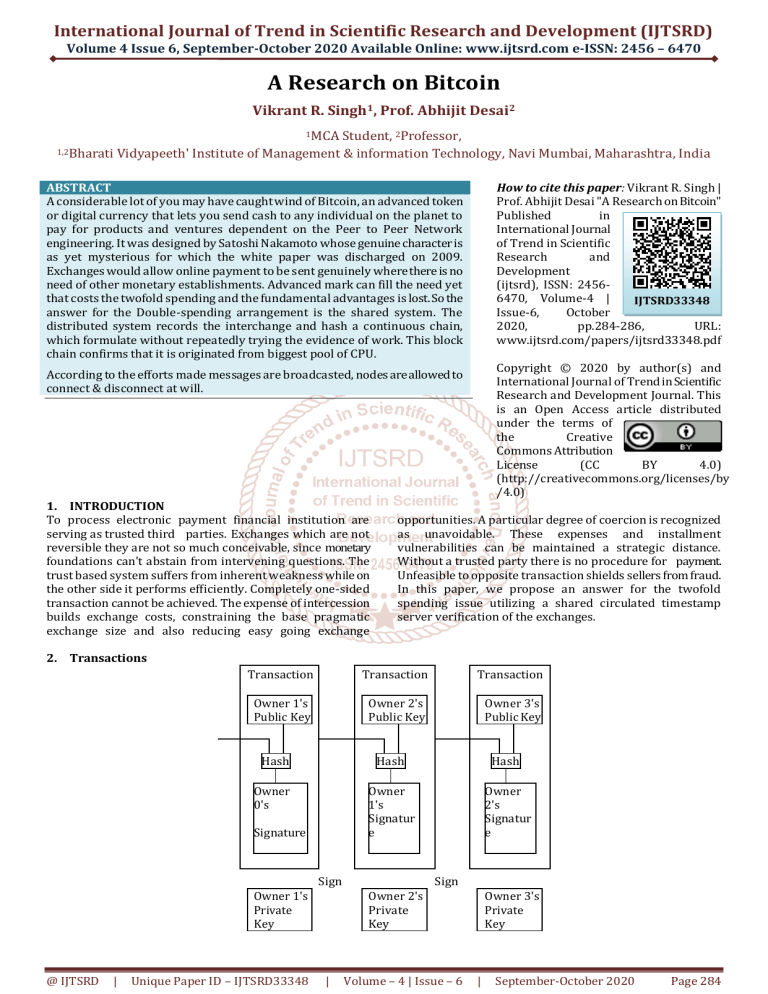
International Journal of Trend in Scientific Research and Development (IJTSRD) Volume 4 Issue 6, September-October 2020 Available Online: www.ijtsrd.com e-ISSN: 2456 – 6470 A Research on Bitcoin Vikrant R. Singh1, Prof. Abhijit Desai2 1MCA 1,2Bharati Student, 2Professor, Vidyapeeth' Institute of Management & information Technology, Navi Mumbai, Maharashtra, India ABSTRACT A considerable lot of you may have caught wind of Bitcoin, an advanced token or digital currency that lets you send cash to any individual on the planet to pay for products and ventures dependent on the Peer to Peer Network engineering. It was designed by Satoshi Nakamoto whose genuine character is as yet mysterious for which the white paper was discharged on 2009. Exchanges would allow online payment to be sent genuinely where there is no need of other monetary establishments. Advanced mark can fill the need yet that costs the twofold spending and the fundamental advantages is lost. So the answer for the Double-spending arrangement is the shared system. The distributed system records the interchange and hash a continuous chain, which formulate without repeatedly trying the evidence of work. This block chain confirms that it is originated from biggest pool of CPU. How to cite this paper: Vikrant R. Singh | Prof. Abhijit Desai "A Research on Bitcoin" Published in International Journal of Trend in Scientific Research and Development (ijtsrd), ISSN: 24566470, Volume-4 | IJTSRD33348 Issue-6, October 2020, pp.284-286, URL: www.ijtsrd.com/papers/ijtsrd33348.pdf Copyright © 2020 by author(s) and International Journal of Trend in Scientific Research and Development Journal. This is an Open Access article distributed under the terms of the Creative Commons Attribution License (CC BY 4.0) (http://creativecommons.org/licenses/by /4.0) According to the efforts made messages are broadcasted, nodes are allowed to connect & disconnect at will. 1. INTRODUCTION To process electronic payment financial institution are serving as trusted third parties. Exchanges which are not reversible they are not so much conceivable, since monetary foundations can't abstain from intervening questions. The trust based system suffers from inherent weakness while on the other side it performs efficiently. Completely one-sided transaction cannot be achieved. The expense of intercession builds exchange costs, constraining the base pragmatic exchange size and also reducing easy going exchange opportunities. A particular degree of coercion is recognized as unavoidable. These expenses and installment vulnerabilities can be maintained a strategic distance. Without a trusted party there is no procedure for payment. Unfeasible to opposite transaction shields sellers from fraud. In this paper, we propose an answer for the twofold spending issue utilizing a shared circulated timestamp server verification of the exchanges. 2. Transactions Transaction Transaction Transaction Owner 1's Public Key Owner 2's Public Key Owner 3's Public Key Hash Hash Hash Owner 0's Owner 1's Signatur e Owner 2's Signatur e Signature Sign Owner 1's Private Key @ IJTSRD | Unique Paper ID – IJTSRD33348 Sign Owner 2's Private Key | Volume – 4 | Issue – 6 Owner 3's Private Key | September-October 2020 Page 284 International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470 An electronic coin can also be referred as digital signature. The coin is transferred to the next by hashing the past exchange and public key of the following owner and adding these to the furthest limit of the coin. To verify the ownership a payee can verify signature. The issue obviously is that the proprietor did not double spend the coin cannot be verified by the payee. The double spending on each transaction can be checked by trusted authority. After every exchange, the coin must come back to the mint, and just coins coming from mint straight forwardly are trusted to be non-double spent. Payee must be able to verify that the previous owners have not signed any prior transactions. For us the earliest transaction is what matters, so no need to care about future attempts to double-spent. 