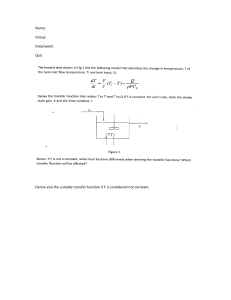
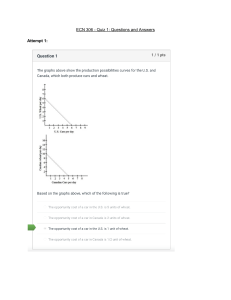
Chapter 2 Quiz 1. While information systems were once primarily used to automate manual processes, they have transformed the nature of work and the shape of organizations themselves. True 2. The activities that lead to getting the right product into the right consumer's hands in the right quantity at the right time at the right cost are known as value chain management. False 3. The successful implementation for change only happens when people accept the need for change and believe that it will improve factors such as productivity and/or customer satisfaction. True 4. "Adapting" is the second stage in Lewin's Change Model, which involves learning new work methods, behaviors, and systems. False 5. Today, many organizations can function and compete effectively without computer-based information systems. False 6. Reengineering and continuous improvement have the same definition. False 7. The information systems operations group is responsible for the day-to-day running of IS hardware to process the organization’s information systems workload. True 8. Over time, disruptive innovation tends to become less attractive to users in a new market. False 9. Opportunities in information systems are available to people from different parts of the world. True 10. A traditional view of information systems holds that organizations use them to control and monitor processes and ensure effectiveness and efficiency. True 11. For someone to be a good CIO, technical ability is the most important characteristic. False 12. According to Lewin's Change Model, an organization must deliberately change old habits, learn new work methods, and accept the new work methods as parts of the job. True 13. Perceived usefulness and ease of use of a system influence an individual’s attitude toward the system. True 14. The diffusion of innovation theory can be useful in planning the rollout of a new information system. True 15. Suppose a retail business has an unwritten rule that "every sales person cooperates with others." This is an example of organizational culture. True 16. A sustaining innovation is one that initially provides a lower level of performance than the marketplace has grown to accept. -> False 17. When an organization hires another firm in another country to perform a specific function on its behalf, it is known as offshoring. -> True 18. Suppose an organization wishes to change for the better. It can accomplish that just by changing people's roles, responsibilities, and lines of authorities. -> False 19. The concept of a value chain is not significant to organizations unless they manufacture products. > False 20. One of the primary roles of a senior IS manager is to communicate with other areas of the organization to determine changing business needs. -> True 21. Organizations cannot have many value chains. False 22. The role of a systems analyst is narrowly defined and seldom involves communications with others. False 23. An organization’s structure is independent of its goals and approach to management. False Chapter 3 Quiz 1. Primary memory, which holds program instructions and data, is not associated with the central processing unit (CPU). False 2. Depending on the brand of tablet you purchase, you may be able to enter data by typing on a keyboard, writing on the screen with a stylus, or speaking into the tablet's microphone. True 3. Cache memory is available in two forms: level 1, which is found on the CPU chip, and level 2, which can be accessed over a high-speed dedicated interface. False 4. RAM stands for random access memory; a form of memory that holds its contents even if the current is turned off or disrupted. False 5. A tablet computer is a low-cost, centrally managed computer with no internal or external attached drives for data storage. False 6. Chip-and-PIN cards employ a computer chip that communicates with a card reader using infrared frequencies so that the cards do not need to be swiped at a terminal. False 7. There are a number of compact disk devices including read-only, recordable, and rewritable. True 8. Completing an instruction involves two phases (instruction and execution), which are each broken down into three steps in each phase. False 9. Each central processing unit (CPU) produces a series of electronic pulses at a predetermined rate, called the clock speed, which affects machine cycle time. True 10. As the difference among computer manufacturers in the areas of price and performance narrows, support for green computing is emerging as a new business strategy for these companies to distinguish themselves from the competition. True 11. Virtual tape technology can decrease data access time, lower the total cost of ownership, and reduce the amount of floor space consumed by tape operations. True 12. A redundant array of independent/inexpensive disks (RAID) is a method of storing data so that data can be accessed more quickly. False 13. Disk mirroring is a method of storing data that generates extra bits of data from existing data, allowing the system to create a "reconstruction map" so that if a hard drive fails, it can rebuild lost data. False 14. Thin client computers are a type of portable single-user