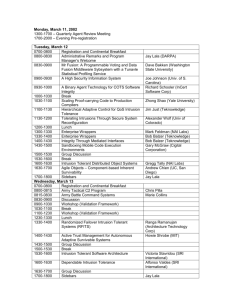
Lecture for Chapter 2.8 (Fall 11)
advertisement
Distributed System Concepts and Architectures Summary By Srujana Gorge Outline • • • • • • • • • Introduction Of Distributed System Goals Transparency Services Communication Network Models Major Design Issues Distributed Computing Environment(DCE) Latest Work Future Work What is Distribution system? • A distributed system is a collection of autonomous computers linked by a computer network that appears to the user as a single computer Why distributed system? • • • • Resource sharing Computation speedup Reliability In event of system resource failure, shift its processing load to another similar resource Categories • Multiple computer systems collaborating to deliver a single application • Multiple applications collaborating together as a system Disadvantages of Distributed Systems • Difficulties of developing distributed software • Networking Problems • Security problems GOALS Design Goals • • • • Efficiency Flexibility Consistency Robustness Why Operating System Services? • OS provides an environment for the executions of the programs. • Services are provided for the convenience of the programmer , to make the programming task easier. • Services provided differ from one operating system to another operating system. Services • • • • • • • • Program Execution I/O Operations File-system manipulation Communications Error Detection Resource Allocation Accounting Protection Communication Network Protocols • For a network architecture, rules and standards must be set up to govern the communication. Communication Protocols are sets of rules that regulate the exchange of messages to reliable and orderly flow of information. • Two most popular network protocol suites: OSI (Open Systems Interconnection) from ISO (International standards organization) TCP/IP(Transmission Control Protocol/Internet Protocol) from the DoD (U..S Department of Defense) Design Issues of Distributed Systems • • • • • • Openness Security Reliability and fault tolerance Scalability Concurrency Achieving Transparency[A. S. Tanenbaum] Distributed Computing Environment • DCE provides a complete Distributed Computing Environment infrastructure. • It provides security services to protect and control access to data, name services that make it easy to find distributed resources, and a highly scalable model for organizing widely scattered users, services, and data. • DCE runs on all major computing platforms and is designed to support distributed applications in heterogeneous hardware and software environments. DCE is a key technology in three of today's most important areas of computing: security, the World Wide Web, and distributed objects. Latest Work: Asian computers join forces against Avian Flu • Computers can simulate a large number of chemical compounds and measure their ability to fit snugly into the chemical coating of a virus, thereby blocking its ability to function properly • “Avian Flu DC2 Refinement” is the latest attack on Avian Flu using Grid Computing • The grid technology allowed 125 processor cores — the heart of every computer — to join forces even though they were thousands of miles apart, All the computing jobs were completed within four weeks. A total of 1,111 CPU-days were used, which is equivalent to running a single computer for over three years. Over 160,000 files generated a large volume of data, about 12.8 gigabytes, which was collated in a database. • Now the community is hardly working to find drugs for virus behind dengue fever. Reference Link: http://www.isgtw.org/feature/feature-asiancomputers-join-forces-against-avian-flu Future Work:A distributed intrusion detection system for wireless ad hoc networks • In multi-hop mobile ad hoc network (MANET), mobile nodes communicate with each other forming a cooperative radio network. • Security remains a major challenge for these networks due to their features of open medium, dynamically changing topologies, reliance on cooperative algorithm. • Most of the currently existing intrusion detection algorithms designed for these networks are insecure, inefficient, and have high rates of false positives. • So, In order to provide the security to manet, a new approach has been proposing to bring out the complementary relationship between key distribution and intrusion detection for developing an intrusion detection protocol for ad hoc networks, which will work even in the failure of nodes. REFERENCES A distributed intrusion detection system for wireless ad hoc networks http://ieeexplore.ieee.org/search/freesrchabstra ct.jsp?tp=&arnumber=4772624 REFERENCES • Distributed Operating Systems & Algorithms, Randy Chow and Theodore Johnson, Addison Wesley, 1997. • Distributed Systems principles and paradigms by Andrew S. Tanenbaum, Maarten van Steen, 2002. • Ge, Z.; Figueiredo, D.R.; Sharad Jaiswal; Kurose, J.; Towsley, D.; Modeling peer-peer file sharing systems, INFOCOM 2003. TwentySecond Annual Joint Conference of the IEEE Computer and Communications Societies. IEEE Volume 3, 30 March-3 April 2003 Page(s):2188 - 2198 vol.3 Thank You! Any Questions?