,
,,
fomputer system component!i,
""'
~ the components of computer system include--------------------a) Hardware
b) Operating system
c) Application programs
d) Users
e) All of the above
What is an Operatinq system?
l?ev
MCO: Operating system is a-----------------a) software
b) hardware
c) peripherical device
d) other
V
MCO: Kernel is a program which is running
a) While the program is executing
b) at all times on the computer.
c) Only at startup
d) Other
MCQ: The operating system acts as an interface between--------------------a) The user of a computer and computer hardware.
b) User and computer software.
c) None of the above.
~ Operating system is a Collection of programs that -----------------a) Control the application software.
b) Link between the hardware and software.
c) Manage resources shared between simultaneous programs.
d) All of the abJ!X@
Chapter:1
Page 5
-
II
Operating system Generations
~ the first generation of Operating system is -----------------a)
b)
c)
d)
Vacuum Tubes
Transistors and Batch Systems
ICs and Multiprogramming
Personal Computers
MCQ;, the second generation of Operating system is -----------------a) Vacuum Tubes
b} Transistors and Batch Systems
c) ICs and Multiprogramming
d) Personal Computers
MCQ: the third generation of Operating system is------------------
a)
b)
c)
d)
Vacuum Tubes
Transistors and Batch Systems
ICs and Multiprogramming
Personal Computers
MCQ: the fourth generation of Operating system is ------------------
a) Vacuum Tubes
b) Transistors and Batch Systems
c) ICs and Multiprogramming
d) Personal Computers
J
[
Am.Na.Sa
OS types
1. Mainframe Operating Systems:
o Room- sized computers found in major corporate data centers.
o processing many jobs at once and need huge amount of 1/0.
o Three kinds of services:
1) A batch system is one that processes routine jobs without any
interactive user present.
users to run jobs on
database.
0
Page 6
-
II
i
2. Server Operating Systems
o Run at servers that serve many u sers over network.
d c-oftware resources.
o Allow the users to share har ware an "'
o Example: Windows 2000
d
3. Multiprocessor Operating Systems
0
Special OS for multiple CPU in a single system.
o Special features for communication, connectivity, and consistency
o Example: Linux
4. Personal Computer Operating Systems
0
Used for word processing, spreadsheets, and Internet access. o
Example: Linux and Vista
s. Handheld Computer Operating Systems
0
Small computer that fits in a shirt pocket and perform small functions. 6.
Embedded Operating Systems
o Run on the computers that control devices that are not generally thought of as
computers.
o Example: TV and Cars
7. Sensor Node Operating Systems
o OS for tiny computers that communicate with each other and with a base
station using wireless communication.
8. Real-Time Operating Systems
o
Have a time as a key parameter.
o
Example: industrial process control systems
9. Smart Card Operating Systems
o Smallest OS which Is credit card sized devices containing a CPU chip.
o
Have very limited processing power and memory.
o Can handle only a
Chapter:1 Revisi1
•
slnsJeJuf1~, :sµch,1$ electronic payments,
·
th t rocesses routine [obs without any interactive user
MCO,;, --------------- 1s one a p
present.
a) batch systems
b) Transaction processing systems
c) Time Sharing Systems
MCO: --------------- is one that allow multiple remote users to run jobs on the computer at
once
a) batch systems
b) Transaction processing systems
c) Time Sharing Systems
ing-Rev,
---
IV
-
Mm;,--------------- is one that handle large numbers of small requests.
a) batch systems
b) Transaction processing systems c)
Time Sharing Systems
MCQ: Which is the false statement regarding batch systems?
a) A long turnaround time is needed for serial batch system.
b) Batch systems are slow in both input and output.
c) Batch systems are slow in both processing and output.
d) A batch system is less complex
MCQ: Which is appropriate for serial batch processing systems a)
Running several programs at a time.
b} Running one programs at a time.
c) Handling of multiple dependent programs at a time.
d) None of the above.
MCO: Which of the following is related to real-time operating systems?
a)
b)
c)
d)
Execution of programs concurrently.
Have a time as key parameter.
Serving several users at a time.
None of the above.
(
J
I
Am.Na.Sa
]
P
a
g
e
8
I
t
I
•
Operating Sys~em Services
1) services provide functions helpful to the user:
a. User interface
• Varies between Command-Line (CLI), Graphics User Interface (GUI), Batch
b. Program execution~
• OS must be able to load, run and terminate the programs.
c. 1/0 operations:
• OS is responsible for transferring data to and from 1/0 devices.
d. File-system manipulation:
• OS help programs to read, write, delete and search files and directories.
e. Communications:
• Processes exchange information, on the same computer or between computers
f. Error detection
• OS to be aware of errors that may occur and take actions that handle them.
2) services provide functions for ensuring efficient operation of the system
g. Resource allocation
• When multiple jobs running concurrently, resources are allocated to each of them.
h. Accounting
• Keep track of which users use how much and what kinds of computer resources.
i. Protection and security
Protection: involves ensuring that all access to system resources is controlled
Security: provide user authentication, extends to defending 1/0 devices
from invalid access attempts
Am.Na.Sa
)
Page 9
I
I
l
_MQl;.. Which of the following is not the function of an operating system?
a) Memory management
b) CPU management
c) 1/0 and file management
d) Debugging programs.
_M,Ql.---------------- provide user authentication and extends to defending external 1/0
devices from invalid access attempts
a) Protection
b) Securit~
c) Privacy
MCO: --------------- involves ensuring that all access to system resources is controlled
a) Protection
b) Security
c) Privacy
/A
,
-I
r
User OS Interface types:
1- Command Interpreter (g}
Allows direct command entry
It gets and processes the next user request and launches the requested programs.
