Chap 12 - The University of Tulsa
advertisement

Chapter 12
Media
Access
Control
(MAC)
Copyright © The McGraw-Hill Companies, Inc. Permission required for reproduction or display.
Chapter 5: Outline
12.1 RANDOM ACCESS
12.2 CONTROLLED ACCESS
12.3 CHANNELIZATION
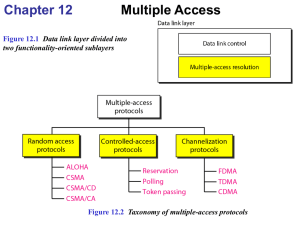
Figure 12.1: Taxonomy of multiple-access protocols
12.3
12-1 RANDOM ACCESS
Random-access implies no station is superior to
another station and none is assigned control
over another.
12.4
12-1 RANDOM ACCESS
Stations use a procedure defined by the protocol
on whether or not to send a message.
This decision depends on the state of the
medium (idle or busy).
12.5
12.12.1 ALOHA
ALOHA is the earliest random access method
developed at the University of Hawaii in early 1970.
12.6
12.12.1 ALOHA
ALOHA was designed for a radio (wireless) LAN, but
it can be used on any shared medium.
12.7
12.12.1 ALOHA
ALOHA shares the medium between the stations.
When a station sends data, another station may
attempt to do so at the same time. The data from the
two stations collide and become damaged.
12.8
Figure 12.2: Frames in a pure ALOHA network
12.9
Figure 12.3: Procedure for pure ALOHA protocol
12.10
Example 12. 1
The stations on a wireless ALOHA network are a maximum
of 600 km apart. Find the propagation time and wait time if
signals propagate at 3 × 108 m/s.
12.11
Example 12. 1
The stations on a wireless ALOHA network are a maximum
of 600 km apart. …
Tp = (600 × 103) / (3 × 108) = 2 ms
The wait time is 2 Tp = 4 ms
12.12
Example 12. 1
The stations on a wireless ALOHA network are a maximum
of 600 km apart. What is the back-off time if
K = 2?
12.13
Example 12. 1
The stations on a wireless ALOHA network are a maximum
of 600 km apart. ... What is the back-off time if
K = 2?
12.14
Example 12. 1
The stations on a wireless ALOHA network are a maximum
of 600 km apart. … What is the back-off time if
K = 2?
The range of R is {0, 1, 2, 3}. This means that TB can be 0,
2, 4, or 6 ms, based on the outcome of the random variable
R.
12.15
Figure 12.4: Vulnerable time for pure ALOHA protocol
12.16
Example 12.2
A pure ALOHA network transmits 200-bit frames on a
shared channel of 200 kbps. What is the requirement to
make this frame collision-free?
12.17
Example 12.2
A pure ALOHA network transmits 200-bit frames on a
shared channel of 200 kbps. What is the requirement to
make this frame collision-free?
Solution
Average frame transmission time Tfr is 200 bits/200 kbps or
1 ms/frame. The vulnerability time is 2 Tfr = 2 ms.
12.18
Example 12.2
A pure ALOHA network transmits 200-bit frames on a
shared channel of 200 kbps. What is the requirement to
make this frame collision-free?
Solution
The vulnerable time is 2 ms.
This means no station should send later than 1 ms before
this station starts transmission and no station should start
sending during the period (1 ms) that this station is sending.
12.19
Example 12. 3
A pure ALOHA throughput efficiency percentage S, is
computed using
S = G × e−2G
Where G = duration * saturation.
12.20
Example 12. 3
A pure ALOHA throughput efficiency percentage is
computed using
S = G × e−2G
Take the derivative wrt-G and set to zero to find the maximum efficiency value.
12.21
Example 12. 3
A pure ALOHA throughput efficiency percentage is
computed using
S = G × e−2G
Take the derivative wrt-G and set to zero to find the maximum efficiency value.
Smax = .184 or 18.4%
12.22
Example 12. 3
A pure ALOHA network transmits 200-bit frames on a
shared channel of 200 kbps. What is the throughput if the
system (all stations together) produces
a. 1000 frames per second?
b. 500 frames per second?
c. 250 frames per second?