computers. False 15. Bioprinting, which uses 3D printers to build human parts and organs from actual human cells, is widely considered to be unethical. False Chapter 4 Quiz 1. On a modern home computer, one can set up accounts for many users and be able to control what resources a user may access. True 2. Utility programs help to perform maintenance, correct problems, merge and sort sets of data, keep track of computer jobs, and compress data files. True 3. The operating system’s application programming interface (API) provides software developers with tools they use to build application software without needing to understand the inner workings of the operating system and hardware. True 4. Windows 10 is an example of application software. False 5. Proprietary software is mass-produced by software vendors to address needs that are common across businesses, organizations, or individuals. False 6. An operating system is a set of programs that controls the computer hardware and acts as an interface with applications. True 7. Your friend has a Mac that runs OS X. If she needs to run a Windows app on it, she can set it to run Windows also. True 8. Most operating systems support virtual memory which allocates space on the hard disk to supplement the immediate, functional memory capacity of RAM. True 9. Each programming language has a set of rules, called the program code of the language. False 10. Yahoo has developed its own Linux-based operating system called Chrome OS False 11. A software suite is a collection of programs packaged together as a bundle and typically includes a word processor, spreadsheet program, graphics program, and more. True 12. A command-based user interface employs icons and menus that people use to send commands to the computer system. False 13. If a large organization wants software that will benefit the entire organization—what's known as enterprise application software—the organization must develop it specifically for the business in order to get the functionality required. False 14. If 10 users can run programs at the same time on the same computer, it is known as multitasking. False 15. The primary function of application software is to apply the power of the computer to enable people, workgroups, and the entire enterprise to solve problems and perform specific tasks. True Chapter 5 Quiz 1. Suppose a manager wishes to analyze historical trends in sales. He would use the online transaction processing (OLTP) system. False 2. Carlos is working with an existing database, but he wants to eliminate some of the columns in the table to create a new, more streamlined database. He will use projection to create his new database. True 3. A relational model splits the information up into many two dimensional data structures. True 4. A collection of data fields that are all related to one object, activity, or individual is called a file. False 5. Sometimes a database can contain "bad data," meaning incomplete, incorrect, inaccurate, or irrelevant records, which can be corrected or deleted through data cleansing. True 6. If "color" is an attribute, then "green" is a data item. True 7. For each data item, a data dictionary usually contains information such as the name of the data item, the range of values that can be used, and the amount of storage needed for the item. True 8. It is possible to restrict access to data depending on the database user's privileges. True 9. An enterprise data model is created only for documentation, but is otherwise inconsequential. False 10. A field is typically a name, number, or combination of characters that describes an aspect of a business object. True 11. DBMSs are used primarily for modeling data. False 12. In the context of the relational database model, selecting involves combining two or more tables. False 13. The relational model describes data using a standard tabular format; all data elements are placed in three-dimensional tables called relations, which are the logical equivalent of files. False 14. One of the primary advantages of a relational database is that it allows tables to be linked to reduce data redundancy and allow data to be organized more logically. True 15. A database administrator (DBA) is an important nontechnical position responsible for defining and implementing consistent principles for a variety of data issues, including setting data standards and data definitions that apply across all the databases in an organization. False Chapter 6 Quiz 1. A telecommunications protocol is any material substance that carries an electronic signal to support communications between a sending and receiving device. False 2. A personal area network (PAN) is a wireless network that connects information networking devices within a small area, such as an office, home, or several floors of a building. False 3. A podcast is a video broadcast over the Internet. False 4. When you use your lab computer to access a printer, you are using the local area network (LAN). True 5. JavaScript can be used to validate data entry in a Web form. True 6. Like other programs, Java software can run only on specific types of computers. False 7. Cascading Style Sheets (CSS) use special Hypertext Markup Language (HTML) tags to globally define font characteristics