Example: UNIX
2- Graphical User Interface (GUI)
implemented as a desktop with file folders, trash cans, and resource icons.
Usually use mouse, keyboard, and monitor
• Example: iPad touchscreen
(
)
Am.Na.Sa
3- Choice of interface
• Allow individuals to select their desired interface, customize its operation, and to
switch between different interfaces
Page 10
-
II
E
Operating System Structures
1- Simple Structure
MS-DOS written to provide the most functionality in the least space.
Not divided into modules
~
application program
Advantages:
o Simple and easy to implement
Disadvantage:
o It does not break the system into
subsystems.
o No distinction between user and kernel.
o Allow direct access to H.W
Examples: MS-DOS
ROM BIOS device drivers
2- Layered Approach
Operating system is divided into a number of layers.
Each layer relies only on services provided by next lower
layer.
Bottom layer (layer 0) is the hardware and the highest (layer
N} is the user interface.
Advantages:
o Allows each layer to be developed and debugged
independently.
Disadvantage:
o What order in which to place the layers.
o Less efficient
(
Examples: UNIX
)
Am.Na.Sa
3- Microkernels
Remove nonessential component from kernel and implement them in the user
space as system applications
Results in small kerneJ (miQ'q~p.eL}
• Advant
I
' ·e_:.,._·, --.~;.:
....,-:- .. ~
,·,:..:
with small functions.
·.t_ .-.. ... : ''..' .C.-1,_e,t,c~.'t~.~.,">;, =-:
Page 11
•
• Disadvantages:
o Performance overhead of user space to kernel space communication
Device
] user
I
I ~ysmrn
~
'\'
Program
J
Driver
mode
CPU
kernel
: •••••••• nx•Si.JQ()S •••••••.• :
memory
managment
±
mtcrokernet
J
hardware
scheduling
mode
4- Modules
Modern OS development is object-oriented, with a relatively small core kernel
and a set of modules which can be linked in dynamically.
Similar to Layered approach: each subsystem has clearly defined tasks and
interfaces
Differ from Layered approach: any module is free to contact any other module.
More efficient than layered approach: eliminating the problems of going through
multiple intermediary layers.
Advantages:
Kernel is small and efficient as microkernel [
o Modules easy linked to any other module
• Example: Solaris
0
Chapter:1
,,,..---------
Am.Na.Sa
Page 12
]
5- Hybrid systems
Combine different structures resulting in hybrid systems that address
performance, security, and usability issues.
Mac OS X structure: designed to run on Apple mac devices
Architecture of Apple's iOS: designed to run on Apple mobile devices
Architecture of Google's Android: Developed for Android smartphones and tablet.
Android Vs. 105
android
iOS
Google
Apple
Linux
OS X, UNIX
Programming lang.
C, C++, java
C, C++, Objective-c
Source model
Open source
Closed, with open source
components
Kernel, UI, and some
The iOS kernel is not open
standard apps
source
Company/ Developer
OS family
Open source
Widgets
Yes
-
No, except in Notification
Center
Internet browsing
Interface
Available on
Google Chrome
Mobile Safari
Touch screen
Touch screen
LG, HTC, Samsung, Sony,
Motorola and others
iPod Touch, iPhone, iPad,
Apple TV
Google maps
Apple maps
Google Hangouts
Facetime
Maps
Video chat
1- OS family of android is
a) Linux
b) Unix
c) Windows
2- Android OS is an example of
a) module systems
b) hybrid systems
c) layered systems
(
Am.Na.Sa
)
3- OS faatJb'~n~~ll.
Page 13
•
I
4- Solaris operating system uses
a) module structure
b) microkernel structure
c) layered structure
Ope
5- mash operating system uses
a) simple OS structure
b) micro kernel structure c)
layered structure
System Calls
'duJing _ R.,
---
...._
MCO: --------------- is a Programming interface to the services provided by the OS.
a) API
~
rI
,.
L
b) System call
c) Functions
d) other
MCQ: system call is accessed by---------------
a.
b.
c.
d.
APf
System call
Functions
other
(
Am.Na.Sa
)
MCO: --------------- is a Set of functions available to an application including the
parameters that are passed to each function and the return values the programmer can
expect.
a. API
b. System call
c. Functions
d. other
~ System calls are written in ------------------- language.
Page 14
~
Swin32 is an API for------------------- operating system.
a. Windows
b. Linux, Unix, Mac OS
c. Java Virtual Machine d.
Other
~
POSIX is an API for------------------- operating system.
a. Windows
b. Linux • Unix • Mac OS c.
Java Virtual Machine d.
Other
• System Call Types:
J
i
i
Process control
File management
end, abort
load, execute
create process, terminate
process
wait event
create file, delete file
open, close
read, write
Device management
protection
set file security
set security descriptor group
request device, release device
read, write device
Communications
Information maintenance
get time or date, set time or
date
create, delete communication
connection
send, receive messages
transfer status information
Am.Na.Sa
Chap
Page 15
OS Operations_
MCQ;, Modern OSs are ------------------- operating systems.
a. Not interrupt driven
b. Interrupt driven
MCQ: -------------- is a software-generated problem caused either by an error
or user request
a) A trap
b) An interrupt
c) User mode
MCQ: ------------------ is a way to invoke a kernel routine because other code run
with a higher priority than user code.
a.
b.
c.
d.
Interrupt
Event
A tarp
Other
MCQ: --------------- is something generated by the hardware device and they don't
happen at predictable places in the user code.
a. Interrupt
b. Event
c. A tarp d.
Other
Dual-/Ylode Operation
MCO: there are -------------- modes of operation in a computer system
a. 1
b.
