Modeling Networks as Graphs
advertisement
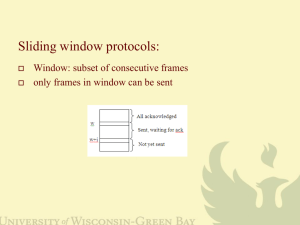
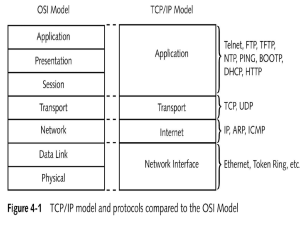
MODELING NETWORKS AS GRAPHS By Sudheer kovi TOPICS COVERED ARE: 1)Network Protocols. a) Stop-and-Wait b) Alternating Bit Protocol c) Sliding Window Protocol d) Transmission Control Protocol 2)Modeling Networks as Graphs. Network? It is a process of inter connection, it can be both connection oriented or wireless. The Need for Networks? Transferring data from one end to the other, either in the form of signals or packets of data. NETWORK PROTOCOLS The job of a network is to enable efficient and reliable communication between hosts, and these protocols are mainly designed for solving the problems like Error control, Flow control, Bandwidth limitation. 1. Error control : while transmitting the data the messages can be lost, corrupted or reordered. 2. Flow control : Incompatibility between the sending and receiving hosts, the receiving host may not be able to process messages as fast as the sending host can send them. 3. Bandwidth limitation : Limitation on the speed in which data is being transferred, if its more or less than the required bandwidth data could be lost. To solve these problems acknowledgement is one of the finest solution, protocol stack is the best way to explain this. Application layer: (World Wide Web and Email) HTTP,SMPT Transport layer: (Transmits messages between client and server) TCP,UDP Network layer: (Relays messages through a series of switches from source to destination) IP Link layer: Transmits messages from one node to the next node Physical layer: Transmits bits across a physical network ETHERNET WIRES,CABLES RADIO FREQUENCY STOP-AND-WAIT Automatic Repeat request (ARQ), is an error control method, and it is a part of stop and wait flow control protocol. If error is detected by receiver, it discards the frame and send a negative ACK (NAK), causing sender to re-send the frame. In case a frame never got to receiver, sender has a timer, where each time a frame is sent, timer is set. If no ACK or NAK is received during timeout period, it re-sends the frame. STOP-AND-WAIT Suppose timeout and sender retransmits a frame but receiver actually received the previous transmission receiver has duplicated copies. A B Frame 0 ACK Frame 1 ACK Frame 2 Timeout Frame 2 ACK Frame 3 Timeout ACK Frame 3 ACK B receive the Duplicate Frame ALTERNATING BIT PROTOCOL The Alternating Bit Protocol doesn’t add arbitrary subscripts. It add a single control bit to each data message and to each ACK. In this if the sender sends the data D0 to receiver it sends the ACK1 indicating that the sender next data message should be D1. To avoid receiving and accepting two copies of same frame, frames and ACKs are alternatively labeled 0 or 1: ACK1 for D0, ACK0 for D1 The Alternating Bit Protocol does not solve all error control problems. ALTERNATING BIT PROTOCOL SENDER RECEIVER D0 D0 ACK 1 D0 ACK 1 D1 ACK1 D0 ACK1 SLIDING WINDOW PROTOCOL The sliding window protocol can solve wasted bandwidth problems by using more sophisticated ARQ technique. In sliding window protocol sequence number is assigned to the messages that sender sends to receiver. The sliding window protocol begins by choosing a window size W. Data messages are initially entered into a FIFO queue, and the sequence number is assigned, that is maintained by the sender. Sliding window protocol is used sending messages on the internet. The message that have been send are shown in the sender’s queue with dark shade. SLIDING WINDOW PROTOCOL Same in the receiver side the received messages are seen with the dark shade. In this it will not wait for the ACK of message ‘n’ before