Unit 07 - LO3
advertisement
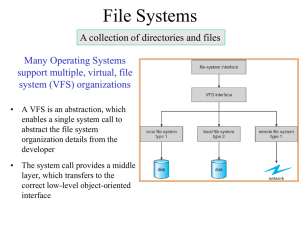
Computer Network Systems LO3 - Know the services provided by network systems P1 describe the types of networks available and how they relate to particular network standards and protocols M1 compare the benefits and disadvantages of peer-to-peer network and client/server networks [IE3] P2 describe why different network standards and protocols are necessary P3 explain the key components required for client workstations to connect to a network and access network resources M2 design a networked solution to meet a particular situation with specific requirements [IE1, CT1] D1 justify the design and choice of components used in a particular networked solution [IE6] P4 explain the function of interconnection devices P5 describe typical services provided by networks D2 evaluate typical services available from a network operating system directory service. P6 make a networked system secure. M3 report on the business risks of insecure networks and how they can be minimised. In this section you will deal with the services provided by a network that allows your clients internal and external facilities not available on stand alone machines. Most of these will run through the server and be provided as services on the machines across the school. You will describe the services and discuss the merits of these services on the operation of the school in terms of functionality, use and practical need. Sections of the criteria in this AO cover: P5 - Describe typical services provided by networks M3 - Describe where different network services would be used D2 - Evaluate typical services available from a network operating system directory service. User accounts are the backbone of network security administration. Through the use of user accounts, you can determine who can access your network, as well as what network resources each user can and cannot access. You can restrict access to the network to just specific computers or to certain hours of the day. In addition, you can lock out users who no longer need to access your network. Every user who accesses a network must have a user account. User accounts allow the network administrator to determine who can access the network and what network resources each user can access. In addition, the user account can be customised to provide features for users, such as a personalized Start menu or a display of recently used documents. Every user account is associated with a username (sometimes called a user ID), which the user must enter when logging in to the network. Each account also has other information associated with it. In particular: The user’s password: This also includes the password policy, such as how often the user has to change his or her password, how complicated the password must be, etc. The user’s contact information: This includes full name, phone number, e-mail address, home address, and other related information. Account restrictions: This includes restrictions that allow the user to log on only during certain times of the day. This feature enables you to restrict your users to normal working hours and can also specify that the user can log on only at certain computers. Account status: You can temporarily disable a user account so that the user can’t log on. Home directory: This specifies a shared network folder where the user can store documents. External Access: These authorize the user to access the network remotely (Intranet access). Group memberships: These grant the user certain rights based on groups to which they belong. Authentication and User rights control what a user can do on a network-wide basis. Permissions Enable the user to fine-tune your network security by controlling access to specific network resources, such as files or printers, for individual users or groups. For example, you can set up permissions to allow users into the accounting department to access files in the server’s Accounts directory. Permissions can also enable some users to read certain files but not modify or delete them. Each network operating system manages permissions in a different way. Whatever the details, the effect is that you can give permission to each user to access certain files, folders, or drives in certain ways. Any permissions that you specify for a folder apply automatically to any of that folder’s subfolders, unless you explicitly specify a different set of permissions for the subfolder. In Novell’s NetWare, file system rights are referred to as trustee rights. NetWare has eight different trustee rights. For every file or directory on a server, you can assign any combination of these eight rights to any individual user or group. Active Directory solves many of the inherent limitations of the Operating Systems domains by creating a distributed directory database that keeps track of every conceivable type of network objects. Like all directories, Active Directory is essentially a database management system. The Active Directory database is where the individual objects tracked by the directory are stored. Active Directory uses a hierarchical database model, which groups items in a tree-like structure. The terms object, organizational unit, domain, tree, and forest are used to describe the way Active Directory organizes its data. The following sections explain the meaning of these important Active Directory terms. Objects The basic unit of data in Active Directory is called an object. Active Directory can store information about many different kinds of objects. The objects you work with most are users, groups, computers, and printers. Objects have descriptive characteristics called properties or attributes. You can call up the