I
C.
3
d. Other
MCO: operating syst
b.
C.
Page 16
1
MCQ,;, user programs run in -----------------a. kernel mode
b. user mode
c. dual mode
MC~ if mode bit is 0, that indicates that the current mode is---------------e. kernel mode
f. user mode
g. dual mode
~ if mode bit is 1, that indicates that the current mode is
a. kernel mode
b. user mode
c. dual mode
(
Am.Na.Sa
► User mode and Kernel mode
MCQ: In ------------, if a program crashes, the entire system will be halted
a) User mode
b) Kernel mode
c) Device management
)
a;
-
)I
l
I
MCQ; -------------- is used to prevent a user program from getting stuck in an infinite loop
or not calling system services and never returning control to the OS.
,;mer
..
a. Event
b. Interrupt
c. Timer
d. trap
MCOi -------------- can be set to interrupt the computer after a specified period.
a. Event
b. Interrupt
c. Timer
d. trap
Concurrency in Operating Systems
MCQ: ---------------- involves multiple processes on a system with a single processor.
a. Multiprogramming
b. Multiprocessing
c. Distributed processing
MCQ: Multiprogramming increases -----------------a. real time
b. execution time
Am.Na.Sa
c. CPU utilization
d. minimizes throughput.
MCQ: --------------- involves multiple processes on a system with multiple processors.
(
a. Multiprogramming
b. Multiprocessing
c. Distributed
processing
MCO: -----------------invo
a. Multiprogram
b. Multiprocessi
c. Distributed
Chapter:1 Revis
]
I
a,
~------------------is the interleaving of processes in time to give the appearance of
simultaneous execution.
a. Concurrency
b. Parallelism
c. sequential processing
MCQ~ ---------------- offers genuine simultaneous execution of processes.
a. Concurrency
ion.
b. Parallelism
c. sequential processing
MCQ: ----------------- is the requirement that when a process Pis accessing a shared
resource R, no other process should be able to access R until P has finished with R.
a.
b.
c.
d.
Deadlocks
Mutual Exclusion
Circular wait
Preemption
MCO: -------------- is a set of blocked processes each holding a resource and waiting to acquire
a resource held by another process.
a. Mutual Exclusion
b. Deadlocks
c. Circular wait
d. Preemption
Am.Na.Sa
\
I
-
How to avoid Deadlocks?
1- Mutual Exclusion
Shared resources such as read-only files do
TO thread has a
LOCK on resource 1.
but requ~es
resource2 for
r,ni1hing execution
-~
resource 1
◄·--I
7I
not lead to deadlocks.
but some resources, such as printers require
TO
DEADLOCK
L.
..
~.,
exclusive access by a single process.
2- Hold and Wait
processes must be prevented from holding
one or more resources while simultaneously
waiting for one or more others.
T1
11 thread has a
LOCK on resource2
but requires
resource1 for finishing
execution.
3- No Preemption
Preemption of process resource allocations can prevent this condition
of deadlocks, when it is possible.
4- Circular Wait
One way to avoid circular wait is to number all resources, and to require that
processes request resources only in strictly increasing (or decreasing} order.
MCQ: ------------------ can be a cause for deadlock
a.
b.
c.
d.
e.
Mutual Exclusion
Hold and wait
Circular wait
No Preemption
All of the above
MCQ: we can avoid deadlock by preventing ------------------
a.
b.
c.
d.
e.
Mutual Exclusion
Hold and wait
Circular wait
No Preemption
All of the_ab_O\l.e
MCO: In deadlock, ------a}
Hold and b)
Mutual e: c}
Circular
Chapter:1 Revisi
(
Am.Na.Sa
)
I
II
ding
I
ons
•
nt
-1
--·
•• A..
2
019
...•
MERR,Y
CHRISTMAS
and
HAPPY
NEW
YEAR
- 1
#221847225
Operating System
CPU Scheduling
Revision
CPU Scheduling -Revi1ion. BY Am.Na.Sa
I
reeaing
ptions
I
I
I
I
True/false. For each statement, write 'T' at the end if it is true and write 'F' i 1 it is
false. If you think the question is ambiguous, state your additional
assumptions clearly.
I. In a time sharing system, the most st!itable criterion for CPU scheduling is to
maximize the CPU utilization [ F ]
2. A round robin scheduling algorithm can be non-preemptive [ F j
3. In a preemptive priority scheduling algorithm, the running process/thread alwaxs
has the highest priority among all read)' prncesses/threads [ T l
Ouestion-1: Assume that the following processes are the only processes in a
computer system and that there are no input/output requests from all the given
processes. Given the following arrival time and CPU burst time for each process,
draw the Gantt chart and compute the average turnaround time and the
average wait time as defined in the textbook for the following CPU scheduling
algorithms:
CPU Burst Time
10
Process Arrival Time
P1
0
P2
2
6
P3
P.1
3
5
l
3
[
Am.Na.Sa
First Come First Service (FCFS).
0
JO
16
17
20
The wait time for
Pl is 0-0=0, for P2
is 10-2 = 8, for P3
is 16-3=13
for P4 is 17-5=12.
-2-
)
I
The turnaround time
[ Am.Na.Sa
for Pl is 10-0=10,
J
for P2 is 16-2=14
for P3 is 17-3=14
for P4 is 20-5=15.
So the average turnaround time is (1 0+ 14+ 14+ 15)/4= 13 .25
Preemptive Shortest Job Next.
l'
0
2345
8
20
12
The wait time for
Pl is 0-0=0, for P2
is 2-2 = 8, for P3
is 3-3=0 for P4 is
5-5=0.
So the average wait time is (0+0+0+0)/4 = 0.
