Slide 1
advertisement

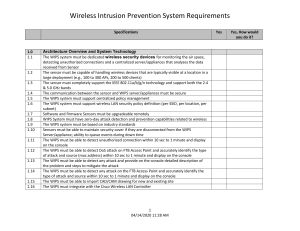
• • • • • • Chapter 14 Wireless Attacks, Intrusion Monitoring and Policy 802.11 Security Basics Legacy 802.11 security Robust Security Segmentation Infrastructure Security VPN wireless Security Exam Essentials • Understand the risk of the rogue access point. – Be able to explain why the rogue AP provides a portal into network resources. Understand that employees are often the source of rogue APs. • Define peer-to-peer attacks. – Understand that peer-to-peer attacks can happen via an access point or through an ad hoc network. Explain how to defend against this type of attack. • Know the risks of eavesdropping. – Explain the difference between casual and malicious eavesdropping. Explain why encryption is needed for protection. • Define authentication and hijacking attacks. – Explain the risks behind these types of attacks. Understand that a strong 802.1X/EAP solution is needed to mitigate them. Exam Essentials • Explain wireless denial-of-service attacks. – Know the difference between layer 1 and layer 2 DoS attacks. Explain why these attacks cannot be mitigated and can only be monitored. • Understand the types of wireless intrusion solutions. – Explain the difference between a WIDS and a WIPS. Understand that most solutions are distributed client/server models. Know the various components of an intrusion monitoring solution as well as the various models. Understand which attacks can be monitored and which can be prevented. • Understand the need for a wireless security policy. – Explain the difference between general and functional policies. Wireless Attacks • Portal to the wired network must be protected – Limit unauthorized access • Limit access to management consoles – Don’t want someone changing settings or passwords • Peer to peer – Watch out for unsecured netwroks Pg 470 Rogue Wireless Devices • Non-Authorized on the network – Not controlled by admin • Set up by hacker – To get access or passwords • Set up by user – Ease of use • Open an unsecured portal to wired network • 802.1x can also help here Pg 471 Peer to Peer • Client attacking client on a WiFi network – Ad-hoc or infrastructure • On infrastructure network, you can disable client to client communications – Public Secure Packet Forwarding • Beware of push to talk Pg 472 Eavesdropping • Easy to do • Casual – Wardriving – Looking for wireless networks • Netstumbler • Malicious – Protocol analyzers and collection of data – Passive, cannot be detected by WIDS/WIPS – Use encryption to protect network Pg 472 Cracking!! • WEP has been cracked • TKIP/CCMP are still secure • Authentication Attacks – Some systems are less secure than others – Dictionary attacks – PSK is weak as well • Will let hackers onto AP • Longer passphrases help Pg 475 MAC Spoofing • MAC Filtering is weak security • Better than nothing Pg 477 Management Interface • Don’t let hackers configure your devices • Disable unused interfaces – SNMP, Telnet, HTTP, • Use more secure interface – SSH, HTTPS • General policy is that management should be done from wired interface Pg 478 Wireless Hijacking • Attacker configures AP to mimic enterprise AP – Same SSID • Attacker can then capture traffic • Can then either set up for man in the middle – Send “real” traffic on and capture details – Bridging the fake AP to real AP • Also can use WiFi phishing – Setting up a false captive portal Pg 479 Denial Of Service • Prevent legitimate users from getting access • Hard to prevent – Need to remove device generating noise/traffic • Layer 1 jamming • Layer 2 – Deauthentication or deassociation packets – Flooding the AP with requests • Spectrum Analyzer can help with layer 1 • Protocol Analyzer will help with Layer 2 Pg 479 Other Attacks • Vendor Specific – Buffer overflow that attacks OS • Social Engineering – Tricking someone into giving away information • PSK!!! Pg 481 Intrusion Monitoring • Wireless Intrusion Detection Systems (WIDs) • Wireless Intrusion Prevention Systems (WIPS) – Can mitigate or respond Pg 481 WIDS • Wired ports must be controlled – Prevent rogue APs • WIDS often go up before network – Check for rogue APs and usage • WIDS server • Management Console • Sensors Pg 482 WIDS Sensors • Dedicated AP like devices that listen and report back to the management console/server • Can also be APs set into sensor mode – Or APs that scan as well as process traffic Pg 482 WIDS Sensors Pg 482 WIDS • Best at watching