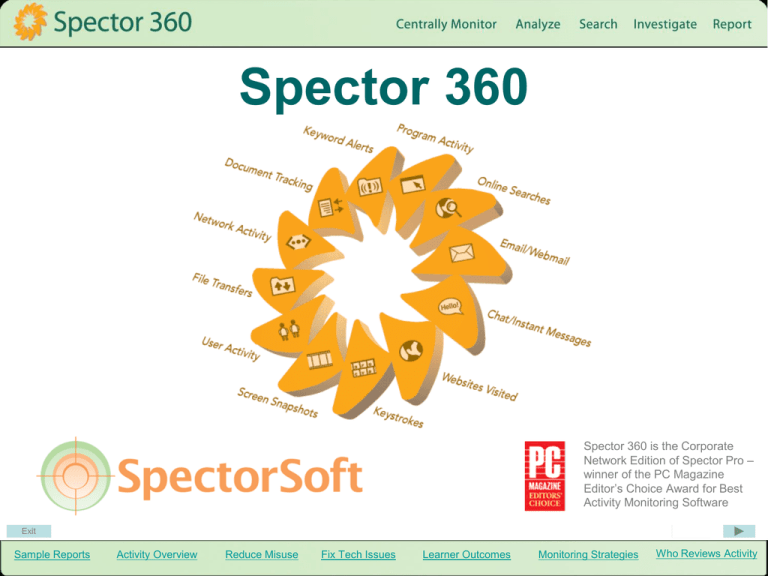
Spector 360
Spector 360 is the Corporate
Network Edition of Spector Pro –
winner of the PC Magazine
Editor’s Choice Award for Best
Activity Monitoring Software
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Reporting
• Websites Visited
• Keystrokes
• Email/Webmail
• Downloads/uploads
• Chat/Instant
Message
• Snapshots
• Program Activity
• Network Activity
• Bandwidth Usage
• Document Tracking
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Reporting
Website Activity
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Website Activity Views
Reporting
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
User Website Detail
Reporting
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Reporting
Network Bandwidth Use
Internet Radio being played
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Network Bandwidth Detail
Reporting
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Network Bandwidth Snapshot
Reporting
This snapshot details adjusting the volume of
Internet radio while working on PowerPoint.
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
User Activity Detail
Reporting
See an interactive demo at http://www.spector360.com/screenshots/UserExplorer/overview.htm
Each tab displays a different type of activity
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Reporting
Keyword Alerts
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Reporting
Sample Reports
These reports represent only a sampling
More can be seen at
http://www.spector360.com/overview/report.htm
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Reporting
Additional Features
• Automated email report delivery
• Monitor files deleted, created, renamed,
printed, transferred (includes files written to CD, DVD or
USB devices)
• Alerts if specified documents are accessed
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
• Red flag irregularities
• See probable cause at a
glance
• Hyperlink to details
“Quick View reports let you
know what’s happening REAL
FAST….For example,…the
Quick View charts are showing
me EXACTLY how many hits
websites are getting. …If you
see a website that shouldn’t be
popular, all you have to do is
click the bar on the chart to find
out what’s going on.”
Robert Haviland, Hickman County Schools
Centerville, Tennessee
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
Miss nothing reporting
Easily spot trends and
irregularities.
e.g., Who seems to be using the
most network bandwidth and why?
“Spector also enabled us to monitor
the time and date students were on
computers as well as all actions
they undertook.”
Music
consuming
bandwidth
Greb Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
Miss nothing reporting
Productivity
What websites are being visited
most frequently and who is
spending the most time browsing
the web? In this example, mlb.com
is a baseball site.
You can drill down to find the
baseball enthusiasts and exactly
how much time they’ve spent.
“The number of students now
engaged in non educational work
on computers is almost nil.”
Greb Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
Miss nothing reporting
Who is transferring the most files?
Productivity
What exactly are they sending out?
Confidential information
To whom are they sending it to?
“The software…enabled us to
monitor the use of USB drives and
other external devices that
previously we did not have access
to.
Students trying to use other
students or staff accounts
has…reduced considerably.”
Greb Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
Miss nothing reporting
Who are the top violators of those
keywords that indicate abuse (e.g.,
sex, bomb, gambling)?
Productivity
Confidential information
Keyword Alerts
“Using key word alerts, we were
able to set flags on files…and
web searching and web
sites…which …would send
notification…that there may be
a breach of…usage policy.