3. Timestamp Server Timestamp server is solution we propose. A block of items are hashed to be time stamped and extensively circulating the hash, in newspaper or unsent post. Timestamp proves the existence of data at the time, In order to enter the hash every timestamp incorporates the past timestamp in its hash. And every timestamp reinforcing the ones preceding it. is dictated by a moving normal focusing on a normal number of squares every hour. On the off chance that they're created excessively quickly, the trouble increments. 5. Network The way to run the framework is according to the accompanying: Newly introduced transactions are communicated to every node. Every node collect as well as work for its block in finding difficult proof of work and blocks are broadcasted to every nodes. Blocks with all transactions valid are accepted by nodes and are not already spent. Node acknowledges the block which is accepted by creating the following block in chain. Hubs consistently believe the longest chain to be the right one and will continue taking a shot at broadening it. On the off chance that two hubs communicate various renditions of the following square all the while, a few hubs may get either first. All things considered, they deal with the first they got, however spare the other branch on the off chance that it turns out to be longer. When the following proof of work is found the tie breaks and also when one branch turns out to be longer; the hubs that were taking a shot at the other branch will at that point change to the more one. New exchange communicates don't really need to arrive at all hubs. For whatever length of time that they arrive at numerous hubs, they will get into a square in a little while. Square communicates are additionally open minded of dropped messages 4. Proof-of-Work We need to use a proof of work framework on a peer to peer for implementing distributed timestamp, as opposed to paper or Usenet posts. The minimum work requirement in the number of zero bits is exponential. Verification is possible by executing single hash. The confirmation of-work likewise tackles the issue of deciding portrayal in dominant part dynamic. In the event that the greater part dependedon “one Internet protocol one vote”. In this case anybody able to allocate numerous IP can subvert. Proof of work is basically one cpu one vote. The dominant part choice is spoken to by the longest chain, which has the best verification of-work exertion put resources into it. In the event that a dominant part of CPU power is constrained by fair hubs, the legit chain can outperform any contending chains and become the quickest. For an assailant to alter the past blocks has to retry the proof of work of the blocks. We will show later that the likelihood of as lower aggressor making up for lost time reduces exponentially as ensuing squares are included. To make up for speeding up and changing enthusiasm for running hubs after some time, the evidence of-work trouble @ IJTSRD | Unique Paper ID – IJTSRD33348 | 6. Reclaiming Disk Space The recent exchange is buried in blocks, the spent is exchanged properly and able to dispose to spare space. So the exchanges are hashed in a Merkle Tree without breaking hash. Old blocks areable to be compacted by nailing off parts of the tree. The inside hashes don't should be put away. A square header without any exchanges would be around 80 bytes. In the event that we guess squares are created at regular intervals, 80 bytes * 6 * 24 * 365 = 4.2MB everyear. With PC frameworks normally selling with 2GB of RAM starting at 2008, and Moore's Law foreseeing current development of 1.2GB every year, stockpiling ought not be an issue. 7. Simplified Payment Verification To check payment the client just need a duplicate block header. The client can get block header by questioning system hubs. The exchange cannot be checked by self, is possible by connecting to a spot in chain. The client sees that system has acknowledged and blocks are added which confirm that network has accepted. All things considered, when the hubs are controlled by fair system the check is mostly reliable until the system is compromised by attacker. But still this can be tricked by an attackers manufactured exchanges for whatever length of time that the assailant can keep on overwhelming the Volume – 4 | Issue – 6 | September-October 2020 Page 285 International Journal of Trend in Scientific Research and Development (IJTSRD) @ www.ijtsrd.com eISSN: 2456-6470 system. One methodology to ensure against this is acknowledge cautions from arrange hubs when they identify an invalid square, provoking the client's product to download the full square and made exchanges aware of affirm the irregularity. Organizations that get visit installments will most likely despite everything need to run their own hubs for progressively autonomous security and speedier check. 