see, is a critical first step in confronting its damaging effect not only on the vulnerable American Muslim community but on American society as a whole. Current domestic surveillance policies promote Islamophobia and discrimination against Muslim-Americans. Greenwald & Hussain 14 (Glenn & Murtaza. Glenn Greenwald is a constitutional lawyer, journalist, and author of four bestselling books on law and politics, including No Place To Hide which discusses the American surveillance state.. Murtaza Hussain is a journalist and political commentator with focuses on human rights and foreign policy. “Meet the Muslim-American leaders the FBI and NSA have been spying on.” Occupy. 7-10-2014. Accessed 7-7-2015. http://www.occupy.com/article/meet-muslim-american-leaders-fbi-and-nsahave-been-spying) The National Security Agency and FBI have covertly monitored the emails of prominent Muslim-Americans—including a political candidate and several civil rights activists, academics, and lawyers—under secretive procedures intended to target terrorists and foreign spies. According to documents provided by NSA whistleblower Edward Snowden, the list of Americans monitored by their own government includes: • Faisal Gill, a longtime Republican Party operative and one-time candidate for public office who held a top-secret security clearance and served in the Department of Homeland Security under President George W. Bush; • Asim Ghafoor, a prominent attorney who has represented clients in terrorism-related cases; • Hooshang Amirahmadi, an Iranian-American professor of international relations at Rutgers University; • Agha Saeed, a former political science professor at California State University who champions Muslim civil liberties and Palestinian rights; • Nihad Awad, the executive director of the Council on American-Islamic Relations (CAIR), the largest Muslim civil rights organization in the country. The individuals appear on an NSA spreadsheet in the Snowden archives called “FISA recap”—short for the Foreign Intelligence Surveillance Act. Under that law, the Justice Department must convince a judge with the top-secret Foreign Intelligence Surveillance Court that there is probable cause to believe that American targets are not only agents of an international terrorist organization or other foreign power, but also “are or may be” engaged in or abetting espionage, sabotage, or terrorism. The authorizations must be renewed by the court, usually every 90 days for U.S. citizens. The spreadsheet shows 7,485 email addresses listed as monitored between 2002 and 2008. Many of the email addresses on the list appear to belong to foreigners whom the government believes are linked to Al Qaeda, Hamas, and Hezbollah. Among the Americans on the list are individuals long accused of terrorist activity, including Anwar al-Awlaki and Samir Khan, who were killed in a 2011 drone strike in Yemen. But a three-month investigation by The Intercept—including interviews with more than a dozen current and former federal law enforcement officials involved in the FISA process— reveals that in practice, the system for authorizing NSA surveillance affords the government wide latitude in spying on U.S. citizens. The five Americans whose email accounts were monitored by the NSA and FBI have all led highly public, outwardly exemplary lives. All five vehemently deny any involvement in terrorism or espionage, and none advocates violent jihad or is known to have been implicated in any crime, despite years of intense scrutiny by the government and the press. Some have even climbed the ranks of the U.S. national security and foreign policy establishments. “I just don’t know why,” says Gill, whose AOL and Yahoo! email accounts were monitored while he was a Republican candidate for the Virginia House of Delegates. “I’ve done everything in my life to be patriotic. I served in the Navy, served in the government, was active in my community—I’ve done everything that a good citizen, in my opinion, should do.” Given that the government’s justifications for subjecting Gill and the other U.S. citizens to surveillance remain classified, it is impossible to know why their emails were monitored, or the extent of the surveillance. It is also unclear under what legal authority it was conducted, whether the men were formally targeted under FISA warrants, and what, if anything, authorities found that permitted them to continue spying on the men for prolonged periods of time. But the five individuals share one thing in common: Like many if not most of the people listed in the NSA spreadsheet, they are of Muslim heritage. “I believe that they tapped me because my name is Asim Abdur Rahman Ghafoor, my parents are from India, I travelled to Saudi Arabia as a young man, and I do the pilgrimage,” says Ghafoor, when told that no nonMuslim attorneys who defended terror suspects had been identified on the list. “Yes, absolutely I believe that had something to do with it.” The FBI—which is listed as the “responsible agency” for surveillance on the five men—has a controversial record when it comes to the ethnic profiling of Muslim-Americans. According to FBI training materials uncovered by Wired in 2011, the bureau taught agents to treat “mainstream” Muslims as supporters of terrorism, to view charitable donations by Muslims as “a funding mechanism for combat,” and to view Islam itself as a “Death Star” that must be destroyed if terrorism is to be contained. John Guandolo, a former FBI counterterrorism official who takes credit for developing a training program for agents on the “Muslim Brotherhood and their subversive movement in the United States,” told The Intercept that he participated in investigations of some of the individuals whose email accounts were monitored. Echoing the “red under every bed” hysteria of the McCarthy era, Guandolo believes that “hundreds” of covert members of the Muslim Brotherhood are active in the United States, that some of them have succeeded in infiltrating the Pentagon, and that CIA director John Brennan is a secret Muslim. Other former and current federal officials say such beliefs are not representative of the FBI or Justice Department. But blatant prejudice against Muslim-Americans is also documented in the Snowden archive. In one 2005 document, intelligence community personnel are instructed how to properly format internal memos to justify FISA surveillance. In the place where the target’s real name would go, the memo offers a fake name as a placeholder: “Mohammed Raghead.” The vast majority of individuals on the “FISA recap” spreadsheet are not named. Instead, only their email addresses are listed, making it impossible in most cases to ascertain their identities. Under the heading “Nationality,” the list designates 202 email addresses as belonging to “U.S. persons,” 1,782 as belonging to “non-U.S. persons,” and 5,501 as “unknown” or simply blank. The Intercept identified the five Americans placed under surveillance from their email addresses. It is unclear whether the government obtained any legal permission to monitor the Americans on the list. The FBI and the Justice Department declined to comment for this story. During the course of multiple conversations with The Intercept, the NSA and the Office of the Director of National Intelligence urged against publication of any surveillance targets. “Except in exceptional circumstances,” they argued, surveillance directly targeting Americans is conducted only with court-approved warrants. Last week, anonymous officials told another news outlet that the government did not have a FISA warrant against at least one of the individuals named here during the timeframe covered by the spreadsheet. The FISA process was enacted in 1978 in response to disclosures that J. Edgar Hoover and a long line of presidents from both parties had used U.S. intelligence agencies to spy on dissidents and political enemies. Intended to allow authorities to covertly investigate suspected spies or terrorists on U.S. soil, the surveillance is often used simply to gather intelligence, not to build a criminal case. The law was revised in 2008—in part to place limits on the controversial program of warrantless wiretaps initiated by George W. Bush after 9/11, and in part to legalize the program’s warrantless eavesdropping on Americans when they speak with foreign surveillance targets. Under current law, the NSA may directly target a “U.S. person” (an American citizen or legal permanent resident) for electronic surveillance only with a warrant approved by the Foreign Intelligence Surveillance Court. Because the FISC operates in complete secrecy—only the Justice Department and the FBI are permitted to attend its proceedings on domestic surveillance—it is impossible to assess how the court applies the standard of “probable cause” in cases of suspected terrorism or espionage. But its rulings are notoriously one-sided: In its 35-year history, the court has approved 35,434 government requests for surveillance, while rejecting only 12. Law enforcement officials familiar with the FISA process told The Intercept that the FISC’s high approval rate is the result of a thorough vetting process that weeds out weak applications before they reach the court. The system, they added, seeks to balance what they consider to be the essential role of surveillance in protecting national security with the civil liberties of potential targets. The NSA issued a statement that reads in part: “No U.S. person can be the subject of FISA surveillance based solely on First Amendment activities, such as staging public rallies, organizing campaigns, writing critical essays, or expressing personal beliefs.” But legal experts have long expressed concern that the secretive nature of the FISA process makes it impossible to know what level of evidence is actually used to authorize surveillance, precisely what it means to be an agent of a foreign power, or whether there is any effective oversight to protect civil liberties. “We have very little idea what this probable cause standard means in individual FISA cases,” says Patrick Toomey, a staff attorney for the National Security Project of the American Civil Liberties Union. “No FISA application or order has ever been publicly disclosed, even to a criminal defendant or his lawyer in cases where the government later brings charges based on that FISA surveillance.” A former Justice Department official involved in FISA policy in the Obama Administration says the process contains too many internal checks and balances to serve as a rubber stamp on surveillance of Americans. But the former official, who was granted anonymity to speak candidly about FISA matters, acknowledges that there are significant problems with the process. Having no one present in court to contest the secret allegations can be an invitation to overreach. “There are serious weaknesses,” the former official says. “The lack of transparency and adversarial process—that’s a problem.” Indeed, the government’s ability to monitor such high-profile Muslim-Americans—with or without warrants—suggests that the most alarming and invasive aspects of the NSA’s surveillance occur not because the agency breaks the law, but because it is able to exploit the law’s permissive contours. “The scandal is what Congress has made legal,” says Jameel Jaffer, an ACLU deputy legal director. “The claim that the intelligence agencies are complying with the laws is just a distraction from more urgent questions relating to the breadth of the laws themselves.” Government agencies have invoked a host of legal theories over the years to justify spying on Americans without obtaining individual FISA warrants. Prior to mid-2008, for example, the NSA could target Americans when they were located on foreign soil simply by obtaining an authorization from the attorney general. The NSA also relies on the so-called “FISA backdoor” to read the emails of Americans communicating with foreign targets without obtaining a warrant, and engages in the bulk collection of “metadata” from Internet service providers without individual warrants. In other cases, it can obtain a warrant against an entire organization—and then monitor the emails of individuals allegedly associated with the group. While the NSA documents do not prove that the government has been systematically monitoring the communications of political dissidents, Jaffer notes that some of the most abusive surveillance practices carried out by the FBI during the 1960s were arguably legal at a time when many Americans believed that the groups targeted by Hoover’s FBI—including antigovernment activists on the left and right—posed a threat to the country. “Some of the government’s surveillance practices today are reminiscent of those earlier abusive practices,” Jaffer says. “Today’s American-Muslim activists occupy the same position that civil-rights and anti-war activists occupied during the 1960s.” Current and former law enforcement officials reject that analogy, and say that the FISA process is too rigorous to permit any abuse. Still, several acknowledge that political speech is sometimes viewed as a sufficient reason to launch an investigation that can culminate in full-blown surveillance. “If you are a political activist calling for violent jihad—yes, that could trigger an investigation,” says Marion “Spike” Bowman, the top FBI lawyer whose office handled all law enforcement requests for FISA surveillance under the Clinton and Bush administrations. Bowman stresses that such investigations are launched only when the bureau believes that speech has crossed the line into incitement. When Edward Snowden turned over a trove of NSA documents last year, he explained that he included the spreadsheet of monitored emails because he wanted to give people subjected to electronic surveillance the opportunity to challenge the spying as unconstitutional. For years, the government has succeeded in having such challenges dismissed on the ground that the various plaintiffs lack standing to sue because they could not prove that they were personally targeted. Thanks to Snowden’s disclosures, those seeking to obtain such a ruling now have specific cases of surveillance against American citizens to examine. So do those charged with reforming the FISA process. Richard Clarke, a former counterterrorism official in the Clinton and Bush administrations, served on the recent White House intelligence review panel convened to address concerns raised by the Snowden revelations. If he had seen the NSA spreadsheet, Clarke says, he would have asked more questions about the process, and reviewed individual FISA warrants. “Knowing that, I would specifically ask the Justice Department: How many American citizens are there active FISAs on now?” he says. “And without naming names, tell me what categories they fall into—how many are counterterrorism, counterintelligence, espionage cases? We’d want to go through [some applications], and frankly, we didn’t. It’s not something that five part-time guys can do—rummage through thousands of FISA warrants.” The “FISA recap” spreadsheet offers a revealing if incomplete glimpse into the murky world of government surveillance. Each email address is accompanied by a date that appears to denote the beginning of surveillance, and another that indicates when it was set to expire. A column called “Collection Status” indicates whether the surveillance was “terminated,” “sustained,” or “pending” as of a particular date. In some cases, the spreadsheet also names the federal agency that requested the surveillance, and a terrorist group, target, or foreign power affiliated with the email address. In addition, each address has a corresponding “Case Notation” code beginning with the prefix “XX.SQF”—a designation that, according to other documents in the Snowden archive, is assigned to all “FISA accounts” as a unique identifier. The five Americans whose email accounts were placed on the list come from different backgrounds, and hold different religious and political views. None was designated on the list as connected to a foreign power. Some have come under sharp public scrutiny for their activities on behalf of Muslim-Americans, and several have been investigated by the government. But despite being subjected to what appears to be long periods of government surveillance, none has been charged with a crime, let alone convincingly linked to terrorism or espionage on behalf of a foreign power. Taken together, their personal stories raise disturbing questions about who the government chooses to monitor, and why. AT: Islamaphobia K Domestic surveillance of Muslim populations is rooted in racialized fear of the other that underpins BOTH a massive authoritarian police state as well as the broader War on Terror. Anti-blackness is not the root cause of this aff either. BUT the aff understands the history of surveillance against the black body and the way that it is now being operationalized against Muslim populations. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] Discussions of the surveillance of Muslim Americans usually begin with 9/11 and make little attempt to locate them in the longer history of racial surveillance in the United States. Yet the continuities are striking, particularly for Black Muslims, who have been seen as extremists and subject to national security monitoring since the 1940s. Already in the late 1960s, Arab American student groups involved in supporting the Palestinian national movement had come under surveillance and, in 1972, the Nixon administration issued a set of directives known as Operation Boulder that enabled the CIA and FBI to coordinate with the pro-Israel lobby in monitoring Arab activists. By the 1980s, but especially after 9/11, a process was under way in which “Muslimness” was racialized through surveillance—another scene of the state’s production of racial subjects. Since all racisms are socially and politically constructed rather than resting on the reality of any biological “race,” it is perfectly possible for cultural markers associated with Muslimness (forms of dress, rituals, languages, etc.) to be turned into racial signifiers.58 This signification then serves to indicate a people supposedly prone to violence and terrorism, which, under the War on Terror, justifies a whole panoply of surveillance and criminalization, from arbitrary arrests, to indefinite detention, deportation, torture, solitary confinement, the use of secret evidence, and sentencing for crimes that “we” would not be jailed for, such as speech, donations to charitable organizations, and other such acts considered material support for terrorism. Significantly, the racial underpinnings of the War on Terror sustain not just domestic repression but foreign abuses—the war’s vast death toll in Afghanistan, Iraq, Pakistan, Somalia, Yemen, and elsewhere could not be sustained without the dehumanization of its Muslim victims. As before, racism at home goes hand in hand with empire abroad. Counterinsurgency thinking that informed the strategies used in Iraq and Afghanistan in the face of popular insurrection are also brought home to be deployed in relation to Muslim American populations. Winning “hearts and minds,” the counterinsurgency slogan first introduced by British colonialists in Malaya, and then adopted by the US military in Vietnam, reappears as the phrase that state planners invoke to prevent “extremism” among young Muslims in the United States. Counterinsurgency in this context means total surveillance of Muslim populations, and building law enforcement agency partnerships with “good Muslims,” those who are willing to praise US policy and become sources of information on dissenters, making life very difficult for “bad Muslims” or those who refuse (in ways reminiscent of the “good” and “bad” Indians). It is a way of ensuring that the knowledge Muslims tend to have of how US foreign policy harms the Middle East, Africa, and Asia is not shared with others. The real fear of the national security state is not the stereotypical Muslim fanatic but the possibility that other groups within US society might build alliances with Muslims in opposition to empire . The various measures that the US national security system has adopted in recent years flow from an analysis of Muslim “radicalization,” which assumes that certain lawabiding activities associated with religious ideology are indicators of extremism and potential violence. Following the preventive logic discussed above, the radicalization model claims to be able to predict which individuals are not terrorists now but might be at some later date. Behavioral, cultural, and ideological signals are assumed to reveal who is at risk of turning into a terrorist at some point in the future.59 For example, in the FBI’s radicalization model, such things as growing a beard, starting to wear traditional Islamic clothing, and becoming alienated from one’s former life are listed as indicators, as is “increased activity in a pro-Muslim social group or political cause.”60 Thus, signifiers of Muslimness such as facial hair, dress, and so on are turned into markers of suspicion for a surveillance gaze that is also a racial (and gendered) gaze; it is through such routine bureaucratic mechanisms that counterterrorism practices involve the social construction of racial others. Official acceptance of the model of radicalization implies a need for mass surveillance of Muslim populations and collection of as much data as possible on every aspect of their lives in order to try to spot the supposed warning signs that the models list. And this is exactly the approach that law enforcement agencies introduced. At the New York Police Department, for instance, the instrumentalizing of radicalization models led to the mass, warrantless surveillance of every aspect of Muslim life. Dozens of mosques in New York and New Jersey and hundreds more “hot spots,” such as restaurants, cafés, bookshops, community organizations, and student associations were listed as potential security risks. Undercover officers and informants eavesdropped at these “locations of interest” to listen for radical political and religious opinions. A NYPD “Moroccan Initiative” compiled a list of every known Moroccan taxi driver. Muslims who changed their names to sound more traditionally American or who adopted Arabic names were investigated and catalogued in secret NYPD intelligence files. It is clear that none of this activity was based on investigating reasonable suspicions of criminal activity. This surveillance produced no criminal leads between 2006 and 2012, and probably did not before or after.61 As of 2008, the FBI had a roster of 15,000 paid informants62 and, according to Senator Dianne Feinstein of the Senate Intelligence Committee, the bureau had 10,000 counterterrorism intelligence analysts in 2013.63 The proportion of these informants and analysts who are assigned to Muslim populations in the United States is unknown but is likely to be substantial. The kinds of infiltration and provocation tactics that had been practiced against Black radicals in the 1960s are being repeated today. What has changed are the rationales used to justify them: it is no longer the threat of Black nationalist subversion, but the threat of Muslim radicalization that is invoked . With new provisions in the Clinton administration’s 1996 Antiterrorism and Effective Death Penalty Act, the FBI can launch investigations of a suspected individual or organization simply for providing “material support” to terrorism—a vague term that could include ideological activity unrelated to any actual plot to carry out violence. While COINTELPRO violated federal laws, today similar kinds of investigation and criminalization of political dissent can be carried out legitimately in the name of countering terrorism. For Muslim populations on the receiving end of state surveillance programs designed to prevent “radicalization,” everyday life increasingly resembles the patterns described in classic accounts of authoritarianism. There is the same sense of not knowing whom to trust and choosing one’s words with special care when discussing politics, and of the arbitrariness and unpredictability of state power.64 With the 2011 leaking of some NYPD intelligence files, individual Muslims have had the disturbing experience of seeing their names mentioned in government files, along with details of their private lives. Numerous businesses, cafés, restaurants, and mosques in New York are aware that the NYPD considers them hotspots and deploys informants to monitor them. And the recent outing of a small number of NYPD informants has meant some Muslims in New York have found that relationships they thought of as genuine friendships were actually covert attempts to gather intelligence.65 Internet Freedom Adv Internet Freedom Good – Court Key Judicial Indepedence Adv JI Adv – Yes Modeling – Generic American Judicial Independence is modeled abroad-It promotes accountable governments, and human rights. Smith, 08 (is a federal judge on the United States Court of Appeals for the Third Circuit.) “PROMOTING THE RULE OF LAW AND RESPECTING THE SEPARATION OF POWERS: THE LEGITIMATE ROLE OF THE AMERICAN JUDICIARY ABROAD” accessed online 7/12/15 http://lr.avemarialaw.edu/Content/articles/AMLR.v7i1.smith.pdf The rule of law1 is fundamental to the freedom enjoyed in the United States today. John Locke explained its essential nature well before the Revolutionary War: Freedom of men under government, is, to have a standing rule to live by, common to every one of that society . . . a liberty to follow my own will in all things, where the rule prescribes not; and not to be subject to the inconstant, uncertain, unknown, arbitrary will of another man. Yet, the rule of law so central to American democracy today has deep historical roots, which long precede even Locke’s lifetime. In ancient Greece, Aristotle considered a variety of constitutions before concluding that “it is more proper that the law should govern than any of the citizens.”3 During our nation’s infancy, Thomas Paine wrote in Common Sense that “the world may know that, so far as we approve of monarchy, that in America the law is king. For as in absolute governments the king is law, so in free countries the law ought to be king; and there ought to be no other.”4 John Adams later memorialized this principle when drafting the Massachusetts State Constitution of 1780, declaring “to the end it may be a government of laws, and not of men.”5 While it was clear the rule of law would play a central role in the federal government following the Revolution, the Founding Fathers deliberated carefully for eleven years before incorporating it into the Constitution in a way that would thwart tyranny and best achieve a free, yet ordered, society.6 The success and stability of our nation today flows, in large part, from our faithful adherence to the rule of law. In addition to its central and vital role in any strong democracy,7 the rule of law has been described as an “unqualified human good.”8 It stands alone in terms of its extensive international endorsement.9 There is a wide consensus among the international community that democratic values, including the rule of law, should be universal— furthered in all nations— because these values preserve and protect human dignity, facilitate accountability in government, and allow access to the political process.10 Reflecting its own growing commitment to fostering democracy abroad, the United States has formally incorporated rule-of-law promotion in its foreign assistance efforts in conjunction with traditional monetary aid .11 The rule of law is increasingly considered one of the most valuable American exports to developing and transitioning nations .12 Effective administration of the rule of law requires an independent, transparent, and accountable judiciary.13 Because of the experience and expertise our federal judges gain in their domestic role, they are well positioned to promote the rule of law abroad. 14 And indeed, federal judges have played a significant role in the effort to advance the rule of law and the democratic values essential to it in other parts of the world. Each year, dozens of federal judges assist in presenting seminars abroad that educate and train judges in other countries on a host of topics including how to oversee a case, how to write an opinion, and the importance of impartiality. I have had the privilege of participating in at least a dozen such programs. Beyond the exhilarating human experiences these programs have provided me, I have gained some background in their structure, objectives, and efficacy. My experience has also given me reason to pause and consider some of the tensions created by the participation of the federal judiciary in efforts to promote the rule of law abroad. One of the more sensitive concerns relates to the federal judiciary’s involvement in matters that touch upon foreign policy, a province conferred by the Constitution to the politically accountable branches of government.15 Judicial participation in these efforts may also raise questions concerning government funding and compliance with judicial ethical obligations. That said, clearly defined roles for participating judges coupled with cognizance of these tensions will allow these important efforts to continue in a manner that maintains the delicate separation-of-powers balance and comports with the Canons of the Code of Conduct for United States Judges.16 JI Adv – Surveillance Key Surveillance laws are especially modeled globally. Ozan O. Varol, 15 Stealth Authoritarianism http://ilr.law.uiowa.edu/files/ilr.law.uiowa.edu/files/ILR_100-4_Varol.pdf The attacks of September 11, 2001, ushered in a new era of surveillance to combat organized crime and terrorism.234 In the United States, for example, the enactment of the USA Patriot Act provided additional surveillance authorities to federal government agencies.235 Many other countries followed suit pursuant to Security Council Resolution 1373, which requires states to change their domestic laws to criminalize terrorism and enact certain surveillance measures.236 Because these surveillance laws are often enacted with the imprimatur of international organizations, they also enjoy a certain level of legitimacy both domestically and internationally. Despite the protections they offer, surveillance laws and institutions can also be employed for two primary anti-democratic purposes. First, surveillance can chill the exercise of civil liberties. As Lilian Mitrou puts it, “Under pervasive surveillance, individuals are inclined to make choices that conform to mainstream expectations.”237 That inclination to support the status quo may impede political and intellectual diversity238 and help protect and entrench the incumbent’s stronghold on government power. In addition, the fear of being watched by the government may cause people to think and speak differently and foment self-censorship.239 Second, governments can use surveillance mechanisms for blackmail. Surveillance can permit the incumbents to gather information about dissidents to blackmail them into silence or discredit them by revealing sensitive, and perhaps embarrassing, secrets to the public.240 In many postcommunist states in Eastern Europe, for example, “secret surveillance files are routinely turned into a weapon in political struggles, seriously undermining democratic processes and freedoms.”241 The information gathered through surveillance can also serve as evidence to prosecute political opponents for non-political crimes. JI Adv – LatAm – Uniqueness – JI Low The Latin American Judiciary is manipulated by the President (retag for the country if you want) Helmke ’14 (Gretchen Helmke, University of Rochester Department of Political Science chair and specializes in comparative politics, “The Puzzle of Purges: A New Theory of Judicial Manipulation with Evidence from Latin America”, http://poseidon01.ssrn.com/delivery.php?ID=1650040660951040650811011260 05012105123084002028060035065096017069124077109105000118025018021 02200800911808312109211500306412010805408602901210102610702811709 00821080170750521251041041120050170810141091110671260901061101221 10088109094125089115116081&EXT=pdf&TYPE=2, Published August 5 2014, Accessed July 13 2015, CMT) Former Venezuelan President Carlos Andrés Pérez provides a perfect case in point. One day after the Supreme Court’s approval of the Attorney General’s accusation of Pérez for mismanaging state funds, the Senate unanimously voted to strip the president of immunity and suspend him from office (Lalander 2010: 138). Or, consider the role that the Paraguayan Supreme Court played in helping congress to oust President Cubas in 1999. Shortly after coming to office, the president issued a decree freeing his political mentor, General Lino Oviedo, from prison, where Oviedo was serving a term for his attempt to lead a coup against the previous government. In response, the Supreme Court struck down the decree and ordered that Oviedo be sent back to prison. The president’s blatant refusal to then comply with the Supreme Court order led Congress to launch its first attempt to impeach Cubas. Although ultimately it took the assassination of vice president Luis Maria Argana, and Cubas’ alleged involvement in it, to succeed in removing the president from office, the Court clearly played a vital role in exacerbating the conflict between the executive and legislative branch to the point where the president’s own survival was at stake. Putting these observations together leads to the opposite pattern of institutional behavior from that captured by conventional wisdom. Whereas insulation theories hold that political 6 uncertainty promotes judicial independence, here I claim just the opposite. In environments where politicians are frequently at risk of being removed from office early, and courts, in part, shape these prospects, the likelihood that the cooperative equilibrium leading to judicial independence obtains will be substantially reduced. Rather, rapid irregular alternations of power force politicians to adopt a warlike mentality. Instead of creating institutions, they destroy them. In turn, two possible types of judicial crises stem from this common mechanism: preemptive strikes and preventive strikes. Preemptive judicial attacks are waged by presidents who are under imminent threat; preventive judicial strikes occur whenever the threat is palpable, but more distal. The differences between former President Lucio Gutiérrez’s attack on the Ecuadorian courts and Bolivian President Evo Morales’ assault on his judiciary help illuminate this distinction. Perhaps nowhere in Latin America has the president’s manipulation of the judiciary in order to cling to power been clearer than it was under Gutiérrez. During his shortlived minority government (2003-2005), the president blatantly used the court as a bargaining chip with his allies. After threats to impeach the president began to mount, Gutiérrez made a fatal last ditch quid pro quo deal with the opposition to pack the court in exchange for the opposition dropping impeachment charges against the president. Given the immediacy of the threat to his presidency, Gutiérrez’s tactical move against the court most closely resembles a preemptive strike. Latin America is transitioning towards JI, despite political corruption and military intervention Popkin, 01 (Margaret Popkin, Executive director due process law foundation, Nov 2001 “Efforts to Enhance Judicial Independence in Latin America: A Comparative Perspective”, http://cejamericas.org/index.php/biblioteca/bibliotecavirtual/doc_view/3787-efforts-to-enhance-judicial-independence-in-latinamerica.html, accessed digitally 7/13/15, SAM) The struggle for judicial independence in Latin America remains an ongoing process, but important developments have taken place in recent years. With the exception of Costa Rica, all the countries included in this study have recently undergone a process of democratic transition after the end of authoritarian rule or, in the case of El Salvador and Guatemala, following an internal armed conflict.3 Not all of Latin America has moved in the same direction nor have all the steps taken yielded positive results. Moreover, new challenges to judicial independence have arisen in the form of massive crime waves, drug trafficking and the efforts to end it, and, in the case of Colombia, frequent threats against judges by the different parties to the armed conflict. Executive efforts to increase control over the judiciary have been undertaken in recent years in Argentina, Panama, and Peru, and concerns have been raised about potential executive intervention elsewhere. Despite the clouds on the horizon, there is substantial consensus that in many countries throughout the region, judiciaries now have a greater degree of external independence – most notably from the executive and the military -- than ever before. JI Adv – Rwanda Judicial Independence in Rwanda is good — reform in 2003 prove Rugege ’07 (Sam Rugege, Chief Justice in Rwanda who was educated at Makerere University and Yale Law school and Oxford University in England, “Judicial Independence in Rwanda”, http://www.mcgeorge.edu/Documents/Conferences/JUDIND_RUGEGE_MASTER. pdf, Published in 2007, Accessed July 13 2015, CMT) Before the 2003-2004 judicial reform in Rwanda, there was substantial corruption among judges, court clerks, and other judicial officers. As a result of these reforms, a number of measures were taken and institutional mechanisms were put in place to combat corruption in the judiciary. First, there was a vetting exercise. The employment of all judges and other court personnel was terminated, and a recruitment exercise took place based on certain criteria. First, all potential judges have to be legally qualified—they must have a minimum of a Bachelor of Laws degree. Part of the problem causing corruption was that judges were not legally qualified, and the temptation to make judicial decisions based on considerations other than law was much higher. Second, they have to be persons of integrity. Those who had a record of corruption or misconduct were excluded. Finally, in addition to the rigorous selection process, there is now a Code of Ethics30 for judges that, among other things, requires impartiality, integrity, and diligence. Article 7 states that “[i]n particular a judge shall refrain from acts of corruption and other related offences and fight against it in an exemplary manner.” Judges and court personnel with a record of corruption are dismissed. The Superior Council of the Judiciary has a committee on discipline which investigates allegations of corruption and other forms of misconduct against judges and other court personnel. Before a final decision is taken by the Council, the accused official is given an opportunity to be heard.31 AT: JI – US – Inevitable Separation of powers guarantees judicial Independence in the United States Ragsdale ’15 (Bruce Ragsdale, served as director of the Federal Judicial History Office at the Federal Judicial Center and as associate historian of the U.S. House of Representatives, “Judicial Independence and the Federal Courts”, fjc.gov, http://www.fjc.gov/public/pdf.nsf/lookup/JudicialIndependence.pdf/$file/Judicia lIndependence.pdf, Published in 2006, Accessed on July 13 2015, CMT) A central principle of the United States system of government holds that judges should be able to reach decisions free from political pressure. The framers of the Constitution shared a commitment to judicial independence, and they organized the new government to ensure that federal judges would have a proper measure of independence from the executive and legislative branches. The Constitution guaranteed that judges would serve “during good behavior” and would be protected from any reduction in their salaries, thus preventing removal by a President who opposed their judicial philosophy and congressional retaliation against unpopular decisions. These twin foundations of judicial independence were well established in the British judicial system of the eighteenth century and had been enacted by many of the new state constitutions following independence from Great Britain. But the constitutional outline for the judiciary also ensured that the court system would always be subject to the political process and thus to popular expectations. The Constitution’s provision for “such inferior courts as the Congress may from time to time ordain and establish,” granted the legislative branch the most powerful voice in deciding the structure and jurisdiction of the nation’s court system. The appointment of judges by the President, with the advice and consent of the Senate, further ensured that important aspects of the judiciary would be part of the political process. The inherent tension between provisions for judicial independence and the Judicial Independence and the Federal Judiciary ~ Federal Judicial Center 2 elected branches’ authority to define the court system has led to recurring debates on judicial tenure and the federal courts’ jurisdiction. Throughout United States history, unpopular court decisions and the general authority of the federal judiciary have prompted calls to limit judges’ terms of office, to define more narrowly the jurisdiction of the federal courts, or to limit judicial review—the courts’ authority to determine the constitutionality of laws. Underlying the debates on judicial independence have been basic questions about the proper balance of Congress’s authority to define the court system and the need to protect a judge’s ability to reach decisions independent of political pressure. The debates have also addressed the extent to which the judiciary should be independent of popular opinion in a system of government where all power is based on the consent of the governed. Other debates have raised the need for safeguards for judicial independence in addition to those provided by the Constitution. JI Adv – China – Uniqueness – JI Low China’s JI is low Weifang, 12 (He Weifang, professor of law at Peking University’s School of Law, in 2011 foreign policy named him to its list of Top 100 Global Thinkers, “The Ongoing Quest for Judicial Independence in Contemporary China”, Pg. 98-99 http://www.brookings.edu/~/media/press/books/2012/inthenameofjustice/inth enameofjustice_chapter.pdf, accessed 7/13/15, SAM) This study has examined to what extent the Chinese judiciary is politically independent, and identified and considered factors that may help explain the degree of judicial independence identified. An exploratory qualitative case study with expert interviews and supplementary secondary data was employed to answer the research question. I created a theoretical framework based on previous studies on judicial independence in authoritarian regimes which separated between four legal issue areas in which the judiciary may be independent: criminal, civil, administrative, and commercial cases. The analysis was devoted to examining the degree of judicial independence in each legal issue area with a focus on interference from both national/central and local political actors through direct case interference, ex parte communication, and policy interference. In each legal issue area I have identified and analyzed explanatory The main finding of this thesis is first and foremost that the Chinese judiciary’s independence is factors. The explanations have been discussed in relation to the existing theories embodied in my theoretical framework. low . Both central and local political organs and actors interfere with judges’ decision-making in various ways, not only through direct case interference and ex parte communication, but also through more indirect policy interference. However, it seems to be mostly local, and not central, political organs and actors that are behind the interference. In political criminal cases, I find that there is substantial political interference, especially direct case interference, both by local and central political actors. This low degree of judicial independence is explained by the regime-related theory and is therefore an expected finding. Political authorities interfere in order to sideline political opponents. In ordinary criminal cases, there also appears to be a quite low degree of judicial independence. This is unexpected and in contrast to previous theory stating that political actors lack incentives to interfere in nonpolitical matters, such as ordinary criminal cases. My findings suggest that it is actually the local police who pressures and interferes with judges in ordinary criminal cases. Their ability to interfere, and the disability of judges to handle criminal cases independently, comes from the fact that police chiefs are often also leaders of local Party organs that are in charge of overseeing the courts. The general view on crime is highly politicized in China, and central political authorities’ are concerned with social and political stability. In turn, the police have been politically empowered by the central authorities. All this has affected the independence of the judiciary in ordinary criminal cases, since the police 94 can impose their will on the courts given their political power. Furthermore, I have argued that the politicized view on crime in general and the close association between Party organs and the police can be traced back to the communist totalitarian regime. JI Adv – JI Good – Democracy JI checks corrupt government, maintains civil rights, and maintains constitutional law Hosseini, 15 (Seyyed Ebrahim Hosseini1, Mehran Ahmadi2, Sa’doun Esmaeili3, and Ako Arya4 1. PhD in International Law, Lecturer in Islamic Azad University Mahabad Branch, Mahabad, Iran 2. M.A. in Private Law, science and research University, Tabriz branch, Tabriz, Iran 3. M.A. in Criminal Law, Islamic Azad University, Damghan, Iran 4. M.A. in International Law, Lecturer in Islamic Azad University Mahabad Branch, Mahabad, Iran, March 2015, “Impact of Judicial Independence Principle on Consolidation of Rule of Law”, pg398-399, http://absronline.org/journals/index.php/masr/article/viewFile/451/470, accessed digitally 7/13/15, SAM) JUDICIAL INDEPENDENCE AND RULE OF LAW Judicial independence principle is vital in the consolidation of the rule of law in international law. This can be examined in some ways. First, the judges free of any political or apolitical pressure would employ legal principles and obligation in dealing with disputes, away from any undue external factors’ leveraging. This attitude strengthens the public respect to the courts and persuades citizens and governance to often refer to the courts to settle their disputes credibly and fairly1. The possibility of fairly settlement of disputes is a vital element in economic and political stability. Economic and political actors shall have faith in an independent and neutral arbitrator to deal with their disputes. This way, rules and regulations are respected. The judges would illuminate the ambiguities in the process of investigation with the examination and clarification of the existing rules and regulations. The judges who use the existing rules, judicial process and unbiased application of the rule to support their decisions regarding any dispute grant a predictable feature to their decisions. Predictability enables the economic and political actors to set their behavior accordingly and this way, they would noticeably help their community’s political stability and economic welloff2. Secondly, the existence of independent courts is necessary to support the individual freedom and right. Individual right might be respected by the constitutions or other rules of the governments, it is however necessary for an independent and unbiased authority to deal with the individual complaints and verdict the realization of their rights. The effective way of doing this issue by the judges is bound to ensure that there is no threat including dismissal, downgrading or even lowering monthly wages or benefits facing them3. Thirdly, the existence of independent courts is the inevitable means to obligate the government to follow the rules and regulations in force within their own territory. In a lawabiding society, the government can be held responsible by the court. Therefore, judicial independence – a division of the powers, plays a significant role in the maintenance of individual rights and freedom. The presence of independent powers would obviously provide the setting for disputes. Some disputes can be settled using political arrangements and strategies. However, it doesn’t seem logical to settle all disputes through political methods (Torbert, 2014). Considering what has been mentioned so far, we can’t help drawing this conclusion that the principle of judicial independence is of top significance in establishment and consolidation of the rule of law principle. It is the judicial independence which ultimately puts the rule of law at first and its absence means the lack of priority for the rule of law in due society. It is clear that the absence of rule of law in a society would put the law under question. As Aristotle states: where there is no rule of law, there is no constitution4. JI Adv – China – Uniqueness – JI Low China no longer wants Judicial Independence Gang 15 (Qian Gang is known for his tenure as managing editor of Southern Weekend, one of China’s most progressive newspapers, Qian Gang is one of China’s foremost journalists. Qian was also a co-creator and executive editor of “News Probe,” CCTV’s pioneering weekly investigative news program with nearly 20 million viewers. Qian collected historical documents for Chinese Boy Students, a book and five-hour documentary series on 120 young Chinese students sent to universities in the United States by the Qing government in the late 19th century, 1/14/15, China Media Project, Who gave “judicial independence” a death sentence?”, http://cmp.hku.hk/2015/01/14/37754/, 7/13/15, HDA) In recent weeks, China has slipped into a place of turmoil with respect to its discourse on the concept of “judicial independence,” or sifa duli (司法独立). The recent hostility in official circles toward what has long seemed a point of consensus within the Chinese Communist Party sends a worrying signal for rule of law in the country. On January 7, more than 100 websites in China re-posted an article from the Party’s official People’s Daily called “Our Rule of Law Cannot Travel the Same Road as the West’s ‘Judicial Independence'” (我们的法治不能 走西方“司法独立”的路子). The article, written by politburo member Zhang Chunxian (张春贤), the top leader of China’s Xinjiang Uygur Autonomous Region, kicked up a storm of confusion on China’s internet. Over the past three decades of reform, the slogan “judicial independence” has been consistently upheld as something positive. Why, now, were the tables turning? In the Maoist Era, the Term Goes “Black” In China’s pre-reform period, political discourse was a simple matter of black or red. Anything that wasn’t red, meaning accepted as a part of Mao Zedong’s official discourse, was by definition “black” — unwelcome and dangerous. After 1949, the Chinese Communist Party announced that it would “repeal all laws, acts and judicial systems of the reactionary and repressive Kuomintang government.” From that point on, the notion of “judicial independence” was mercilessly criticized, branded a “black word” (黑色词语). One of the chief goals during the first few years of Communist rule in China was to redefine the relationship between the country’s new rulers and the administration of justice. When the Provisional Organization Procedures for People’s Courts (人民法院暂行组织条例) were promulgated in September 1951, Communist authorities emphasized that courts at every level must accept the leadership and oversight of corresponding government leaders (People’s Daily, September 5, 1951). The case was made more directly in the October 30 edition of the People’s Daily that same year, which stated that “judicial work must actively serve politics” ( 司法工作必须积极地为政治服务) From 1952 to 1953, judicial organs in China engaged in what was described as a struggle “to oppose the old legal concepts” (反对旧法观念). Among the concepts on the chopping block: the belief that it was a violation of the principle of “judicial independence” for Party chiefs at the city and county levels to serve concurrently as presidents of the local court (法院院长); the belief that it intruded on the rights and responsibilities of judges to allow court presidents priority in the issuing of sentences; the belief that allowing military judge advocates to actively repress counter-revolutionaries obstructed the independent exercise of judicial organs (People’s Daily, August 22, 1952); the belief that “criminal law is subject to universality” (刑法具有世界性), that it must stress “the protection of the rights of the individual” and that “all are equal before the law” (People’s Daily, October 17, 1952). Despite this “struggle,” China’s new constitution, introduced in 1954, maintained some notion of court independence, saying in Article 78 that “the people’s courts shall exercise trials independently, subject only to the law” (人民法院独立进行审判,只服从 法律). Furthermore, the constitution made clear in Article 83 that “the people’s prosecutors at various levels shall exercise their powers independently, without interference from local state organs.” All notions of independence were tossed out the window during the 1957 Anti-Rightist Movement. The idea of judicial independence was roundly condemned in the October 9, 1957, edition of the People’s Daily. The official front-page commentary was called, “Serious Struggles Are Still Ahead on the Front Lines of the Legal System” JI Adv – JI Good – Econ/Stability Judiciary Independence key to economic growth and stability McCormack 11 (Wayne McCormack professor in the college of law at the University of Utah, 2011, Foreign Aid and Judicial Independence, http://aiddata.org/sites/default/files/wright_et_al_2015_aid_judicial_independence.pdf, 7/10/15, HDA) The post-Colonial Era has brought a new awareness and immediacy to the role of the judiciary. The rule of law is critical to the safety and welfare of any society. In the past decade, almost every nation in the world has faced crises of one sort or another. Several nations are attempting to recover from a crisis of mass violence or trying to escape a pattern of violence. Less volatile developing nations may be experiencing economic and social crises while making the transition into the global economy. Meanwhile, developed nations have hit roadblocks involving both economics and security. In all of these instances, the judiciary is a critical player, and judicial independence becomes a major concern. The articles in this Symposium address various aspects of the role of the judiciary in times of crisis. Most of them speak from the perspective of a specific country—the United Kingdom, United States, India, Iraq, and Israel. The sixth article draws on the author’s experience with the former Soviet republics and the Middle East to make the point that many governments are in transition, just as the United States was in transition for much of its history. It might not be immediately clear why the current experiences of developed countries such as the United Kingdom and the United States are considered times of crisis compared to the struggles of post-Ba’athist Iraq, or how the comparatively well-established but still maturing judiciaries of Israel and India relate to the others. The details of those correlations will emerge later, but for now, it will suffice to say that the judiciaries of all of these countries have faced challenges to their autonomy and authority, while the countries themselves have faced challenges to national security and economic stability. These articles discuss countries that are in crisis for at least three different reasons. Two countries are faced with violent threats to their population from nonstate actors: the United States and Israel. Two are in transition to new judicial models: the United Kingdom and India. Some are founding new governments: Iraq and the former Soviet countries. In the past decade, the West has mounted Herculean development efforts in a variety of settings: emerging economies (primarily in southern Asia, Africa, and South America), the former Soviet bloc, and countries embroiled in violence. In all of these settings, judges face the daunting task of achieving impartiality, maintaining their independence, and simultaneously providing some measure of accountability for their own actions. As emerging nations have struggled both politically and economically, a dominant theme has been the need for developed nations to lend expertise to developing nations.1 Among the assumptions inherent in that theme are the following. The developing nations in particular need complementary economic and legal systems; neither can exist without the other. The health of the people necessitates a functioning and at least minimally fair economic system—without which there is no point in attempting to build other systems. The operation of an economic system requires a credible legal system, one that is also functioning and at least minimally fair—without assurance that disputes will be resolved by the rule of law, little investment can occur and therefore very little productive work can be performed. Simultaneously, infrastructure needs civil engineering, food provision needs agricultural expertise, and so on. Because neither an economic nor a legal system can thrive in the chaos of wartime, there is a dilemma posed by violence and the rule of law. A justice system can hardly operate effectively in the midst of chaos, but chaos is difficult to forestall without a functioning justice system. That reality may bedevil U.S. efforts in places such as Afghanistan, but it also confronts many judges on a daily basis in societies facing lesser levels of violence. The stereotype of the judge sitting solemnly above the fray and detached from reality has opened the judiciary to some ridicule, and even some harsh attacks. While there is some merit in the stereotype, judges themselves are aware of the need to maintain connection to the real world. JI Adv – JI Good – Democracy/Econ Judicial independence key to democracy and economic growth Wright et al. 15 (Joe Wright an associate professor in the Department of Political Science at Pennsylvania State University and previously held the Jeffrey L. and Sharon D. Hyde Early Career Professorship. He completed my Ph.D. at UCLA in 2007. Prior to arriving in State College, he was a post-doctoral research associate at Princeton University and a visiting faculty fellow at the University of Notre Dame. Dr. Dietrich is an Assistant Professor of Political Science at the University of Missouri, Columbia. Prior to joining Mizzou, she was a Postdoctoral Research Associate at the Niehaus Center for Globalization and Governance at Princeton University. She received her Ph.D. in Political Science at Penn State University in 2011. Molly Ariotti is a fourth year graduate student in Political Science at Penn State, with a major field in comparative politics (minors in methods and geography). I completed my undergraduate work at Binghamton University, which consisted of a double major in Political Science and Geography. 