Common RECON Recommended Controls
advertisement
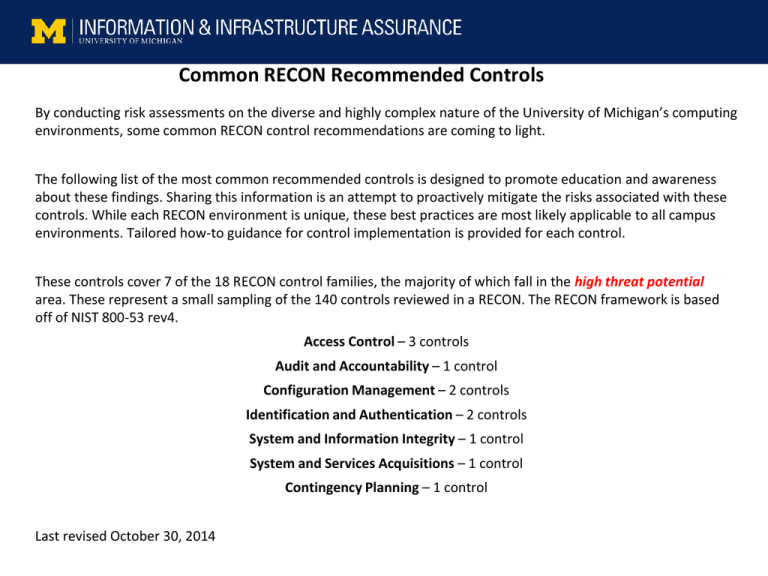
Common RECON Recommended Controls By conducting risk assessments on the diverse and highly complex nature of the University of Michigan’s computing environments, some common RECON control recommendations are coming to light. The following list of the most common recommended controls is designed to promote education and awareness about these findings. Sharing this information is an attempt to proactively mitigate the risks associated with these controls. While each RECON environment is unique, these best practices are most likely applicable to all campus environments. Tailored how-to guidance for control implementation is provided for each control. These controls cover 7 of the 18 RECON control families, the majority of which fall in the high threat potential area. These represent a small sampling of the 140 controls reviewed in a RECON. The RECON framework is based off of NIST 800-53 rev4. Access Control – 3 controls Audit and Accountability – 1 control Configuration Management – 2 controls Identification and Authentication – 2 controls System and Information Integrity – 1 control System and Services Acquisitions – 1 control Contingency Planning – 1 control Last revised October 30, 2014 Common RECON Recommended Controls High Threat Potential CONTROL Access Control – 3 controls The intent of this control family is to align with the premise that: “Organizations must limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems) and to the types of transactions and functions that authorized users are permitted to exercise.” CONTROL TITLE AC-2 AC-3 ACCESS CONTROL POLICY AND PROCEDURES ACCOUNT MANAGEMENT ACCESS ENFORCEMENT AC-4 INFORMATION FLOW ENFORCEMENT AC-5 AC-6 SEPARATION OF DUTIES LEAST PRIVILEGE AC-7 UNSUCCESSFUL LOGIN ATTEMPTS AC-8 AC-9 AC-11 AC-12 SYSTEM USE NOTIFICATION PREVIOUS LOGON SESSION LOCK SESSION TERMINATION AC-14 PERMITTED ACTIONS WITHOUT IDENTIFICATION OR AUTHENTICATION AC-16 AC-17 AC-18 SECURITY ATTRIBUTES REMOTE ACCESS WIRELESS ACCESS AC-19 ACCESS CONTROL FOR MOBILE DEVICES AC-20 USE OF EXTERNAL INFORMATION SYSTEMS AC-22 PUBLICLY ACCESSIBLE CONTENT AC-1 Common RECON Recommended Controls AC-2 Account Management Control Implementation Guidance: Account management protocols that address the management of accounts, including the creating, activating, modifying, review, disabling and removing of accounts, must be maintained. Accounts include: individual, group, application and system accounts. Administrators must be notified when: 1. Personnel events that will affect account status (e.g., hiring, transfer or termination); 2. Events that will affect the status of other types of accounts; 3. Security incidents which compromise accounts and will require immediate action. Reference the Institutional Data Resource Management Policy (SPG 601.12 ), Information Security Policy (SPG 601.27 ), and Privacy and the Need to Monitor and Access Records (SPG 601.11 ). For additional information visit the Identity and Access Management website. Common RECON Recommended Controls AC-8 System Use Notification (Logon Banner) Control Implementation Guidance: Institute standard system use banner that references acceptable use policies, such as: “By your use of these resources, you agree to abide by the Proper Use of Information Resources, Information Technology, and Networks at the University of Michigan (SPG 601.07), Privacy and the Need to Monitor and Access Records (SPG 601.11), in addition to all relevant state and federal laws.” AC-9 Previous Logon Notification (Access) Control Implementation Guidance: Display the date, time, and preferably IP of the last successful user’s logon. In the UMROOT Active Directory there is a domain controller GPO setting which can be enabled on the individual systems. The setting is “Display information about previous logons during user logon”. Common RECON Recommended Controls High Threat Potential CONTROL CONTROL TITLE AU-1 AUDIT AND ACCOUNTABILITY POLICY AND PROCEDURES The intent of this control family is to align with the premise that: AU-2 AUDIT EVENTS “Organizations must: (i) create, protect, and retain information system audit AU-3 CONTENT OF AUDIT RECORDS records to the extent needed to enable the monitoring, analysis, AU-4 AUDIT STORAGE CAPACITY investigation, and reporting of unlawful, unauthorized, or inappropriate AU-5 RESPONSE TO AUDIT PROCESSING FAILURES AU-6 AUDIT REVIEW, ANALYSIS, AND REPORTING AU-7 AUDIT REDUCTION AND REPORT GENERATION AU-8 TIME STAMPS AU-9 PROTECTION OF AUDIT INFORMATION Audit and Accountability – 1 control information system activity; and (ii) ensure that the actions of individual information system users can be uniquely traced to those users so they can be held accountable for their actions.” AU-11 AUDIT RECORD RETENTION AU-12 AUDIT GENERATION Common RECON Recommended Controls AU-2 Audit Events (System and Application Logging) Control Implementation Guidance: Enable logging of security and/or auditing events on systems that store or process sensitive data. Security events may include: account creation, account modification, password