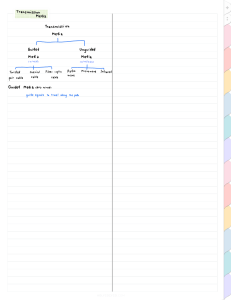
THE UNIVERSITY OF THE WEST INDIES EXAMINATIONS OF DECEMBER 2022 Code and Name of Course: MGMT 2006 – Management Information Systems 1 Paper: BSc Date and Time: December 14th at 4pm Duration: Two Hours INSTRUCTIONS TO CANDIDATES: This paper has 2 pages and 3 questions. Department Of Management Studies MGMT 2006 – Management Information Systems 1 Final Exam – St. Augustine Complete ALL Questions ©The University of the West Indies Course Code MGMT 2006 Complete ALL Questions Question 1 Briefly describe the following five terms: CRM, End User Development, Experts Systems, CIA Triangle, Tacit Knowledge (10 Marks) CRM: Customer Relationship Management (CRM) refers to the practices, strategies, and technologies that companies use to manage interactions with customers and potential customers. The aim of CRM is to improve customer satisfaction, loyalty, and retention by analyzing customer data, tracking customer behavior, and optimizing customer interactions at all touchpoints . End User Development: End User Development (EUD) refers to the process by which nonprogrammers develop software applications to meet their specific needs. EUD tools and platforms enable end-users to create, modify, and customize software applications without relying on IT professionals. EUD is becoming increasingly popular as users seek to automate routine tasks and optimize their workflow. Expert Systems: Expert Systems are computer programs that use artificial intelligence (AI) and machine learning (ML) algorithms to mimic the decision-making capabilities of a human expert in a particular field. These systems can be used in various applications, such as medical diagnosis, financial analysis, and legal research, among others. Expert systems can provide accurate, consistent, and reliable solutions to complex problems, even in the absence of a human expert. CIA Triangle: The CIA Triangle is a widely recognized model in the field of information security that stands for Confidentiality, Integrity, and Availability. Confidentiality refers to the protection of sensitive information from unauthorized access, disclosure, or theft. Integrity refers to the assurance that information is accurate, complete, and reliable. Availability refers to the accessibility of information and systems when needed. Tacit Knowledge: Tacit Knowledge is a type of knowledge that is difficult to formalize, articulate, or transfer to others. It refers to the skills, expertise, and insights that people acquire through experience, observation, and practice. Tacit knowledge is often intuitive, implicit, and context-specific, and is therefore difficult to codify or document. Tacit knowledge is particularly valuable in fields where human judgment and intuition play a critical role, such as art, design, and leadership. ©The University of the West Indies Course Code MGMT 2006 Question 2 As Campus CIO you need to select a transmission media type to connect about three dozen buildings to the campus network backbone. What types are available, and which would you recommend given the very high data traffic requirements . (10 Marks ) As the Campus CIO, there are several transmission media types available for connecting the buildings to the campus network backbone. These include: • Fiber Optic Cable: Fiber optic cable is an excellent choice for high-speed data transmission. It offers high bandwidth and is capable of carrying large amounts of data over long distances without signal degradation. It is also immune to electromagnetic interference and provides high security against tapping. • Twisted Pair Cable: Twisted pair cable is a common type of transmission media that is used in local area networks (LANs). It consists of pairs of wires that are twisted together to reduce interference. It offers good bandwidth and is relatively inexpensive, but it is not suitable for long distances. • Coaxial Cable: Coaxial cable is another type of transmission media that is commonly used in LANs. It consists of a central conductor surrounded by insulation, a shield, and an outer jacket. It offers high bandwidth and is suitable for longer distances than twisted pair cable. Given the very high data traffic requirements, I would recommend using fiber optic cable for connecting the buildings to the campus network backbone. Fiber optic cable offers the highest bandwidth and is capable of carrying large amounts of data over long distances without signal degradation. It is also immune to electromagnetic interference and provides high security against tapping. Although it is more expensive than other types of transmission media, the benefits of using fiber optic cable outweigh the cost. ©The University of the West Indies Course Code MGMT 2006 Question 3 The SDLC has been criticized for being too slow to keep up with a dynamic environment. Given that you know need to introduce a modern supply chain management system what alternative techniques are available and what would you recommend. (10 Marks) The SDLC (Software Development Life Cycle) is a traditional approach to developing software that includes stages such as requirements gathering, design, development, testing, deployment, and maintenance. While it provides a structured approach to software development, it has been criticized for being too slow and inflexible to keep up with the fast-paced and dynamic environment of modern businesses. There are several alternative techniques available that can be used to develop software in a more agile and flexible manner. Some of these include: • Agile software development: This approach emphasizes collaboration, flexibility, and adaptability in software