The turnaround time
for Pl is 20-0=20,
for P2 is 12-2=10
for P3 is 4-3=1
for P4 is 8-5=3.
So the average turnaround time is (2o+lo+1+3)/4=8.5
Am.Na.Sa
CPU Sc
-3-
I
I
-I
Round-Robin with time quantum of 4,
P1
0
4
8 9
13
The wait time
for Pl is 0-0=0,
for P2 is 4-2 = 2,
16
[
18
Am.Na.Sa
20
J
for P3 is 8-3=5
for P4 is 13-5=8.
So the average wait time is (0+2+5+8)/4 = 3.75
The turnaround time
for Pl is 20-0=20,
for P2 is 18-2=16
for P3 is 9-3=6
for P4 is I 6-5= 11.
So the average turnaround time is (20+16+6+1 l)/4=13.25
(
Am.Na.Sa
I
I
I
-4-
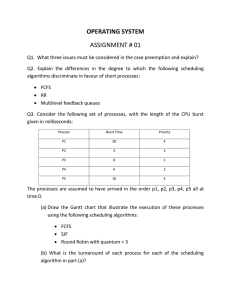
Ouestion-2: Consider the following set of processes, with the length of the CPU
burst given in milliseconds.
Process
Burst
Priority
time
12
Pl
3
[
Am.N~
1
1
P2
2
P3
3
1
P4
4
6
2
P5
The processes are assumed to have arrived in the order Pl, P2, P3, P4, PS, all at
time 0.
(a) Draw four Gantt charts that illustrate the execution of these processes using
the following scheduling algorithms: FCFS, SJF, nonpreemptive priority
(a smaller priority number implies a higher priority), and RR (quantum
=2)
(b) What is the turnaround time of each process for each of the scheduling
algorithms in part (a)
( c) What is the waiting time of each of these scheduling algorithms ?
(d) Which of the algorithms results in the minimum average waiting time
( over al 1 processes) ?
I
0
FCFS:
Pl
I
12
P2
I
P4
A1n.Na.Sa
(
I13
P3
I
P3
I
15
P4
I
4
PS
I
PS
I
Pl
J
22
16
SJF:
[
0
P2
1
-
10
]
22
22
-s
-
]
RR:
i PI I
I
P2 P3
14 16 18 20 22
I
P4
I Ps I
PI
I
PS / PI
I
PU PI
I
PI
I ill
0 2 3 5 6 8 IO 12
Turnaround Time:
FCFS -> Pl: 12, P2: 13, P3: 15, P4: 16, P5: 22
SJF-> Pl: 22, P2: 1, P3: 4, P4: 2, P5: 10
Non-preemptive priority-> Pl: 19, P2: 1, P3: 21, P4: 22, PS:~· RR> Pl: 22, P2: 3, P3: 5, P4: 6, P5: 16
Waiting Time:
FCFS -> Pl: 0, P2: 12, P3: 13, P4: 15, P5: 16
SJF-> Pl: 10, P2: 0, P3: 2, P4: 1, P5: 4
Non-preemptive priority-> Pl: 7, P2: 0, P3: 19, P4: 21, P5: 1 RR->
Pl: 10, P2: 2, P3: 3, P4: 5, P5: 10
Minimum average waiting time:
SJF
[
Am.Na.Sa
J
Question-3: Suppose that the following processes arrive for execution at the times
indicated. Each process will run for the amount of time listed. In answering the
questions, use non-preemptive scheduling, and base all decisions on the
information you have at the time the decision must be made.
Process
Pl
P2
P3
Arrival
time
0.0
0.4
1.0
Burst time
8
4
1
(a)What is the average turnaround time for these processes with the
FCFS scheduling algorithm ?
(b) What is the the SJF sch
CPU Scheduling - Revisio
-6-
I
I
I
I
(c) Compute what the average turnaround time will be if tl-e
CPU is left
idle for the first 1 unit and then SJF scheduling is used.
Answer:
(a)
I
FCFS:
Pl
I
0
P2
P3
I
12
8
13
-
1.
Pl: 8-0 = 8
P2: 12-0.4 = 11.6
P3: 13-1 = 2
Avg: 10.53
,,
)
tfl
~19
Merry
(b)
I
,.....••.."'
CHRIST1v1AS
I
Pl
0
.,
- H.appyNewYear -
SJF:
8.
I P3 I
I
P2
9
13
I
Pl: 8 - 0 = 8
P2: 13 - 0.4 = 12.6
P3: 9 - 1 = 8
Avg: 9.53
[
Am.Na.Sa
(c)
I Idle I P3 I
0
1
P2
2
I
6
I
Pl
14
Pl:14-0=14
P2: 6 - 0.4 = 5.6
P3: 2 - 1 = 1
Avg: 6.87
CPU Scheduling-
-7-
)
I
I
I
I
I
Enmplel
For the following set of processes, draw a Gant diagram representing the
allocation of the CPU and calculate the average Ttunarom1d time and average wait
time using FCFS, SJF, and Round Robin (q == 3). Show all calculations.