sending the message n+1 The Sliding window protocol cannot be modeled as a finite state machine because of the need to store the message sequence number. SENDER 0 1 2 3 4 5 6 7 RECEIVER 8 9 10 11 12 13 14 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 0 0 1 2 3 4 5 6 7 8 1 9 10 11 12 13 14 2 A3 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 3 4 0 1 2 3 4 5 6 7 8 5 9 10 11 12 13 14 6 A4 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 TRANSMISSION CONTROL PROTOCOL In the internet protocol stack, the transport layer sits immediately below the application layer. Transmission Control Protocol is the most widely used Internet protocol Web, HTTP, SMPT, FTP, and Telnet. TCP is a two way, reliable, byte stream oriented end-to-end protocol. TCP connection is established by a three step handshake procedure: one host initiates the connection, and the other acknowledges it, and the originator then confirms the acknowledgement. In TCP ones connection is open then data can be transmitted between the two hosts until the connection is closed. TRANSMISSION CONTROL PROTOCOL In this a connection progress through a series of states during its lifetime. The states are : LISTEN, SYN-SEND, SYN-RECEIVED, ESTABLISHED, FIN-WAIT-1, FIN-WAIT-2, CLOSED-WAIT, CLOSING, LAST-ACK,TIME-WAIT, and CLOSED. CLOSED represents the state when there is no Transmission Control Block. The transition in the below diagram has a label of the form <event> / <action>. CLOSED rcv SYN sen SYN, ACK SYN RCVD rcv ACK of SYN x CLOSE snd FIN LISTEN SEND SND SYN CLOSE Delete TCB SYN SENT Rcv SYN, ACK sen ACK ESTEB CLOSE snd FIN rcv FIN snd ACK FIN WAIT-1 rcv FIN rcv ACK of FIN snd ACK x Active OPEN Create TCB snd SYN CLOSE Delete TCB Passive OPEN create TCB CLOSED WAIT CLOSE sen FIN LAST ACK CLOSING FIN WAIT-2 rcv ACK of FIN x rcv FIN TIME WAIT snd ACK Timeout = 2MSL Delete TCB CLOSED rcv ACK of FIN x MODELING NETWORKS AS GRAPHS In this we generally model a network to a graph, in which processors correspond to vertices and links to edges by doing so we can solve many problems associated to it. Let g be a undirected graph with vertices V an edges U . Edges corresponds to laying cables between two vertices. One of the efficient technique to find the minimum spanning tree, we use kruskal’s algorithm. Consider spanning tree T where T(G)-subset of edges of G. Where T has no cycles, G is connected to every other vertex using just the edges in T. MODELING NETWORKS AS GRAPHS In this we have 2ways to determine efficient path. 1. Shortest Path 2. Eulerian Circuit MODELING NETWORKS AS GRAPHS Shortest-Path : Given a weighted graph and two vertices u and v, we want to find a path of minimum total weight between u and v. Length of a path is the sum of the weights of its edges. G is an unweighted, undirected graph. Where u and v are Vertices in G. k ≥ 0, there exists a path from u to v whose length is at most k. MODELING NETWORKS AS GRAPHS Example: Shortest path between ‘S’ and ‘T’ 23 2 s 3 9 18 14 30 15 6 2 6 11 5 5 19 4 6 16 20 7 44 t MODELING NETWORKS AS GRAPHS EULERIAN CIRCUIT: The shortest way to traverse all the links in a network is via an Eulerian Circuit. We check the network to verify that all links are working properly. It describe the network as a graph G. Where vertices corresponds to network nodes. Edges corresponds to network links. Where vertex cover C of a graph G with vertices v, and edges E is a subset of v. In this every edge E touches at least one vertices in C. REFERENCES 1. Automata, Computability and Complexity : theory and application by Rich, Elaine. 2. http://en.wikipedia.org/wiki/Sliding_window_protocol 3. users.ecs.soton.ac.uk/sqc/EL336/CNL-5.pdf THANK YOU