Notes - College of Business
advertisement

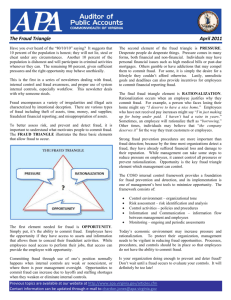
Using the Internet to Investigate Fraud William N. Dilla, CPA, Ph.D. wdilla@iastate.edu December 17, 2010 Person of the Year 2010 Presentation Objectives We will learn about: – Using the Internet to develop a predication of fraud – How a fraud investigators might use the Internet – Using the Internet for background checks – Protecting one’s self on the Internet Two Fraud Triangles The “motivation triangle” – Pressure / Incentives – Opportunity – Attitude / Rationalization The “element triangle” – Theft Act – Concealment – Conversion The Motivation Triangle Pressure / Incentives – – – – Living beyond means Vice (gambling, drugs, etc.) Financial Emergencies Bonuses or stock options (financial reporting fraud) Opportunity – Poor internal controls – Override of internal controls – Collusion Attitude / Rationalization – – – – Dishonest individual “Everyone else is doing it” “They owe it to me” “I’ll just borrow the money” The Element Triangle Theft Act – Rarely observed directly Concealment – Often causes anomalies, investigate with: • Analytical procedures • Data mining • Examination of documents Conversion – Sales of stolen assets – Living beyond means • Investigate with wealth analysis – Perpetrator brags to others Where can the Internet assist with fraud investigation? Motivation triangle – Pressure / Incentives – Opportunity – Attitude / Rationalization Element triangle – Theft Act – Concealment – Conversion Aviva, USA Case Exercise: Pretend you are an investigator who has just discovered a predication of fraud involving Phyllis and Marla Stevens. Perform an Internet search to gather information supporting your case. Additional Information for Stevens’ Case Current residence – Des Moines, IA Previous residence – Indianapolis, IN Aviva, USA Case Alleged $5.9 million fraud over four years Used terminated employee identity to generate fraudulent commission payments Another Aviva employee noticed a discrepancy (“accidental” discovery) Alleged perpetrator (Phyllis Stevens) and spouse (Marla Stevens) owned considerable property and had made substantial political contributions Substantial cash withdrawals made before alleged perpetrator’s arrest Categories of Available Information Free websites Proprietary websites Databases only accessible to law enforcement Starting Point—General Purpose Sites google.com bing.com yauba.com – Privacy safe – Allows search by source type (e.g., news, images, document type) – Easy to navigate Learn how to use advanced features People Search Sites spokeo.com – Notoriously inaccurate! zabasearch.com / intelus.com – These two are linked – Better quality sites, costs to get information pipl.com – “Deep web search” engine – Shows links to other sites peekyou.com – Provides links to multiple sites others?? – search term “people search sites” Exercise: find yourself on one of these sites News Sites Free resources Proprietary resources – factiva.com – nexis.com Public and college libraries Auction Sites ebay.com craigslist.com searchtempest.com Photo / Video Sites flickr.com picasa.com images.google.com / images.bing.com youtube.com video.google.com Blogs technorati.com icerocket.com – Icrerocket also for searching social networks, images Social Networks linkedin.com twitter.com facebook.com weddingchannel.com lococitato.com – Shows maps of relationships between facebook users What if the information you’re looking for is “private”? “Friend” person Attempt to e-mail What if you don’t want to use your real identity? – See next slide Pretexting Private investigators will set up “fake” accounts For fun, look up: – Jorge Beale – Jinger Rytand NOT a strategy for non-professionals! Background checks on the Internet New hires New clients Free sources – Many of the sources we’ve discussed already, plus: – http://www.bbb.org/us/ – http://www.linkedin.com/ • Is the job candidate’s online information the same as what they gave you? • See “LinkedIn’s top 10 overused resume phrases” at CNN.com Other Background Check Resources Partly free – Individual information • BRB Publications http://www.publicrecordsources.com/ • http://www.intelius.com/ – Business information (Dun and Bradstreet) http://www.dnb.com – Charity information http://www2.guidestar.org/ Entirely fee-based – Personal information summary http://www.spokeo.com – Online background check http://www.ussearch.com Protecting Yourself “Opt-out” of background check information possible, but not easy Proprietary privacy services available Social networks, blogs, etc. – Set privacy settings – Careful who you friend – Careful what you share!!! – See “The internet and the end of Summary Internet searches useful for: – Preliminary fraud investigation – Basic background checks Hire a professional for more involved investigations Be careful what you post and who you friend! For more on this topic: – Cynthia Hetherington – http://www.hetheringtongroup.com/ – Look under “Training” Electronic version of this presentation: – http://www.bus.iastate.edu/wdilla/Acct591/default.asp