Homework 1
advertisement
CS 6378 Advanced Operating Systems
Homework 1
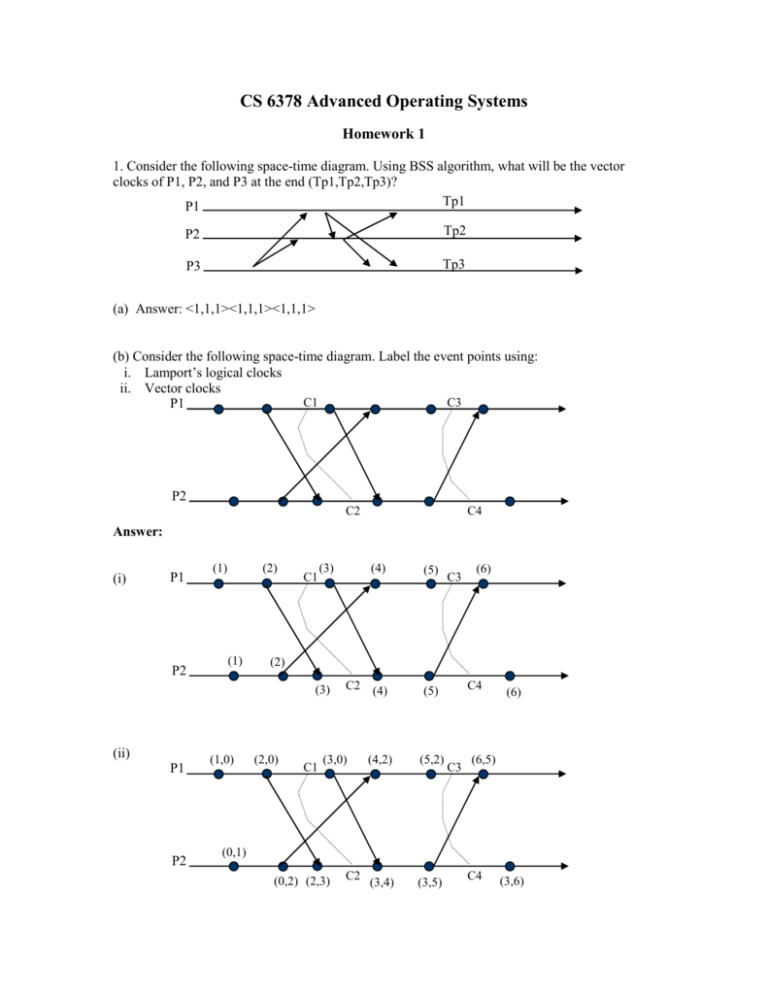
1. Consider the following space-time diagram. Using BSS algorithm, what will be the vector
clocks of P1, P2, and P3 at the end (Tp1,Tp2,Tp3)?
Tp1
P1
P2
Tp2
P3
Tp3
(a) Answer: <1,1,1><1,1,1><1,1,1>
(b) Consider the following space-time diagram. Label the event points using:
i. Lamport’s logical clocks
ii. Vector clocks
C1
C3
P1
P2
C2
C4
Answer:
(i)
P1
P2
(1)
(2)
(1)
C1
(3)
P1
P2
(1,0)
(5)
C2 (4)
(5)
C3
(6)
(2)
(3)
(ii)
(4)
(2,0)
C1
(3,0)
(4,2)
(5,2)
(3,4)
(3,5)
C4
C3
(6)
(6,5)
(0,1)
(0,2) (2,3)
C2
C4
(3,6)
(c) What is vector time of cuts {C1, C2, C3} and {C4, C5, C6}in the space-time diagram below.
P1
C1
C5
P2
C2
C3
C6
Answer:
Vector time (C1,C2,C3) = {2,3,3}. Vector time of (C4, C5, C6) = {6,6,5}
2. Consider a distributed system that has computers C1 and C2. In C1, integer data type is
represented with 32 bits and character with 16 bits. In C2, an integer uses 16 bits while a
character uses 8 bits. Now, an Ada program has a procedure RemoteOperate(m: integer; n:
character; var x: integer) that can be invoked by C2 on C1. (Such a remote invocation implies
that parameters m and n should be passed by C2 to C1 and parameter x should be returned from
C1 to C2). Design a packing and an unpacking stub procedure on C2 and C1 to enable the
invocation of the procedure RemoteOperate.
Answer:
(Different answers possible.)
