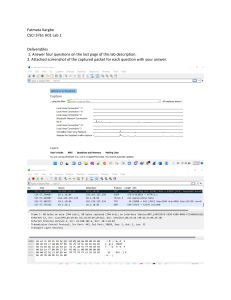
1. Assignment Scope Description: In this project, I will play the role of a forensic analyst and I have to investigate a h4ck3d computer. My job is to conduct a forensic examination of the artifact and document any evidence related to the hacked computer. Victim name is Rana, who has complained to the police. Officers got a .pcap file. I have to continue my investigation using this file as an artifact from Rana’s Computer. 2. Investigating the artefact: I'm here to look into this some more. I've been using Wireshark 3.6.3. What makes me use Wireshark when there are other instruments for sniffing available? The most famous and commonly used network protocol analyzer in the world is called Wireshark. Allows us is the de facto (and frequently de jure) standard across many commercial and non-profit companies, governmental organizations, and educational institutions. It allows users to see what is occurring on our network at a microscopic level. Since Linux and Windows operating systems both support Wireshark, it is generally usable. What is Wireshark used for? ● Capturing data packets ● Identifying and analyzing protocols ● Isolating and identifying source and destination traffic ● Inspecting the contents of data packets. 3. Relevant Findings: 1. There is an insecure service which the attacker has targeted to exploit by login. Please identify that service. from the .pcapng file, which is the artifact. Wireshark may be used to run it, and we can observe the log number, time, traffic source, destination, protocol duration, and other details. So after investing I have found that the insecure service which the attacker has targeted to exploit by login is: - FTP SERVICE Screenshot is given below 2. Identify the username by which the attacker is trying to login (you can use the filter related with the service discovered in the first question). Using the FTP service filter and the credentials tools integrated into Wireshark, we can quickly determine the username the attacker is attempting to use to log in. From the artifact we can identify that the username is: -jenny 3. Was the attacker able to login successfully? If yes, collect the evidence of login. Yes. The Attacker was successfully able to login. Username: jenny Password: password123 4. Identify the working directory after the attacker logged in. Working Directory: "/var/www/html" 5. What has been done by the attacker to gain a reverse shell? (whether the attacker has written any script or downloaded something, specify any filename/script type/urls etc what you have found) I discovered the following URL in the.pcapng file, which the attacker utilized to obtain a reverse shell. Url : http://pentestmonkey.net/tools/php-reverse-shell File name: Shell.php This is a very common reverse shell created by pentestmonkey in the PHP language. Screenshots are copied from Azizul Haque. 4. Lesson learned: Learning network forensics and fundamental penetration testing techniques are combined in the assignment. I have learned a lot from this assignment as I investigated the provided file using wireshark. 1. How to extract the password from a.pcapng file that was left by an attacker. 2. There were several different services in operation here, but the attacker only used the FTP service to obtain access. 3. How to make a reverse shell as well as how to identify one from an item. 4. I can read what's going behind the service using the TCP stream. 5. What kinds of code are developed to gain access to the reverse shell is another thing I've discovered. 6. I have discovered it even though the attacker used a command to get root shell access. 7. Attackers also download the project “Reptile” for github using the git clone command. There are other important learning materials available in this assignment which I have learned. Most Importantly I have learned various things about wireshark.