12.23
Example 12. 3
A pure ALOHA network transmits 200-bit frames on a
shared channel of 200 kbps. What is the throughput if the
system (all stations together) produces 1000 frames per
second?
Solution part a
The frame duration = (200bits/frame)/ (200kbits/sec)
Saturation = 1000 frames/sec
G = duration * saturation = 1
S = .135 or 135 frames/sec survive on average.
12.24
Example 12. 3
A pure ALOHA network transmits 200-bit frames on a
shared channel of 200 kbps. What is the throughput if the
system (all stations together) produces 1000 frames per
second?
Solution part a
The frame duration = (200bits/frame)/ (200kbits/sec)
Saturation = 1000 frames/sec
G = duration * saturation = 1
S = .135 or 135 frames/sec survive on average.
12.25
Example 12. 3 (continued)
Solution b. If the system creates 500 frames per second, or
1/2 frames
Duration =
Saturation =
G=
S=
12.26
Example 12. 3 (continued)
Solution b. If the system creates 500 frames per second, or
1/2 frames
Duration = 1 ms / frame
Saturation = 500 frames / sec
G = .5
S is about 92 frames (18.4% survive)
12.27
Slotted ALOHA
Each station must be synchronized to send
frames on a frame duration interval.
Figure 12.5: Frames in a slotted ALOHA network
12.29
Slotted ALOHA Vulnerability
The vulnerability time is half of the pure
ALOHA
Figure 12.6: Vulnerable time for slotted ALOHA protocol
12.31
Example 12. 4
The slotted ALOHA throughput efficiency percentage is
computed using
S = G × e−G
Take the derivative wrt-G and set to zero to find the maximum efficiency value.
12.32
Example 12. 4
The slotted ALOHA throughput efficiency percentage is
computed using
S = G × e−G
Take the derivative wrt-G and set to zero to find the maximum efficiency value.
Smax = 36.8%
12.33
Example 12. 4
A slotted ALOHA network transmits 200-bit frames using a
shared channel with a 200-kbps bandwidth. Find the
throughput if the system (all stations together) produces 250
frames per second.
12.34
12.12.2 CSMA
CSMA method was developed to reduce collisions.
The chance of collision can be reduced if a station
senses the medium before trying to use it.
12.35
12.12.2 CSMA
Carrier sense multiple access (CSMA) requires that
each station first listen to the medium (or check the
state of the medium) before sending.
(no more than one station can “talk” at a time.)
12.36
Figure 12.7: Space/time model of a collision in CSMA
12.37
Figure 12.8: Vulnerable time in CSMA
12.38
Persistence Methods
Persistence methods are used to reduce
the possibility of a collision.
Persistence Methods
Three common persistence methods:
1-persistence
non-persistence
p-persistence
Figure 12.9: Behavior of three persistence methods
12.41
Exponential Back-off
Let K = number of retries.
K is incremented for each retry up to a
maximum number of retries.
Let N = { 0, 1, … , 2^K - 1 }
Choose a random number from the set N.
Multiply the result time the propagation time.
Wait and retry
Figure 12.10: Flow diagram for three persistence methods
12.43
12.12.3 CSMA/CD
The CSMA method does not specify the procedure
following a collision.
Carrier sense multiple access with collision detection
(CSMA/CD) augments the algorithm to handle the
collision.
12.44
12.12.3 CSMA/CD
Here a station monitors the medium after it sends a
frame to see if the transmission was successful.
If so, the station is finished.
Otherwise, there is a collision, and the frame is resent.
12.45
Figure 12.11: Collision of the first bits in CSMA/CD
12.46
Figure 12.12: Collision and abortion in CSMA/CD
12.47
Example 12. 5
CSMA/CD
When a station sends a frame, it transmits and listens
simultaneously to the sent-signal.
If while listening, the signal is distorted, then a collision has
occurred and the transmission is ended.
12.48
Example 12. 5
A network using CSMA/CD has a bandwidth of 10 Mbps. If
the maximum propagation time (including the delays in the
devices and ignoring the time needed to send a jamming
signal, as we see later) is 25.6 μs, what is the minimum size
of the frame?
