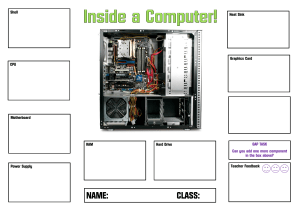
Components of an Operating System An operating system (OS) is a complex software program that serves as an intermediary between a computer's hardware and its user applications. It provides essential services and manages various resources to ensure smooth and efficient operation of the computer. The components of an operating system typically include: 1. Kernel: The core component of the operating system that manages hardware resources, such as CPU, memory, and I/O devices. It provides essential services like process management, memory management, and device management. 2. Process Management: Handles the creation, scheduling, and termination of processes or tasks. It ensures that multiple processes can run concurrently on a computer. 3. Memory Management: Manages the allocation and deallocation of memory to processes. This includes virtual memory management to provide an illusion of larger memory space than physically available. 4. File System: Manages files and directories, including creation, deletion, reading, and writing of data. It also handles file permissions and access control. 5. Device Management: Controls and communicates with hardware devices, such as printers, keyboards, mice, disks, and network interfaces. Device drivers are used to interface with specific hardware components. 6. User Interface: Provides a way for users to interact with the computer, either through a command-line interface (CLI) or graphical user interface (GUI). 7. Networking: Manages network connections and communication, enabling the computer to connect to networks, the internet, and other devices. 8. Security and Access Control: Enforces security policies, authentication, and authorization to protect the system and user data from unauthorized access or malicious software. 9. Error Handling and Logging: Detects and manages errors, logs system events, and provides information for debugging and troubleshooting. 10. Utilities: Includes various system utilities and tools for tasks like system configuration, software updates, and performance monitoring. 11. Interprocess Communication (IPC): Provides mechanisms for processes to communicate and share data with each other, such as pipes, sockets, and shared memory. 12. System Calls: Interfaces that allow user-level applications to request services from the kernel. They act as bridges between user-space and kernel-space. 13. Schedulers: Control the allocation of CPU time to processes and determine which process should run next. Different schedulers may be used for real-time systems, desktops, or servers. 14. Power Management: Manages the power state of the hardware components to optimize energy consumption and extend battery life on laptops and mobile devices. These components work together to ensure the proper functioning of the computer system, providing an environment in which users and software applications can run effectively and efficiently. The specific features and implementations of these components can vary between different operating systems (e.g., Windows, Linux, macOS) and their versions. what are the parts and work of memory management in operating system Memory management is a crucial part of an operating system (OS) responsible for managing a computer's memory resources. Its primary function is to allocate, control, and optimize the use of memory to ensure that processes run efficiently and without interference. Here are the key components and functions of memory management in an OS: Memory Allocation: Process Allocation: Memory management allocates memory space to individual processes as they are created. Each process requires a portion of memory to store its code, data, and stack. Memory Protection: . Access Control: Memory management enforces access controls to prevent processes from accessing memory regions that do not belong to them. Unauthorized access can lead to data corruption or security breaches. 1. Memory Mapping: Virtual Memory: Many modern operating systems use virtual memory, which allows processes to access more memory than physically available. Memory management maps virtual addresses to physical addresses, and it swaps data between RAM and storage (e.g., hard disk) as needed. 2. Address Translation: Address Translation: Memory management translates virtual memory addresses used by processes into physical memory addresses. This translation ensures that processes can access the correct physical memory locations. 3. Memory Deallocation: Process Termination: When a process terminates or is no longer needed, memory management deallocates the memory it occupied, making it available for other processes. 4. Memory Fragmentation: Fragmentation Management: Memory management addresses both external fragmentation (unused memory blocks between allocated blocks) and internal fragmentation (wasted memory within allocated blocks). Techniques like compaction and paging are used to reduce fragmentation. 