-
Process
Pl
P2
Arrival Time
P3
P4
4
P5
5
P6
6
Total Burst Ti.me
I
0
1
2
-
12
l
I
5
2
7
3
FCFS:
P2 I
Pl
I
12
0
I
Process
P3
13
Arrival
P6
P5
I P4
27
18 20
Finish Turnaround
(finish - arrival)
Burst
time
30
Wait Time
(Turnaround - CPU
time)
Pl
P2
P3
P4
PS
P6
Average:
0
1
2
12
13
18
20
27
30
4
5
6
12 - 0 = 12
13 - l = 12
18 - 2 = 16
20- 4= 16
27 - 5 = 22
30- 6 = 24
(12 + 12 + 16 + l6 +
22 +24)/6 =102/6 =
17
12
1
5
2
7
3
(0 + 11 + 11 + 14 +
15 +21)/6 = 72/6 =
12
[
SJF (NOD Prttmptive):
Pl
0
CPU Scheduling-
12 - 12 = 0
12 - 1 = 11
16 - 5 = 11
16 - 2= 14
22 - 7 = 15
24-3=21
Am.Na.Sa
PS
P3
P2
15
11
]
23
30
-8-
II
II
Arrival Finish Turnaround
Process
Burst
time
(finish - arrival)
Pl
0
P2
P3
1
2
P4
4
P5
5
P6
Average:
6
12
13
23
15
30
18
12-0= 12
Wait Time
(Ttunaround
- CPU time)
12- 12 = 0
12 - 1 = 11
21 - 5 = 16
12
1
5
2
13 - 1 = 12
23-2=21
15 - 4 = 9
30 - 5 = 25
18-6=12
I
9•2=7
25-7=18
7
12 - 3 = 9
(0 + 11 + le + 7 +
18 + 9)/6 = 10.17
3
(12 + 12 + 21 + 9 +
25 + 12)/6 = 91/6 =
15.17
SJF (Preemptive) (SRTF):
0
1
2
4
5
6
9
Arrival
Finish
Pl
0
30
30- 0 = 30
P2
P3
P4
1
2
2
4
9
6
2-1=1
9-2=7
6-4=2
PS
5
P6
6
19
12
Process
Average:
i.
CPU Scheduling-
Pl
P5
P6
19
12
Turnaround
(finish - arrival)
19- S = 14
12-6 =6
(30 + 1 + 7 + 2 +
+6'V6=60/6=
10
14
Burst
time
30
Wait Time
(Turnaround - CPU
time)
12
30 - 12 = 18
(1+11)
1
1- I =O
5 (2+3) 7 - 5 =2
2
2-2=0
7
14 - 7 = 7
3
6-3=3
(18 + 0 + 2 + 0 + 7
+ 3)/6 = 30/3 = 5
-9-
Round Robin (q=3):
[ P1
I
0
l
4
3
Process
I I I I
P6 P3 Pl PS Pl
P1 I P4 I PS
P2 P3
10 12
7
15
I Arrival / Finish / Turnaround
(finish - arrival)
18 20
I ~urst
tune
23
29 30
26
I Wait
Time - CPU
(Turnaround
time
Pl
P2
P3
P4
PS
0
1
29
4
20
12
30
18
2
4
5
6
P6
Average:
___,
29 - 0 = 29
4 - I= 3
20 - 2 = 18
12-4= 8
30 - 5 = 25
18-6=12
12
1
5
2
7
3
29 - 12 = 17
3 - 1 =2
18 - 5 = 13
8 -2= 6
25 - 7 = 18
(29 + 3 + 18 + 8 +
12 - 3 = 9
(17+2+13+6+
25 + 12)/6 = 95/6 =
15.83
18 + 9)/6 = 65/6=
10.83
Example3
Consider the following set of processes with the indicated arrival time. The length of the
CPU - burst time is given in milliseconds.
Process
Pl
P2
P3
P4
PS
Arrival Time
Total Burst Time
0
2
4
12
9
6
10
5
3
1
[
]
Am.Na.Sa
For each of the following scheduling algorithms, draw the Gantt chart and compute the
average waiting time of these processes execution.
a) Preemptive SJF schedPl
0
P2 I P3
2
4
CPU Scheduling-Re--'-•
Pl
s
30
- 10 -
I
7
Waiting time
Scheduling Policy
P2
Pl
0+(20-2) = 18 I 0+1+8=9
Preemptive SJF
P3
P4
P5
0
0
1
scheduling
(18+9+1) I 5 = 5.6 ms
b) RR sclleduling with q = 3 ms
NOTE: if the process quantum is finished and new process enter the system at the
same time, then the new process will be served first.
l l I I
Pl
P1 / P2 I Pl P3 P4 P2
0
3
6
Scheduling Policy
9
10
13
16
I
Average
P5
19
I
P4
22
I
P2
I
Pl
27
24
30
\Vaiting time
Pl
RR
I
13+7+8 = 18
P2
1+7+8=16
P3
P4
P5
5
4+9=13
9
Arn.Na.Sa
)
I (18+16+5+13+9) I 5 = 12.2 ms
- 11 -
xample: Consider the following processes:
Process Arrival
Time
Pl
0
P2
0
5
P3
P4
10
PS
10
Priority Burst Time 4
3
2
2
1
17
15
15
3
9
Using preemptive SJF (SRTF), preemptive Priority. 1- Draw Gantt
charts.
2- Find the average turnaround, waiting, and response time. 3Find context switch
[
Preemptive SIP (SRTF)
/PL/P2
/ IO
j 13
1 PS
t I8
I
P3
27
Pl
Am.Na.Sa
~
Preemptive priority
{P2
I
I
IP3s
- 12 -
]
I
1. ---------- algorithm must be non-preemptive only
~)FCFS
b)SJF
d) None of the mentioned
2. ---------- algorithm must be preemptive only
a) FCFS
b) SJF
c) RR
d) None of tne mentioned
3. ------------ is a goal of batch systems.
a) minimize turnaround time
b) maximize
proportionality
c) minimize response time
d) none of the mentioned
4. ------------ is a goal of interactive systems.
a) minimize turnaround time
b) maximize
proportionality
c) minimize response time
d) none of the mentioned
5. ------------ is a goal of real time systems.