4/6/15, Penn State University, “Foreign Aide and Judicial Independence”, http://aiddata.org/sites/default/files/wright_et_al_2015_aid_judicial_independence.pdf, 7/10/15, HDA) In the past two decades, donor governments increasingly embrace judicial independence as an important component of advancing democracy. We develop and test an argument that links foreign aid to judicial independence through the mechanism of incumbent-led democracy promotion. Because judicial independence improves the investment environment necessary for sustained economic growth, both donors and recipient governments generally have an interest in using aid resources to improve judicial independence. Thus foreign aid should increase judicial independence. During election periods, however, when judicial independence can influence the distribution of power in the recipient country, incumbents are more likely to find aid investments in an independent judiciary politically costly. Therefore, during election periods in recipient countries, donor and recipient interests are less likely to align and the relationship between aid and judicial independence should weaken. We employ an instrumental variable model to test this argument with a global sample of aid-eligible countries. The literature on the effects of foreign aid has received considerable attention among academics and policy-makers. While some evidence exists that links aggregate foreign aid flows to democratic progress (Goldsmith, 2001; Dunning, 2004; Wright, 2009; Heckelman, 2010; Bermeo, 2011), other work suggests that aid is similar to a resource curse, where “windfall” income in the form of foreign aid hinders development by supporting the survival of nonrepresentative institutions (Moss, Pettersson and van de Walle, 2006; Djankov, Montalvo and Reynal-Querol, 2008; Morrison, 2009; Bueno de Mesquita and Smith, 2009).1 Foreign aid is heterogeneous, however,2 which has prompted scholars to disagregate aid into distinct sectors and delivery mechanisms to investigate external influence on democratic change. This work demonstrates that donors are selective when allocating foreign aid across different sectors and types (Dietrich, 2013, Forthcoming) and that they carefully choose among different strategies to shape democratic change (Dietrich and Wright, 2015). Even within the individual category of democracy and governance aid, which has served as focal point for students of external promotion (Carothers, 2007; Bush, 2015), donors link aid with different outcomes and deliver the assistance using different mechanisms. For instance, donors can promote democracy via bottom-up pressure, by financing civil society groups and opposition (Finkel et al., 2008). They can also pursue incumbent-led democracy promotion tactics whereby donor governments collaborate with the incumbent government in efforts to strengthen the capacity of state institutions.3 Dietrich and Wright (2015) show that incumbent-led democracy promotion is the most common strategy among donors across time.4 This particular strategy dovetails with donor efforts to promote development as it focuses on the build-up of indigenous state capacity. Funding of civil society and opposition, on the other hand, is more infrequent. It can work against development objectives in the short-term if the bottom-up pressure causes political instability.5 In this paper, we develop and test an argument that links foreign aid to judicial independence through the mechanism of incumbent-led democracy promotion. Over time, donor governments have increasingly embraced judicial independence as an important pillar for advancing democracy. Some have even argued that the establishment of the “rule of law”, including judicial independence, is necessary before democratic deepening can occur (Carothers, 2007). Donor governments typically promote judicial independence in two ways: they can require recipient governments to engage in judicial reform through conditions attached to economic aid. Alternatively, they can directly invest in judicial reform by designing specific aid projects that guide the recipient public sector in their implementation. In both cases, donors rely on cooperation by local authorities in recipient countries. Among students of economic development, judicial independence is thought of as a sine qua non for the enforcement of property rights and contracts (Haggard and Tiede, 2011) as well as for lowering transaction costs associated with captial investment (Williamson, 1985). Over time evidence has accumulated documenting a systematic positive link between judicial independence and economic growth (Feld and Voigt, 2003; Henisz, 2000). From this growth perspective, it is easy to see how incumbents in recipient countries can benefit from institutionalizing judical review. And although donors and incumbent governments may disagree over the motives that drive the promotion of judicial independence –whether they originate in theories of democratic change or economic growth – we posit that donor and incubment goals largely align in favor of judicial independence. We expect this alignment between donors and incumbents to hold across democracies and autocracies6 but we expect it to weaken during election times, when independent courts can directly influence election outcomes.7 The conditional nature of our argument suggests that foreign aid should increase judicial independence unless judicial review becomes politically costly. As costs of judicial independence increase, which we argue occurs when incumbents stand for re-election, we expect incumbents to withdraw their support from externally funded judicial reform activities, or increase control over the judiciary branch to maintain their position of power. This incentive should sharpen when elections are more closely contested. This study contributes to our understanding of democracy promotion in two ways. First, it presents a new framework that accounts for heterogeneity among donor governments’ democracy promotion stratgies and electoral dynamics in aid-receving countries. Second, it establishes that judicial independence is not only an important area through which donors can influence the democratic process abroad. It also posits that the electoral cycle shapes incumbent governments’ incentives to use aid resources to implement judicial review. The results directly reinforce a line of work that focuses on the testing of the various causal mechanisms through which donors promote democracy abroad. JI Adv – JI Good – Econ Judicial independence creates economic growth Feld and Voigt 04 (Lars Feld is a Public Economics, Public Finance, Law and Economic. Stefan Voigt is a Development Economics, Institutional Economics, Law and Economics. 2004, ResearchGate, Judicial Independence and Economic Growth: Some Proposals Regarding the Judiciary, http://www.researchgate.net/publication/237619174_Judicial_Independence_and_Economic_ Growth_Some_Proposals_Regarding_the_Judiciary1, 7/10/15, HDA) The judiciary has frequently been called “the least dangerous branch” (e.g., Hamilton 1787/1961, Federalist Paper #78). This evaluation might be one reason why the judiciary is rarely moved to center stage during discussions concerning issues of constitution al design. To give just one example: in his treatise on “Comparative Constitutional Engineering,” Sartori (1994) deals extensively with electoral systems (majoritarian vs. proportional) as well as with the modus of electing the executive (presidential vs. parliamentary systems) but the term “judiciary” does not even appear in the index. It has, however, been hypothesized that judicial independence (JI) is one central aspect in the proper functioning of the judiciary as part of the concept of separation of powers as it has been developed by Montesquieu and further concretized by Hamilton, Madison, and Jay, the authors of the Federalist Papers. Feld and Voigt (2003) have recently presented two indicators that aim at making judicial independence measurable. Their first indicator deals with de jure independence, i.e. the independence of the superior courts as it can be deduced from legal documents. Their second indicator deals with de facto independence, i.e. the degree of independence that the superior courts factually enjoy. Estimating the impact of judicial independence on economic growth, Feld and Voigt (2003) find that while de jure judicial independence does not have an impact on economic growth, de facto judicial independence positively influences real GDP per capita growth in a sample of 56 countries. The impact of de facto judicial independence on economic growth is robust to outliers, to the inclusion of several additional economic, legal and political control variables and to the construction of the index. The authors thus conclude that judicial independence matters for economic growth. If judicial independence matters for growth, economists ought to reconsider its role when discussing issues of constitutional design. Accordingly, the main question of this paper is to ask what components of de jure and de facto judicial independence are particularly conducive to economic growth and ho w they interact with the constitutional and legal environment in the different countries.3 This investigation is based on a cross section of 73 countries extending the Feld and Voigt (2003) data set. In a first step, we replicate the result of the former paper—namely that the independence of superior courts matters for economic growth—for the extend ed data set. In a second step, we inquire into the effects of the organizational structure of the judiciary. In a third step it is asked whether institutional arrangements that are not part of the judiciary themselves have an impact on economic growth and whether there is an interaction of other constitutional and legal provisions with JI. We find that de facto JI has a robust and highly significant positive impact on economic growth. Looking at the components of de jure JI, the specification of the procedures, of the accessibility and of the term length of highest court judges in the constitution show a modestly significant positive impact on economic growth, while a wide accessibility of the highest court as well as the highest court’s power for constitutional review are negatively affecting economic growth. The other components of de jure JI do not appear to have an impact. With respect to de facto JI, no deviations from ‘normal’ average term length, low numbers of changes of the number of judges since 1960 and a competitive income of judges are the main factors influencing growth. With regard to the impact of the organizational structure of the courts on economic growth, we find no significant differences between courts organized as constitutional c ourts and courts 3 The World Bank ha s been involved in a number of programs dealing with similar, yet not identical goals: whereas our interest focuses on the independence of the judiciary from the other two government branches, the World Bank ha s often put emphasis on the efficiency of the court system . Dakolias (1999) has explained that efficiency-enhancing me asures within the judiciary can be kicked off without having to wait for the consent of th e other government branches. A more recent description of the organized differently. Concerning the additional constitutional and legal environment, our results indicate that the positive impact of de facto JI on economic growth is stronger in presidential than in parliamentary systems as well as in systems with a high extent of checks and balances. De facto JI appears to be effective independent of the age of a constitution. On the contrary, if a state is able to implement de facto JI, countries with older constitutions have a growth disadvantage. To non-economists, the approach take n in this paper might appear very odd: according to many, the primary function of the judiciary would be to enhance justice, fairness, or equity. Yet, these goals do not necessarily conflict with economic growth. If the degree to which these other goals are realized can be kept constant and different institutional arrangements promise different levels of growth (or per capita income), it makes sense to argue in favor of the implementation of those institutional arrangements that are most conducive to economic growth. In this paper, we are concerned with the economic consequences of institutional choices regarding the judiciary broadly conceived. It is thus a positive paper. As long as the underlying goal—economic growth—is shared, it can easily be turned into constitutional advice . The choice of institutional arrangements itself will, however, not be endogenized. We are thus not concerned with possible reasons of constitution-makers to choose different institutional arrangements with regard to the judiciary (for this question, see Landes and Posner 1975, Ramseyer 1994, and Ginsburg 2002). The remainder of the paper is organize d as follows: in section 2, there will be a short review of the existing literature, section 3 presents a number of hypotheses concerning the effects of JI, judicial structure and the structure of state organization on economic growth, the section 4 contains the description of our data set as well as own World Bank’s activities can be found in a recent edition of the World Development Report (2002, especially chapter 7). estimations. In section 5, some preliminary conclusions regarding constitutional design are drawn, and section 6 concludes. JI Adv – JI Good – Lesotho Judicial Independence key to Lesotho stability Ellett 13 (Rachel Ellett is Associate Professor of Political Science. Rachel received her PhD in Political Science from Northeastern University in 2008. Her research is located at the intersection of politics and law. Rachel writes on judicial politics, rule of law and development, and lawyers as political actors in southern and eastern Africa and the commonwealth Caribbean. She has conducted fieldwork in Uganda, Tanzania, Malawi, Botswana, Lesotho, Barbados and Trinidad. She recently published "Going off bench: Protecting Judicial Autonomy in Competitive Clientelist Regimes" with Alexei Trochev in the Journal of Law and Courts (2014) and "Courts and the emergence of statehood in post-colonial Africa" in Northern Ireland Legal Quarterly (2013). She has also published in Comparative Politics, PS and Law and Courts. In 2013 her book "Pathways to Judicial Power in Transitional States: Perspective from Africa Courts" was released by Routledge. Rachel consults with the U.S. based organization Freedom House and has written extensive reports on judicial independence in Lesotho and Malawi, 5/29/13, Freedom House Southern Africa, Politics of Judicial Independence in Lesotho, https://freedomhouse.org/sites/default/files/Politics%20%20of%20Judicial%20Independence% 20in%20Lesotho.pdf, 7/10/15, HDA) Lesotho is a small landlocked country entirely surrounded by South Africa. Since gaining independence from British rule in 1960 Lesotho has faced manifold challenges towards achieving political stability and sustained economic growth. The population of Lesotho remains overwhelmingly rural-agrarian and despite some economic growth, gains in GNI per capita have been small and life expectancy has dropped. In 2011 Lesotho placed below average for countries classified by the United Nations as ‘low human development.’1 Since transitioning from authoritarian rule in the early 1990s Lesotho has struggled to establish a stable multiparty democracy, particularly during election periods. These challenges are compounded by the failure to fully address fundamental governance issues such as the relationship between traditional institutions and the state.2 As is the case in all democratic states, the establishment of mechanisms of accountability is critical to political and economic development in Lesotho. To be truly effective these institutions must span the formal and informal sector and, they must transect horizontal and vertical dimensions of accountability.3 Policymakers and academics have increasingly turned their attention to the foundational importance of strong, transparent and fully functional rule of law institutions to economic and political development. First and foremost the courts’ role in resolving conflict is essential to maintenance of the rule of law. A stable and predictable investment climate is rooted in the ability of courts to apply the law in a predictable and consistent manner. Second, in transitioning democracies the courts can play an important role in acting as a restraint on overzealous executives, hegemonic political parties and human rights abusers. Given the importance of rule of law to both political and economic development, it is within this context that Freedom House Southern Africa has commissioned a report on judicial independence in Lesotho. The Lesotho judiciary’s history as paramount defender of the rule of law is uneven. Despite being infused with a fairly robust set of institutional protections and a history of strong personnel, the judiciary continues to face a number of challenges. These challenges relate to three major substantive areas: 1) long-term resources constraints, 2) public perceptions of corruption and weak independence and, 3) a hostile and unstable political environment. The goals of this report are twofold: Part I assesses the current state of judicial independence in Lesotho; Part II reviews the scope and type of interference experiences by the Lesotho judiciary. Finally, while the introduction to this report provides analysis and description of the historical backdrop to contemporary Lesotho the greater part of the analysis focuses on the last ten years (2002-2012). Each section of the report is structured around a taxonomy of judicial independence/interference. Judicial independence is compartmentalized into five broad descriptive categories; each of which contains a number of sub-elements. These sub-elements are captured through a combination of checklist items and descriptive analysis. Category i Scope of Judicial Power and Category ii Differentiation and Separation of Powers focus on the formal legal and political distribution of power as it relates to the judiciary. Category iii Internal Institutional Safeguards examines the internal factors – both formal and informal – that shape and protect judicial independence. Category iv Transparency speaks to the need for access to information in order to monitor judicial independence. Finally, Category v External Institutional support articulates the significance of judicial allies’ in buttressing strong judicial institutions. Seeking to move beyond a rigid constitutional definition of judicial independence to a more holistic approach, this framework is interdisciplinary and captures both the informal and formal relationships between courts, government, groups and individuals. The taxonomy of interference is captured across five major categories: Manipulation of Personnel, Institutional Assaults, Personal Attacks on Judges, Budget Manipulation and, Attempted Cooption of Judges. This section of the report is a straightforward description of the interference experienced by judges in Lesotho over the last ten years. The overall performance of the Lesotho judiciary exhibits no substantially serious issues related to professionalism and/or independence. After applying the framework (see Figure 2) to Lesotho three broad weaknesses were observed: 1. Separation of Powers Chronic underfunding and inadequate autonomy from the Ministry of Justice continues to be a serious drag on the performance of the judiciary. Further, it undermines institutional legitimacy in the eyes of the public and weakens the morale of judicial officers. 2. Internal Institutional Safeguards Perceptions of judicial independence in Lesotho are very weak. Perceived weaknesses are primarily due to structural problems related to the appointments procedures and internal administrative structure. 5 6 3. External Institutional Support There has been an increase in the politicization of the judiciary and attacks on judicial independence since the 2007 election. This is due in part to the amplified political volatility and subsequent split within the ruling Lesotho Congress for Democracy (LCD) party which has necessitated keeping the judiciary under tight control. 4. These weaknesses are further detailed and diagrammed in Figure 1 below: JI Adv – Yes Model – Iraq Iraq ready to model Judicial Independence Gluck 08 (Jason Gluck is a senior program officer for Rule of Law and director of USIP's Constitution-Making Program. Gluck's focus is on the design and implementation of constitution-making processes in post-conflict and transitional states. He has advised government officials and civil society actors on issues of constitutional reform in Burma, Iraq, Liberia, Libya, Sierra Leone, Somalia, Sudan, South Sudan, Yemen and elsewhere. Substantively, Gluck's areas of expertise include constitutional design, federalism and minority rights. 3/17/08, United States Institute of Peace, Judicial Independence in Iraq, http://www.usip.org/programs/projects/judicial-independence-in-iraq, 7/10/15, HDA) ROL played a key role in helping to create the Iraqi Committee for Judicial Independence (ICJI), a network of representatives from the government, judiciary, and civil society that provides crucial input on issues facing the country’s judiciary. ROL continues to work with ICJI to educate members of the judiciary and the general public on the issue of judicial independence. ROL played an important role in helping create the Iraqi Committee on Judicial Independence, a consortium of representatives from the Ministries of Human Rights and Justice, the judiciary, the legal community, civil society organizations, academia and the media from across Iraq. The ICJI has provided a forum for the development of consensus recommendations regarding the country's judicial system, and continues to consult with the Constitutional Review Committee and the Council of Representatives more generally to gain assurances for the independence of the judiciary. Following the judicial federalism conference in March 2009, ROL hosted a two-day conference on judicial independence – a particularly timely and much needed conference given that only in 2009 was the Kurdish judiciary separated from the KRG Ministry of Justice. The conference expanded on previous work by USIP to assist judicial authorities and civil society organizations in securing safeguards for the independence of the judiciary. One outcome is the consideration of opening a Kurdistan branch of ICJI. Other results from the conference and next steps will feed into a weeklong training of judges in coordination with the CEELI Institute this summer. ROL has encouraged building the capacity of the judiciary, which has been enacted through a number of Iraqi-owned developments. ICJI began hosting educational seminars for members of the Council of Representatives and has provided recommendations to parliament on constitutional amendments and draft laws impacting the independence of the judiciary. A staff member from ICJI spearheaded the first law journal in Iraq (see the first issue below), and ICJI recently successfully completed its third annual ICJI conference (report forthcoming). JI Adv – Yes Model – Brazil, Dubai Brazil, Dubai, and Ghana all looking to model there courts Georgia Law N.D. (The University of Georgia School of Law is regarded as one of the nation's top law schools. Our school offers the Juris Doctor degree (J.D.) , the Master of Laws degree (LL.M.), and the Master in the Study of Law degree (M.S.L.) and features a welcoming community in a charming locale. The challenging curriculum and experienced professors dedicated to teaching the theoretical foundations of law and providing hands-on experience make Georgia Law an excellent place for your legal studies, University Law, International Judicial Training Program (IJTP) at the University of Georgia, http://www.law.uga.edu/international-judicial-training-program-ijtp-university-georgia, 7/10/15, HDA) A strong and independent judiciary is the foundation of a democratic country's stability. The International Judicial Training Program (IJTP) seeks to foster increased judicial independence, efficiency, and accountability, thereby increasing public and investor confidence in national judiciaries. The emphasis on judicial independence, court administration, case management, ethics, continuing education, and implementation is designed to foster long-term, systemic change in participant countries. IJTP is a collaboration between the University of Georgia School of Law's Dean Rusk Center and the university's Institute of Continuing Judicial Education. Since its inception in 1998, the program has trained more than 1000 judges and court personnel at the University of Georgia School Of Law. Its participants have hailed from countries such as Argentina, Armenia, Brazil, Egypt, Ghana and the Czech Republic. IJTP facilitates reform by offering capacity-building judicial administration programs tailored to the individual needs of each participating country. Designed to introduce foreign judges and court personnel to the U.S. judicial system, IJTP hosts seminars (up to two weeks) at the UGA School of Law and at sites throughout the state and includes sessions with the Georgia Supreme Court, Georgia Court of Appeals, and other specialized courts. Examples of topics covered in prior training programs include court administration, judicial budgeting, caseload management, alternative dispute resolution, court technology, and judicial ethics and professionalism . IJTP Partnerships Brazil Since 1998, when the Supreme Court of the State of Pernambuco, Brazil, requested that its judges and court personnel be trained by the University of Georgia on issues concerning continuing education, more than fifty judges, administrators, and members of the Pernambuco judiciary have trained through IJTP. The idea was to train a cadre of judges and court personnel who would constitute the backbone of Pernambuco's Institute of Continuing Judicial Education. One of the many outcomes of the strong partnership between IJTP and the Pernambuco judiciary was the development of a Code of Judicial Conduct by the Pernambuco Supreme Court. Dubai In November 2009, IJTP traveled to Dubai and conducted 3 days of training for 30 members of the United Arab Emirates and the Bahrain judiciary in case flow management and judicial leadership. This marked the first time that IJTP partnered with a foreign organization – The Dubai Judicial Institute (DJI). Prominent speakers included Judge Doris Downs of Fulton County Superior Court, Judge David Emerson, current member of the Georgia Supreme Court Technology Advisory Committee and Judicial Counsel of Georgia; and Mark Beer, Registrar of the Dubai International Financial Centre Courts. Ghana IJTP expanded into Ghana as part of concrete plans to further extend the program's reach in other countries and regions. Rusk Center staff collaborated with Ghana Judicial Service officials to identify concrete strategies for reform within the guidelines of the Ten-Year Strategic Plan for the Judicial Service—a reform structure developed by the United Nations Development Programme's National Institutional Renewal Programme (NIRP). Under the sponsorship of this UNDP and the World Bank, members of the Judicial Service of Ghana, Ministry of Finance, and Ministry of Justice, as well as the informational technology consultant to the Judicial Service, attended a program on court automation at UGA. The training led to the implementation of a Fast Track Court in Ghana, which reduced the average time for adjudication of cases, originally five-to-seven years, to six months. This model court has drawn the attention of international donors who are willing to fund a number of additional Fast Track Courts in Ghana. JI Adv – Pakistan – Uniqueness – JI Low Judicial corruption runs rampant in Pakistan Iqbal N.D. (Nasira Iqbal, is a retired judge of Lahore High Court. She is married to Justice (R) Dr. Javid Iqbal (Sr.), Hilal-e-Imtiaz, Former Chief Justice of Lahore High Court and retired judge of the Supreme Court of Pakistan, N.d., American Bar Association, Judicial Independence Abroad: The Struggle Continues, http://www.americanbar.org/publications/human_rights_magazine_home/human_rights_vol36 _2009/winter2009/judicial_independence_abroad.html, 7/10/15, HDA) Judicial independence in Pakistan is perhaps best understood through the prism of military intervention and multiple revisions of the Pakistani Constitution. When Pakistan was created in 1947, its founders envisioned a state where the constitution would be supreme. It would provide for a division of powers among the executive, the legislature, and the judiciary, each able to function independently in its own sphere. In 1949, Pakistan’s Constituent Assembly passed the Objectives Resolution, which stated that the territories included in Pakistan would form a federation; that those internal units would be autonomous and would guarantee fundamental rights, equality before law, status, opportunity, social, economic, and political justice, freedom of thought, expression, belief, worship, and association; and that the independence of the judiciary would be fully secured. However, Pakistan has been under martial law for more than half of its sixty-one years, and its constitution has been rewritten several times during that period, notably in 1956, 1962, and 1973. These constitutions, in turn, were abrogated or suspended by military adventurers when they imposed martial law. Nonetheless, the Objectives Resolution formed the preamble of the three successive constitutions and in 1985 became a substantive part of the constitution. The constitutional provisions regarding the powers and composition of superior courtsСthose delineating the qualifications, appointment, and terms and conditions of service of judgesСin theory guarantee judicial independence. Fighting for citizens’ rights. While Pakistan has witnessed its share of dubious court decisions, it likewise has seen an honest and determined effort to seek judicial decisional independence. Among the former, the Supreme Court on three occasions relied on the doctrine of “state necessity” to declare that martial law had been validly imposed in State v. Dosso (1958), Begum Nusrat Bhutto v. Chief of Army Staff (1977), and Zafar Ali Shah v. General Pervez Musharraf (2000). Yet in 1972, after General Yahya Khan resigned and handed over power to the popularly elected government of Zulfiqar Ali Bhutto, the Supreme Court, headed by Chief Justice Hamoodur Rahman, held in Asma Jilani v. Government of Punjab (1972), that the assumption of power and the martial law proclaimed by Khan in 1969 was unconstitutional and invalid. These contradictory judgments demonstrate that whenever the constitution is abrogated or suspended, the independence of the judiciary goes into eclipse, yet when there is a civilian, democratic government, the courts assert their independence as guardians of the constitution. For the most part, courts have worked independently and for the good of the citizenry, providing relief against excesses of the executive. They have held that when a statutory functionary acts in an oppressive and unjust manner, courts have the power to grant relief to the aggrieved party. Murree Brewery Ltd. v. Government of Pakistan (1972). Similarly, courts have held that all legal steps taken by citizens are meant to advance the cause of justice, not to entrap litigants in a blind corner so as to frustrate the purpose of law. Thus a mere slip up on procedure cannot operate as an impediment to the dispensation of justice. Mir Mazar v. Azim (1993). In Shehla Zia v. WAPDA (1994), the Supreme Court expanded the fundamental rights to life and dignity by including protection of the environment and quality of life. In Mohtarma Benazir Bhutto v. President of Pakistan (1998), it held that tapping of telephones and eavesdropping by government authorities was immoral, illegal, and unconstitutional. In Sh. Liaquat Hussain v. Federation of Pakistan (1999), the Supreme Court declared that the establishment of military courts for the trial of civilians was beyond the powers enumerated in the Pakistan Constitution. Attempting to elevate the status of women, in Ghulam Ali v. Mst Ghulam Sarwar Naqvi (1990) the Supreme Court declared that no waiver by a female can deprive her of her right to inheritance of immovable property and the law of limitation would not operate as a bar to her claim. Supporting women’s right to education, the court declared that if numerous girl students qualified for admission to medical colleges on the basis of merit, the provision of special seats for female students could not restrict their number. Shirin MunirКv.КGovernment of Punjab (1990). In 2001, the Lahore High Court declared the Pakistan Citizenship Act of 1951 was discriminatory and invalid to the extent that it provides that the foreign spouse of a Pakistani male is eligible for acquiring Pakistan nationality but the foreign male spouse of a Pakistani female citizen is not entitled to this benefit. That court also held that free consent of a woman is a prerequisite for a valid marriage ( Mst. Humaira Mehmood v. State (1999)) and that murder in the name of “honor” is not merely the physical elimination of a man or a woman, it is at the sociopolitical level a blow to the concept of a free, dynamic, and egalitarian society ( Muhammad Siddique v. State (2002)). Thus, whenever the country was governed under a constitution, the judiciary acted independently to safeguard the rights of the citizens and to uphold the rule of law. But when judges were called upon to adjudicate on the imposition of martial law while the constitution was held “in abeyance,” they thought it wiser to exercise judicial prudence. They were aware that if they delivered a judgment that was not acceptable, the military dictators could remove them with impunity and replace them with eager opportunists, precipitating a descent into chaos. Pressure by the public or media for upholding the independence of the judiciary was lacking. Against this backdrop, the courts tried to ensure governance according to law rather than to the whims of military commanders. This mode of reasoning represents one strain of Pakistani judical thought, adopted by Chief Justice Muhammad Munir, which may be termed “judicial pragmatism.” It has been opposed by another, “judicial purism,” espoused by Rahman and other eminent judges who have followed his example. Recent encroachments on independence. The defining moment in the Supreme Court’s move toward judicial independence came on March 9, 2007, when Chief Justice Iftikhar Muhammad Chaudhry was suspended by General Pervez Musharraf on alleged charges of misuse of power when he did not oblige Musharraf and refused to resign. He had worked hard to clear the backlog of cases while simultaneously taking suo moto notice and deciding thousands of human rights cases of poor and vulnerable victims of injustice across the country. He gave judgments against the excesses of public functionaries regardless of the consequences. In the Pakistan Steel Mills case, he declared that the Cabinet Committee on Privatization, headed by the prime minister, grossly violated the law in selling the mills. While pursuing the case of so-called “missing persons,” he held the government responsible and observed that it was the duty of the state to protect people’s lives and to ensure their safety. He also canceled, as harmful to the environment, the New Murree Project and other urban development schemes undertaken by the government to benefit various members of the power elite. Thousands of lawyers, citizens, and the media rallied to his support. Lawyers took to the streets in peaceful processions and boycotted the courts. Ultimately, Chaudhry was reinstated by the judgment of a fifteen-member bench of the Supreme Court on July 20 of that year. On November 3, however, Musharraf preempted an impending court decision against his reelection and invoked emergency powers, suspending the constitution. Under his directions, the chief justice and seven other judges were arrested. Musharraf replaced Chaudhry with Justice Abdul Hameed Dogar. Dogar promptly obliged by declaring Musharraf validly elected as president and by declaring valid Musharraf’s National Reconciliation Ordinance, which provided immunity from prosecution to numerous corrupt public functionaries. Martial law was lifted and a considerably disfigured version of the constitution was restored on December 15. General elections were held in February 2008. On March 24, the newly elected government released Chaudhry, his colleagues, and his family from incarceration. Musharraf resigned under pressure on August 18. Asif Ali Zardari, who promised to restore Chaudhry to office, was elected president on September 6, but the restoration of the judiciary to its pre-November 3, 2007, position has still not come to pass. Those who have benefited from the judgments of a pliant judiciary, particularly by the validation of the dubious National Reconciliation Ordinance, are not eager to accept an independent judiciary. However, the lawyers’ movement and the proactive media have forced average citizens to realize that good governance, economic and social justice, peace, stability, freedom from terror, and credibility in the comity of nations cannot be achieved without an independent judiciary. The future destiny of Pakistan will be determined by the elected representatives of the people. Rule of law must be upheld by an independent, impartial judiciary. The alternative is a descent into chaos. Hon. Nasira Iqbal is a retired justice who served on the Lahore High Court in Lahore, Pakistan. A View from Kenya by Hon. Mary A. Ang’awa The lack of confidence in the Kenyan judiciary has a long history. This was recently borne out by the elections of December 2007. When the results were announced, the losers felt cheated and were angry. When they were told, “If you are not satisfied with the election results, go to court and challenge them,” they responded, “We have no confidence in the judiciary; we refuse to go to court.” As a judicial officer of twenty-seven years at that time, fourteen on the High Court of Kenya, this remark cut me to the core. Instead of organized and rational legal intervention, violence broke out and the country burned. It was a crushing blow to be unable to arbitrate, comment, or intervene in the events because a matter cannot be judicially reviewed unless it is brought before a court by any party. I attempted to join independent groups established to foster peace among the communities, but this severely limited my ability to ascertain whether there might be potential litigants among them. Some constitutional background. The Kenyan judiciary is based on the British system, with the major difference being that no jury system exists. The judiciary is comprised of three tiers, including (1) the subordinate courts, presided over by magistrates; (2) the superior courts, presided over by puisne judges of the High Court; and (3) the Court of Appeal, presided over by the judges of appeal. The judges have security of tenure, whereas the magistrates do not. Like most Commonwealth countries, Kenya adapted a constitution that was used by most of the former British colonies when they gained their independence. Nearly all of these constitutions contained the Declaration of Human Rights. In the current Kenyan Constitution, the executive powers are vested in the president as head of the executive branch, and the legislative power is vested in Parliament, but no similar enactment was made concerning the judicial authority being vested in the judiciary. This created an imbalance between the judiciary and the legislature and executive, with the outcome that the judiciary was constructed on the weakest foundation. Attempts at reform. This shortcoming, and others, of the current constitution were patently evident to many Kenyans. The chapter in the constitution on the judiciary was clearly one where the public wanted reform. The Constitution of Kenya Review Commission was established in 2002, and it was intended to be driven by the people rather than by the government. The Review Commission mandated “an advisory panel of eminent Commonwealth judicial experts” to reconsider the chapter on the Kenyan judiciary and to give its input on the proposed new constitution. Surprisingly, the Court of Appeal resisted this panel’s investigations and fielded two separate court cases to stop the review process. Similarly, a committee established for the judiciary by the chief justice ended its meetings with the commission. In protest, members of the Law Society wore yellow ribbons on their robes and took to the streets. The few judges who openly supported the review process found themselves transferred to stations far distant from the capitol, which is what happened to me. In the end, the dispute boiled down to one issue: Should there be a separate court, known as a Supreme Court, that would address constitutional issues and that would not be presided over by the current judges of the Court of Appeal? Some interested parties suggested that all the judges should resign simultaneously and reapply for their jobs afresh. This time their actual qualifications would be taken into account, such as the extent of their work experience and whether they had obtained additional academic law degrees. In May 2002, the panel of experts released a report finding a “crisis of confidence” in the judiciary. The panel suggested this was caused by the politicization of appointments of judicial officers, and it pointed to the need for a guarantee of security of tenure and for judicial remuneration to be delineated in the constitution, so that judicial officers would be protected from job uncertainty and salary cuts. They also concluded that reforms were urgently required to restore public confidence in the judiciary and that enhanced transparency, independence, and accountability were necessary. Further, they opined that widespread corruption had crippled and compromised the judiciary, regardless of the constitutional issues. Yet 2002 was an election year, and Parliament was dissolved earlier than scheduled, forcing the work of the commission to come to a halt. After the 2002 elections, a new government assumed power, ending twenty-four years of rule by the previous government. When the review process began again, a new draft that had been reworked by the government under the auspices of the attorney general was substituted for the original draft, the effect of which was to compromise it considerably. The stakeholders on the reforms of the judiciary nonetheless were of the opinion that the legal reforms contained in the new proposed draft should emphasize making the judiciary independent, accountable, and effective. The drafters opposed making reforms piecemeal. They declared that financial and budgeting autonomy for the judiciary was essential. They felt that the process for judicial appointment should be clearly outlined, as should the provisions for discipline and removal of judges from office. They similarly felt that access to justice issues and the backlog of cases needed to be made part of the reform agenda. If such reforms were enacted, they said, this would restore public confidence in the judiciary. The newly proposed constitution, which advocated land reform and many other provisions not related directly to the judiciary, was voted down in a national referendum in late 2005, and as such the 2007 general elections were held under the old rules. Further, the judicial reforms that had been instituted piecemeal in the interim, while substantial, nonetheless did not inspire confidence in the independence of the judiciary to resolve the disputes that arose after those elections. To understand this, we need to look at what comprises independence of the judiciary. To quote Wikipedia, Judicial independence is the doctrine that decisions of the judiciary should be impartial and not subject to influence from the other branches of government or from private or political interests. In most cases, judicial independence is secured by giving judges long tenure, and making them not easily removable. Some definitions of judicial independence distinguish only decisional independence and institutional independence. I am nevertheless persuaded that judicial independence may be divided into four categories that I have discussed in greater depth elsewhere. These are (1) judicial independence, which relates to the decision-making process; (2) juridical independence, which relates to the finality of the decision; (3) administrative independence, which relates to the autonomy of management of affairs; and (4) budgetary independence, which relates to being autonomous financially. Judicial self-regulation and progress. As far back as 1998, in recognition of problems within the judiciary, the chief justice set up a Committee on the Administration of Justice (commonly known as the Kwach Committee), which admitted for the first time that corruption existed within the judiciary. Unfortunately, the chief justice passed away shortly thereafter and the next chief justice did not fully implement the findings of this report before resigning when the new government came to power. In September 2003, the next chief justice established another commission, commonly known as the Ringera Commission, which prepared a report that called for the full implementation of the Kwach Committee report. It similarly noted that judicial corruption was rampant. In a separate report, the commission named twenty-five judges and eighty-three magistrates as being corrupt, and both reports were disclosed to the press. The effect was damaging. Most of the judicial officers opted to resign and take their dues. A few faced the tribunal and were reinstated. Unfortunately, the disciplinary procedures were irregular because no fair hearing was given nor strict rule of law followed. Hence, the security of tenure was compromised. The judiciary then set up a standing committee in 2005 known as the Ethics and Governance Subcommittee. Its first incarnation, known as the Onyango Otieno Committee, continued to investigate corruption. It was still so much a problem that in May 2006 Transparency International, a global organization fighting corruption, named the judiciary as the No. 6 “bribe taker” in Kenya, which was nevertheless an improvement from the No. 3 slot in the year 2004. Today, the judiciary does not appear in that list. The Onyango Otieno Committee took a different approach and kept secret the names of those found corrupt. To date, no disclosure or actions taken against those who have been found wanting has been made public, and no official report has been published by the government. This committee was followed by the Kariuki Kihara Committee in 2007, and it, too, has not published open accusations against judges or magistrates. The days when the security of tenure was curtailed by Parliament in order to fire judges appear to have passed. The executive rarely interferes in judicial decision making. The infrastructure of courts is being upgraded. Judges have been provided with computers that work well, especially in Nairobi. One of the most positive aspects surrounding the judiciary is that law reporting, which did not exist for twenty years, is now flourishing. An annual colloquium is now held regularly to interact and exchange views. The recent taxation on judges’ allowance was reconsidered. A training institute for judicial officers was established and will long be remembered as an extremely positive milestone in Kenya’s judicial reform history. Conclusion. The failure of confidence in the Kenyan judiciary can be explained by the lack of independence of the judiciary, which in turn has been compromised by corruption. To achieve this independence, the judiciary must be made autonomous and achieve budgetary and financial independence from the executive. This would require a change in the constitution to give authority to the judiciary to be independent. Kenya needs to work toward complete transparency in the selection of judges. Judges themselves must be diligent in upholding the rule of law in an environment that is conducive to doing so. In the end, we are left with a larger question: Is judicial independence and a regular adherence to the rule of law possible where only sixty-one judges of the Court of Appeal and the High Court, working together with 250 magistrates, serve a population of thirty-four million? It is only a matter of time before the Supreme Court will face calls for new measures of accountability to act as a counterweight to the new judicial independence. The trigger may be a high profile and politically-sensitive human rights case. In order to defend the new judicial independence, the Supreme Court must cultivate a public commitment to its lawmaking role by demonstrating governance improvements resulting from the new institutional arrangements. In Canada, the principal justification for the Supreme Court's role in fundamental rights cases is the ‘dialogue theory'. First popularised in a 1997 law review article by Peter W. Hogg and Allison A. Bushell, dialogue theory posits that while judges exercise discretion, they are engaged in an interactive dialogue with the other branches of government about rights issues.72 The theory places limits on the judicial role by emphasising that Parliament has the final word in the dialogue as a result of the structure of the Charter of Rights and Freedoms. 