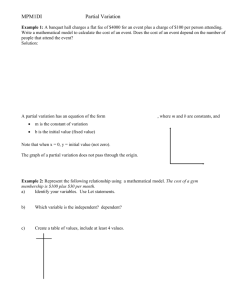
Top 5 Cyber crimes and tips for prevention AYUSH AGARWAL RA2111033010146 The majority of successful cyber attacks – 91% according to a study by PhishMe – begin when curiosity, fear, or a sense of urgency entices someone to enter personal data or click on a link. Phishing emails mimic messages from someone you know or a business that you trust. They are designed to trick people into giving up personal information or clicking on a malicious link that downloads malware. Thousands of phishing attacks are launched every day. Stop trusting your emails. They are not always what they seem. Security awareness and Phishing training can empower your team to defend against phishing attacks by showing the telltale signs and teaching them how to recognize targeted phishing campaigns and malicious links and encouraging them to stay away from links and attachments and go directly to websites by typing the real URL into their browser. The word spoof means to hoax, trick, or deceive. Website spoofing is when a website is designed to look like a real one and deceive you into believing it is a legitimate site. This is done to gain your confidence, get access to your systems, steal data, steal money, or spread malware. Website spoofing works by replicating a legitimate website with a big company’s style, branding, user interface, and even domain name in an attempt to trick users into entering their usernames and passwords. This is how the bad guys capture your data or drop malware onto your computer. What you can do: The easiest thing you can do is ignore and delete anything you’re not anticipating. Legitimate companies will have multiple ways to contact you in the event they need to reach you. Save time and frustration by applying common sense logic and evaluating the “urgency” of the message. Also, pick up the phone or go directly to the trusted domain to inquire. Ransomware is a modern day, technical twist on a crime that has been around for ages – extortion. At its core, ransomware works when criminals steal something of great value and demand payment in exchange for its return. For most businesses, this involves the encryption of company data. When ransomware hits, businesses come to a standstill, and employees cannot do their jobs. Without restorable back-up data, the company is generally at the mercy of the attacker who will hold your data hostage in exchange for a decryption key you can buy with Bitcoin. Back your data up and then do it again… in a separate location. Frequency and redundancy are key to your success. If you only back up your system weekly, or if your backup is infected, you’re in for a lot of trouble. AYUSH AGARWAL RA2111033010146 Norton defines malware as “malicious software” specifically designed to gain access to or damage a computer. In the case of ransomware, it’s designed to hold your data hostage, but that isn’t the only kind. There can be multiple objectives for malware – power, influence, money, information – but the result is always the same – a time consuming, often expensive recovery effort. Common types of malware include: Viruses that spread, damage functionality, and corrupt files Trojans disguised as legitimate software that quietly create backdoors to let other malware into your network Worms that can infect all of the devices connected to a network Ransomware that holds your data hostage Botnets – a network of infected devices that work together under the control of an attacker : Be cautious about email attachments, avoid suspicious websites (look at the spellings carefully), install and continually update a high-quality antivirus program. The Internet of Things is a brave new world that has opened insights into our daily routines and our business processes to the web. Whether we like it or not, all of these internet-connected objects are collecting and exchanging data. As you know, data is valuable and for that reason, hackers will look to exploit any devices that aggregate it. The more “things” we connect – the juicier the reward becomes for hackers. That’s why it’s important to remember that personal passwords and business passwords all belong to humans… with memories that we know are going to let us down from time to time. Use a password generator to secure all devices with unique passwords. HERE ARE 2 OF THE EXAMPLES OF CYBER CRIMES AND PUNISHMENTS AYUSH AGARWAL Female hacker arrested in Lahore who released obscene videos and pictures of women Female hacker arrested in Lahore for releasing obscene videos and pictures of women! Hina, a hacker girl who released obscene videos and pictures of women in the provincial capital, has been arrested. While objectionable content and WhatsApp numbers have been recovered from her mobile phone. According to media reports, Hina, a blackmailer who released obscene videos and pictures of women. This female hacker has left behind men who hacked other people’s accounts and shared objectionable photos and videos of women. An investigation revealed that Hina Mahmood hacked the citizen’s Hotmail, Skype, Instagram, and shared objectionable photos and videos of 2 women on the hacked account. According to the Federal Investigation Agency (FIA), the investigation also revealed that Hina also made women’s videos viral through 2 WhatsApp numbers and resorted to Virtual Private Network (VPN) for this purpose, which cannot be traced. According to sources, the FIA traced and arrested the hacker from the mobile data on the complaint of a citizen and a woman, while also obtaining objectionable materials and WhatsApp numbers from the mobile recovered from him. Man getting 5 years in jail for sharing nude video of ex shows India is waking up to revenge porn In a heartening judgment, a court in Tamluk, East Midnapore, Bengal, has sentenced a 23-year-old man to five years in jail and slapped him with a fine of Rs 9,000 for uploading objectionable pictures and videos of a girl on the internet. This is likely to be the first case of “revenge porn” conviction in India. The judge has also directed the state government to treat the 20-year-old complainant as a rape survivor and grant compensation accordingly. According to the police, the girl and the convict had been in a relationship for three years. The nude videos had been shot by the girl herself on her phone, which the man accessed. He then began blackmailing her, after which she called off the relationship. To extract “revenge”, he uploaded the video clips on various porn sites in May 2017. To make sure the girl was recognised, he added her name, and her father’s name and nickname to the videos. It is not the victim’s fault Shame should not stand in the way of a victim’s quest for justice. In a lot of cases, the accused access or record such pictures without the victim’s consent. Even if they shared them willingly, it is not the victims who should be shamed for trusting someone, but the perpetrators for abusing that trust in the lowest way possible – turning moments of trust and intimacy into weapons to harm someone’s dignity, privacy and reputation. Women often do not approach the police fearing more harassment and humiliation. This needs to change, and can be helped to a great degree by supportive family and friends. Law enforcement agencies too need to be more sensitive as by discouraging victims from coming forward, they are indirectly helping the accused. What the law says “Revenge porn” is circulating someone’s intimate pictures and videos without their consent, usually by former romantic partners. Once on social media or porn sites, the pictures can be viewed by millions of people, and it can be very difficult to track down every website on which they have been shared to get them removed. This violates the victim’s privacy over and over, in effect meaning her ordeal – and her trauma – never end. In the Midnapore case, public prosecutor Chatterjee called it “virtual rape”. AYUSH AGARWAL RA2111033010146