a) minimize turnaround time
proportionality
c) minimize response time
b) maximize
d) Meeting deadlines
6. FCFS scheduling result in the shortest possible average
response time when the jobs arrive in ready queue with ------
b) shortest burst time first
a) longest burst time first
c) mix of long and short burst time
7. RR scheduling behave Identically to FCFS when quantum (q) is
a) g is large
c) q is zero
CPU Sd1l'1.lulin2 - R
. , .b) qJ, sm,.:
· · · · ""
-13
-
I
7
a. RR
I
scheduling perform poorly compared to FCFS when
quantum (q) is a) q is large
b) g is small
c) q is zero
d) none of the above
9. ---------- scheduling
algorithm works best when the incoming processes
are short with no specific order
a) FCFS
b) RR
c) SJF
d) priority
10. ---------- scheduling algorithm works best when the incoming
processes are mix of long and short with time requirement
a) FCFS
b) RR
c) SJF
d) priority
11 ...•.•••• _ scheduling algorithm works best when the
incoming processes are mix of user based and kernel based
processes a) FCFS
c) SJ
b) RR
12. there is no difference
between non preemptive SJF
d) priority
and proomptive SJF (SRTF)
scheduling if process arrives
---------
..•
.ru all processes arrive at same time b)
processes arrive at different times
- 14
-
14- An SJF algorithm is simply a priority algorithm where the priority
is:
/
I
I
a} the predicted next CPU burst
b) the inverse of the predicted next CPU burst
( Am.Na.Sa
l __________ _
c) the current CPU burst
d) anything the user wants
15- In --------- algorithm, User's share of CPU= (time since login/n).
a) Guaranteed
b) shortest process next
c) lottery
d) fair share
16- Which of the following scheduling algorithms gives minimum
average waiting time?
b) SJF
a) FCFS
d) Priority
c) Round - robin
17- Which of the following process scheduling algorithm may lead to
starvation
a) FIFO
b) Round Robin
c) shortest job first
18- Which of the following statements are true?
I. Shortest remaining time first scheduling may cause starvation
11. Preemptive scheduling may cause starvation
III. Round robin and FCFS don't cause starvation
IV. preemptive priority may cause starvation
a) I only
b) I and Ill only
C) II and Ill only
d) L IL Ill and lX
CPU Scheduline -
- 15 -
J
19- the most common thread scheduling algorithms are
a) priority and RR
b) SJF and RR
c) FCFS and SJF
d) None of the above
[
Am.Na.Sa
)
,I'
00
rn-rt "~'
----------------r:I ----____ ~~~~~=~~Allocation
(MCQs) Group 1: Memory
1 The main memory accommodates:
·
.
b) cpu
a) Qperat1ng system
d) all of the mentioned
c) user processes
I
I
II 2. In contiguous memory af~cation~gle contiguous section of
a
each process is contarne rn
a)
s1
I
I
I
memory
. d . a single contiguous section of
b) all processes are oontaine in
memo~
.
c) the memory spac_e is contiguous
d) none of the mentioned
f 3. The relocation (base) register helps in :
I
a) providing more address space to processes
b) a different address space to processes
c) to ~rotect the address spaces of processes
d) none
of the mentioned
I
f
I
ff
I
4. With relocation and limit registers, each logical address
must
be ______ the limit register.
a) less than
b) equal to
c) greater than
d) none of the mentioned
I
I
I
5. The operating system and the other processes are
protected from being modified by an already running process
because :
a) they are in different memory spaces
b) they are in different logical
addresses c) they have a protection
algorithm
II
IL
dl every address generated by the CPU is being checked
against the relocation and limit registers
6. When memory is divided into several fixed sized partitions
each partition may contain
a) exactly one nrnN::u:~~
c) multiple process
I
----
MCQ: Memory Manage
.. . .
. Page 1
#1 ---
I
'
I
l
I
•
I
a} enough total memory
exists to satisfy a request but not contiguous I f b) the total memory is
15. External fragmentation exists when:
insufficient to satisfy a request .
I
. c) a request cannot be satisfied even when the total memory 1s free I
d) none of the mentioned
fI
I
16. External fragmentation will not occur when:
I
a) first fit is used b) best fit is used
c) worst fit is used d) no matter which algorithm used, it always occur
If
I
I
17. Sometimes the overhead of keeping track of a hole might be:
a) larger than the memory
c) very small
II
b) larger than the hole itself
d) all of the mentioned
II
II
II
II
II
18. When the memory allocated to a process is slightly larger
than the process, then:
a) internal fragmentation occurs
b) external fragmentation occurs
c) both internal and external fragmentation occurs
(MCQs)
Group
2: Swapping
processes
d) neither
internal
nor external
fragmentation
occurs
f' f
r 1. Address Binding is :
a) going to an address in memory
b) locating an address with the help of another address
c) binding two addresses together to form a new address in a
different memory space
dl a mapping from one address space to another
I
2. Binding of instructions and data to memory addresses can be
done at:
a) Compile time
b) Load time
c) Execution time
d) All of the mentioned
I
3. If the process can be moved during Its execution from one
memory segment to another. then. b~ndlng must be:
'
I
~J i~~~~~du~~ill~a~ ~;;~""' . , / . . . . ·.· .
,f ., .;. pi~e~me
·---
MCQ: Memory
Managem
--
11
II
I
__
...
•
Page 3
---------------,
r
1
d. .
4. Dynamic loa mg 1s:
.
a) loading multip_le routines dy~a~rncally
b) loading a ro~trne onl_y when it is calle.ct
c) loading multiple routines randomly
d) none of the mentioned
I
I
I
I s.
