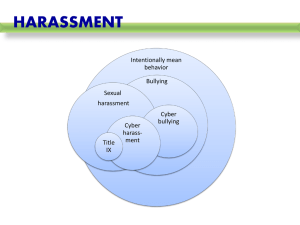
Cyber-Bullying and Online Harassment
advertisement

Cyber-Bullying and Online Harassment: Awareness and Best Practices for Prevention By Edward J. Lazaros, Ph.D. Department of Technology Ball State University Muncie, IN 47306 Phone: 765-285-5647 Fax: 765-285-2162 E-mail: ejlazaros@bsu.edu Awareness • School bullying has typically occurred when one individual is in a position of power over another because of a difference in physical strength or stature. • Unlike face-to-face bullying, cyber-bullying can be perpetrated by anyone. bp3.blogger.com Awareness • As Beckerman & Nocero (2003) report “anonymity is a factor in why this form of harassment is growing. Sitting behind a computer working the keyboard gives students a sense of power and control they do not have in a face-to-face situation” (p. 39). blogs.edweek.org Awareness • Cyber-bullying and online harassment are often confused. Smith, Mahdavi, Carvalho, Fisher, Russell, and Tippett (2008) define cyber-bullying as “an aggressive, intentional act carried out by a group or individual, using electronic forms of contract, repeatedly and over time against a victim who cannot easily defend him or herself” (p. 376). • According to Wolak, Mitchell, and Finkelhor (2007), “we do not recommend using the term “bullying” to describe all online interpersonal offenses, because they vary so widely in their characteristics. We suggest using “online harassment,” with disclaimers that it does not constitute bullying unless it is part of or related to offline bullying” (p. 57). Complexity of the Problem • Because students are using technology, it is often difficult to monitor and prevent these incidents. Often, it is difficult to investigate these incidents. • Authorities often have difficulty identifying who is causing the bullying or harassment. www.piquaoh.org Complexity of the Problem • In 2006, Megan Meier started talking to a boy named Josh Evans on MySpace. He claimed to be a 16-year-old boy who lived nearby and was home schooled. • "Megan gets an e-mail, or a message from Josh on her MySpace on Oct. 15, 2006, saying, 'I don't know if I want to be friends with you any longer because I hear you're not nice to your friends,'“ He also posted lies about her online. • Josh never existed. It was 49 year old Lori Drew who was the mother of one of Megan’s former friends. Complexity of the Problem • Keith and Martin (2004) describe why technology purchased to keep children safe may become cyber-bullying or harassment instruments: In the past several years, parents have provided cell phones for their children in order to keep track of them and to keep them safe. The same cell phones that make parents feel more connected to their children have become tools of harassment. And the newest forms of cell phones include the ability to send text messages, pictures, and even live video. In the hands of bored teenagers, these additions can become weapons for bullies to spread rumors as well as pictures of unsuspecting kids in locker rooms (p. 225). Complexity of the Problem • It is often not easy for a school administrator to determine the perpetrator. As Beckerman & Nocero (2003) report, “it changes with each transfer, much like the elementary school game of “telephone” – the end message never matches the original. And, because the original was generated to create anger and frustration, the problem is magnified” (p. 39). • As Beckerman & Nocero report “just when you think you have located the culprit, you find out that the screen name and password have been shared with others or the original screen name has been subtly modified to create confusion. For example, John234 becomes J0hn234” (p. 39). First Amendment Protection • Prior to school administrators intervening and using nonlegal solutions or the resorting to the law to deal with cyber-bullying or online harassment, consideration must first be given to the First Amendment rights of the student perpetrator. • The U.S. Constitution Bill of Rights 1st Amendment does offer protection. According to Madison (1791), “Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the Government for a redress of grievances” (p. 1). First Amendment Protection • A landmark First Amendment case pertaining to free speech in school was Tinker v. Des Moines. • In Tinker v. Des Moines (1969), John Tinker and his siblings wore black armbands to their Des Moines school to protest the Vietnam War. • The principals of the school suspended the children because they felt the armbands would provoke disturbances. • This case was brought before the United States Supreme Court voted seven to two in favor of Tinker, based on the First Amendment to the United States Constitution dealing with free speech, press, and assembly. • The principals did not provide evidence to show that wearing the armbands would substantially interfere with appropriate school discipline. First Amendment Protection • School officials should try to apply the Tinker principle in every situation. They should try to determine if the situation substantially interferes with appropriate school discipline. Failing to do so could be costly for the school. First Amendment Protection • In Dwyer v. Oceanport School District (2005), The United States District Court of New Jersey found that the Oceanport School District in New Jersey had to pay an 8th grade student Ryan Dwyer a $117,500 settlement in 2005 because they