Slides for lecture 5
advertisement

CMSC 414
Computer and Network Security
Lecture 5
Jonathan Katz
Announcements
Midterm on March 15
Modes of encryption
Used for encrypting a long message m1, …, mn
ECB
– Ci = FK(mi); the ciphertext is (C1, …, Cn)
CBC
– IV; Ci = FK(mi Ci-1); the ciphertext is (IV, C1, …, Cn)
OFB (stream cipher mode)
– IV; zi = FK(zi-1); Ci = zi mi; the ciphertext is (IV, C1, …, Cn)
CTR (stream cipher mode)
– IV; zi = FK(IV+i); Ci = zi mi; the ciphertext is (IV, C1, .., Cn)
Others…
Security?
ECB should not be used
– Why?
Not even secure against ciphertext-only attacks
The effect of ECB mode
original
encrypted using ECB mode
*Images
from Wikipedia
Other modes
CBC, OFB, and CTR modes are secure against
chosen-plaintext attacks
CBC, OFB, and CTR modes are not secure against
chosen-ciphertext attacks
*Images
from Wikipedia
Message integrity
Message integrity
m
m’
Encryption does not provide integrity
“Since encryption garbles the message, decryption
of a ciphertext generated by an adversary must be
unpredictable”
– WRONG
E.g., one-time pad, CBC-/CTR-mode encryption
Why is this a concern?
– Almost always, integrity is needed in addition to
secrecy
– Lack of integrity can lead to lack of secrecy
Use message authentication codes (MACs)
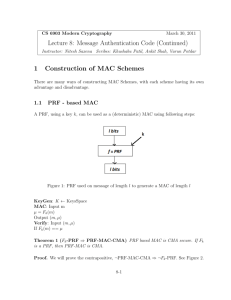
Message authentication code (MAC)
In the private-key setting, the tool for achieving
message integrity is a MAC
Functionality:
– MACK(m) = t (we call t the “tag”)
– VrfyK(m, t) = 0/1 (“1” = “accept” / ”0”=“reject”)
– Correctness…
MAC usage
Bob
Alice
m, t
k
t = Mack(m)
k
Vrfyk(m’,t’) ??
•Shared key k
•Sender computes a tag t on the message m
using k
•Receiver verifies the message/tag pair using k
MAC usage
Bob
K
Defining security
Attack model:
– A random key k is chosen
– Attacker is allowed to obtain t1 = MACk(m1), …, tq =
MACk(mq) for any messages m1, …, mq of its choice
Attacker is successful if it outputs a forgery; i.e.,
(m, t) with:
– m ≠ mi for all i
– VrfyK(m, t) = 1
For any time-bounded adversary, the probability
of a successful attack should be small
Defining security
Is the definition too strong?
– When would an attacker be able to obtain tags on any
messages of its choice?
– Why do we count it as a break if the adversary outputs
a forgery on a “meaningless” message?
– Main point: we want a secure MAC to be usable in any
setting where message integrity is needed
Replay attacks
A MAC inherently cannot prevent replay attacks
Replay attacks must be prevented at a higher level
of the protocol!
– (Note that whether a replay is ok is applicationdependent)
Replay attacks can be prevented using nonces,
timestamps, etc.
– Will discuss more later
A MAC for short messages
Let F be a block cipher with n-bit output
To authenticate m using key k, compute
t = Fk(m)
Vrfyk(m, t): output 1 iff t = Fk(m)
Why is this secure?
(Informal) sketch of security
Replace Fk with a random permutation f
– Can do this since F is a block cipher
Seeing f(m1), …, f(mq) does not help to predict
f(m) for any m{m1,…,mq}
– If adversary outputs (m, t), the probability that t is
correct is roughly 2-n
– For n large enough, the probability of forgery is small