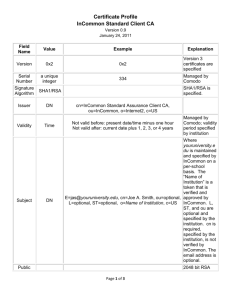
I2-RemoteProofingv
advertisement
How Do You Establish Student Identity Remotely: A Survey Keith Hazelton, University of Wisconsin-Madison Ann West, Internet2/InCommon Federation 2010 Fall Internet2 Member Meeting – Atlanta, Georgia Topics Identity Proofing Redux Survey Results Process Discussions What’s the Question? Recruit, admit, register, and award degrees to remote students But who are these people and how do you know they are who they say they are? No set of remote identity practices reviewed by key privacy and regulatory experts Thesis Statement The process by which you link the physical person to his/her identity information and to his/her credential is critical. If this is done poorly, there is little or no assurance that the person using that credential to authenticate and access services and information is who you believe them to be. It could be anyone, or multiple people over time. If this linking is weak, even the most complete personal information and the strongest credential will not improve the assurance of identity. Atomic Components Individual Identity Proofing Credentialing Credential Identity Record Credentialing The Actors Identity Vetting is the process by which information about a person is gathered. Certain aspects are verified (like mail or email address). Identity Proofing is the process by which the physical person is linked to his/her identity information. Credentialing is the process where the user is linked to his/her credential (netid) and the credential is added to his/her identity record. Authentication is verifying that the person seeking access to a resource is the one previously identified and approved. Proper authentication requires that the processes that precede it are not compromised. Financial Aid Info Received Admissions Registration Process Identity Assured ✔ Third-party Info Received FIRST CONTACT MADE APPLICATION RECEIVED ACCEPTED DEPOSIT PAID REGISTERED/O RIENTATION Your Certainty Identity Management On-boarding Identity Vetting Credentialing Identity Proofing Financial Aid Info Received Admissions Registration Process Identity Assured ✔ Third-party Info Received FIRST CONTACT MADE APPLICATION APPLICATION RECEIVED ACCEPTED DEPOSIT PAID Your Certainty Identity Management On-boarding Identity Vetting Credentialing Identity Proofing REGISTERED/O REGISTERED/O RIENTATION RIENTATION Financial Aid Info Received Admissions Registration Process Third-party Info Received FIRST CONTACT MADE Identity Assured ✔ APPLICATION APPLICATION RECEIVED ACCEPTED Your Certainty Identity Management On-boarding Identity Vetting Credentialing Identity Proofing DEPOSIT PAID REGISTERED/O REGISTERED/O RIENTATION RIENTATION Remote Proofing Survey InCommon Federation and AACRAO Survey of current practice Focus on business process; not technology Distance Education Audience Degree-granting programs Sent to 2,000 AACRAO Institutional Contacts Preliminary results reflect 100 institutions Q4: When do you first learn about prospective students? 22 Web queries 10 Email queries Q 6: How do you establish an initial communications channel with the prospect? (Check all that apply.) Other -Facebook -N/A -In person Q7: At what point is the first login credential chosen or assigned (e.g. email address, user id/password pair, etc.)? Q8: For what purposes are this initial login credential used? (Check all that apply.) Q10: If the initial login credential is assigned by a system, how do you communicate the credential to the remote person? (Check all that apply.) Q15: At what point is supporting documentation about an individual received from external third parties (e.g., testing service, etc)? (Check all that apply.) Q18: At what point do you perform primary identity proofing of the individual? (Definition) Q19: Which business office is involved in doing the identity proofing of remote individuals? (Check all that apply.) Q23: What document-related evidence do you require from the person to prove their physical identity and how is it sent to you? Q24: What other methods do you use to prove the physical identity of the person? (Check all that apply.) Identify - Minister - Verisign - Exam Proctor - Principal -Transcripts - LMS Vendor -Pastor/Ment or -Background Checks Q27: If changes were proposed to the identity proofing process for distance education students, who would be involved in the decision? (Check all that apply). Random Comments “When applying for financial aid, the FAFSA process has certain requirements and that is the documentation for most students. “ “Doing something beyond what we currently do would be extremely inconvenient for students and prospects. It would also be very labor intensive for staff. “ “My concern is access students allow parents, spouse and significant others without completing the proper consent to disclose forms for this access.” “This information is extremely confidential, just as SS information is confidential. I am not sure anyone should look at this data except for key representatives within an assigned admission area….” Preliminary Conclusions 1/3 not doing id proofing 2/3 say they are id proofing – but are they? Ideas/Proposals: Off Campus In Person Person submits an application and is accepted. There is thirdparty information on file. Institution sends notary one-time password and identity information. If subject provides convincing matching evidence to notary…. Subject is linked to identity record. Notary hands sealed envelope with a one-time token/URL to the individual so he/she can claim the credential. Subject is linked to the credential. Ideas/Proposals: Third Party Information By phone/website: Ask prospect knowledge-based questions on identity information obtained from third parties. If they answer correctly, provide the subject with a one-time token/URL via email/mailing address in the identity record. Subject is linked to the identity record. Using an address in the identity record for delivery strengthens link between subject and identity record. Subject is linked to credential. Ideas/Proposals: And This One? Person submits an application and is accepted. There is third-party information on file. Application is self-asserted information. Subject is not linked to third-party information. Institution provides a one time token/URL to the subject to their email/mailing address on record. Credential is linked to identity record. Subject is not linked to identity record. Resources InCommon IAM Online – Remote Identity Proofing Webinar http://internet2.na6.acrobat.com/p25014162 InCommon Student Services Collaboration Group https://spaces.internet2.edu/display/InCCollaborate /InC-Student Questions? Keith Hazelton, UW-Madison hazelton@doit.wisc.edu Ann West, Internet2/InCommon awest@internet2.edu