5. Page Tables and Segmentation: Page Tables: In virtual memory systems, page tables are used to manage the mapping between virtual addresses and physical addresses. They enable efficient address translation. Segmentation: In some systems, memory is divided into segments, each with its own access rights and attributes. Memory management handles segmentation and ensures processes do not violate memory boundaries. 6. Swapping and Paging: Swapping: When physical memory becomes scarce, memory management may temporarily move entire processes or portions of processes to secondary storage (e.g., disk) to free up physical memory. This process is known as swapping. Paging: Another technique used in virtual memory systems involves dividing memory into fixed-size blocks called pages. Memory management swaps pages in and out of physical memory, improving efficiency and reducing fragmentation. 7. Memory Compaction: Compaction: In systems with external fragmentation, memory management may periodically rearrange memory to consolidate free memory blocks, reducing wasted space. 8. Memory Protection and Isolation: Protection Rings: Some operating systems employ protection rings or privilege levels to isolate processes and ensure that lower-privileged processes cannot access the memory of higher-privileged ones. 9. Cache Management: Cache Control: Memory management may coordinate with hardware-level memory caches to optimize data access speeds. 10. Error Handling: Error Detection: Memory management may include error detection mechanisms to identify and handle memory-related errors such as hardware faults or corruption. what are the primary and secondry memory Primary memory (also known as main memory or RAM) and secondary memory are two distinct types of computer storage that serve different purposes within a computer system. Here's an explanation of both: 1. Primary Memory (RAM - Random Access Memory): Nature: Primary memory is the computer's main working memory, and it is volatile, meaning its contents are lost when the computer is powered off or restarted. Purpose: RAM is used to store data and instructions that the CPU (Central Processing Unit) and running programs need for immediate processing. It provides quick access to data, allowing the CPU to work with data in real time. Speed: Primary memory is much faster than secondary memory (typically measured in nanoseconds), making it ideal for tasks that require quick access to data and programs. Capacity: RAM capacity varies from computer to computer but is typically measured in gigabytes (GB) or terabytes (TB) in modern systems. Examples: DDR4 or DDR5 RAM modules used in desktops and laptops. 2. Secondary Memory (Storage Devices): Nature: Secondary memory refers to non-volatile storage devices that retain data even when the computer is powered off. These devices are typically slower than primary memory. Purpose: Secondary memory is used for long-term data storage. It holds the computer's operating system, applications, user files, and data that need to persist beyond a single session. Speed: Secondary memory devices, such as hard disk drives (HDDs) and solidstate drives (SSDs), are slower than RAM but offer high-capacity storage. Capacity: Secondary memory devices have much larger storage capacities compared to RAM. HDDs and SSDs can have capacities ranging from hundreds of gigabytes to multiple terabytes. Examples: Hard disk drives (HDDs), solid-state drives (SSDs), USB flash drives, external hard drives, optical discs (e.g., DVDs and Blu-rays). In summary, primary memory (RAM) is a fast but volatile form of memory used for temporarily storing data and instructions that the CPU needs while running programs. Secondary memory consists of non-volatile storage devices used for long-term data storage, including the computer's operating system, applications, and user files. Both types of memory serve crucial roles in the functioning of a computer system, with primary memory focusing on immediate data access, and secondary memory focusing on data persistence and long-term storage. what are the types of operating system Operating systems can be categorized into several types based on various criteria, including their intended use, design principles, and architecture. Here are some common types of operating systems: 1. Single-User, Single-Tasking OS: Designed for single users and can run only one application at a time. Examples include early personal computer OS like MS-DOS. 2. Single-User, Multi-Tasking OS: Supports a single user running multiple applications concurrently. Most modern desktop and laptop operating systems, such as Windows, macOS, and Linux, fall into this category. 3. Multi-User OS: Designed to support multiple users simultaneously. These OS can manage resources and provide services to multiple users or processes. Unix, Linux, and various server operating systems fall into this category. 