12.49
Example 12. 5
A network using CSMA/CD has a bandwidth of 10 Mbps. If
the maximum propagation time (including the delays in the
devices and ignoring the time needed to send a jamming
signal, as we see later) is 25.6 μs, what is the minimum size
of the frame?
The propagation-time times the bit rate will give the number
of bits on the the link. But, that's not enough because, ...
12.50
Example 12. 5
A network using CSMA/CD ...
The propagation time times the bit rate will give the number
of bits on the the link.
The device is listening, but must listen for twice the
propagation time to sense a collision. Therefore it must
continuously send data for twice the propagation time.
12.51
Example 12. 5
A network using CSMA/CD has a bandwidth of 10 Mbps. If
the maximum propagation time (including the delays in the
devices and ignoring the time needed to send a jamming
signal, as we see later) is 25.6 μs, what is the minimum size
of the frame?
Solution
The minimum frame transmission time is Tfr = 2 × Tp =
512.2 μs. This means, in the worst case, a station needs to
transmit for a period of 512.2 μs to detect the collision. The
minimum size of the frame is 10 Mbps × 512.2 μs = 512 bits
or 64 bytes. This is actually the minimum size of the frame
for Standard Ethernet.
12.52
Figure 12.13: Flow diagram for the CSMA/CD
12.53
Figure 12.14: Energy level during transmission, idleness, or collision
12.54
12.12.4 CSMA/CA
Carrier sense multiple access with collision avoidance
(CSMA/CA) was invented for wireless networks.
12.55
12.12.4 CSMA/CA
Collisions are avoided through the use of CSMA/CA’s
three strategies:
1. The interframe space (DIFS & SIFS),
2. The contention window, and
3. Control frames (RTS, CTS, ACK).
12.56
Figure 12.15: Flow diagram for CSMA/CA
12.57
Figure 12.16: Contention window
12.58
Figure 12.17: CMACA and NAV
12.59
NAV
Network Access Vector – stations not
involved in the communication receive a
CTS frame or RTS frame.
The non-active stations can wait via the
NAV.
12-2 CONTROLLED ACCESS
In controlled access, the stations consult one
another to find which station has the right to
send.
12.61
12-2 CONTROLLED ACCESS
In controlled access, the stations consult one
another to find which station has the right to
send.
A station cannot send unless it has been
authorized to send.
12.62
12-2 CONTROLLED ACCESS TYPES
Reservation,
Polling,
Token Passing.
12.63
12.2.1 Reservation
A station makes a reservation before sending data.
12.64
12.2.1 Reservation
Each station has an allotted time slot where it can
reserve and insert its message.
12.65
Figure 12.18: Reservation access method
12.66
12.2.2 Polling
Polling works with topologies in which one device is
designated as a primary station and the other devices
are secondary stations.
12.67
12.2.2 Polling
All data exchanges must be made through the primary
device even when the ultimate destination is a
secondary device.
The primary device controls the link; the secondary
devices follow its instructions.
12.68
12.2.2 Polling
It is up to the primary device to determine which
device is allowed to use the channel at a given time.
12.69
12.2.2 Polling
Primary station control frames.
•SEL = select, used by the primary device when it
wishes to send
•POL = used to solicit transmission from
secondary devices
•ACK = acknowledge receipt from a secondary
device
12.70
12.2.2 Polling
Secondary station control frames.
•ACK = acknowledge receipt from primary device
•NACK = non-ACK is used when there is nothing
to send.
12.71
Figure 12.19: Select and poll functions in polling-access method
12.72
12.2.3 Token Passing
Stations in this network are organized in a logical
ring: there is a predecessor and a successor to each
node.
The predecessor is the station which is logically
before the station in the ring;
the successor is the station which is after the station in
the ring.
12.73
12.2.3 Token Passing
The predecessor is the station which is logically
before the station in the ring; the successor is the
station which is after the station in the ring.
12.74
12.2.3 Token Passing
A special packet called a token moves from station to
station.