properties of an object by double-clicking the object in the management console. Domains A domain is the basic unit for grouping related objects in Active Directory. Typically, domains correspond to departments in a company. For example, a company with separate Accounting, Manufacturing, and Sales departments might have domains named (you guessed it) Accounting, Manufacturing, and Sales. Or the domains correspond to geographical locations. For example, a company with offices in Corby, Kettering, and Oakley might have domains named Cor, Ket, and Oak. DNS, which stands for domain name system, is the TCP/IP facility that lets you use names rather than numbers to refer to host computers. Without DNS, you’d buy books from 207.171.182.16 instead of from www.amazon.com, you’d sell your used furniture at 66.135.192.87 instead of on www.ebay.com, and you’d search the Web at 216.239.51.100 instead of at www.google.com. More importantly internally you would access Mac Address 323j234j23jhfdj44 rather than ITSuite_01. Understanding how DNS works internally and how to set up a DNS server is crucial to setting up and administering a TCP/IP network. Internally the DNS addressing assigns TCP/IP addresses to workstations automatically. DNS addresses are used mainly by corporations and large TCP/IP networks to configure their clients, although they are also used by some Internet service providers. When a client accesses a TCP/IP network, the DNS server assigns the client an IP address, a subnet mask, and a gateway, if needed. The DNS server has a range of possible IP addresses from which to choose. Each time the client logs off of the network, the IP address goes back into a pool and might be assigned to another client logging on to the network. Letting the DNS server configure clients when they attach to the network saves the administrator of a large IP network a lot of time and effort. A DNS server can grant a lease to a client. The lease provides one IP address for use by the client. Each time the client logs on to the network, the IP address is registered to the client and all activity on the network is linked to that login account. Basically when a student logs in, everything they do and see is registered, web addresses accessed, emails sent, programs run, everything but a key log of their activity. P5.1 - Task 1 – Describe the facility and importance of Directory Services within a network environment. M3.1 – Task 2 – Describe the need for implementation of these Directory Services within a Primary School System in terms of security, Data Protection and ease of student use. D2.1 – Task 3 – Within your PowerPoint, evaluate the Directory Services need your business needs to take to secure their Networks. Account Management Authentification Management Active Directory DNS E-mail is a great way to give your employees the means to collaborate and share information with co-workers, vendors, manufacturers, customers, and students. A mail server is a server that handles the network’s e-mail needs. It is configured with email server software, such as Microsoft Exchange Server. Exchange Server is designed to work with Microsoft Outlook, the e-mail client software that comes with Microsoft Office. Most mail servers actually do much more than just send and receive electronic mail. Hardware wise this usually is a dedicated server that handles the client (software) processes the tens of thousands of emails that come in every day and manages these emails to the client. With the server software, emails are processed before rerouting. A server application like Exchange Server will: ◦ Spam and virus filter through the emails ◦ Block DOS attacks ◦ Filter for swearwords ◦ Flag up erroneous or dangerous emails ◦ Process attachments, groups, reminders, and account information. ◦ Manage the email folder limits. IRC (Internet Relay Chat) is a popular method used on the Internet and in private networks to chat between computers and sometimes share applications. IRC is an open protocol that uses TCP access. An IRC server can connect to other IRC servers to expand the IRC network. Users access IRC networks by connecting a client to a server. There are many client implementations such as mIRC or XChat and server implementations. Most IRC servers do not require users to register an account but a user will have to set a nickname before being connected. The standard structure of a network of IRC servers is a tree. Messages are routed along only necessary branches of the tree but network state is sent to every server. This architecture has a number of problems. A misbehaving user can cause major damage to the network and whether intentional or a accident, requires a lot of network traffic. Adding a server to a large network means a large background bandwidth load on the network and a large memory load on the server. Once established however, each message to multiple recipients is delivered by multicast which means each message travels a network link exactly once. This is a strength in comparison to non-multicasting protocols such as Simple Mail Transfer Protocol (SMTP). A discussion board is a tool which allows groups to communicate online. It is quite similar to e-mail, but is separate from your e-mail account and is accessed, stored and organised centrally. All the group can read all the messages. You can read old messages or post new messages at any time. A discussion board is made up of ‘forums’ – folders containing messages on a particular subject, ‘threads’ – each thread is a series of messages about the same topic, and ‘messages’ – each message is an individual contribution to a conversation (like a single e-mail). Students can discuss topics or issues Students can