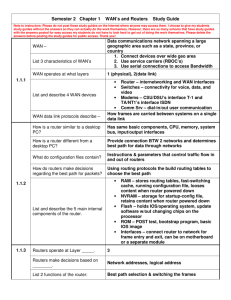
WAN topology
Network design
WAN topology
Topic 5
Agenda
•
Enterprise topology
•
Functions and components
•
Security
•
Design goals
•
Physical standards
•
Topologies
•
WAN link types
Enterprise Composite Network Model
• A hierarchal and scalable blue-print for network designers
• Enterprise campus
– The elements for network operation within one campus (building)
– Designed to provide high availability, scalability, and flexibility
– Includes a campus backbone, a server farm, building access and building distribution modules and a network management module
• Enterprise edge
– Efficient and secure communication between the enterprise campus and remote locations, business partners, mobile users, and the Internet
– Aggregates connectivity, provides traffic filtering and inspection and routing to the enterprise campus
– Includes WAN, VPN, internet access, and e-commerce modules
• Service provider edge
– Enables communication with other networks
– Uses different WAN technologies and Internet service providers (ISPs)
Enterprise Composite Network Model
Service Providers
• Tier 1 provider
– National or international backbone with at least DS-3, OC-3 to OC-48 connectivity
– All its routes from bilateral peering arrangements
– 24/7 network operations center
– Customers are primarily other providers, but it may support a large enterprise also
• Tier 2 Provider
– Regional or national presence
– High bandwidth backbones and 24/7 operations
– Buys transit (discounted) from a Tier 1 provider for traffic that goes outside the region
– Gets all its regional routes through peering arrangements.
• Tier 3 Provider
– Typically a regional provider for a small or medium-sized region
– Buys transit from multiple upstream providers
– Runs a default-free routing table
• Tier 4 and Tier 5 Providers
– Metropolitan provider multi-homed to two regional providers
– Small, single-homed provider that connects end users via dialup, cable modem, or wireless service
Enterprise edge module
• Edge distribution
– Interface to the enterprise network
– Web security appliances and Intrusion Prevention appliances
• E-commerce
– DMZ security zones with internet facing servers, network services such as DNS, FTP and NTP, email, websites and web portal
– Separates internal and external services such as DNS, intranet and collaboration services
• Internet connectivity
– Safe and secure access to internet for corporate users, and remote users
• Remote access VPN
– Corporate access to remote users such as tele-workers and mobile workers
• WAN
– Wan networks such as Frame Relay and ATM to other sites
– Site-to-site VPNs for branch and partner sites
– Protection services such as Intrusion Protection services
Components
• Inner switch
– Provide connectivity between core and campus VLANs and firewall
• Firewall
– Stateful access control and deep packet inspection
– Controlling user’s internet bound traffic
– Protecting public services in DMZ
• Outer switches
– Provides connectivity between the firewall and the edge router
• Edge routers
– Route traffic from enterprise to the internet via one or more ISPs
– Security such as ACLs and uRPF
• Remote access appliances
– Terminate remote-access VPNs such as SSL and Ipsec VPNs
Design goals for the edge
•
Availability
• Eliminate any single point of failure on the network
– Redundancy
• High availability for internet, extranet, and virtual private network (VPN) with redundant interfaces, standby devices, redundant links and devices
• Reliability by duplicating any required component whose failure could disable critical applications – a channel service unit (CSU), a power supply, a WAN trunk, internet connectivity
– Affordability
• Trade-offs may be required
Design goals for the edge
• Backup paths
– How much capacity does the backup path support?
– How quickly will the network begin to use the backup path?
– Common for a backup path to have less capacity than a primary path and use different technologies
– Automatic failover is necessary for mission-critical applications
– What about the cable to the ISP – often the weakest link
• Multi-homing the internet connection
– Providing an enterprise network with more than one entry into the Internet.
• Circuit diversity
– Different carriers sometimes use the same facilities
– Ensure that your backup really is a backup
Design goals for the edge
•
Management
– Configurations
– Monitor traffic flows
– Monitor protocol and process efficiency
– Security baselines
• Device access
• Routing security
• Device resilience
• Policy enforcement
Designing process
•
What are the business and technical goals for the Enterprise Edge?
– Who are the user communities?
– What is the health of the existing network?
– Where are the traffic flows?
•
What technologies?
•
What topology?
•
What link type?