Curse word
The alert list…includes flags for
things like remote desktop,
administrator and other key
staff login codes.”
Curse word
Greg Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
Spot trends
Productivity
Confidential information
What are the top online search
terms being used and do they look
suspicious?
Keyword Alerts
“We discovered…searches
by…students in Google for
keywords such as sex, porn, etc.”
Online search terms
Greg Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
Miss nothing reporting
Productivity
Confidential information
Search for a word/phrase across
the entire user base. e.g., a racial
epithet or sexual term in an
anonymous email.
Keyword Alerts
Online search terms
Lawsuit protection
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Activity Overview
Miss nothing reporting
Productivity
Confidential information
Keyword Alerts
Online search terms
Lawsuit protection
User activity
Who is arriving at work late and
leaving early?
Who is taking frequent breaks and
just how long are they?
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Reduce Computer Misuse
Stop PC and Internet abuse
Provide proof of student identity and activity
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Detect & Stop
These Activities
• Offensive chat/email
• Game playing
• Bullying
• Bypassing web filters
• Threats to students,
teachers, and school
• Student hacking
• Illegal downloads
• Bandwidth abuse
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Offensive chat and email
“First we put the keyword (alert)
list (of inappropriate words) on
the library PCs….The very first
day…the first hour…we had 10
alerts. And there are only 31
PCs in the library, so 1/3 of the
PCs sent alerts the first day.”
Larry Koby, New Castle Community School
New Castle, Indiana
“Several students…managed to
use a bypass proxy web site to
access MSN Messenger.”
Greg Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Offensive chat & email
“At one time, the site (at which
one can insert a person’s name
and it creates a violent image
of that person “destroyed”)
attracted quite a few, but once
a student tried it with Spector in
place, the outcome of the
prank was decidedly different.”
Bullying
Jeff Hunt, Park Rapids Area School District
Park Rapids, Minnesota
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Offensive chat & email
“An uncomplimentary
anonymous web email was
sent to the assistant principal
from a PC within the school
system network.
Bullying
Threats to students,
teachers, school
(A threatening) note (was)
found, (which) was composed
on a PC and printed out.”
Larry Koby, New Castle Community School
New Castle, Indiana
(Note: Spector detects these
activities and identifies the user.)
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Offensive chat & email
“Students were using an ‘antiproxy’ program, bypassing the
content filter by bouncing off
another server. With Spector,
now we can monitor even that.”
Bullying
Threat to students,
teachers, school
Larry Koby, New Castle Community School
New Castle, Indiana
Bypass web filters
“We were seeing sexual sites
visited. But since the
introduction of Spector, we rarely
see anything like that.”
Jeff Hunt, Park Rapids Area School District
Park Rapids, Minnesota
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Offensive chat & email
“We were subject to some
hacking attacks that almost
shut our network down.
Spector allowed us to discover
who the culprits were.
Bullying
Threat to students,
teachers, school
The student body is running
scared because the word is out
that the IT department is now
mysteriously able to find out
which students are causing
havoc in the computer
systems.”
Bypass web filters
Student hacking
Robert Frost, Highland School of Technology
Gaston County, North Carolina
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Offensive chat & email
Bullying
“Students were storing mpeg's
and games on the server and
renaming them to hide them
from being seen in their profiles.
Threats to students,
teachers, school
Bypass web filters
The word spread like wildfire
and it has stopped that kind of
behavior cold.”
Student hacking
Robert Frost, Highland School of Technology
Gaston County, North Carolina
Illegal downloads
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Computer Misuse
Offensive chat & email
“A keystroke logger (was
found) on a library PC. It was
downloaded off the
Internet…(and) capturing
passwords….very frightening
for us.
Bullying
Threats to students,
teachers, school
Bypass web filters
I felt we were protected from
the outside, but were we
protected from ourselves?
Spector showed us we needed
to do more.”
Student hacking
Illegal downloads
Larry Koby, New Castle Community School
New Castle, Indiana
Risk in general
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Resolve Technical Problems
• View error Messages
• Identify malware sources
• Document Procedures
• Save staff time
• Reduce Bandwidth
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Resolve Technical Problems
“The screenshots show
me error messages and
exactly what led up to a
problem.”
View error messages
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Resolve Technical Problems
View error messages
Identify malware sources
“(Students) go to websites and
cookies get placed that change
the behavior of Internet
Explorer. I can discover the
website that caused the
problem and block it for
everyone.”