changes, failed or successful logon, and file last access time. Note: While enabling file last access time is extremely beneficial in forensic investigations there maybe system degradation in doing so, use this setting (fsutil behavior set disablelastaccess 0) with caution. Send security and/or audit logs to a centralized logging server. A centralized logging server in your organization may be a simple syslog host or you could consider using a more robust commercial product solution such as Splunk. Examples of a particularly useful log file(s) to be sent to a syslog host include: ● Windows systems Application, Security and System log files; ● Mac systems the audit logs are usually located in /private/var/audit; ● Linux hosts sudo action log file. Common RECON Recommended Controls High Threat Potential CONTROL Configuration Management – 2 controls CM-1 CONTROL TITLE CONFIGURATION MANAGEMENT POLICY AND PROCEDURES The intent of this control family is to align with the premise that: CM-2 BASELINE CONFIGURATION “Organizations must: (i) establish and maintain baseline configurations and CM-4 SECURITY IMPACT ANALYSIS inventories of organizational information systems (including hardware, CM-6 CONFIGURATION SETTINGS software, firmware, and documentation) throughout the respective system CM-7 LEAST FUNCTIONALITY development life cycles; and (ii) establish and enforce security configuration settings for information technology products employed in organizational information systems. “ CM-8 INFORMATION SYSTEM COMPONENT INVENTORY CM-10 SOFTWARE USAGE RESTRICTIONS CM-11 USER-INSTALLED SOFTWARE Common RECON Recommended Controls CM-6 Configuration Settings Control Implementation Guidance: The system should have a configuration document or checklist that describes how the system is configured and the system’s purpose/function. The checklist should list IP information, any open ports, system accounts, patching testing and implementation practices and describe the systems backup settings. The system should also be monitored for any changes. Tripwire is an open source solution for monitoring the changes in a systems environment. Reference: http://sourceforge.net/projects/tripwire. CM-7 Least Functionality Control Implementation Guidance: Only enable services in Information Systems that are deemed necessary for required business functions (services). To confirm the open services/ports on a host, run an NMAP scan against the host. Reference: http://nmap.org Supplemental Guidance: For example, do not enable a File Transfer Protocol server if there is no business need to have a FTP (File Transfer Protocol) service. When applicable, consider using a secure protocol over a non secure protocol. If there is a need for a file transfer service, consider the sFTP (Secure File Transfer Protocol). Also, access should be limited to clients who actually need to utilize this service e.g., limit the incoming connections from an approved IP address or authorized networks. For off-campus connections, consider restricting access to the Virtual Private Network (VPN). Common RECON Recommended Controls High Threat Potential Identification and Authentication – 2 controls CONTROL IA-1 The intent of this control family is to align with premise that: “Organizations must identify information system users, processes acting on IA-2 behalf of users, or devices and authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational information systems. “ IA-3 IA-4 IA-5 IA-6 IA-7 IA-8 CONTROL TITLE IDENTIFICATION AND AUTHENTICATION POLICY AND PROCEDURES IDENTIFICATION AND AUTHENTICATION ORGANIZATIONAL USERS DEVICE IDENTIFICATION AND AUTHENTICATION IDENTIFIER MANAGEMENT AUTHENTICATOR MANAGEMENT AUTHENTICATOR FEEDBACK CRYPTOGRAPHIC MODULE AUTHENTICATION IDENTIFICATION AND AUTHENTICATION NONORGANIZATIONAL USERS Common RECON Recommended Controls IA-2 Identification and Authentication Organizational Users Control Implementation Guidance: Unique identifiers (uniqnames) should be used whenever possible. Users must also abide by Identity Misrepresentation (SPG 601.19 ) along with Proper Use of Information Resources, Information Technology, and Networks at the University of Michigan (SPG 601.07 ). Enhanced consideration of two factor authentication should also be made. The two factor solution at U-M is known as MToken. Two factor should be considered for use with administrator and other privileged accounts and/or activities. Contact the ITS Service Center for assistance with installation. IA-5 Authenticator Management (Passwords) Control Implementation Guidance: Do NOT use default passwords in systems and/or applications. A process must be in place to ensure that default vendor passwords are changed prior to the deployment of the devices or applications. Some operating systems and applications require you to set an initial password upon installation. Passwords should also meet the minimal standards as described in the ITS document Choosing and Changing a Secure UMICH Password (R1162). Minimum standards include using nine or more characters, and having at least three of these: lowercase, uppercase, numerals and punctuations. Also, the password must not be a