One can design a generic message format for sending and receiving parameters: <N, L1, V1, L2,
V2,…> where N is the number of parameters in the message, L1 is the number of bytes used for
1st parameter, V1 is its value, L2 is the number of bytes used for 2nd parameter, V2 is its value, …
At C2:
Packed Message: <2, 2, V1, 1, V2>
Unpacked Message: <1, 4, V1>
At C1:
Packed Message: <1, 4, V1>
Unpacked Message: <2, 2, V1, 1, V2>
Pseudo-code can be specified to represent the above packing and unpacking.
3. We saw that SES (Schiper-Eggli-Sandoz) algorithm has a problem in handling multicast
messages. The modified SES algorithm handles multicasts by using an N * N matrix (N being the
number of processes in the system). However, the modified SES is inefficient when N is high and
multicast messages are sent only to few of the processes in the system. For instance, consider a
100 processes system where a multicast message 10 bytes (as an example) is sent to, say, 5
processes. Here, this message needs to carry the 100*100 byte matrix of the modified SES
algorithm for delivering 10 bytes to 5 processes.
Can you device a compromise between the original and modified SES algorithms? The intention
is to achieve multicasting without incurring the overhead of the N * N matrix. Let us call this
compromise as “extended” SES algorithm. To start with, the extended SES algorithm can support
multicasting by inserting <Pi, t> (of all the Pis that are receiving the multicast message) in the
V_P and sending this V_P along with the message itself. (instead of sending the <Pi,t> tuples
after the message as per the original SES algorithm). Can you complete the specification of this
extended SES algorithm and explain it through an example how this extended SES algorithm
work? This specification should explain clearly how the sender would send messages and the
rules employed for delivering & buffering by the receiver.
(Note: the original and modified SES algorithms are given in Appendix for your reference).
Answer:
1. Along with each message (instead of after sending the message), <Pi,t> of all multicast
receivers are sent. So V_P is written before sending a message, not after.
2. On the receiving side:
Delivery condition: Compare t in <Pi,t> and Tpi. Deliver the message only if
t[j] = Tpi[j] – 1, where j is the sender & i is the receiver.
Tpi[k] >= t[k] for all k != i
After delivery, update Tpi such that Tpi[j] := t[j]. Merge V_P entries as in the original SES
algorithm.
4. A distributed computation application uses Huang’s termination detection algorithm.
Computation starts at process P (which acts as the controlling agent). P asks P1 to do some
computation. P1 requests P2 to do part of its computation. P2 passes on part of its job to P3. After
some time, P1 uses P4 to carry out another part of its computation and P3 gets P5 to do some part
of its job. Draw a process-tree diagram and mention the weights assigned to each process.
Now, P4 completes and hands over the results. Draw the process-tree diagram at this stage.
Answer:
--- Straight forward answer, following the lecture notes ---5.
a. Consider the Chandy-Lamport algorithm for recording consistent state information.
i. Sending Marker by P:
1) P records its state.
2) For each outgoing channel C, P sends a marker on C
before P sends further messages along C.
ii. Receiving Marker by Q:
1) If Q has NOT recorded its state: (a). Record the
state of C as an empty sequence. (b) SEND marker (use
above rule).
2) Else (Q has recorded state before): Record the state
of C as sequence of messages received along C, after
Q’s state was recorded and before Q received the
marker.
In the above algorithm, what is the significance of (ii)(1)(a)?, i.e., “If Q has NOT recorded
its state: (a). Record the state of C as an empty sequence.”
Answer:
P1
P2
E1 E2 E3 E4 M(1,1)
T
(ii) (1)(a): State of P1 = {Send(E1,E2,E3,E4)}. State of P2 = {Receive(E1,E2,E3,E4)}. State of
channel is empty since P2 records all the receive events in its state.
[ To understand the “Else” part, i.e., (ii)(1)(b)
Now assume that, P2 has recorded its state at T. When the marker M arrives, P2 does not record
its state again. So state of C is {Receive(E1,E2,E3,E4)}
]
b. Explain how FIFO channels assumption + the markers help to record consistent states. You
may use an example space-time diagram to explain your answer, if you feel like.
Answer:
Consider the figure for 4(a). Here, if messages E1-E4 are recorded as sent in P1, then E1-E4 will
always be recorded as received (either in the state of P2 or in the state of C). Reason: marker will
arrive only AFTER E1-E4 because of the FIFO condition. Hence, no inconsistent messages in the
global state.