for a variety of page elements as well as how those elements are laid out on a Web page. True 8. The Transmission Control Protocol (TCP) is responsible for managing IP addresses and Internet domain names. False 9. A virtual private network (VPN) supports a secure, encrypted connection between a company’s employees and remote users through a third-party service provider. True 10. The Internet is the infrastructure on which the Web exists. True 11. When you point the remote control to turn on/off the TV, the remote is using radio frequency True 12. Video content can be placed on the Internet using the same approach as a blog. True 13. Sensors that can monitor and report on data about traffic and parking conditions are part of a network of physical objects known as the Internet of Technology. False 14. There is no way a manufacturing firm would implement an Internet of Things because the risk of hacking is far too high. False 15. In a Hypertext Markup Language (HTML), the markers are codes that tell the browser how to format the text or graphics that will be displayed. False Chapter 7 Quiz 1. In 1992, the Supreme Court ruled that online retailers must collect sales taxes even in states where they lack a physical presence. False 2. Smart card use is restricted to data associated with financial transactions. False 3. Consortium-operated exchanges are open to any set of buyers and sellers within a given market. False 4. If you abandon an online shopping cart, the seller does not care what you were shopping for. False 5. In the past, market segmentation has been easy for B2B marketers because firmographic data was easy to obtain. False 6. Bartering is a technique used by advertisers to recapture shoppers who abandoned a Website without making a purchase. False 7. Smart cards are less protected from misuse that conventional credit, charge, and debit cards because the smart card information is not encrypted. False 8. The length of sales process for a typical business-to-business (B2B) e-commerce is shorter than that for a typical consumer-to-consumer (C2C) e-commerce. False 9. Consumers who have enrolled in mobile banking and downloaded the mobile application to their cell phones can check their credit card balances before making major purchases. True 10. An electronic exchange is an electronic forum where manufacturers, suppliers, and competitors buy and sell goods, trade market information, and run back-office operations. True 11. The three basic components of a successful e-commerce model include content, commerce, and community. True 12. An organization uses buy-side e-commerce to purchase goods and services from its suppliers. True 13. A mobile advertiser can find how many people clicked on his ad and how many people bought his product or service. True 14. In Kenya and Tanzania, it is not uncommon for citizens to carry out common financial transactions using mobile phones. True 15. The Asia-Pacific region has overtaken North America as the region with the largest B2C sales and now accounts for over one-third of total worldwide B2C sales. True Chapter 8 Quiz 1. Smaller lot sizes from vendors will help reduce the purchasing complexities for the consumer. True 2. The efficiency of processes for managing customer payments can vary; some processes are more efficient than others. True 3. Using the hosted software model implies that a small business firm needs to employ a fulltime IT person to maintain key business applications. False 4. A designer would use computer aided manufacturing (CAM) to create, analyze, and modify the design of a component. False 5. Enterprise resource planning (ERP) systems work directly with manufacturing machines on the production floor. False 6. The ability to capture and analyze all customer interactions, generate appropriate responses, and gather data to create and build effective and efficient marketing campaigns is known as contact management. False 7. In an organization, a transaction processing system (TPS) supports routine operations associated with its business processes. True 8. XYZ Inc. assigned a part-time mid-level manager to supervise the implementation of an enterprise resource planning (ERP) system. The project has a high risk of failure. True 9. Large organizations were the first to take on the challenge of implementing enterprise resource planning (ERP). True 10. Organizations frequently need to customize a vendor's enterprise resource planning (ERP) software to integrate other business systems. True 11. To successfully implement a supply chain management system, an organization must be able to integrate its systems with its suppliers. True 12. Implementation of an enterprise resource planning (ERP) system provides an organization with an opportunity to also upgrade the information technology that it uses. True 13. It is acceptable to for transaction processing systems to capture inaccurate data. False 14. A customer relationship management (CRM) system helps a company to plan, execute, and control all the activities involved in raw material sourcing and procurement, conversion of raw materials to finished products, and the warehousing and delivery of finished product to customers. False 15. Legacy systems typically run on the latest hardware. False