“I can discover how a virus was
introduced.”
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Resolve Technical Problems
View error messages
Identify malware sources
Document Procedures
“I use the screenshots to
document installations and
configuration changes for later
review.”
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Resolve Technical Problems
Error Messages
Identify malware sources
“The incidents are few and far
between now. And that alone
saves us work. We don’t have
to ‘clean’ the machines as often
as before.”
Jeff Hunt, Park Rapids Area School District
Park Rapids, Minnesota
Document procedures
Save staff time
“We have found that our
support workload is reduced
because the kids don’t try to
crash the PCs any more, and
if a machine does fail, we can
see from the log what was
happening when it failed. This
makes it much easier to fix.”
Fungai Chawira, St Augustine’s High School
London, England
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Resolve Technical Problems
View error messages
Identify malware sources
“It only takes a moment to see
who’s hogging bandwidth. Right
now, on the bandwidth chart, I see
one user bringing down large
amounts of data…. It looks like lots
of music.”
Robert Haviland, Hickman County Schools
Centerville, Tennessee
Document Procedures
“We found a folder with 60-80
songs in it on one of our file
servers … way down deep. We
wouldn’t have found the songs
without Spector.”
Save staff time
Reduce Bandwidth
Todd Kumpola, Rapids Area School District
Park Rapids, Minnesota
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Improve Learner
Outcomes
“The ability to easily monitor, report and follow up on
misuse…has changed student practices and improved
teaching and learning.
…teachers…complained that students were now
completing work in half the time…and they would have to
create additional work for them.”
Greg Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Improve Learner Outcomes
Increase Time on Target
“We discovered about 30% of students
playing games, which are hidden from
teachers’ views as they walk past.”
Greg Gebhardt, Lowanna College
Victoria, Australia
“Instead of playing games, they now
listen to the teacher….
Classroom productivity has absolutely
increased using Spector. Teachers now
feel like they can talk TO the students,
as opposed to having to stand BEHIND
them.”
Jeff Hunt, Park Rapids Area School District
Park Rapids, Minnesota
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Improve Learner Outcomes
Diagnose Student Weaknesses
For example: A student has
poor web search technique
and chooses the first
search entry or paid ads.
You actually see it happen.
“If a teacher believes that a
particular child has not been
concentrating in class…he can
come to us after the lesson and
ask to see the record of the
child’s activity during the
lesson.”
Fungai Chawira, St Augustine’s High School
London, England
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Improve Learner Outcomes
Assess Understanding
Teachers can watch the learning process by reviewing
assignments, email and chat conversations.
Instant Messaging Example
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Improve Learner Outcomes
Expose Dishonesty
Review communications for suspicious activity.
Email Example
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Example of Plagiarism
Improve Learner Outcomes
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
• Deterrence
• Detection
• Investigation
• Discipline
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Deterrence
In a study of high school computer use,
off-task activity immediately declined 67%
after students viewed a monitoring
announcement at each login, which
included sample reports.
After scofflaws were disciplined and word
spread, median off-task activity declined
94%.
Results demonstrated that a highly visible
detection strategy and vigorous
enforcement of Acceptable Use Policy
significantly deters unacceptable
computer activity.
“With evidence of inappropriate PC
activity, a student is confronted. Word
then spreads like wildfire, and the end
result is productivity increases and the
incidence of malicious actions drops
to near zero.”
Jeff Hunt, Park Rapids Area School District
Park Rapids, Minnesota
“It’s a lot easier to fight off temptation
when you know there are
consequences. Spector is like radar,
or an unmarked car. It keeps the good
kids good.”
South Plainfield H.S., Plainfield, Illinois
Larry Koby, New Castle Community School
New Castle, Indiana
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Deterrence
“The keyword alert feature is really
wonderful. the very first day … the first
hour … 1/3 of the PCs sent alerts.
These were Word documents with
inappropriate language.”
Larry Koby, New Castle Community School
New Castle, Indiana
Detection
“Two students…had staff passwords
and…used these to have unrestricted
access to parts of the internet and more.”
Greg Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Deterrence
“The Principal called us to get the
information and - with a Spector
snapshot - we did. The guilty student
was caught.”
Detection
Jeff Hunt, Park Rapids Area School District
Park Rapids, Minnesota
Investigation
“Being able to print a copy of what the
student has typed is proof enough and
amazes the student that we have the
information.”