follow a train of thought Users can negotiate and share ideas. Discussions can be monitored and filtered by a forum host. Remote access e.g. via mobiles is becoming a more popular method of gaining access to features on the network on the move. Many major mobiles have email access that allows the business world to access information and documents any time of the day as long as they are within a hotspot range. All it requires is permission from the Network Manager, an IP or WPA key, an SSID number or a restricted internet access account. There are benefits: Instant access to emails Wi-Fi access Ability to open and read attached documents With more advanced phones, ability to adapt and edit documents GPS tracking Users with multiple email accounts can also redirect these emails to their phones to allow access to more confidential information, adding the ability to Skype, and have Intranet access means more availability and work presence. But there are downsides too. One of the most useful tools available to system administrators is a program called Remote Desktop Connection, or RDC for short. RDC lets you connect to a server computer from your own computer and use it as if you were actually sitting at the server. In short, RDC lets you administer your server computers externally. All that is necessary is the software that comes with Windows and some configuration, and possibly a remote machine dedicated to external access. This will allow your clients to: Access their work files from home Access network drives and files Directly transfer files from home to active folders Allow the running of applications remotely including software on the remote machine. Allow remote monitoring of the network by the network manager. Allow multiple users to access this. File transferring is the ability within Server and Client Operating Systems to set user rights onto a file by assigning the file to a group. A group account is an account that doesn’t represent an individual user. Instead, it represents a group of users who use the network in a similar way. Instead of granting access rights to each of these users individually, you can grant the rights to the group and then assign individual users to the group. When you assign a user to a group, that user inherits the rights specified for the group. For example, suppose that you create a group named “Accounting” for the accounting staff and then allow members of the Accounting group access to the network’s accounting files and applications. Then, instead of granting each accounting user access to those files and applications, you simply make each accounting user a member of the Accounting group. Groups are one of the keys to network management nirvana. As much as possible, you should avoid managing network users individually. Instead, clump them into groups and manage the groups. When all 50 users in the accounting department need access to a new file share, would you rather update 50 user accounts or just one group account? A user can belong to more than one group. Then, the user inherits the rights of each group. For example, suppose that you have groups set up for Accounting, Sales, Marketing, and Finance. A user who needs to access both Accounting and Finance information can be made a member of both the Accounting and Finance groups. Likewise, a user who needs access to both Sales and Marketing information can be made a member of both the Sales and Marketing groups. You can grant or revoke specific rights to individual users to override the group settings. For example, you may grant a few extra permissions for the manager of the accounting department. You may also impose a few extra restrictions on certain users. Social networking is becoming more and more popular for business purposes as well as personal purposes. With advances in social networking sites, people can access files, information, images and contacts. To set up a social network site within a business, all it requires is a section of a server dedicated to the operating needs, a set of restrictive accounts set up for the users that will allocate file space for them as well as a GUI (Front Screen), and a set of tools that will allow the user to customise their space and save this customisation to their account name. Software such as Noodle, Elgg, Mahara and AROUNDMe. Benefits include: Restricting down client use of other sites Accessible storage of information and contacts File storage with ftp Access from home – remote access and storage Monitored by company for etiquette. P5.2 – Task 4 – Describe the Range of Communication Services available to companies and the potential benefits of monitoring and controlling access to these. M3.2 – Task 5 – Describe the need for monitoring Communication Services within a Primary School System in terms of security, Data Protection and filtered student use. D2.2 – Task 6 – Within your PowerPoint, evaluate the procedures your organisations should take to secure their Communication Systems. Email Remote Desktop IRC Discussion Boards Social Networking Remote Access File Transfer One of the most important functions of a network operating system is its ability to share resources with other network users. The most common resource that’s shared is the server’s file system. A network server must be able to share some or all of its disk space with other users so that those users can treat the server’s disk space as an extension of their own computer’s disk space. The Network OS allows the system administrator to determine which portions of the server’s file system to share. Although an entire hard drive can be shared, it is not commonly done. Instead, individual directories or folders are shared. The administrator