development. It involves breaking the development process into small, iterative cycles, with frequent feedback and testing. • DevOps: DevOps is a software development methodology that emphasizes collaboration and communication between development and operations teams. It focuses on automating the software development process and streamlining the deployment and maintenance of software. • Rapid application development (RAD): This approach involves prototyping and iterative development, with a focus on rapid development and deployment of software. It emphasizes user involvement and feedback to ensure that the software meets the needs of the business. • Continuous Integration and Continuous Deployment (CI/CD): This approach involves automating the build, testing, and deployment of software to enable faster and more frequent releases. Based on the need to introduce a modern supply chain management system, I would recommend using an Agile software development approach. This will enable the development team to collaborate closely with stakeholders, quickly adapt to changing requirements, and deliver software in small, iterative cycles that can be tested and refined based on feedback. This approach will help ensure that ©The University of the West Indies Course Code MGMT 2006 the supply chain management system meets the needs of the business and can be quickly adapted to changing market conditions. Question 4 The eConnect and Learn (eCal) laptop project has been criticized as a failure given that it did little to improve learning outcomes in secondary schools. Using the terminology introduced in this course, indicate what you think went wrong and make suggestions as to how it could have been improved. (10 Marks) The eConnect and Learn (eCal) laptop project was aimed at improving learning outcomes in secondary schools through the provision of laptops to students. However, the project was criticized as a failure as it did little to improve learning outcomes. There are several reasons why the project may have failed, including: • Lack of proper planning: It is possible that the project was not properly planned, and there was no clear strategy for implementing it. Without a clear plan, it would have been difficult to ensure that the laptops were being used effectively in the classroom. Lack of user involvement. • Poor implementation: Even if there was a plan, poor implementation can still cause the project to fail. There may have been insufficient resources or training provided to teachers, which could have prevented them from using the laptops effectively in the classroom. • Inadequate monitoring and evaluation: It is also possible that there was insufficient monitoring and evaluation of the project's progress. Without regular monitoring, it would have been difficult to identify any issues early on and make necessary adjustments to the project. To improve the project's success, the following suggestions could be made: • Develop a clear plan: The project should have a clear plan with specific objectives and strategies for implementation. This would help to ensure that all stakeholders are on the same page and working towards a common goal. • Provide training and resources: Teachers and students should be provided with adequate training and resources to ensure that they can use the laptops effectively in the classroom. • Regular monitoring and evaluation: The project should be regularly monitored and evaluated to identify any issues early on and make necessary adjustments. This would help to ensure that the project is on track and achieving its objectives. ©The University of the West Indies Course Code MGMT 2006 Overall, the success of the eConnect and Learn (eCal) laptop project would have depended on proper planning, effective implementation, and regular monitoring and evaluation. By incorporating the above suggestions, it could have been possible to improve learning outcomes in secondary schools through the use of laptops. Question 5 What technique would you use to decide how to allocate your limited budget to securing your company's dozens of information systems , some critical , some less so. always seems like there isn't enough money to go around . (10 Marks ) To decide how to allocate a limited budget to securing a company's information systems, one approach is to use a risk-based approach. This involves assessing the risks associated with each information system and allocating resources accordingly. The risk assessment process typically involves the following steps: • Identify assets: Identify all the assets within the company that need to be protected, such as hardware, software, data, and personnel. • Identify threats: Identify potential threats to each asset, such as unauthorized access, malware attacks, natural disasters, and human error. • Assess vulnerabilities: Determine the vulnerabilities of each asset, such as weak passwords, outdated software, and insufficient security controls. • Analyze the likelihood and impact of each risk: Estimate the likelihood of each threat occurring and the potential impact it would have on the asset and the company. • Prioritize risks: Rank the risks based on their likelihood and impact to determine which ones pose the greatest risk to the company. • Allocate resources: Allocate resources to address the highest priority risks first, based on the available budget. By using a risk-based approach, companies can prioritize their security investments based on the level of risk associated with each information system, and ensure that limited resources are allocated where they are needed most. End of Exam ©The University of the West Indies Course Code MGMT 2006