Tactical network solutions
advertisement

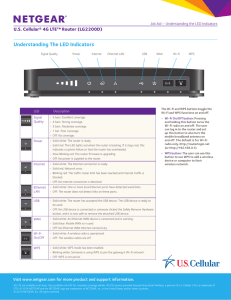
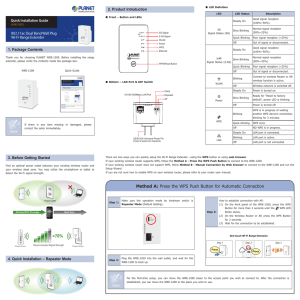
Reaver is the Linux tool used to implement a Brute Force Attack against Wi-Fi Protected Setup registrar PINs in order to recover WPA/WPA2 passphrases. Since 2007 the Wi-Fi Alliance provided industry wide setup solutions for home and small business environments. Allows for typical users with little knowledge of wireless configurations and security settings to configure a new wireless network. By default (out-of-the-box) WPS is always active on all devices. WPS is marketed as being secure, however newly discovered design and implementation flaws allow attackers to gain access. Allows users to enter an 8 digit PIN to connect to a secured network without having to enter a passphrase. When the user supplies the correct PIN the access point essentially gives the user the WPA/WPA2 PSK that is needed to connect to the network. User pushes a button on both the Access Point and new wireless device (e.g. printer, PC, NIC) Internal Registrar User enters WPS PIN of the Wi-Fi adapter into the web interface of the Access Point. External Registrar User enters WPS PIN of the Access Point into the client device (e.g. PC, laptop) Is a WPA attack tool developed by Tactical Network Solutions that exploits a protocol flaw in the Wi-Fi Protected Setup (WPS). This vulnerability exposes a side-channel attack against Wi-Fi Protected Access (WPA) versions 1 and 2 allowing the extraction of the Pre-Shared Key (PSK) used to secure the network. Determine an Access Point's PIN and then extract the PSK and give it to the attacker. An authentication attempt can take between 0.5 and 3 seconds to complete. Once the PIN of the Access Point has been discovered the Access Point then hands the requesting device the passphrase. Cisco/Linksys Buffalo Netgear ZyXEL D-Link Technicolor Belkin Disable WPS, however this may not be available on all devices. Tactical network solutions. (2011). Retrieved from http://www.tacnetsol.com/products