can control which users are allowed to access each shared folder. Because file sharing is the reason many network servers exist, network operating systems have more sophisticated disk management features than are found in desktop operating systems. For example, most network operating systems have the ability to manage two or more hard drives as if they were a single drive. In addition, most can create mirrors, which automatically keeps a backup copy of a drive on a second drive. Other benefits include: The ability to share files or work on the same file by multiple people The ability to set rights to files Remote access to files through RDC Restricted times on files for exams Undelete options on files and programs Group allocation of a file P5.3 – Task 7 – Describe the Process and Benefits to companies of configuring File Sharing management services. M3.3 – Task 8 – Describe the circumstances in which File Sharing management takes place with a school environment. D2.3 – Task 9 – Within your PowerPoint, evaluate the procedures your organisations should take to secure their student information if instigating file sharing rights. A database server is a server computer that runs database software, such as Microsoft’s SQL Server 2000. Database servers are usually used along with customized business applications, such as accounting or marketing systems. Everything piece of stored information on the network is stored in some kind of database. For instance a domain is a method of placing user accounts and various network resources under the control of a single directory database. All the information about a member of staff is stored on a database (age, name, address, qualifications, wages), this is linked to the Active directory database (groups, rights, files and folders, permission) and this is linked to Workgroups (students they teach, subjects they deliver, Intranet rights) and this is linked to the reports database (Reviews, reports, Assessments). Linking all these is the key to a good working network. From the moment we log in to the moment we log off, we would expect this database structure to be intact, easily accessible and available at all times. Programs like Microsoft Server, MySql, and Active directories help us to achieve that task. Protecting that structure is also important, under the Data protection Act that information must be kept safe, under the Child Protection Act that information needs to be restricted, under good working practices that information needs to be backed up regularly on and off site which means backup servers, tape drives, UPS and management systems. When a user running a Web browser requests a page, the browser uses HTTP to send a request via TCP to the Web server. When the Web server receives the request, it uses HTTP to send the requested Web page back to the browser, again via TCP. A Web server is a server computer that runs software that enables the computer to host an Internet Web site. The two most popular Web server programs are Microsoft’s IIS (Internet Information Services) and Apache. The job of this web server is to: Monitor incoming traffic Filter sites Send and receive search requests and display results Allocate the search result to the appropriate computer Allocate rights to searches for restricted users The job of a good server is to learn from the results, allowing the network manager to adapt the content addresses and filter these blocks appropriately such as tunnels, pipes, proxy bypasses etc. With the internet changing all the time, this is an ongoing routine, helped by the use of network logs. A proxy server (or Application Gateway) is a server that sits between a client computer and a real server. The proxy server intercepts packets that are intended for the real server and processes them. The proxy server can examine the packet and decide to pass it on to the real server, or it can reject the packet. Or the proxy server may be able to respond to the packet itself, without involving the real server at all. For example, Web proxies often store copies of commonly used Web pages in a local cache. When a user requests a Web page from a remote Web server, the proxy server intercepts the request and checks to see whether it already has a copy of the page in its cache. If so, the Web proxy returns the page directly to the user. If not, the proxy passes the request on to the real server. Application gateways are aware of the details of how various types of TCP/IP servers handle sequences of TCP/IP packets, so they can make more intelligent decisions about whether an incoming packet is legitimate or is part of an attack. As a result, application gateways are more secure than simple packetfiltering firewalls, which can deal with only one packet at a time. A good proxy server will: Learn from attacks and add them to a barred list Download updates from an online security system like Janet Filter the network as an added level of protection. Act as a barrier, together with the firewall and SSL against DOS attacks. P5.4 – Task 10 – Describe the need for Databases, Web and Proxy Services on a system to ensure consistent functionality. M3.4 – Task 11 - Describe the circumstances in which Application Management takes place with a school environment. D2.4 – Task 12 – Within your PowerPoint, evaluate the procedures your organisations should take to secure their Application Software if instigating student management rights. Although you can share a printer or scanner on a network by attaching the device to a server computer, many printers have network interfaces built in. This lets you connect the printer directly to the network. Then network users can connect to the printer and use it without going