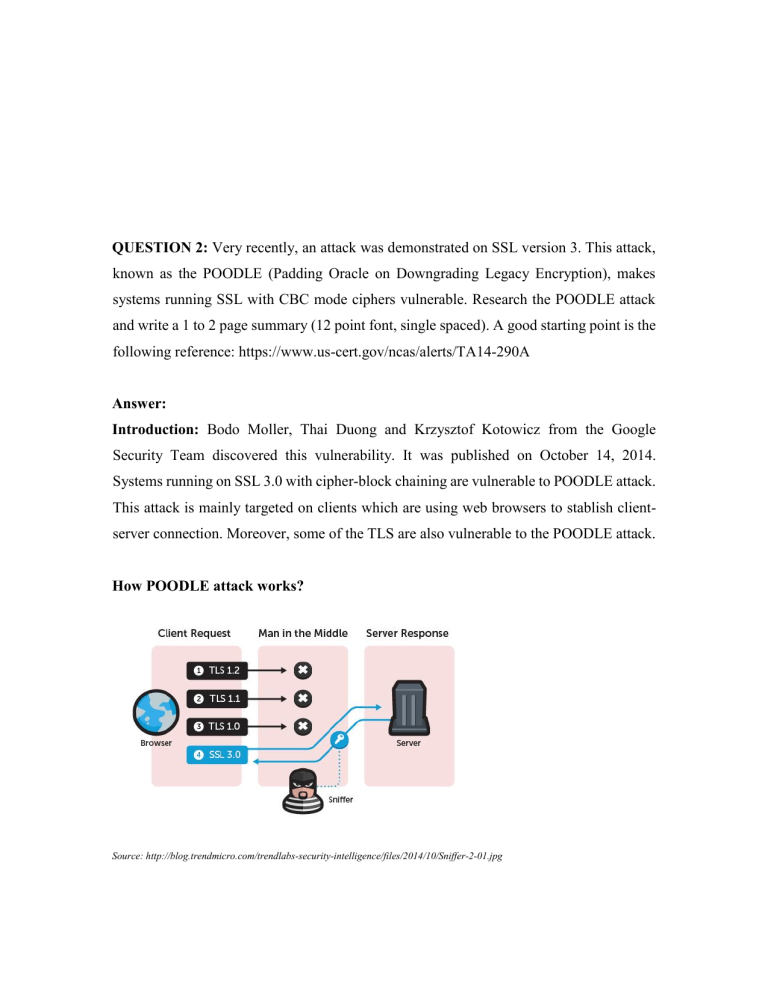
QUESTION 2: Very recently, an attack was demonstrated on SSL version 3. This attack, known as the POODLE (Padding Oracle on Downgrading Legacy Encryption), makes systems running SSL with CBC mode ciphers vulnerable. Research the POODLE attack and write a 1 to 2 page summary (12 point font, single spaced). A good starting point is the following reference: https://www.us-cert.gov/ncas/alerts/TA14-290A Answer: Introduction: Bodo Moller, Thai Duong and Krzysztof Kotowicz from the Google Security Team discovered this vulnerability. It was published on October 14, 2014. Systems running on SSL 3.0 with cipher-block chaining are vulnerable to POODLE attack. This attack is mainly targeted on clients which are using web browsers to stablish clientserver connection. Moreover, some of the TLS are also vulnerable to the POODLE attack. How POODLE attack works? Source: http://blog.trendmicro.com/trendlabs-security-intelligence/files/2014/10/Sniffer-2-01.jpg Poodle takes advantage of backward compatibility of SSL/TLS protocol version. SSL 3.0 is an obsolete and insecure protocol and it is been replaced by TLS 1.0, TLS 1.1 and TLS 1.2. But due to backward compatibility of many TLS with SSL 3.0, if the attacker is able to modify the connection request and force the client and server to use SSL 3.0 protocol, which can be done by man-in-the-middle attack. If the attacker is able to change the protocol to SSL 3.0 than it is very easy to decrypt the messages sent between client and server. They only need to make 256 SSL 3.0 requests to reveal one byte of encrypted messages. There are two other conditions for a successful attack: 1) Attacker much gain control of client side SSSL connection, such as he must be able to vary the length of input. 2) Attacker much also have access to encrypted data. How to mitigate POODLE attack? There is no fix for SSL 3.0 version, however, we can protect our systems by just disabling SSL 3.0 support. This can be achieved by disallowing our systems to downgrade itself to SSSL 3.0 version. There is another quick fix for the prerequisites conditions of POODLE attack. TLS_FALLBACK_SCSV can be used to prevent Man in the Middle attack. But this will require both client and server to support TLS_FALLBACK_SCSV for version downgrade attack. References: 1. POODLE 12, April 2015. Available online: http://en.wikipedia.org/wiki/POODLE 2. Bodo Moller, Thai Duong and Krzysztof Kotowicz, October 14, 2014 Available online: https://www.openssl.org/~bodo/ssl-poodle.pdf 3. SSL 3.0 Protocol Vulnerability and POODLE Attack, December 10, 2014, Available online: https://www.us-cert.gov/ncas/alerts/TA14-290A