4. Real-Time OS (RTOS): Optimized for systems with strict timing requirements, such as embedded systems, robotics, and industrial control systems. RTOS guarantees that tasks meet specific deadlines. Examples include VxWorks and QNX. Network OS: Primarily designed for managing network resources and services. They include features like file sharing, print sharing, and network protocols. Novell NetWare is an example. Distributed OS: Designed for distributed computing environments, where multiple computers work together as a single system. They manage resources across a network, such as distributed file systems. Examples include Google's Chrome OS and Amoeba. Mobile OS: Designed for smartphones, tablets, and other mobile devices. They are optimized for touch interfaces and mobile hardware. Examples include Android, iOS, and Windows Mobile. Embedded OS: Tailored for embedded systems with limited hardware resources, often built into devices like appliances, automobiles, and industrial machines. Examples include Embedded Linux and VxWorks. Multi-Core and Parallel OS: Designed to leverage multiple CPU cores and parallel processing capabilities efficiently. They are essential for high-performance computing (HPC) and servers with multiple processors. Server OS: Optimized for server hardware, emphasizing stability, reliability, and performance. Examples include Windows Server, Linux Server distributions (e.g., CentOS, Ubuntu Server), and various Unix-based server OS. Clustered OS: Used in clusters of computers or servers to provide high availability, load balancing, and fault tolerance. They ensure that services remain available even if individual nodes fail. Examples include Microsoft Cluster Server (MSCS) and Linux High Availability (HA) clusters. Hypervisor or Virtualization OS: Provides virtualization capabilities to run multiple virtual machines (VMs) on a single physical server. Examples include VMware ESXi, Microsoft Hyper-V, and Xen. Real-Time Linux: A variant of the Linux kernel configured to meet real-time requirements. It combines the features of a general-purpose OS with real-time capabilities. Time-Sharing OS: Primarily designed for mainframes, these OS allocate CPU time to multiple users and processes in small time slices to give the illusion of concurrent execution. Hybrid OS: Combines features of multiple types of operating systems. For example, modern desktop operating systems often incorporate features found in real-time or embedded systems. 5. 6. 7. 8. 9. 10. 11. 12. 13. 14. 15. Operating systems can also be categorized based on their kernel type, such as monolithic kernels, microkernels, and exokernels, each with its own design principles and trade-offs. The choice of OS type depends on the specific requirements and use cases of the computing environment. Thread OS Within a program, a Thread is a separate execution path. It is a lightweight process that the operating system can schedule and run concurrently with other threads. The operating system creates and manages threads, and they share the same memory and resources as the program that created them. This enables multiple threads to collaborate and work efficiently within a single program. Long Term or Job Scheduler It brings the new process to the ‘Ready State’. It controls the Degree of Multiprogramming, i.e., the number of processes present in a ready state at any point in time. It is important that the long-term scheduler make a careful selection of both I/O and CPU-bound processes. I/O-bound tasks are which use much of their time in input and output operations while CPU-bound processes are which spend their time on the CPU. The job scheduler increases efficiency by maintaining a balance between the two. They operate at a high level and are typically used in batch-processing systems. Short-Term or CPU Scheduler It is responsible for selecting one process from the ready state for scheduling it on the running state. Note: Short-term scheduler only selects the process to schedule it doesn’t load the process on running. Here is when all the scheduling algorithms are used. The CPU scheduler is responsible for ensuring no starvation due to high burst time processes.The dispatcher is responsible for loading the process selected by the Short-term scheduler on the CPU (Ready to Running State) Context switching is done by the dispatcher only. A dispatcher does the following: 1. Switching context. 2. Switching to user mode. 3. Jumping to the proper location in the newly loaded program. Medium-Term Scheduler It is responsible for suspending and resuming the process. It mainly does swapping (moving processes from main memory to disk and vice versa). Swapping may be necessary to improve the process mix or because a change in memory requirements has overcommitted available memory, requiring memory to be freed up. It is helpful in maintaining a perfect balance between the I/O bound and the CPU bound. It reduces the degree of multiprogramming.