73 Dialogue theory has been expressly endorsed by the Supreme Court of Canada.74 Yet observers have pointed out that the Canadian dialogue is sometimes more like a judicial monologue given political reluctance to challenge judicial decisions that hold rhetorical advantages, particularly in human rights cases.75 In the result, legislative ‘responses' include the repeal of offending statutory provisions or the taking of other action in direct compliance with judicial directives, such as the Reference re Manitoba Language Rights case, where the legislature hastily translated its entire repertoire of statutory legislation into the French language before the Supreme Court of Canada's declaration of invalidity took effect (which would have resulted in a “legal vacuum with consequent legal chaos” given that all statutory instruments exclusively in English were held to be unconstitutional and thus invalid).76 Dialogue theory might provide some answers to the legitimacy concerns of judicial lawmaking but it is a descriptive theory in that it does not immediately justify why courts should be part of a dialogue in the first place, particularly if there is no such thing as a ‘correct' policy answer: what makes judicial values superior to the values of the executive or legislature? Some evidence relating to the improved quality of the democratic process as a result of judicial contributions may be required.77 Even as a descriptive theory, dialogue offers an idealised view that overstates the Government's participation in the discussion over rights, which is potentially misleading and could increase the comfort of courts to engage in politically-charged lawmaking: dialogue theory cuts against the grain of deference to the elected branches of government by actively seeking out the pronouncements of courts as an important part of the on-going dialogue. Despite these limitations, it seems that some form of dialogue theory looms on the horizon in the United Kingdom given the dialogic structure of the Human Rights Act.78 It remains to be seen, however, whether the Government will be comfortable sharing governance with the courts and ultimately dencentralising its political power. A further justification offered for the new judicial independence is the increased capacity of the courts to hold the executive to account. The Supreme Court has seized upon the accountability function to justify its institutional autonomy. In his February 2011 speech, Lord Phillips stated that because “the individual citizen is subject to controls imposed by the executive in respect of almost every aspect of life”, courts must review executive actions for legality, and thus “it is from executive pressure or influence that judges require particularly to be protected”.79 However, English judges have had little difficulty in holding the executive to account through judicial review for decades, so it is not entirely clear how the new judicial independence enhances this role.80 If the idea is that the scope and intensity of judicial supervision will be expanded through judicially-constructed rules as a result of the new judicial independence, it raises many of the same legitimacy concerns over judicial lawmaking as previously discussed. The impact of the new judicial independence on other judicial functions must also be considered. While this article focused on the lawmaking of appellate courts, the functions of the courts cannot be so neatly divided, especially in the public mind. Changes to one judicial function may alter the functioning of others. Emboldened and institutionally autonomous courts, wading deeper into controversial issues pitting individuals against the political majority, may undermine public confidence in the core judicial function of dispute resolution. By revealing the political nature of rights-based adjudication, the decisions of courts in controversial cases may threaten the perceived impartiality of the trial judge in resolving ordinary conflict. Paradoxically, in such a situation, the new judicial independence would counteract the very thing it was designed to do: protect the status of the judge as a third party to the dispute. As a result of this possibility, a critical eye must be cast upon the direction in which the new judicial independence leads the courts to ensure continued public confidence in the administration of justice. JI Adv – Turkey – Uniqueness – JI Low Turkey’s independence Judicial independence id declining Misztal and Michek 14 (Blaise Misztal is the director of the national security program at the Bipartisan Policy Center (BPC), having previously served as the project’s associate director and senior policy analyst. At BPC, Misztal has researched a variety national security issues, including: Iran and its nuclear program; cyber security; stabilizing fragile states; and public diplomacy in the 21st century. He has testified before Congress and published op-eds in The Washington Post, The Wall Street Journal, The Weekly Standard, The New Republic, and Roll Call. In addition, Misztal wrote and directed the 2009 “Cyber ShockWave” simulation that aired on CNN. Jessica Michek joined the Bipartisan Policy Center (BPC) as an administrative assistant for the Foreign Policy Project in February 2014, having started with BPC as an intern in May 2013. Prior to joining BPC, Michek served as a virtual intern for the U.S. Embassy in Bahrain, working to monitor trials related to the unrest in Bahrain since the Arab Spring. As an undergraduate, Michek focused her studies on the Middle East and North Africa, studying abroad in Amman, Jordan and writing her honors thesis on the impact of U.S. aid on Jordan’s foreign policy. Michek graduated with honors from Oberlin College in May 2013 with a B.A. in politics, having also received Oberlin’s John D. Lewis Memorial Prize for excellence in international politics, 12/12/14, Bipartisan Policy Center, HSYK Elections and the Future of Judicial Independence in Turkey, http://bipartisanpolicy.org/blog/hsyk-elections-and-the-future-of-judicialindependence-in-turkey/, 7/13/15, HDA) Turkey’s judiciary is losing its independence. At issue is a seeming commitment of a majority of new HSYK members to issue rulings and decrees in support of the ruling party. Indeed, progovernment candidates ran on a platform promising to “work in harmony with the executive,” proclaiming their subservience to Erdoğan and the AKP. A CHP deputy explained, “[i]t shows that the rule of separation of power is being destroyed. Constitutionally there has to be a separation of power and the judicial system has to be impartial and apolitical.” As an opposition deputy stated, “[t]his HSYK is the AKP’s.” Ahmet Gündel, a retired Supreme Court of Appeals prosecutor has voiced fear that the government may attempt to use the HSYK to punish judges and prosecutors who attempt to investigate government corruption or those who will not toe the government line. As he explained, “[t]he [members of the judiciary] will fear that they might, after a complaint against them, be reassigned to another post [in another town], be investigated or be expelled from the profession.” Indeed, the new HSYK has already acted in the government’s favor, requiring an investigation into military commanders who ordered the stopping and searching of trucks belonging to Turkey’s National Intelligence Organization (MIT) en route to Syria in January 2014. The trucks were alleged to be carrying explosives and weapons to be supplied to the Syrian opposition. While the previous HSYK did not give permission to launch an investigation into the generals involved in the incident, the government’s more agreeable HSYK readily acquiesced. JI Adv – JI Good – Nigerian Stability Nigeria Judicial Independence create stability Ige 08 (John Olagake Ige was a Justice for the Nigerian Supreme court, 11/9/08, THE INDEPENDENCE OF JUDICIARY AS A PANACEA FOR STABILITY OF DEMOCRACY IN NIGERIA: PAPER PRESENTED BY YUSUF O. ALI ESQ; SAN AT THE LUNCHEON IN HONOUR OF HON. JUSTICE OLAGOKE IGE, http://www.yusufali.net/articles/the_independence_of_judiciary_as_a_panacea_for_stability_o f_democracy_in_nigeria.pdf, 7/13/15, HDA) The issue of stability of democracy in Nigeria is a perennial one. There has been no permanent solution to recurring unstable democratic system we experience in Nigeria. However, there is no doubt; a strong and independent judiciary promotes the rule of 'aw. It checks acts of dictatorship and the rule of terror by the ruling class. It is so helpful in the promotion of justice and fair play. When the public feels confident in its adjudicator's roles, the judiciary is often described as the last hope of the common man. The judiciary as often described as the last hope of common man has a very big task ahead, this task could be illustrated by the statement made by a former judge of Lagos State High Court, Justice Akinola R. in his paper, Salute to cournge", The story of Justice Yahaya Jinadu: published by Nigerian Law Publications Ltd. In 1989 at pages 139 - 140. The Honourable Judge stated thus: "I believe the judiciary has an important role to play in this country as it is the last hope of the common man. The judiciary has to be firm, fair and courageous and must not employ any form of double standards. It is not right in my view to regard or treat the court of Justice as an extension of the Federal Ministry of Justice. I cannot cordon any attempt to destroy the judicial system in this country using me as a scape goat." In recent times, it is a matter of common knowledge that there has been a fair amount of loss of faith in the judicial process and adjudication in resolving conflicts and members of the public in certain instances preferred the use of self help, to the use of the judicial processes. The processes had been characterized with serious allegations of corruption, abuse of office, claim of ethnic lopsidedness in the appointment of judicial officers and so on. It is against the background of the above observation that this paper seeks to examine how an independent judiciary can be a viable and everlasting solution to the stability of democracy in Nigeria. Before going into the main theme of this paper, it is pertinent at this juncture to define certain terms used in the topic that is: independence, judiciary, panacea, stability and democracy i. Independence: it is freedom from control from dependence on or control by another person, organization or state, ii. Judiciary: this is a branch of government saddled with dispensation and administration of justice, iii. Panacea: it is a case of solution to an identified problem, iv. Stability: this is a quality of condition of being stable. v. Democracy: it is a free and equal representation of people in a system of government. The free and equal right of every person to participate in government often practiced by electing representatives of the people by the majority of people. It is also important to note at this juncture that this paper will be divided into some headings and I shall take the heading one after the other. JI Adv – Eastern Europe – Uniqueness – Transition Now Eastern Europe Striving for judicial independence OSCE 2010 (The OSCE has a comprehensive approach to security that encompasses politicomilitary, economic and environmental, and human aspects. It therefore addresses a wide range of security-related concerns, including arms control, confidence- and security-building measures, human rights, national minorities, democratization, policing strategies, counterterrorism and economic and environmental activities. All 57 participating States enjoy equal status, and decisions are taken by consensus on a politically, but not legally binding basis, 7/10/10, JUDICIAL INDEPENDENCE IN EASTERN EUROPE, SOUTH CAUCASUS AND CENTRAL ASIA Challenges, Reforms and Way Forward, http://www.osce.org/odihr/71178?download=true, 7/13/15, HDA) Balancing the independence of the judiciary with the need for democratic legitimacy in a society governed by the rule of law is a challenge for every participating State. The legacy of the Socialist legal tradition has shaped justice systems in a great number of OSCE participating States. After departure from the doctrine of “unity of state power”, these States in the past two decades have implemented numerous reforms, both legislative and institutional, which were intended to foster separation of powers and judicial independence. The time is now ripe for a fresh look at these efforts, to assess their success in establishing truly independent judiciaries, as well as identify remaining challenges in strengthening them. Therefore, ODIHR and the Max Planck Institute for Comparative Public Law and International Law (MPI) have undertaken an assessment of 4 the state of judicial independence across the OSCE region which provides the basis for developing an ODIHR strategy for this sector. The primary purpose of the project is to identify impediments and recognize good practices for the makeup of independent judiciaries in the participating States of the OSCE, and assist the States, with a predominant focus on Eastern Europe, South Caucasus and Central Asia, in adhering to their commitments. For the assessment phase of the project, ODIHR designed a questionnaire on judicial independence and commissioned country reports from independent experts. The questionnaire benefitted from feedback by MPI and the Council of Europe Venice Commission and covers the most relevant aspects of judicial independence, as outlined in several international instruments. Special attention has been given, inter alia, to the administration of the judiciary including budget management, the role of judicial councils, selection and appointment of judges, tenure and promotion, remuneration, case assignment systems, disciplinary procedures, immunity, ethics and resources. As second step in the assessment phase of the judicial independence project, the expert meeting in Kyiv was intended to result in concrete recommendations to the participating States on how to further strengthen judicial independence in the region. The comparative analysis of independent expert reports in the first step had led to the identification of subtopics for the expert meeting, namely (1) Judicial Administration – judicial councils, judicial self-governing bodies and the role of court chairs; (2) Judicial Selection – criteria and procedures; and (3) Accountability versus Independence in Adjudication. These subtopics were also subject to discussion at separate working sessions at the recent Human Dimension Seminar on Strengthening Judicial Independence and Public Access to Justice on 17-19 May 2010 in Warsaw. The meeting was attended by 27 prominent scholars and senior practitioners from 19 participating States, in addition to experts from ODIHR, MPI and the Council of Europe including its Venice Commission. The OSCE field presences in Moldova, Ukraine and Skopje were also represented. The meeting aimed to serve as a platform for in-depth discussion of challenges in selected areas related to judicial independence, critical examination of the impact of past reforms, as well as identification of good practice examples from participating States. Terror Adv Terror Adv – Entrapment Link Use of aggressive intelligence collection practices against Muslim communities fails and risks increased terrorism – entrapment increases false information and alienates communities. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] Because the FBI's post-9/11 establishment of a preventative stance towards terrorism 5Link to the text of the note has increased the need for intelligence, 6Link to the text of the note the agency has [237] turned to the increased use of immigration law and residence status to recruit more confidential informants. 7Link to the text of the note Although the FBI does not comment on its informant recruitment methods, 8Link to the text of the note numerous stories similar to Farahi's have been reported since 9/11. 9Link to the text of the note In fact, allegations of the FBI's aggressive use of past [238] violations of immigration laws to pressure individuals whom the agency believes may have terrorism knowledge have repeatedly surfaced. 10Link to the text of the note The Informants, a yearlong investigation into the FBI's use of informants, led by Trevor Aaronson and the University of California at Berkeley's Reporting Program in conjunction with Mother Jones, details the FBI's expanded use of informants in terrorism investigations. 11Link to the text of the note Of the approximately five hundred federal terrorism prosecutions conducted since 9/11, about half used an informant, 12Link to the text of the note and forty-nine of them were the result of work done by agent provocateurs. 13Link to the text of the note Aaronson's investigation also shed light on the FBI's use of immigration law and the threat of deportation to incentivize informants to cooperate. 14Link to the text of the note Aaronson explains, A typical scenario will play out like this: An FBI agent trying to get someone to cooperate will look for evidence that the person has immigration troubles. If they do, he can ask [Immigration and Customs Enforcement (ICE)] to begin or expedite deportation proceedings. If the immigrant then chooses to cooperate, the FBI will tell the court that he is a valuable asset, averting deportation. 15Link to the text of the note [239] Using the threat of immigration consequences like deportation to produce terrorism intelligence presents novel problems for the intelligence gathering process and the informants. When individuals are pressured into becoming informants by the threat of deportation, which may remove them from their family and all sources of support, the decision essentially becomes a Hobson's choice . 16Link to the text of the note Informants recruited in this manner who also lack legitimate ties to foreign terrorist organizations 17Link to the text of the note have an enormous incentive to fabricate information to fulfill their end of the agreement and avoid deportation. 18Link to the text of the note Attorney Stephen Downs of Project SALAM explained, Community life is shattered as the government often forces Muslim immigrants to spy on their own communities or give false testimony with the threat that the Muslim's immigration status will be "revised" if the Muslims do not cooperate. Such practices generate fear and alienation in the Muslim community and diminish our security rather than enhance it . 19Link to the text of the note As Downs notes, the intelligence these informants provide can be unreliable, 20Link to the text of the note because these individuals may feel they must offer up something to the government to avoid being removed from their families, jobs, and lives. The threat of false intelligence is grave. In addition to the possibility of entrapment 21Link to the text of the note by agent provocateurs, false intelligence may encourage ethnic and religious profiling of Muslim and Middle Eastern communities, 22Link to the text of the note chill free speech , 23Link to the text of the note and waste finite intelligence resources. Recruitment through [240] immigration law also affords less protection to informants than recruitment done by offering monetary rewards or reductions in sentencing. 24Link to the text of the note For example, unlike criminal offenses, there is no statute of limitations governing civil penalties like deportation, removal, or exclusion orders, which means that the FBI can use immigration violations to leverage cooperation from out-of-status individuals who have been in the country for years. Moreover, unlike an informant who is promised a sentence reduction or lessened charges and who can enforce his or her bargain with the government through plea bargaining, an informant promised immigration benefits has no way of enforcing these promises. 25Link to the text of the note Furthermore, the Sixth Amendment's guarantee of counsel 26Link to the text of the note does not apply to immigration violations. 27Link to the text of the note Finally, according to some reported cases, the government has failed to reward informants with the promised immigration benefits after receiving their cooperation. 28Link to the text of the note With fewer bargaining options, less protection, and potentially more to lose 29Link to the text of the note than informants recruited through monetary incentives or promises of sentence reductions, there is greater incentive for informants "flipped" 30Link to the text of the note via [241] immigration violations to provide unreliable information. Furthermore, due to the latitude afforded to the executive branch in national security matters, there is a darker veil of secrecy shrouding measures for recruiting terrorism informants than for other types of informants. 31Link to the text of the note Immigration status offers a valuable way for the FBI to elicit cooperation and collect intelligence from individuals who otherwise would not be forthcoming. However, this method for collecting intelligence can prove counterproductive when indiscriminately applied to situations where the informants lack useful connections to terrorist groups. Decreased intelligence benefits, lack of protection for informants, and increased ethnic and religious profiling suggest that changes to how the FBI recruits terrorism informants with immigration threats and rewards are needed. Terror Adv – Informants Key Informants are key to preventing terrorism. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] While there are no detailed studies on the differences between terrorism informants and traditional informants because the FBI keeps most of this information confidential, 47Link to the text of the note broad observations can still be made. First, the FBI's preventative stance on terrorism has significantly increased reliance on informants' intelligence. 48Link to the text of the note After 9/11, the FBI drastically expanded the use of [244] informants 49Link to the text of the note from around 1,500 in 1975 50Link to the text of the note to an estimated 15,000 today. 51Link to the text of the note Informants have become the number one tool for preventing terrorist acts. 52Link to the text of the note Terror Adv – Informants Key Voluntary informants are key. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] [254] By virtue of their connections and daily interactions, those active in a particular community are in the best position to notice when others in the community act strangely. Unlike informants who may be new to the community and who other members may view with suspicion, well-established community members may already know what is going on in their community and can more accurately spot genuine threats. Terror Adv – Uniqueness – FBI Fails Now Current FBI surveillance targets muslim communities, causing resentment of the FBI. Shamas ‘13 Diala Shamas, Diala Shamas is a staff attorney at the Creating Law Enforcement Accountability & Responsibility (CLEAR) project, based out of Main Street Legal Services at CUNY School of Law. 10-31-2013, "Where’s the Outrage When the FBI Targets Muslims?," Nation, http://www.thenation.com/article/wheres-outrage-when-fbi-targets-muslims/ our clients are targeted by FBI agents inquiring into the most intimate and protected areas of their lives stopped in front of their neighbors or children And the interrogations are far from voluntary FBI agents regularly warn our clients who invoke their right to have an attorney present that “they can do this the easy way or the hard way.” One client was so frightened by the agents’ threats that he agreed to accompany them to FBI headquarters and let them strap him to what they claimed was a polygraph machine for four hours as they peppered him with questions While the precise number of these interviews is not available we often ask for a show of hands in the room of people who have themselves been interrogated by law enforcement The interrogations have a devastating chilling effect on communities After a visit by the FBI un-joining groups and deleting the news articles he had posted in the hope that would spare him from a repeat The interrogations are also deeply stigmatizing he—the majority are young Muslim men—is perceived On a daily basis, . They are approached at night at their homes, , solicited outside their subway stops or interrogated at their workplaces in front of their colleagues and customers. GET THE LATEST NEWS AND ANALYSIS DELIVERED TO YOUR INBOX EVERY MORNING. SIGN UP . , accused him of lying and then turned around and asked him to work for them as an informant. , our experience suggests they are omnipresent. When CLEAR members facilitate Know-Your-Rights workshops at mosques in New York City, , or know others who have been, . In many mosques, every hand will go up. . Being pressed about their religious and political affiliations or their community activities inevitably makes our clients h esitate before being active in their mosque or community. , one 20-year-old client scrubbed his Facebook account, . It did not work. : when an individual is approached for questioning, by his peers as someone under investigation, and from whom people want to keep their distance Our clients regularly explain that they agreed to get into the FBI agents’ cars because they did not want to let them into their homes and expose their families I’ve had conversations with college students weighing the pros and cons of taking up a leadership position in their Muslim student group Instead of weighing their class workload against their extracurricular commitments the balancing involved exposure to further FBI questioning if they were to become more “active” Muslims and whether their past experience being questioned by the FBI would be bad for the organization . , but also did not want their neighbors to see them. . , , , as other students may hesitate to join. I can’t tag cards to save my life. US counterterrorism expansion into the Muslim-American community functions under the assumption that those individuals and groups are “terrorists” which creates a radicalization of the community and an “us v. them” mindset Williams 2012 (“Suspicious Minds: The American Consciousness, Domestic Security And The Radicalization Of Muslim-Americans”, Ronald E. Williams II, has over ten years of experience with the US Department of Justice (DoJ). His current work at DoJ involves developing and administering technical assistance in order to effectively partner with the department to combat terrorism, human trafficking, organized crime, corruption and financial crimes. Williams’ other work includes investigating allegations of racial discrimination, Guest Commentaries- Security Today, November 07, 2012 http://www.hstoday.us/columns/guestcommentaries/blog/suspicious-minds-the-american-consciousness-domestic-security-and-theradicalization-of-muslim-americans/3ede05589b6d0296ab8dc8edb5c12ca9.html) Immediately following the September 11, 2001 terrorist attacks, the priorities, energies and resources of the FBI concentrated on the proactive objective of preventing future terrorist incidents. In pursuit of this new strategy, the FBI understood that the success of this highly complex mission depended on cooperation from the Muslim-American community – specifically the need to understand its culture, history, religion and language. These early cooperation efforts were successful in part because many Muslims had sought to define themselves as Americans. And like most Americans, they, too, play an important role in ensuring domestic security, if by no other means than providing pertinent information to include identifying questionable behavior and activities. Taken at face value, these early partnerships developed into successful examples of intelligence-led policing. But if one is to seriously bisect this relationship, one would reasonably conclude that as potential terrorist suspects and targets become numerous and branches, and as deception operations become more sophisticated, domestic security and counterterrorism efforts will expand, reaching deep into the Muslim-American community, oftentimes crossing sensitivity lines, as was evidenced by the New York City Police Department’s surveillance of the region’s Muslim community. As a result of this cultural infiltration, the Muslim-American community has become, by and large, suspicious of government counterterrorism programs. The Muslim-American community has justified its suspicions on what it perceives to be American predispositions of both Islam in general, and Muslims in particular. As the American mainstream consciousness overtly claim that not all Muslims are violent, anti-American or prone to engage in terrorism while subconsciously believing the opposite and privately expressing such, the latter mindset will inevitably influence domestic counterintelligence/counterterrorism prerogatives. In the most subtle forms, these prerogatives will include identifying specific racial and ethnic groups/individuals as the sources, financiers and sympathizers of Islamic-oriented terrorism – a de facto policy that will never be officially sanctioned for it contradicts our own understanding of race neutrality. Hence, the radicalization of our own racial, ethnic and religious population will undoubtedly be the most complex challenge for our domestic security. Note that theories abound attempting to explain radicalization. Most popular among academics is the notion that a disaffected group perceives that the current government structure is the cause of some kind of injustice against them, and continues to nurture an environment of inequality (i.e. political, social, economical). With no legitimate means through which to seek redress, the group thus turns to more radical ways to demand justice and equality, oftentimes turning to violent behavior or other forms of criminal and subversive activity. While this formula may explain radicalization at the theoretical level and in homogenous environments, it does not adequately address the core elements of radicalization currently underway in the United States. If one is to fully understand American radicalization, one must critically recall the realities of American history. To be sure, any candid discussion of counter-radicalization efforts involving homegrown Islamic radicalism must first be predicated on the proposition that racialization is an indivisible element of the American consciousness. Racialization is to be defined as the process by which a racial or ethnic group is understood through the prism of racial generalizations. It is distinct from racism, which constitutes specific attitudes directed at a racial or ethnic group based on hatred of one race on the premise of inferiority. From racialization, the concept of “Us versus Them” matures, and the cultural subordination of a subordinate group by the dominate group is an accepted practice throughout the mainstream. Muslim-American radicalization is shaped by the struggle to define “American” and the community’s refusal to assimilate which causes a split between the traditional definition of the “American” and the Muslim-American communities, i.e. the “Us” v. “them” mindset which breeds resentment and radicalization Williams 2012 (“Suspicious Minds: The American Consciousness, Domestic Security And The Radicalization Of Muslim-Americans”, Ronald E. Williams II, has over ten years of experience with the US Department of Justice (DoJ). His current work at DoJ involves developing and administering technical assistance in order to effectively partner with the department to combat terrorism, human trafficking, organized crime, corruption and financial crimes. Williams’ other work includes investigating allegations of racial discrimination, Guest Commentaries- Security Today, November 07, 2012 http://www.hstoday.us/columns/guestcommentaries/blog/suspicious-minds-the-american-consciousness-domestic-security-and-theradicalization-of-muslim-americans/3ede05589b6d0296ab8dc8edb5c12ca9.html) Racial and ethnic categorization is a default mindset of the American psyche. It is deeply and skillfully woven into our national fabric, as is the ardent defense of the principles of the First Amendment. To deny this strain of our cultural DNA is to remain disadvantaged when pursuing any real efforts to understand the undercurrents of Muslim-American radicalization. Important to note is that the American public consciousness has become hyper-sensitive to the discussion of race and aloof to experiences from history. With each generation, American perceptions on race and the racial order are refined, resulting from the inherent push-pull relationship between the racial majority (“Us”) and the racial minority (“Them”). As these perceptions further root themselves into the American mainstream consciousness, the management thereof is, in truth, dominated by the racial majority. Since perceptions management is controlled by the racial majority, it stands to reason that the terms affecting the political and cultural narrative are too controlled by this majority. But in the face of bold demographic shifts, greater racial and ethnic diversity (especially without any desire to fully assimilate), and the real possibility of the racial majority becoming the numerical minority, control of the narrative becomes a strategic objective. Here, the starting point of the narrative revolves around two ideas: 1) How is “American” defined; and 2) What groups constitute “Americans?” Understand that these are two distinctly separate and important concepts that form the undercurrents of Muslim-American radicalization. During the early years of the republic, the mainstream view was that America was to be a place where distinct groups could retain their individual identity while simultaneously assimilating and submitting to the idea that is America: Acknowledging that the protection of the Constitution and the principles enshrined therein is the only obligation of an American citizen. However, the unique irony is that the American mainstream has always maintained a working level of cultural ignorance of its ethnic minority groups, and whereby the racial majority categorized and separated “us” from “them.” Recognize that throughout most of American history, an “American” was categorized as only those people of English origin, or those who were Protestant, or white or hailed from northern Europe. But at this juncture in our history, we must recognize that the American mainstream is being pushed and pulled by a variety of factors such as immigrant populations (in this country legally or otherwise) who refuse to culturally assimilate and agitate ethnonationalist sentiment. This psycho-cultural conflict has forced the American public consciousness into default mode. As mainstream America continues to become suspicious of Muslim-Americans and vice versa, the “Us versus Them” construct, based on existing racial paradigms, will be categorized in two ways: 1) White/African-Americans (“Us”) versus Muslim-Americans (“Them”); and 2) White Americans (“Us”) versus African-Americans (“Us”) versus “Muslim-Americans” (“Us”). What is absolute of the “Us versus Them” construct is that it results in alienation that breeds resentment which, in turn, manifests into political radicalization. Terror Adv – Informants Key FBI Surveillance of Muslim communities distrupts trust making counter terror efforts impossible Currier 15 ( Cora Currier is a journalist with a focus on national security, foreign affairs, and human rights. As a reporting fellow at ProPublica, she covered national security and finance, 1/21/15, “ SPIES AMONG US: HOW COMMUNITY OUTREACH PROGRAMS TO MUSLIMS BLUR LINES BETWEEN OUTREACH AND INTELLIGENCE”, The Intercept, https://firstlook.org/theintercept/2015/01/21/spies-among-us-community-outreach-programsmuslims-blur-lines-outreach-intelligence/, 7/8/15, HDA) Last May, after getting a ride to school with his dad, 18-year-old Abdullahi Yusuf absconded to the Minneapolis-St. Paul airport to board a flight to Turkey. There, FBI agents stopped Yusuf and later charged him with conspiracy to provide material support to a foreign terrorist organization—he was allegedly associated with another Minnesota man believed to have gone to fight for the Islamic State in Syria. To keep other youth from following Yusuf’s path, U.S. Attorney Andrew Luger recently said that the federal government would be launching a new initiative to work with Islamic community groups and promote after-school programs and job training–to address the “root causes” of extremist groups’ appeal. “This is not about gathering intelligence, it’s not about expanding surveillance or any of the things that some people want to claim it is,” Luger said. Luger’s comments spoke to the concerns of civil liberties advocates, who believe that blurring the line between engagement and intelligence gathering could end up with the monitoring of innocent individuals. If past programs in this area are any guide, those concerns are well founded. Documents obtained by attorneys at the Brennan Center for Justice at New York University School of Law, and shared with the Intercept, show that previous community outreach efforts in Minnesota–launched in 2009 in response to the threat of young Americans joining the al-Qaeda-linked militia al-Shabab, in Somalia—were, in fact, conceived to gather intelligence. A grant proposal from the St. Paul Police Department to the Justice Department, which the Brennan Center obtained through a Freedom of Information Act request to the FBI, lays out a plan in which Somali-speaking advocates would hold outreach meetings with community groups and direct people toward the Police Athletic League and programs at the YWCA. The proposal says that “the team will also identify radicalized individuals, gang members, and violent offenders who refuse to cooperate with our efforts.” “It’s startling how explicit it was – ‘You don’t want to join the Police Athletic League? You sound like you might join al-Shabab!’” said Michael Price, an attorney with the Brennan Center. *** The Islamic State may be the new face of religious extremism, but for a number of years, law enforcement in St. Paul and Minneapolis have had to contend with the appeal of al-Shabab to members of the country’s largest Somali population—more than 20 young men have reportedly left Minnesota to fight with the group since 2007. Dennis Jensen, St. Paul’s former assistant police chief, had spent years studying relations between police and the city’s Somali community, which is largely composed of recent immigrants from a war zone who have little reason to trust the authorities. But the al-Shabab threat galvanized the Department to see their work as a frontline for counterterrorism. Jensen told the Center for Homeland Defense and Security in 2009 that extremist recruitment added “a greater sense of urgency about what we are doing,” he said. “We’re up front about what our intentions are. It’s not a secret we’re interested in radicalized individuals.” (Jensen did not respond to emailed questions from the Intercept.) Jensen helped design a new program for St. Paul–a two-year initiative called the African Immigrant Muslim Coordinated Outreach Program, which was funded in 2009 with a $670,000 grant from the Justice Department. The outreach push would help police identify gang members or extremists, using “criteria that will stand up to public and legal scrutiny,” according to the proposal submitted to the Justice Department. “The effort of identifying the targets will increase law enforcement’s ability to maintain up-to-date intelligence on these offenders, alert team members to persons who are deserving of additional investigative efforts and will serve as an enhanced intelligence system,” the proposal reads. The Center for Homeland Defense and Security, in the 2009 interview with Jensen, characterized it as “developing databases to track at-risk youth who may warrant follow-up contact and investigation by law enforcement.” Asad Zaman, executive director of the Muslim American Society of Minnesota, said that his organization got funding through the program to hire a police liaison. They held meetings once or twice a month for two years, usually involving 20 or so community members and a few local cops. “The officers talked about drug enforcement and gangs and recruitment and domestic violence. Everyone loved it when they brought their bomb-sniffing robot once,” he recalled. He said he was not told about an intelligence component, though he had been asked to keep track of attendees at outreach meetings. “Several times [the police department] asked me whether that was possible to turn over the list of people at the programs, and I said, ‘It ain’t gonna happen,’” Zaman said. Steve Linders, a St. Paul Police spokesman, said that “the intelligence aspect never came to fruition. The program evolved away from that.” He said that they would sometimes pass information that community members brought to their attention to the FBI, but that was the extent of the bureau’s involvement. Linders said that people were not required to sign in to outreach meetings and there was no list of people who refused to participate, as originally proposed. “It was a conscious decision,” not to follow the plan laid out in the grant application, Linders said. “We frankly got more out of the program when we viewed it more as a way to get [community groups] resources and get their trust and partnership,” he said. For the Brennan Center’s Price, the shifting description just underlines how such programs can mislead the public. “I’m glad to hear they appear to have had a change of heart,” he said, “but it would be in everybody’s interest to clarify at the outset that they are collecting information for intelligence purposes, or that they are not.” The program “still raises questions for me,” Price added. “What led them to at first propose intelligence gathering, and then do an about face?” *** Around the same time that St. Paul developed its program, the FBI was leading a parallel push to leverage community outreach for intelligence. In 2009, it launched “Specialized Community Outreach Teams,” which would “strategically expand outreach to the Somali community to address counterterrorism-related issues” in Minneapolis and several other cities around the country. Then-FBI director Robert Mueller described the teams as part of an effort “to develop trust, address concerns, and dispel myths” about the FBI. In an internal memo obtained by the Brennan Center, however, the teams were called a “paradigm shift,” allowing “FBI outreach to support operational programs.” The co-mingling of intelligence and outreach missions would appear to run afoul of the FBI’s own guidelines for community engagement, the 2013 version of which state that officers must maintain “appropriate separation of operational and outreach efforts.” The FBI would not say if the “Specialized Community Outreach Teams” (which have ended) would be allowed under the new guidance, though in a statement, the FBI said the guidance “does not restrict coordination with operational divisions to obtain a better understanding of the various violations (i.e. terrorism, drugs, human trafficking, white collar crime, etc.) which may be impacting communities.” “If the guidance would allow this program to continue, then it just confirms that it’s full of loopholes,” said Price, of the Brennan Center. This isn’t the first FBI outreach program to raise these concerns. The American Civil Liberties Union has documented cases in recent years in San Francisco and San Jose where federal agents visited mosques and attended Ramadan dinners in the name of outreach, all the while keeping records on the participants. Some of the programs were well-meaning attempts at educating Islamic leaders about the threat of hate crimes, but nonetheless ended up collecting private information, according to Mike German, a former FBI agent who worked on this issue for the ACLU (he is now also with the Brennan Center). In other cases, “FBI agents were going out with outreach officers or mimicking community outreach to exploit it for intelligence purposes,” he said. Lori Saroya, until recently executive director of the Council on American-Islamic Relations Minnesota, said that people weren’t always aware of their rights when faced with outreach visits. “We had cases of people inviting FBI agents in for tea or to have dinner, not knowing they didn’t have to let them in,” she said. It’s this precedent that gives pause to critics of a new White House initiative to “counter violent extremism.” Though it is ostensibly aimed at extremists of all stripes, the outreach push has largely framed the involvement of Islamic community groups as key to helping authorities “disrupt homegrown terrorists, and to apprehend would-be violent extremists,” in Attorney General Eric Holder’s words. Luger’s plan for the Minneapolis area is part of this initiative, run jointly between the Justice Department, National Counterterrorism Center, and the Department of Homeland Security. Los Angeles and Boston are the other pilot cities. Details about the undertaking are still vague, though the attacks in Paris this month refocused attention on the issue, and the White House abruptly scheduled a summit on the topic for February (it was postponed last fall, without explanation.) German is doubtful about the prospects. “Countering violent extremism” is a relatively young science, and he points to studies that have failed to identify predictable indicators of what makes someone decide to commit ideologically motivated violence. Pumping resources into underserved communities is great, says German, but some of these programs may end up just alienating the communities they are intended to work with. “It suggests that the entire community is a threat, or a potential threat, and something to be managed,” he said. Target Surveillance of Muslim groups strains trust with authorities – makes counter terror impossible Patel and Price 12 (Faiza Patel is Co-Director of the Liberty and National Security Programme at the Brennan Centre for Justice. She is also a member of the United Nations Human Rights Council's Working Group on the Use of Mercenaries. Michael Price is Counsel of the Liberty and National Security Programme at the Brennan Centre for Justice. He was the National Security Coordinator for the National Association of Criminal Defense Lawyers, 4/12/12, Aljazeera, Surveillance of American Muslims: A tale of three cities, http://www.aljazeera.com/indepth/opinion/2012/04/201241061612704789.html, 7/8/15, HDA) The flood of reports about the New York City Police Department's surveillance of American Muslims - in mosques, restaurants, bookstores and even elementary schools in New York, New Jersey, New Orleans and beyond - has triggered a range of responses around the country. Mayor Michael Bloomberg and Police Commissioner Ray Kelly have defended the programme, suggesting that such wholesale surveillance of Muslims is necessary to keep the City safe. The NYPD certainly has a formidable task and has protected New Yorkers through times of high alert. But the reactions of public officials in cities such as Los Angeles and Chicago, which have also faced serious terrorist threats, suggest that effective counterterrorism does not require such a stark choice between our liberty and our safety. Honest efforts to build partnerships with American Muslim communities present an alternative approach to terrorism that has proven to be both successful and respectful of our Constitutional values. New York City is understandably sensitive to terrorism concerns. As both Mayor Bloomberg and Commissioner Kelly have repeatedly acknowledged, keeping New York safe requires the police to build trust with American Muslim communities who may be best positioned to provide information necessary to avert a terrorist plot. Indeed, studies show that up to 40 per cent of the tips that have been used to stop terrorists have come from American Muslims. But the NYPD's decision to monitor Muslim communities solely on the basis of their religion is not conducive to building relationships of trust. The fraying of the fragile relationship between the police and Muslim New Yorkers has been vividly on display since reports of these programmes first emerged, with several Muslim leaders boycotting the Mayor's annual interfaith breakfast, declining meetings with the Police Commissioner and staging repeated protests outside City Hall. These connections are vital not only to counterterrorism efforts, but also to ensure that Muslim communities feel comfortable enough communicating with local police to help solve everyday crimes. Decades of research show that perceptions of police legitimacy influence the willingness of communities to co-operate with officers. The FBI, which has faced its own challenges with respect to its treatment of Muslim communities, has publicly criticised the NYPD's approach because it has strained relations with American Muslims who have generally "embraced" law enforcement's counterterrorism mission. NYPD's approach Public officials in other cities have rushed to distance themselves from the NYPD's approach. In Chicago, Mayor Rahm Emanuel said the city would never permit its officers to spy on Muslim communities as the NYPD has done, promising: "We don't do that in Chicago and we're not going to do that". As reports emerged that the NYPD had spied on Muslim neighbourhoods in Newark, New Jersey, the Chicago Police Department, now run by the former head of the Newark Police Department, quickly issued an order prohibiting "bias based policing". In Los Angeles, the Deputy Chief of the Police Department, Michael Downing, stressed that his department considered the Muslim community a key partner in fighting terrorism. In his view: "There is no reason for us to survey Muslim students or where people buy their meat; that is not suspicious to us. That is how someone lives their life." Indeed, in 2007, the LAPD considered and rejected a New York-style plan to "map" Muslim communities because of concerted opposition from both Muslim and civil rights groups. But the difference between these police departments is not just one of attitude towards American Muslim communities. Los Angeles and Chicago conduct their counterterrorism work primarily in partnership with the FBI. The NYPD, however, houses a stand-alone counterterrorism and intelligence operation that costs taxpayers more than $100 million a year and employs 1,000 officers. But unlike the FBI, which is overseen by an Inspector General reporting to Congress, the NYPD's intelligence operation is conducted without any meaningful oversight. If the NYPD insists on modelling itself as a mini-FBI, then it should be subject to the same level of oversight - an independent Inspector General. New Yorkers are grateful to the NYPD for its work in protecting the city. However, our nation's historical commitment to civil liberties and religious tolerance must not be brushed aside by talismanic claims of national security. An Inspector General could bring greater transparency to the murky world of intelligence gathering, serving as an honest broker to determine whether NYPD programmes comply with the law. By developing and sharing credible information that would allow both our elected leaders and New Yorkers to better evaluate police programmes, the Inspector General could help break the current cycle of accusations and denials. And such transparency would help restore the badly battered trust between the NYPD and minority communities and lead to a stronger, more effective police force. Let us not forget that all Americans - Muslims, Jews, Christians, Buddhists, Hindus and atheists alike - are committed to the security of our country and our country will be safest when we all work together towards this goal. A report that the U.S. government conducted electronic surveillance on five prominent Muslim Americans is troubling. It deserves a fuller response from the government than a boilerplate assurance that it doesn't choose targets of surveillance based on their political or religious views. The notion that the FBI would target innocent individuals because of their views isn't fantastic in light of the agency's past activities. Relying on a spreadsheet supplied by former National Security Agency contract worker Edward Snowden, the online news site Intercept reported that, between 2006 and 2008, the government tracked the email accounts of Faisal Gill, who had served in the U.S. Department of Homeland Security, and four other men, including Nihad Awad, executive director of the Council on American-Islamic Relations, this country's largest Muslim civil rights organization. The article suggested that the men might have been targeted for surveillance because of their religion or peaceful advocacy, although no evidence of that was given. It noted that all of the men deny involvement in terrorism. None has been charged with a crime arising from the surveillance. The article also quotes a former FBI counter-terrorism official as spinning outlandish theories about Muslim Brotherhood infiltration of the United States, and it refers to a directive for intelligence personnel that used "Mohammed Raghead" as the name of a hypothetical surveillance target. It isn't clear whether any or all of the men were subjected to surveillance under the provisions of the Foreign Intelligence Surveillance Act. That 1978 law requires the government to demonstrate to a special court that there is probable cause that an American citizen or permanent resident is an agent of a foreign power or terrorist organization. (It's possible that there can be probable cause to subject someone to surveillance for foreign intelligence purposes without there being probable cause to charge him with a crime.) The notion that the FBI would target innocent individuals because of their views isn't fantastic in light of the agency's past activities, and profiling of Muslims was an unfortunate aspect of the official reaction to 9/11. That doesn't mean that the past is prologue in this case and that these five men were the victims of religious bias, but the suspicion is understandable. The American Civil Liberties Union and several other organizations have called on President Obama to make a "full public accounting" of the government's surveillance practices. It's unrealistic to expect the administration to publicize classified information in specific cases, but the FBI's inspector general should inquire into the circumstances of these investigations and any broader role that religious stereotyping might be playing in the selection of targets for surveillance. FBI targeted Surveillance of Muslims alienates Muslim communities who are key for counter-terrorism efforts CAIR 12 (The Council on American-Islamic Relations (CAIR) is a grassroots civil rights and advocacy group and CAIR America's largest Muslim civil liberties organization, with regional offices nationwide, 10/1/12, “FBI COUNTER TERRORISM MEASURES CREATING MISTRUST IN AMERICAN MUSLIM COMMUNITIES, CAIR Chicago, http://www.cairchicago.org/blog/2012/10/fbicounter-terrorism-measures-creating-mistrust-in-american-muslim-communities, 7/8/15, HDA) Since the September 11th, 2001 attacks, the FBI has placed an emphasis on preventing further terrorist attacks on U.S. soil. To do so, they have focused their energy on preemptive measures, seeking to discover terrorists before their dreams of destruction can be realized. However, this effort has not been without controversy, as many of the “terrorists” claim foul play and entrapment. These accusations refer to the FBI’s strategy of placing informants within specific communities, in particular the American Muslim community, and having them seek out radical elements for further “assessment.” Recently, the FBI appears to have conducted blanket surveillance of broad sections of the American Muslim community, leading to a number of foiled terrorist plots. However, a closer look into some of these foiled terrorist attempts reveals that the planning, materials, funding, and even transportation for these attacks have almost all been provided to these disgruntled young men by the FBI themselves. This raises a very serious question: Would these young men still pose a terrorist threat to the U.S. had the FBI not engaged them, and even provided them with all the resources necessary to commit these acts of violence? Though the legal definition of entrapment makes it hard to clearly define these cases as such, the methods used by the FBI in recent years create an impression of racial profiling on a scale reminiscent of the oppression of Japanese Americans during the Second World War. Apparently, the FBI feels that American Muslims are guilty by association until proven innocent through extensive, and extremely intrusive, surveillance campaigns. In an article published by The Guardian (UK), Paul Harris interviewed former FBI informant Craig Monteilh, who gave an inside account of the FBI’s domestic counter terrorism efforts. Monteilh, having been an integral part of the hunt for Muslim terrorists, characterized the methods used by the FBI as “…a joke, a real joke. There is no real hunt. It’s fixed.” Monteilh began working for the FBI as a confidential informant in 2006, participating in an operation referred to as “Flex,” where he posed as a Syrian by the name of Farouk Aziz. By this alias, Monteilh was ordered to spend time in Orange County, California, mosques and Islamic centers until the Muslim community there became comfortable enough to accept him as a fellow member. From there he was tasked with recording any and all conversations he had with members of the community, subtly suggesting radical ideas to those he talked to in hopes of luring out more extreme members. According to Monteilh, the aim of his investigation was to record members saying specific words or phrases that could justify further investigations. “The skill is that I’m going to get you to say something. I am cornering you to say ‘jihad.’” But that’s not all Monteilh was tasked with doing. He even reports of being told to use private information about members of the Islamic community, such as individuals’ being homosexual or having an affair, as blackmail in order to recruit more informants. In one case he was even told to have sex with women of the community in order to get closer to them. And despite his best efforts to “corner” members into saying the “right” words, or using their religious stigmas towards sexuality against them, Monteilh was unsuccessful in producing any material initiating a serious terrorist investigation. In fact, one of the communities that he was attempting to infiltrate got a restraining order against him and even reported him to the FBI, unaware that he was actually working for them. Surely, however, this is an isolated incident of misconduct…this couldn’t happen in a nation that respects the constitutionally protected civil liberties of ALL its citizens. I wish I could say that was the truth. According to an article written for The New York Times, of the 22 most frightening foiled terrorist plots since the September 11th, 2001 attacks, 14 have been the products of operations very similar to that described by Monteilh. In 2009, four men were arrested in Newburgh, New Jersey, for planning to bomb Jewish synagogues and shoot down military aircraft with Stinger anti-aircraft missiles. Referred to as the Newburgh Four, and portrayed as hardcore “Islamic extremists,” these men were all convicted and sentenced to lengthy jail terms. But after reviewing the case, it is hard not to notice that the profiles of these four men didn’t fit those of hardened terrorist masterminds. Rather, their lives were characterized by drug and financial problems, criminal histories (for petty crimes), and in one case schizophrenia. Furthermore, the fifth man involved in this plot, the one who provided the plans, weapons, transportation, and an offer of $250,000, a free car and vacation to the others, was none other than a well-paid FBI informant. This case has raised serious doubt as to whether these four men would have posed any sort of threat had they not been approached by an FBI agent who offered to pay large sums of money for their cooperation. Considering that one of the four, David Williams, was having trouble raising the money to pay for a much needed liver transplant for his sick brother, these men look more like paid thugs than terrorist masterminds. Susanne Brody, an attorney representing one of the four, claimed that “We have as close to a legal entrapment case as I have ever seen.” Unfortunately, the list of cases nearly identical to these goes on, from the Liberty City Six, whose plans never surpassed the discussion stage, to the Fort Dix Five, where one FBI informant’s past included attempted murder and another admitted in court that two of the men convicted were never aware of any terrorist plot (both