Lab 12 – Cisco Firewall
advertisement

http://webpages.uncc.edu/~tkombol/Classes_2014_Fall/ITIS2110/2110LabSchedule.htm#wk13
Lab 13
◦ In-lab project work time
TA available for help
◦ Will take attendance
◦ Quick lecture on project expectations
◦ Status sheet with signatures due by end of lab period
Lab 14
◦ Project due
◦ Presentations
Brief
overview
Your network is 152.8.0.0/16.
Everyone has the same IP address range
Any address that starts with 152.8 is
considered local.
A local network
Anything else is “outside”
Rules specify source and destination IP
addresses
Rules are for many types of interface
2 styles for IP
◦ Basic (in bound only from a source)
◦ Extended (in and out bound)
We’ll concentrate on the extended IP style
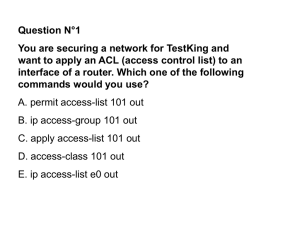
access-list number
{permit | deny}
[protocol]
{any | ipaddr mask | host ipaddr}
{any | ipaddr mask | host ipaddr}
[operator port | established]
[log]
◦
◦
◦
◦
Bold items are entered verbatim
[…] items are optional
{…} must be entered
| denotes “or”
◦ The command must be all on one line
access-list 111 permit tcp any host 152.8.1.10 eq 80
access-list
◦ All firewall configuration ACL commands start with this keyword
number
◦ A number typically between
E.g. IP is 0-99 or 1300-1999, IPX is 100-199 or 2000-2699
Think of it as the name of the list
Number range implies type of protocol involved
permit or deny
◦ Whether to permit or deny this packet of information if
conditions match
protocol (optional)
◦ Type of protocol for this packet: IP, ICMP, SNMP, UDP or TCP
If omitted, then this command pertains to all network traffic
regardless of protocol
Source Address
◦ Internet address of the sender of the packet
◦ Can be:
any - This access command applies to packets from any source
host ipaddr - Command applies to one particular computer
IP address of the computer
Dotted decimal format (i.e. 152.8.1.2)
ipaddr mask – “sub-net” range affected
IP network address of the packet's source
Dotted-decimal format
Followed by a mask (dotted-decimal format)
When comparing the packet's source address, any address bit whose
mask bit is one is ignored
152.8.12.47 0.0.255.255
represents all IP addresses whose first 16 bits match
Destination Address
◦ Internet address of the network packet's destination
Specified in the same three formats as the source address
Operator (optional)
◦ Applies to TCP or UDP ports only
◦ Indicates how the port number in the packet should be
compared
◦ If omitted, command applies for all ports
eq
lt
gt
neq
range
equal
less than
greater than
not equal
a range of ports
Must specify two different port numbers
est
established connections
Allows packets to pass through the firewall from the
Internet if they are the response to a connection
established from within the intranet
Port (optional)
◦ TCP/UDP destination port number
◦ If omitted, command applies for all port numbers
◦ Port number must be specified if an operator is given
Log (optional)
◦ Whether to log this entry to the console
Commands are case insensitive
◦ Note: all access-list commands must fit on one line
◦ Comments can be included configuration
Comments start with an exclamation point ( ! )
Examples:
◦ access-list 111 permit tcp any host 152.8.1.10 eq 80
Permits any computer on the Internet to connect to the
computer whose
IP host address is 152.8.1.1
uses the TCP protocol
port 80
◦ access-list 123 deny any 178.22.8.9 0.0.255.255
This will prohibit any computer from accessing a computer on
the 178.22 domain using any protocol
When a packet arrives at your firewall
◦ it will be compared with each access-list statement
in the order they appear
The first statement that applies to that
packet determines if it is permitted or denied
For incoming traffic
◦ Implicit deny everything else at the end of the
access-lists
For outgoing traffic
◦ Implicit permit everything else at the end of the
access-lists
IP address format:
any
host 152.8.1.10
matches one IP address
152.8.1.1 0.0.255.255
matches anything
matches a (sub)network
Note: the Cisco netmask is backwards from what you're used to!
Called an inverse mask
0's mean "don't care"
access-list 101 deny tcp any 152.8.0.0 0.0.255.255 eq 80
Block all incoming TCP traffic to port 80
“any” is the source address
“152.8.0.0 0.0.255.255” is the destination.
In this case, it refers to any IP address that starts
with 152.8.
This blocks packets from entering your
network from outside
Protects your internal or rogue Web servers
access-list 101 deny tcp 152.8.0.0 0.0.255.255 any eq 80
Block all outgoing TCP traffic to port 80
“152.8.0.0 0.0.255.255” is the source
“any” is the destination.
block all packets from the local network to
the everything on port 80 outside
access-list 101 allow tcp any host 152.8.1.10 eq 80
access-list 101 deny tcp any 152.8.0.0 0.0.255.255 eq 80
Block all incoming port 80 traffic EXCEPT traffic to
our Web server
152.8.1.10
152.8.0.0 0.0.255.255
Second rule blocks packets from outside to all inside
A packet going to the Web server
First rule permits packets to the Web server
Matches the first rule and stops being processed
Packet allowed to go to the Web server
A packet going anywhere else
Doesn't match the first rule, so it gets caught by the second
rule
It is denied, or blocked
We don't want employees in a certain subnet
reading Reddit while at work. Block packets
from 152.8.100.0/24 to www.reddit.com
(72.246.25.35)
access-list 101 deny tcp 152.8.100.0 0.0.0.255 host 72.246.25.35
Note: we're only interested in IP addresses starting with
152.8.100, so the netmask is 0.0.0.255
The ACLs are for an interface
◦ E.g for a specific Ethernet port (plug)
For extended IP rules need ACLs:
◦ For the outward facing ports (the internet)
◦ For the internal ones
Each rule needs source and destination
addresses
The protocol for a service isn't always TCP
The number after “access-list” isn't important
DNS, for example, uses UDP
You can leave out the protocol entirely to operate on
all protocols.
Can use the same number for every rule
Should use a number for the type of rule
Any incoming packets not covered by a rule
are blocked by default
Any outgoing packets not covered by a rule are
allowed by default
Mode
Access Method
Prompt
User Exec
Begin a new session
Router>
Privileged Exec
Enter enable from user Exec
Router#
Global Configuration
Enter configure from privileged Exec
Mode
Enter interface FastEthernet number
from global mode
Router(config)#
Interface Configuration
Router(config-if)#
•These Cisco IOS command modes are hierarchical.
•When you begin a router session, you are in user EXEC mode.
•You can see a list of available commands for a particular mode by entering a question
mark (?) at the prompt.
When the 850 is reset:
◦ Get a default UID of “cisco” and PW of “cisco”
◦ One time use only!
◦ Must create a new user for use next time
restart/login
Otherwise will need to reset the router and start all
over again!
Minicom
◦ Don’t forget to turn line wrap on!
When first started or reset the Cisco 850
router does absolutely nothing
Must turn on and configure services
◦ Enable NAT
◦ Enable and configure DHCP
◦ Set up ACLs (Access Control Lists)
This lab will use Minicom to configure the
router through the serial port
Answer the questions and the items marked **
Work in pairs
When “fresh from the box” or reset:
◦ The router is a brick
Does nothing
◦ Needs to be configured
Includes new ID and PW
Optional:
◦ Turn in copy of lab with comments
Only if errors or incomplete instructions
Short paper describing the lab with an
introduction, body and summary
Answer the questions and the **ed items