Being the one eyed man
advertisement

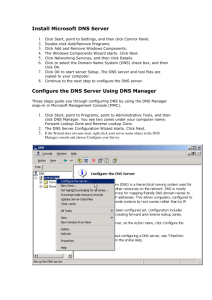
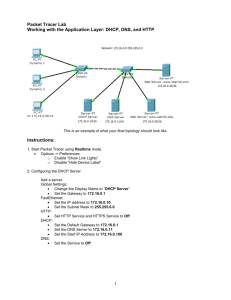
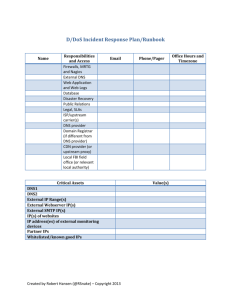
Incident Detection: MacGyver Style Ben Jackson, Mayhemic Labs SOURCEBoston April 18th, 2012 Agenda Improving the Kill Chain Moving on from Prevention Finding Data in Unexpected Places Canaries, Claymores, and Labyrinths Simple Anomaly Detection Thoughts expressed here are neither the opinions or beliefs of my employer. Kill Chain The “Kill Chain” Developed by the United States Air Force to describe the concept of target identification, force dispatch to target, decision and order to attack the target, and finally the destruction of the target. Kill Chain Find – Locate the Target Fix – Identify the Target Track – Watch the Target Target - Determine Strategy Engage – Eliminate the Target Assess – Determine if it worked Things that we’re good at… Find Fix Track Target Engage Assess Things that we’re not good at… Find Fix Track Target Engage Assess Prevention is a dirty word Stop focusing on prevention Right now, your environment is getting attacked with malware made earlier today Plus, it hasn’t even been submitted to your AV vendor You aren’t going to prevent that Prevention should be part of your strategy, and not your strategy itself How bad are we? Verizon DBIR sums it up 92% of all data breach incidents were discovered by a third party 85% of all breaches took three or more weeks to discover Both of these figures were up 6% from last year Let’s face it, we’re doing it wrong How can we improve? Lots of excuses: “I don’t have tools” “I don’t have manpower” “I don’t have a budget” “It’s too difficult” Go cry, emo CISO Solution TRY HARDER I know what you’re thinking… But hear me out! Detection is the new black Accept you are going to get compromised Liberating, isn’t it? Let’s work on rapidly detecting compromises when they happen Let’s do it MacGyver Style! Watched far too much MacGyver in my formative years When faced with an impossible task: Take stock of your tools Analyze Work the problem Improvise Be sure to carry a swiss army knife Or in my case, multi-tool Data: It’s freaking everywhere Some background In my previous life, I was a developer in public health statistics “Diet Bioinformatics” Firm believer in thinking by the numbers With enough data, you can rule the world I, for one, welcome our new Google overlords Data: It’s freaking everywhere Data is in places that you wouldn’t expect Your network keeps information just to run smoothly Let’s use that data to find abnormal behavior Case Study Wayback Machine set for March 2010 Problem: Difficult to use blacklists to check traffic to malware sites Firewall logs available, but far too many sites to check Equivalent to trying to identify needles in a very large haystack. Plus, some of the needles may not actually be there. Budget limited tools available… Time to get ingenious! A Quick DNS Tutorial A Quick DNS Tutorial Solution: DNS Scraping Didn’t care about the sites users weren’t visiting Only cared about ones they were visiting Figured by leveraging blacklists and non recursive DNS lookups, it could be determined what sites other hosts were querying How DNS Scraping Works How DNS Scraping Works How DNS Scraping Works Phase 3: Profit! If someone was querying a blacklisted site, further research was required The number of sites that needed to be searched was cut down from 2000+ to 5 or less This was awesome Mostly because I’m lazy It’s far from perfect DNS records with extremely low time to live (TTL) values give us a very small window to locate them Fast flux can be as low as 5 seconds Number of queries can total to over 10000 More DNS servers? More queries But, better then nothing! This statement is false! Everyone gets annoyed at false positives Anti Malware Software Intrusion Prevention Systems Everyone should be worried about false negatives What’s happening in your network that isn’t being detected? More importantly, how do we detect it? Old and busted: Honeypots Honeypots are great They provide great information for researchers Honeypots also are bad Lots of risk, little reward They’re a time suck to maintain Thankfully, you never needed to worry about patching them New Hotness: Canaries Somewhat like honeypots Well monitored Extremely permissive No one should be using them Only not… Fully patched Not designed to be compromised Not externally facing The best of both worlds Give you an early warning for scans within the environment Fully patched and managed, so less likely to get compromised Unless someone drops some 0 day Permissive and monitored, so if someone pokes at it, you know Canaries aren’t just computers Pen Testers <3 Rogue APs OK, let’s give an attacker a rogue AP Unencrypted Default SSID Merrily handing out DHCP addresses Log everything claymore.py Runs on a computer set up to broadcast as a rogue AP Upon handing out a DHCP address, runs a port scan on the client computer Generates an alert message and mails it along with the scan to an email address. When the trap is sprung… What good does it do? Primarily captures two kinds of people Bad Actors “Curious” Users Either way, folks you would want to know are trying to poke around This can provide as little or as much access at you want Do ye seek a grail? Anomaly detection is the holy grail of analysts Also incredibly hard to do What is “normal” for your network? More importantly, are we sure what this is normal is actually normal? Are we owned already? Do ye seek a grail? Maybe not… Works great on paper My SQL Server should only be doing SQL Server-y things However, not to much in practice Wait, why is that SQL server FTPing out to Sweden? Oh… Anti-Virus update… Or worse, it’s using a CDN to grab software updates Let’s adjust the goalposts However, let’s try to apply this to other areas Where does your user base surf to on an average day? Both work related and non-work related Does it really change that much? People like routines The good, the bad, and the… Err… The stuff we know is good The stuff we know is bad Devious Deviations Deviations from the baseline will give “interesting” stuff The “Good” Legitimate traffic (Shopping, Research, etc) The “Bad” Exploit Kits, Crimeware, BlackHat SEO The “Ugly” Errr… “Not work safe” material Why reinvent the wheel? Marcus Ranum created “NBS” in 2003 “Never Before Seen” Simple tool that implements something that we’re still trying to get done correctly today “If we’ve never seen it before, by definition… it’s an anomaly” Seen it before? No? Log it. Network NBS Let’s apply that to network events Has that event happened before? No? Log it! Analysis is left to be done by the analyst Only you will know what is normal for your network Oko Simple framework to detect “never before seen” network events Currently processes firewall and DHCP events Next up: Proxy and DNS Something we haven’t seen? Alert to syslog Named after the Soviet ICBM early warning system Some shortcomings Doesn’t provide any context You’re on your own, bub Lights up like a Christmas tree for abnormal, but authorized activity New server? PANIC! All the data extraction from logs is left to you Handles JSON via ZeroMQ In summary… There are lots of bits out there on your network, harness them to your advantage Use these techniques in your own environment Remember, when faced with an impossible task, inventory your tools… And ask yourself… Questions? Ur Feedback, I haz it? http://www.surveymonkey.com/sourceboston12 Contact Info Ben Jackson e-Mail: bbj@mayhemiclabs.com Twitter: @innismir Web/Code: http://mayhemiclabs.com