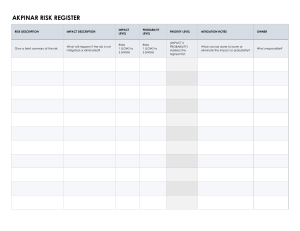
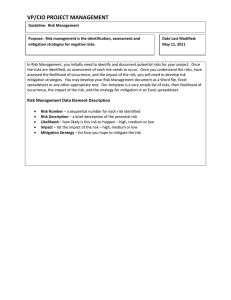
What is risk mitigation? 1.Identify all possible events in which risk is presented. A risk mitigation strategy takes into account not only the priorities and protection of missioncritical data of each organization, but any risks that might arise due to the nature of the field or geographic location. A risk mitigation strategy must also factor in an organization's employees and their needs. 2.Perform a risk assessment, Which involves quantifying the level of risk in the events identified. Risk assessments involve measures, processes and controls to reduce the impact of risk. 3.Prioritize risks, Which involves ranking quantified risk in terms of severity. One aspect of risk mitigation is prioritization -- accepting an amount of risk in one part of the organization to better protect another. By establishing an acceptable level of risk for different areas, an organization can better prepare the resources needed for BC, while putting fewer mission-critical business functions on the back burner. 4.Track risks, monitoring Risk Which involves monitoring risks as they change in severity or relevance to the organization. It's important to have strong metrics for tracking risk as it evolves, and for tracking the plan's ability to meet compliance requirements. 5.Implement and monitor progress, evaluating Which involves reevaluating the plan's effectiveness in identifying risk and improving as needed. In business continuity planning, testing a plan is vital. Risk mitigation is no different. Once a plan is in place, regular testing and analysis should occur to make sure the plan is up to date and functioning well. Risks facing data centers are constantly evolving, so risk mitigation plans should reflect any changes in risk or shifting priorities. Types of risk mitigation strategies There are several types of risk mitigation strategies. Often, these strategies are used in combination with each other, and one may be preferable over another, depending on the company's risk landscape. They are all part of the broader practice of risk management. Risk avoidance is used when the consequences are deemed too high to justify the cost of mitigating the problem. For example, an organization can choose not to undertake certain business activities or practices to avoid any exposure to the threat they might pose. Risk avoidance is a common business strategy and can range from something as simple as limiting investments to something as severe as not building offices in potential war zones. Risk acceptance is accepting risk for a given period of time to prioritize mitigation efforts on other risks. Risk transfer allocates risks between different parties, consistent with their capacity to protect against or mitigate the risk. One example of this would be a defective product built with some amount of third-party material. The producer of the product may transfer responsibility for a certain fraction of the risk because of this. Risk monitoring is the act of watching projects and the associated risks for changes in the impact of the associated risks. Risk can affect any combination of performance, cost and scheduling; therefore, different strategies should be used to address risks based on the way they affect these factors. For example, it might be more important for a company to perform well than for it to save money in a certain project scenario. The company would likely employ a risk acceptance strategy, temporarily prioritizing risks that affect performance more heavily than cost. A diagram showing how quantitative risk assessment can be used to evaluate the likelihood and impact of risk events. Risk mitigation best practices Below are some risk mitigation best practices that information security professionals should follow: Make sure stakeholders are involved at each step. Stakeholders may be employees, managers, unions, shareholders or clients. All perspectives are important for developing a comprehensive, holistic risk mitigation strategy. Create a strong culture around risk management. This means communicating the values, attitudes and beliefs surrounding risk and compliance from the top down. It's important for every employee to have risk awareness, but the probability of a strong culture is greatly improved when management sets the tone. Communicate risks as they arise. Risk awareness must be strong throughout the entire organization, so facilitating communication of new, high-impact risks is important to keep everyone up to speed. Ensure risk management policy is clear So employees are able to follow it. Roles and responsibilities should be clearly defined, and each defined risk needs a clear process for dealing with it. Continuously monitor possible risks. Risk monitoring practices should also be clearly defined and implemented to continuously improve the risk mitigation plan. Risk mitigation tools One commonly used risk mitigation tool is a risk assessment framework (RAF). An RAF provides an organization with an outline of which systems are at high or low risk and presents information for both technical and nontechnical personnel. An RAF can be used as a risk mitigation tool by presenting consistent risk assessment and reporting methods. Common RAFs include the Risk Management Guide for Information Technology Systems from the National Institute of Standards and Technology (NIST); the Operationally Critical Threat, Asset, and Vulnerability Evaluation (OCTAVE) from Carnegie Mellon University; and Control Objectives for Information and Related Technology (COBIT) from the Information Systems Audit and Control Association (ISACA). The Miter website also offers comprehensive guidelines for risk mitigation. Some other commonly used risk mitigation tools are: A probability and impact matrix. A SWOT (strengths, weaknesses, opportunities, threats) analysis. A root cause analysis. CONTACT US What is Risk Mitigation? The Four Types and How to Apply Them Welcome to our guide to risk mitigation, where we will explore the key concepts, strategies, and best practices to effectively manage and mitigate risks in your organization. Whether you are a seasoned risk professional or new to the field, this guide will provide you with valuable insights and practical tips for implementing a successful risk mitigation plan. The Corporate Risk Mitigation Checklist 1.Gain management support. This gets overlooked a lot, but it’s very important. You have to communicate with management about the importance of assessing (and reassessing) risk and get their buy-in. Otherwise everything else you do will likely be for nothing. 2.Identify team members. Who’s going to help you conduct the risk assessment? Needed are a leader, subject matter experts, and technical writers. The SMEs are key; you need to get to the operational leadership to be able to obtain a clear, informed view of the risks facing the company. 3.Identify risks. What are the areas externally and internally that pose threats to the organization? Think about natural disasters, technological risks, risks involving single points of failure (whether they reside in equipment or people), and risks arising from your location. For more on identifying risks, see this post on conducting threat and risk assessments. 4.Assess and prioritize the risks. Evaluate risks in terms of how severe the impact would be if they occurred and also the likelihood of their occurring. Prioritize in this order: High impact and highly likely to occur o High impact and less likely to occur o Low impact and highly likely to occur o Low impact and less likely to occur 5.Determine mitigation options. The main risk mitigation options are: o Avoid the risk (exit activities that bring it on or turn over to a third party) o Reduce the risk (take steps to reduce the likelihood of a negative event occurring) o Accept the risk (live with the risk, acknowledging that if the threat occurs the organization will have to bear the consequences) 6.Develop the mitigation plan. Work out what approach the company will take to deal with each of its high priority risks. 7.Test the plan. Where appropriate, test the mitigation solutions or steps to ensure they are working as intended. 8.Implement the plan. Execute on the mitigation plan as developed and tested. o 9.Monitor the plan. Keep taps on the progress of your implementation as well as on the business environment, which is subject to change. 10. Review and update the plan. Repeat steps 3-8 on a continuous basis in recognition of the fact that risk mitigation is not a project but an on-going process. An additional item that could be added is measuring residual risk, which was discussed in detail in this post from a couple of weeks ago.