were sentenced to life in prison). According to Mike German, a former FBI agent now working for the ACLU, “Most of these terrorist suspects had no access to weapons unless the government provided them. I would say that showed they were not the biggest threat to the U.S.” According to German, the FBI has been expanding its tools for carrying out such investigations, something he considers a “terrible prospect.” But are the tools used in these cases legitimate, even by the FBI’s own standards? According to the Domestic Investigations and Operations Guide (DIOG – FBI, 2008), these tactics are questionable at best. Section four of the DIOG, entitled “[O]n Privacy and Civil Liberties, and ‘Least Intrusive Methods,’” it states that each investigation must have a clearly defined and approved purpose and that this purpose is prohibited from being “based solely on race, ethnicity, national origin or religion.” What’s more telling is, in section 4.2 B, on the exercise of religion, the DIOG states that, …solely because prior subjects of an investigation of a particular group were members of a certain religion and they claimed a religious motivation for their acts of crime or terrorism, other members’ mere affiliation with that religion, by itself, is not a basis to assess or investigate – absent a known and direct connection to the threat under assessment or investigation. However, the blanket surveillance of Muslim communities in California described by Monteilh, and the recently uncovered case of NYPD eavesdropping on the entire New York Muslim community, seem to clearly violate these regulations. It has recently become ever clearer that many of these investigations have been initiated solely because these communities happen to be Muslim, with no prior evidence of suspicious behavior whatsoever. Assistant Chief Thomas Galati, head of NYPD’s secret Demographics Unit charged with this task, admitted that after nearly six years of monitoring the Muslim community in New York they were unable to come up with a single investigation. But it doesn’t stop there. The DIOG (Domestic Investigations and Operations Guide) places a heavy emphasis on the protection of First Amendment rights, stating that no investigations can be initiated based solely in response to ones expression of these rights, or solely to monitor their expression of them. Of course, however, freedom of speech in the United States does not protect all language. The DIOG refers to a U.S. Supreme Court ruling, Brandenburg v. Ohio (1969), where the court ruled that the government may not prohibit the advocacy of force or violence except when such activity is intended to provoke imminent (emphasis added by DIOG) lawless activity, and is likely to do so. However, according to the testimony given by Monteilh, using the word “jihad” (which has two meanings, the main meaning having nothing to do with “holy war”) was enough to initiate an investigation. But simply using the word “jihad” does not provoke imminent lawless behavior; therefore, being protected under the First Amendment rights that the FBI is prohibited from using as their sole justification for initiating an investigation. The blanket recording of conversations with members of the Muslim community, all of whom had said absolutely nothing to provoke imminent lawless behavior, is a clear violation of both DIOG regulations and the Brandenburg (1969) ruling. Lastly, the DIOG also mandates the use of the least intrusive methods possible for conducting intelligence gathering operations and lists the use of wiretaps, electronic surveillance, and informants as “very intrusive.” The fact that the FBI has chosen to use such methods, especially on populations and individuals that have presented no prior evidence of wrongdoing, suggests that this regulation means little to the Bureau. Though the FBI has played a significant role in keeping America safe from further terrorist attacks, it also seems clear that some of their efforts have been severely misguided, even jeopardizing their ability to do the best job possible. The fact that Monteilh was reported to the FBI by the very community he was trying to infiltrate, suggests that these investigations are an unwarranted waste of valuable resources; and one of the most valuable resources in the counter terrorism efforts of the FBI, according to the DIOG, is “the trust and confidence of the American public.” Ironically, the very next statement in the DIOG is, “…and because that trust and confidence can be significantly shaken by our failure to respect the limits of our power, special care must be taken by all employees to comply with these limitations.” However, many experts agree that the FBI’s recent conduct regarding such cases has created an atmosphere of distrust within the American Muslim community. According to civil rights groups, American Muslims feel as if they are being unjustly targeted by the authorities for investigations simply because of their faith, “triggering a natural fear of the authorities among people that should be a vital defense against real terror attacks.” Instead of alienating the Muslim population, whose cooperation is essential to counter terrorism efforts, the FBI should push itself to comply with their own procedures and legal precedent established by the nation’s highest court, and focus their energy on investigating proven threats to society. This would help to rebuild the trust of the American Muslim community, as well as put pressure on the individuals that actually intend to do harm. Government Islamophobia and Surveillance harm crucial counterterrorism relations Al-Marayati 11 (Salam Al-Marayati is executive director of the Muslim Public Affairs Council, an American institution which informs and shapes public opinion and policy by serving as a trusted resource to decision makers in government, media and policy institutions, 10/19/12, Las Angeles Times, The wrong way to fight terrorism, http://articles.latimes.com/2011/oct/19/opinion/la-oe-almarayati-fbi-20111019, 7/8/15, HDA) We in the Muslim American community have been battling the corrupt and bankrupt ideas of cults such as Al Qaeda. Now it seems we also have to battle pseudo-experts in the FBI and the Department of Justice. A disturbing string of training material used by the FBI and a U.S. attorney's office came to light beginning in late July that reveals a deep anti-Muslim sentiment within the U.S. government. If this matter is not immediately addressed, it will undermine the relationship between law enforcement and the Muslim American community — another example of the ineptitude and/or apathy undermining bridges built with care over decades. It is not enough to just call it a "very valid concern," as FBI Director Robert Mueller told a congressional committee this month. The training material in question provided to FBI agents at the academy in Quantico, Va. — as first reported by Wired magazine's Danger Room blog — contained bigoted and inflammatory views on Muslims, including claims that "devout" Muslims are more prone toward violence, that Islam aims to "transform a country's culture into 7th century Arabian ways," that Islamic charitable giving is a "funding mechanism for combat" and that the prophet Muhammad was a "violent cult leader." Wired also found a 2010 presentation by an analyst working for the U.S. attorney's office in Pennsylvania that warns of a " 'Civilizational Jihad' stretching back from the dawn of Islam and waged today in the U.S. by 'civilians, juries, lawyers, media, academia and charities' who threaten 'our values.' The goal of that war: 'Replacement of American Judeo-Christian and Western liberal social, political and religious foundations by Islam.'" Such baseless and inflammatory claims shall best be left to those few who share Al Qaeda's agenda of keeping America in a perpetual state of war with Islam. In other words, the rhetoric of Al Qaeda and these law enforcement trainers are opposite sides of the same coin of hate. If our law enforcement and intelligence agencies continue to use incorrect and divisive training literature, the crucial partnership between the Muslim American community and law enforcement will slowly disintegrate. According to the Muslim Public Affairs Council's Post-9/11 Terrorism Incident Database, these partnerships have proved effective in keeping our nation safe. Nearly 40% of Al Qaeda-related plots threatening the American homeland since 9/11 have been foiled thanks to tips from Muslims. One example of this is the so-called Virginia 5 case in 2009, in which information from the Muslim community in Virginia led to the arrest in Pakistan of five Muslims from Virginia who were trying to join an Al Qaeda group. Last year, in another case, members of a Maryland community warned law enforcement about Antonio Martinez, who had recently converted to Islam. He was subsequently arrested after he allegedly tried to blow up a military recruitment center. More important, Muslim leaders, not FBI agents, can more effectively battle Al Qaeda's destructive ideas. I have worked for more than 20 years with law enforcement and Muslim American communities, and one of the biggest consequences of these training sessions and use of this material is the setback of a vital relationship that required years to build. I know justifiable criticism can be levied against some Muslim leaders in America for not aggressively promoting civic engagement, for not being self-critical enough and for not distancing themselves from rabble-rousers. But how can we persuade Muslim American communities to stay at the table when the food on the table is filled with poison? These training manuals are making it more difficult for Muslim Americans to foster any trust with law enforcement agencies. Biased and faulty training leads to biased and faulty policing. The real challenge now is getting the partnership back on track, and for the FBI and the Justice Department to take the following steps: issue a clear and unequivocal apology to the Muslim American community; establish a thorough and transparent vetting process in selecting its trainers and materials; invite experts who have no animosity toward any religion to conduct training about any religious community to law enforcement. Finally, the White House needs to form an interagency task force that can conduct an independent review of FBI and Justice Department training material. The following words are etched into the walls of the FBI headquarters building in Washington: "The most effective weapon against crime is cooperation … of all law enforcement agencies with the support and understanding of the American people." Atty. Gen. Eric H. Holder Jr. and FBI Director Mueller, take some leadership on this matter, or the partnership we've built to counter violent extremism will forever be handicapped. The question you have to answer is simple: Are we on the same team or not? FBI sting operations have destroyed relations with Muslims communities- only stopping this targeting with build trust to help counter-terrorism effort HRW 14 (The Human Rights Watch is a nonprofit, nongovernmental human rights organization made up of roughly 400 staff members around the globe. Its staff consists of human rights professionals including country experts, lawyers, journalists, and academics of diverse backgrounds and nationalities. Established in 1978, Human Rights Watch is known for its accurate fact-finding, impartial reporting, effective use of media, and targeted advocacy, often in partnership with local human rights groups, 7/21/14, HRW, “US: Terrorism Prosecutions Often An Illusion”, https://www.hrw.org/news/2014/07/21/us-terrorism-prosecutions-oftenillusion, 7/8/15, HDA) The US Justice Department and the Federal Bureau of Investigation (FBI) have targeted American Muslims in abusive counterterrorism “sting operations” based on religious and ethnic identity, Human Rights Watch and Columbia Law School’s Human Rights Institute said in a report released today. Many of the more than 500 terrorism-related cases prosecuted in US federal courts since September 11, 2001, have alienated the very communities that can help prevent terrorist crimes. The 214-page report, “Illusion of Justice: Human Rights Abuses in US Terrorism Prosecutions,” examines 27 federal terrorism cases from initiation of the investigations to sentencing and post-conviction conditions of confinement. It documents the significant human cost of certain counterterrorism practices, such as overly aggressive sting operations and unnecessarily restrictive conditions of confinement. “Americans have been told that their government is keeping them safe by preventing and prosecuting terrorism inside the US,” said Andrea Prasow, deputy Washington director at Human Rights Watch and one of the authors of the report. “But take a closer look and you realize that many of these people would never have committed a crime if not for law enforcement encouraging, pressuring, and sometimes paying them to commit terrorist acts.” Many prosecutions have properly targeted individuals engaged in planning or financing terror attacks, the groups found. But many others have targeted people who do not appear to have been involved in terrorist plotting or financing at the time the government began to investigate them. And many of the cases involve due process violations and abusive conditions of confinement that have resulted in excessively long prison sentences. The report is based on more than 215 interviews with people charged with or convicted of terrorism-related crimes, members of their families and their communities, criminal defense attorneys, judges, current and former federal prosecutors, government officials, academics, and other experts. In some cases the FBI may have created terrorists out of law-abiding individuals by suggesting the idea of taking terrorist action or encouraging the target to act. Multiple studies have found that nearly 50 percent of the federal counterterrorism convictions since September 11, 2001, resulted from informant-based cases. Almost 30 percent were sting operations in which the informant played an active role in the underlying plot. In the case of the “Newburgh Four,” for example, who were accused of planning to blow up synagogues and attack a US military base, a judge said the government “came up with the crime, provided the means, and removed all relevant obstacles,” and had, in the process, made a terrorist out of a man “whose buffoonery is positively Shakespearean in scope.” The FBI often targeted particularly vulnerable people, including those with intellectual and mental disabilities and the indigent. The government, often acting through informants, then actively developed the plot, persuading and sometimes pressuring the targets to participate, and provided the resources to carry it out. “The US government should stop treating American Muslims as terrorists-in-waiting,” Prasow said. “The bar on entrapment in US law is so high that it’s almost impossible for a terrorism suspect to prove. Add that to law enforcement preying on the particularly vulnerable, such as those with mental or intellectual disabilities, and the very poor, and you have a recipe for rampant human rights abuses.” Rezwan Ferdaus, for example, pled guilty to attempting to blow up a federal building and was sentenced to 17 years in prison. Although an FBI agent even told Ferdaus’ father that his son “obviously” had mental health problems, the FBI targeted him for a sting operation, sending an informant into Ferdaus’ mosque. Together, the FBI informant and Ferdaus devised a plan to attack the Pentagon and US Capitol, with the FBI providing fake weaponry and funding Ferdaus’ travel. Yet Ferdaus was mentally and physically deteriorating as the fake plot unfolded, suffering depression and seizures so bad his father quit his job to care for him. The US has also made overly broad use of material support charges, punishing behavior that did not demonstrate an intent to support terrorism. The courts have accepted prosecutorial tactics that may violate fair trial rights, such as introducing evidence obtained by coercion, classified evidence that cannot be fairly contested, and inflammatory evidence about terrorism in which defendants played no part – and asserting government secrecy claims to limit challenges to surveillance warrants. Ahmed Omar Abu Ali is a US citizen who alleged that he was whipped and threatened with amputation while detained without charge in Saudi Arabia – after a roundup following the 2003 bombings of Western compounds in the Saudi capital of Riyadh – until he provided a confession to Saudi interrogators that he says was false. Later, when Ali went to trial in Virginia, the judge rejected Ali’s claims of torture and admitted his confession into evidence. He was convicted of conspiracy, providing material support to terrorists, and conspiracy to assassinate the president. He received a life sentence, which he is serving in solitary confinement at the federal supermax prison in Florence, Colorado. The US has in terrorism cases used harsh and at times abusive conditions of confinement, which often appear excessive in relation to the security risk posed. This includes prolonged solitary confinement and severe restrictions on communicating in pretrial detention, possibly impeding defendants’ ability to assist in their own defense and contributing to their decisions to plead guilty. Judges have imposed excessively lengthy sentences, and some prisoners suffer draconian conditions post-conviction, including prolonged solitary confinement and severe restrictions on contact with families or others, sometimes without explanation or recourse. Nine months after his arrest on charges of material support for terrorism and while he was refusing a plea deal, Uzair Paracha was moved to a harsh regime of solitary confinement. Special Administrative Measures (SAMs) – national security restrictions on his contact with others – permitted Paracha to speak only to prison guards. “You could spend days to weeks without uttering anything significant beyond ‘Please cut my lights,’ ‘Can I get a legal call/toilet paper/a razor,’ etc., or just thanking them for shutting our light,” he wrote to the report’s researchers. After he was convicted, the SAMs were modified to permit him to communicate with other inmates. “I faced the harshest part of the SAMs while I was innocent in the eyes of American law,” he wrote. These abuses have had an adverse impact on American Muslim communities. The government’s tactics to seek out terrorism suspects, at times before the target has demonstrated any intention to use violence, has undercut parallel efforts to build relationships with American Muslim community leaders and groups that may be critical sources of information to prevent terrorist attacks. In some communities, these practices have deterred interaction with law enforcement. Some Muslim community members said that fears of government surveillance and informant infiltration have meant they must watch what they say, to whom, and how often they attend services. “Far from protecting Americans, including American Muslims, from the threat of terrorism, the policies documented in this report have diverted law enforcement from pursuing real threats,” Prasow said. “It is possible to protect people’s rights and also prosecute terrorists, which increases the chances of catching genuine criminals. Terror Adv – Radicalization Link NSA and FBI surveillance specifically targeted Arab-American communities. Further discriminatory surveillance risks key co-op, possible radicalization. Risen ‘14 (Internally quoting Vanda Felbab-Brown, a senior fellow on foreign policy at the Brookings Institution. Tom Risen is a reporter for U.S. News & World Report. “Racial Profiling Reported in NSA, FBI Surveillance” - U.S. News & World Report - July 9, 2014 - http://www.usnews.com/news/articles/2014/07/09/racial-profiling-reported-in-nsa-fbisurveillance) Congregants pray at a mosque in Paterson, New Jersey. The NSA and FBI reportedly spied on prominent Muslim Americans following the 9/11 attacks, according to a leaked government document. The National Security Agency and the FBI have reportedly been overzealous trying to prevent terrorist attacks to the point that anti-Islamic racism in those agencies led to the surveillance of prominent Muslim-Americans, revealing a culture of racial profiling and broad latitude for spying on U.S. citizens. An NSA document leaked by former agency contractor Edward Snowden to reporter Glenn Greenwald shows 202 Americans targeted among the approximately 7,485 email addresses monitored between 2002 and 2008, Greenwald’s news service The Intercept reports. [READ: Glenn Greenwald Suggests There's a Second NSA Leaker] To monitor Americans, government agencies must first make the case to the Foreign Intelligence Surveillance Court that there is probable cause that the targets are terrorist agents, foreign spies or “are or may be” abetting sabotage, espionage or terrorism. Despite this filter The Intercept identified five Muslim-Americans with high public profile including civil rights leaders, academics, lawyers and a political candidate. NSA Spied On U.S. Muslims Like ‘Hoover Did On MLK’ Daily Caller Racial profiling of Muslims by security officers has been a controversy since the terrorist attacks of 2001 spiked fears about al-Qaida trainees preparing more attacks. The New York Police Department has disbanded its unit that mapped New York’s Muslim communities that designated surveillance of mosques as “terrorism enterprise investigations” after pressure from the Justice Department about aggressive monitoring by police. A 2005 FBI memo about surveillance procedures featured in The Intercept story uses a fake name “Mohammed Raghead” for the agency staff exercise. This latest report about email surveillance of successful Muslim-Americans is akin to “McCarthyism” that fed paranoia about communist spies during the Cold War, says Reza Aslan, a professor at the University of California, Riverside. “The notion that these five upstanding American citizens, all of them prominent public individuals, represent a threat to the U.S. for no other reason than their religion is an embarrassment to the FBI and an affront to the constitution,” Aslan says. There is a risk of radicalization among citizens Americans, evidenced by some who have gone to fight jihads in Syria and Somalia, but mass shootings carried out by U.S. citizens of various racial backgrounds occurs much more often, says Vanda Felbab-Brown, a senior fellow on foreign policy at the Brookings Institution. Since 1982, there have been at least 70 mass shootings across the U.S. “We have seen very little domestic terrorism in the U.S.,” Felbab-Brown says. This lack of terrorism is due in part to the willingness of the Islamic community to cooperate with law enforcement to identify possible radical threats, out of gratitude that the U.S. is a stable, secure country compared with the Middle East, she says. [ALSO: Privacy Watchdog Says NSA Spying Legal, Effective] “That could go sour if law enforcement becomes too aggressive, too extreme,” she says. Terror Adv – Yes Nuclear Terror Threat exists, and terrorists have the capability and motivation Brill et al 15(Kenneth C. Brill is a former U.S. ambassador to the International Atomic Energy Agency (IAEA) and the founding director of the U.S. government’s National Counterproliferation Center. John H. Bernhard is a former Danish ambassador to the IAEA and the Organization for Security and Co-operation in Europe and a former legal adviser in the Danish Foreign Ministry. They are members of the Nuclear Security Governance Experts Group, “A Convention on Nuclear Security: A Needed Step Against Nuclear Terrorism,” 6/1/15, https://www.armscontrol.org/ACT/2015_06/Features/A-Convention-on-Nuclear-Security-ANeeded-Step-Against-Nuclear-Terrorism 7/8/15) Some wonder whether the threat of nuclear terrorism exists outside of novels and Hollywood action films. The administrations of President George W. Bush and Obama have made clear the threat is real. Other global leaders, including those from the other 52 countries that have participated in the nuclear security summits, have done the same. Successive U.S. directors of national intelligence have outlined the reality of the threat in testimony to Congress and in their national intelligence strategies. Yukiya Amano, the director-general of the International Atomic Energy Agency (IAEA), and his immediate predecessor, Mohamed ElBaradei, have described nuclear terrorism as a threat that needs urgent attention. A nuclear terrorist attack, particularly one involving fissionable materials, would produce devastating international political, economic, humanitarian, and environmental consequences. Expert studies have concluded that even a small nuclear explosion in a major city would immediately kill tens of thousands of people and cause even more deaths subsequently. The explosion would destroy infrastructure over a wide area, and radiation would make a larger area unusable for many years. The costs of attending to the human casualties, relocating large numbers of people, and undertaking new construction and the cleanup of land and buildings, combined with the costs arising from bankruptcies, trade dislocations, and the disruption of energy and other supplies, would most likely be in the trillions of dollars.[2] Terrorists also could make a device from radiological substances, which are used globally for medical, research, and industrial purposes. A radiological dispersal device, or “dirty bomb,” would produce fewer casualties, but could result in significant consequences and costs for health, infrastructure, and the environment. Such a device also could make many blocks in an urban area too contaminated for humans to work or live in without time-consuming remediation. This would be very expensive and very disruptive to people’s lives, the environment, and the economy. Terrorist use of any type of nuclear device would cross an important psychological threshold for the public, governments and terrorist groups themselves, taking questions of national and international security into uncharted waters. At least five terrorist groups, including al Qaeda and the Islamic State, have demonstrated an interest in acquiring and using nuclear material or a nuclear weapon. Terrorists do not need to steal a nuclear weapon. An improvised nuclear device, which would have the explosive power comparable to the weapons used in Hiroshima and Nagasaki, can be made from highly enriched uranium or plutonium being used for civilian purposes. The Islamic State indicated its interest in nuclear terrorism with a boast about constructing a dirty bomb after stealing 88 pounds of unenriched uranium compounds from a university laboratory when it overran Mosul, Iraq, in 2014.[3] The continued loss, theft, and illegal movement of nuclear and other radioactive materials demonstrate that material is available for terrorists to acquire and use as a weapon. Since 1993, the IAEA has logged some 2,500 cases related to the theft, loss of control, unauthorized possession, or illicit trafficking of nuclear and other radioactive material.[4] The insecurity of nuclear and other radioactive material continues, with some 150 cases of theft, loss of control, or illicit trafficking reported annually. At least 18 cases of confirmed thefts or loss of weapons-usable nuclear material have occurred, the latest in 2011. The growing global demand for nuclear energy for power production and industrial, medical, and research uses means there will be an increasing amount of nuclear material in a growing number of countries that needs to be secured in the future. The impact of a terrorist nuclear explosion would be felt far beyond the city and country where it occurred. The entire global community would be affected, particularly those least able to afford it. In a 2005 speech, UN Secretary-General Kofi Annan said an act of nuclear terrorism “would stagger the world economy and thrust tens of millions of people into dire poverty” and create “a second death toll throughout the developing world.”[5] Other likely impacts would be an enhanced focus on security to prevent future nuclear attacks. This would affect international trade and investment, development assistance, and quite possibly domestic and international systems of governance. For all these reasons, nuclear terrorism must be prevented, as no response could undo the pervasive damage an incident would inflict on individuals, societies, and global approaches to governance and security. Convergence of three factors: loose nukes, new nukes, and new nuclear states, makes nuclear terrorism likely Schwartz 15 (Benjamin Schwartz, served in a variety of national security positions within the United States government, including in the Department of State, Department of Defense, and Department of Energy, Jan 22, 2015, “Right of Boom: The Aftermath of Nuclear Terrorism” https://books.google.com/books?hl=en&lr=&id=kx90BQAAQBAJ&oi=fnd&pg=PT16&dq=%22nuc lear+terrorism%22+&ots=0eodK81fLB&sig=Udz6i4kLUHb3hE66PGweV9zgBSg#v=onepage&q=% 22plausible%20deniability%22&f=false 7/8/2015 ZEC) Over seventy years has passed since the dawn of the nuclear age without a nuclear shot fired in anger. In that time, the world's nuclear powers have built enough atomic bombs to destroy the planet many times over. It is no exaggeration to describe this arms race as humankind approaching the edge of a nuclear abyss, staring down at Armageddon and slowly stepping back. Today the historical record makes clear that a minor miscalculation during the 1962 Cuban Missile Crisis would have sparked a war with casualties in the hundreds of millions.' Not only was atomic warfare avoided during those fourteen days in October 1962 and during the subsequent decades of the Cold War, but today an apocalyptic scenario involving the exchange of multikiloton warheads is extremely unlikely. This accomplishment is a testament to the wisdom of world leaders and the effectiveness of the modern state, though surely some credit is due to divine providence, fate, or extraordinary good luck. Yet just as this nuclear threat was receding another gradually emerged. Today, the risk of a single atomic bomb detonating in a city like Dubai, New York, Singapore, or Washington, DC, is higher than at any point in history. Why? Because the diffusion of nuclear weapons designs, materials, and know-how mean that it is or soon will be plausible for malign actors to conduct a clandestine nuclear attack with limited or no attribution. In 2004, Graham Allison warned that the chance of this type of attack taking place would be somewhere between "inevitable" and "highly likely" unless three conditions, which he referred to as the "Three No's," were met: (1) "no loose nukes." meaning vulnerable nuclear weapons and/or fissile material; (2) "no new nascent nukes," which means no new national capabilities to enrich uranium or reprocess plutonium; and (3) "no new nuclear weapons states." Unfortunately, ten years have passed and in that time each of the three conditions has been violated. The impacts of nuclear terrorism go beyond the initial loss of the detonationi.e. infrastructure damage and its impact on the economy, radiation, etc. Trimble 15 (David Trimble, serves as a Director in the U.S. Government Accountability Office’s Natural Resources & Environment group in Washington DC. Mr. Trimble provides leadership and oversight on Nuclear Security, Safety, and Nonproliferation issues. Mr. Trimble has also led GAO’s work on EPA management and environmental issues such as climate change, hydraulic fracturing, toxic chemicals, and water and air regulations , 2015, “GAO: Two Decades Evaluating the Impact and Effectiveness of U.S. Nuclear and Radiological Material Security Programs” from “Nuclear Threats and Security Challenges” pg. 4 7/8/2015 ZEC) One of the most serious threats facing the United States and other countries is the possibility that other nations or terrorist organizations could steal a nuclear warhead or nuclear weaponusable materials from poorly secured stockpiles around the world. or that nations could divert nuclear material intended for peaceful purposes to the development of nuclear weapons.' Of great concern is that terrorists could fashion a crude nuclear bomb made from either highly enriched uranium (HEU) or plutonium into an improvised nuclear device. Such a device would create an explosion producing extreme heat. powerful shockwaves and intense radiation that would be immediately lethal to individuals within miles of the explosion. as well as radioactive fallout over thousands of square miles. Nonproliferation experts estimate that a successful improvised nuclear device could devastate the heart of a medium- sized U.S. city and could cause hundreds of thousands of deaths and injuries. as well as pose long-term cancer risks to those exposed to the radioactive fallout. Radiological material also poses a significant security threat to the United States and the international community. Radiological material-such as cobalt-60. cesium- I37, and iridium-l92-is encapsulated or sealed in metal to prevent its dispersal and is commonly called a sealed radiological source. Sealed radiological sources are used worldwide for many legitimate purposes. such as medical. industrial. and agricultural applications. The total number of these sources in use worldwide is unknown because many countries do not systematically account for them. If certain types of these sources were obtained by terrorists. they could be used to produce a simple and crude but potentially dangerous weapon-known as a radiological dispersion device, or dirty bomb. Although experts believe that a dirty bomb would result in a limited number of deaths. it could have severe economic consequences. Depending on the type. amount. and form. the dispersed radiological material could cause radiation sickness for people nearby and produce serious economic and psychological disruption associated with the evacuation and subsequent cleanup of the contaminated area. Nuclear terrorism is both likely and dangerous- ramification of an attack have both devastating and global ramifications Pitts-Kiefer 14 (Samantha Pitts-Kiefer, Senior Project Ofcer, Nuclear Threat Initiative (NTI) completed a master’s degree in public administration at the Harvard Kennedy School where she focused on foreign policy and national security. At the Kennedy School, Pitts-Kiefer studied under Graham Allison and Matthew Bunn and was Graham Allison’s course assistant, 2014, “NUCLEAR NIGHTMARES” http://www.nti.org/media/pdfs/Nuclear_Nightmares.pdf?_=1417020879 7/8/15 ZEC) During the Cold War, the United States and the Soviet Union built up vast amounts of nuclear weapons and materials. The Cuban Missile Crisis heightened fears that the nuclear arms race could result in destruction on a massive scale, whether as a result of an intentional or accidental launch and detonation of a nuclear bomb. As the Cold War came to a close, a new threat emerged: nuclear terrorism. With the disintegration of the Soviet Union, nuclear weapons and materials were left scattered across hundreds of sites in former Soviet states prompting urgent concern that smugglers or terrorists would steal enough material for a bomb. Russia and the United States worked together, through the Nunn-Lugar Cooperative Threat Reduction Program, to dismantle and destroy thousands of weapons and to ensure that the nuclear materials from those weapons were disposed of safely. Despite all that has been achieved, the security of weapons-usable nuclear materials remains an urgent concern, while at the same time terrorist groups have grown more sophisticated and more adept at carrying out mass-casualty attacks. So, today’s leaders and citizens face a chilling prospect: the detonation of a crude nuclear weapon built by terrorists with materials stolen or purchased on the black market. Though the al Qaeda that attacked the United States on 9/11 has been much diminished, al Qaeda affiliates in the Arabian Peninsula and Northern Africa, ISIL, and terrorist organizations like al-Shabaab in Somalia remind us that the terrorist threat is dynamic, constantly evolving, and, most of all, enduring. At the same time, the materials needed to build a bomb are spread around the world. Globally, there are approximately 2,000 metric tons of weapons-usable nuclear material (plutonium and highly enriched uranium or HEU) located at hundreds of sites—some of them poorly secured—scattered across twenty-five countries. Building one bomb requires only enough HEU to fill a five-pound bag of sugar or a quantity of plutonium the size of a grapefruit. Terrorists also have access to the technology and know-how needed to build a crude nuclear device, and a number of terrorist groups have in the past stated a desire to acquire and use a nuclear bomb. The consequences of detonating such a bomb in a major city would be staggering: hundreds of thousands of casualties; longlasting environmental damage; economic losses in the hundreds of billions; and considerable political and social ramifications. No matter where a bomb is detonated, the consequences would reverberate around the globe. To build a bomb the biggest challenge terrorists face is obtaining enough HEU or separated plutonium. Every step after acquiring the material—building the bomb, transporting it, and detonating it—is easier for terrorists to take and harder for the international community to stop. So it is imperative that terrorists don’t get a hold of the materials. Today, there are myriad ways that a well-organized and sufficiently-funded terrorist group could seize the materials they need to build an improvised nuclear device that would destroy the heart of a city. They could send a team of armed assailants to overwhelm guards at an understaffed nuclear facility or to attack a convoy transporting weapons-usable nuclear materials from one facility to another. A terrorist or criminal network could corrupt insiders or use a cyberattack to defeat security controls. That is why ensuring that all weapons-usable nuclear material is properly secured to the highest standards is the key to preventing nuclear terrorism. Risk of nuclear terror is high and likely Ogilvie-White 2014 Dr Tanya Ogilvie-White, former senior analyst at the Australian Strategic Policy Institute; Stanton nuclear security fellow at the International Institute for Strategic Studies, senior lecturer in international relations at the University of Canterbury, Preventing Nuclear Terrorism, Australia’s Leadership Role, https://www.aspi.org.au/publications/preventing-nuclear-terrorism-australiasleadership-role/SR63_prevent_nuclear_terrorism.pdf The main worry about the theft and trafficking of nuclear and radiological materials is that they will end up in the hands of terrorist groups, who will use them in INDs or RDDs. Even in the case of an RDD, which is a more likely scenario but would be much less lethal than an IND, radioactive contamination in a densely populated area could have serious economic and social consequences. Although a successful RDD attack has never been perpetrated, there’s evidence that terrorists have invested in such devices: Chechen separatists were involved in two incidents involving radioactive materials in November 1995 and December 1998, and more recently intelligence agencies in mainland Europe, Thailand, the UK and the US have managed to foil RDD plots before they reached fruition. In 2012, the International Atomic Energy Agency (IAEA) Incident and Trafficking Database reported 160 incidents involving the illegal trade and movement of nuclear or other radioactive material across national borders. Of those, 17 involved possession and related criminal activities, 24 involved theft or loss and 119 involved other unauthorised activities. Two incidents involved highly enriched uranium (HEU) in unauthorised activities. There were also three incidents involving dangerous Category 1–3 radioactive sources, two of which were thefts. Information reported to the database demonstrates that: • the availability of unsecured nuclear and other radioactive material persists • although effective border control measures help to detect illicit trafficking, effective controls aren’t uniformly implemented at all international border points • individuals and groups are prepared to engage in trafficking this material. The possibility of RDD or, worse, IND detonation is real and, while the risks need to be kept in perspective, they need to be taken seriously . One of the most worrying recent cases of illicit trafficking involving HEU occurred in June 2011 in Moldova, where officials arrested six people with a quantity of weapon-grade material. The group claimed to have access to plutonium and up to 9 kilograms of HEU, which they were willing to sell for $31 million. A serious buyer, reportedly of North African origin, appears to have been involved and remains at large. Research reactors are considered vulnerable to thefts of nuclear and radiological materials because they’re often located on university campuses or in larger scientific research centres, which are relatively open to the public or have many users and visitors. Moreover, other than the amended Convention on the Physical Protection of Nuclear Material, which has yet to enter into force, there’s no internationally binding requirement for securing these facilities. Since 2003, however, the US and the IAEA have been working with various countries to reduce the risks associated with research reactors. Many countries with HEU-fuelled research reactors, including some in Australia’s near neighbourhood, have taken part in securing HEU and converting the reactors to use low-enriched uranium (LEU). In particular, HEU has been removed and secured from Indonesia, the Philippines, Thailand and, most recently, Vietnam. Of course, LEU-fuelled research reactors remain a target for terrorists who wish to spread ionising radiation or damage a symbolic facility representing technological progress, and most research reactors have substantial quantities of sealed sources that are potentially vulnerable to theft. its High risk - acquisition know-how and , motivation Robichaud 14 (Carl, specialist in nuclear policy at Carnegie Corporation of New York, The Hill, "Preventing nuclear terrorism requires bold action," http://webcache.googleusercontent.com/search?q=cache:sIkI4u49jooJ:thehill.com/blogs/congr ess-blog/homeland-security/201395-preventing-nuclear-terrorism-requires-boldaction+&cd=11&hl=en&ct=clnk&gl=us) Nuclear terrorism is one of the most serious threats of the 21st century. Fortunately, the threat is a preventable one: consolidate and lock down weapons-usable materials and you dramatically reduce the risks. At the Nuclear Security Summit this week, President Obama and more than 50 world leaders will gather in The Hague with an opportunity to take a major step forward in doing just that. But taking the next step in this process will require strong leadership and skillful diplomacy. Though they rarely make the headlines, cases of smuggling, theft or loss of nuclear and radiological materials are alarmingly frequent. Over the past few years we’ve seen incidents from Moldova to India, South Africa to Japan. Just a few months ago in Mexico, carjackers unwittingly heisted radiological materials that, in the wrong hands, could have done significant harm. In fact, more than one hundred thefts and other incidents are reported to the International Atomic Energy Agency (IAEA) each year. In many of these instances we still do not know where the material came from, who stole it, or where it was headed. Nuclear technology is widespread, used not only in power production but in medicine, mining, and other industries. As a result, dozens of countries possesses radiological materials that could be used in a “dirty bomb.” Beyond that, over 25 countries have highly-enriched uranium or plutonium—enough to build more than 20,000 new weapons like the one that destroyed Hiroshima and almost 80,000 like the one that destroyed Nagasaki. In the wrong hands, it wouldn’t take much plutonium or highly enriched uranium to fashion a nuclear device. You could fit a bombs-worth of this material into a lunch box. Al-Qaeda and other terrorist groups around the globe have expressed intent to acquire weapons-usable materials. If they succeed there is little doubt they would use such a device. Thus the spread of these materials is a grave threat—not only to the United States but to any country that relies upon the global economy, which would be severely disrupted if an attack ever succeeded. Robert Gates, former U.S. Secretary of Defense, noted that, “Every senior leader, when you’re asked what keeps you awake at night, it’s the thought of a terrorist ending up with a weapon of mass destruction, especially nuclear.” 2 – its High risk - acquisition know-how and , motivation Robichaud 14 (Carl, specialist in nuclear policy at Carnegie Corporation of New York, The Hill, "Preventing nuclear terrorism requires bold action," http://webcache.googleusercontent.com/search?q=cache:sIkI4u49jooJ:thehill.com/blogs/congr ess-blog/homeland-security/201395-preventing-nuclear-terrorism-requires-boldaction+&cd=11&hl=en&ct=clnk&gl=us) Nuclear terrorism is one of the most serious threats of the 21st century. Fortunately, the threat is a preventable one: consolidate and lock down weapons-usable materials and you dramatically reduce the risks. At the Nuclear Security Summit this week, President Obama and more than 50 world leaders will gather in The Hague with an opportunity to take a major step forward in doing just that. But taking the next step in this process will require strong leadership and skillful diplomacy. Though they rarely make the headlines, cases of smuggling, theft or loss of nuclear and radiological materials are alarmingly frequent. Over the past few years we’ve seen incidents from Moldova to India, South Africa to Japan. Just a few months ago in Mexico, carjackers unwittingly heisted radiological materials that, in the wrong hands, could have done significant harm. In fact, more than one hundred thefts and other incidents are reported to the International Atomic Energy Agency (IAEA) each year. In many of these instances we still do not know where the material came from, who stole it, or where it was headed. Nuclear technology is widespread, used not only in power production but in medicine, mining, and other industries. As a result, dozens of countries possesses radiological materials that could be used in a “dirty bomb.” Beyond that, over 25 countries have highly-enriched uranium or plutonium—enough to build more than 20,000 new weapons like the one that destroyed Hiroshima and almost 80,000 like the one that destroyed Nagasaki. In the wrong hands, it wouldn’t take much plutonium or highly enriched uranium to fashion a nuclear device. You could fit a bombs-worth of this material into a lunch box. Al-Qaeda and other terrorist groups around the globe have expressed intent to acquire weapons-usable materials. If they succeed there is little doubt they would use such a device. Thus the spread of these materials is a grave threat—not only to the United States but to any country that relies upon the global economy, which would be severely disrupted if an attack ever succeeded. Robert Gates, former U.S. Secretary of Defense, noted that, “Every senior leader, when you’re asked what keeps you awake at night, it’s the thought of a terrorist ending up with a weapon of mass destruction, especially nuclear.” Terror Adv – Nuclear Terror Causes Extinction Causes US-Russia miscalc—extinction Barrett et al, RAND Stanton nuclear security fellow, 2013 [Anthony, PhD in Engineering and Public Policy from Carnegie Mellon University, and Director of Research at Global Catastrophic Risk Institute—AND Seth Baum, PhD in Geography from Pennsylvania State University, Research Scientist at the Blue Marble Space Institute of Science, and Executive Director of Global Catastrophic Risk Institute—AND Kelly Hostetler, BS in Political Science from Columbia and Research Assistant at Global Catastrophic Risk Institute, 6-24-13, Science & Global Security: The Technical Basis for Arms Control, Disarmament, and Nonproliferation Initiatives, Volume 21, Issue 2, “Analyzing and Reducing the Risks of Inadvertent Nuclear War Between the United States and Russia,” Tanfonline] War involving significant fractions of the U.S. and Russian nuclear arsenals, which are by far the largest of any nations, could have globally catastrophic effects such as severely reducing food production for years, 1 potentially leading to collapse of modern civilization worldwide, and even the extinction of humanity. 2 Nuclear war between the United States and Russia could occur by various routes, including accidental or unauthorized launch; deliberate first attack by one nation; and inadvertent attack. In an accidental or unauthorized launch or detonation, system safeguards or procedures to maintain control over nuclear weapons fail in such a way that a nuclear weapon or missile launches or explodes without direction from leaders. In a deliberate first attack, the attacking nation decides to attack based on accurate information about the state of affairs. In an inadvertent attack, the attacking nation mistakenly concludes that it is under attack and launches nuclear weapons in what it believes is a counterattack. 3 (Brinkmanship strategies incorporate elements of all of the above, in that they involve intentional manipulation of risks from otherwise accidental or inadvertent launches. 4 ) Over the years, nuclear strategy was aimed primarily at minimizing risks of intentional attack through development of deterrence capabilities, and numerous measures also were taken to reduce probabilities of accidents, unauthorized attack, and inadvertent war. For purposes of deterrence, both U.S. and Soviet/Russian forces have maintained significant capabilities to have some forces survive a first attack by the other side and to launch a subsequent counterattack. However, concerns about the extreme disruptions that a first attack would cause in the other side's forces and command-and-control capabilities led to both sides’ development of capabilities to detect a first attack and launch a counter-attack before suffering damage from the first attack. 5 Many people believe that with the end of the Cold War and with improved relations between the United States and Russia, the risk of East-West nuclear war was significantly reduced. 6 However, it also has been argued that inadvertent nuclear war between the United States and Russia has continued to present a substantial risk. 7 While the United States and Russia are not actively threatening each other with war, they have remained ready to launch nuclear missiles in response to indications of attack. 8 False indicators of nuclear attack could be caused in several ways. First, a wide range of events have already been mistakenly interpreted as indicators of attack, including weather phenomena, a faulty computer chip, wild animal activity, and control-room training tapes loaded at the wrong time. 9 Second, terrorist groups or other actors might cause attacks on either the United States or Russia that resemble some kind of nuclear attack by the other nation by actions such as exploding a stolen or improvised nuclear bomb, 10 especially if such an event occurs during a crisis between the United States and Russia. 11 A variety of nuclear terrorism scenarios are possible. 12 Al Qaeda has sought to obtain or construct nuclear weapons and to use them against the United States. 13 Other methods could involve attempts to circumvent nuclear weapon launch control safeguards or exploit holes in their security. 14 It has long been argued that the probability of inadvertent nuclear war is significantly higher during U.S.– Russian crisis conditions, 15 with the Cuban Missile Crisis being a prime historical example. It is possible that U.S.–Russian relations will significantly deteriorate in the future, increasing nuclear tensions. There are a variety of ways for a third party to raise tensions between the United States and Russia, making one or both nations more likely to misinterpret events as attacks. 