Security and remote access
• Business and technical goals
– Confidentiality and privacy
– Integrity
– Availability
• Security technologies
– Security zones, ACLs and network address translation
– Access control
• AAA services
• Auditing
– Protection
• Application inspection
• Monitoring and intrusion protection
– Privacy
• Encryption
• Remote access
– Remote access VPNS, SSL and Ipsec VPNS
– Site-to-site VPNS
WAN topologies
• Full mesh
– Every router is connected to every other router for complete redundancy
– Good performance because there is just a single link delay between any two sites
– The number of links in a full-mesh topology is
• (N * (N – 1)) / 2
– Expensive to deploy and maintain, hard to optimize, troubleshoot, and upgrade
– Scalability limits for groups of routers that broadcast routing updates or service advertisements (20% broadcast rule)
• Partial mesh
– Not every router is connected to every other router
– Compromise solution
• Partial redundancy
• Less cost
• Less performance as some destinations might require traversing intermediate links
• Hub and spoke (Star)
– Common hierarchical design
– Destinations are reached via the ‘hub’
• Peer
– No redundancy, least expensive, easiest setup
Choosing a WAN link connection
• What is the purpose of the WAN?
• What is the geographic scope?
• What are the traffic requirements? Type, volume, quality and security
• Should the WAN use a private or public infrastructure?
• For a private WAN, should it be dedicated or switched?
• For a public WAN, what type of VPN access do you need?
• Which connection options are available locally?
• What is the cost of the available connection options?
WAN link connection methods
•
Private
– Dedicated
• Leased lines Point-to-Point and Point-to-Multipoint PPP HDLC
– Switched
• Circuit Switched, PSTN, ISDN
• Packet Switched, Frame Relay, X.25, ATM (cells)
•
Public
– Internet
• DSL, cable, broadband wireless
• Satellite
• Metro Ethernet
Leased lines
• Permanent dedicated connections leased from carrier
– T1 1.544 Mb/s
– T3 44.736 Mb/s
– E1 2.048 Mb/s (Australia)
– E3 34.064 Mb/s (Australia)
• A router serial port is required for each leased line connection.
• A CSU/DSU and the actual circuit from the service provider are also required.
– CSU/DSU is a Channel Service Unit/Data Service Unit that terminates T1/E1 carrier lines
• Lower latency and jitter
• No call setup required
Public networks
• DSL
– Always-on connection technology that uses existing PSTN infrastructure and DSL access multiplexer (DSLAM) at the provider location
– Varying data rates of up to 8.192 Mb/s and distance limitations
• Cable
– Always-on connection that uses existing cable TV infrastructure
– Bandwidth shared by users
• Broadband wireless – WiMax
– High-speed broadband service over metro distances for many users
– Provides broad coverage like a cell phone network
• Satellite
– Rural users, upload speed is about one-tenth of download speed
– Satellite dish, two modems (uplink and downlink), and coaxial cables
• Metro Ethernet
– Reduced expenses and administration
– Easy integration with existing networks
Circuit switching
• Establishes a circuit between hosts before communication can start
• Initial very fast call setup to establish a dedicated circuit or path which cannot be used by others until call tear down
• ISDN
– Time-division multiplexed (TDM) digital signals
– Uses 64 kb/s bearer channels (B) for carrying voice or data and a signaling, delta channel (D) for call setup and call management
– Basic Rate Interface (BRI)-ISDN is intended for the home and small enterprise and provides two 64 kb/s B channels and a 16 kb/s D channel
– Primary Rate Interface (PRI)-ISDN provides 30 B channels and one D channel, for an E1 link of 2.048 Mb/s
• ISDN links are used by enterprises as an extra capacity and backup link
Packet switching
• Packets are routed individually and can follow different paths to destination and arrive out of order
• Connection oriented packet switching verifies the existence of the destination with a 3-way handshake
• Frame Relay
– Permanent and shared connectivity for voice and data traffic using virtual circuits (up to 4 Mbp/s)
– Frame Relay is ideal for connecting enterprise LANs
• Asynchronous Transfer Mode (ATM)
– Small, fixed-length cells carrying data, voice and video traffic over private and public networks
Physical WAN serial standards
•
Standards to define how to transmit and receive signals
– EIA/TIA-232
– EIA/TIA-449
– EIA-530
– High-Speed Serial Interface (HSSI)
– V.24
– V.35
– X.25
– X.21
– G.703
Agenda
•
Enterprise topology
•
Functions and components
•
Security
•
Design goals
•
Physical standards
•
Topologies
•