through a server. Even if you connect a printer directly to the network, it’s still a good idea to have the printer managed by a server computer running a network operating system such as Windows Server 2003. That way, the server can store print jobs sent to the printer by multiple users and print the jobs in the order in which they were received. After you have installed the network printer, printing to the network printer is a snap. You can print to the network printer from any Windows program by using the File➪Print command to summon the Print dialog box. Near the top of this dialog box is a drop-down list titled Name, which lists all the printers that are installed on your computer. Choose the network printer from this list and then click OK to print your document. The benefits include: Print Servers hold jobs until the printer is ready even when turned off. Network printers can be shared by everyone They can be restricted to a group or just a room Installing drivers can be done from the network Pcount can allocate funds and restrict users who have printed too much Replacing the printer is as simple as replacing one installation and changing the DNS queue. Using network programs the printer can be monitored. P5.5 – Task 13 – Describe the need for sharing devices on a system to ensure consistent availability. M3.5 – Task 14 - Describe the circumstances in which Device Sharing Management takes place with a school environment. Many network servers exist solely for the purpose of making disk space available to network users. As networks grow to support more users, and users require more disk space, network administrators are constantly finding ways to add more storage to their networks. One way to do that is to add additional file servers. However, a simpler and less expensive way is to use network attached storage, also known as NAS. A NAS device is a self-contained file server that’s preconfigured and ready to run. All you have to do to set it up is take it out of the box, plug it in, and turn it on. NAS devices are easy to set up and configure, easy to maintain, and less expensive than traditional file servers. A typical entry-level NAS device is the Dell 725N. This device is a self-contained file server built into a small rackmount chassis. It supports up to four hard drives with a total capacity up to one terabyte. After that the network can have added rack mounted hard drives, and as the network grows, more hard drives. The benefits include: Upgradeable Can have backup drives Can use shared allocation and rights to files Users can have their own space which can increase or decrease Admin and Student drives can be separate for security reasons Drive letters can be allocated for easier use. P5.6– Task 15 – Describe the need for Storage Space allocation and management on a system to ensure consistent functionality. M3.6 – Task 16 - Describe the circumstances in which Storage Management takes place with a school environment. D2.5 – Task 17 – Within your PowerPoint, evaluate the Storage Space needs of your organisations and the procedures that should be taken to allocate required student and department space. Places where wireless Internet access is available to the public are called hot spots. Some organizations, such as BT Wi-fi, have established a network of hot spots across the nation. Other organizations, such as a local coffee shop, might have only one hot spot. In some cases, Internet access is free. In other cases, the organization running the hot spot requires users to pay based on their usage or subscribe to a service. An average subscription costs £20 to £30 per month. There are many issues involved from Security to Access Rights, Capability to Compatibility when it comes to working through the network with Mobile Access. Security: To make IP addressing transparent for mobile users—A person visiting your office, for example, could attach to your network and receive an IP address without having to change the laptop’s configuration. Transferring – Phones have the ability to upload either remotely or directly, direct access will involve Bluetooth, USB or Wi-Fi access, all of which needs configuring. Remotely this will require authentication which again can be an issue with storage, theft, times out access etc. Connectivity – Signals break up, it is that simple, and transferring information usually require a constant stream of packets or rick losing packets. For some files one fraction of a second of loss can damage a file. In mobile wireless, the receiver can be located anywhere within the transmitter’s range. This allows the receiver to roam from one place to another while continuing to pick up its signal. Reassociation - Connecting to a different access point requires Reassociation. Reassociation occurs when a mobile user moves out of one access point’s range and into the range of another. It might also happen if the initial access point is experiencing a high rate of errors. VoIP, (Voice Over IP (Internet Protocol) works much the same as a regular telephone. However, instead of connecting to the public telephone network, your phones connect directly to the Internet. The main benefit is reduced cost, especially if you make a lot of long distance phone calls. When you use a normal phone to make a long distance call, your voice is transmitted (usually in digital form) over a network called the Public Switched Telephone Network, or PSTN. Along the way, you’re charged by-the-minute fees by your long distance service provider. When you use VoIP, your voice is still converted into digital form. However, instead of being sent over private networks owned by telephone companies, it is sent over the Internet. Because the Internet