Cybersecurity:
Mitigating
Business Risk
IT.CAN 2014
18th Annual Conference
October 20th 2014
Panelist – Benoit-Luc St-Pierre, KPMG
Benoit-Luc St-Pierre, CISA, CISSP
Directeur / Manager
Management et Gestion des risques / Management and Risk Consulting
KPMG LLP
bstpierre@kpmg.ca
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
1
2. What are the most challenges pertaining to security risks when IT
contracting?
1. Data location risks
• Make sure that the party you are dealing with does not store and/or outsource the
work – implicitly your data – to a third party in foreign countries or to an external
organization with poor cyber security practices.
2. Proper due diligence
• It is a good security practice to ensure proper background checks have been done on
external contractors that will have privileged access to your data prior beginning of the
work. Federal Canadian Government clearance requirement such as the “Reliability
Status” and “Secret” levels for individual is very common.
• Depending on the risks involved, ensuring that the 3rd party has a cyber insurance
with adequate coverage.
3. Addressing 3rd party cyber security risks
• New 3rd party vendor access to the network could introduce new risks and threat
source to data integrity and confidentiality.
• Depending on the nature of the service delivered by the 3rd party, it could be a good
practice to ensure that 3rd party vendor have implemented sound security practices. It
is very common for outsourcing IT companies to perform independent IT controls and
security audits
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
2
3. What is the most important cybersecurity technical development and
why?
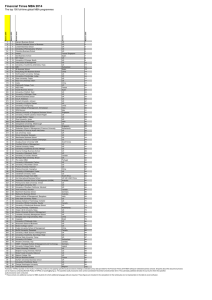
Cybersecurity Framework for
Critiqua Infrastructure
Cyber Security Questionnaire
Issuer (Country)
NIST (US)
OSFI (Canada)
Issue date
February 12, 2014
October 28, 2013
Industry
Power and water utilities, gas and oil
transportation*
Federally Regulated Financial Institutions
(Banks, Trusts, some Credit Unions,
Insurance Companies)*
Highlights
Controls are divided in 5 sections
(functions):
1. Identify (Governance, assets and
risk mgmt, etc..)
2. Protect (access control, data
security, protective tech, etc..)
3. Detect (Security monitoring, etc..)
4. Respond (Communications,
analysis, Mitigations, etc,,)
5. Recover (Recovery planning, etc..)
Self-assessment questionnaire on cyber
security practices designed to assess the
maturity level (5 levels) of the organization.
Divided in 6 sections:
1. Organization and Resources
2. Cyber Risk and Control Assessment
3. Situational Awareness
4. Threat and Vulnerability Risk
Management
5. Cyber Security Incident Management
6. Cyber Security Governance
*Can be adapted or used in any type of industry
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
3
3. What is the most important cybersecurity technical development and
why?
The “Cyber Kill Chain” methodology developed by Lockheed Martin in 2011, is gaining traction in
organizations which are constantly under pressure of advance persistence Threat (APT).
Developed in response to the increasing threat of APTs across the globe, this methodology
breakdown an attack in 7 chained steps. An attacker must have successfully executed all steps
to “win” while the defender has to block the attacker in any one of the steps to stop the attack.
Reconnaissance
Weaponization
Delivery
Exploitation
Installation
Command & Control
07
DATA
THEFT
06
CALL
HOME
05
DROPPER
FILE
04
EXPLOIT
KIT
03
REDIRECT
02
LURE
RECON
01
Action on Objectives
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
4
4
4. What is one of the most useful practice when addressing
cybersecurity risks?
1 - Test the effectiveness of your cyber security controls and your incident response
process. Knowing that your security is good is better than just thinking / assuming it is
good.
2 - Security monitoring / analytics is crucial for rapid breach detection and response
actions. Failure to act upon security alerts could be disastrous. For example, malware
detection alerts were sent to Target security team but they did not act in a timely
manner to stop the attack.
3 - Performing an independent assessment of your cyber defenses (firewalls, IDS/IPS,
WAF, anti-virus, anti-spam, DLP, etc..). This can materialized in many forms such as:
•
Network penetration testing (at least once a year);
•
Web application security testing (common attack vector for data breaches);
•
Social engineering testing (common attack vectior for APTs);
•
Physical testing (building & server room access, card security, piggy backing);
•
System security configuration audits : servers, workstations, firewall rules,
databases, etc..