for layer 2 attacks • Can set alarms for “risky” traffic • Set thresholds – Different alert types • Overlay • Integrated • Integration enabled Pg 482 WIPS • Infrastructure device – This classification refers to any client station or access point that is an authorized member of the company’s wireless network. A network administrator can manually label each radio as an infrastructure device after detection from the WIPS or can import a list of all the company’s radio card MAC addresses into the system. • Unknown device – The unknown device classification is assigned automatically to any new 802.11 radios that have been detected but not classified as rogues. Unknown devices are considered interfering devices and are usually investigated further to determine whether they are a neighbor’s devices or a potential future threat. • Known device – This classification refers to any client station or access point that is detected by the WIPS and whose identity is known. A known device is initially considered an interfering device. The known device label is typically manually assigned by an administrator to radio devices of neighboring businesses that are not considered a threat. Pg 485 WIPS • Rogue device – The rogue classification refers to any client station or access point that is considered an interfering device and a potential threat. Most WIPS define rogue access points as devices that are actually plugged into the network backbone and are not known or managed by the organization. Most of the WIPS vendors use a variety of proprietary methods of determining whether a rogue access point is actually plugged into the wired infrastructure. • If a client is classified as a rogue, the WIPs can mitigate attack – Deauthenticate, deassociate – Spoof MAC of Rogue Pg 485 WIPS • Rogue device – The rogue classification refers to any client station or access point that is considered an interfering device and a potential threat. Most WIPS define rogue access points as devices that are actually plugged into the network backbone and are not known or managed by the organization. Most of the WIPS vendors use a variety of proprietary methods of determining whether a rogue access point is actually plugged into the wired infrastructure. • If a client is classified as a rogue, the WIPs can mitigate attack – Deauthenticate, deassociate – Spoof MAC of Rogue – Use SNMP to disable the wired port it is connected to Pg 485 Mobile WIDS • Laptop Version of the products • Mobile capabilities – Radio Card is sensor • Use to physically track down a Rogue AP – Some layer 1 functionality built in Pg 485 Spectrum Analyzer • Use for security as well as surveys • Many can look at the RF signature and tell you what kind of device it is • Mobile and distributed – Like WIDs Pg 487 Wireless Security Policy • How and what are you monitoring • How often should PSKs change Pg 487 Wireless Security Policy • General Security Policy • Functional Security Policy • Legislative Compliance Pg 487 Policy Recommendations • General Security Policy • Functional Security Policy • Legislative Compliance Pg 490 Exam Essentials • Understand the risk of the rogue access point. – Be able to explain why the rogue AP provides a portal into network resources. Understand that employees are often the source of rogue APs. • Define peer-to-peer attacks. – Understand that peer-to-peer attacks can happen via an access point or through an ad hoc network. Explain how to defend against this type of attack. • Know the risks of eavesdropping. – Explain the difference between casual and malicious eavesdropping. Explain why encryption is needed for protection. • Define authentication and hijacking attacks. – Explain the risks behind these types of attacks. Understand that a strong 802.1X/EAP solution is needed to mitigate them. Exam Essentials • Explain wireless denial-of-service attacks. – Know the difference between layer 1 and layer 2 DoS attacks. Explain why these attacks cannot be mitigated and can only be monitored. • Understand the types of wireless intrusion solutions. – Explain the difference between a WIDS and a WIPS. Understand that most solutions are distributed client/server models. Know the various components of an intrusion monitoring solution as well as the various models. Understand which attacks can be monitored and which can be prevented. • Understand the need for a wireless security policy. – Explain the difference between general and functional policies.