Dean Edwards, Maxwell Adventist Academy
Kenya
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Deterrence
“And because Spector provides who,
what, when, and where, we were able to
go to the Assistant Principal, who started
calling students into the office.”
Larry Koby, New Castle Community School
New Castle, Indiana
Detection
Investigation
“Some students didn’t believe the hype
and next week were amazed when they
were called into the office and shown
why we had removed them from the
network.”
Greg Gebhardt, Lowanna College
Victoria, Australia
Discipline
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Investigation Example
•
Spector 360 Quick View panels and
alerts show probable cause.
•
In-depth review of the student follows.
•
Visual evidence is sent to the assistant
principal.
•
The student is shown the evidence and
is disciplined.
•
The student spreads the word, which
deters other students from violating
Acceptable Use Policy.
Monitoring Strategies
“One student was repeatedly
trying to access porn sites,”
said Haviland. “With Spector
360 and its keyword alerts, I
received reports on it all. We
kept records, took them to
the assistant principal, and
the student went to ISS (InSchool Suspension). The
other kids heard about it and
that cut down that activity A
LOT!”
Robert Haviland, Hickman County Schools
Centerville, Tennessee
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Methods
• Random monitoring
• Upon request
• Formal investigations
• Keyword alerts
• Automated reporting
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Review of a student’s
computer use
Random monitoring
Only 10 minutes to review a
week’s activity
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
When inappropriate
behavior is suspected
Random monitoring
Examples:
Upon request
• Poorly done
assignments
• Switching screens when
you walk by
• Complaints by students
• Suspicious activity
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Serious violations
Random monitoring
• Cheating
Upon request
• Racial, Sexual harassment,
bullying
• School and teacher threats
Formal Investigations
“…video dumps have been used as
evidence for law enforcement in cases
of cyberbullying and…selling of illegal
goods on eBay.”
Greg Gebhardt, Lowanna College
Victoria, Australia
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Random monitoring
Receive immediate email
notification of words and
phrases detected in:
Upon request
• Email
Formal Investigations
• Instant Messages
• Websites
Keyword Alerts
• Keystrokes
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Monitoring Strategies
Random monitoring
Upon request
Formal Investigations
Keyword Alerts
Reports
(print, email, export, automated delivery)
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Who Reviews Activity
• IT Staff
• Teachers
• Administrators
• Parents
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Who Reviews Activity
“In this case, the Principal
called us to get the information
and - with a Spector snapshot
- we did. The guilty student
was caught.”
IT staff
Larry Koby, New Castle Community School
New Castle, Indiana
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Who Reviews Activity
“The persons in charge are able
to view the PCs they are in
charge of... They get the alerts,
they do the viewing, and they
take the appropriate action.
IT staff
Teachers
Spector has been an eye-opener
for teachers…. (they) are not
being circumvented, and they
appreciate that.”
Larry Koby, New Castle Community School
New Castle, Indiana
“I get keyword alerts emailed to me,
then I send a message to the
responsible teacher.”
Robert Haviland, Hickman County Schools
Centerville, Tennessee
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Who Reviews Activity
IT staff
“And because Spector provides
who, what, when, and where, we
were able to go to the Assistant
Principal, who started calling
students into the office.”
Teachers
Administrators
Larry Koby, New Castle Community School
New Castle, Indiana
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Who Reviews Activity
“Spector has enabled us to verify to
parents large downloads…or
printing jobs, when (students) have
made claims to their parents that
others have been using their
account.”
IT staff
Teachers
Greg Gebhardt, Lowanna College
Victoria, Australia
“(Monitoring) is much better than
having parents and students
complaining of harassment as
they have in the past.”
Administrators
Dean Edwards, Maxwell Adventist Academy
Kenya, Africa
Parents
One school automates summary
email reports to each parent.
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
As computers need anti-virus
software, so do they need
monitoring protection software.
“I believe monitoring
software is going to become
a workstation standard. If
you’re not monitoring, I’d say
you have to ask yourself
why.”
Chris Hoerske
Drexel Chemical Company
“Will the time come
when monitoring
software is as
important as anti-virus
software? The time is
here now! You need to
have a tool like
Spector in your
repertoire.”
Regional Credit Union
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity
Exit
Sample Reports
Activity Overview
Reduce Misuse
Fix Tech Issues
Learner Outcomes
Monitoring Strategies
Who Reviews Activity