Web Accessibiliy and Sensitive Data Considerations
advertisement
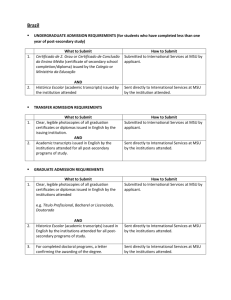
Sensitive Data Accessibility Financial Management College of Education Michigan State University Agenda for today Sensitive data management Basic computer security issues Financial management Physical Security Q: What are examples of security threats? Q: What does information security mean to you? Q: Why do we need to know this? Levels of sensitivity for data Institutional data: all of the data held by MSU, in any form or medium, for normal business operations. Public Sensitive Confidential Public data Not protected and generally made publically available, without restriction or limitation Directories Library card catalogs Course catalogs Institutional policies Sensitive data Protected by institutional policy, guidelines, or procedures – may be public/FOI-able (freedom of information) Salary data Detailed institutional accounting and budget data Personally restricted directory data Confidential data 1. 2. 3. Institutional data that could be used for identity theft Protected by law, contract, or University policy Records of the university security measures SSN payment/credit card health records student records Sensitive data management at MSU PCI DSS - Payment Card Industry Data Security Standard – Fine up to $500,000 MSU’s Managing Sensitive Data site at http://eis.msu.edu/sid/ Sensitive data management at MSU Use Institutional Data only for University purposes. Minimize the potential for their improper disclosure or misuse. Individually responsible for the security and integrity of Institutional Where to look for confidential data Digital Laptop computers, Desktop computers Phones, thumb drives Network drives, web and file servers Email attachments, social networking sites Paper Sticky notes, notepads, paper files Receipts PAN forms and other official documents Travel documentation “Do I absolutely need this data?” If not, get rid of it. As soon as you no longer need the data, delete it. Don’t leave sensitive data on computers or PDAs that can be stolen. Make sure the computer, where the data is stored, is protected against viruses, worms, etc. Be careful distributing the data via email or paper forms. Q: What should you do if an incident occurs on your computer? Q: what should you do if you find a thumb drive in the hall way? College Policy College policy can be found from this website http://education.msu.edu/csg/ All college staff are required to attend sensitive data awareness seminar every three years. No one should keep SSN and credit card number on your computer and shared drive. In practical terms, this means? No confidential data on college servers or computers There is no reason to store SSNs on a computer, so don’t. If you need to use SSNs at all, work with us to make sure they are handled with a minimum of risk. If you absolutely must have SSNs, credit card numbers, or any other sensitive data on paper, destroy paper sheets as soon as you don’t need the data anymore. If you need to keep the data, lock the papers up, then destroy them as soon as you can. Most important: Know the policy, be can minimize exposure. aware of how you Q: what should you do when your salvage your PC? Internet use security When you browse Internet Set your browser security to medium/medium-high Add safe sites to trusted sites Block pop-up windows in your browser Clear cookies and cache for browser periodically Log out of secure apps when not in use use screen saver to lock the screen Do not write down passwords Be aware when use Instant messenger, chatting Video: Spyware Video: Do not leave your computer unlocked Basic computer use protection Strong password, but easy to remember Install anti virus program and update automatically Updates Windows system automatically Turn on Windows built-in firewall Set the Internet browser security medium-high Do not download free programs from internet Do not use flash drive as your main storage Salvage computer only after clean the hard drive Email Phishing Phishing (use of e-mail messages that appear to be sent from a trusted source.) Spelling Mistakes Incorrect Graphics Personal Information The URL Video: Email hoax File management Manage by folders Save on the server (\\edshare.educ.msu.edu) Name files properly (do not use space or #, $, ~, !) View files with different layout Stop using floppy disks; use thumb drive to transfer file Email management Organize by folders and sub-folders Financial Management Oversight Segregation of duties: More than one person needed to complete a record transaction. Implement mitigating controls if staffing resources do not permit desired segregation of duties. Adequate oversight: at least take samples. Pay attention to high risk areas: cash and inventories. Take periodic inventory. Monthly reconciliation of P-card statement is required. Physical Security Protect valuables (yours and others) Be aware of and report suspicious activity Good descriptions NOT heroics Keys Doors Please remember to take the survey after you receive the email with a link. Thanks.