16 Absent retaliation, it is sufficient to trigger extinction. Robock, Rutgers University environmental sciences professor, 2011 [Alan, Nature International weekly journal of science 473, 5-19-11, “Nuclear winter is a real and present danger” http://www.nature.com/nature/journal/v473/n7347/full/473275a.html] Yet the environmental threat of nuclear war has not gone away. The world faces the prospect of a smaller, but still catastrophic, nuclear conflict. There are now nine nuclear-weapons states. Use of a fraction of the global nuclear arsenal by anyone, from the superpowers to India versus Pakistan, still presents the largest potential environmental danger to the planet by humans. That threat is being ignored. One reason for this denial is that the prospect of a nuclear war is so horrific on so many levels that most people simply look away. Two further reasons are myths that persist among the general public: that the nuclear winter theory has been disproved, and that nuclear winter is no longer a threat. These myths need to be debunked. The term 'nuclear winter', coined by Carl Sagan and his colleagues in a 1983 paper1 in Science, describes the dramatic effects on the climate caused by smoke from fires ignited by nuclear attacks on cities and industrial areas. In the 1980s my colleagues and I calculated, using the best climate models available at the time, that if one-third of the existing arsenal was used, there would be so much smoke that surface temperatures would plummet below freezing around the world for months, killing virtually all plants and producing worldwide famine. More people could die in China from starvation than in the nations actively bombing each other. As many countries around the world realized that a superpower nuclear war would be a disaster for them, they pressured the superpowers to end their arms race. Sagan did a good job of summarizing the policy impacts2 in 1984: although weapons were continuing to be built, it would be suicide to use them. The idea of climatic catastrophe was fought against by those who wanted to keep the nuclear-weapon industry alive, or who supported the growth of nuclear arsenals politically3. Scientifically, there was no real debate about the concept, only about the details. In 1986, atmospheric researchers Starley Thompson and Stephen Schneider wrote a piece in Foreign Affairs appraising the theory4 and highlighting what they saw as the patchiness of the effect. They coined the term 'nuclear autumn', noting that it wouldn't be 'winter' everywhere in the aftermath of a nuclear attack. They didn't mean for people to think that it would be all raking leaves and football games, but many members of the public, and some pronuclear advocates, preferred to take it that way. The fight over the details of the modelling caused a rift between Sagan and Schneider that never healed. When I bring up the topic of nuclear winter, people invariably tell me that they think the theory has been disproved. But research continues to support the original concept. By 2007, models had began to approximate a realistic atmosphere up to 80 kilometres above Earth's surface, including the stratosphere and mesosphere. This enabled me, and my coauthors, to calculate for the first time that smoke particles would be heated by the Sun and lifted into the upper stratosphere, where they would stay for many years5, 6. So the cooling would last for much longer than we originally thought. Dark days Many of those who do accept the nuclear-winter concept think that the scenario applies only to a mass conflict, on a scale no longer conceivable in the modern world. This is also false. A 'small' nuclear war between India and Pakistan, with each using 50 Hiroshima-size bombs (far less than 1% of the current arsenal), if dropped on megacity targets in each country would produce climate change unprecedented in recorded human history5. Five million tonnes of black carbon smoke would be emitted into the upper troposphere from the burning cities, and then be lofted into the stratosphere by the heat of the Sun. Temperatures would be lower than during the 'Little Ice Age' (1400–1850), during which famine killed millions. For several years, growing seasons would be shortened by weeks in the mid-latitudes (see 'A decade of cooling). Brian Toon at the University of Colorado in Boulder, Richard Turco at the University of California, Los Angeles, Georgiy Stenchikov at Rutgers University in New Brunswick, New Jersey, and I, all of whom were pioneers in nuclear-winter research in the 1980s, have tried, along with our students, to publicize our results. We have published refereed journal articles, popular pieces in Physics Today and Scientific American, a policy forum in Science, and now this article. But Foreign Affairs and Foreign Policy, perhaps the two most prominent foreign-policy magazines in English, would not even review articles we submitted. We have had no luck getting attention from the US government. Toon and I visited the US Congress and gave briefings to congressional staff on the subject two years ago, but nothing happened as a result. The US President's science adviser John Holdren has not responded to our requests — in 2009 and more recently — for consideration of new scientific results in US nuclear policy. Yes Extinction – AT: No Retaliation Retaliation causes global nuclear war Hellman, Professor Emeritus of Electrical Engineering, Stanford University, 8 [Martin, Spring, “Risk Analysis of Nuclear Deterrence”, http://nuclearrisk.org/3likely.php] Nuclear proliferation and the specter of nuclear terrorism are creating additional possibilities for triggering a nuclear war. If an American (or Russian) city were devastated by an act of nuclear terrorism, the public outcry for immediate, decisive action would be even stronger than Kennedy had to deal with when the Cuban missiles first became known to the American public. While the action would likely not be directed against Russia, it might be threatening to Russia (e.g., on its borders) or one of its allies and precipitate a crisis that resulted in a fullscale nuclear war. Terrorists with an apocalyptic mindset might even attempt to catalyze a full-scale nuclear war by disguising their act to look like an attack by the U.S. or Russia. That escalates to global nuclear war Speice, JD Candidate, February 2006 [Patrick, 47 Wm and Mary L. Rev. 1427, Lexis] The potential consequences of the unchecked spread of nuclear knowledge and material to terrorist groups that seek to cause mass destruction in the United States are truly horrifying. A terrorist attack with a nuclear weapon would be devastating in terms of immediate human and economic losses. n49 Moreover, there would be immense political pressure in the United States to discover the perpetrators and retaliate with nuclear weapons, massively increasing the number of casualties and potentially triggering a full-scale nuclear conflict. N50 In addition to the threat posed by terrorists, leakage of nuclear knowledge and material from Russia will reduce the barriers that states with nuclear ambitions face and may trigger widespread proliferation of nuclear weapons. n51 This proliferation will increase the risk of nuclear attacks against the United States [*1440] or its allies by hostile states, n52 as well as increase the likelihood that regional conflicts will draw in the United States and escalate to the use of nuclear weapons. Yes Extinction – AT: Not Feasible Nuclear terrorism is feasible, there are no barriers and there’s motivation for an attack now Bunn et al. 14 [March 2014, Matthew Bunn is a Professor of Practice at the Harvard Kennedy School. His research interests include nuclear theft and terrorism; nuclear proliferation and measures to control it; the future of nuclear energy and its fuel cycle; and innovation in energy technologies, he served as an adviser to the White House Office of Science and Technology Policy, as a study director at the National Academy of Sciences, and as editor of Arms Control Today, author or co-author of more than 20 books or major technical reports, and over a hundred articles in publications, Martin B. Malin, the Executive Director of the Project on Managing the Atom at the Belfer Center for Science and International Affairs at Harvard’s Kennedy School of Government, focuses on arms control and nonproliferation in the Middle East, US nonproliferation and counter-proliferation strategies, and the security consequences of the growth and spread of nuclear energy. Malin taught international relations, American foreign policy, and Middle East politics at Columbia University, Barnard College, and Rutgers University, served as Director of the Program on Science and Global Security at the American Academy of Arts and Sciences. Nickolas Roth is a research associate at the Project on Managing the Atom. Mr. has a Masters of Public Policy from the University of Maryland. While at Maryland, he served as a research assistant for the Center for International and Security Studies’ Nuclear Materials Accounting Project. He has expertise in national security issues related to US nuclear weapons policy. William H. Tobey is a Senior Fellow at the Belfer Center for Science and International Affairs. He was most recently Deputy Administrator for Defense Nuclear Nonproliferation at the National Nuclear Security Administration. There, he managed the US government’s largest program to prevent nuclear proliferation and terrorism by detecting, securing, and disposing of dangerous nuclear material. Mr. Tobey also served on the National Security Council Staff in three administrations, in defense policy, arms control, and counter-proliferation positions. He has participated in international negotiations ranging from the START talks with the Soviet Union to the Six Party Talks with North Korea. He is chair of the board of directors of the World Institute for Nuclear Security, “Advancing Nuclear Security: Evaluating Progress and Setting New Goals,” http://belfercenter.ksg.harvard.edu/files/advancingnuclearsecurity.pdf] Unfortunately, nuclear and radiological terrorism remain real and dangerous threats.1 The conclusion the assembled leaders reached at the Washington Nuclear Security Summit and reaffirmed in Seoul remains correct: “Nuclear terrorism continues to be one of the most challenging threats to international security. Defeating this threat requires strong national measures and international cooperation given its potential global political, economic, social, and psychological consequences.”2 There are three types of nuclear or radiological terrorist attack: • Nuclear weapons. Terrorists might be able to get and detonate an assembled nuclear weapon made by a state, or make a crude nuclear bomb from stolen separated plutonium or HEU. This would be the most difficult type of nuclear terrorism for terrorists to accomplish— but the devastation could be absolutely horrifying, with political and economic aftershocks reverberating around the world. • “Dirty bombs.” A far simpler approach would be for terrorists to obtain radiological materials— available in hospitals, industrial sites, and more—and disperse them to contaminate an area with radioactivity, using explosives or any number of other means. In most scenarios of such attacks, few people would die from the radiation—but the attack could spread fear, force the evacuation of many blocks of a major city, and inflict billions of dollars in costs of cleanup and economic disruption. While a dirty bomb attack would be much easier for terrorists to carry out than an attack using a nuclear explosive, the consequences would be far less—an expensive and disruptive mess, but not the heart of a major city going up in smoke. • Nuclear sabotage. Terrorists could potentially cause a Fukushima-like meltdown at a nuclear reactor or sabotage a spent fuel pool or high-level waste store. An unsuccessful sabotage would have little effect, but a successful one could spread radioactive material over a huge area. Both the scale of the consequences and the difficulty of carrying out a successful attack would be intermediate between nuclear weapons and dirty bombs. Overall, while actual terrorist use of a nuclear weapon may be the least likely of these dangers, its consequences would be so overwhelming that we believe it poses the most significant risk. A similar judgment drove the decision to focus the four-year effort on securing nuclear weapons and the materials needed to make them. Most of this report will focus on the threat of terrorist use of nuclear explosives, but the overall global governance framework for nuclear security is relevant to all of these dangers. The danger of nuclear terrorism is driven by three key factors—terrorist intent to escalate to the nuclear level of violence; potential terrorist capability to do so; and the vulnerability of nuclear weapons and the materials needed to enable terrorists to carry out such an attack—the motive, means, and opportunity of a monstrous crime. Terrorist intent. While most terrorist groups are still focused on small-scale violence for local political purposes, we now live in an age that includes some groups intent on inflicting largescale destruction to achieve their objectives. Over the past quarter century, both al Qaeda and the Japanese terror cult Aum Shinrikyo seriously sought nuclear weapons and the nuclear materials and expertise needed to make them. Al Qaeda had a focused program reporting directly to Ayman al-Zawahiri (now head of the group), which progressed as far as carrying out crude but sensible conventional explosive tests for the nuclear program in the desert of Afghanistan. There is some evidence that North Caucusus terrorists also sought nuclear weapons—including incidents in which terrorist teams were caught carrying out reconnaissance on Russian nuclear weapon storage sites, whose locations are secret.3 Despite the death of Osama bin Laden and the severe disruption of the core of al Qaeda, there are no grounds for complacency. There is every reason to believe Zawahiri remains eager to inflict destruction on a nuclear scale. Indeed, despite the large number of al Qaeda leaders who have been killed or captured, nearly all of the key players in al Qaeda’s nuclear program remain alive and at large—including Abdel Aziz al-Masri, an Egyptian explosives expert who was al Qaeda’s “nuclear CEO.” In 2003, when al Qaeda operatives were negotiating to buy three of what they thought were nuclear weapons, senior al Qaeda officials told them to go ahead and make the purchase if a Pakistani expert with equipment confirmed the items were genuine. The US government has never managed to determine who the Pakistani nuclear weapons expert was in whom al Qaeda had such confidence—and what he may have been doing in the intervening decade. More fundamentally, with at least two, and probably three, groups having gone down this path in the past 25 years, there is no reason to expect they will be the last. The danger of nuclear terrorism will remain as long as nuclear weapons, the materials needed to make them, and terrorist groups bent on large-scale destruction co-exist. Potential terrorist capabilities. No one knows what capabilities a secret cell of al Qaeda may have managed to retain or build. Unfortunately, it does not take a Manhattan Project to make a nuclear bomb—indeed, over 90 percent of the Manhattan Project effort was focused on making the nuclear materials, not on designing and building the weapons. Numerous studies by the United States and other governments have concluded that it is plausible that a sophisticated terrorist group could make a crude nuclear bomb if it got enough separated plutonium or HEU.4 A “gun-type” bomb, such as the weapon that obliterated Hiroshima, fundamentally involves slamming two pieces of HEU together at high speed. An “implosion-type” bomb, which is needed to get a substantial explosive yield from plutonium, requires crushing nuclear material to a higher density— a more complex task, but still plausible for terrorists, especially if they got knowledgeable help. Many analysts argue that, since states spend billions of dollars and assign hundreds or thousands of people to building nuclear weapons, it is totally implausible that terrorists could carry out this task. Unfortunately, this argument is wrong, for two reasons. First, as the Manhattan Project statistic suggests, the difficult part of making a nuclear bomb is making the nuclear material. That is what states spend billions seeking to accomplish. Terrorists are highly unlikely to ever be able to make their own bomb material—but if they could get stolen material, that step would be bypassed. Second, it is far easier to make a crude, unsafe, unreliable bomb of uncertain yield, which might be delivered in the back of a truck, than to make the kind of nuclear weapon a state would want in its arsenal—a safe, reliable weapon of known yield that can be delivered by missile or combat aircraft. It is highly unlikely terrorists will ever be able to build that kind of nuclear weapon. Remaining vulnerabilities. While many countries have done a great deal to strengthen nuclear security, serious vulnerabilities remain. Around the world, there are stocks of nuclear weapons or materials whose security systems are not sufficient to protect against the full range of plausible outsider and insider threats they may face. As incidents like the intrusion at Y-12 in the United States in 2012 make clear, many nuclear facilities and transporters still grapple with serious problems of security culture. It is fair to say that every country where nuclear weapons, weaponsusable nuclear materials, major nuclear facilities, or dangerous radiological sources exist has more to do to ensure that these items are sustainably secured and accounted for. At least three lines of evidence confirm that important nuclear security weaknesses continue to exist. First, seizures of stolen HEU and separated plutonium continue to occur, including, mostly recently HEU seizures in 2003, 2006, 2010, and 2011.5 These seizures may result from material stolen long ago, but, at a minimum, they make clear that stocks of HEU and plutonium remain outside of regulatory control. Second, in cases where countries do realistic tests to probe whether security systems can protect against teams of clever adversaries determined to find a weak point, the adversaries sometimes succeed—even when their capabilities are within the set of threats the security system is designed to protect against. This happens with some regularity in the United States (though less often than before the 9/11 attacks); if more countries carried out comparable performance tests, one would likely see similar results. Third, in real non-nuclear thefts and terrorist attacks around the world, adversaries sometimes demonstrate capabilities and tactics well beyond what many nuclear security systems would likely be able to handle (see the discussion of the recent Västberga incident in Sweden). being caught.6 And terrorists are unlikely to have enough money to make a substantial difference in either the odds of regime survival or the wealth of a regime’s elites, even in North Korea, one of the poorest countries on earth. On the other hand, serious risks would arise in North Korea, or other nuclear-armed states, in the event of state collapse—and as North Korea’s stockpile grows, one could imagine a general managing some of that stockpile concluding he could sell a piece of it and provide a golden parachute for himself and his family without getting caught. No one knows the real likelihood of nuclear terrorism. But the consequences of a terrorist nuclear blast would be so catastrophic that even a small chance is enough to justify urgent action to reduce the risk. The heart of a major city could be reduced to a smoldering radioactive ruin, leaving tens to hundreds of thousands of people dead. The perpetrators or others might claim to have more weapons already hidden in other major cities and threaten to set them off if their demands were not met—potentially provoking uncontrolled evacuation of many urban centers. Devastating economic consequences would reverberate worldwide. Kofi Annan, while serving as Secretary-General of the United Nations, warned that the global economic effects of a nuclear terrorist attack in a major city would push “tens of millions of people into dire poverty,” creating a “second death toll throughout the developing world.”7 Attacks are feasible Bunn, et al, 13 [October 2nd 2013, Bunn, Matthew, Valentin Kuznetsov, Martin B. Malin, Yuri Morozov, Simon Saradzhyan, William H. Tobey, Viktor I. Yesin, and Pavel S. Zolotarev. "Steps to Prevent Nuclear Terrorism." Paper, Belfer Center for Science and International Affairs, Harvard Kennedy School, October 2, 2013, Matthew Bunn. Professor of the Practice of Public Policy at Harvard Kennedy School andCo-Principal Investigator of Project on Managing the Atom at Harvard University’s Belfer Center for Science and International Affairs. • Vice Admiral Valentin Kuznetsov (retired Russian Navy). Senior research fellow at the Institute for U.S. and Canadian Studies of the Russian Academy of Sciences, Senior Military Representative of the Russian Ministry of Defense to NATO from 2002 to 2008. • Martin Malin. Executive Director of the Project on Managing the Atom at the Belfer Center for Science and International Affairs. • Colonel Yuri Morozov (retired Russian Armed Forces). Professor of the Russian Academy of Military Sciences and senior research fellow at the Institute for U.S. and Canadian Studies of the Russian Academy of Sciences, chief of department at the Center for Military-Strategic Studies at the General Staff of the Russian Armed Forces from 1995 to 2000. • Simon Saradzhyan. Fellow at Harvard University’s Belfer Center for Science and International Affairs, Moscow-based defense and security expert and writer from 1993 to 2008. • William Tobey. Senior fellow at Harvard University’s Belfer Center for Science and International Affairs and director of the U.S.-Russia Initiative to Prevent Nuclear Terrorism, deputy administrator for Defense Nuclear Nonproliferation at the U.S. National Nuclear Security Administration from 2006 to 2009. • Colonel General Viktor Yesin (retired Russian Armed Forces). Leading research fellow at the Institute for U.S. and Canadian Studies of the Russian Academy of Sciences and advisor to commander of the Strategic Missile Forces of Russia, chief of staff of the Strategic Missile Forces from 1994 to 1996. • Major General Pavel Zolotarev (retired Russian Armed Forces). Deputy director of the Institute for U.S. and Canadian Studies of the Russian Academy of Sciences, head of the Information and Analysis Center of the Russian Ministry of Defense from1993 to 1997, section head - deputy chief of staff of the Defense Council of Russia from 1997 to 1998, "Steps to Prevent Nuclear Terrorism," http://belfercenter.ksg.harvard.edu/files/JTA%20eng%20web2.pdf] In 2011, Harvard’s Belfer Center for Science and International Affairs and the Russian Academy¶ of Sciences’ Institute for U.S. and Canadian Studies published “The U.S. – Russia Joint Threat¶ Assessment on Nuclear Terrorism.” The assessment analyzed the means, motives, and access of¶ would-be nuclear terrorists, and concluded that the threat of nuclear terrorism is urgent and real.¶ The Washington and Seoul Nuclear Security Summits in 2010 and 2012 established and demonstrated a consensus among political leaders from around the world that nuclear terrorism poses a serious threat to the peace, security, and prosperity of our planet. For any country, a terrorist attack with a nuclear device would be an immediate and catastrophic disaster, and the negative effects would reverberate around the world far beyond the location and moment of the detonation. Preventing a nuclear terrorist attack requires international cooperation to secure nuclear materials,¶ especially among those states producing nuclear materials and weapons. As the world’s two¶ greatest nuclear powers, the United States and Russia have the greatest experience and capabilities¶ in securing nuclear materials and plants and, therefore, share a special responsibility to lead¶ international efforts to prevent terrorists from seizing such materials and plants.¶ The depth of convergence between U.S. and Russian vital national interests on the issue of¶ nuclear security is best illustrated by the fact that bilateral cooperation on this issue has continued¶ uninterrupted for more than two decades, even when relations between the two countries¶ occasionally became frosty, as in the aftermath of the August 2008 war in Georgia.¶ Russia and the United States have strong incentives to forge a close and trusting partnership to¶ prevent nuclear terrorism and have made enormous progress in securing fissile material both at¶ home and in partnership with other countries. However, to meet the evolving threat posed by¶ those individuals intent upon using nuclear weapons for terrorist purposes, the United States and¶ Russia need to deepen and broaden their cooperation.¶ The 2011 “U.S. - Russia Joint Threat Assessment” offered both specific conclusions about the¶ nature of the threat and general observations about how it might be addressed. This report builds¶ on that foundation and analyzes the existing framework for action, cites gaps and deficiencies,¶ and makes specific recommendations for improvement.¶ “The U.S. – Russia Joint Threat Assessment on Nuclear Terrorism” (The 2011 report¶ executive summary): • Nuclear terrorism is a real and urgent threat. Urgent actions are required to reduce the risk. The risk is driven by the rise of terrorists who seek to inflict unlimited damage, many of¶ whom have sought justification for their plans in radical interpretations of Islam; by the¶ spread of information about the decades-old technology of nuclear weapons; by the increased¶ availability of weapons-usable nuclear materials; and by globalization, which makes it easier¶ to move people, technologies, and materials across the world. • Making a crude nuclear bomb would not be easy, but is potentially within the capabilities of¶ a technically sophisticated terrorist group, as numerous government studies have confirmed.¶ Detonating a stolen nuclear weapon would likely be difficult for terrorists to accomplish, if¶ the weapon was equipped with modern technical safeguards (such as the electronic locks¶ known as Permissive Action Links, or PALs). Terrorists could, however, cut open a stolen¶ nuclear weapon and make use of its nuclear material for a bomb of their own. • The nuclear material for a bomb is small and difficult to detect, making it a major challenge¶ to stop nuclear smuggling or to recover nuclear material after it has been stolen. Hence, a primary¶ focus in reducing the risk must be to keep nuclear material and nuclear weapons from¶ being stolen by continually improving their security, as agreed at the Nuclear Security Summit¶ in Washington in April 2010. • Al-Qaeda has sought nuclear weapons for almost two decades. The group has repeatedly¶ attempted to purchase stolen nuclear material or nuclear weapons, and has repeatedly attempted¶ to recruit nuclear expertise. Al-Qaeda reportedly conducted tests of conventional¶ explosives for its nuclear program in the desert in Afghanistan. The group’s nuclear ambitions¶ continued after its dispersal following the fall of the Taliban regime in Afghanistan.¶ Recent writings from top al-Qaeda leadership are focused on justifying the mass slaughter of¶ civilians, including the use of weapons of mass destruction, and are in all likelihood intended¶ to provide a formal religious justification for nuclear use. • While there are significant gaps in coverage of the group’s activities, al-Qaeda appears to¶ have been frustrated thus far in acquiring a nuclear capability; it is unclear whether the the¶ group has acquired weapons-usable nuclear material or the expertise needed to make such¶ material into a bomb. Furthermore, pressure from a broad range of counter-terrorist actions¶ probably has reduced the group’s ability to manage large, complex projects, but has not¶ eliminated the danger. However, there is no sign the group has abandoned its nuclear ambitions.¶ On the contrary, leadership statements as recently as 2008 indicate that the intention to¶ acquire and use nuclear weapons is as strong as ever. There are no checks on acquisition – lack of border controls and ease of theft Ogilvie-White, independent researcher specializing in nuclear issues, and Santoro, senior fellow at the Pacific Forum CSIS, 14 [Dr Tanya, independent researcher specializing in nuclear issues, based in Canberra, Australia. Previously, she was senior analyst at the Australian Strategic Policy Institute; Stanton nuclear security fellow at the International Institute for Strategic Studies, UK; nuclear non-proliferation researcher at the Mountbatten Centre for International Studies, trustee of the New Zealand Centre for Global Studies, a member of the Council on Security Cooperation in the Asia-Pacific, Asia-Pacific representative of the Fissile Material Working Group, and associate editor of Asian Security. Dr David Santoro is a senior fellow at the Pacific Forum CSIS. He directs the Forum’s nuclear policy programs and works on nonproliferation and nuclear security, disarmament, and deterrence, on which he has published widely. Prior to joining the Forum, he worked on nuclear policy issues in France, Australia, Canada, and the United Kingdom, including at the Institute for International Strategic Studies as a Stanton nuclear security fellow, Australian Strategic Policy Institute, “Preventing Nuclear Terrorism, Australia’s Leadership Role,” https://www.aspi.org.au/publications/preventing-nuclear-terrorism-australias-leadershiprole/SR63_prevent_nuclear_terrorism.pdf] The main worry about the theft and trafficking of nuclear and¶ radiological materials is that they will end up in the hands of¶ terrorist groups, who will use them in INDs or RDDs. Even in¶ the case of an RDD, which is a more likely scenario but would¶ be much less lethal than an IND, radioactive contamination¶ in a densely populated area could have serious economic and¶ social consequences. Although a successful RDD attack has¶ never been perpetrated, there’s evidence that terrorists have¶ invested in such devices: Chechen separatists were involved¶ in two incidents involving radioactive materials in November¶ 1995 and December 1998, and more recently intelligence¶ agencies in mainland Europe, Thailand, the UK and the US¶ have managed to foil RDD plots before they reached fruition. In 2012, the International Atomic Energy Agency (IAEA)¶ Incident and Trafficking Database reported 160 incidents¶ involving the illegal trade and movement of nuclear or other¶ radioactive material across national borders. Of those,¶ 17 involved possession and related criminal activities,¶ 24 involved theft or loss and 119 involved other unauthorised¶ activities. Two incidents involved highly enriched uranium¶ (HEU) in unauthorised activities. There were also three¶ incidents involving dangerous Category 1–3 radioactive¶ sources, two of which were thefts. Information reported to¶ the database demonstrates that:¶ • the availability of unsecured nuclear and other¶ radioactive material persists¶ • although effective border control measures help to¶ detect illicit trafficking, effective controls aren’t uniformly¶ implemented at all international border points¶ • individuals and groups are prepared to engage in¶ trafficking this material. The possibility of RDD or, worse, IND detonation is real and,¶ while the risks need to be kept in perspective, they need to be¶ taken seriously. One of the most worrying recent cases of illicit trafficking¶ involving HEU occurred in June 2011 in Moldova, where¶ officials arrested six people with a quantity of weapon-grade¶ material. The group claimed to have access to plutonium¶ and up to 9 kilograms of HEU, which they were willing to sell¶ for $31 million. A serious buyer, reportedly of North African¶ origin, appears to have been involved and remains at large. Research reactors are considered vulnerable to thefts of¶ nuclear and radiological materials because they’re often¶ located on university campuses or in larger scientific research¶ centres, which are relatively open to the public or have¶ many users and visitors. Moreover, other than the amended¶ Convention on the Physical Protection of Nuclear Material,¶ which has yet to enter into force, there’s no internationally¶ binding requirement for securing these facilities. Since¶ 2003, however, the US and the IAEA have been working¶ with various countries to reduce the risks associated with¶ research reactors. Many countries with HEU-fuelled research¶ reactors, including some in Australia’s near neighbourhood,¶ have taken part in securing HEU and converting the reactors¶ to use low-enriched uranium (LEU). In particular, HEU has¶ been removed and secured from Indonesia, the Philippines,¶ Thailand and, most recently, Vietnam. Of course, LEU-fuelled¶ research reactors remain a target for terrorists who wish¶ to spread ionising radiation or damage a symbolic facility¶ representing technological progress, and most research¶ reactors have substantial quantities of sealed sources that¶ are potentially vulnerable to theft. It only takes .001 of a stockpile to kill Harrell, Associate at the Project on Managing the Atom at Harvard University’s Belfer Center for Science and International Affairs, 3-24-14 [Eben, “We’re Not Prepared for a Nuclear Heist,” TIME, http://time.com/33802/were-notprepared-for-a-nuclear-heist/, 3-24-14] How did an 82-year-old nun come so close to getting her hands on highly enriched uranium?¶ In September 2009, a group of masked men armed with automatic weapons and explosives arrived on the roof of a cash depot in Vastberg, Sweden in a helicopter. The men blasted their way through a skylight and hoisted millions of dollars up to the hovering aircraft — the operation took less than 20 minutes. When police rushed to respond they discovered a bag with the word “bomb” at their heliport — a diversion planted by the thieves — and caltrops (road spikes) near the depot to slow down their response on the ground. While many of the thieves were caught after an investigation, most of the money was never recovered.¶ The Vastberg heist was not a nuclear event, but a new report from my colleagues at Harvard University makes the case that the incident should have deeply troubling implications for the leaders from over 50 countries convening in the Netherlands on March 24-25 for a summit on nuclear security. The stark truth is that many locations around the world that store highly enriched uranium (HEU) and plutonium — the essential ingredients of nuclear weapons — would not be able to repel an attack from adversaries using tactics and weapons as sophisticated as those used by the Vastberg thieves. An amount of plutonium that would fit in a soda can would be enough for terrorists to construct a crude nuclear bomb capable of reducing the heart of a major city to rubble (it wouldn’t require much HEU, either). Today, there are approximately 1440 tons of HEU and 500 tons of separated plutonium in hundreds of buildings in dozens of countries around the world; the theft of only .001 percent of this stockpile could lead to hundreds of thousands of deaths. Easy to access materials. Dahl, Reuters, 3-25-14 [Fredrik, “U.S. and Russia agree on nuclear terrorism threat - up to a point” http://www.reuters.com/article/2014/03/25/us-nuclear-security-summitidUSBREA2O12820140325] Since 1991, the number of countries with nuclear weapons-usable material has roughly halved from some 50.¶ However, more than 120 research and isotope production reactors around the world still use HEU for fuel or targets, many of them with "very modest" security measures, a Harvard Kennedy School report said this month.¶ "With at least two and possibly three groups having pursued nuclear weapons in the past quarter century, they are not likely to be the last," the report said.¶ Referring to a push to use low-enriched uranium (LEU) as fuel in research and other reactor types instead of HEU, the summit statement said: "We encourage states to continue to minimize the use of HEU through the conversion of reactor fuel from HEU to LEU, where technically and economically feasible.¶ "Similarly, we will continue to encourage and support efforts to use non-HEU technologies for the production of radio-isotopes, including financial incentives," it said.¶ An apple-sized amount of plutonium in a nuclear device and detonated in a highly populated area could instantly kill or wound hundreds of thousands of people, according to the Nuclear Security Governance Experts Group (NSGEG) lobby group.¶ But a so-called "dirty bomb" is seen as a more likely threat than an atomic bomb: conventional explosives are used to disperse radiation from a radioactive source, which can be found in hospitals or other places that may not be very well secured.¶ In December, Mexican police found a truck they suspected was stolen by common thieves and which carried a radioactive medical material that could have provided such an ingredient.¶ In another incident that put nuclear security in the spotlight and embarrassed U.S. officials, an elderly nun and two peace activists have admitted breaking into a Tennessee defense facility in 2012 where uranium for atomic bombs is stored. Yes Extinction – AT: No Risk Nuclear terrorism is probable – new report Burns, AP, 1-8-14 [Robert, “The Dangerous Weak Link in Nuclear Security,” http://www.realcleardefense.com/articles/2014/01/08/the_dangerous_weak_link_in_nuclear_s ecurity_107023.html] The number of countries possessing the makings of a nuclear bomb has dropped by almost onequarter over the past two years, but there remain "dangerous weak links" in nuclear materials security that could be exploited by terrorist groups with potentially catastrophic results, according to a study released Wednesday.¶ The study by the Nuclear Threat Initiative said Mexico, Sweden, Ukraine, Vietnam, Austria, the Czech Republic and Hungary have removed all or most of the weapons-usable nuclear materials on their territories since 2012.¶ That has reduced the number of countries with one kilogram or more of weapons-usable nuclear materials, such as highly enriched uranium, to 25 from 32 two years ago, the study said. The Nuclear Threat Initiative is a private, non-partisan group that advocates reducing the risk of the spread of nuclear weapons.¶ "That's a big deal," said Page Stoutland, vice president of the group's nuclear materials security program. "Getting rid of the materials is one less country where somebody could potentially steal weapons-usable material."¶ Among the 25 countries with weapons-usable nuclear materials, the study ranked Australia as having the best nuclear security arrangements, followed by Canada, Switzerland, Germany and Norway. The U.S. was ranked No. 11. The weakest nuclear security is in Israel, Pakistan, India, Iran and North Korea, according to the study, which assessed factors such as accounting methods, physical security and transportation security.¶ The drop in the number of countries possessing such materials could be seen as modestly encouraging for President Barack Obama's declared ambition to lock down all of the world's highly enriched uranium and plutonium -- the building blocks of a nuclear weapon. There are an estimated 1,400 tons of highly enriched uranium and almost 500 tons of plutonium stored in hundreds of sites around the world.¶ The report said a significant portion of these materials is poorly secured and vulnerable to theft or sale on the black market. Relatively small amounts of highly enriched uranium or plutonium are required to build a nuclear bomb, which is a declared ambition of terrorist groups such as al-Qaida.¶ "The result of a nuclear blast at the hands of terrorists or a rogue state would be catastrophic -with dire consequences that would stretch across the globe for economies, commerce, militaries, public health, the environment, civil liberties and the stability of governments," the report said.¶ The Obama goal, first proclaimed in 2009, will be the focus of a summit meeting of world leaders in the Netherlands in March. And although concern about the security of nuclear materials is generally directed at Iran, North Korea and Pakistan, the study released Wednesday said the United States has its own vulnerabilities.¶ It cited two recent incidents in the U.S. that point up imperfections in U.S. control of nuclear weapons materials, including a July 2012 break-in by anti-war protesters at the Y-12 complex in Oak Ridge, Tenn., that stores the nation's supply of weapons-grade uranium, makes nuclear warhead parts and provides nuclear fuel for the Navy.¶ The study by the Nuclear Threat Initiative also cited the firing in October of the No. 2 commander of U.S. Strategic Command, which is in charge of nuclear war planning and would operate nuclear weapons if a president ordered their use. Vice Adm. Tim Giardina was fired amid allegations of involvement with counterfeit gambling chips -- an allegation that raises questions about the potential corruption of nuclear secrets. Giardina has been under investigation by the Naval Criminal Investigative Service; results have not been released.¶ The Giardina matter, combined with the break-in at Oak Ridge, suggests that "it is dangerous and inappropriate" to take the security of U.S. nuclear materials for granted, the Nuclear Threat Initiative study said. Yes a threat. Chibarirwe, Trumpet, 7-7-13 [Anthony, “IAEA Chief Warns of Threat of Nuclear Terrorism” http://www.thetrumpet.com/article/10787.19.0.0/world/terrorism/iaea-chief-warns-of-threatof-nuclear-terrorism] At a conference on enhancing global nuclear security efforts, the director general of the United Nations International Atomic Energy Agency (iaea), Yukiya Amano, warned of the possibility of terrorist attacks involving radioactive material. The conference, held at the organization’s headquarters in Vienna last Monday, was attended by over 1,300 delegates from 120 countries and 20 international and regional organizations. Amano’s chief concern was the potential use of a crude nuclear device—a “dirty bomb,” as it’s often called. Such a bomb may not necessarily be a weapon of “mass destruction” but rather of “mass disruption.” Experts believe dirty bombs are much more likely to be detonated than actual nuclear bombs because of the relative ease in obtaining radioactive materials. How serious is the threat of crude radioactive bombs? To answer that question, Amano referred to a foiled smuggling and trafficking incident in Moldova two years ago. The smugglers had tried to avoid detection by using special radiation shields, showing “a worrying level of knowledge.” The case ended well, but “unfortunately,” said Amano, “we cannot be sure if such cases are just the tip of the iceberg.” Every year, the iaea receives hundreds of reports of thefts and unauthorized activities involving radioactive materials. While there hasn’t yet been a terrorist attack involving nuclear bombs or dirty bombs, Amano cautioned: “[T]his must not lull us into a false sense of security. If a ‘dirty bomb’ is detonated in a major city, or sabotage occurs at a nuclear facility, the consequences could be devastating. The threat of nuclear terrorism is real, and the global nuclear security system needs to be strengthened in order to counter that threat.” George Moore, a senior iaea analyst from 2007 to 2012, noted that “many experts believe it’s only a matter of time before a dirty bomb or another type of radioactive dispersal device is used, with some expressing surprise that it hasn’t happened already.” The destruction and disruption that could be caused by dirty bombs can be seen in the fairly simple pressure cooker bombs that paralyzed Boston in April. As our article “Death by a Thousand Cuts” noted, the Boston bombing cost three lives as well as hundreds of millions of dollars. Makeshift radioactive bombs could be similarly costly. Cleaning up nuclear contamination could take months, and for some buildings, decontamination could be a greater challenge than to destroy and rebuild. As unpleasant as this reality is, the fact of the matter is that the world remains vulnerable to nuclear terrorism, and the United States, Britain and Israel face the greatest risk. These nations have enemies determined to destroy them, or at least cripple them structurally or economically. Some of these foes are undeterred by religion, morals or death. For some, what they perceive happening after death actually motivates them. [Tom note- Citing IAEA director general and SENIOR IAEA analyst] Yes Extinction – AT: Safeguards Even the 2010 Summit regulations fail- increased security and culture shift is key Harrell, Associate at the Project on Managing the Atom at Harvard University’s Belfer Center for Science and International Affairs, 3-24-14 [Eben, “We’re Not Prepared for a Nuclear Heist,” TIME, http://time.com/33802/were-notprepared-for-a-nuclear-heist/, 3-24-14] How did an 82-year-old nun come so close to getting her hands on highly enriched uranium?¶ In September 2009, a group of masked men armed with automatic weapons and explosives arrived on the roof of a cash depot in Vastberg, Sweden in a helicopter. The men blasted their way through a skylight and hoisted millions of dollars up to the hovering aircraft — the operation took less than 20 minutes. When police rushed to respond they discovered a bag with the word “bomb” at their heliport — a diversion planted by the thieves — and caltrops (road spikes) near the depot to slow down their response on the ground. While many of the thieves were caught after an investigation, most of the money was never recovered.¶ The Vastberg heist was not a nuclear event, but a new report from my colleagues at Harvard University makes the case that the incident should have deeply troubling implications for the leaders from over 50 countries convening in the Netherlands on March 24-25 for a summit on nuclear security. The stark truth is that many locations around the world that store highly enriched uranium (HEU) and plutonium — the essential ingredients of nuclear weapons — would not be able to repel an attack from adversaries using tactics and weapons as sophisticated as those used by the Vastberg thieves. An amount of plutonium that would fit in a soda can would be enough for terrorists to construct a crude nuclear bomb capable of reducing the heart of a major city to rubble (it wouldn’t require much HEU, either). Today, there are approximately 1440 tons of HEU and 500 tons of separated plutonium in hundreds of buildings in dozens of countries around the world; the theft of only .001 percent of this stockpile could lead to hundreds of thousands of deaths.¶ Categorizing nuclear terrorism as the gravest global security threat, President Obama convened the first biennial Nuclear Security Summit in 2010 as part of a fouryear goal to secure all vulnerable nuclear materials worldwide. By elevating the issue of nuclear security to the level of presidents and prime ministers, the summit process resulted in indisputable successes. Four years later, the report by Harvard points out, many countries have strengthened their rules and procedures for securing nuclear materials, and 13 countries eliminated all the HEU or separate plutonium on their soil entirely, including, thank god, Ukraine (you really don’t want HEU hanging around in a country on the verge of war). For these and other reasons, the summits have made the world a safer place.¶ Nonetheless, every country that still has nuclear weapons, plutonium or HEU has more to do to ensure these items are effectively and lastingly secured — including the United States. Some facilities still require physical enhancements, such as more armed guards, physical barriers, and so on. Others have only minimal protections against insiders stealing nuclear material or sabotaging facilities. In most cases, the biggest obstacle remains security culture. All the bells, whistles and hairtrigger seismic detectors in the world won’t make a difference if security personnel are not vigilant. The Harvard report quotes Eugene Habiger, former security czar at the U.S. Department of Energy: “good security is 20% hardware and 80% culture.”¶ In the U.S. in 2012, an 82-year old nun and two other peace protestors broke into Y-12, a facility in Tennessee that contains the world’s largest repository of highly enriched uranium (HEU) in metal form and until the incident was colloquially known as “the Fort Knox of HEU” for its state-of-the-art security equipment. The nun bypassed multiple intrusion-detection systems because faulty cameras had not been replaced and guards at the central alarm station had grown weary of manually validating sensors that produced frequent false alarms. When the protestors started hammering on the side of a building that contains enough HEU for hundreds of weapons, the guards inside assumed the noise was coming from construction workers that they had not been told were coming. She and her fellow protestors were eventually challenged by a single guard. Terror Adv – Yes Bioterror Terrorists could have bioweapons James Kirkup, 13 (Deputy Political Editor, 3-26-2013, "Biological attacks 'getting easier for terrorists'," Telegraph.co.uk, http://www.telegraph.co.uk/news/uknews/terrorism-in-theuk/9955007/Biological-attacks-getting-easier-for-terrorists.html, accessed 7/8/15, SM) Charles Farr, the Director of the Office for Security and Counter-Terrorism, said that extremists have ever greater access to the information and technology required to create and spread germ agents or other biological weapons. He spoke as an official assessment suggested that countering the threat to the UK from international terrorism is becoming harder and more expensive. The Home Office has published an annual report on its Contest counter-terrorism strategy, which warned that Islamic terrorist threats are now spread more widely across the world, requiring “very significant resources” to combat. The report showed that security officials and intelligence agencies believe that a priority for Britain is improving its ability to detect biological attacks, treat victims and decontaminate attack sites. “Biological will get easier from a terrorist point of view,” Mr Farr said. Related Articles Republican terrorists claim car bomb was meant for G8 summit 25 Mar 2013 MI5 chief to step down, Theresa May says 25 Mar 2013 Car bomb found near Lough Erne G8 venue 23 Mar 2013 Major terror attack on scale of 7/7 foiled every year in UK, police reveal 21 Mar 2013 Syria opposition demands protection from Patriot shield 26 Mar 2013 Factors facilitating such attacks include the availability of formulae and other information on the internet; increasing teaching of biological sciences at universities, and “greater availability of technology,” he said. Mr Farr, a former MI6 officer, declined to give further details of the threat, but the Home Office report hints at a range of new precautions. Last year, the Home Office began enforcing a new list of controlled biological agents to “ensure that dangerous pathogens and toxins that are required in important medical and scientific research are used and held securely.” Lessons learned from the security operations for the London Olympic Games have “informed the wider programme of planning for high impact biological attacks,” the report said. The Home Office report also said that British authorities continue to plan for a Mumbai-style attack by terrorist gunmen. In particular, the emergency services have been working on plans to treat and extract casualties from an attack scene even while violence continues. Details are secret, but it is believed that special teams of armed police officers and volunteer paramedics have been trained to operate under fire. Mr Farr also revealed that even as officials prepare for such attacks, the counter-terrorism budget is coming under pressure to make cuts. Security and intelligence agencies are having to “find savings” to fund the battle against al-Qaeda, he said. In some cases, that means reducing manpower. The warnings about the money available for counter-terrorism come as ministers discuss a Spending Review that is likely to impose more cuts on the Home Office budget after the next general election. Danny Alexander, the Chief Secretary to the Treasury, told the Daily Telegraph last week that the Home Office could not be spared cuts in the 2015/16 round. The Home Office report on British counterterrorism warned that the UK faces a more complicated and widespread threat, which is more costly to address. “The terrorist threats we face are now more diverse than before, dispersed across a wider geographical areas, and often in countries without effective governance,” it said. “This poses significant challenges to our national security and to the security and intelligence agencies and departments working on counter-terrorism: operating in these areas is difficult and dangerous, requires very significant resources and is complicated and at times made impossible by the breakdown of governance and law and order.” Mr Farr said that the changing nature of the threat puts new financial pressure on the Home Office and other agencies. “It takes more to do the same amount of counter-terrorism work,” he said. “We have to find savings.” He added: “Across the whole of the CT budget, which is in the region of £1 billion, you would expect to find some efficiency savings. Technology means that in some areas, you can do the same with fewer people.” The Home Office report also warned that British Muslims fighting in Syria’s civil war could return home to carry out terrorist attacks. 2ac Answers AT: T – Geography Domestic surveillance means surveillance of US citizens. Unegbu, Howard University JD candidate, 2013 [Cindy, 57 How. L.J. 433, “NOTE AND COMMENT: National Security Surveillance on the Basis of Race, Ethnicity, and Religion: A Constitutional Misstep” Lexis, accessed 7-6-15, TAP] Recently, the government has been granted a broad authority to monitor domestic individuals for purposes of national security without requiring any suspicion of criminal or terrorist activity. 73Link to the text of the note Many counterterrorism authorities have addressed monitoring procedures; 74Link to the text of the note however, two specific laws are gaining much criticism--the NCTC and [446] the FBI Domestic Investigations and Operations Guide (DIOG). These authorities are discussed and analyzed below. AT: Terror Talk No link, root cause, or epistemological problem with the aff – the aff does not replicate bias against Muslims or Middle Eastern communities BUT DOES solve based on statistics. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] Notably, the argument that Muslims and Middle Easterners are in the best position to provide accurate intelligence on terrorist activities within their respective communities risks fueling the government's conflation of those communities with terrorism. 122Link to the text of the note However, in analyzing how best to procure counterterrorism intelligence, it would be amiss not to recognize the FBI's and other law enforcement agencies' heavy focus on Muslim and Middle Eastern communities. This is largely due to most recognized foreign terrorist organizations being based out of the Middle East or having Islamic ties. 123Link to the text of the note Law enforcement efforts, immigration law, surveillance policies, and pre-9/11 incidents like the 1993 attack on the World Trade Center have categorized the typical terrorist as male, Middle Eastern, and devoutly Muslim. 124Link to the text of the note The reality is that even though recently immigrated Muslims and Middle Easterners have become synonymous with terrorism, terrorists come from various ethnicities, religions, and communities. 125Link to the text of the note While acknowledging and attempting not to replicate that stereotype, this Comment seeks to recommend ways to improve the relationship between law enforcement and potential terrorism informants who typically belong to the same religion or ethnicity as those they surveil. The government's focus on Muslim and Middle Eastern communities as potential breeding grounds for terrorist groups also directs the focus of this Comment. However, this Comment resists the broad characterization of these communities as prone to extremism and violence. In fact, a recent statistical analysis of terrorism activity after 9/11 discredits the stereotype that Muslims and Middle Easterners account for most of the terrorism within the United States. 126Link to the text of the note In total, the report found that U.S.-originated non-Muslims accounted for 107 post-9/11 plots while U.S.-originated Muslims accounted for 49. 127Link to the text of the note Conversely, the report found that cooperation with Muslim communities helped prevent 40 percent of all Al-Qaeda plots after 9/11. 128Link to the text of the note As the report notes, "[a] singular focus on Muslim terrorists is both bad for national security and civil society … . Numerous studies and experts have stated that there is no reliable [255] "terrorist profile.'" 