A station can only send messages while it holds the
token.
The token can be held for a limited amount of time
before it is sent to the successor
12.75
12.2.3 Token Passing
The token can be held for a limited amount of time
before it is sent to the successor
… priorities can be configured by setting a different
holding time for each station.
12.76
12.2.3 Token Passing
The dual ring, common with the FDDI
implementation, allows for some redundancy if there
is a failure on one of the rings.
12.77
12.2.3 Token Passing
Each node on the ring must be able to re-generate the
token if the token is lost or damaged.
12.78
12.2.3 Token Passing
The ring is vulnerable to loss of a station unless the
star ring is used. The central hub of a star ring is
called an MAU (multi-access unit)
12.79
12-3 CHANNELIZATION
Channelization is a multiple-access
method where the available bandwidth of a link
is shared among stations by
1. time
2. frequency
3. code
12.80
12-3 CHANNELIZATION
Three common channelization protocols are:
TDMA = Time Division Multiple Access
FDMA = Frequency Division Multiple Access
CDMA = Code Division Multiple Access
12.81
12.3.1
FDMA divides
frequency bands.
FDMA
the
available
bandwidth
into
Each station is allocated a band of frequencies for
data transmission.
12.82
FDM vs FDMA
FDM is at the physical layer, combining low
bandwidth channels into a high bandwidth
channel.
Used for the first generation analog mobile
phone system.
FDM vs FDMA
FDMA is at the data-link layer.
Each station always uses the same band.
Each stations transmits over the shared link
media without a multiplexer.
Bandpass filters are used at the stations to
separate the signals.
12.3.1
FDMA
Each station is allocated a band to send its data.
Each station also uses a bandpass filter to confine the
transmitter frequencies.
Satellite communications and the cellular phone
AMPS use FDMA.
12.85
Figure 12.21: Frequency-division multiple access (FDMA)
12.86
12.3.2 TDMA
Time-Division Multiple Access (TDMA) is where
stations share bandwidth in time.
12.87
12.3.2 TDMA
Each station is allocated a time slot during which it
can send data.
Each station transmits its data in its assigned time
slot.
This requires all the stations be synchronized
12.88
12.3.2 TDM vs TDMA
TDM operates at the physical layer.
– Low bandwidth channels are combined into a
high bandwidth channel using a multiplexer.
12.89
12.3.2 TDM vs TDMA
TDMA operates at the data-link layer.
– Stations transmit through one shared channel
– Each station transmits when its assigned time
slot is available.
12.90
12.3.2 TDM vs TDMA
TDMA is used for digital cellular systems using GSM
(Global System for Mobile Communication)
TDMA became available with the 2nd generation
mobile phone service (2G).
12.91
Figure 12.22: Time-division multiple access (TDMA)
12.92
12.3.3 CDMA
Code-division multiple access
conceived several decades ago.
(CDMA)
Advances in electronic technology have
implementation possible.
12.93
was
made its
12.3.3 CDMA
CDMA differs from FDMA and TDMA in that all
stations transmit simultaneously each using all the
available frequency bandwidth.
12.94
Figure 12.23: Simple idea of communication with code
12.95
Figure 12.24: Chip sequences
12.96
Chip properties
Length of the chip is the number of stations
sharing the link.
The dot product of any two different chips is
zero.
The dot product of a chip with itself is n,
where n = number of communicating
stations.
Figure 12.25: Data representation in CDMA
12.98
Figure 12.26: Sharing channel in CDMA
12.99
Figure 12.27: Digital signal created by four stations in CDMA
12.100
Figure 12.28: Decoding of the composite signal for one in CDMA
12.101
Figure 12.29: General rules and examples of creating Walsh tables
12.102
Walsh Table
Each chip is read from a row in the Walsh
table.
Example 12.6
Find the chips for a network with
a. Two stations
b. Four stations
12.104
Example 12. 7
What is the number of sequences if we have 90 stations in
our network?
12.105
Example 12.8
Prove that a receiving station can get the data sent by a
specific sender if it multiplies the entire data on the channel
by the sender’s chip code and then divides it by the number
of stations.
12.106