8. Combining and Splitting Value Despite the fact that it is conceivable to deal with coins independently, it is cumbersome to make a different exchange for each penny in an exchange. To permit an incentive to be part and consolidated, exchanges contain different sources of info and yields. Regularly there will be either a solitary contribution from a bigger past exchange or various data sources joining littler sums, and at most two yields: one for the installment, what's more, one reestablishing the change, accepting any, back to the sender. It ought to be noticed that fan - out, where an exchange relies upon a few exchanges, and those exchanges rely upon some more, isn't an issue here. There will never be the need to extricate a total independent duplicate of an exchange's history. 9. Privacy The conventional financial model accomplishes a degree of security by constraining access to data to the gatherings in question and the confided in outsider. The need to report all exchanges freely blocks this technique, yet system can be secured by interrupting the progress of data and the public key to be kept anonymous. People understand that someone tries to send to someone else without connecting to anybody. As an extra firewall, another key hold every action to stay coupled to a proprietor. Some connecting is as yet unavoidable with multi-input exchanges, which essentially uncover that their data sources were claimed by a similar proprietor. The hazard is that if the proprietor of a key is uncovered, connecting could uncover different exchanges that had a place with a similar proprietor. 10. Conclusion We are proposing a trust independent framework for electronic exchange. The coins are developed using digital signatures which identifies the authority of coins. Yet it is not @ IJTSRD | Unique Paper ID – IJTSRD33348 | completed without an approach to forestall twofold spending. To settle this, we proposed a shared system utilizing evidence of-work to record an open history of exchanges that rapidly turns out to be computationally unfeasible for an aggressor to change if genuine hubs control a larger part of CPU power. The system is hearty in its unstructured effortlessness. Hubs work at the same time with little coordination. They don't should be recognized, since messages are not steered to a specific spot and just should be conveyed on a best exertion premise. Hubs are free to leave and join again system. They vote with their CPU power, communicating their acknowledgment of legitimate squares by chipping away at broadening them and dismissing invalid squares by declining to deal with them. Any required guidelines and motivating forces can be authorized with this agreement component. References [1] W. Dai, "b-money," http://www.weidai.com/bmoney.txt, 1998. [2] H. Massias, X. S. Avila, and J.-J. Quisquater, "Design of a secure times tamping service with minimal trust requirements," In 20th Symposium on Information Theory in the Benelux, May 1999. [3] S. Haber, W. S. Stornetta, "How to time-stamp a digital document," In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991. [4] D. Bayer, S. Haber, W. S. Stornetta, "Improving the efficiency and reliability of digital time-stamping," In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993. [5] S. Haber, W.S. Stornetta, "Secure names for bit-strings," In Proceedings of the 4th ACM Conferenceon Computer and Communications Security, pages 28-35, April 1997. [6] A. Back, "Hashcash - a denial of service countermeasure," http://www.hashcash.org/papers/hashcash.pdf, 2002. [7] R. C. Merkle, "Protocols for public key cryptosystems," In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980. [8] W. Feller, "An introduction to probability theory and its applications," 1957. Volume – 4 | Issue – 6 | September-October 2020 Page 286