129Link to the text of the note When compared to the actual threat posed by members of Muslim and Middle Eastern communities, then, the FBI's explicit target of Muslim and Middle Eastern communities is excessive. AT: Speaking for Others Representations are key to transform consciousness Spivak ’95 (Gayatari Chakravorty Spivak, a University Professor at Columbia University where she is a founding member of the school's Institute for Comparative Literature and Society, “Can the Subaltern Speak?” http://www.mcgill.ca/files/crclaw-discourse/Can_the_subaltern_speak.pdf, Published in December of ‘95 dawg, Accessed July 9th 2015, CMT) If this is, indeed, Deleuze’s argument, his articulation of it is problematic. Two senses of representation are being run together: representation as ‘speaking for’, as in politics, and representation as ‘re-presentation, as in art or philosophy. Since theory is also only ‘action’, the theoretician does not represent (speak for) the oppressed group. Indeed, the subject is not seen as a representative consciousness (one re-presenting reality adequately). These two senses of representation — within state formation and the law, on the one hand, and in subject-predication, on the other — are related but irreducibly discontinuous. To cover over the discontinuity with an analogy that is presented as a proof reflects again a paradoxical subject-privileging. ^12 Because ‘the person who speaks and acts… is always a multiplicity’, no ‘theorizing intellectual… [or] party or… union’ can represent ‘those who act and struggle’ (FD, p. 206)? These immense problems are buried in the differences between the ‘same’ words: consciousness and conscience (both conscience in French), representation and re-presentation. The critique of ideological subject-be effaced, as can the active theoretical practice of the ‘transformation of consciousness’. The banality of leftist intellectuals’ lists of self-knowing, politically canny subalterns stands revealed; representing them, the intellectuals represent themselves as transparent. If such a critique and such a project are not to be given up, the shifting distinction between representation within the state and political economy, on the one hand, and within the theory of the Subject, on the other, must not be obliterated. Let us consider the play of vertreten (‘represent’ in the first sense) and darstellen (‘represent’ in the second sense) in a famous passage in The Eighteenth Brumaire of Lous Bonaparte, where Marx touches on ‘class’ as a descriptive and transformative concept in a manner somewhat more complex than Althusser’s distinction between class instinct and class position would allow. AT: Legalism/Legal Reform Good The USA Freedom Act is a key component to providing civil liberties to all citizens Black ’15 (Edward J. Black, Mr. Black received his Bachelor of Arts degree from Muhlenberg College and his Juris Doctor degree from the American University Washington College of Law where he won honors in the area of international law, “Congress to Vote on Surveillance Reforms After Misuse”, HuffingtonPost.com, http://www.huffingtonpost.com/edward-j-black/congress-to-vote-onsurve_b_7342718.html, Published May 21 2015, Accessed July 8th 2015, CMT) The damage wrought by the government's overreach to the fundamental trust between tech companies and their users will be difficult to reverse, but it must start with reform of the mass surveillance programs and improved transparency and oversight. Fortunately, the Senate now has an opportunity to speak definitively on the future of the NSA's mass collection of metadata. A broad coalition of civil liberties groups, technology companies, and trade associations, including my own, have publicly agreed the USA FREEDOM Act is the right first step on the path towards reforming the U.S. government's surveillance practices. The USA FREEDOM Act ends the government's bulk collection of call records and includes substantial oversight and transparency mechanisms designed to ensure that domestic surveillance agencies and programs are held accountable. At its core, the bill requires government access to call data for intelligence purposes to be targeted and limited, rather than all-encompassing. USA FREEDOM also provides for a civil liberties advocate to appear before the secret FISA courts that authorize surveillance programs. Lastly, the bill allows companies that receive data requests from the NSA to combat misperceptions by reporting the kind and quantity of those requests with more detail, while respecting national security concerns over excessive disclosure. When dealing with secret law and intelligence authorities, there are inherent risks for overreach, as recognized in the recent appellate court decision regarding the bulk call records collection program. Pressure for, perhaps well-intentioned, but expansive interpretations of limited authorities are inevitable when law is made in the shadows. As such, there can never be enough light shed on such processes. While the USA FREEDOM Act does much to improve public oversight over the government's surveillance authorities, we would welcome further legislative efforts to strengthen the bill's transparency provisions and collection limitations. Notably, because the USA FREEDOM Act's primary goal is to provide reform and address privacy and civil liberties concerns, it explicitly does not include a mandate that companies retain user data for surveillance purposes. Such a requirement, if included by amendment or otherwise, would necessarily undermine the bill's reforms and pose further privacy and security risks to the public given the considerable secrecy surrounding surveillance practices. The United States must set an example in reforming its mass surveillance programs. The longer they remain intact, the greater the opportunity for other governments to cite them as justification for even more invasive programs with fewer checks and balances. Every day we wait leads to further erosions of civil liberties worldwide, and deepens the gulf between the tech industry and its users -with serious economic consequences. The Senate should pass the USA FREEDOM Act and take a critical first step toward preserving the public's civil liberties and restoring trust in both the tech sector and the U.S. government. That trust is necessary for both innovation and the sustained health of the Internet and all it offers citizens and businesses around the world. Legal reform is a successful part of American political culture McCann ’94 (Michael W. McCann, a professor of political science at the University of Washington, “Rights at Work: Pay Equity Reform and the Politics of Legal Mobilization”, Books.Google.com, https://books.google.com/books?id=WtoAayu603kC&printsec=frontcover#v=one page&q&f=false, Published June 25 1994, Accessed July 8th 2015, CMT) The first and perhaps most general factor that deserves recognition is the rich legacy of rightsbased legal reform within modern American political culture. As Scheingold has argued, “most Americans… are responsive to legal symbols… There is a strong current of belief in rights… We believe that politics is and should be conducted in accordance with patterns of rights and obligations” (1974:13; Haskell 1987; Minow 1990). This general legal consciousness was significantly deepened and expanded by the succession of social movements that, since the 1930s, demanded state support for new citizen rights. These movements included above all the battles for worker rights and the civil rights movement, followed by movements advancing the rights of women, the poor, the disabled, homosexuals, the elderly, and consumers, among others. Such struggles not only have benefited their specific constituencies in various degrees, but also in turn created new political openings for subsequent activism around pay equity and other rights (see Tarrow 1983). This is true in several ways. Reforms like the civil rights movement normalize social differences McCann ’94 (Michael W. McCann, a professor of political science at the University of Washington, “Rights at Work: Pay Equity Reform and the Politics of Legal Mobilization”, Books.Google.com, https://books.google.com/books?id=WtoAayu603kC&printsec=frontcover#v=one page&q&f=false, Published June 25 1994, Accessed July 8th 2015, CMT) Most obviously, such earlier movements provided the guiding normative logics for evolving rights claims by many long-marginalized citizens. This “revolution of rising entitlements,” as Daniel Bell once called it, has been driven in particular by claims about race- and gender-based discrimination (see Olson 1984:5–7). Activists whom I interviewed spoke of the enormous debt owed to the civil rights movement as a progressive consciousness raising experience in American history that prepared the way for later struggles. In fact, many activists pointed out that one of the first pay equity rights battles was the Memphis strike by black male sanitation workers in 1968, during which Martin Luther King was assassinated. The more important factor at the mass level, however, is that legal discourses about discrimination, segregation, equal rights, and the like had permeated the general public as well as workplace-specific environments for decades. As a result, officially sanctioned claims to equal rights have become part of everyday understandings and expectations among citizens to an increasingly significant degree.^10 National public opinion polls revealing widespread support for the pay equity idea, once it is explained as a remedy for sex discrimination, provide some confirmation for this claim. ^11 Legal reforms can change social relations for minorities Jolls ’15 (Christine Jolls, the Director of the Law and Economics Program at the National Bureau of Economic Research with a Ph.D in Economics from MIT,” Antidiscrimination Law’s Effects on Implicit Bias” law.yale.ed, http://www.law.yale.edu/documents/pdf/Faculty/Antidiscrimination_Laws_Effec ts.pdf, Last Revised March 31 2015, Accessed July 8th 2015, CMT) For purposes of the present paper, by contrast, the nature of the relationship between implicit bias and the kinds of decisions policed by antidiscrimination law is not important. This is so because the paper’s essential goal is to describe how existing antidiscrimination law – although it has been broadly criticized for not aiming at implicitly biased behavior in any significant way – nonetheless tends to have the effect of reducing implicit bias in important contexts. For this descriptive claim about the effects of current antidiscrimination law on implicit bias to be of interest, it is only necessary that implicit bias be correlated with some actual behavior that we might care about, whether or not this is behavior that antidiscrimination law can directly regulate. What was said just above establishes clearly that the first correlation exists. (Thus, for instance, the evidence suggests that implicit bias is linked to an individual’s general friendliness toward African-Americans or members of other targeted groups. While neither current antidiscrimination law nor any plausible reform of this law could directly regulate such general friendliness, it is nonetheless relevant to learn that existing antidiscrimination law reduces implicit bias and, thus, the pattern of general unfriendliness associated with such bias.) In contrast to the case of existing proposals for reforming antidiscrimination law, an important virtue of the project of this paper is that it is not necessary that implicit bias be correlated with the specific 16 behaviors – such as employment decisions, admissions to educational institutions, and membership or participation in voluntary organizations – that antidiscrimination law policies. Society is self-checking; implicit racism is eliminating itself through diversity (retag if needed) Jolls ’15 (Christine Jolls, the Director of the Law and Economics Program at the National Bureau of Economic Research with a Ph.D in Economics from MIT,” Antidiscrimination Law’s Effects on Implicit Bias” law.yale.ed, http://www.law.yale.edu/documents/pdf/Faculty/Antidiscrimination_Laws_Effec ts.pdf, Last Revised March 31 2015, Accessed July 8th 2015, CMT) Laws regulating discrimination in the workplace are a basic component of American antidiscrimination law and have been the site of many of the existing critiques of the failure of existing doctrines to target implicitly biased behavior.58 But, notwithstanding these critiques, even the simplest feature of such laws – prohibiting certain hiring, firing and promotion practices – will often have the effect of reducing the degree of implicit workplace bias through the simple mechanism of increasing workplace diversity.59 1. Social Science Evidence on the Effects of Diverse Populations A striking set of results in the social science literature on implicit bias demonstrates that diversity in the surrounding population will often shape and affect the degree of implicit bias individuals exhibit. The studies suggest that the others present in an individual’s environment can significantly reduce the degree of implicit bias as measured by the Implicit Association Test (IAT) described above. At a broader level, both these studies and the evidence discussed later in this Part demonstrate the way in which the environment in which individuals find themselves structures and affects the degree of implicit bias such individuals exhibit on the IAT and similar measures. One notable study of the effects of population make-up on implicit bias showed that individuals who were administered an inperson IAT by an African-American experimenter exhibited substantially less implicit racial bias than individuals who were 58 See supra notes 32-37 and accompanying text. 59 “Diversity” is used throughout this paper to refer to an increase in the representation of a traditionally underrepresented group. Theoretically such an increase could make a particular population less “diverse” if this specific population was not initially characterized by the general pattern of underrepresentation; but the usage here, which accords with popular usage, seems workable for purposes of this paper. 20 administered an in-person IAT by a white experimenter.60 In other words, subjects’ speed in categorizing black-unpleasant and whitepleasant (stereotypeconsistent) pairs was closer to their speed in categorizing black-pleasant and white-unpleasant (stereotypeinconsistent) pairs when an African-American experimenter was standing in front of the room than when a white experimenter was standing in front of the room. AT: Topicality The aff is topical – it meets its, domestic surveillance, curtail, and substantial. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] III. Limitations on the FBI's Use of Informants Cromitie demonstrates that the FBI lacks substantial restraints on how it recruits and uses informants. Currently, there are four restrictions on how the FBI recruits informants: (1) internal FBI limitations, (2) constitutional limitations, (3) the entrapment defense and the outrageous government conduct doctrine, and (4) enforcement of nondeportation agreements in plea bargains. Because these limitations have neither curtailed the FBI's mismanagement of informants nor ensured a high degree of accuracy in information obtained, these restrictions have failed to protect both the public from terrorism and informants from abuse. 156Link to the text of the note A. Attorney General Guidelines The Attorney General's Guidelines on FBI Confidential Human Sources 157Link to the text of the note ("Guidelines"), issued in 2006 by the Department of Justice, 158Link to the text of the note are agency guidelines, not regulations, and as such have no binding legal effect. 159Link to the text of the note [259] Much of the problem of FBI informant misuse stems from this fact. The Guidelines outline the rules the FBI should follow in undercover investigations involving informants, which include documenting new informants and recording agreements made. 160Link to the text of the note The Guidelines are also subject to review and modification by the Attorney General in accordance with federal laws, and are afforded great deference by the courts. 161Link to the text of the note The major problems with the Guidelines, however, are that they lack consequences, are not subject to judicial review, and are not followed by agents. 162Link to the text of the note While the Guidelines may have internal consequences 163Link to the text of the note for FBI agents who violate them, they have no meaningful effect beyond internal regulation and cannot be enforced by the public via judicial review. 164Link to the text of the note Judicial review for violations only occurs when criminal prosecutions reveal the FBI's activities in the investigation. 165Link to the text of the note However, the informants in these cases typically remain confidential, and any inquiry into their actions does not extend beyond the handling agent's conduct and the recruitment methods used. 166Link to the text of the note Evidence shows that in many cases, FBI agents fail to follow the Guidelines when recruiting and handling informants. A 2005 study conducted by the Department of Justice Office of the Inspector General found that the FBI did not provide enough support to agents to properly follow the pre-2006 Attorney General Guidelines Regarding the Use of Confidential Informants. 167Link to the text of the note In fact, noncompliance with the guidelines was a problem in 87 percent of the cases the Inspector General reviewed. In particular, agents failed to properly review the suitability of potential informants, properly document informants' illegal activities, and notify informants of their limitations. 168Link to the text of the note Given the high levels of noncompliance and agents' nearly unlimited discretion in extending immigration rewards, agent abuse is likely also high. [260] Immigration rewards appear only once in the Guidelines, yet this single reference exemplifies the impunity with which law enforcement procures informants. The Guidelines state that "no promises or commitments can be made, except by the United States Department of Homeland Security, regarding the alien status of any person or the right of any person to enter or remain in the United States." 169Link to the text of the note The Guidelines also note that informants should receive this information if and when they have any issues regarding immigration status. 170Link to the text of the note While acknowledging that FBI agents may only offer immigration benefits to informants pursuant to DHS's agreement, the Guidelines do not answer the questions raised by this arrangement. Unlike monetary rewards, for which the Guidelines establish a number of rules regarding proper payment procedures and conditions, 171Link to the text of the note it is not clear under what circumstances immigration rewards must be documented and whether they are subject to conditions similar to those of monetary rewards. Their brief appearance in the Guidelines shows the FBI's recognition of immigration benefits as a method to elicit informant cooperation, but details on their use are nonexistent. This absence of information indicates that agents may possess vast discretion when using immigration rewards to recruit informants. It also indicates that executing these rewards is ultimately in the hands of DHS. B. Constitutional Limitations In theory, both the Fourth Amendment and the Due Process Clause of the Fifth Amendment restrict the FBI's use of informants in terrorism investigations. However, neither Amendment has actually limited the Agency's recruitment tactics when dealing with subjects facing immigration-related pressures to serve as informants. The Fourth Amendment's prohibition against unreasonable searches and seizures 172Link to the text of the note does not offer any substantive restrictions on the FBI's use of informants in terrorist investigations. In criminal investigations where the Fourth Amendment does apply, it places few restrictions on the use of information gathered by informants. 173Link to the text of the note To obtain a warrant based on intelligence gathered by an informant, the information must be reliable in establishing the requisite probable cause. 174Link to the text of the note In matters of national security however, the search standard is less stringent than the probable cause standard [261] used in criminal investigations. 175Link to the text of the note In fact, the United States Supreme Court has never held that the Fourth Amendment applies to national security investigations. 176Link to the text of the note In particular, the Foreign Intelligence Surveillance Act of 1978 (FISA) 177Link to the text of the note shields federal agents from standard criminal warrant requirements when carrying out electronic surveillance and searches. The Foreign Intelligence Surveillance Court, a secret court 178Link to the text of the note created by FISA to issue warrants in national security investigations, 179Link to the text of the note only requires probable cause that "the target of the electronic surveillance is a foreign power or an agent of a foreign power." 180Link to the text of the note Hence, because agents do not have to produce evidence of criminal activity before initiating electronic or physical surveillance, they are able to use informants more freely. 181Link to the text of the note Under FISA, the Attorney General can also authorize surveillance for up to a year without court order. 182Link to the text of the note Furthermore, in 1982, President Reagan's Executive Order No. 12,333 identified the FBI as the primary gatherer of domestic intelligence and held that the Attorney General holds the power to carry out warrantless searches and surveil agents of foreign powers. 183Link to the text of the note Executive Order No. 12,333 essentially paved the way for the FBI's use of informants to conduct domestic surveillance of foreign agents, including members of foreign terrorist organizations, without [262] adhering to the restrictions inherent in the use of informants in domestic criminal investigations. In domestic criminal investigations, agents are required by law to corroborate informants' intelligence and credibility before a warrant is issued. 184Link to the text of the note However, under Executive Order No. 12,333, this corroboration is not required in terrorism investigations. 185Link to the text of the note For informants facing deportation and immense pressure to cooperate, these lax warrant requirements remove an important check on the validity of their intelligence. The requirements also give the FBI more opportunities to abuse its power. Although no court has explicitly found Executive Order No. 12,333 constitutional, no court has found it unconstitutional and thus it remains good law. Indeed, the Northern District of Illinois found that FBI reliance on the Order in conducting physical searches for foreign intelligence gathering was reasonable. 186Link to the text of the note AT: S-6 Reform CP – No Solvency – Entrapment CP doesn’t solve the entrapment internal link – it still results in the false production of intelligence because it provides an incentive for intelligence. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] The examples discussed supra in Part II illustrate how the overbroad and indiscriminate use of informants, particularly those recruited with immigration threats or rewards, harms the acquisition of useful information, fails to identify and protect against legitimate threats, chills speech, and encourages ethnic and religious profiling. Immigration law offers less protection to informants than promises of leniency in criminal matters, thus increasing the potential for informants to produce faulty intelligence. Part III, supra, demonstrates that limitations on FBI dealings with informants are practically nonexistent. AT: S-6 Visa Reform CP – No Solvency – Circumvention No solvency – circumvention. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] Reports indicate that no S-6 visas were issued to terrorism informants between 1994 and 2006. 252Link to the text of the note There is also no indication of how many S-6 visas, if any, were processed during this time. The lack of incentives for the FBI to apply for S-6 visas on behalf of informants may be responsible for this. That is, while the prospect of legal permanent residency may be tempting bait for the FBI to dangle in front of potential informants, the bureaucratic process involved in obtaining an S-6 visa is discouraging. 253Link to the text of the note Hence, while the FBI may tout S-6 visas to potential informants, the use of coercive and unapproved [271] threats of deportation is more likely to result in cooperation - with less time, effort, and oversight. Since informants waive their recourses in S-6 visa agreements, the FBI suffers no legal backlash when it fails to fulfill promises made to them. 254Link to the text of the note Essentially, the potential benefits of using the S-6 visa are outweighed by the lengthy process involved, especially if the FBI can circumvent the process or break its promises. In the end, the FBI has no real reason to seek an S-6 visa for an informant. AT: S-6 Visa Reform CP – No Solvency The CP is insufficient to solve – too narrow to solve the aff. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] Changing the S-6 visa program and focusing on the FBI's use of immigration incentives to recruit informants may seem too narrow to appreciably influence national security and community relations. However, the point of this Comment is a narrow one: to showcase one problematic aspect in the way the FBI handles human intelligence. The recommendations here would not fully solve the problems of privacy violations, ethnic and religious profiling, and informant misuse. The use of immigration law and status to leverage informants is not the only way that the FBI recruits informants, and the S-6 visa program would likely remain relatively small even if expanded. However, as previously explained, the proposed changes to the S-6 visa would generate a more transparent system and more fruitful intelligence, and would help ensure the FBI operates within the scope of its power. Individuals pressured to provide intelligence information would have a legitimate chance to receive an S-6 visa, and the FBI would have a greater incentive to stop its overtly coercive recruitment tactics such as deportation threats. AT: Race K – No Root Cause The 1AC is a prerequisite to the alternative – the 1AC posits a critique of the national security state that is a better starting point and explanation for the current manifestations of the impact of the K than the alternative. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] The election of Barack Obama as president in 2008 was said to have ushered in a new “postracial” era, in which racial inequalities were meant to be a thing of the past. African Americans and Muslim Americans placed their hopes in Obama, voting for him in large numbers. But in the so-called post-racial era, the security narrative of hard-working families (coded white) under threat from dangerous racial others has been as powerful as ever. The unprecedented mass deportation of more than two million people during the Obama presidency is one form taken by this post-racial racialized securitization. Over the last two decades, the progressive criminalization of undocumented immigrants has been achieved through the building of a militarized wall between Mexico and the United States, hugely expanding the US border patrol, and programs such as Secure Communities, which enables local police departments to access immigration databases. Secure Communities was introduced in 2008 and stepped up under Obama. It has resulted in migrants being increasingly likely to be profiled, arrested, and imprisoned by local police officers, before being passed to the federal authorities for deportation. Undocumented migrants can no longer have any contact with police officers without risking such outcomes. There is an irony in the way that fears of “illegal immigration” threatening jobs and the public purse have become stand-ins for real anxieties about the neoliberal collapse of the old social contract: the measures that such fears lead to—racialization and criminalization of migrants—themselves serve to strengthen the neoliberal status quo by encouraging a precarious labor market. Capital, after all, does not want to end immigration but to profit from “a vast exploitable labor pool that exists under precarious conditions, that does not enjoy the civil, political and labor rights of citizens and that is disposable through deportation.”66 What brings together these different systems of racial oppression—mass incarceration, mass surveillance, and mass deportation—is a security logic that holds the imperial state as necessary to keeping “American families” (coded white) safe from threats abroad and at home. The ideological work of the last few decades has cultivated not only racial security fears but also an assumption that the security state is necessary to keep “us” safe. In this sense, security has become the new psychological wage to aid the reallocation of the welfare state’s social wage toward homeland security and to win support for empire in the age of neoliberalism. Through the notion of security, social and economic anxieties generated by the unraveling of the Keynesian social compact have been channeled toward the Black or Brown street criminal, welfare recipient, or terrorist . In addition, as Susan Faludi has argued, since 9/11, this homeland in need of security has been symbolized, above all, by the white domestic hearth of the prefeminist fifties, once again threatened by mythical frontier enemies, hidden subversives, and racial aggressors. That this idea of the homeland coincides culturally with “the denigration of capable women, the magnification of manly men, the heightened call for domesticity, the search for and sanctification of helpless girls” points to the ways it is gendered as well as racialized.67 AT: Race K – Binaries DA/Coalitions Good The alternative doesn’t solve the case – the alternative reifies the black white binary which is inadequate in addressing the modern surveillance regime. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] Better oversight of the sprawling national security apparatus and greater use of encryption in digital communication should be welcomed. But by themselves these are likely to do little more than reassure technologists, while racialized populations and political dissenters continue to experience massive surveillance. This is why the most effective challenges to the national security state have come not from legal reformers or technologists but from grassroots campaigning by the racialized groups most affected. In New York, the campaign against the NYPD’s surveillance of Muslims has drawn its strength from building alliances with other groups affected by racial profiling: Latinos and Blacks who suffer from hugely disproportionate rates of stop and frisk. In California’s Bay Area, a campaign against a Department of Homeland Security-funded Domain Awareness Center was successful because various constituencies were able to unite on the issue, including homeless people, the poor, Muslims, and Blacks. Similarly, a demographics unit planned by the Los Angeles Police Department, which would have profiled communities on the basis of race and religion, was shut down after a campaign that united various groups defined by race and class. The lesson here is that, while the national security state aims to create fear and to divide people, activists can organize and build alliances across race lines to overcome that fear. To the extent that the national security state has targeted Occupy, the antiwar movement, environmental rights activists, radical journalists and campaigners, and whistleblowers, these groups have gravitated towards opposition to the national security state. But understanding the centrality of race and empire to national security surveillance means finding a basis for unity across different groups who experience similar kinds of policing: Muslim, Latino/a, Asian, Black, and white dissidents and radicals. It is on such a basis that we can see the beginnings of an effective multiracial opposition to the surveillance state and empire. AT: Race K – Perm & AT: Legalism/Colorblindness The aff may be colorblind BUT the permutation solves – the alternative is not to reject legal reform but to understand that legal reform alone isn’t enough. This answers colorblindness AND legalism. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] Better oversight of the sprawling national security apparatus and greater use of encryption in digital communication should be welcomed. But by themselves these are likely to do little more than reassure technologists, while racialized populations and political dissenters continue to experience massive surveillance. This is why the most effective challenges to the national security state have come not from legal reformers or technologists but from grassroots campaigning by the racialized groups most affected. In New York, the campaign against the NYPD’s surveillance of Muslims has drawn its strength from building alliances with other groups affected by racial profiling: Latinos and Blacks who suffer from hugely disproportionate rates of stop and frisk. In California’s Bay Area, a campaign against a Department of Homeland Security-funded Domain Awareness Center was successful because various constituencies were able to unite on the issue, including homeless people, the poor, Muslims, and Blacks. Similarly, a demographics unit planned by the Los Angeles Police Department, which would have profiled communities on the basis of race and religion, was shut down after a campaign that united various groups defined by race and class. The lesson here is that, while the national security state aims to create fear and to divide people, activists can organize and build alliances across race lines to overcome that fear. To the extent that the national security state has targeted Occupy, the antiwar movement, environmental rights activists, radical journalists and campaigners, and whistleblowers, these groups have gravitated towards opposition to the national security state. But understanding the centrality of race and empire to national security surveillance means finding a basis for unity across different groups who experience similar kinds of policing: Muslim, Latino/a, Asian, Black, and white dissidents and radicals. It is on such a basis that we can see the beginnings of an effective multiracial opposition to the surveillance state and empire. AT: K - General – Social Death Social death can only be understood in the context of surveillance – the condition for the possibility of non-human was the rise of the surveillance state – the 1ac is a necessary starting point for understanding the K, not the alt. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] National security surveillance is as old as the bourgeois nation state, which from its very inception sets out to define “the people” associated with a particular territory, and by extension the “non-peoples,” i.e., populations to be excluded from that territory and seen as threats to the nation. Race, in modern times, becomes the main way that such threats—both internal and external—are mediated; modern mechanisms of racial oppression and the modern state are born together. This is particularly true of settler-colonial projects, such as the United States, in which the goal was to territorially dispossess Indigenous nations and pacify the resistance that inevitably sprang up. In this section, we describe how the drive for territorial expansion and the formation of the early American state depended on an effective ideological erasure of those who peopled the land. Elaborate racial profiles, based on empirical “observation”—the precursor to more sophisticated surveillance mechanisms—were thus devised to justify the dispossession of native peoples and the obliteration of those who resisted. AT: K – General – No Root Cause The critique does not solve the root cause of the modern surveillance state – the history of surveillance is far more complex than the reductionist view of the alternative – that means it fails to solve the case – national security is the most accurate historical explanation of the modern surveillance state. This card EXPLICITLY says whiteness was not the reason for the creation of the modern surveillance state. This card also says the KKK was targeted by surveillance – the K likely cannot explain that. Kundnani, New York University media culture and communication professor, and Kumar, Rutgers University media studies and Middle East studies professor, 2015 [Arun and Deepa, “Race, surveillance, and empire” http://isreview.org/issue/96/racesurveillance-and-empire, accessed 7-11-15, TAP] By 1890, coast-to-coast colonization was effectively complete, with the surviving Native American population consigned to reservations. Thereafter, the priority became the projection of US power further afield, again justified through a racialized understanding of American exceptionalism. As Paul Kramer writes in the context of the US conquest of the Philippines: [T]he war’s advocates subsumed US history within longer, racial trajectories of “Anglo-Saxon” history which folded together US and British imperial histories. The Philippine-American War, then, was a natural extension of Western conquest, and both taken together were the organic expression of the desires, capacities, and destinies of “Anglo-Saxon” peoples. Americans, as AngloSaxons, shared Britons’ racial genius for empire-building, a genius which they must exercise for the greater glory of the “race” and to advance “civilization” in general. Unlike other races, they “liberated” the peoples they conquered; indeed, their expressions of conquest as “freedom” proliferated as the terrors they unleashed became more visible.31 The resistance that Filipinos mounted to American benevolence could then only be seen as an atavistic barbarism to be countered through modern techniques of surveillance and repression. While local police departments within the United States had begun to develop techniques of political surveillance, it was under the US colonial regime in the Philippines that systematic and widespread surveillance of political opponents and the manipulation of personal information as a form of political control was first institutionalized. A unit within the police called the Constabulary Information Section was established in Manila in 1901, founded by Henry Allen, a former military attaché to Tsarist Russia.32 The Constabulary Information Section cultivated hundreds of paid Filipino agents across the country, making it “scarcely possible for seditionary measures of importance to be hatched without our knowledge,” as Allen wrote to President Theodore Roosevelt.33 The techniques of compiling dossiers on dissidents’ private lives, spreading disinformation in the media, and planting agents provocateurs among militants were applied to combating radical nationalist groupings in Manila. Control over information proved as effective a tool of colonial power as physical force. As historian Alfred W. McCoy notes, during World War I police methods that had been tested and perfected in the colonial Philippines migrated homeward to provide both precedents and personnel for the establishment of a US internal security apparatus.… After years of pacifying an overseas empire where race was the frame for perception and action, colonial veterans came home to turn the same lens on America, seeing its ethnic communities . . . as internal colonies requiring coercive controls.34 On this basis, a domestic national security apparatus emerged, with notions of race and empire at its core. From 1917, the FBI and police department red squads in US cities increasingly busied themselves with fears of subversion from communists, pacifists, anarchists, and the ten million German Americans who were suspected of harboring disloyalties. During World War I, thirty million letters were physically examined and 350,000 badgecarrying vigilantes snooped on immigrants, unions, and socialists.35 Concerns over privacy set limits to such surveillance after the war, but with increasing left-wing and right-wing radicalization in the 1930s, President Roosevelt decided to issue a secret executive order that authorized a shift in the FBI’s role from a narrowly conceived law enforcement agency focused on gathering evidence for criminal prosecutions into an intelligence agency. Thereafter, it was dedicated to spying on “subversive” political movements (primarily communists, but also fascists) and countering their ability to influence public debate. This meant the FBI systematically identifying subversives based on “ideological and associational criteria.”36 It also opened the door to the burgeoning counter-subversion practices that the bureau would launch over the following decades. Already during World War II, the FBI was collecting detailed files on suspected communists while Black organizations such as the National Association for the Advancement of Colored People and the Nation of Islam were also surveillance targets.37 At the end of the Second World War, the United States emerged as one of two superpowers on the world stage. Pushing back against the isolationists, Cold War liberals made the case for the establishment of a permanent national security state. According to historian Paul Hogan, the national security mindset that emerged involved a conviction that a new era of total war had dawned on the United States. In total war, the battle was not confined to the front lines but extended to the home front as well, as did the awesome destruction that modern weapons could inflict not only on military combatants but also on industry, urban centers, and civilian populations. Modern war was total war in this sense that modern armies depended on the output of citizen soldiers in farms and factories behind the battle line. In total war all of the nation’s resources and all of its energy and talent had to be mobilized on behalf of the war effort, thereby obliterating the old distinction between civilian and military, between citizen and soldier, between home front and the front line. When American leaders talked about total war they did so in these terms and also in terms that recognized that modern weapons could bring massive destruction from great distances with barely a moment’s notice. In the new age, American leaders would no longer have the time to This was an updating and reworking of the settler-colonial mentality, with the notion of Manifest Destiny being explicitly drawn on in making the case for an exceptional American empire. The notion of the “citizen-soldier” was built upon earlier settler-colonial racialized security narratives. However, American exceptionalism, as it emerged in this period, was based on the premise that the United States was not only unique among other nations and therefore destined to play a leading global role, but also a nation built upon liberal principles. This meant that the centrality of whiteness to the security debate the issue of war or peace or to prepare at a slow pace.38 narrative was muted and less prominent. Even though the white middle-class home was cast as the locus of a privatized notion of self-defense and military preparedness through government civil defense policies and programs,39 the image of the US empire was one of liberalism, inclusivity, and the “melting pot.” The United States sought quite consciously to differentiate itself from past empires as it positioned itself to be one of two hegemons on the global stage. In this context, the existence of Jim Crow segregation was an embarrassment for the ruling class. In 1947, the National Security Act was passed which entrenched “security” as a key element of the postwar order. Every aspect of life—the social, political, intellectual, and economic—was conceived as playing a role in national defense, and a massive security establishment was built up. The 1947 act created the Office of the Secretary of Defense, the Joint Chiefs of Staff, the National Security Council (NSC), and the Central Intelligence Agency (CIA). The National Security Agency (NSA) was formed in 1952, conceived as an organization to carry out the gathering of “signals intelligence.” there was also the integration of corporate America, of universities, of research institutions, and of the media into the machinery of the national security state. The earlier distinctions between the citizen and soldier and between the home front and the battle front were blurred to shore up an imperial system at home and abroad. Surveillance was central to During this period, sustaining and reproducing this system. From the 1940s to the early 1970s, FBI wiretapping and bugging operations focused on a wide range of movements, activists, and public figures. The following list of targets compiled by historian Athan Theoharis gives a flavor of the surveillance and is worth quoting in full: Radical activists (David Dallin, Charles Malamuth, C. B. Baldwin, Frank Oppenheimer, Bertolt Brecht, Thomas Mann, Heinrich Mann, Helene Weigel, Berthold Viertel, Anna Seghers, Bodo Uhse, Richard Criley, prominent liberal and radical attorneys (Bartley Crum, Martin Popper, Thomas Corcoran, David Wahl, Benjamin Margolis, Carol King, Robert Silberstein, National Lawyers Guild, Fred Black), Radical labor leaders and unions (Harry Bridges; United Auto Workers; National Frank Wilkinson), Maritime Union; National Union of Marine Cooks and Stewards; United Public Workers; United Electrical Radio and Machine Workers; Food, Tobacco, Agricultural and Allied Journalists (I. F. Stone, Philip Jaffe, Kate Mitchell, Mark Gayn, Leonard Lyons, William Beecher, Marvin Kalb, Henry Brandon, Hedrick Smith, Lloyd Norman, Hanson Baldwin, Inga Arvad), Civilrights activists and organizations (Martin Luther King, Jr.; Malcolm X; Southern Christian Leadership Conference; National Association for the Workers; International Longshoremen’s and Warehousemen’s Union; CIO Maritime Committee; Congress of Industrial Organizations Council), Advancement of Colored People; March on Washington Movement; Gandhi Society for Human Rights; Elijah Muhammad; Nation of Islam; Stokely Carmichael; H. Rap Brown; Student Non-Violent Coordinating Committee; Alabama Peoples Education Association; Committee to Aid the Monroe Defendants; Southern Conference for Human Welfare; Black Panther Party; Universal Negro Improvement Association; African Liberation Day Committee), The Students for a Democratic Society, Ku Klux Klan, National Committee to Abolish HUAC, Socialist Workers Party, Washington Bookstore Association, Northern California Association of Scientists, Federation of American Scientists, American Association of Scientific Workers, pre–World War II isolationists (Henry Grunewald, Ethel Brigham, John O’Brien, Lillian Moorehead, Laura Ingalls, America First, Jehovah’s Witnesses, Los Angeles Chamber of Commerce), and even prominent personalities (Joe Namath, Harlow Shapley, Edward Condon, Edward Prichard, Muhammad Ali, Benjamin Spock).40 In a bid to shape public opinion, the FBI also launched a mass media campaign in 1946 that released “educational materials” to In the late 1950s, the FBI launched its secret counterintelligence program (COINTELPRO), which used provocateurs and informants to infiltrate communist groups initially, but later widened to include Puerto Rican nationalists, the student movement, the civil rights movement, and Black liberation movements. About 1,500 of the 8,500 American Communist Party members were likely FBI informants in the early 1960s. By the end of the decade, agents who had previously worked in US foreign intelligence were transferring to the burgeoning field of domestic intelligence to spy on radical movements, whether employed by the bureau, military intelligence, or the expanding red squads in local police departments.41 A key part of the FBI’s countersubversion strategy was the manipulation of political activists into committing criminal acts so that they could be arrested and prosecuted. Agents provocateurs working for the FBI cooperative journalists and legislators. initiated disruptions of meetings and demonstrations, fights between rival groups, attacks on police, and bombings. FBI agents also secretly distributed derogatory and scurrilous In an attempt to “neutralize” Martin Luther King, Jr., who, the FBI worried, might abandon his “obedience to white liberal doctrines” (as indeed he did), he was placed under intense surveillance, and attempts were made to destroy his marriage and induce his suicide. In various cities, the FBI and local police used fake letters and informants to stir up violence between rival factions and gangs to disrupt the Black Panther Party.43 In a number of cases, police departments or federal agents carried out the direct assassination of Black Panthers.44 material to police, Congress, elected officials, other federal agencies, and the mass media.42 Terror DA Answers AT: Terror DA – Link Not True View the link to the Terror DA through a skeptical lens – any “success stories” were rigged by the FBI. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] Many argue that tactics like recruiting informants through immigration law and surveilling mosques are necessary to prevent terrorist attacks, and that national security must be the nation's top priority, whatever the cost. These arguments fail to recognize that when informants lack a specific target and direction, the gathered intelligence does not necessarily enhance the nation's security. Instead, the FBI - with little concern for the actual gravity of the original threat posed by the suspect - creates an elaborate terrorism plot for the surveillance targets to participate in. 100Link to the text of the note After 9/11, many individuals who showed no signs of violence or extremism prior to involvement with informants and government-created plots have been prosecuted under terrorism charges. 101Link to the text of the note Until the informants provided the means, these individuals did not have the finances or the proper connections to conceive and carry out these terrorism plans. Although orchestrating these plots makes the FBI's preventative stance appear successful in the public eye, it diverts law enforcement resources from focusing on real targets. AT: Terror DA Racial, ethnic, and religious profiling fails – entrapment produces fabricated information. Stabile, University of California Berkeley School of Law JD, 2014 [Emily, 102 Calif. L. Rev. 235, “COMMENT: Recruiting Terrorism Informants: The Problems with Immigration Incentives and the S-6 Visa” Lexis, accessed 7-12-15, TAP] Since the FBI's post-9/11 establishment of a preventative stance toward terrorism has increased the need for intelligence, the agency has turned to the increased use of immigration law to recruit additional confidential informants. Using the threat of immigration consequences - particularly deportation - to produce terrorism intelligence presents novel problems for both the intelligence gathering process and the informants. Informants recruited in this manner who also lack established ties to foreign terrorist organizations have an enormous incentive to fabricate information to fulfill their end of the agreement and avoid deportation. Recruiting informants via immigration law also affords less protection than recruiting them by offering monetary rewards or reductions in sentencing. Furthermore, the FBI's recruitment tactics encourage ethnic and religious profiling, alienating Muslim and Middle Eastern communities. Although Congress created the S-6 visa classification specifically to induce cooperation from informants in terrorism investigations, the visa is rarely used due to its stringent eligibility requirements for informants. In order for law enforcement to successfully use the S-6 visa program and to encourage the trust of and cooperation from informants, legislative overhaul is needed. An S-6 visa program that emphasizes pre-existing ties to terrorist organizations, increases the availability of S-6 visas, and lowers the barriers to the visas' use will produce counterterrorism intelligence that is more reliable and actionable and provide greater protection for civil liberties and to informants themselves. Mass Surveillance Fail Mass surveillance is fundamentally ineffective at preventing terrorism – three reasons Schneier 15 (Bruce. Bruce Schneier is a renowned security and cryptology technologist, a fellow at the Berkman Center for Internet and Society at Harvard Law School, a program fellow at the New America Foundation's Open Technology Institute, a board member of the Electronic Frontier Foundation, an Advisory Board Member of the Electronic Privacy Information Center, and the Chief Technology Officer at Resilient Systems, Inc. He has testified before Congress and is the author of Data and Goliath. 3-24-2015. “Why Mass Surveillance Can’t, Won’t And Never Has Stopped A Terrorist”. The Daily Digg. http://digg.com/2015/why-mass-surveillance-cant-wont-and-never-has-stoppeda-terrorist. Accessed 7-9-2015. KC) Data mining is offered as the technique that will enable us to connect those dots. But while corporations are successfully mining our personal data in order to target advertising, detect financial fraud, and perform other tasks, three critical issues make data mining an inappropriate tool for finding terrorists. The first, and most important, issue is error rates. For advertising, data mining can be successful even with a large error rate, but finding terrorists requires a much higher degree of accuracy than data-mining systems can possibly provide. Data mining works best when you’re searching for a well-defined profile, when there are a reasonable number of events per year, and when the cost of false alarms is low. Detecting credit card fraud is one of data mining’s security success stories: all credit card companies mine their transaction databases for spending patterns that indicate a stolen card. There are over a billion active credit cards in circulation in the United States, and nearly 8% of those are fraudulently used each year. Many credit card thefts share a pattern — purchases in locations not normally frequented by the cardholder, and purchases of travel, luxury goods, and easily fenced items — and in many cases data-mining systems can minimize the losses by preventing fraudulent transactions. The only cost of a false alarm is a phone call to the cardholder asking her to verify a couple of her purchases. Similarly, the IRS uses data mining to identify tax evaders, the police use it to predict crime hot spots, and banks use it to predict loan defaults. These applications have had mixed success, based on the data and the application, but they’re all within the scope of what data mining can accomplish. Terrorist plots are different, mostly because whereas fraud is common, terrorist attacks are very rare. This means that even highly accurate terrorism prediction systems will be so flooded with false alarms that they will be useless. The reason lies in the mathematics of detection. All detection systems have errors, and system designers can tune them to minimize either false positives or false negatives. In a terroristdetection system, a false positive occurs when the system mistakenly identifies something harmless as a threat. A false negative occurs when the system misses an actual attack. Depending on how you “tune” your detection system, you can increase the number of false positives to assure you are less likely to miss an attack, or you can reduce the number of false positives at the expense of missing attacks. Because terrorist attacks are so rare, false positives completely overwhelm the system, no matter how well you tune. And I mean completely: millions of people will be falsely accused for every real terrorist plot the system finds, if it ever finds any. We might be able to deal with all of the innocents being flagged by the system if the cost of false positives were minor. Think about the full-body scanners at airports. Those alert all the time when scanning people. But a TSA officer can easily check for a false alarm with a simple pat-down. This doesn’t work for a more general data-based terrorism-detection system. Each alert requires a lengthy investigation to determine whether it’s real or not. That takes time and money, and prevents intelligence officers from doing other productive work. Or, more pithily, when you’re watching everything, you’re not seeing anything. The US intelligence community also likens finding a terrorist plot to looking for a needle in a haystack. And, as former NSA director General Keith Alexander said, “you need the haystack to find the needle.” That statement perfectly illustrates the problem with mass surveillance and bulk collection. When you’re looking for the needle, the last thing you want to do is pile lots more hay on it. More specifically, there is no scientific rationale for believing that adding irrelevant data about innocent people makes it easier to find a terrorist attack, and lots of evidence that it does not. You might be adding slightly more signal, but you’re also adding much more noise. And despite the NSA’s “collect it all” mentality, its own documents bear this out. The military intelligence community even talks about the problem of “drinking from a fire hose”: having so much irrelevant data that it’s impossible to find the important bits. We saw this problem with the NSA’s eavesdropping program: the false positives overwhelmed the system. In the years after 9/11, the NSA passed to the FBI thousands of tips per month; every one of them turned out to be a false alarm. The cost was enormous, and ended up frustrating the FBI agents who were obligated to investigate all the tips. We also saw this with the Suspicious Activity Reports — or SAR — database: tens of thousands of reports, and no actual results. And all the telephone metadata the NSA collected led to just one success: the conviction of a taxi driver who sent $8,500 to a Somali group that posed no direct threat to the US — and that was probably trumped up so the NSA would have better talking points in front of Congress. The second problem with using datamining techniques to try to uncover terrorist plots is that each attack is unique. Who would have guessed that two pressure-cooker bombs would be delivered to the Boston Marathon finish line in backpacks by a Boston college kid and his older brother? Each rare individual who carries out a terrorist attack will have a disproportionate impact on the criteria used to decide who’s a likely terrorist, leading to ineffective detection strategies. The third problem is that the people the NSA is trying to find are wily, and they’re trying to avoid detection. In the world of personalized marketing, the typical surveillance subject isn’t trying to hide his activities. That is not true in a police or national security context. An adversarial relationship makes the problem much harder, and means that most commercial big data analysis tools just don’t work. A commercial tool can simply ignore people trying to hide and assume benign behavior on the part of everyone else. Government data-mining techniques can’t do that, because those are the very people they’re looking for. Adversaries vary in the sophistication of their ability to avoid surveillance. Most criminals and terrorists — and political dissidents, sad to say — are pretty unsavvy and make lots of mistakes. But that’s no justification for data mining; targeted surveillance could potentially identify them just as well. The question is whether mass surveillance performs sufficiently better than targeted surveillance to justify its extremely high costs. Several analyses of all the NSA’s efforts indicate that it does not. The three problems listed above cannot be fixed. Data mining is simply the wrong tool for this job, which means that all the mass surveillance required to feed it cannot be justified. When he was NSA director, General Keith Alexander argued that ubiquitous surveillance would have enabled the NSA to prevent 9/11. That seems unlikely. He wasn’t able to prevent the Boston Marathon bombings in 2013, even though one of the bombers was on the terrorist watch list and both had sloppy social media trails — and this was after a dozen post-9/11 years of honing techniques. The NSA collected data on the Tsarnaevs before the bombing, but hadn’t realized that it was more important than the data they collected on millions of other people. Mass surveillance plays a negligible role in initiating successful terrorist investigations Bergen et al 14 (Peter, David Sterman, Emily Schneider, and Baily Cahall. Peter Bergen is the director of the National Security Program at the New America Foundation, where David Sterman and Emily Schneider are research assistants and Bailey Cahall is a research associate. 