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
5
5. What is one of the most important best practice when dealing with
data breaches?
1. Have a plan ready for external communications. Customers, shareholders
and regulators are now very demanding on organizations to respond quickly.
2. Have a cybersecurity incident response team with experienced people.
3. Have data breach containment procedures well documented and tested.
4. Maturity of the forensic shop is an important factor, it must be competent
and fast. For large incident it a good practice to engage an independent party
to secure the evidences and perform the investigation.
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
6
6. What do you consider as being the biggest impact triggered by
Edward Snowden’s revelations?
•
NDAs and personnel security vetting does not suffice for organizations to protect
against internal threat. The application of a very structured and global cybersecurity
framework should be implemented by organizations.
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
7
7. CYBER INSURANCE: What are some of the key consideration for companies
considering cyber insurance or seeking to improve coverage in a renewal?
1 - Good understanding of cybersecurity risks and their mitigating controls in place
before buying cyber security insurance.
2 - Cybersecurity maturity level of the organization. It is important that companies
assess themselves or by a third party before buying cyber security insurance.
3 - Have well designed and effective security controls in place. The weaker in
terms of cyber security risks is the IT environment the more likely are the premium fees
to be higher.
4 - Companies may have to disclose to an insurer their cyber security risks and
demonstrate mitigating controls through self-questionnaire or 3rd party audit on
behalf of the insurer.
5 - Choose cyber insurance product with the best added value for the
organization. Chubb, for example, offers some customers a form of no-loss deductible
on some cyber policies where – if no claims are made in a given year – part of the
deductible is returned to the customer in order to be used on enhancing their level of
security (i.e.: performing external penetration tests, etc..).
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
8
Extra slides
Threat awareness | The cyber criminals
Petty Criminals
Motives: Financial gain
Organized Criminals
Motives: Financial gain
Hacktivists / Terrorists …
Motives: Political support
State sponsored
Motives: State agenda
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
10
Data Breaches in the News 2004-2014
Data source: http://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
11
Lesson learned from Target data breach – Highlights
1. Having sufficient cyber insurance coverage – The data breach cost them at least $235 million dollars
so far and they were only able to recoup $90 million from their cyber insurance policy coverage.
Hackers stole the financial and personal information of 110 million customers.
2. Third party can be a potential data breach source – The root cause of the breach was identified to
be from a small Pennsylvania HVAC company compromised remote access account. Hackers targeted
the third party company first. Then they managed to obtain vendor remote access VPN credentials and
access Target’s network. Third party vendor remote access was for electronic billing, contract
submission and project management.
3. Act upon alerts received – Malware detection alerts were sent to Target security team but they did not
act in a timely manner to stop the attack.
4. Network segregation is important – It appears that hackers were successful at accessing POS
systems from a less sensitive network area. PCI regulation is very strict about POS network access
controls.
5. Data breaches impact shareholders as well – Stock price lost 11.3% of its value in the first 3 months
after public disclosure. Also CEO Gregg Steinhafel was removed by the Board of Directors on May 5
2013. On May 28, Institutional Shareholder Services (ISS) recommended that Target shareholders
vote out seven of its 10 board members including members of the Audit and Corporate Responsibilities
committees.
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
12
Lesson learned from Target data breach – Stock price don’t like bad
publicity
Stock price lost 11.3% of its value in the first 3 months
© 2014 KPMG LLP, a Canadian limited liability partnership and a member firm of the KPMG network of independent member firms affiliated with KPMG International Cooperative (“KPMG International”), a Swiss
entity. All rights reserved. KPMG CONFIDENTIAL.
13
Thank you
Presentation by Benoit-Luc St-Pierre
KPMG CONFIDENTIAL
The information contained herein is of a general nature and is not
intended to address the circumstances of any particular individual
or entity. Although we endeavor to provide accurate and timely
information, there can be no guarantee that such information is
accurate as of the date it is received or that it will continue to be
accurate in the future. No one should act on such information
without appropriate professional advice after a thorough
examination of the particular situation.
© 2014 KPMG LLP, a Canadian limited liability partnership and a
member firm of the KPMG network of independent member firms
affiliated with KPMG International Cooperative (“KPMG
International”), a Swiss entity. All rights reserved.
The KPMG name, logo and “cutting through complexity” are
registered trademarks or trademarks of KPMG International.