uses the IP protocol, the digital data that represents your voice must be converted into packets that can be sent reliably over IP. Hence the name, Voice Over IP, or VoIP. The benefits to a business of VoIP include: Free calls to other VoIP connections Ability to send files on more secure systems Running through a network would allows users to VoIP internally An “Always On Connection” indicates locality using an IP address. Reduces the need for email and mobiles P5.7 – Task 18 – Describe the facility of VOIP and Mobile Working within a Networking environment. M3.7 – Task 19 - Describe the circumstances in which VOIP and Mobile Working takes place with a school environment. There are two kinds of authentication that goes on when a user switches on a machine, User and Hardware. User authentication – This happens every time a user tries to access something, Logging on to the machine requires user rights to the network through a stored database of names and passwords, it then kicks in a series of commands linked to the machine called a script that gives the user rights to areas on the network from that machine. When they print, they need user rights, when they access the network, they needs Internet permission rights, when they go onto the VLE they need rights, ePm rights, Group rights, Directory rights, student and staff rights, read and write rights Etc. All these are tied up in scripts stored on the network that load every time a student logs in. Setting these is the job of the network manager, and setting levels is their job too. A teacher has more rights than a students, an administrator in finance needs rights to the finance database etc. Hardware Authentication – This happens when a user tries to add something to the network, a scanner, a printer, their phone, a piece of software etc. There are two levels of Hardware rights, User and Administrator, there can be multiple administrators and each can have a different level of access. It stands to reason that at least one network user must have the authority to use the network without any of the restrictions imposed on other users. This user is called the administrator. The administrator is responsible for setting up the network’s security system. To do that, the administrator must be exempt from all security restrictions. In a locked down system, only the administrator has Hardware rights to protect the network. P5.8 – Task 20 – Describe the Policies of Authentication and the benefits of setting these access rights. M3.8 – Task 21 – Describe the circumstances in which Authentification Rights takes place with a school environment. D2.6 – Task 22 – Within your Client’s system, describe the different Access and Authentification Rights between Students and Staff and discuss the need for this security measure. P5.1 - Task 1 – Describe the facility and importance of Directory Services within a network environment. M3.1 – Task 2 – Describe the need for implementation of these Directory Services within a Primary School System in terms of security, Data Protection and ease of student use. D2.1 – Task 3 – Within your PowerPoint, evaluate the Directory Services need your business needs to take to secure their Networks. P5.2 – Task 4 – Describe the Range of Communication Services available to companies and the potential benefits of monitoring and controlling access to these. M3.2 – Task 5 – Describe the need for monitoring Communication Services within a Primary School System in terms of security, Data Protection and filtered student use. D2.2 – Task 6 – Within your PowerPoint, evaluate the procedures your organisations should take to secure their Communication Systems. P5.3 – Task 7 – Describe the Process and Benefits to companies of configuring File Sharing management services. M3.3 – Task 8 – Describe the circumstances in which File Sharing management takes place with a school environment. D2.3 – Task 9 – Within your PowerPoint, evaluate the procedures your organisations should take to secure their student information if instigating file sharing rights. P5.4 – Task 10 – Describe the need for Databases, Web and Proxy Services on a system to ensure consistent functionality. M3.4 – Task 11 - Describe the circumstances in which Application Management takes place with a school environment. D2.4 – Task 12 – Within your PowerPoint, evaluate the procedures your organisations should take to secure their Application Software if instigating student management rights. P5.5 – Task 13 – Describe the need for sharing devices on a system to ensure consistent availability. M3.5 – Task 14 - Describe the circumstances in which Device Sharing Management takes place with a school environment. P5.6– Task 15 – Describe the need for Storage Space allocation and management on a system to ensure consistent functionality. M3.6 – Task 16 - Describe the circumstances in which Storage Management takes place with a school environment. D2.5 – Task 17 – Within your PowerPoint, evaluate the Storage Space needs of your organisations and the procedures that should be taken to allocate required student and department space. P5.7 – Task 18 – Describe the facility of VOIP and Mobile Working within a Networking environment. M3.7 – Task 19 - Describe the circumstances in which VOIP and Mobile Working takes place with a school environment. P5.8 – Task 20 – Describe the Policies of Authentication and the benefits of setting these access rights. M3.8 – Task 21 – Describe the circumstances in which Authentification Rights takes place with a school environment. D2.6 – Task 22 – Within your Client’s system, describe the different Access and Authentification Rights between Students and Staff and discuss the need for this security measure.