1-2014. “Do NSA’s Bulk Surveillance Programs Stop Terrorists?” New America Foundation – National Security Program. https://www.newamerica.org/downloads/IS_NSA_surveillance.pdf. Accessed 7-9-2015. KC) Traditional investigative methods initiated 60 percent of the cases we identified. In 5 percent of the cases, a violent incident occurred prior to prevention, and in 28 percent of the cases – involving 62 individuals – court records and public reporting do not identify which methods initiated the investigation. The unclear cases may have been initiated by an undercover informant, a family member tip, other traditional law enforcement methods, CIA- or FBI generated intelligence, NSA surveillance of some kind, or any number of other methods. Additionally, some of these cases may be too recent to have developed a public record large enough to identify which investigative tools were used. In 23 of these 62 unclear cases (37 percent), an informant was involved, though we were unable to determine whether the informant initiated the investigation. The widespread use of informants suggests that if there was an NSA role in these cases, it was limited and insufficient to generate evidence of criminal wrongdoing without the use of traditional investigative tools. NSA surveillance of any kind, whether bulk or targeted of U.S. persons or foreigners, played an initiating role in only 7.5 percent of cases. To break that down further: The controversial bulk collection of telephone metadata appears to have played an identifiable role in, at most, 1.8 percent of the terrorism cases we examined. In a further 4.4 percent of the cases, NSA surveillance under Section 702 of targets reasonably believed to be outside of the country that were communicating with U.S. citizens or residents likely played a role, while NSA surveillance under an unknown authority likely played a role in 1.3 percent of the cases we examined. Metadata collection doesn’t stop terrorism Bergen et al 14 (Peter, David Sterman, Emily Schneider, and Baily Cahall. Peter Bergen is the director of the National Security Program at the New America Foundation, where David Sterman and Emily Schneider are research assistants and Bailey Cahall is a research associate. 1-2014. “Do NSA’s Bulk Surveillance Programs Stop Terrorists?” New America Foundation – National Security Program. https://www.newamerica.org/downloads/IS_NSA_surveillance.pdf. Accessed 7-9-2015. KC) However, our review of the government’s claims about the role that NSA “bulk” surveillance of phone and email communications records has had in keeping the United States safe from terrorism shows that these claims are overblown and even misleading.* An in-depth analysis of 225 individuals recruited by al-Qaeda or a like-minded group or inspired by al-Qaeda’s ideology, and charged in the United States with an act of terrorism since 9/11, demonstrates that traditional investigative methods, such as the use of informants, tips from local communities, and targeted intelligence operations, provided the initial impetus for investigations in the majority of cases, while the contribution of NSA’s bulk surveillance programs to these cases was minimal. Indeed, the controversial bulk collection of American telephone metadata, which includes the telephone numbers that originate and receive calls, as well as the time and date of those calls but not their content, under Section 215 of the USA PATRIOT Act, appears to have played an identifiable role in, at most, 1.8 percent of these cases. NSA programs involving the surveillance of non-U.S. persons outside of the United States under Section 702 of the FISA Amendments Act played a role in 4.4 percent of the terrorism cases we examined, and NSA surveillance under an unidentified authority played a role in 1.3 percent of the cases we examined. Regular FISA warrants not issued in connection with Section 215 or Section 702, which are the traditional means for investigating foreign persons, were used in at least 48 (21 percent) of the cases we looked at, although it’s unclear whether these warrants played an initiating role or were used at a later point in the investigation. (Click on the link to go to a database of all 225 individuals, complete with additional details about them and the government’s investigations of these cases: http://natsec.newamerica.net/nsa/analysis). Surveillance of American phone metadata has had no discernible impact on preventing acts of terrorism and only the most marginal of impacts on preventing terrorist related activity, such as fundraising for a terrorist group. Furthermore, our examination of the role of the database of U.S. citizens’ telephone metadata in the single plot the government uses to justify the importance of the program – that of Basaaly Moalin, a San Diego cabdriver who in 2007 and 2008 provided $8,500 to al-Shabaab, al-Qaeda’s affiliate in Somalia – calls into question the necessity of the Section 215 bulk collection program.5 According to the government, the database of American phone metadata allows intelligence authorities to quickly circumvent the traditional burden of proof associated with criminal warrants, thus allowing them to “connect the dots” faster and prevent future 9/11-scale attacks. Yet in the Moalin case, after using the NSA’s phone database to link a number in Somalia to Moalin, the FBI waited two months to begin an investigation and wiretap his phone. Although it’s unclear why there was a delay between the NSA tip and the FBI wiretapping, court documents show there was a two-month period in which the FBI was not monitoring Moalin’s calls, despite official statements that the bureau had Moalin’s phone number and had identified him.6,7 This undercuts the government’s theory that the database of Americans’ telephone metadata is necessary to expedite the investigative process, since it clearly didn’t expedite the process in the single case the government uses to extol its virtues. Additionally, a careful review of three of the key terrorism cases the government has cited to defend NSA bulk surveillance programs reveals that government officials have exaggerated the role of the NSA in the cases against David Coleman Headley and Najibullah Zazi, and the significance of the threat posed by a notional plot to bomb the New York Stock Exchange. No War Contention No War No war – democracy, trade, and IGOs check conflict escalation Shermer 14 (Michael. Michael Shermer is a journalist and writer, editor for The Skeptic, and contributor to Scientific American. 10-14-2014. “Perpetual Peace”. Scientific American. http://www.scientificamerican.com/article/perpetual-peace/. Accessed 7-8-2015. KC) In their 2001 book Triangulating Peace, political scientists Bruce Russett and John Oneal employed a multiple logistic regression model on data from the Correlates of War Project that recorded 2,300 militarized interstate disputes between 1816 and 2001. They assigned each country a democracy score between 1 and 10, based on the Polity Project, which measures how competitive its political process is, as well as the fairness of its elections, checks and balances of power, transparency, and so on. The researchers found that when two countries scored high on the Polity scale, disputes between them decreased by 50 percent, but when one country was either a low-scoring democracy or an autocracy, it doubled the chance of a quarrel between them. Kant also suggested that international trade (economic interdependency) and membership in international communities (transparency and accountability) reduce the likelihood of conflict. So in their model Russett and Oneal included data on the amount of trade between nations and found that countries that depended more on trade in a given year were less likely to have a militarized dispute in the subsequent year. They also counted the number of intergovernmental organizations (IGOs) that every pair of nations jointly belonged to and ran a regression analysis with democracy and trade scores. Overall, democracy, trade and membership in IGOs (the “triangle” of their title) all favor peace, and if a pair of countries are in the top 10th of the scale on all three variables, they are 81 percent less likely than an average pair of countries to have a militarized dispute in a given year. How has the democratic peace theory held up since 2001? With all the conflict around the world, it seems like peace is on the rocks. But anecdotes are not data. In a 2014 special issue of the Journal of Peace Research, Uppsala University political scientist Håvard Hegre reassessed all the evidence on “Democracy and Armed Conflict.” He stated that “the empirical finding that pairs of democratic states have a lower risk of interstate conflict than other pairs holds up, as does the conclusion that consolidated democracies have less conflict than semi-democracies.” Hegre is skeptical that economic interdependence alone can keep countries from going to war— the “Golden Arches Theory of Conflict Prevention” popularized by Thomas Friedman's observation that no two countries with McDonald's fight—unless their economies are in democratic nations. He wonders, reasonably, if there might be some other underlying factor that explains both democracy and peace but does not suggest what that might be. I propose human nature itself and our propensity to prefer the elements of democracy. Peace is a pleasant by-product. World Wars doesn’t disprove no war – none of the conditions that make modern peace possible existed Weede 4 (Erich. Erich Weede is a professor of sociology at the University of Bonn in Germany, as well as an author and journalist. Fall 2004. “The Diffusion of Prosperity and Peace by Globalization”. The Independent Review (The Independent Review, v. IX, n. 2, Fall 2004, ISSN 1086-1653, Copyright © 2004, pp. 165–186). http://www.independent.org/pdf/tir/tir_09_2_1_weede.pdf. Accessed 7-82015. KC) Before discussing illustrations of the capitalist peace, I should consider a standard historical objection against it. Certainly, economic interdependence, including trade, between the Western powers and the central European powers before World War I was quite strong. Nevertheless, World War I occurred. What does this evidence imply about the capitalist peace in general and about “peace by trade” in particular? First, it reminds us that all macropolitical propositions—and certainly those discussed here— are probabilistic instead of deterministic statements. We should always expect exceptions. Second, “peace by trade” is not the only component of capitalist-peace theory applicable here. Another is “peace among democracies.” The democratic character of Germany and its allies before World War I is debatable. By contemporary standards, even the democratic character of the United Kingdom before World War I is not beyond suspicion because of franchise limitations. So World War I is not a clear exception to the democratic component of the capitalist peace. Third, no one should believe that trade and democracy, or the capitalist peace, suffice to explain the presence or absence of military disputes and war. At most, we can claim that “capitalist-peace theory” summarizes some known pacifying effects, but it does not summarize conflictpromoting variables and their effects (Russett 2003). As quantitative researchers documenting the pacifying effects of democracy and trade have found again and again (for example, Oneal and Russett 1997, 1999; Russett and Oneal 2001), power balances matter, too. Before World War I, the balance of power between the opposing coalitions was fairly even. There were no pacifying preponderance effects. Although one cannot claim World War I to be a case demonstrating the value of capitalist-peace theory, neither does it undermine the theory seriously. It may be argued that the different long-term effects of the settlements of World Wars I and II derive from failure or success in applying a capitalist-peace strategy to the losers of the war. After World War I, France, which determined the peace settlement more than any other nation, failed to promote a capitalist peace. Immiseration and desperation in Germany contributed to Hitler’s ascent to power and indirectly to World War II, in which France had to be saved by its allies. After World War II, the United States pursued a capitalist-peace strategy toward the vanquished and succeeded in making allies out of Germany and Japan. International trade prevents war Weede 4 (Erich. Erich Weede is a professor of sociology at the University of Bonn in Germany, as well as an author and journalist. Fall 2004. “The Diffusion of Prosperity and Peace by Globalization”. The Independent Review (The Independent Review, v. IX, n. 2, Fall 2004, ISSN 1086-1653, Copyright © 2004, pp. 165–186). http://www.independent.org/pdf/tir/tir_09_2_1_weede.pdf. Accessed 7-82015. KC) Fourth, bilateral trade reduces the risk of war between dyads of nations (Oneal and Russett 1997, 1999; Russett and Oneal 2001). As to why trade contributes to the prevention of war, two ideas come to mind. First, war is likely to disrupt trade. The higher the level of trade in a pair (dyad) of nations is, the greater the costs of trade disruption are likely to be. Second, commerce might contribute to the establishment or maintenance of moral capital (Ratnapala 2003), which has a civilizing and pacifying effect on citizens and statesmen. In the context of this article, however, answering the question of why trade affects conflict-proneness or providing the answer with some microfoundation is less important than establishing the effect itself in empirical research. Although some writers have questioned or even rejected the “peace by trade” proposition, their criticisms are not convincing. Beck, Katz, and Tucker (1998) raised the serious technical issue of time dependence in the time-series cross-section data, but Russett and Oneal (2001; see also Oneal 2003 and Oneal and Russett 2003b) responded to the objections raised against their earlier work and demonstrated that those objections do not affect their substantive conclusions. For a while, Hegre’s (2000) study seemed to necessitate a qualification of the “peace by trade” proposition. He found that the pacifying effect of trade is stronger among developed countries than among less-developed countries. More recently, however, Mousseau, Hegre, and Oneal corrected this earlier finding and reported: “Whereas economically important trade has important pacifying benefits for all dyads, the conflictreducing effect of democracy is conditional on states’ economic development” (2003, 300). Gelpi and Grieco (2003) suggested another qualification. In their view, trade no longer pacifies relations between autocratic states. According to Mansfield and Pevehouse (2003), another modification of the “peace by trade” proposition might be required. The institutional setting, such as preferential trade agreements, matters. It is even conceivable that other forms of economic interdependence, such as crossborder investments, exercise some pacifying impact. Foreign direct investment (FDI) certainly promotes prosperity, growth, and democracy (de Soysa and Oneal 1999; de Soysa 2003), but the conceivable pacifying impact of FDI still lacks sufficient empirical investigation. The most radical criticism comes from Barbieri (2002), according to whom bilateral trade increases the risk of conflict. As outlined by Oneal and Russett (2003a, 2003b; Oneal 2003; Russett 2003), her conclusion results from disregarding the military power of nations—that is, their different capabilities to wage war across considerable distances. Should we really proceed on the presumption that war between Argentina and Iraq is as conceivable as between the United States and Iraq or between Iran and Iraq? Of course, trade has no pacifying effect on international relations wherever the risk of conflict is extremely close to zero to begin with. Even this inadequate. Russett and Oneal (2001) refer instead to a Kantian peace, which is composed of three components: the democratic peace, peace by trade, and peace by collaboration in international governmental organizations (IGOs). In their research, the IGO element of the Kantian tripod is the weakest and least robust one. I do not know who invented the term capitalist peace. I have heard it spoken more frequently than I have seen it in print, but in any event it is a felicitous term. handling of the power and distance issue by itself does not suffice to support her conclusions. If the military-conflict variable is restricted to those conflicts that resulted in at least one fatality, then trade is pacifying, whether power and distance are adequately controlled or not. Moreover, Barbieri (2003) herself found some pacifying effect of economic freedom and openness to trade on the war involvement of nations. In spite of the attempted criticism of Russett and Oneal’s findings, the “peace by trade” proposition stands and enjoys powerful empirical support. Another issue also must be considered. Barbieri’s (2002) measures are based on dyadic trade shares relative to national trade, whereas Russett and Oneal’s measures are based on dyadic trade shares relative to the size of national economies. Gartzke and Li (2003) have demonstrated—arithmetically as well as empirically— that trade shares relative to national trade may rise when nations are disconnected from world trade. Nations may concentrate most of their trade on a few partners and remain rather closed economies. If Barbieri’s and Oneal and Russett’s measures of bilateral trade and their effects are simultaneously considered, then Barbieri’s trade shares exert a conflictenhancing effect and Oneal and Russett’s trade dependence exerts a conflict-reducing effect. This finding of Gartzke and Li’s study not only replicates the substantive findings of both main contenders in the debate about trade and conflict, but it remains robust whether one relies on the Oneal and Russett data or on the Barbieri data, whether one includes all dyads or only dyads for which there is some risk of military conflict to begin with. If one is interested in finding out whether more trade is better or worse for the avoidance of military conflict, then it seems more meaningful to focus on a measure that is related to openness at the national level of analysis, as Oneal and Russett (1997, 1999, 2003a, 2003b; Russett and Oneal 2001) have done, than on a measure that may be high for fairly closed economies, as Barbieri (2002) has done. Actually, the pacifying effect of trade might be even stronger than the pacifying effect of democracy (Oneal and Russett 1999, 29, and 2003a, 160; Gartzke 2000, 209), especially among contiguous pairs of nations, where conflict-proneness is greater than elsewhere. Moreover, trade seems to play a pivotal role in the prevention of war because it exerts direct and indirect pacifying effects. In addition to the direct effect, there is the indirect effect of free trade as the consequent growth, prosperity, and democracy reduce the risk of militarized disputes and war. Because the exploitation of gains from trade is the essence or purpose of capitalism and free markets, I label the sum of the direct and indirect international security benefits “the capitalist peace,” of which “the democratic peace” is merely a component.1 Even if the direct “peace by trade” effect were discredited by future research, economic freedom and globalization would still retain their crucial role in overcoming mass poverty and in establishing the prerequisites of the democratic peace. For that reason, I (Weede 1996, chap. 8) advocated a capitalist-peace strategy even before Oneal and Russett (1997, 1999) convinced me of the existence of a directly pacifying effect of trade. An Asian statesman understood the capitalist peace intuitively even before it was scientifically documented and established. According to Lee Kuan Yew, “The most enduring lesson of history is that ambitious growing countries can expand either by grabbing territory, people or resources, or by trading with other countries. The alternative to free trade is not just poverty, it is war” (qtd. in “Survey: Asia” 1993, 24). Great power war is impossible if US responsibly manages foreign relations Ward 14 (Alex. Alex Ward is a specialist on US defense policy and strategy at the Atlantic Council’s Brent Scowcroft Center on International Security. 8-22-2014. “Only US Can Prevent Great Power War.” The Diplomat. http://thediplomat.com/2014/08/only-us-can-prevent-great-power-war/. Accessed 7-8-2015. KC) Although the world currently satisfies Gilpin’s three preconditions, there need not be pessimism. For one, current relations between the United States and China are nowhere near the point where a potential great war between them is possible, and there is no other rivalry nearing that of Washington and Beijing. Second, some of the trends that can cause harm, like rapid technological progress, can also be used to help stabilize the global order. To be sure, technology could be used to curb the desolation brought on by expectedly low water, food, and energy levels. Finally, and most importantly, Gilpin’s guidance is certainly not comprehensive. There are more variables for which to account (i.e. the effect of nuclear weapons) that dictate whether or not a great power war may take place. That said, Gilpin’s framework serves as a good rubric by which to measure the current global climate. By all measures, this is certainly a dangerous time. But Gilpin’s preconditions shouldn’t be misconstrued as predictive or fatalistic. Indeed, the United States, as the hegemon, has the capability (and responsibility) to preserve the international order and lead the world out of this mess. By keeping good relations with partners and allies, deterring adversaries, reversing the perception of its decline, and leveraging technological capabilities for global good, there is a decent chance that the U.S. can make the great-power-war-incubation period fade away. Should the United States not seize this moment, and ensure that China is a responsible partner in the current global system alongside it, then the chance of a great power war cannot be dismissed, however remote. Surveillance Education Key Explicit Education about surveillance key – its prevents oppressive government policies and other strategies fail Doctorow ’13 (June 14th 2013, Cory Doctorow is an activist, and co-editor of the blog Boing Boing - blog focused on politics, The Guardian, “The NSA's Prism: why we should care” http://www.theguardian.com/technology/blog/2013/jun/14/nsa-prism DA:7/8/15 CB) **Edited for Gendered Language The revelations about Prism and other forms of NSA dragnet surveillance has got some people wondering what all the fuss is. When William Hague tells us that the innocent have nothing to fear from involuntary disclosure, it raises questions about exactly what harms might come about from being spied upon. Here are some reasons you should care about privacy, disclosure and surveillance. We're bad at privacy because the consequences of privacy disclosures are separated by a lot of time and space from the disclosures themselves. It's like trying to get good at cricket by swinging the bat, closing your eyes before you see where the ball is headed, and then being told, months later, somewhere else, where the ball went. So of course we're bad at privacy: almost all our privacy disclosures do no harm, and some of them cause grotesque harm, but when this happens, it happens so far away from the disclosure that we can't learn from it. You should care about privacy because privacy isn't secrecy. I know what you do in the toilet, but that doesn't mean you don't want to close the door when you go in the stall. You should care about privacy because if the data says you've done something wrong, then the person reading the data will interpret everything else you do through that light. Naked Citizens, a short, free documentary, documents several horrifying cases of police being told by computers that someone might be up to something suspicious, and thereafter interpreting everything they learn about that suspect as evidence of wrongdoing. For example, when a computer programmer named David Mery entered a tube station wearing a jacket in warm weather, an algorithm monitoring the CCTV brought him to the attention of a human operator as someone suspicious. When Mery let a train go by without boarding, the operator decided it was alarming behaviour. The police arrested him, searched him, asked him to explain every scrap of paper in his flat. A doodle consisting of random scribbles was characterised as a map of the tube station. Though he was never convicted of a crime, Mery is still on file as a potential terrorist eight years later, and can't get a visa to travel abroad. Once a computer ascribes suspiciousness to someone, everything else in that person's life becomes sinister and inexplicable. You should care about dragnet surveillance because it gives cops bigger haystacks with proportionately fewer needles. The 9/11 Commission said that America's spooks had everything they needed to predict the attacks – but it was lost amid all the noise of overcollected data. Since then, the overcollection has gone into overdrive – the haystacks are enormous, but they still have the same number of needles in them. I want my skies safe, just like you – so I want my spooks doing their job well, not simply sucking up all the data in the hopes it it will be useful some day. You should care about surveillance because you know people who can be compromised through disclosure: people who are gay and in the closet; people with terminal illnesses; people who are related to someone infamous for some awful crime. Those people are your friends, your neighbours, maybe your kids: they deserve a life that's as free from hassle as you are with your lucky, skeleton-free closet. You should care about surveillance because once the system for surveillance is built into the networks and the phones, bad guys [People] (or dirty cops) can use it to attack you. In Greece, someone used the police back door on the national phone company's switches to listen in on the prime minister during the 2005 Olympic bid. Chinese hackers used Google's lawful interception back door to hack Gmail and figure out who dissidents talked to. Our communications systems are more secure if they're designed to keep everyone out – and adding a single back door to them blows their security models up. You can't be a little bit pregnant, and the computers in your pocket and on your desk and in your walls can't be a little bit insecure. Once they're designed for surveillance, anyone who can bribe or impersonate a cop can access them. As for Hague: if the innocent have nothing to fear from disclosure, then why did his own government demand an unprecedented system of secret courts in which evidence of UK intelligence complicity in illegal kidnapping and torture can be heard? Privacy, it appears, is totally essential for the powerful and completely worthless for the rest of us. Surveillance education key – its critical to prevent global totalitarianism – three strategies Schneier ’13 (Bruce Schenier Bruce Schneier is an American cryptographer, computer security and privacy specialist, and writer. He is the author of several books on general security topics, computer security and cryptography, The Guardian, “The US Government Has Betrayed the Internet. We Need to Take It Back.”, http://xa.yimg.com/kq/groups/20568679/1893962603/name/2013+09+07-SchneierThe+US+Government+Has+Betrayed+the+Internet.+We+Need+to+Take+It+Back.pdf DA:7/8/15 CB) Government and industry have betrayed the internet, and us. By subverting the internet at every level to make it a vast, multi-layered and robust surveillance platform, the NSA has undermined a fundamental social contract. The companies that build and manage our internet infrastructure, the companies that create and sell us our hardware and software, or the companies that host our data: we can no longer trust them to be ethical internet stewards. This is not the internet the world needs, or the internet its creators envisioned. We need to take it back. And by we, I mean the engineering community. Yes, this is primarily a political problem, a policy matter that requires political intervention. But this is also an engineering problem, and there are several things engineers can - and should - do. 9/7/13 The US Government Has Betrayed the Internet. We Need to Take It Back. 2/3 One, we should expose. If you do not have a security clearance, and if you have not received a National Security Letter, you are not bound by a federal confidentially requirements or a gag order. If you have been contacted by the NSA to subvert a product or protocol, you need to come forward with your story. Your employer obligations don't cover illegal or unethical activity. If you work with classified data and are truly brave, expose what you know. We need whistleblowers. We need to know how exactly how the NSA and other agencies are subverting routers, switches, the internet backbone, encryption technologies and cloud systems. I already have five stories from people like you, and I've just started collecting. I want 50. There's safety in numbers, and this form of civil disobedience is the moral thing to do. Two, we can design. We need to figure out how to re-engineer the internet to prevent this kind of wholesale spying. We need new techniques to prevent communications intermediaries from leaking private information. We can make surveillance expensive again. In particular, we need open protocols, open implementations, open systems - these will be harder for the NSA to subvert. The Internet Engineering Task Force, the group that defines the standards that make the internet run, has a meeting planned for early November in Vancouver. This group needs to dedicate its next meeting to this task. This is an emergency, and demands an emergency response. Three, we can influence governance. I have resisted saying this up to now, and I am saddened to say it, but the US has proved to be an unethical steward of the internet. The UK is no better. The NSA's actions are legitimizing the internet abuses by China, Russia, Iran and others. We need to figure out new means of internet governance, ones that makes it harder for powerful tech countries to monitor everything. For example, we need to demand transparency, oversight, and accountability from our governments and corporations. Unfortunately, this is going play directly into the hands of totalitarian governments that want to control their country's internet for even more extreme forms of surveillance. We need to figure out how to prevent that, too. We need to avoid the mistakes of the International Telecommunications Union, which has become a forum to legitimize bad government behavior, and create truly international governance that can't be dominated or abused by any one country. Generations from now, when people look back on these early decades of the internet, I hope they will not be disappointed in us. We can ensure that they don't only if each of us makes this a priority, and engages in the debate. We have a moral duty to do this, and we have no time to lose. Dismantling the surveillance state won't be easy. Has any country that engaged in mass surveillance of its own citizens voluntarily given up that capability? Has any mass surveillance country avoided becoming totalitarian? Whatever happens, we're going to be breaking new ground. Again, the politics of this is a bigger task than the engineering, but the engineering is critical. We need to demand that real technologists be involved in any key government decision making on these issues. We've had enough of lawyers and politicians not fully understanding technology; we need technologists at the table when we build tech policy. To the engineers, I say this: we built the internet, and some of us have helped to subvert it. Now, those of us who love liberty have to fix it. Surveillance education key – Its critical to prevent oppression and successfully solve all security risks – Regulation absent education fails Mameli ’08 (Peter A. Mameli, Ph.D. John Jay College of Criminal Justice, Critical Issues in Justice and Politics, Volume 1, Number 1, pages 31-41, “TRACKING THE BEAST: TECHNO-ETHICS BOARDS AND GOVERNMENT SURVEILLANCE PROGRAMS” https://www.suu.edu/hss/polscj/journal/V1N1.pdf#page=41 DA: 7/8/15 CB) Democratic nation-states are experiencing a surge in surveillance programs as a result of terrorist attacks in the United States, Spain and the United Kingdom over the last six years. With the growth of surveillance operations comes a need to ensure that not only the security of the state is protected, but also the civil liberties of the populace. This paper examines methods of accountability, transparency and oversight that can be applied to monitor and control such efforts through heightened cooperation between government surveillance entities and established oversight practitioners. In particular, the primary recommendation made here is for law enforcement organizations across levels of response to consider developing and implementing Techno-Ethics Boards in order to ensure that the ongoing practice of surveillance in a free society can be scrutinized and held to an acceptable standard for a democratic country. Introduction In Thomas Hobbes’ 1651 treatise, “Leviathan,” he examined the condition of man, government and the human spirit. Hobbes’ work and thought lives on today among realist, neo-realist and conservative political thinkers. His ideas are continuously referred to in international relations theories and discourse as a jumping off point for scholars and practitioners alike. Hobbes saw the legitimate power of government as vested in the sovereign, once the commonwealth had agreed to such power transference. The sovereign could then apply their will and power to mitigate a natural world of anarchic behavior among human beings that pitted each against all. This natural world left people in a quandary, facing a myriad of problems within a state of constant war that would impact on survival. Noting among the chief threats: TRACKING THE BEAST: TECHNO-ETHICS BOARDS & GOVERNMENT SURVEILLANCE PROGRAMS 32 “and which is worst of all, continual fear, and danger of violent death; and the life of man, solitary, poor, nasty, brutish, and short.” (Hobbes, 1968, p.186). As the post September 11, 2001 world of New York City and Washington D.C., the post March 11, 2004 world of Madrid, Spain, and the post July 7, 2005 world of London, England show us, democratic nation-states and their people are once again facing fear of violent death in a seemingly anarchic world without rules – and searching for answers to this plight. The current response has been to strengthen an emerging surveillance society in many respects, encouraging wider electronic surveillance techniques, increasing data mining and manipulation, and enhancing profiling and recognition initiatives (see American Civil Liberties Union, 2004, for an example of the experience in the United States). This is Leviathan’s legacy – the beast with a million eyes and ears, threatening a true Hayekian nightmare (Hayek, 1976). But does it need to be so? Enhanced surveillance is considered as warranted by many under the current circumstances, but such practices come with a responsibility (Lyon, 2003). The responsibility to weigh and balance the individual rights of the populace against the security needs of the state. Accomplishing such a goal is complex and multi-faceted. One element of the puzzle to put into place involves establishing accountability and oversight mechanisms that can help create transparency of government run surveillance operations to the public. To date, both discussion of this matter and its implementation have been found wanting. Looking at electronic surveillance one finds a multitude of techniques that are now at the disposal of those in power to monitor and examine both individual and population wide practices (Marx, 2002: pp. 12-13). From closed circuit television (CCTV) to video and computer monitoring, to polygraphs, to data aggregation and manipulation, wiretapping and enhanced eavesdropping methods, a web of surveillance is being woven around people within society (see Muller and Boos, 2004: p. 162, for one such example in Zurich, Switzerland). The impacts are varied, as are the success rates. Regarding advances with technology such as CCTV alone, we find a variety of strengths and weaknesses resulting from application. Clearly, after the London train and bus bombing in 2005, it was obvious that CCTV was invaluable in tracking down terrorists after the attack. The roving monitoring system provided police with quick and effective PETER A. MAMELI 33 tracking evidence that allowed for a swift and capable operational response. This incident should make plain that CCTV has something to offer society, yet all the news about CCTV may not be good. Does CCTV have any preventative capabilities for stopping terrorist attacks before they take place? Or are we simply inundating our surroundings with cameras for the sake of after the fact evidence gathering? If so, at what price to our everyday freedoms are we allowing our fears to push us? Further still, Goold notes that the effect of CCTV on police behavior can be both positive and negative, and that there needs to be a means of ensuring that the police do not interfere with the processes of complex surveillance regimes to protect themselves from charges of misconduct (Goold, 2003: pp. 200201). Muller and Boos also point out that there are a variety of dimensions to consider when reviewing CCTV systems simply for their effectiveness, and that the dimensions and sophistication of CCTV systems can impact on its overall value (2004: pp. 165-171). Given the above questions, many consider it necessary to begin developing means of accountability and oversight that can ensure correct usage of this technology in a way that the public can feel both safe and secure with. And this is only a brief discussion of one type of surveillance system. There are many, with equally weighty concerns to ponder. Ultimately, the question first becomes one of ends. Although there are no doubt those who would disagree, it is assumed here that the purpose of said surveillance is at least intended to be benign, and aimed at protection of both the individual and state despite the negative externalities that may arise. But what are the goals we are seeking to achieve when contemplating managing the growing surveillance world? Is it to control what we are creating so that we strike a balance between security and liberty? Or, are we seeking to give these tools and their users flexibility outside of our oversight capabilities in order to calm our nerves and assuage our fears? Despite the compelling needs associated with protection and security, the only answer that a democratic society can provide is the former. With this position clarified we can then move on to the questions of means. Oversight of Surveillance Programs Central to the discussion of accountability of government surveillance programs is the question of what methods of oversight are at our disposal to ensure surveillance technologies, techniques and results are reasonably controlled and monitored? And more importantly, how can these methods of oversight be implemented productively? For instance: TRACKING THE BEAST: TECHNO-ETHICS BOARDS & GOVERNMENT SURVEILLANCE PROGRAMS 34 ‚ How can auditing of surveillance activities best serve to create public transparency without sacrificing operational secrecy? ‚ How can program evaluations be developed to provide information to elected officials, administrators and citizens as to the success or failure of surveillance efforts without compromising their effectiveness? ‚ Do contracts with independent vendors need to require that their work on building new surveillance systems undergo scrutiny by independent ethics boards familiar with the complexities of the technology? ‚ Should RFPs stipulate that such new efforts take place within frameworks of ethics requirements determined beforehand by numerous entities with expertise in the field in question? ‚ Should deployment and implementation of surveillance tools undergo ongoing scrutiny by entities comprised of internal and external monitors to ensure compliance with acceptable standards and norms of application in a democratic society? Answering these questions, and more, holds the future of this field in the balance. Some of these methods can be used up front (RFPs, contracting requirements and formative program evaluations) and others can appear throughout the life of surveillance operations (performance and financial audits, interim and summative program evaluations, and performance measurement reporting). The problems arise with the willingness and ability to structure these activities into the logic of ongoing surveillance operations across levels of government. Are such oversight activities mandated and expected to happen in regular patterns with regular reporting to elected officials and the public, or simply desired and left to occur at the will of the agencies and oversight bodies involved? It appears that the latter is the case more often than not – and this needs to change. The question is how? To date, hard law and regulation have served as a less than ideal means of managing surveillance activities across levels of government where oversight responsibilities are concerned. While such legal tools hold a necessary place among the approaches to monitoring and controlling such operations after long and detailed public discussion is engaged in (such as developing actual law, and codified rules of practice for established techniques such as wiretapping), it has at times proven PETER A. MAMELI 35 ineffective in certain areas of practice and has required that effective oversight is needed to rectify emerging problems. For one recent example we need look no further than problems the Federal Bureau of Investigation (FBI) has encountered with their surveillance practices. While the USA PATRIOT Act has authorized the use of National Security Letters, essentially administrative subpoenas, by the FBI in investigations of international terrorism and foreign spying (Doyle, 2006), a Department of Justice, Office of Inspector General (OIG) report identified that there was insufficient monitoring of the implementation of this tool by its field offices in the earlier part of this decade. These findings raised questions of impropriety and illegality in the resulting FBI surveillance activities (Associated Press, 2007). It is important that this step was taken by the OIG before waiting for problems to find their way into the court system for settlement through judicial review of administrative operations. And it is just this type of occurrence that points out the weaknesses and openings for abuse that can develop between the development of hard law and regulation and its resulting implementation. In other situations, developers of hard law and regulation can find themselves struggling to offer the insight required to do the job of managing surveillance activities effectively where newer forms of technology are involved. For example, unique expertise that exists among private sector professionals developing technology and innovations within certain fields, such as facial recognition imaging, enables them to operate at such high levels that without commensurate knowledge at their disposal government regulators and elected officials may find themselves challenged to create control mechanisms that are on point. Understanding these shortcomings, a more flexible means of ongoing oversight needs to be sought out that can provide stability as implementation of hard law and regulation requirements are pursued. One approach to managing our growing surveillance society is to heighten flexible governmental regulation and oversight activities through the exploration of what has been termed “soft law” and/or “soft regulation.” Discussions of soft law and soft regulation can be considered as a part of an emerging discussion on the overall value of regulation and governance that has recently come to the foreground (Braithwaite, Coglianese, and Levi-Faur, 2007). Soft law and soft regulation are inexact terms that cover a multitude of quasi-legislative, often non-binding instruments used to enhance government efforts to regulate service delivery areas. These instruments hopefully enable policy changes to emerge and harden TRACKING THE BEAST: TECHNO-ETHICS BOARDS & GOVERNMENT SURVEILLANCE PROGRAMS 36 through voluntary application and adherence in both confrontational and politicized atmospheres where a wide array of players from the public, private and non-governmental sectors are involved (see Brandsen, Boogers and Tops, 2006: p. 550-551; and Mameli, 2000, p. 203-204). Such tools have been referred to broadly as “unofficial guidelines” that deliver information to those being regulated (Brandsen, Boogers and Tops, 2006: p. 546). Some of the instruments that communicate these ideas include codes of governance, quality standards, letters of advice, handbooks, manuals, reports, declarations, recommendations, guidelines and resolutions, to name a few (see Brandsen, Boogers and Tops, 2006: p. 546; and Mameli, 2000, p. 203). The result is hopefully a collaborative effort at ensuring quality service delivery by all parties involved in the process. Sometimes they can even result in the drafting of binding legal agreements after a slow process where policy diffusion is accepted and validated by the players affected. In the case of government surveillance programs construction and delivery of mutually acceptable guidelines for the ongoing management and oversight of these activities would likely enhance their reliability in the eyes of the public. Among the guidelines provided could be agreement to the need for time driven audits and program evaluations, ongoing development of relevant performance measurement indicators, public reporting expectations, and the use of Techno-Ethics Boards to resolve issues of ethical concern while developing advice for carrying out surveillance activities from the beginning of operations through to their conclusion. However, while such an approach promises to relieve problems and pressures that have surfaced with surveillance programs there are quandaries to overcome as well. Quasi-legislative instrumentation of the nature discussed here is voluntarily adhered to and presents an uncertain edict to those on the receiving end. The intent is obvious. The authors believe that others should follow these “suggestions” and upgrade their operations accordingly. Yet there is no mandated action to be taken. These are not new laws or regulatory rules that must be followed, they are something else indeed. Important enough to be taken note of, but ignored at one’s own professional and personal peril (Brandsen, Boogers and Tops, 2006: p. 550-551). Complicating matters further, soft law and soft regulation often suggests that new implementation norms be followed and attested to through self-reporting by the entities that are charged with providing a particular service. Yet given that a gap exists between hard law and regulation and implementation in this sensitive policy area, I PETER A. MAMELI 37 believe such an approach to remedying some of the complications involved may very will find success if crafted carefully. This conundrum frames a central discussion point that needs to be entertained here. How does soft law and soft regulation consistently result in something more than soft, or even abdicated, governance? Even if governance was found lacking before, does this yield a better answer? How can you be sure you have not let the fox guard the henhouse when you are counting on the fox to give you a daily testament to his/her actions? Given this problem, it is important to begin by noting that there are two sides to the coin of soft law and soft regulation. The first side of the coin views the use of such unofficial guidelines as necessary tools to distribute new information to agents perceived as needing to update and improve their services while still creating room for innovative practices to flourish. This view assumes good faith on the part of those being regulated to honestly pursue addressing the suggested course of action, or to offer a better path to follow . The other side of the coin is one where the suggested changes are not implemented due to a lack of comprehension or ability on the part of the receiver, a lack of leverage on the part of the sender, or worst of all, a desire to engage in fraud, waste or abuse by keeping loopholes open and outside eyes closed by one or both (see Brandsen, Boogers and Tops, 2006: p. 547-548 for a nice break out of possible paths regulated parties can take in reaction to unofficial guidelines). Both sides of the coin are relevant aspects of the discussion about the implications these instruments pose for practitioners of soft law and soft regulation in complex environments. In unpacking these concerns it is important to first examine weaknesses that complicate the process, and then note how particular forms of collaborative (rather than adversarial) interaction between oversight entities and those being inspected can improve possibilities for progress through enlightened, triangulated oversight. Next, addressing elements of performance measurement and management that can be used in constructing transparent and accountable partnerships between oversight agents and those being inspected must be further examined. Together, these efforts represent an attempt to stretch the current discourse on regulating new and complex surveillance technologies into less well traveled areas of thought. Considering a role for oversight personnel in government surveillance operations that runs counter to the logic of reaction and punishment that often permeate such discussions, and then offering a tool to build trust between these parties and enhance capacity to achieve success, this framework can hopefully create room for free TRACKING THE BEAST: TECHNO-ETHICS BOARDS & GOVERNMENT SURVEILLANCE PROGRAMS 38 thinking and discussion about soft law and regulation in regard to the surveillance society of the future. Techno-Ethics Boards And Government Surveillance The use of soft law and soft regulation opens doors to programmatic innovation and improvement when constructed well. In practice it can serve to mitigate administrative confusion and folly when implementation of perceived surveillance norms, set out in hard law and regulation, founders due to imprecise understandings of how to accomplish desired ends. However, it is also true that political stressors and unclear messages from central authorities regarding unofficial guidelines can drag down the potential gains of the process by causing those being regulated to stifle innovation and simply toe the line in order to avoid being cited during inspections and oversight – even though these are not clear infractions that they will be called on (Brandsen, Boogers and Tops, 2006: p. 550-551). In such a scenario, the process that should lead to an active interchange of ideas between the center and the periphery that results in continuous improvement only leads to a game of follow the leader, or worse, resistance. Further still, poorly developed unofficial guidelines that do not provide effective problem resolution can also allow for abuse in application by practitioners. We should be striving to shut off the mains that allow illegal activity to flow forward by crafting useful soft law and regulation that also improves results. In the world of surveillance operations such a goal is of great value in and of itself given the threats to liberty, privacy and civil rights that hang in the balance. The question that emerges becomes: How can the relationship between those sending the soft forms of guidance and those receiving it be made to work better? Can we ensure transparency, attain accountability, improve effectiveness, prevent misconduct and enable innovation all at once? And, can individuals charged with overseeing surveillance programs help this development along in a front to back process? The answer seems to boil down to partnership and how to achieve it. If creative interchange between all parties is what is desired, then trust must be created to allow the interchange to flourish. But the trust needs to run through the entire process. Trust must exist in the formulation of the quasi-legislative instruments and advice up front, and then in the oversight process that is created afterward. However, it is hard to create that level of trust when there is resistance to oversight in PETER A. MAMELI 39 sensitive areas of national security (involving surveillance operations, or any other activity). Certainly the recent problems between the United States Central Intelligence Agency and its own Office of Inspector General, where the former challenged the investigative methods of the latter in politically sensitive reviews, attest to this dilemma (Mazzetti and Shane, 2007). Indeed, at the time of this writing the agency has successfully managed to create two new positions to oversee the actions of it’s own internal watchdog (Miller, 2008)! Yet oversight and accountability of national security activities must exist, and so the conundrum surrounding trust is laid bare. One undeniable finding from the CIA’s situation so far is that a lack of trust in oversight operations distracts an organization from accomplishing its mission, at the very least. Therefore, it seems clear that trust needs to be established early on rather than as an afterthought or result of a crisis if government is to function effectively. Trust can be developed in a number of ways at the beginning of the process when advice is crafted and distributed to surveillance practitioners in soft or hard forms. The first model that could be accessed to accomplish this is where the public sector defers to nongovernmental parties from the start in the development of said guidelines (see Brandsen, Boogers and Tops, 2006: p. 552; and, Bernstein and Cashore, 2007 for other examples). This is similar to a model of rulemaking that Weimer refers to as “private rulemaking” (Weimer, 2006: p. 569). It is important to note that the private rulemaking model is different than “negotiated rulemaking,” where external parties engage in the process but don’t control it, or “agency rulemaking,” where experts and advisory boards are only invited in to offer their insight and support (Weimer, 2006: p. 569). Yet while these approaches can create buy-in early that will help to ease relationships in the future, and should also be pursued when developing soft law, it does not fully address the negative reactions to oversight discussed above that follow down the road. Another level of trust needs to be developed in order to get over this hurdle. And, it is incumbent on the personnel charged with such oversight to help facilitate that trust. But how can this be achieved when thinking in the world of inspection is colored by expectations of adversarial relationships, rather than collaborative ones? One way is to explore the creation of a means that will ensure constructive engagement between the parties who could be involved with such a process from front to back. To achieve this purpose I am suggesting developing Techno-Ethics Boards. Akin to Institutional TRACKING THE BEAST: TECHNOETHICS BOARDS & GOVERNMENT SURVEILLANCE PROGRAMS 40 Review Boards (IRBs) in universities, and Bioethics Boards in health