Understanding - SOURCE Conference
advertisement

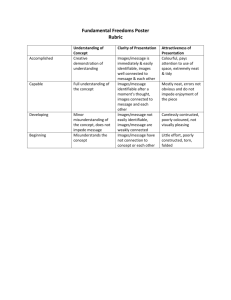
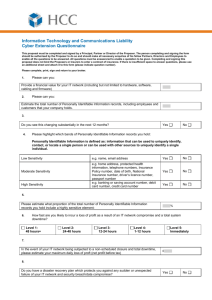
Understanding: The Key to Protecting Highly Sensitive Personally Identifiable Information Timothy J. Brueggemann, Ph.D. Introduction The reliance of organizations on the collection and storing of data HSPII is defined as information which can be used to discern or to trace an individual’s identity either alone or when combined with other information which is held in the public domain Access to information and data is easier than ever to obtain, use, and share Introduction – cont. Lost or stolen laptops Challenges that face an organization today Increase organizational efficiency the protection of the HSPII New perspectives in organizational security have grown from the increased amount of government legislation and increased public awareness. Data security is an area that is one of the most studied, and often the area that is the most confused with a HSPII program. Privacy As a legal right privacy was defined by Samuel D. Warren and Louis D. Brandeis in 1890 as “the right to be let alone” Not currently enacted into law In the 1960s and 1970s congress became increasingly concerned about the amount of data being stored on databases Legislation The Privacy Act of 1974 Health Insurance Portability and Accountability Act (HIPAA) Family Education Rights Act (FERPA) Electronic Communications Privacy Act (ECPA), 18 U.S.C. 2510-2521 Problem Areas Increases in online technology Attacks on privacy occur in many areas Employment Records The Internet Government Databases Corporate Databases The Study Define the level of understanding the IT worker had on HSPII at their organization Four areas reviewed Knowledge of HSPII Program Ascription to Technology Ascription to Technology – Belief Senior Management Involvement The Study – cont. The population for this study was comprised of all IT workers employed by Fortune 500 companies within and outside of the United States. A convenience sample was taken from one large Fortune 500 company. Approximately 8,000 IT employees A random sample of 10% of the IT staff was selected A minimum response rate of 260, 32.5%, was necessary to represent the 800 employees selected to participate Actual response rate was 332 or 41.5% The Study – cont. Six hypotheses were formed for this study. H1: The time in the Information Technology field has a relationship to the Information Technology workers’ understanding of Personally Identifiable Information Programs. H2: The education level of Information Technology employees has a relationship to their understanding of Personally Identifiable Information Programs. H3: The length of time with the company of Information Technology employees has a relationship to their understanding of Personally Identifiable Information Programs. H4: There is a difference in the understanding of Personally Identifiable Information Programs between those who have employees that report to them and those who do not have employees report to them. H5: The role of Information Technology employees has a relationship to their understanding of Personally Identifiable Information Programs. H6: The age of Information Technology employees has a relationship to their understanding of Personally Identifiable Information Programs. Hypothesis 1: Time Working in Information Technology Hypothesis 2: Formal Education of IT and HSPII Understanding Hypothesis 3: Length of Time with the Company and HSPII Understanding Hypothesis 4: Employees Who Have Direct Reports and HSPII Understanding Hypothesis 6: Age of Employee and HSPII Understanding Hypothesis 6: Role of Employee and HSPII Understanding Summary 1. Explored the understanding level of HSPII programs by the IT professional 2. Additional insights gained from this study 3. The age group of the IT professional Concluding Remarks The possibility of data loss continuously threatens the security and the availability of IT systems and IT resources. The HSPII program must be a reiterative process and must be ongoing for it to be of value. IT systems and applications need to continually be examined and evaluated to determine any new risks that may arise around HSPII data security. One of the, if not the primary, risk to any HSPII program is a lack of understanding of the individuals most involved in protecting the data; the IT professional. Questions?