IA-IS-Relationship-Discussion_Grabski
advertisement

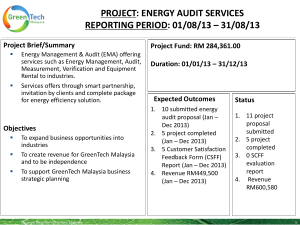
Discussion of: “The Relationship between Internal Audit and Information Security: An Exploratory Investigation” Severin Grabski Michigan State University 2011 UWCISA Symposium Toronto, Canada Stated Objective Investigate the nature of the relationship between information security and internal audit • Important – Critical component of Corporate Governance • Motivation needs to be more than “no empirical research exists” Tasks Accomplished • Established that the IA role has been generally ignored in the literature • Conducted semi-structured interviews with IA and IS security professionals • Identified factors that impact the nature of the relationship between IA and IS functions But… • Had sense of concern Proposed Model IA vs. IS Control View • IA • IS Stage of attempted penetration o Configuration – (Preventive) o Access (Preventive) • IA Review o Monitoring – Detective o Monitoring – (Detective) Control objective o Preventive o Detective o Corrective • What’s missing? • What happened to Corrective? Proposed Model But… “…no empirical research investigating how well the two functions work together.” (p.5) Proposed Model • Never addresses Role of IA and IS • How Should IA and IS Interact? o Model only shows tasks and how they are reviewed • Is there Theory for this Interaction? SOX & IT Governance • Case Study of Charles Schwab Corporation (Damianides 2005) • Top management sought improved IT Governance Framework o IA recommended COBIT o Improve IS controls o Enhance IT & Business Processes o Map audits to COBIT • On a high level, this shows units working together Proposed Model But… (p. 131)?? So How Did This Proposed Model Occur? From Here! Includes Monitoring & Documentation Basis for Proposed Model But… • Ransbotham & Mitra (2009) Model is about external attacks on an organization – information security compromise process • How does this relate to “Internal” Controls? • How does this relate to securing the system from the “Innocent Incompetent”? Proposed Model So How Did We Get Figure 3? Proposed Model NEVER TESTED! I Got Lost! I Need a Map I Need a THEORY Where’s the Theory? • While there has not been any study of IA and IS working together, there has been many studies of organizations and institutional structure • Possible theory – Neo-institutional Theory Neo-institutional Theory • Should be used for studying IT security issues in organizations (Bjorck 2004) o Can be used to explain differences in formal and actual security behavior o Can be used to explain why formal security structures are created and not fully implemented • Can be used to explain how institutional factors influence the behavior of individuals (Hu et al. 2007) Neo-institutional Theory • Organizations are structured by phenomena in institutional environment and become isomorphic with them • Two parts Institutionalism Isomorphism Institutionalism • Process in which components of formal structure become accepted, and are seen as appropriate and needed • Decision to adopt depends upon whether the innovation will improve internal processes Isomorphism • Explains how institutional structures and practices propagate among organizations o Coercive Isomorphism (External pressure) o Mimetic Isomorphism (Imitation) • Software selection (Tingling & Parent 2002) o Normative Isomorphism (Professionalism) • Mediating role of top management in ES assimilation (Liang et al. 2007) Benefit of Theory • Guide formulation of constructs & interview questions • Focus does not need to be on testing neo-institutional theory • Focus can be on extending theory • Could still use case-based approach Research Instrument • Discuss “perceived inequality” o Never appears in research instrument o What does appear is “Working Relationship” • Suggest that “Organizational Characteristics” impact relationship o “Working Relationship,” “Audit Demographics,” and “IT Demographics” are used Setting - Education • Concern about Security o More or less in Education than Business? o Many Laws (FERPA, GLBA, PCI, HIPPA, States also have laws/penalties for data disclosure, etc.) impact Universities • Manuscript states that security was not an overarching strategic factor. • How can security not be a major concern? Research Method • Good Approach • Did the participants get the opportunity to review the transcripts and correct errors/omissions? • Need to state in the Research Method section that an IA and IS security person were interviewed at institutions that did not outsource IA (information is only in Table 1) Findings • Technical Knowledge o Tech knowledge deeper relationships o Or is it that they know the correct questions to ask and can bring value to the IS team? • Communication Skills o If IA explains what & why, than IS is cooperative • Auditor’s Perception of the Role of IA vis-à-vis Information Security Findings • Does Technical Knowledge Result in Improved Communication Skills & Result in Increased Cooperation with IS? IS perceived top management to be very supportive of information security but, adequate resources were not necessarily forthcoming (in Not For Profit) Findings • How can IS and IA work smarter with fewer (limited) resources? For Profit • Budgetary Support • Incentive for Audit Compliance • Why? Security Issues Related to Financial Results IT Corporate Governance Relationships Matter IS IA IA IS IS IS Relationships Matter • A collaborative relationship between the internal audit and information systems security functions increases user compliance, improves the effectiveness of internal audit (P6 A&B) • More interesting question: How is a collaborative relationship established? Additional Survey • Interviewed CIO o IA was “bad guy” in the past o IA had stringent standards o Didn’t understand that IT Security is situational (practical, unsecure to totally secure but impractical) • SSN need high security • Other stuff can be wide-open o Had to work with IA to be “practical” • Could not apply all of COBIT all the time! o IA acts like an extra set of eyes & ears • Working smarter Additional Survey • IA did not want to disclose standards used in audit o Releasing audit standards viewed as “teaching to the test” o Needed to get shared understanding of standards good practices • IS can now share these good practices • Facilitates audit • IS can help invent technologies to meet new standards, e.g., PCI, etc. Additional Survey • IA tells IS the annual audit plan • IS uses IA for help garnering additional resources o Card Lock system for Server Rooms o Expanded for Physical Security across campus • CIO & IA Director have mutual respect • This “Top Management” directly influences the other IA and IS unit employees Summary • Need clear evolutionary path from literature to Figure 2 to Figure 3 • Theory • Gap between questions in research instrument and issues identified in the manuscript • Relationship to ERM • Operationalize Constructs • Model Specified Correctly? Closing Comments • Enjoyed manuscript • Do we know if the proposed model (Figure 3) would change if the IA and IS were viewed as belonging to o “High performing” organizations? o “Low performing” organizations?