simple phrase or contain parts of your name. User’s identity should be verified prior to receiving their initial password. Shared group account passwords must be changed when staffing changes occur. Common RECON Recommended Controls High Threat Potential System and Information Integrity – 1 control CONTROL SI-1 The intent of this control family is to align with the premise that: “Organizations must: (i) identify, report, and correct information and SI-2 SI-3 information system flaws in a timely manner; (ii) provide protection from SI-4 malicious code at appropriate locations within organizational information SI-5 systems; and (iii) monitor information system security alerts and advisories SI-7 and take appropriate actions in response. “ SI-8 SI-12 CONTROL TITLE SYSTEM AND INFORMATION INTEGRITY POLICY AND PROCEDURES FLAW REMEDIATION MALICIOUS CODE PROTECTION INFORMATION SYSTEM MONITORING SECURITY ALERTS, ADVISORIES, AND DIRECTIVES SOFTWARE AND INFORMATION INTEGRITY SPAM PROTECTION INFORMATION OUTPUT HANDLING AND RETENTION Common RECON Recommended Controls SI-2 Flaw Remediation (Vulnerability Management) Control Implementation Guidance: System flaws are identified and corrected. Preform ongoing patching of your systems and applications. To assist your flaw remediation processes vulnerability scans may be requested by sending an email to: iia.vulnscans@umich.edu. Procedures are followed for testing and implementing firmware and software updates. Testing of software and firmware updates should be done prior to the deployment of the patches, especially to production systems. Flaw remediation should be incorporated into the configuration management processes. There are various patch management methodologies which can be part of your configuration management solution. An example for a Windows system would be the use of System Center Configuration Manager (SCCM). In addition to (SCCM), Big Fix is used as a configuration management solution. Common RECON Recommended Controls Medium Threat Potential CONTROL System and Services Acquisitions – 1 control SA-1 The intent of this control family is to align with the premise that: SA-2 “Organizations must: (i) allocate sufficient resources to adequately protect SA-3 organization information systems: (ii) employ system development life cycle processes that incorporate information security considerations; (iii) employ software usage and installation restrictions; and (iv) ensure that third-party SA-4 SA-5 SA-9 CONTROL TITLE SYSTEMS AND SERVICES ACQUISITION POLICY AND PROCEDURES ALLOCATION OF RESOURCES SYSTEM DEVELOPMENT LIFE CYCLE ACQUISITION PROCESS INFORMATION SYSTEM DOCUMENTATION EXTERNAL INFORMATION SYSTEM SERVICES providers employ adequate security measures to protect information, applications, and/or services outsourced from the organization.” Common RECON Recommended Controls SA-3 System Development Life Cycle Control Implementation Guidance: A system development life cycle should be developed and maintained which incorporates information security. The earlier security controls are addressed within the development life cycle, the more effective their implementation will be. It is much less costly to design security from the start, than to retrofit a system once it is deployed. IIA security consulting services can be ordered on the IT Services Portal: http://services.it.umich.edu/it-securityconsulting Common RECON Recommended Controls Medium Threat Potential CONTROL Contingency Planning – 1 control The intent of this control family is to align with the premise that: “Organizations must establish, maintain, and effectively implement plans for emergency response, backup operations, and post-disaster recovery for organizational information systems to ensure the availability of critical information resources and continuity of operations in emergency situations.” CP-1 CP-2 CP-3 CP-4 CP-6 CP-7 CP-8 CP-9 CP-10 CONTROL TITLE CONTINGENCY PLANNING POLICY AND PROCEDURES CONTINGENCY PLAN CONTINGENCY TRAINING CONTINGENCY PLAN TESTING ALTERNATE STORAGE SITE ALTERNATE PROCESSING SITE TELECOMMUNICATIONS SERVICE INFORMATION SYSTEM BACKUP INFORMATION SYSTEM RECOVERY AND RECONSTITUTION Common RECON Recommended Controls CP-2 Contingency Planning Control Implementation Guidance: For systems that are classified as mission critical, a contingency plan should be made available. A system, activity or function can be defined as mission critical if its failure or unavailability, even for a unit-defined short timeframe, will affect essential business or unit operations in an unacceptable way. Mission critical systems, activities, and functions are determined by each unit. If a system, activity, or function's failure can be tolerated longer than the unit-defined time period, it is not mission critical. The plan should list the recovery objectives and restoration priorities. The plan should list the roles, responsibilities and have the participants’ contact information. The plan should be tested and updated as needed on a regular basis. IIA contingency planning consultation services can be ordered on the IT Services Portal: http://services.it.umich.edu/it-security-drbc-planning