I
If
I
I
I
1_
The advantage of dynami~ loa~ing is that :
a) A used routine is used multiple times
b} An unu~_ed ~out~ne is never loaded
c) CPU ut1llzat1on_ increases
d) All of the mentioned
I
II
I
I
II
I
6. The _________________________ swaps processes in and out of the memory.
I
I
f
f
a) Memory manager
c) CPU manager
b) CPU
d) User
7. If a higher priority process arrives and wants service, the
memory manager can swap out the lower priority process to
execute the higher priority process. This swapping is called :
a) priority swapping
b) pull out, push in
c) roll out. roll in
d) none of the mentioned
I f
I
1
8. If binding is done at assembly or load time, then the process
__ be moved to different locations after being swapped out
Ib) must
and in again.
a) can
c) can never
j
f
I
I
d) may
9. In a system that does not support swapping,
a} the compiler normally binds symbolic addresses to relocatable
addresses
b) the compiler normally binds symbolic addresses to physical
addresses
c) t~e l?ader binds relocatable addresses to physical addresses
d) binding of symbolic ad~ress_ es_ to-phy~i~al addr~sses normally
takes place during execut,~n
I
I
f
I
I
1
I
I
>i>,~ ·.,; . __
L
-----
~~
MCQ: Memory Management Page 4
I
I
I
--
I
r---------------, I
I o.I
I
I
I
I
II
f
1
The address generated by the CPU is ref~rred to as :
a) Physical address
b) Logical address
c) Neither physical nor logical
d) None of the mentioned
I
I
I
11. The address loaded into the memory address register of the
I
memory is referred to as :
a) Physical address
c) Neither physical nor logical
b) Logical address
d) None of the mentioned
I
12. The run time mapping from virtual to physical addresses is
done by a hardware device called the :
a) Virtual to physical mapper
b) Memory management unit
c) Memory mapping unit
d) None of the mentioned
I
I
I
f
f
I
13. The base register is also known as the :
a) basic register
b) regular register
cl re!QcatiQn register
d) delocation register
14. The size of a process is limited to the size of:
a) physical memory
b) external storage
c) secondary storage
d) none of the mentioned
15. If execution time binding is being used, then a process
________ be swapped to a different memory space.
a) has to be
b) can never
c)mu~
d)may
I
I
f
16. Swapping requires a
a) mot~erboard
c) monitor
II
I
I
I
I
I
I
I
I
______ I
I
d) backing store
b) keyboard
17. The backing store is generally a:
a) fast disk
7jr ~tu~:~se enough to accommodate. copies of all memory images
I
I ~\ ::~~/fb~r:!~~;i::-;. . . . . '
A' "'' - .• ·,,,;,¥,~•;.. .
I
I
I
I
.---------------,I
1 a. The _______________consists of all processes whose memory images
I
I
I
queue
are in the backing store or in memory and are ready to run.
I
a) wait queue
c) cpu
b) ready
d) secondary storage
I
I
I
I
19. The ________________________ time in a swap out of a running process and
swap in of a new process into the memory is very high.
g) conts1xt - switch
b) waiting
c) execution
d) all of the mentioned
If
I .
20. T~~ major part of swap time is ____________ time.
1
f c) execution
d) none of the mentioned I
f 21. Swapping __ be done when a process has pending VO, or I
I
a) wa1t1ng
has to execute 1/0 operations only into operating system buffers.
a) must
b) can
c) must never.
d) may be
f
f
I
b) transfer
22. Swap space i~ allocated :
a) _as a c~unk of disk
c) into a file system
I
I
I
I
I
I
I
I
I
b) separate from a file system
d) all of the mentioned
I
I
I
I
I
I
I
I
I
I
I
'L::
~---
---
Memory Man .
I!
__ ..•
Page 6
~-r---------- -, -----.•....•..
II llilg~
Mb.f1m1e ~ffr.aieeJ «:tmesf 01,,~>
II
I
I
II
II
I
I
I
I
I
I
2.
After reading
first 2 options
8.
After reading
all 4 options
/ Operating System
I Memory Management
Part-2
/ MCQ
I
L
_
I
I
I
I
I
I
,-:----------·------,
II
f [ (MCQs) Group 1: Memory Manag;:ment
f 1. CPU fetches the instruction from
f value of
a) program counter
c) instruction register
mernury according to the
b) ;tatus register
d) ()rogram status word
f 2. A memory buffer used to accommodate a speed differential is
fI called
b}
f
a) stack pointer
c) accumulator
II
II
II
cache
d) disk buffer
3. Which one of the following is the address generated by CPU?
a) physical address
b) absolute address
c) logical address
d) none of the mentioned
4. Run time mapping from virtual to physical address is done by
a) Memory management unit
b) CPU
c) PCl
d) None of the mentioned
I
I
I
I
I
I
I
I
I
II
f 6. The address of a page table in memory is pointed by
l
I
I
I
I
5. Memory management technique in which system stores and
a) stack poi_nter b) page table base register
retrieves data from secondary storage for use in main memory
c) page register
d) program counter
is called
b) paging
a) fragmentation
7. Program
always deals with
d) none of the mentioned
mapping
a)c)logical
address
f
f
I
c) physical address
B. The page table contains
I
b) absolute address
d) relative address
c) page size
---
MCQ: Memory Man
I
I
I
III
b) page off set
d) none of the mentioned
I
I
---Page 1
-----a------,
--rg_
'
~)
I
'
I
Whal is compaction? .
a) a technique for overcoming internal fr ugmentat1on
b) a paging technique
.
a technique tor overcoming external fr;~ .1mentat1on
d) a technique ·tor overcoming fatal error
I 10. Operating System maintains the page table for
b)
I I c) each instruction
d) each address
a) each process
each thread
1 l (MCQs) Group 2: Paging
f 1. Physical memory is broken into fixed-sized blocks called ------ l
'a) frames
c) backing store
f
ff c) backing store
.
