Chapter 10

Maintaining Network Health
Active Directory Certificate Services
Public Key Infrastructure (PKI)
Provides assurance that you are communicating with the entity you think you are.
Allows two parties to communicate though an algorithm know as public key cryptography.
Each client has a public key and a private key
No need for a pre-shared key
Combining the two allows us to communicate securely
This is more efficient than a pre-shared key.
PKI Terms
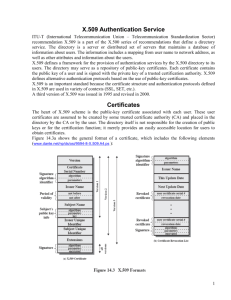
Certification Authority(CA) – issues and manages digital certificates for the PKI
Digital Certificate – digital document that contains information about a particular user, computer, or device.
Holds the public key.
Smart Cards – credit card like devices that have a digital certificate installed on them. Used to log into resources.
Self-enrollment – Allows users to request their own certificates.
Autoenrollment – Automatically enroll for certificates.
Recovery Agents – Used to recovery lost certificates.
PKI Terms continued
Web Enrollment – self enrollment through a Web
Browser.
Online Responder – responds to requests from clients about the status of a specific certificate.
Standalone CA – not integrated with AD.
Enterprise CA – integrated with AD, ideal implementation
Installing Certificate Services is a Role we can select.
Managing Certificate Enrollments
In and AD environment you can automate the distribution of certificates.
This is controlled through Group Policy
In non-Active Directory environments you must manually enroll for certificates.
Use the certificate wizard in the Certificates MMC.
Enroll through the web by typing the in the servers web address in a web browser.
Maintaining a Server 08 CA
Be sure to designate a Recovery Agent incase of lost certificates. Only the Recovery Agent can recover these.
You can assign users to one or more of the following predefined security roles:
CA Administrator – overall management
Certificate manager – issuing and managing certificates
Backup operator – back up and restore OS files and folders and CA information
Auditors – Able o manage and read security logs on a computer running AD CS role.
Introducing Network Access Protection
NAP helps protect from “unhealthy” computers from coming onto the network.
Connecting computers are “evaluated”
If they meet the criteria of the NAP policy they are permitted access to the network
If they do not the criteria they are either:
Denied access to the network
Sent to Remediation network
Remediation servers allow noncompliant computers to become compliant. IE. The remediation network my have the antivirus software available for install.
NAP enforcement Methods
DHCP enforcement – easiest method. If the NAP client is out of compliance the DHCP server will assign an address with limited access.
IPSec enforcement – uses health certificates. If a client is out of compliance it will not get the health certificate and therefore wont be able to communicate through IPSec or on the network.
VPN enforcement – restricts the level of access that a remote client can obtain. IE. Work laptops get full access, home laptops get limited access
802.1X enforcement – restricts on physical connections
NAP demonstration
You Learned (cont.)
A PKI allows two parties to communicate securely without ever having communicated with one another before in any previous communication through the use of a mathematical algorithm called public key cryptography.
Lesson 10
You Learned (cont.)
PKI certificates are managed through Certificate
Authorities that are hierarchical, which means that you can have many subordinate CAs within an organization that chain upward to a single root CA.
A Certificate Revocation List (CRL) identifies certificates that have been revoked or terminated.
Lesson 10
You Learned (cont.)
Web enrollment allows users to connect to a
Windows Server 2008 CA through a Web browser to request certificates and obtain an upto-date Certificate Revocation List.
Lesson 10
You Learned (cont.)
When deploying a Windows-based PKI, two different types of CAs can be deployed: enterprise CAs and standalone CAs. A standalone CA is not integrated with Active
Directory and relies on administrator intervention to respond to certificate requests.
Lesson 10
You Learned (cont.)
An enterprise CA integrates with Active
Directory. It can use certificate templates as well as Group Policy Objects to allow for autoenrollment of digital certificates, as well as store digital certificates within the Active Directory database for easy retrieval by users and devices.
Lesson 10
You Learned (cont.)
Network Access Protection (NAP) is a policy enforcement mechanism that is used to allow or reject access to Windows network resources on the basis of policy decisions, such as whether the Windows Firewall is turned on or if anti-virus signatures are up to date.
Lesson 10
You Learned (cont.)
NAP can be configured with one of four built-in enforcement mechanisms: DHCP, 802.1X, IPSec, and
VPN.
The NAP client includes one or more System Health
Agents (SHAs), which map to System Health Validators
(SHVs) within the NAP server architecture.
Lesson 10