violated the First Amendment rights when he was suspended from school in 2003 for a website that he created. www.oceanport.k12.nj.us First Amendment Protection • The website criticized the Maple Place school in Oceanport, New Jersey. The website criticized individual teachers and the school principal as well as a derogatory picture of the school principal. Interestingly, the website made various references to First Amendment rights, including: “This page protected by the U.S. Constitution”, and “Don’t even try to make me take my website down because it is illegal to do so”. He created the website at his house and outside of school hours. The court found that Ryan did not publish any material which could reasonably be expected to cause a material and substantial disruption to the operation of the school. Because of this, he could not be disciplined without violating his First Amendment rights to free speech. First Amendment Protection • Threats of violence are not protected by the First Amendment, so school administrators should also determine if there is violence associated with the cyber-bullying situation. • In Watts v. United States (1969), the Supreme Court said that threats of violence are not protected by the First Amendment. • When a student is involved with a cyber-bullying or online harassment incident that substantially interferes with appropriate school discipline and violence is prevalent, the school will most likely be able to punish the student for his/her actions. First Amendment Protection • In J.S. ex rel H.S. v. Bethlehem Area School District (2002), a student created a web site which had an image of a teacher’s face that changed to resemble Adolf Hitler. The same teacher was depicted with a decapitated head with dripping blood. • The web site requested donations of $20.00 so that a hit man could be hired to kill the teacher. • The Supreme Court in Pennsylvania decided that although the web site was not created at school, the site was aimed at a specific school and it’s personnel and did cause a material disruption when using the Tinker (1969) standard so the student could be punished for the web site. www.wallpaperez.info Best Practices for Cyber Bullying • Hummell (2007) recommends schools develop acceptable use policies (AUPs). • McKinney (n.d.) also emphasizes the importance of an acceptable use policy, “an acceptable use policy will assist staff, students and their parents know and comply with appropriate boundaries” (p. 90). • According to McKinney (n.d.), “disciplinary measures for violating the acceptable use policy or otherwise misusing or abusing the Internet should be listed in the policy and the student handbook” (p. 91). Best Practices for Cyber Bullying • Keith and Martin (2004, p.227) recommend the following Tips for children: • Never share or give out personal information, PIN numbers, phone numbers, etc. • Tell a trusted adult. • Do not read messages by cyber bullies. • Do not delete messages; they can be used to take action. • Bullying through instant messaging and chat rooms can often be blocked. • Do not open a message from someone you don’t know. • Do not reply to the person bullying or harassing you. Best Practices for Cyber Bullying • • • • • • • Keith and Martin (2004, p.227) recommend the following Tips for parents: Pay attention! Know how and when your children are using the Internet. Become more tech savvy. Install blocking or filtering software. Encourage your child to talk to you if they are being bullied. Limit your child’s time using the Internet. Develop a family online agreement Best Practices for Cyber Bullying • Keith and Martin (2004, p.227) recommend the following Tips for schools: • Develop school policies for acceptable Internet and cell phone use. Enforce them. • Zero tolerance for bullying in any form. • Ensure that children and young people are aware that all bullying concerns will be dealt with sensitively and effectively. • Ensure that parents / guardians expressing bullying concerns have them taken seriously. Closing Recommendation! • Do what you do best as technology teachers! Educate students about cyber-bullying and online harassment. This is one way to make positive inroads to curb these problems in the educational setting. Works Cited • • • • • • • • • • • Beckerman, L., & Nocero, J. (2003). High-tech student hate mail. Education Digest, 68(6), 37-40. Dwyer v. Oceanport School District No. 03-6005 (2005). Hummel, L. (2007). Cyber-bullying: what is it and how to prevent it. Delta Kappa Gamma Bulletin, 73(3), 26-27. In J.S. ex rel H.S. v. Bethlehem Area School District., 569 A.2d 639 (2002). Keith, S. & Martin, M. (2004). Cyber-bullyng: Creating a culture of respect in a cyber world. Reclaiming Children & Youth, 13(4), 224-228. Madison, J. (1791). United States bill of rights. Philadelphia. McKinney, J. (n.d.). The legal handbook for Indiana school administrators: Educators.cc. Smith, P., Mahdavi, J., Carvalho, D., Fisher, S., Russell, S., & Tippett, N. (2008). Cyberbullying: its nature and impact in secondary school pupils. Journal of Child Psychology and Psychiatry, 49(4), 376-385. Tinker v. DesMoines School Dist., 393 U.S. 503 (1969). Watts v. United States, 394 U.S. 705 (1969). Wolak, J., Mitchell, K., & Finkelhor, D. (2007). Does online harassment constitute bullying? An exploration of online harassment by known peers and online-only contacts. Journal of Adolescent Health, 46(6), 51-58.