settings, Techno-Ethics Boards in law enforcement settings would be charged with advising surveillance practitioners on how to go about implementing hard law and regulation on these matters. They would also be responsible for addressing ongoing questions of acceptable practice that would evolve as technology (and crime) changes. However, different from IRBs, they would not have the ability to prevent the implementation of surveillance programs. Due to the need for security, and the sensitive nature of information that may need to remain protected even from the Board itself, final calls on implementation would still remain with law enforcement personnel directly involved with the activity. Hence, the Board’s oversight of said surveillance operations would still have limits. Yet this additional layer of scrutiny would no doubt aid in clarifying problems and halting preventable errors through the application of soft governance built on soft instrumentation. IRBs have been used within universities for decades in order to protect human and animal subjects from research abuses (Neuman, 2003: p.129). While the protections of subjects and procedures for construction of a Techno-Ethics Board to provide guidance to government surveillance programs might indeed differ from an IRB, it is no doubt a worthwhile enterprise to begin exploring. Could such a body stop abuses from happening where law enforcement is trying to protect national security, but going beyond acceptable norms of practice? If so, it is at least worth the effort to take a hard look at the possibilities for such Boards. Why risk making the error of creating a new type of Stanley Milgram scenario, where both surveillance practitioners and their subjects become victims of overzealous observation efforts, if it can be short-circuited (Singleton, Jr. and Straits, 2005: p. 519)? As with federally mandated IRBs a Techno-Ethics Board would require a spray of appropriate expertise and talent, with a membership of at least five parties (Singleton, Jr. and Straits, 2005: p. 530). My recommendations would include, at a minimum: one lawyer, one ethicist, one technology expert, one oversight expert, and one field practitioner. As with IRB appointments, sensitive demographic information would also need to be taken into account in the development of a Techno-Ethics Board in order to ensure a balance of backgrounds are represented (O’Sullivan, Rassell and Berner, 2007: p. 261). All may come from government circles, or none. However, there are complications that come with including non-governmental entities in security driven operations that makes for a quandary in this regard. It is more likely, given the PETER A. MAMELI 41 information and context that surveillance reviews would take place under, that personnel would need to be drawn from across differing law enforcement agencies (and perhaps levels of government) more so than from outside parties. Regardless of who is chosen to serve however, the goal, of course, would not be to create a confrontational atmosphere but rather a mutually supportive one where professionals concerned with surveillance and its implications could gather to address real world implementation concerns. Surveillance education is key to high school students – they’re a top target of surveillance – three different programs. Burns ’10 (David R Burns is Fulbright Senior Research Fellow, India United States Department of State Bureau of Educational and Cultural Affairs, Associate Professor (with tenure) of Digital Media Art and Animation Southern Illinois University, Conferência Internacional de Artes de Novas Mídias “Borders, surveillance, and control in the digital age” http://bshi.dburns.com/pdf/drburns_softborders.pdf DA: 7/8/15 CB) The US Department of Homeland Security administers the Student and Exchange Visitor Information System (SEVIS) in connection with the US-VISIT program. SEVIS was designed to track and monitor international students before they arrive in and during their stay in the US. SEVIS includes data on close to a million foreign students, exchange visitors, and their dependents that is collected before they enter, when they enter, and during their stay in the US. This information includes “biographical information of the student or exchange visitor and their dependents (name, place and date of birth, spouse and children's data); academic information (status, date of study commencement, degree program, field of study, institutional disciplinary action); employment information (employer name and address, employment beginning and end dates); school information (campus address, type of education or degrees offered, session dates), and exchange visitor program information” (Electronic Privacy Information Center, 2005). This information combined with the personal information collected for obtaining a visa through the US-VISIT program builds a well-defined profile of students and visitors in the US. However, this type of program is not restricted to international students. The US Department of Education has expressed its desire to monitor and track US students. In 2005, the Department of Education released a feasibility report for a national Student Unit Record System to track US students using individually identifiable information such as “name, Social Security Number, date of birth, address, race/ethnicity, gender, and field of study that are attached to an individual student’s record” (Cunningham, A., Milam, J., & Stratham C., 2005). The system would also include academic performance, receipt of financial aid from federal, state, and institutional sources and track students as they move to different institutions (Cunningham, A., Milam, J., & Stratham, C., 2005). The US Department of Education is continuing to develop plans for this student surveillance system that would be accessible to not only to the US Department of Education, but also to the US Attorney General’s office and the US Justice Department for national Borders, surveillance, and control in the digital age David R. Burns 6 security purposes (Electronic Privacy Information Center, 2005). In 2003, the US Department of Defense also began compiling a large-scale student database of personal information for recruiting purposes. The US Department of Defense has proposed that it plans to continue gathering personal information on American students including minors as young as 16 years old. According to the Electronic Privacy Information Center, the database will be “managed by a private direct marketing firm and will include such information as grade point average, ethnicity, and social security number” of each student (Electronic Privacy Information Center, 2005). The US government entering into a large scale marketing agreement and capitalizing on students’ personal information is a new development in the way the government agencies are accessing and controlling their citizens’, including minors’, personal information for non-security related projects. Bogard (2006) comments that control over “access to data on you, but not by you, is the goal of police (corporate, state) control of surveillance networks”. Government’s use of personal student information for marketing purposes is a new development in the way governments are leveraging the formerly private information they collect on citizens of all ages. These three programs, SEVIS, Student Unit Record System, and the DOD database; combined with the US-VISIT program illustrate the creation of a powerful Orwellian surveillance system to track international and US students across and within US borders. The US Department of Homeland Security has already granted the FBI access to SEVIS and US-VISIT (Field, 2004). This new area of collaboration between academic institutions and government agencies to track and monitor students is a critical area to watch for potential abuses of personal privacy. A critical issue to consider is who or what governmental and non-governmental institutions have access to all of the personal information being collected and for what purposes? The US Department of Homeland Security reports that the US-VISIT program “provides biometric identification and analysis services to federal, state and local agencies” (US Department of Homeland Security, 2008). In the past, the US Department of Homeland Security required that airlines and cruise companies report personal passengers’ information to them. If this information is combined with individuals’ credit card information, a more complete profile of each individual becomes clear. Companies like Acxiom collect individuals’ contact information, estimated incomes, home values, occupations, religions, shopping habits and keep records for TransUnion, one of the world’s largest credit reporting agencies. All of this data has been shared with the US government since 9/11 (O’ Harrow, 2005). When this data is combined with information from SEVIS and the Department of Defense databases, government and nongovernment institutions have the potential to create a more complete system that can be used to profile, index, track and monitor individuals. 5. CONCLUSION The tiers of surveillance technology used to monitor, track, and control individuals’ movements within, across and outside borders described in this paper indicate a shift from public and private institutions’ physical control and physical monitoring of individuals to their electronic control and electronic monitoring of individuals. This type of electronic, panopticonal surveillance and control ranges from government satellites, which monitor individuals’ communications, to portable electronic devices, which provide information about individuals’ physical locations, to virtual border controls, which allow institutional border control programs to automatically read individuals’ biometric data. Private and public institutions’ use of these new surveillance technologies has allowed older models of localized, physical controls over individuals within, across and outside of physical borders to be replaced with an electronic, decentralized apparatus of control that transcends physical borders. Public and private institutions’ use of this electronic, decentralized apparatus of control to track individuals’ vehicles, portable electronic devices and biometric data presents potential concerns about individuals’ personal privacy. Public and private institutions are moving toward a ubiquitous, seamless model of surveillance and control that extends beyond tracking and monitoring individuals’ physical movements across international borders to tracking and monitoring individuals’ physical and virtual movements across localized micro-borders such as streets, stores, and homes. This new model relies not only on deterritorialization and biometrics but also on individuals’ electronic identities. In the past, individuals were able to opt out of being monitored and controlled by living without mobile phones, the latest technological gizmos for their vehicles, and traveling across distant physical borders. Now individuals can no longer avoid the gaze of surveillance and prevent the collection of their personal information as they move across localized physical and virtual borders. ****Surveillance education in debate is critical to teach advocacy skills that solve totalitarianism, and the failure of surveillance policies – it is the only way for a public opinion to be formed - Sweden proves. Kullenberg ’09 (Kullenberg, Christopher, PhD, University Gothenburg, His dissertation concerns the statistical social sciences, their epistemic problems and their role in modern societies, and contains a case-study of the SOM-institute, a Gothenburg research center that has been very successful in providing large surveys, "The social impact of IT: Surveillance and resistance in present-day conflicts." How can activists and engineers work together pg. 37-40. http://fiff.de/publikationen/fiff-kommunikation/fk-2009/fiff-ko-12009/fiko_1_2009_kullenberg.pdf DA: 7/8/15 CB) Since the 9/11 attacks the world has been challenged with intrusive legislation upon civil liberties and increased use of surveillance technologies. As this development is proceeding rapidly, both from a legal point of view and the technological side, it takes more than parliamentary politics to pursue a democratic and open discussion about these matters. This is where the civil society, or rather the civil societies, need to collaborate. Thus, I will propose that engineers, software-programmers and people in the private sector of Information Technology could co-operate with activists, human-rights organizations and citizen-journalists in a very productive manner. I will also give tangible examples on how such activities have been pursued in Sweden during a controversy on the role of signals intelligence. Surveillance and war. Issues that keep arising in the backwaters of the “wars” on terrorists, drugs, and trafficking are often complex and require technical and legal expertise, not only to be understood, but more importantly, to be taken seriously in the public debate by the media. In order to avoid laws are passed without a proper debate or that technologies are implemented as merely technical solutions, I will propose that criticism could have a positive task in building a collaborative informational infrastructure, an effective media strategy, and other innovations. Let me give an example from Sweden. During 2008, a law was passed which allowed the government to pursue extensive signals intelligence on the Internet. It was termed the FRA-law in the press, since the authority responsible for signals intelligence is called Forsvarets Radioanstalt [1], which is the equivalent to the NSA in the United States, or the BND in Germany. The FRA was previously only allowed to search and intercept radio traffic, but this new law would allow the authority to intercept all internet traffic , by monitoring so-called “co-operation points” at the Internet Service Providers. By copying all the information passing through the cables, the FRA will be able to extract traffic-data from, the multitude of data, both domestic and international. Consequently, a mode of operation which was developed in the context of the post-war arms race will be transferred to the Internet as this law is effectuated during 2009. However, the Internet is largely used by private and corporate communication, rather than military information, a fact that raises questions concerning privacy, integrity and the rights to private communication. I will argue that if it were not for the active formation of a public, this law would have been passed without resistance or criticism . In order to understand how this works, the notion of a “public” is borrowed from the philosopher John Dewey, who explicitly stresses the importance of communication: “But participation in activities and sharing in results are additive concerns. They demand communication as a prerequisite. /…/ Communication of the results of social inquiry is the same thing as the formation of public opinion .” [2] Crucial to the formation of a participatory public issue, and to allow it to build political pressure, is there free flow of information in the sense that it operates without restrictions, something which is very different compared to traditional theories of mass-communication. This is where the Internet has a very interesting potential since its architecture, at least ideally, promotes participation, sharing and communication, which is precisely what Dewey is asking for. However, it seems that this free flow cannot be guaranteed by the internet alone, since the same abilities can be used for intrusive surveillance. Panspectric Surveillance. How are we then to conceive of contemporary technologies of surveillance? One way is to ask how technologies are used throughout society, by analyzing their performances and abilities in socio-technical assemblages. Digital technologies, besides sharing certain properties in hardware such as microprocessors, electricity-based operations and abilities to process instructions and algorithms, usually share many networked, or social effects. The internet as an assemblage of computers, routers, switches and all kinds of IP-based technologies, such as mobile devices and satellites, shapes emergent forms of effectuation. For example file-sharing, voice-transmission, e-mails etc. are all dependent on interconnectivity. Also, they operate on the potentiality of decentralization and read-write capacities, and on the ability to transfer the analogue world to a digital realm, which we see in the digitalization of images, sounds, and even in the keystrokes of keyboard. There is however a critical paradox built into our mundane technologies. We may use digital cameras on our mundane technologies. We may use digital cameras on our holiday trips and post the images on a blog, but we may also use the same capacities for an IP-based surveillance camera. The present any technologies are this at the same time what may liberate sounds, texts, images and videos from their “material imprisonment” and geographical spatiality, while they simultaneously make possible for what is called panspectric surveillance [3] The concept of panspectrocism comes from philosopher Manuel DeLanda, who situates the origin of these technologies in war. It is worthwhile to quote from his work War in the Age of Intelligent Machines (1991) in length: “There are many differences between the Panopticon and the Panspectron /…/ Instead of positiong some human bodies around a central sensor, a multiplicity of sensors is deployed around all bodies: its antenna farms, spy satellites and cable-traffic intercepts feed into its computers all the information that can be gathered. Thus is then processed through a series of “filters” or key-word watch lists. The Panspectron does not merely select certain bodies and certain (visual) data about them. Rather, it compiles information about all at the same time, using computers to select the segments of data relevant to its surveillance tasks [4].” DeLanada thus argues that the technologies we face in contemporary debates on Internet surveillance, originate in post-war setting which culminated during the cold war. Signals intelligence which culminated during the cold war. Signals intelligence was born in a combination of radio interception, transferring analogue signals to digital information, and computers which calculated patterns, attached meta-data, and filtered out only the relevant pieces of information in a multiplicity of signals. The birth of the panspectric technological framework, at least an abstract sense, this came from warfare. However, it was developed and refined during times when consumer technologies were not yet digital, and usually not even made for two-way communication (TV. Press, radio). What we see today is a complete change of orders. Signals intelligence performed by governments, such as the NSA, the FRA or the BND have entered a territory populated by ordinary citizens, rather than tanks, spy satellites and nuclear weapons. Contemporary panspectric surveillance depends on the interconnectedness of sensors and computational methods such as data mining, sociograms and databases. Sensors include RFID-chips, digital CCTV-cameras, credit cards, mobile phones, internet surveillance etc., and they all have the ability to record an ever increasing part of our everyday lives. This is where we get close to the etymology of the words pan-, which means everything, and spectrum which is the entire range of detectable traces. The radical digitalisation of our societal functions and everyday lives, reconfigures and prolongs the range of surveillance. However, to make sense of this enormous abundance of data, methods of reducing complexity and finding relevant traces are needed. This is where the other pole of panspectrocism emerges; the need for supercomputers and advanced software and statistics. The FRA has bought one of the fastest supercomputers in the world, and it is plugged directly into the central fibre-cables of the Swedish Internet Service Providers. They will consequently receive a copy of all traffic-data, and then process it in several steps in order to find patterns. The problem is, however, that traffic-data (which contains information about with whom, at what time, how frequently etc. we communicate) can say a great deal about you and your life. If we make social network analyses of the meta-data you give off during a normal day, the surveyor can probably find out who most of your friends are, and where you are most likely to be located. With more and more data, the surveyor is able to tell your religion, sexuality, political affiliation and consumer behaviour. Citizen Journalism, Pirate Parties and Activists We can make a tripartite division of activities that may challenge the increasing use of legal and technological means of mass surveillance; citizen journalism, pirate parties and activism. They may sometimes resonate in the same direction, towards a clear goal, but their basic properties and relations are essentially heterogeneous. Issues, such as the FRA-law, can only stir up reactions and become “issues proper” if, following Dewey, there is communication between actors allowing them to react to what is imposed on them . It has been said that the case of the FRA-law was the first time in Swedish history that traditional newspapers lagged the blogosphere, and for the centre-conservative government the force of citizen journalism came as quite a surprise. The blogosphere displayed a few interesting abilities by cooperating and sharing knowledge. One important aspect of raising issues, needed to be accounted for in this case, is speed. Paul Virilio argues in his book Speed and Politics, that: “If speed thus appears as the essential fall out of styles of conflicts and cataclysms, the current arms race is in fact only the arming of the race toward the end of the world as a distance, in other words as a field of action.” [5] Speed turns distance into action, and citizen journalism has a higher velocity than the traditional media, being dependent on printing presses, paid and professional journalists, or hierarchical organisations. During the passing of the FRA-law, the only ones being able to read legal documents, do proper research, and have a constructive discussion, were bloggers. In this case (and I do not want to generalise this observation to be valid for „the media“ in general) we may say that the allocation of resources was much more efficient than that of large media corporations. The critical task for the blogosphere in making a successful attempt at stopping this law is knowledge production. Surveillance technologies and intrusive legislations are complex matters which are often secretive in character. Signals intelligence is maybe an extreme case, since details about methods and search criteria is necessarily kept away from the public. The first step in the case of the FRA was ontopolitical, in the sense that there was (and still is) a struggle to define whether signals intelligence is mass-surveillance, which would be a disaster for integrity, or simply a means to target very few „enemies of society“ (terrorists). Bloggers analysed legal documents and government white papers, as a kind of swarm intelligence, and could argue convincingly that they entailed many legal exceptions for the FRA in registering political opinions, sexual orientation or religious background. The counter-argument from advocates of the law did not convince the bloggers, and the traditional media started covering the issue extensively. During the summer of 2008, there were articles in the newspaper almost every day for months, and many bloggers wrote extensively in both arenas [There’s also a warrant in the card that says speed of conveying information solves, so speed good] High School Students learning about Surveillance is key to solve war and threatconstruction that justifies atrocities Ralston ’14 http://www.global.asc.upenn.edu/app/uploads/2015/04/MiltonWolf-2014-Compendium.pdf#page=41 Increasing state surveillance of the internet and a seeming lack of global accountability and best practices regarding foreign and domestic internet policies demands the attention of students, scholars, and practitioners of media and communication, political science, sociology, computer science, and the like. With these concerns in mind, the 2014 Milton Wolf Seminar highlighted themes of surveillance, visibility, disclosure, and espionage in the digital age. This essay seeks to touch upon some of these themes, and to present a case for the study of ontological security in international relations as a way to explain, in part, U.S. practices of surveillance following the leaks by former National Security Administration (NSA) contractor Edward Snowden. Politically, the stakes are high as cyberpolitics becomes an issue of “high politics” in the study of international relations; states and the agents who produce narratives about the state frame cyber discourse in ways that attempt to justify practices of surveillance, espionage, and censorship. States justify intrusion into cyberspace in the name of stability and an idealized self-image. This, can prove violent and costly, with parallels to justifying war on the basis of empire in offline venues. In cyber venues, the United States in particular has had to justify state intrusion into cyber venues. Void of routinized responses to “traditional” threats, the state must reshape or reconfigure its self-image in order to combat the contradictions inherent in state intrusions into cyberspace. Taking in consideration such concerns and dynamics, this essay first sets out to explain ontological security in the study of international relations and the discursive practices of U.S. state agents in justifying state surveillance practices. It then concludes by drawing parallels between these discursive practices and various presentations at the 2014 Milton Wolf Seminar. Ontological Security in International Relations Theory Physical security concerns dominate realist accounts of security in world politics (Mitzen 2006: 342). Ontological security in international relations goes beyond the premise that states are solely concerned with physical security. The assumption that states only seek physical security, Mitzen (2006: 364) argues, constrains international relations theory by failing to explain why states may seek or continue conflict at the expense of physical security. Inherent in the conception of a state’s ontological security is the notion of the state as person, or at the very least, that states are concerned with their own self-image. 20 Ontological security is about constructing and maintaining the stability of a state’s self-image. Power, in this regard, can be understood in terms 20 See Wendt (2004) for a discussion of the validity and appropriateness of understanding the state as person in international relations theory. 40 of “a centralized body’s internal capacity to perceive its ability to operate upon its own selfimage, as well as influence others and determine outcomes” (Steele 2010: 15). Thus, power is not solely based upon a state’s ability to make other actors do what they would otherwise not do, to pose material threats to other states, or assert global influence; power is about the state’s recognition that it can use and recreate its own self-image. States put forward narratives about themselves through state agents, such as government officials. State actions must be justified, even if they go against the grain of international norms or expectations (Steele 2008: 10). What is particularly interesting about the U.S response to the Snowden disclosures is the manner in which the disclosures were framed, the contradictions that arose as a result of this framing, and how the narratives that the state produced regarding NSA practices harken back to the self-image-making of the U.S. state. Why the United States? When examining speeches made by U.S. state agents, publications regarding U.S. citizenship, and the ways the United States is presented in popular culture, common trends emerge: The United States is presented as exceptional, as a land of shared values-- liberty, freedom, and prosperity—which were created by the nation’s founding fathers. David Campbell (1998: 131) suggests that America is an imagined community “par excellence.” America, like all other states, is dependent upon practices that make up its ontological being. However, as Campbell (1998) argues: Defined, therefore, more by absence than presence, America is peculiarly dependent on representational practices for its being. Arguably more than any other state, the imprecise process of imagination is what constitutes American identity (p. 91). Space and time in reference to U.S. identity is crucial to this analysis because successful fulfillment of ontological state security is predicated upon that state’s ability to maintain a consistent self-identity and self-image. Void of a people as a foundational element, the United States’ self-identity is quite fleeting, and, thus, hinges on representational, symbolic, and iconic imagery in order to ascribe to itself some form of identity (Campbell 1998: 132). The U.S. State Narrative In a speech made prior to Snowden’s disclosures, President Obama spoke of the necessity to secure cyber infrastructure while maintaining the internet as a free and open space: Our pursuit of cybersecurity will not—I repeat, will not include—monitoring private sector networks or Internet traffic. We will preserve and protect the personal privacy and civil liberties that we cherish as Americans. Indeed, I remain firmly committed to net neutrality so we can keep the Internet as it should be—open and free. In light of the Snowden disclosures, a contradiction arises between the actual behavior of the state through its national security agency and the self-image of the state. President Obama sends two distinct and seemingly irreconcilable messages regarding cyberspace: First, the United States, as a centralized power, recognizes the tensions that it must mediate between security and 41 liberty; Second, the United States has a vision for cyberspace, one focused on being “open and free.” But free for whom? U.S. security policy is decentralized insofar as it attempts to do too much while still trying to keep a constant self-image (See Campbell 1998 and Gould and Steele 2014). Cyberspace is not an “American thing,” but from cyberspace comes a multitude of images that only exacerbate the imagined nature of American identity. Thus, what cyberspace is and what cyberspace means, from an American perspective, is inherently American. Addressing the “noise” surrounding the practices of the National Security Administration, President Obama first noted the history of intelligence gathering by the United States: At the dawn of our Republic, a small, secret surveillance committee, born out of the Sons of Liberty, was established in Boston. And the group’s members included Paul Revere. At night, they would patrol the streets, reporting back any signs that the British were preparing raids against America’s early patriots. In order to find footing and precedent in the face of ontological insecurity in cyberspace two rhetorical moves are deployed. First, history is resurfaced and reworked to create a seemingly appropriate metaphor for the present. This history is doused in a patriotic whitewash, whereby particular events are chosen but not others that are perhaps more indicative and relevant to the current situation. Further, the parallels put forward by Obama are not parallels at all; the nature of surveillance, global politics, globalization, and technology are not the same as they were 200 or so years ago. This history serves to maintain the state’s self-image over time. Campbell (1998: 130) notes that the American quasi-war with France “demonstrated how previously established discursive strategies of otherness could be invoked in novel circumstances to provide powerful modes of understanding.” Much in the same way, President Obama’s return to history serves not only to ground justifications for NSA activities in seemingly consistent practices of state surveillance, but also in actions against threats from an “other,” in this case, the British during the Revolutionary War. Threats in cyberspace come from a plethora of sources, including: other states, non-state actors, rogue Americans, or even cyberspace itself. Obama’s second rhetorical move is to argue for American exceptionalism. He goes on to note, But America’s capabilities are unique, and the power of new technologies means that there are fewer and fewer technical constraints on what we can do. That places a special obligation on us to ask tough questions about what we should do. The justification for (at least toned down) policies of NSA surveillance centers on the notion that “someone has to do it,” and “we can do it better than anyone else.” America’s status as “the world’s only superpower,” as President Obama declares, opens itself up for interrogation. At the end of his speech on NSA reforms, President Obama demonstrates, perhaps unintentionally, that ontological insecurity is a powerful motivator for the United States in cyberspace: When you cut through the noise, what’s really at stake is how we remain true to who we are in a world that is remaking itself at dizzying speed. Whether it’s the ability of 42 individuals to communicate ideas, to access information that would have once filled every great library in every country in the world, or to forge bonds with people on the other side of the globe, technology is remaking what is possible for individuals and for institutions and for the international order. This is not to say that the United States consciously and reflexively recognizes its ontological insecurity in its relationship to cyberspace. However, the examples that are raised concerning the dangers of cyberspace—from cyberspace as a mechanism for terrorist mobilization to cyber wars of the future—do not paint an entirely clear picture of what makes cyberspace something truly different in global politics. This shift is not universal, or at least to the same degree, for every state. Cyberspace may provide a vehicle for dissent, organization, etc. for every state, but it burdens states that are fixed in terms of physical security and depend on an idealized self-image. States are pressured into explaining the contradictions that arise as a result of their self-image (freedom, openness, transparence, for example) and state-led intrusions into cyberspace. Foreign Policies of the Internet: Surveillance and Disclosure Revisited The 2014 Milton Wolf Seminar brought to bear, and framed well, this theoretical construction of state ontological security in international relations. In particular, many of the presentations dealt with the critical problematic of the balance that must be struck between state self-interest by way of national security and internet diplomacy, global governance, and transparency. Panelists discussed this problematic in various contexts ranging from state censorship of information, international law, and state sovereignty. The internet, and cyberspace more generally, has very real physical characteristics that are often forgotten in discourses of a “borderless digital world” or the metaphor of the internet as a “cloud.” Indeed, the internet is built upon a physical framework, logical building blocks, and interaction (Choucri 2012); and each of these “layers” carries very real political ramifications. State ontological security in cyberspace, as described above, assumes the structural realities of power in international relations regarding the internet, and seeks to elaborate upon how states, beyond concern for their physical security, come to justify surveillance practices on the internet. In this sense, the Milton Wolf Seminar proved invaluable as practitioners and scholars sought to elaborate upon the role of the internet, censorship, privacy, and surveillance in diverse contexts including the national policies and practices of Russia, South Africa, the United States, China, and Britain. Further, the seminar participants elaborated upon shifting or different physical as well as content-layer considerations that need to be taken into account, such as changing modes of internet use, types of surveillance practices, and statecraft in the digital age. The discussion held over the course of the two-day seminar invoked more questions than answers; analysis of such issues has thus far moved, as one seminar participant described, “glacially” alongside the need for internet governance. Thus, the seminar was both timely and a necessary given the salience of internet security, privacy, and surveillance in international politics, along with the perhaps shifting role of the state, and traditional concepts of international politics: state power, sovereignty, and global governance. Uniqueness – Terror High Al-Quada is actively expanding into India through Huji. Terror attacks through the county are actively being attempted. Daily Star 7/3 'Huji Plans, 7-3-2015, "'Huji plans Qaeda merger'," Daily Star, http://www.thedailystar.net/backpage/huji-plans-qaeda-merger-106585 Harkat-ul-Jihad-al-Islami, Bangladesh (Huji-B) leaders were preparing to build their organisational capability to join al-Qaeda in Indian Subcontinent (AQIS). They wanted to go on a bombing spree after Eid to let everyone know that they exist. Rapid Action Battalion made the claim after arresting 12 alleged Huji leaders and activists. Arrestee Maulana Mainul Islam Mahim's job was to coordinate with AQIS and organise the Huji leaders and activists to join al-Qaeda. Arrestee Mufti Zafar Amin Salman was acting as an adviser for the whole operation, Rab officials said. Rab also said the arrestees were trying to label themselves as “Dawate Tabliq” and “313 Badrer Sainik”. Their plan was to join AQIS after the two organisations had spread across Bangladesh. “ They [arrested militants] had a plan to carry out bomb attacks across the country after Eid to send a message to the inactive members of militant outfits about their existence,” said Mufti Mahmud Khan, Rab's Legal and Media wing director, at a press briefing at its headquarters in the capital yesterday. He said their plan was to get as much media coverage as possible through the bomb attacks and recruit more operatives. Rab officials said the militants had so far recruited 50 operatives and of them, 20 were supposed to have training at a madrasa in Bogra. The Rab's claim about the arrestees' attempt to set up a link with AQIS could not be verified. Journalists had not been allowed to ask the arrestees questions when they were paraded before the media yesterday. After becoming stronger by recruiting more operatives , they had a plan to work under AQIS, Rab claimed. Al-Qaeda leader Ayman al-Zawahiri in last September had announced an Indian subcontinent branch of al-Qaeda for Bangladesh, India , Pakistan and Myanmar. Earlier, in a video posted on Jihadist Forum on May 2, AQIS claimed the responsibility for the murder of writer-blogger Avijit Roy. In the video, AQIS leader Asim Umar said his organisation carried out the attack on Avijit and “other blasphemers" in Bangladesh and Pakistan. Rab officials, however, said they so far did not find any link between the arrestees and the murders and the AQIS claim. They said they would interrogate them further in remand about the murders and the claim. Mufti Mahmud Khan told reporters that Maulana Mayeen Uddin alias Abul Jandal, a death-row in mate and a top Huji leader, had been communicating with the arrestees from jail. The arrestees had been planning a Trishal-style ambush on a prison van to snatch away Mayeen from custody, he said. In February last year, militants attacked a prison van in Trishal of Mymensingh and liberated three condemned JMB leaders from police custody. A policeman was killed in the attack. Two of the escapees are still at large while the other one was killed in a shootout. Huji had wanted to free Mayeen by attacking and cutting the grills of Kashimpur Jail, Rab claimed, adding that realising it was very risky, they planned for an ambush. On information that Huji men were gathering in the capital from across the country, several teams of Rab-4 detained them at Sadarghat, Airport Railway Station and Mirpur during the last two days. The other arrestees were: Mohammad Saidul Islam alias Sayeed Tamim, Mosharraf Hossain, Abdur Rahman Bapary, Al Amin Ibrahim, Mozahidul Islam Nakib, Ashraful Islam alias Abul Hashem, Robiul Islam, Habib Ullah, Shohidul Islam, and Altaf Hossain. Rab during its drive in a Mirpur house also seized bomb-making materials and manuals, and books on jihad. Terror attacks have been sharply on the rise. Lee 6/10 Matthew Lee, 6-10-2015, Matthew Less is State Department correspondent at Associated Press"US: 35 percent spike in global terror attacks in 2014," NorthJersey, http://www.northjersey.com/news/us-35-percent-spike-in-global-terror-attacks-in-20141.1359476 Extremists in Iraq, Afghanistan and Nigeria unleashed a savage rise in violence between 2013 and 2014, according to new statistics released by the State Department. Attacks largely at the hands of the Islamic State and Boko Haram raised the number of terror acts by more than a third, nearly doubled the number of deaths and almost tripled the number of kidnappings . The figures contained in the department's annual global terrorism report say that nearly 33,000 people were killed in almost 13,500 terrorist attacks around the world in 2014. That's up from just over 18,000 deaths in nearly 10,000 attacks in 2013, it said. Twenty-four Americans were killed by extremists in 2014, the report said. Abductions soared from 3,137 in 2013 to 9,428 in 2014, the report said. The report attributes the rise in attacks to increased terror activity in Iraq, Afghanistan and Nigeria and the sharp spike in deaths to a growth in exceptionally lethal attacks in those countries and elsewhere. There were 20 attacks that killed more than 100 people each in 2014, compared to just two in 2013, according to the figures that were compiled for the State Department by the National Consortium for the Study of Terrorism and Responses to Terrorism at the University of Maryland. Among the 20 mass casualty attacks in 2014 were the December attack by the Pakistani Taliban on a school in Peshawar, Pakistan that killed at least 150 people and the June attack by Islamic State militants on a prison in Mosul, Iraq, in which 670 Shiite prisoners died. At the end of 2014, the prison attack was the deadliest terrorist operation in the world since Sept. 11, 2001, according to the report. The State Department's counterterrorism coordinator said the numbers don't reflect improvements by the U.S. and its partners in stamping out terrorism financing, improving information sharing, impeding foreign fighters and forming a coalition to fight the Islamic State. "We have made progress," Ambassador Tina Kaidanow said. Terror attacks took place in 95 countries in 2014, but were concentrated in the Mideast, South Asia and West Africa. Iraq, Pakistan, Afghanistan, India and Nigeria accounted for more than 60 percent of the attacks and, if Syria is included, roughly 80 percent of the fatalities, the report found. The rise in kidnappings is mainly attributable to sharp increases in mass abductions by terrorist groups in Syria, notably the Islamic State and the al-Qaida-linked alNusra Front. In Nigeria, Boko Haram was responsible for most, if not all, of the nearly 1,300 abductions in Nigeria in 2014, including several hundred girls from a school in Chibok. By contrast, fewer than 100 terror-related kidnappings were reported in Nigeria in 2013, according to the report. Al-Quada has active control of regions of Yemen. France 24, 7/8 An Alliance, 8-7-2015, "A report from an al Qaeda-controlled city in Yemen," Observers, http://observers.france24.com/content/20150708-yemen-mukalla-al-qaeda-control As Yemen slides into chaos, al Qaeda in the Arabian Peninsula (AQAP) has taken advantage of the deteriorating security and political situation to gain further ground in the country . The jihadist group recently took control of a large chunk of the southeastern province of Hadhramaut. Our Observer explains how AQAP's jihadists have been tightening their grip over the region and its inhabitants on a daily basis. Air strikes carried out by an alliance of Gulf states have largely slowed the advance of Shiite Houthi rebels in southern Yemen. But that hasn't been their only consequence. In just four months AQAP has managed to wrest control of several cities in Hadhramaut , including the region's capital, the port city of Mukalla. Militants have even taken over the local branch of Yemen's central bank, police stations and military headquarters. "They've started patrolling while carrying megaphones" Our Observer, Mohamed, is a journalist based in Mukalla. At the start, the arrival of al Qaeda improved security in the city because thefts and looting had been on the rise since the beginning of the air strikes. The group's members were very reassuring towards the residents. They said that they had no intention of applying Sharia law straight away, but favoured dialogue with the local population. "AQAP members burned markets where khat is sold" But little by little, the group began imposing its laws. Firstly, they burned down markets where khat is sold [Editor's note: a popular soft drug in Yemen]. They also banned sale of the drug, though they didn't lay into users. They also started patrolling the streets of the city. Often, the fighters would stop women if they found that their veils didn’t conform to AQAP rules, or if they found their perfume to be too strong. At first, it was not so bad. The AQAP militants were happy enough just giving out 'advice'. US efforts to stop groups like ISIS have been unsuccessful Sisk 7/6 Richard Sisk, 7-6-2015, Richard Sisk has more than 40 years experience in journalism as a reporter and editor for the wire services and the N.Y. Daily News. He has embedded with U.S. troops in Afghanistan and Iraq, and reported from Beirut, Tel Aviv, Bosnia, Kosovo, Panama, Haiti, Guatemala, Northern Ireland, Vietnam, Eritrea and other conflict zones"$500M US Program Has Only Trained 60 Syrians to Fight ISIS," Military, http://www.military.com/dailynews/2015/07/07/500m-us-program-has-only-trained-60-syrians-to-fight-isis.html Defense Secretary Ashton Carter said Tuesday that only 60 so-called "moderate" Syrian rebels were currently being trained by the U.S. in the $500 million program that had been slated to put 3,000 fighters into the field against ISIS by the end of this year. Carter told the Senate Armed Services Committee that he regretted disclosing that the number was so low but "I wanted to tell the truth. The number 60, as you all recognize, is not an impressive number. The number is much smaller than we hoped for at this point." The $500 million Syrian training program authorized by Congress was intended to train and equip up to 5,400 fighters annually, with about 3,000 projected to be ready by the end of this year. Cater said that Army Maj. Gen. Michael Nagata of U.S. Central Command, who is leading the Syrian training program, had about 7,000 potential recruits identified but "It's obviously going to take time, obviously" to vet and prepare them. SASC Chairman Sen. John McCain, R-Ariz., who earlier gave a scathing critique of the Obama administration's entire approach to the campaign against the Islamic State of Iraq and Syria (ISIS), said that "given the poor numbers of recruited and trained Syrian fighters thus far, I am doubtful we can achieve our goal of training a few thousand this year." " I got to tell you that after four years, Mr. Secretary, that is not a very impressive number, " said McCain. He suggested that the recruiting effort was failing because the U.S. has yet to tell the Syrian rebels whether the U.S. would protect them from attack by the regime of Syrian President Bashar al-Assad. McCain asked: "Is that fair to these young men to say we are sending you in to fight ISIS only, and by the way, we will decide on the policy whether to defend you if you are barrel bombed?" Carter and Joint Chiefs Chairman Gen. Martin Dempsey, U.S. training program for Iraqis was also falling far short of its goals. About 8,800 have been trained for the Iraqi Security Force (ISF), and another 2,000 for counter- who also testified at the hearing, said that the terrorism activities, against projections that 24,000 would be fielded by the end of this year, Carter said. The hearing marked what was likely to be the last Congressional testimony by Dempsey, who will retire in October. On Thursday, the committee will hold a confirmation hearing for Dempsey's designated successor, Marine Commandant Gen. Joseph Dunford. The hearing also offered McCain and Dempsey what was probably their last opportunity to renew their long-standing feud over tactics, strategy, readiness and budgets going back years. Their disputes reached the point two years ago where McCain put a temporary hold on Dempsey's renomination as JCS Chairman. UQ- The US is losing the war on terror, Us intervention has created more terrorist activity Jebreal ‘14 Rula Jebreal, 11-26-2014, Rula Jebreal is a Palestinian-Italian foreign policy analyst, journalist, novelist and screenwriter. She was a commentator for MSNBC."Rula Jebreal: Why America is losing the war on terror — and the Islam debate is so flawed," No Publication, http://www.salon.com/2014/11/26/rula_jebreal_why_america_is_losing_the_war_on_terror_a nd_the_islam_debate_is_so_flawed/ America is losing the longest war in its history . An enemy that had comprised a couple of hundred desperate men hiding in caves in eastern Afghanistan when the “war on terror” got underway following the 9/11 attacks is incarnated today as 20,000 fighting men in the Islamic State movement. And far from hiding in caves, ISIS has brazenly raised its black flag over vast swaths of territory in Syria and Iraq – countries that, in 2001, had been two of the most secular societies in the Middle East. Thus the fruits of the trillions of dollars and thousands of American lives – and hundreds of thousands of unnamed innocent civilians in the Middle East and Asia – devoured by the war on terror, which the Obama administration now says could rage for another 30 years. Given its costs, consequences and failures, the war on terror has provoked remarkably little sensible public debate in the U.S. The country that congratulated itself for having killed Osama bin Laden has not asked itself why that fact seems to have mattered so little to the trajectory of the conflict. And politicians and pundits have been largely indifferent to the devastating Only when jihadists began disseminating macabre, but well-produced videos of the brutal decapitation of American captives did U.S. attention turn, once again, to Iraq and Syria. Desultory military strikes followed, but little explanation to the American people about what has gone wrong — except, perhaps, among TV info-tainers such as Bill Maher, who insist that the problem lies within Islam itself. It may be comforting to see the ISIS phenomenon as determined by theology rather than the result of mass regional and American incompetence. It’s conventional wisdom among the Arab world’s secular democrats to view ISIS as a byproduct of the U.S. invasion of Iraq. We wrecked a country, destroying its institutions and security forces, creating a vacuum that drew in jihadists from across the globe . Al-Qaida had not operated in Iraq before the invasion; it moved in after the invasion, setting up shop in the Sunni communities antagonized by the U.S.-led occupation. Similarly, ISIS has exploited the alienation of the Sunni population from the consequences of U.S. intervention in Afghanistan, Iraq and Libya. sectarian Shiite-led government of Prime Minister Nuri al-Maliki to gain control of much of northern and western Iraq. Independent Judiciary Good – India Independent judiciary is important in India Firstpost 6/18 National, 6-18-2015, "Right to appoint judges is part of judicial independence: Lawyers body tells SC," Firstpost, http://www.firstpost.com/india/right-appoint-judges-part-judicialindependence-lawyers-body-tells-sc-2302012.html The right of judiciary to insist on appointing judges is a "vital" part of its independence and basic structure of the Constitution which has been taken away by the National Judicial Appointments Commission (NJAC), a lawyers body on Thursday told the Supreme Court. Senior advocate and jurist Fali S Nariman, appearing for the Supreme Court Advocates on Record Association (SCAORA), told a five-judge bench headed by Justice JS Khehar that the right to have its say in the appointments is the "core" of the independence of the judiciary. "Right to insist is the core of the right. It is the right of appointment. It is not the only part of independence of judiciary but it is a vital part of it," he told the bench, also comprising justices J Chelameswar, MB Lokur, Kurian Joseph and Adarsh Kumar Goel which is hearing the petitions challenging the validity of the NJAC Act. Independent Judiciary Good – Turkey Independent judiciary is important in Turkey. Cihan 6/30 Cihan Haber Ajansı, 06-30-2015, "Judge: Turkey should restore judicial independence ," Cihan Haber Ajansı: Doğru ve hızlı haberin adresi, http://en.cihan.com.tr/en/judge-turkey-shouldrestore-judicial-independence-1810721.htm Writing on his Twitter account on Sunday, Supreme Board of Judges and Prosecutors (HSYK) member Mahmut Şen said the government should listen to the 10 international organizations that have urged Turkey to restore judicial independence. “It is not enough to say that we are right, fair, impartial and independent. If we cannot convince international organizations and the public of this, then there is a serious problem,” Şen said. The HSYK member listed the international organizations that have criticized Turkey over government intrusion in the judiciary, which include the European Parliament (EP) in its Turkey progress report, Human Rights Watch (HRW), the Consultative Council of European Judges (CCJE), the European Association of Judges (EAJ), the Venice Commission, the United Nations Office of the High Commissioner for Human Rights (OHCHR) and the Group of States against Corruption (GRECO). “If these 10 organizations say similar things in their reports, then either we are acting in a way that contradicts the universal norms in [judicial] appointment and discipline issues, or we have failed to clearly express the reasons behind our actions,” Şen said. The judge also said that ignoring such reports might lead to rulings against Turkey from the European Court of Human Rights (ECtHR ). There should be no special conditions for Turkey when it comes to the universal rules of law, which aim to promote fundamental rights and must be applied in every situation, Şen stated . Independent Judiciary Good – Human Rights Independent judiciary key to human rights UN 6/13 UN News Service Section, 6-13-2015, "UN News," http://www.un.org/apps/news/story.asp?NewsID=51146#.VZ7XUM6polI Despite all these efforts, however, the Secretary-General cautioned that the road to development must be sustained by a deep commitment to human rights. “There is no peace without development. No development without peace. And neither is possible without a respect for human rights,” he stated. Adding that violations of human rights are “often warning signs of much worse to come,” Mr. Ban reminded those gathered of his Human Rights Up Front initiative which worked to address human rights violations before they escalate. To that point, he voiced concern about the perceived “deterioration of some aspects of human rights – a shrinking democratic space” across Central Asia. Curbing freedoms, he said, might create “an illusion of stability in the short-run” but ultimately would foster “a breeding ground for extremist ideologies.” “The failure to respect human rights, build accountable institutions, promote political participation, and ensure opportunity for all creates gaps,” continued the Secretary-General. “Young people should be sent a message: democracy in Central Asia can work.” “Around the world, the way to confront threats is not more repression, it is more openness. More human rights. The road to a stable future is by strengthening the rule of law. By fighting corruption. By ensuring an independent judiciary . By guaranteeing free media. By building just societies. By empowering citizens,” he added.