I
I
II
II
I
b) pages
d) none of the mentioned
2. Logical memory is broken into blocks of the same size called -- •
a) tram es
I
f
b) pages
d) none of the mentioned
3. Every address generated by the CPU is divided into two parts:
a) frame bit & page number
b) page number & page offset
c) page offset & frame bit
d) frame offset & page offset
I
f
f 5. The __ table contains the base address of each page in l
4. The----'----- is used as an index into the page table.
a) frame bit
b) page number
c) page offset
d) frame offset
I
f cl page
6. The size of a page Is typically:
a) varied
c) power of 4
I ~-----MCQ: Memory Man ·
I
II
I
I
I
I
physical memory.
a) process
I
II
1
b) memory
d) frame
b) power of 2
d) none of the mentioned
.,.,, .
---- II
---- _______ .•.•
Page 2
I
I
I
I
------UI-----,
---r7
I
I
If the size of logical address space is 2 to the power of m, and
·a page size is 2 to the power of n addre.aslnq ~nits, then the
high order __ bits of a logical addresss designate the page number, and the __
J
I
low order bits designate the page offset.
a) m, n
c) m - n, m
f
f
I
b) n, m
d) m - n, n
I
a. With paging there is no ____________________
I
track of how many frames have been allocated, how many are
many are available.
a) page
b) mapping
I
I
I
fragmentation.
b) external
d) none of the mentioned
a) internal
c) either
f
type of
f 9. The operating system maintains a __________table that keeps I
J
f c) tram~
I
I
there, and how
1
d) memory
I
I
I
___________ I
10. Paging increases the ________________ time.
a) waiting
b) execution
cl cont~xt - switch
d) all of the mentioned
f
f
f
11. Smaller page tables are implemented as a set of
.
a) queues
b) stacks
cJ counters
d) registers
f 12. The page table re~isters should be bu!lt with
I
b) very hrgh speed logic
d) none of the mentioned
a) very tow speed loqic
c) a large memory space
If
f
I
f
I
I
___________ I
13. Each entry in a Translation lookaside buffer (TLB) consists of:
al key
b) value
cJ bit value
d) constant
I
I
I
paqe number is not found in the TLB, then it is known as a ='1
a) TLB miss
b) Buffer miss
c) TLB hit
d) All of the mentioned
14. If a
LI
-~;
MCQ: Memory Man ·
---
Page 3
1,
I
I
rI r15.----f
•••• !' _______________________ ,
An --- uniquely identifies proces ses and is used to
I
provide address space protection for tl ~at process. . . .
a) address space locator
b) .::1ddress space 1d~nt1f,er
·
c) address process identifier
d) !'~one of the mentioned
I
I
16. The percentage of times a page number is found in the TLB
is known as :
a) miss ratio
b) hit ratio
.
c) miss percent
d) None of the ment1o~ed
I
-
I
I I
I I
I
I I
I I
I I
I f
byl
I I
I
I f d)
the valid - invalid bit is set to valid, it means that the I
I associated
If 18. When
page :
I
I
1
17. Memory protection in a paged environment Is accomplished
protection algorithm with each page
b) restricted access rights to users
c) restriction on page visibility
protection bit with each page
a) is in the TLB
c) has data in it
f
I
I f 19.
I J valid r
IJ
a)
I
I
I
I
20. In a paged memory, the page hit ratio is 0.35. The required to
access a page in secondary memory is equal to 100 ns. The
time required to access a page in primary memory is 1 o ns.
The average time required to access a page is :
a) 3.0 ns
b) 68.0 ns
c) 68.5 ns
d) 78.5 ns
If
I
I
I
L~CQ: Memory Mana
1
b} is in the process's logical address space
d) is the system's physical address space
Illegal addresses are trapped using the __ bit.
a) error
b) protection
c)
invalid
d) access
f
I
I
I
I
I
Pooo .1.
I
I
I
I
22. In paged memory
systems, if the page size is
increased, then the internal
fragmentation generally:
a) becomes less
c) remains constant
b) becomes more
d) none of the mentioned
2. In paging the user provides only __________ which is
partitioned by the hardware into __________ and ____ _
a) one address, page number, offset
b) one offset, page number, address
c) page number, offset, address
d) none of the mentioned
3. Each entry in a segment table has a:
a} segment base
c) segment value
b) segment peak
d) none of the mentioned
4. The segment base contains the :
I
as
I
--...a
Page 5
---------------,
1
I
_ The segment limit contains the:
a) starting logical address of the process
.
b) starting physical address of the segment in me1mo~
I1
5
i;J segment
length d) none of the rnent1oned
I 6. IThe offset 'd' of the logical address must be :
I
I
a) greater than segment limit
I
I
f
I
Q) between O and segment limit
c) between O and the segment number
d) greater than the segment number
,·
I
7. If the offset is legal:
a) it is used as a physical memory address itself
b) it is subtracted from the segment base to produce the physical
\
f
memory address I
c) it is added to the segment base to produce the physical memory
If
slddress
\
I
d) none of the mentioned
I
8. When the entries in the segment tables of two different
processes point to the same physical location :
a) the segments are invalid
b) the processes get blocked
c;) segments are shared
d) all of the mentioned
f
f
I
f
I I
I
I
\
\
I
9. The protection bit is 0/1 based on :
a) write only
c) r!;lad -write
\
b) read only
d) none of the mentioned
\
I
I
I
I
I
I
I
____
..
•
I
I
LMCQ:
Page 6
I
I
I